Securing your MySQL server
0 likes311 views
MySQL security is not trivial. This presentation will walk you trough some of the more important decisions you have to take, when configuring a MySQL server instance
1 of 40
Download to read offline






































Ad
Recommended
Nagios Conference 2013 - Sheeri Cabral - Alerting With MySQL and Nagios



Nagios Conference 2013 - Sheeri Cabral - Alerting With MySQL and NagiosNagios This document discusses using Nagios to monitor MySQL databases. It describes official and third-party Nagios plugins for MySQL monitoring, including check_mysql, check_mysql_query, and a custom Perl script called mysql_health_check.pl. The custom script allows flexible monitoring of system and status variables, caching of results, and calculations of rates and comparisons to previous runs. Example Nagios command definitions are provided to monitor connections, query rates, uptime, and other metrics.
HTTP For the Good or the Bad



HTTP For the Good or the BadXavier Mertens A review of the webshells used by bad guys. How they are protected but also mistakes in their implementation. This talk was presented at the OWASP Belgium Chapter Meeting in May 2017.
Summer of Fuzz: macOS



Summer of Fuzz: macOSJeremy Brown Thinking of fuzzing applications on OS X can quickly lead to a passing conversation of "ooh exotic Mac stuff", "lets fuzz the kernel" or it can otherwise not be thought of as an exciting target, at least for looking for crashes in stuff other than Safari or the iPhone. While there are some intricacies and nuance involved, workaround for security protections to enable debugging and finding tools that work and work well, this research will detail how it can be done in a reliable way and make the topic more tangible and easier to digest, kind of like how people think about using AFL on Linux: it "just works". We'll explore some of the overlooked attack surface of file parsers and some network services on Mac, how to fuzz userland binaries and introduce a new fuzzer that makes setup and crash triage straightforward while poking at some Apple core apps and clients. Have you ever thought "This thing has got to have some bugs" but think twice because it's only on available on Mac and not worth the effort? If so, you may now find yourself both more motivated and better equipped to do some bug hunting on the sleek and eventually accommodating Mac OS.
Dynamic Database Credentials: Security Contingency Planning



Dynamic Database Credentials: Security Contingency PlanningSean Chittenden In a dynamic infrastructure world, let's stop pretending credentials aren't public knowledge in an organization and just assume that they have already been leaked, now what?
Two scoops of Django - Security Best Practices



Two scoops of Django - Security Best PracticesSpin Lai The presentation is based on the book 「Two scoops of Django : Best Practices for Django 1.5」by Daniel Greenfeld and Audrey Roy.
HTTP For the Good or the Bad - FSEC Edition



HTTP For the Good or the Bad - FSEC EditionXavier Mertens A review of the webshells used by bad guys. How they are protected but also mistakes in their implementation. This talk was updated and presented at the FSEC conference in Croatia, September 2017.
TLS/SSL MAC security flaw



TLS/SSL MAC security flawNate Lawson The document summarizes a security flaw in TLS/SSL that allows attackers to decrypt encrypted traffic by exploiting timing differences in error handling. Specifically, when padding is incorrect on encrypted records, servers may respond at different speeds depending on the stage the error is detected. This creates a timing side channel that can be used to gradually decrypt the last byte of records. The flaw was addressed in TLS 1.1 by standardizing error handling behavior. The document recommends not revealing too many error details and avoiding timing side channels to prevent similar attacks.
Unsecuring SSH



Unsecuring SSHJeremy Brown This document summarizes various techniques for attacking SSH clients and servers by exploiting insecure configurations and options. It begins with an introduction explaining the goals of understanding practical attacks beyond typical secure configuration advice. It then covers attacks using X11 forwarding, disabling strict host key checking, agent forwarding, and stream local binding. Specific examples are provided for man-in-the-middle attacks using ARP spoofing, capturing credentials by impersonating SSH servers, and escalating privileges by reusing SSH agent sockets. The document aims to demonstrate real-world risks of deviating from default secure configurations.
Attacking Big Data Land



Attacking Big Data LandJeremy Brown In this talk, we'll break down how one can exploit an ecosystem that enables management, querying, processing, and storage of, yes you guessed it, copious amounts of data. Hadoop and its many friends have been making their way into companies analyzing (sometimes, after massively collecting...) such data for years now, but they also make it easy to find organizations deploying things internally with security either off by default or otherwise exposed to various critical misconfigurations and access control issues.
If you're running engagements, this should also give you a headstart on what to look for, how to attack networks where these products are running along with a few good ways to make them more defendable. Because if you want to defend well, you need to optimize towards mitigating actual risk vs theoretical, and there's no better way to determine if attacks are real than trying them out yourself. Let's say you just want to better understand how to shell out on servers running Apache Cassandra, Drill, Mesos... well, it may add a few pages to your playbook.
(FYI this is the version of the slides without a conference template-- hopefully NoConName will share the templated version online as well)
[1.2] Трюки при анализе защищенности веб приложений – продвинутая версия - С...![[1.2] Трюки при анализе защищенности веб приложений – продвинутая версия - С...](https://cdn.slidesharecdn.com/ss_thumbnails/1-141207105957-conversion-gate02-thumbnail.jpg?width=560&fit=bounds)
![[1.2] Трюки при анализе защищенности веб приложений – продвинутая версия - С...](https://cdn.slidesharecdn.com/ss_thumbnails/1-141207105957-conversion-gate02-thumbnail.jpg?width=560&fit=bounds)
![[1.2] Трюки при анализе защищенности веб приложений – продвинутая версия - С...](https://cdn.slidesharecdn.com/ss_thumbnails/1-141207105957-conversion-gate02-thumbnail.jpg?width=560&fit=bounds)
![[1.2] Трюки при анализе защищенности веб приложений – продвинутая версия - С...](https://cdn.slidesharecdn.com/ss_thumbnails/1-141207105957-conversion-gate02-thumbnail.jpg?width=560&fit=bounds)
[1.2] Трюки при анализе защищенности веб приложений – продвинутая версия - С...OWASP Russia This document summarizes techniques for detecting XXE and SSRF vulnerabilities using DNS records. It describes how an attacker can configure their own DNS server to return their IP address instead of the actual domain, allowing them to detect if the application makes external requests. It also discusses challenges of detecting these vulnerabilities, and provides examples of how to test for them including checking web server access logs for requests to domains controlled by the attacker. The document then covers additional techniques like bypassing content security policies, detecting real users behind Cloudflare, and exploiting URL encoding to bypass input filtering.
URL to HTML



URL to HTMLFrancois Marier What happens in between the time you type a URL in your browser and the time you see the fully rendered page.
Integrity protection for third-party JavaScript



Integrity protection for third-party JavaScriptFrancois Marier Modern web applications depend on a lot of auxiliary scripts which are often hosted on third-party CDNs. Should an attacker be able to tamper with the files hosted on such a CDN, millions of sites could be compromised. Web developers need a way to guarantee the integrity of scripts hosted elsewhere.
This is the motivation behind a new addition to the web platform being introduced by the W3C: sub-resource integrity. Both Firefox and Chrome have initial implementations of this new specification and a few early adopters are currently evaluating this feature.
Da APK al Golden Ticket



