Security of RSA and Integer Factorization
- 1. Security of RSA and Integer Factorization Public Key Size Matters: Demo of decrypting RSA 768-bits ciphertext Dr. Dharma Ganesan, Ph.D.,
- 2. Disclaimer ● The opinions expressed here are my own ○ But not the views of my employer ● The source code fragments and exploits shown here can be reused ○ But without any warranty nor accept any responsibility for failures ● Do not apply the exploit discussed here on other systems ○ Without obtaining authorization from owners 2
- 3. Agenda ● Brief overview of public key cryptography ● RSA formal definition ● Integer Factorization ● Demo - break RSA-768 bits encryption ● Discussion/Recommendation ● Slides are intended for newcomers to Cryptography 3
- 4. Goal ● Demonstrate that security of RSA is rooted in computational hardness of integer factorization ● If the prime factors of a number are known, game over! ● Let’s see how to exploit 768-bits RSA modulus 4
- 5. Prerequisite Some familiarity with the following topics will help to follow the rest of the slides ● Group Theory (Abstract Algebra/Discrete Math) ● Modular Arithmetic (Number Theory) ● Algorithms and Complexity Theory ● If not, it should still be possible to obtain a high-level overview 5
- 6. How can Alice send a message to Bob securely? 6 Public Key PuA ● Alice and Bob never met each other ● Bob will encrypt using Alice’s public key ○ Assume that public keys are known to the world ● Alice will decrypt using her private key ○ Private keys are secrets (never sent out) ● Bob can sign messages using his private key ○ Alice verifies message integrity using Bob’s public key ○ Not important for this presentation/attack ● Note: Alice and Bob need other evidence (e.g., passwords, certificates) to prove their identity to each other ● Who are Alice, Bob, and Eve? Private Key PrA Public Key PuB Private Key PrB
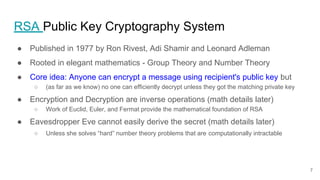
- 7. RSA Public Key Cryptography System ● Published in 1977 by Ron Rivest, Adi Shamir and Leonard Adleman ● Rooted in elegant mathematics - Group Theory and Number Theory ● Core idea: Anyone can encrypt a message using recipient's public key but ○ (as far as we know) no one can efficiently decrypt unless they got the matching private key ● Encryption and Decryption are inverse operations (math details later) ○ Work of Euclid, Euler, and Fermat provide the mathematical foundation of RSA ● Eavesdropper Eve cannot easily derive the secret (math details later) ○ Unless she solves “hard” number theory problems that are computationally intractable 7
- 8. 8 .... Note: There is a change in the notation of symbols in other publications since 1977. We will not use symbols w, r, s. e will be used but with a different meaning (explained in next slides).
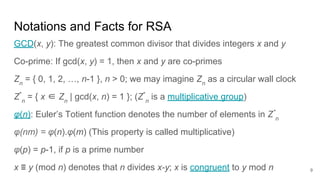
- 9. 9 Notations and Facts for RSA GCD(x, y): The greatest common divisor that divides integers x and y Co-prime: If gcd(x, y) = 1, then x and y are co-primes Zn = { 0, 1, 2, …, n-1 }, n > 0; we may imagine Zn as a circular wall clock Z* n = { x ∈ Zn | gcd(x, n) = 1 }; (Z* n is a multiplicative group) φ(n): Euler’s Totient function denotes the number of elements in Z* n φ(nm) = φ(n).φ(m) (This property is called multiplicative) φ(p) = p-1, if p is a prime number x ≡ y (mod n) denotes that n divides x-y; x is congruent to y mod n
- 10. RSA - Key Generation Algo. (Fits on one page) 1. Select an appropriate bitlength of the RSA modulus n (e.g., 2048 bits) ○ Value of the parameter n is not chosen until step 3; small n is dangerous (details later) 2. Pick two independent, large random primes, p and q, of half of n’s bitlength ○ In practice, p and q are not close to each other to avoid attacks (e.g., Fermat’s factorization) 3. Compute n = p.q (n is also called the RSA modulus) 4. Compute Euler’s Totient (phi) Function φ(n) = φ(p.q) = φ(p)φ(q) = (p-1)(q-1) 5. Select numbers e and d from Zn such that e.d ≡ 1(mod φ(n)) ○ Many implementations set e to be 65537 (Note: gcd(e, φ(n)) = 1) ○ e must be relatively prime to φ(n) otherwise d cannot exist (i.e., we cannot decrypt) ○ d is the multiplicative inverse of e in Zn 6. Public key is the pair <n, e> and private key is 4-tuple <φ(n), d, p, q> Note: If p, q, d, or φ(n) is leaked, RSA is broken immediately 10
- 11. Formal definition of the RSA function ● RSA: Zn → Zn ● Let m and c ∈ Zn ● c = RSA(m) = me mod n ● m = RSA-1 (c) = cd mod n ● e and d are called encryption and decryption exponents, respectively ● Usually a padding scheme is applied before encryption ○ Not relevant for this presentation ● Note: Attackers know c, e, and n but not d 11
- 12. RSA Source Code (sample) ● RSACoreEngine.java implements the RSA and RSA-1 functions ○ See the method processBlock ● RSA(input) = inpute mod n { return input.modPow( key.getExponent(), key.getModulus()); } ● The implementation for RSA-1 is a bit involved (Chinese-Remainder Theorem) ○ To speed-up the computation of inputd mod n, it computes inputd mod p and mod q ○ Not relevant for this presentation 12