Da APK al Golden TicketGiuseppe Trotta An attacker was able to gain access to an internal network by phishing a secretary's smartphone. They then used lateral movement techniques like pass-the-hash to escalate privileges and access sensitive files. This included obtaining Domain Admin credentials for the "adm.arazzi" user. The attacker was ultimately able to exfiltrate data and establish persistence on the network.
User Credential handling in Web Applications done right



User Credential handling in Web Applications done righttladesignz In my work I often see very bad practices how the users' passwords are treated in web applications. This is a short summary of the current state of the art, how to do it the right way.
Application Security around OWASP Top 10



Application Security around OWASP Top 10Sastry Tumuluri Caution: This is a dated presentation; uploaded for reference. While the principles remain valid, specifics may have changed.
This presentation was made for software developers in Chandigarh - as a part of the NULL & OWASP Chandigarh Chapter activities.
It covers the basics of secure software development and secure coding using OWASP Top 10 as a broad guide.
Web application Security



Web application SecurityLee C This document provides a summary of a presentation on web application security. It introduces the presenter and outlines topics that will be covered, including injection attacks like SQL injection and cross-site scripting (XSS), cross-site request forgery (CSRF), password storage techniques, and defenses against these attacks. Examples of each attack type are demonstrated. Defenses like input validation, output encoding, anti-XSS libraries, synchronizer tokens for CSRF, and password hashing with salts are discussed. The importance of secure coding practices and continued learning are emphasized.
HashiCorp Vault Workshop:幫 Credentials 找個窩



HashiCorp Vault Workshop:幫 Credentials 找個窩smalltown Credentials 究竟該儲存在哪邊才算安全一直是個很尷尬的問題,外洩的消息更是時有耳聞;而一般的應用程式設計時,很少考量到如何定期去更新 Credentials,這時 DevOps 的救星 HashiCorp 發現了大家的需求,因而推出 Vault 來作為 Credentials 的歸宿,其主要最大的兩大功能就是讓大家可以將 Credentials 安心地存放在其中,並且針對一些特定的應用服務提供動態 Credentials 的功能,此 Workshop 主要分成三個主軸:
- Vault 基本使用
- Dynamic Credentials 使用方式
- Vault 在生產環境使用的最佳準則
Using npm to Manage Your Projects for Fun and Profit - USEFUL INFO IN NOTES!



Using npm to Manage Your Projects for Fun and Profit - USEFUL INFO IN NOTES!async_io The document discusses how to use npm (Node Package Manager) to manage projects and dependencies. It recommends initializing projects using npm init or express, which will generate a package.json file. This file is used to specify dependencies, dependency versions, private packages, devDependencies, and engine requirements. Precise dependency specifications and semantic versioning help manage updates. npm handles automated installation and updating of dependencies.
Mitigating CSRF with two lines of codes



Mitigating CSRF with two lines of codesMinhaz A V This presentation was used in OWASP Taiwan Week 2017 at Taipei & Kaohsiung. It talks about what Cross Site Request Forgery is, what are different ways to prevent it. And how it can be mitigated with OWASP CSRF Protector with just two lines of codes.
DDoS: Practical Survival Guide



DDoS: Practical Survival GuideHLL The presentation was delivered by Alexander Lyamin, CEO of HLL (Qrator network), at the RIPE 64 Meeting on 16 – 20 April 2012 in Ljubljana.
DDoS mitigation techniques: poor mans version (low rate HTTP attacks). Every solution works. Not always. Not for everyone.
Integrity protection for third-party JavaScript



Integrity protection for third-party JavaScriptFrancois Marier Modern web applications depend on a lot of auxiliary scripts which are often hosted on third-party CDNs. Should an attacker be able to tamper with the files hosted on such a CDN, millions of sites could be compromised. Web developers need a way to guarantee the integrity of scripts hosted elsewhere.
This is the motivation behind a new addition to the web platform being introduced by the W3C: sub-resource integrity (http://www.w3.org/TR/SRI/). Both Firefox and Chrome have initial implementations of this new specification and a few early adopters such as Github are currently evaluating this feature.
When Crypto Attacks! (Yahoo 2009)



When Crypto Attacks! (Yahoo 2009)Nate Lawson In-depth list of attacks against various crypto implementations. Developers seem to have gotten the message not to design their own ciphers. Now, we're trying to get the message out that you shouldn't be implementing your own crypto protocols or constructions, using low-level crypto libraries. Instead, developers should work at a higher level, using libraries like GPGME, Keyczar, or cryptlib. If you do end up designing/implementing your own construction, getting it reviewed by a third party is an expensive but vital task.
Webinar slides: How to Secure MongoDB with ClusterControl



Webinar slides: How to Secure MongoDB with ClusterControlSeveralnines Watch the slides of our webinar on “How to secure MongoDB with ClusterControl” and find out about the essential steps necessary to secure MongoDB and how to verify if your MongoDB instance is safe.
The recent MongoDB ransom hack caused a lot of damage and outages, while it could have been prevented with maybe two or three simple configuration changes. MongoDB offers a lot of security features out of the box, however it disables them by default.
In this webinar, we explain which configuration changes are necessary to enable MongoDB’s security features, and how to test if your setup is secure after enablement. We also demonstrate how ClusterControl enables security on default installations. And we cover how to leverage the ClusterControl advisors and the MongoDB Audit Log to constantly scan your environment, and harden your security even more.
AGENDA
What is the MongoDB ransom hack?
What other security threats are valid for MongoDB?
How to enable authentication / authorisation
How to secure MongoDB from ransomware
How to scan your system
ClusterControl MongoDB security advisors
Live Demo
SPEAKER
Art van Scheppingen is a Senior Support Engineer at Severalnines. He’s a pragmatic MySQL and Database expert with over 15 years experience in web development. He previously worked at Spil Games as Head of Database Engineering, where he kept a broad vision upon the whole database environment: from MySQL to Couchbase, Vertica to Hadoop and from Sphinx Search to SOLR. He regularly presents his work and projects at various conferences (Percona Live, FOSDEM) and related meetups.
Practical django secuirty



Practical django secuirtyAndy Dai The document discusses the top 10 security issues from the OWASP 2013 report and provides solutions for securing a Django application. It covers issues like injection, broken authentication, cross-site scripting, sensitive data exposure, and insecure configurations. The document emphasizes that software security is difficult but important, and recommends following best practices like input validation, access control, and using security features built into Django.
JavaFest. Nanne Baars. Web application security for developers



JavaFest. Nanne Baars. Web application security for developersFestGroup Security is an important topic for developers however security is often an afterthought in a project. This presentation will focus on practices which developers need to be aware of, and make security fun again. This is an in depth talk about 10 topics not an overview for security best practices.
Security in NodeJS applications



Security in NodeJS applicationsDaniel Garcia (a.k.a cr0hn) This document provides an overview of common security vulnerabilities in Node.js code and their solutions. It discusses injection flaws like SQL injection and log injection, broken authentication and session management issues like insecure cookie handling, cross-site scripting vulnerabilities, insecure direct object references, sensitive data exposure without encryption, cross-site request forgery, and unvalidated redirects/forwards. For each vulnerability, it provides an example of vulnerable Node.js code, how an attacker could exploit it, and recommendations for more secure coding practices. The goal is to help developers learn security best practices through examples of real flaws and their fixes.
Challenges Building Secure Mobile Applications



Challenges Building Secure Mobile ApplicationsMasabi This document discusses the challenges of building secure mobile applications. It covers why security is important for mobile, how to secure applications in an insecure mobile environment, and case studies of mobile security implementations. Some key points discussed include using HTTPS for end-to-end security, securing the key exchange process, ensuring strong entropy for keys, implementing message integrity checks, and supporting a wide range of mobile devices and networks.
Django Web Application Security



Django Web Application Securitylevigross This document discusses security best practices for Django web applications. It begins by introducing the author and their background in Python, Django, and computer security. It then covers common web vulnerabilities and attacks like information disclosure, input validation issues, session hijacking, and denial of service. Throughout, it provides recommendations for how to configure Django and code defensively to mitigate these risks, such as using parameterized queries, input sanitization, secure sessions, and cross-site request forgery protection. It emphasizes adopting a layered security approach and being vigilant about updates and monitoring.
So you want to be a security expert



So you want to be a security expertRoyce Davis This document discusses techniques for penetration testing without uploading malware. It describes using DCERPC and Metasploit modules to execute commands, dump passwords, and extract all domain hashes from a domain controller. Uploading shells can be detected, so these methods leverage native Windows functions like the Service Control Manager to perform tasks without leaving artifacts. Command execution through psexec allows tasks like backing up registry hives to extract hashes offline without antivirus detection.
Application and Server Security



Application and Server SecurityBrian Pontarelli This is my presentation from Denver Startup Week 2016 on security for applications and servers. This presentation covers everything you need to know about securing a Linux server and your application.
Ad
More Related Content
What's hot (20)
Attacking Big Data Land



Attacking Big Data LandJeremy Brown In this talk, we'll break down how one can exploit an ecosystem that enables management, querying, processing, and storage of, yes you guessed it, copious amounts of data. Hadoop and its many friends have been making their way into companies analyzing (sometimes, after massively collecting...) such data for years now, but they also make it easy to find organizations deploying things internally with security either off by default or otherwise exposed to various critical misconfigurations and access control issues.
If you're running engagements, this should also give you a headstart on what to look for, how to attack networks where these products are running along with a few good ways to make them more defendable. Because if you want to defend well, you need to optimize towards mitigating actual risk vs theoretical, and there's no better way to determine if attacks are real than trying them out yourself. Let's say you just want to better understand how to shell out on servers running Apache Cassandra, Drill, Mesos... well, it may add a few pages to your playbook.
(FYI this is the version of the slides without a conference template-- hopefully NoConName will share the templated version online as well)
[1.2] Трюки при анализе защищенности веб приложений – продвинутая версия - С...![[1.2] Трюки при анализе защищенности веб приложений – продвинутая версия - С...](https://cdn.slidesharecdn.com/ss_thumbnails/1-141207105957-conversion-gate02-thumbnail.jpg?width=560&fit=bounds)
![[1.2] Трюки при анализе защищенности веб приложений – продвинутая версия - С...](https://cdn.slidesharecdn.com/ss_thumbnails/1-141207105957-conversion-gate02-thumbnail.jpg?width=560&fit=bounds)
![[1.2] Трюки при анализе защищенности веб приложений – продвинутая версия - С...](https://cdn.slidesharecdn.com/ss_thumbnails/1-141207105957-conversion-gate02-thumbnail.jpg?width=560&fit=bounds)
![[1.2] Трюки при анализе защищенности веб приложений – продвинутая версия - С...](https://cdn.slidesharecdn.com/ss_thumbnails/1-141207105957-conversion-gate02-thumbnail.jpg?width=560&fit=bounds)
[1.2] Трюки при анализе защищенности веб приложений – продвинутая версия - С...OWASP Russia This document summarizes techniques for detecting XXE and SSRF vulnerabilities using DNS records. It describes how an attacker can configure their own DNS server to return their IP address instead of the actual domain, allowing them to detect if the application makes external requests. It also discusses challenges of detecting these vulnerabilities, and provides examples of how to test for them including checking web server access logs for requests to domains controlled by the attacker. The document then covers additional techniques like bypassing content security policies, detecting real users behind Cloudflare, and exploiting URL encoding to bypass input filtering.
URL to HTML



URL to HTMLFrancois Marier What happens in between the time you type a URL in your browser and the time you see the fully rendered page.
Integrity protection for third-party JavaScript



Integrity protection for third-party JavaScriptFrancois Marier Modern web applications depend on a lot of auxiliary scripts which are often hosted on third-party CDNs. Should an attacker be able to tamper with the files hosted on such a CDN, millions of sites could be compromised. Web developers need a way to guarantee the integrity of scripts hosted elsewhere.
This is the motivation behind a new addition to the web platform being introduced by the W3C: sub-resource integrity. Both Firefox and Chrome have initial implementations of this new specification and a few early adopters are currently evaluating this feature.
Da APK al Golden Ticket



Da APK al Golden TicketGiuseppe Trotta An attacker was able to gain access to an internal network by phishing a secretary's smartphone. They then used lateral movement techniques like pass-the-hash to escalate privileges and access sensitive files. This included obtaining Domain Admin credentials for the "adm.arazzi" user. The attacker was ultimately able to exfiltrate data and establish persistence on the network.
User Credential handling in Web Applications done right



User Credential handling in Web Applications done righttladesignz In my work I often see very bad practices how the users' passwords are treated in web applications. This is a short summary of the current state of the art, how to do it the right way.
Application Security around OWASP Top 10



Application Security around OWASP Top 10Sastry Tumuluri Caution: This is a dated presentation; uploaded for reference. While the principles remain valid, specifics may have changed.
This presentation was made for software developers in Chandigarh - as a part of the NULL & OWASP Chandigarh Chapter activities.
It covers the basics of secure software development and secure coding using OWASP Top 10 as a broad guide.
Web application Security



Web application SecurityLee C This document provides a summary of a presentation on web application security. It introduces the presenter and outlines topics that will be covered, including injection attacks like SQL injection and cross-site scripting (XSS), cross-site request forgery (CSRF), password storage techniques, and defenses against these attacks. Examples of each attack type are demonstrated. Defenses like input validation, output encoding, anti-XSS libraries, synchronizer tokens for CSRF, and password hashing with salts are discussed. The importance of secure coding practices and continued learning are emphasized.
HashiCorp Vault Workshop:幫 Credentials 找個窩



HashiCorp Vault Workshop:幫 Credentials 找個窩smalltown Credentials 究竟該儲存在哪邊才算安全一直是個很尷尬的問題,外洩的消息更是時有耳聞;而一般的應用程式設計時,很少考量到如何定期去更新 Credentials,這時 DevOps 的救星 HashiCorp 發現了大家的需求,因而推出 Vault 來作為 Credentials 的歸宿,其主要最大的兩大功能就是讓大家可以將 Credentials 安心地存放在其中,並且針對一些特定的應用服務提供動態 Credentials 的功能,此 Workshop 主要分成三個主軸:
- Vault 基本使用
- Dynamic Credentials 使用方式
- Vault 在生產環境使用的最佳準則
Using npm to Manage Your Projects for Fun and Profit - USEFUL INFO IN NOTES!