- 13. Security assumption of RSA: Factorization Problem ● 15 = 5 . 3 ● 21 = 7 . 3 ● 143 = 11 . 13 ● Given a number n find two prime numbers p and q such that n = p . q ● If this problem is solved for a large n, security of RSA is compromised 13
- 14. Problem statement: Break the RSA-768 bits ● Recall that c = RSA(m) = me mod n ○ c is the ciphertext and m is the plaintext ● Breaking of the RSA function means finding m from c ○ Equivalently, reverse the plaintext from the ciphertext ● Formally, given <c, e, n> find m such that RSA(m) = c 14
- 15. RSA-768 bits Example 15 RSA-768 has 232 decimal digits (768 bits), and was factored on December 12, 2009 over the span of two years, by Thorsten Kleinjung, Kazumaro Aoki, Jens Franke, Arjen K. Lenstra, Emmanuel Thomé, Pierrick Gaudry, Alexander Kruppa, Peter Montgomery, Joppe W. Bos, Dag Arne Osvik, Herman te Riele, Andrey Timofeev, and Paul Zimmermann
- 16. RSA-768 bits - Encryption public class RSAWeakKeyDemo { public static void main(String [] args) throws Exception { BigInteger n = new BigInteger("1230186684530117755130494958384962720772853569595334792197322452 1517264005072636575187452021997864693899564749427740638459251925573263034 5373154826850791702612214291346167042921431160222124047927473779408066535 1419597459856902143413"); BigInteger e = new BigInteger("65537"); PublicKey pubKey = RSAService.getPublicKey(n, e); byte[] ciphertext = RSAService.encrypt(pubKey, args[0]); // error check for args[0]? System.out.println(javax.xml.bind.DatatypeConverter.printHexBinary(ciphertext)); } } 16
- 17. RSA-768 - Encrypt a plaintext $ java RSAWeakKeyDemo "Glenn was here" 7C93E5C41364520991CF359321991B7AC2118E02ADC81913B8D6A70B08B38 4BB8EBF96C5C31C92F48DEDA3080D427E622A365682B64890BCB1F5C3571 9D06A03F0BCF3F5C55A160A5A9C754700348A6A9B11B8F5E06AA428BA1A5 F54B471C64D ❖ I will demonstrate how to take the ciphertext and reconstruct the plaintext ➢ This was possible because the prime factors of the public modules n are available 17
- 18. Let’s decrypt the ciphertext ● Recall that the public modulus n has 768 bits and was already factored ● p = 33478071698956898786044169848212690817704794983713768568912431388982883793 878002287614711652531743087737814467999489 ● q = 36746043666799590428244633799627952632279158164343087642676032283815739666 511279233373417143396810270092798736308917 ● We know that φ(n) = φ(p.q) = φ(p)φ(q) = (p-1)(q-1) ● To decrypt we need to find the decryption exponent d such that e.d ≡ 1(mod φ(n)) ● Thus, we can find d by taking the inverse of e in φ(n) 18
- 19. Program to decrypt the ciphertext 19
- 20. Demo: Let’s reverse the plaintext from ciphertext $ time java RSABreakWeakKey 7C93E5C41364520991CF359321991B7AC2118E02ADC81913B8D6A70B08B38 4BB8EBF96C5C31C92F48DEDA3080D427E622A365682B64890BCB1F5C3571 9D06A03F0BCF3F5C55A160A5A9C754700348A6A9B11B8F5E06AA428BA1A5 F54B471C64D Plaintext: Glenn was here real 0m0.973s user0m0.540s sys 0m0.068s 20
- 21. Discussion/Conclusion 21 ● Security of RSA depends on computation hardness of integer factorization ● A list of known RSA numbers is: https://en.wikipedia.org/wiki/RSA_numbers ● This list shows that so far 768-bits RSA modulus is factored ○ Given a public key, the private prime numbers factors p and q are known to the world ● The demo showed how to decrypt ciphertext when prime factors are known! ● Implementations have to keep ahead by choosing a large public key size ○ At the time of writing, 1024-bits are not factored; 2048-bits is recommended
- 22. References ● W. Diffie and M. E. Hellman, “New Directions in Cryptography,” IEEE Transactions on Information Theory, vol. IT-22, no. 6, November, 1976. ● R. L. Rivest, A. Shamir, and L. Adleman, “A method for obtaining digital signatures and public-key cryptosystems,” CACM 21, 2, February, 1978. ● A. Menezes, P. van Oorschot, and S. Vanstone, “Handbook of Applied Cryptography,” CRC Press, 1996. ● C. Paar and J. Pelzl. “Understanding Cryptography: A Textbook for Students and Practitioners,” Springer, 2011. ● https://en.wikipedia.org/wiki/RSA_numbers 22
- 23. Appendix - Source of RSAService Wrapper 23














![RSA-768 bits - Encryption
public class RSAWeakKeyDemo {
public static void main(String [] args) throws Exception {
BigInteger n = new
BigInteger("1230186684530117755130494958384962720772853569595334792197322452
1517264005072636575187452021997864693899564749427740638459251925573263034
5373154826850791702612214291346167042921431160222124047927473779408066535
1419597459856902143413");
BigInteger e = new BigInteger("65537");
PublicKey pubKey = RSAService.getPublicKey(n, e);
byte[] ciphertext = RSAService.encrypt(pubKey, args[0]); // error check for args[0]?
System.out.println(javax.xml.bind.DatatypeConverter.printHexBinary(ciphertext));
}
}
16](https://image.slidesharecdn.com/rsasecurityandintegerfactorization-180317161620/85/Security-of-RSA-and-Integer-Factorization-16-320.jpg)