Using npm to Manage Your Projects for Fun and Profit - USEFUL INFO IN NOTES!async_io The document discusses how to use npm (Node Package Manager) to manage projects and dependencies. It recommends initializing projects using npm init or express, which will generate a package.json file. This file is used to specify dependencies, dependency versions, private packages, devDependencies, and engine requirements. Precise dependency specifications and semantic versioning help manage updates. npm handles automated installation and updating of dependencies.
Mitigating CSRF with two lines of codes



Mitigating CSRF with two lines of codesMinhaz A V This presentation was used in OWASP Taiwan Week 2017 at Taipei & Kaohsiung. It talks about what Cross Site Request Forgery is, what are different ways to prevent it. And how it can be mitigated with OWASP CSRF Protector with just two lines of codes.
DDoS: Practical Survival Guide



DDoS: Practical Survival GuideHLL The presentation was delivered by Alexander Lyamin, CEO of HLL (Qrator network), at the RIPE 64 Meeting on 16 – 20 April 2012 in Ljubljana.
DDoS mitigation techniques: poor mans version (low rate HTTP attacks). Every solution works. Not always. Not for everyone.
Integrity protection for third-party JavaScript



Integrity protection for third-party JavaScriptFrancois Marier Modern web applications depend on a lot of auxiliary scripts which are often hosted on third-party CDNs. Should an attacker be able to tamper with the files hosted on such a CDN, millions of sites could be compromised. Web developers need a way to guarantee the integrity of scripts hosted elsewhere.
This is the motivation behind a new addition to the web platform being introduced by the W3C: sub-resource integrity (http://www.w3.org/TR/SRI/). Both Firefox and Chrome have initial implementations of this new specification and a few early adopters such as Github are currently evaluating this feature.
When Crypto Attacks! (Yahoo 2009)



When Crypto Attacks! (Yahoo 2009)Nate Lawson In-depth list of attacks against various crypto implementations. Developers seem to have gotten the message not to design their own ciphers. Now, we're trying to get the message out that you shouldn't be implementing your own crypto protocols or constructions, using low-level crypto libraries. Instead, developers should work at a higher level, using libraries like GPGME, Keyczar, or cryptlib. If you do end up designing/implementing your own construction, getting it reviewed by a third party is an expensive but vital task.
Webinar slides: How to Secure MongoDB with ClusterControl



Webinar slides: How to Secure MongoDB with ClusterControlSeveralnines Watch the slides of our webinar on “How to secure MongoDB with ClusterControl” and find out about the essential steps necessary to secure MongoDB and how to verify if your MongoDB instance is safe.
The recent MongoDB ransom hack caused a lot of damage and outages, while it could have been prevented with maybe two or three simple configuration changes. MongoDB offers a lot of security features out of the box, however it disables them by default.
In this webinar, we explain which configuration changes are necessary to enable MongoDB’s security features, and how to test if your setup is secure after enablement. We also demonstrate how ClusterControl enables security on default installations. And we cover how to leverage the ClusterControl advisors and the MongoDB Audit Log to constantly scan your environment, and harden your security even more.
AGENDA
What is the MongoDB ransom hack?
What other security threats are valid for MongoDB?
How to enable authentication / authorisation
How to secure MongoDB from ransomware
How to scan your system
ClusterControl MongoDB security advisors
Live Demo
SPEAKER
Art van Scheppingen is a Senior Support Engineer at Severalnines. He’s a pragmatic MySQL and Database expert with over 15 years experience in web development. He previously worked at Spil Games as Head of Database Engineering, where he kept a broad vision upon the whole database environment: from MySQL to Couchbase, Vertica to Hadoop and from Sphinx Search to SOLR. He regularly presents his work and projects at various conferences (Percona Live, FOSDEM) and related meetups.
Practical django secuirty



Practical django secuirtyAndy Dai The document discusses the top 10 security issues from the OWASP 2013 report and provides solutions for securing a Django application. It covers issues like injection, broken authentication, cross-site scripting, sensitive data exposure, and insecure configurations. The document emphasizes that software security is difficult but important, and recommends following best practices like input validation, access control, and using security features built into Django.
JavaFest. Nanne Baars. Web application security for developers



JavaFest. Nanne Baars. Web application security for developersFestGroup Security is an important topic for developers however security is often an afterthought in a project. This presentation will focus on practices which developers need to be aware of, and make security fun again. This is an in depth talk about 10 topics not an overview for security best practices.
Security in NodeJS applications



Security in NodeJS applicationsDaniel Garcia (a.k.a cr0hn) This document provides an overview of common security vulnerabilities in Node.js code and their solutions. It discusses injection flaws like SQL injection and log injection, broken authentication and session management issues like insecure cookie handling, cross-site scripting vulnerabilities, insecure direct object references, sensitive data exposure without encryption, cross-site request forgery, and unvalidated redirects/forwards. For each vulnerability, it provides an example of vulnerable Node.js code, how an attacker could exploit it, and recommendations for more secure coding practices. The goal is to help developers learn security best practices through examples of real flaws and their fixes.
Challenges Building Secure Mobile Applications



Challenges Building Secure Mobile ApplicationsMasabi This document discusses the challenges of building secure mobile applications. It covers why security is important for mobile, how to secure applications in an insecure mobile environment, and case studies of mobile security implementations. Some key points discussed include using HTTPS for end-to-end security, securing the key exchange process, ensuring strong entropy for keys, implementing message integrity checks, and supporting a wide range of mobile devices and networks.
Django Web Application Security



Django Web Application Securitylevigross This document discusses security best practices for Django web applications. It begins by introducing the author and their background in Python, Django, and computer security. It then covers common web vulnerabilities and attacks like information disclosure, input validation issues, session hijacking, and denial of service. Throughout, it provides recommendations for how to configure Django and code defensively to mitigate these risks, such as using parameterized queries, input sanitization, secure sessions, and cross-site request forgery protection. It emphasizes adopting a layered security approach and being vigilant about updates and monitoring.
Similar to Securing your MySQL server (20)
So you want to be a security expert



So you want to be a security expertRoyce Davis This document discusses techniques for penetration testing without uploading malware. It describes using DCERPC and Metasploit modules to execute commands, dump passwords, and extract all domain hashes from a domain controller. Uploading shells can be detected, so these methods leverage native Windows functions like the Service Control Manager to perform tasks without leaving artifacts. Command execution through psexec allows tasks like backing up registry hives to extract hashes offline without antivirus detection.
Application and Server Security



Application and Server SecurityBrian Pontarelli This is my presentation from Denver Startup Week 2016 on security for applications and servers. This presentation covers everything you need to know about securing a Linux server and your application.
Tatu: ssh as a service



Tatu: ssh as a servicePino deCandia Tatu is an Open Source project that automates SSH certificate and bastion management for OpenStack clouds.
DEF CON 23 - CASSIDY LEVERETT LEE - switches get stitches



DEF CON 23 - CASSIDY LEVERETT LEE - switches get stitchesFelipe Prado This document discusses network security monitoring of industrial control systems. It provides tips on safely capturing network data from ICS environments, such as using test environments first and working with vendors. It recommends starting with basic open-source tools like SecurityOnion and tcpdump. The document highlights focusing on top talkers, bandwidth usage, encrypted communications, and anomalies. It stresses the importance of including both IT and OT stakeholders and having a plan to address security responsibilities and upgrades.
Training Slides: 302 - Securing Your Cluster With SSL



Training Slides: 302 - Securing Your Cluster With SSLContinuent This document discusses securing a Tungsten cluster with SSL. It explains what SSL is and why it is used. It then covers deploying SSL for cluster communications and for the Tungsten connector. For the cluster, SSL is enabled in tungsten.ini and certificates are generated and distributed. For the connector in proxy mode, MySQL certificates must be imported into keystores and SSL configured from the connector to the database. SSL can also be configured from the application to the connector. Successful SSL encryption is verified using tcpdump and checking the Tungsten connection status. The next steps will cover the Tungsten dashboard.
Securing Cassandra for Compliance



Securing Cassandra for ComplianceDataStax This document discusses securing Cassandra for compliance or paranoia. It covers encrypting data at rest and on the wire, authentication and authorization, and securing management tools like JMX. Encrypting data at rest can be done with options like dmcrypt, Vormetric, or DSE encryption. Node to node encryption and SSL is recommended to encrypt data on the wire. Role-based access control in Cassandra 2.2 allows for authentication and authorization. Securing JMX involves SSL and password-based authentication.
Hardening cassandra q2_2016



Hardening cassandra q2_2016zznate Describes in detail the security architecture of Apache Cassandra. We discuss encryption at rest, encryption on the wire, authentication and authorization and securing JMX and management tools
Multiple instances second method



Multiple instances second methodVasudeva Rao This document outlines how to configure multiple instances of MySQL on a single server. It describes commenting out port settings in the my.cnf file, creating configuration blocks for two instances, cloning the data directory for the second instance, and using mysqld_multi to start and manage the instances. Running mysqld_multi report verifies that both instances are running on different ports (3306 and 3307). Clients can connect to each instance by specifying the unique port or socket file location.
Defending Against Attacks With Rails



Defending Against Attacks With RailsTony Amoyal Let's face it, the web can be a dangerous place. So how do you protect your users and yourself? Tony Amoyal answers that and more as he shows how Rails can help protect against miscreants.
X64服务器 lnmp服务器部署标准 new



X64服务器 lnmp服务器部署标准 newYiwei Ma The document provides guidelines for deploying an L.N.M.P environment on a 64-bit server. It specifies directory locations for source code, installed software, scripts and logs. It also outlines steps to update the system, install and configure MySQL, Nginx, PHP and other packages, including compiling Nginx with specific modules and options, setting Nginx as a service, and enabling syntax highlighting for Nginx configuration files.
SQL Server Exploitation, Escalation, Pilfering - AppSec USA 2012



SQL Server Exploitation, Escalation, Pilfering - AppSec USA 2012Scott Sutherland During this presentation attendees will be introduced to lesser known, yet significant vulnerabilities in SQL Server implementations related to common trust relationships, misconfigurations, and weak default settings. The issues that will be covered are often leveraged by attackers to gain unauthorized access to high value systems, applications, and sensitive data. An overview of each issue, common vectors of attack, and manual techniques will be covered. Finally newly created Metasploit modules and TSQL scripts will be demonstrated that help automate the attacks. This presentation will be valuable to penetration testers who are looking for faster ways to gain access to critical data and systems. Additionally, it should be worth while for developers and database administrators who are interested in gaining a better understanding of how to protect their applications and databases from these attacks.
More security blogs by the authors can be found @
https://www.netspi.com/blog/
Password (in)security



Password (in)securityEnrico Zimuel The 7th June 2012 Linkedin was hacked. More than 6 million LinkedIn passwords was compromised. The real shocking news was not the theft but the fact that the attackers were able to decrypt many of these passwords. Why it happened? The answer is simple: a bad design of the password security. In this talk I presented how to choose "secure" user's passwords and how to safely store it from a programmer's perspective.
This talk has been presented during the MOCA 2012, http://moca.olografix.org/moca2012
How to Use Cryptography Properly: The Common Mistakes People Make When Using ...



How to Use Cryptography Properly: The Common Mistakes People Make When Using ...POSSCON Andy Watson
Ionic Security - Lead Developer
POSSCON 2015
4/14/2015
Security Track - 11:00 AM Talk
Asterisk_MySQL_Cluster_Presentation.pdf



Asterisk_MySQL_Cluster_Presentation.pdfDelphini Systems Consultoria e Treinamento This document discusses setting up an Asterisk cluster with MySQL replication. It describes installing Asterisk and MySQL, configuring Asterisk Realtime Architecture (ARA) to store configurations and dial plans in a MySQL database, and setting up MySQL replication between a master and slave databases to share information across the Asterisk cluster. Key steps include creating MySQL users, tables, and configuring the master and slaves for replication, as well as configuring Asterisk's res_mysql.conf file to connect to the database.
P@ssw0rds



P@ssw0rdsWill Alexander This document discusses password security and best practices. It notes that 66% of corporate network breaches are due to weak passwords. Passwords should not be stored in plaintext or with reversible encryption, but rather hashed with salts. Hashing strengthens security but using salts is important to avoid rainbow table attacks. The document recommends choosing long, unique passphrases rather than short, dictionary words for passwords. It also advocates the use of password managers and two-factor authentication for strongest security.
Secure WordPress Development Practices



Secure WordPress Development PracticesBrandon Dove Keep user data secure by sanitizing all input and output, using nonces to verify requests, and whitelisting/blacklisting known safe data formats. Common attacks like XSS, CSRF and viruses can be prevented by escaping output, validating referrers, and using antivirus software. The document provides links to WordPress resources on data validation and security best practices.
Securing Cassandra



Securing CassandraInstaclustr Securing Cassandra involves considering authentication, authorization, encryption, and availability. Authentication involves setting an authenticator like PasswordAuthentication and checking credentials. Authorization controls permissions through an authorizer like CassandraAuthorizer. Encryption can encrypt internode communication and data at rest. Availability requires considering things like resource throttling, system keyspace replication, and denial of service attacks.
Instaclustr: Securing Cassandra



Instaclustr: Securing CassandraDataStax Academy Security is often an afterthought; configured and applied at the last minute before rolling out a new system. Instaclustr has deployed Cassandra for customers with many different requirements.
From deployments in Heroku requiring total public access through to private data centres, we will walk you through securing Cassandra the right way.
Cassandra and security



Cassandra and securityBen Bromhead Security is often an afterthought; configured and applied at the last minute before rolling out a new system. Instaclustr has deployed Cassandra for customers with many different requirements.
From deployments in Heroku requiring total public access through to private data centres, we will walk you through securing Cassandra the right way.
Owning computers without shell access dark



Owning computers without shell access darkRoyce Davis My Talk From DerbyCon 3.0.
Link to Video Presentation:
https://www.youtube.com/watch?v=8hx6QG4SMdc
Ad
More from Marian Marinov (20)
How to start and then move forward in IT



How to start and then move forward in ITMarian Marinov This is a presentation on how to start and how to move forward in IT
Thinking about highly-available systems and their setup



Thinking about highly-available systems and their setupMarian Marinov In this talk you will learn about the things you need to consider when building a HA system.
We will start with basic networking, then cover some storage options and we will finish with configuring the brains of it using corosync+pacemaker.
There are many links in the presentation for additional reading.
Understanding your memory usage under Linux



Understanding your memory usage under LinuxMarian Marinov This talk describes how the linux kernel works with the memory and covers areas that are not very well understood, like memory reclaim and OOM killer.
How to implement PassKeys in your application



How to implement PassKeys in your applicationMarian Marinov PassKeys is relatively new way of authentication. This presentation aims to provide a bit of guidance on how you can implement them in your own application.
Dev.bg DevOps March 2024 Monitoring & Logging



Dev.bg DevOps March 2024 Monitoring & LoggingMarian Marinov The document discusses Marian Marinov's experience monitoring various systems and infrastructure. He aims to have a single solution for log and metrics collection but ends up with multiple Grafana dashboards and different log collectors. Collectd was found to be the easiest to set up and provides the most out-of-the-box metrics, while solutions like Elasticsearch and Kibana require too many resources for smaller setups. There is no single solution that can monitor everything.
Basic presentation of cryptography mechanisms



Basic presentation of cryptography mechanismsMarian Marinov This document summarizes Marian Marinov's presentation on cryptography. It discusses password cracking using John the Ripper, analyzing languages using frequency analysis to crack codes like the Enigma machine. It also covers chosen plaintext/ciphertext attacks, known plaintext attacks, and how these were used to crack protocols like SSL. Common attacks on SSL like BEAST, CRIME, and POODLE are outlined. Finally, cracking WiFi passwords using tools like Aircrack-ng is briefly discussed.
Microservices: Benefits, drawbacks and are they for me?



Microservices: Benefits, drawbacks and are they for me?Marian Marinov This presentation outlines the benefits and drawbacks of using microservices and designing your application as microsevices.
Introduction and replication to DragonflyDB



Introduction and replication to DragonflyDBMarian Marinov This is a talk that introduces the migration from Redis to DragonflyDB and shares the some numbers from dragonflydb.io website.
Message Queuing - Gearman, Mosquitto, Kafka and RabbitMQ



Message Queuing - Gearman, Mosquitto, Kafka and RabbitMQMarian Marinov This document summarizes and compares several message queuing systems: Gearman, Mosquitto, Kafka, and RabbitMQ. It discusses their pub/sub models, broker architectures, message/topic storage and delivery methods, actual communication protocols, and Java ecosystems. The key points are that these systems provide asynchronous communication between applications using a broker, each with different architectures, storage and delivery semantics, and Java client libraries.
How to successfully migrate to DevOps .pdf



How to successfully migrate to DevOps .pdfMarian Marinov The document discusses considerations for adopting DevOps practices. It compares traditional system administration approaches to infrastructure deployment versus using DevOps tools like Terraform and Nomad. While tools abstract complexity, it is important to understand the underlying systems. When adopting DevOps, teams should ensure adequate expertise in tools, thoroughly test deployments, and document environments. Abstraction through tools can cause issues if providers do not support needed functionality or changes require modifying tool configurations instead of the systems directly.
How to survive in the work from home era



How to survive in the work from home eraMarian Marinov This document discusses strategies for working securely from home. It covers hardware availability and security issues when working remotely. On the hardware side, it recommends having backup equipment like a second laptop or WiFi in case of equipment failure. For security, it emphasizes that convenience often comes at the cost of security. The biggest security risks are viruses, malware, and phishing attacks. It provides strategies for securing the operating system, browser, and email client to reduce these risks, such as using separate profiles, disabling remote content loading, and not automatically opening files. Virtual machines are recommended for opening suspicious files to isolate any potential compromise. Overall, the document stresses balancing security with convenience when working remotely.
Managing sysadmins



Managing sysadminsMarian Marinov Management of system administrators and devops teams is different then managing Developers.
This presentation shows key differences and what to worry about :)
Improve your storage with bcachefs



Improve your storage with bcachefsMarian Marinov Introduction and rationale behind the bcachefs.
This presentations explains why bcachefs exists and how you can mange one.
Control your service resources with systemd 



Control your service resources with systemd Marian Marinov This document discusses using systemd to manage control groups (cGroups) and set resource limits for processes and services. It describes how systemd simplified cGroup management by creating a cGroup for each service and allowing configuration via service files and drop-in files. Specific configuration options like memory and CPU limits can be set directly in the service file, via a slice file that multiple services reference, or using systemctl commands. Systemd provides unified management of cGroups and services.
Comparison of-foss-distributed-storage



Comparison of-foss-distributed-storageMarian Marinov This document summarizes Marian Marinov's testing and experience with various distributed filesystems including CephFS, GlusterFS, MooseFS, OrangeFS, and BeeGFS. Some key findings are:
- CephFS requires significant resources but lacks redundancy for small clusters. GlusterFS offers redundancy but can have high CPU usage.
- MooseFS and OrangeFS were easy to setup but MooseFS offered better reliability and stats.
- Performance testing found MooseFS and NFS+Ceph to have better small file creation times than GlusterFS and OrangeFS. Network latency was identified as a major factor impacting distributed filesystem performance.
- Tuning efforts focused on NFS
Защо и как да обогатяваме знанията си?



Защо и как да обогатяваме знанията си?Marian Marinov Презентацията от лекцията ми на DEV.BG ALL IN ONE
Sysadmin vs. dev ops



Sysadmin vs. dev opsMarian Marinov This document compares and contrasts the roles of system administrators (sysadmins) and DevOps engineers. It discusses that sysadmins are primarily focused on installing, configuring, and maintaining operating systems, software, and company products on local servers and PCs. DevOps engineers, on the other hand, work with cloud platforms, APIs, infrastructure as code, automation tools, and focus on monitoring through tools like Elasticsearch and Prometheus. It also provides examples of how sysadmins and DevOps engineers differ in their approaches to configuration management, monitoring, and debugging infrastructure issues.
DoS and DDoS mitigations with eBPF, XDP and DPDK



DoS and DDoS mitigations with eBPF, XDP and DPDKMarian Marinov The document compares eBPF, XDP and DPDK for packet inspection. It describes the speaker's experience using these tools to build a virtual machine that can handle 10Gbps of traffic and drop packets to mitigate DDoS attacks. It details how eBPF and XDP were able to achieve higher packet drop rates than iptables or a custom module. While DPDK could drop traffic at line rate, it required specialized hardware and expertise. Ultimately, XDP provided the best balance of performance, driver support and programmability using eBPF to drop millions of packets per second.
Challenges with high density networks



Challenges with high density networksMarian Marinov Marian Marinov is the chief system architect and head of the DevOps department at SiteGround.com. He discussed the challenges of high-density networks including large broadcast domains, limited MAC/ARP tables, and bandwidth constraints. Some solutions proposed were using VLANs, layered network designs, and overlay technologies like VXLAN and NVGRE to divide the network into smaller segments and increase scalability.
SiteGround building automation



SiteGround building automationMarian Marinov At SiteGround we built our own building automation and this is the PCB we designed to control the lights in the office.
Ad
Recently uploaded (20)
Degree_of_Automation.pdf for Instrumentation and industrial specialist



Degree_of_Automation.pdf for Instrumentation and industrial specialistshreyabhosale19 degree of Automation for industrial and Instrumentation learners.
DT REPORT by Tech titan GROUP to introduce the subject design Thinking



DT REPORT by Tech titan GROUP to introduce the subject design ThinkingDhruvChotaliya2 This a Report of a Design Thinking
Data Structures_Introduction to algorithms.pptx



Data Structures_Introduction to algorithms.pptxRushaliDeshmukh2 Concept of Problem Solving, Introduction to Algorithms, Characteristics of Algorithms, Introduction to Data Structure, Data Structure Classification (Linear and Non-linear, Static and Dynamic, Persistent and Ephemeral data structures), Time complexity and Space complexity, Asymptotic Notation - The Big-O, Omega and Theta notation, Algorithmic upper bounds, lower bounds, Best, Worst and Average case analysis of an Algorithm, Abstract Data Types (ADT)
Level 1-Safety.pptx Presentation of Electrical Safety



Level 1-Safety.pptx Presentation of Electrical SafetyJoseAlbertoCariasDel Level 1-Safety.pptx Presentation of Electrical Safety
IntroSlides-April-BuildWithAI-VertexAI.pdf



IntroSlides-April-BuildWithAI-VertexAI.pdfLuiz Carneiro ☁️ GDG Cloud Munich: Build With AI Workshop - Introduction to Vertex AI! ☁️
Join us for an exciting #BuildWithAi workshop on the 28th of April, 2025 at the Google Office in Munich!
Dive into the world of AI with our "Introduction to Vertex AI" session, presented by Google Cloud expert Randy Gupta.
"Boiler Feed Pump (BFP): Working, Applications, Advantages, and Limitations E...



"Boiler Feed Pump (BFP): Working, Applications, Advantages, and Limitations E...Infopitaara A Boiler Feed Pump (BFP) is a critical component in thermal power plants. It supplies high-pressure water (feedwater) to the boiler, ensuring continuous steam generation.
⚙️ How a Boiler Feed Pump Works
Water Collection:
Feedwater is collected from the deaerator or feedwater tank.
Pressurization:
The pump increases water pressure using multiple impellers/stages in centrifugal types.
Discharge to Boiler:
Pressurized water is then supplied to the boiler drum or economizer section, depending on design.
🌀 Types of Boiler Feed Pumps
Centrifugal Pumps (most common):
Multistage for higher pressure.
Used in large thermal power stations.
Positive Displacement Pumps (less common):
For smaller or specific applications.
Precise flow control but less efficient for large volumes.
🛠️ Key Operations and Controls
Recirculation Line: Protects the pump from overheating at low flow.
Throttle Valve: Regulates flow based on boiler demand.
Control System: Often automated via DCS/PLC for variable load conditions.
Sealing & Cooling Systems: Prevent leakage and maintain pump health.
⚠️ Common BFP Issues
Cavitation due to low NPSH (Net Positive Suction Head).
Seal or bearing failure.
Overheating from improper flow or recirculation.
Lidar for Autonomous Driving, LiDAR Mapping for Driverless Cars.pptx



Lidar for Autonomous Driving, LiDAR Mapping for Driverless Cars.pptxRishavKumar530754 LiDAR-Based System for Autonomous Cars
Autonomous Driving with LiDAR Tech
LiDAR Integration in Self-Driving Cars
Self-Driving Vehicles Using LiDAR
LiDAR Mapping for Driverless Cars
railway wheels, descaling after reheating and before forging



railway wheels, descaling after reheating and before forgingJavad Kadkhodapour railway wheels, descaling after reheating and before forging
π0.5: a Vision-Language-Action Model with Open-World Generalization



π0.5: a Vision-Language-Action Model with Open-World GeneralizationNABLAS株式会社 今回の資料「Transfusion / π0 / π0.5」は、画像・言語・アクションを統合するロボット基盤モデルについて紹介しています。
拡散×自己回帰を融合したTransformerをベースに、π0.5ではオープンワールドでの推論・計画も可能に。
This presentation introduces robot foundation models that integrate vision, language, and action.
Built on a Transformer combining diffusion and autoregression, π0.5 enables reasoning and planning in open-world settings.
15th International Conference on Computer Science, Engineering and Applicatio...



15th International Conference on Computer Science, Engineering and Applicatio...IJCSES Journal #computerscience #programming #coding #technology #programmer #python #computer #developer #tech #coder #javascript #java #codinglife #html #code #softwaredeveloper #webdeveloper #software #cybersecurity #linux #computerengineering #webdevelopment #softwareengineer #machinelearning #hacking #engineering #datascience #css #programmers #pythonprogramming
The Gaussian Process Modeling Module in UQLab



The Gaussian Process Modeling Module in UQLabJournal of Soft Computing in Civil Engineering We introduce the Gaussian process (GP) modeling module developed within the UQLab software framework. The novel design of the GP-module aims at providing seamless integration of GP modeling into any uncertainty quantification workflow, as well as a standalone surrogate modeling tool. We first briefly present the key mathematical tools on the basis of GP modeling (a.k.a. Kriging), as well as the associated theoretical and computational framework. We then provide an extensive overview of the available features of the software and demonstrate its flexibility and user-friendliness. Finally, we showcase the usage and the performance of the software on several applications borrowed from different fields of engineering. These include a basic surrogate of a well-known analytical benchmark function; a hierarchical Kriging example applied to wind turbine aero-servo-elastic simulations and a more complex geotechnical example that requires a non-stationary, user-defined correlation function. The GP-module, like the rest of the scientific code that is shipped with UQLab, is open source (BSD license).
Value Stream Mapping Worskshops for Intelligent Continuous Security



Value Stream Mapping Worskshops for Intelligent Continuous SecurityMarc Hornbeek This presentation provides detailed guidance and tools for conducting Current State and Future State Value Stream Mapping workshops for Intelligent Continuous Security.
Data Structures_Searching and Sorting.pptx



Data Structures_Searching and Sorting.pptxRushaliDeshmukh2 Sorting Order and Stability in Sorting.
Concept of Internal and External Sorting.
Bubble Sort,
Insertion Sort,
Selection Sort,
Quick Sort and
Merge Sort,
Radix Sort, and
Shell Sort,
External Sorting, Time complexity analysis of Sorting Algorithms.
some basics electrical and electronics knowledge



some basics electrical and electronics knowledgenguyentrungdo88 This chapter discribe about common electrical divices such as passive component, the internaltional system unit and international system prefixes.
DATA-DRIVEN SHOULDER INVERSE KINEMATICS YoungBeom Kim1 , Byung-Ha Park1 , Kwa...



DATA-DRIVEN SHOULDER INVERSE KINEMATICS YoungBeom Kim1 , Byung-Ha Park1 , Kwa...charlesdick1345 This paper proposes a shoulder inverse kinematics (IK) technique. Shoulder complex is comprised of the sternum, clavicle, ribs, scapula, humerus, and four joints.
Avnet Silica's PCIM 2025 Highlights Flyer



Avnet Silica's PCIM 2025 Highlights FlyerWillDavies22 See what you can expect to find on Avnet Silica's stand at PCIM 2025.
Securing your MySQL server
- 2. Who am I? :)
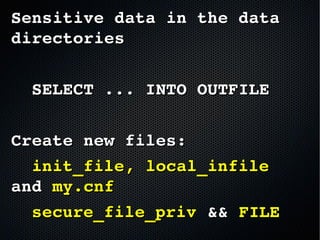
- 4. Why?Why? ➢ Passwords stored in plain text ➢ E-Mail addresses ➢ Physical addresses ➢ Phone numbers ➢ Transaction information ➢ Sessions ➢ etc.
- 15. Chrooting the MySQL Chrooting the MySQL daemondaemon chroot=/var/lib/mysql chroot=/var/lib/mysql
- 16. Chrooting will:Chrooting will: ➢ restrict FS access to the chroot dir ➢ prevent read/write to system files ➢ require SSL certs in the chroot dir ➢ restrict, where the temporary files can be created ➢ restrict the pid and log file locations
- 17. Firewalling the MySQLFirewalling the MySQL ➢ DO NOT PUT MySQL on unrestricted public interfaces # iptables -N mysql # iptables -A mysql -j ACCEPT -s IP_1 # iptables -A mysql -j ACCEPT -s NET_1 # iptables -A mysql -j DROP # iptables -A INPUT -j mysql -p tcp --dport 3306
- 18. Firewalling the MySQLFirewalling the MySQL ➢ Only disallow specific user (app_userapp_user) # iptables -A OUTPUT -j DROP -p tcp --dport 3306 -m owner ! --uid-owner app_userapp_user
- 19. Firewalling the MySQLFirewalling the MySQL ➢ or more then one user, but not everyone: # iptables -N mysql_out # iptables -A mysql_out -j ACCEPT -m owner --uid-owner app_user1app_user1 # iptables -A mysql_out -j ACCEPT -m owner --uid-owner app_user2app_user2 # iptables -A mysql_out -j DROP # iptables -I OUTPUT -j mysql_out -p tcp --dport 3306
- 20. Firewalling the MySQLFirewalling the MySQL ➢ or you want only one specific user, to be restricted from MySQL # iptables -A OUTPUT -j DROP -p tcp --dport 3306 -m owner --uid-owner dev_user1dev_user1
- 22. The effects of:The effects of: # chmod 600 /var/lib/mysql/mysql.sock# chmod 600 /var/lib/mysql/mysql.sock - Only root & mysql have access to it- Only root & mysql have access to it - restrict all users- restrict all users - use sudo for devs- use sudo for devs dev_user1 ALL=(mysql) PASSWD:/usr/bin/mysqldev_user1 ALL=(mysql) PASSWD:/usr/bin/mysql
- 23. The socket protection:The socket protection: Your app needs access to the socket, so:Your app needs access to the socket, so: # groupadd# groupadd web_appweb_app # usermod -a -G# usermod -a -G web_appweb_app mysqlmysql # usermod -a -G# usermod -a -G web_appweb_app app_userapp_user # chmod 660 /var/lib/mysql/mysql.sock# chmod 660 /var/lib/mysql/mysql.sock # chgrp# chgrp web_appweb_app /var/lib/mysql/mysql.sock/var/lib/mysql/mysql.sock
- 24. MySQL authenticationMySQL authentication ➢ never leave a user without a password ➢ try not use the % in the host part of an account ➢ hostnames instead of IPs for user authentication and set skip_name_resolve ➢ do not set old_passwords=0 ➢ (pre mysql 4.1, hashing func. was producing 16bytes hash string)
- 26. MySQL authenticationMySQL authentication mysql> SELECT PASSWORD('mypass');mysql> SELECT PASSWORD('mypass'); +--------------------++--------------------+ | PASSWORD('mypass') || PASSWORD('mypass') | +--------------------++--------------------+ | 6f8c114b58f2ce9e || 6f8c114b58f2ce9e | +--------------------++--------------------+ - try to avoid the mysql_native_password plugin(which- try to avoid the mysql_native_password plugin(which produces 41bytes hash string)produces 41bytes hash string) mysql> SELECT PASSWORD('mypass');mysql> SELECT PASSWORD('mypass'); +-------------------------------------------++-------------------------------------------+ | PASSWORD('mypass') || PASSWORD('mypass') | +-------------------------------------------++-------------------------------------------+ | *6C8989366EAF75BB670AD8EA7A7FC1176A95CEF4 || *6C8989366EAF75BB670AD8EA7A7FC1176A95CEF4 | +-------------------------------------------++-------------------------------------------+
- 27. The mysqlunsha1 attack y = SHA1(password) On every connection the server sends a salt(s) and the client computes a session token(x) x = y XOR SHA1(s + SHA1(y) ) the server will verify it with: SHA1(x XOR SHA1(s + SHA1(y) )) = SHA1(y) MySQL authenticationMySQL authentication
- 34. MySQL SQL SecurityMySQL SQL Security ➢ SQL SECURITY ➢ DEFINER vs. INVOKER CREATE DEFINER = 'admin'@'localhost' PROCEDURE p1() SQL SECURITY DEFINERDEFINER BEGIN UPDATE t1 SET counter = counter + 1; END; ➢ Triggers and evnets are always executed with definer's context
- 38. Other limitationsOther limitations ➢ Galera gcache is not encrypted ➢ .frm files are not encrypted ➢ mysqlbinlogs can no longer read the files ➢ Percona XtraBackup can't backup encrypted data ➢ Audit plugin can't create encrypted output ➢ general and slow logs, can't be encrypted ➢ error.log is not encrypted




