Security Testing
2 likes1,971 views
Security Testing is a process to determine how well a system protects against unauthorized internal or external access or wilful damage. It is performed to check whether there is any information leakage in the sense by encrypting the application or using wide range of software etc..
1 of 14













Ad
Recommended
What is security testing and why it is so important?



What is security testing and why it is so important?ONE BCG Security Testing is described as a type of Software Testing that assures software systems and applications are free from any vulnerabilities, threats, risks that may cause a big loss. Security testing of any system is about uncovering all likely loopholes and weaknesses of the system which might end up in a loss of information, revenue, repute at the hands of the employees or outsiders of the Organization.
Security Testing for Test Professionals



Security Testing for Test ProfessionalsTechWell This document provides an overview of a presentation titled "Security Testing for Test Professionals" given by Jeff Payne of Coveros, Inc. The presentation introduces concepts of information security, software security, risk assessment and security testing. It discusses security requirements including functional security requirements and non-functional security requirements. The presentation also covers testing for common attacks and integrating security testing into the software development process. Sample exercises are provided to help identify threats, assets, and risks for an application and to define security requirements and test cases.
Generic threats to mobile application



Generic threats to mobile applicationVikrant Kansal This paper covers security issues that a security analyst may look for during vulnerability assessment and penetration testing on case–by-case basis. Issues covered in the paper are generic and can be considered across all the mobile platforms.
Security testing



Security testingbaskar p Security testing is performed to identify vulnerabilities in a system and ensure confidentiality, integrity, authentication, authorization, availability and non-repudiation. The main techniques are vulnerability scanning, security scanning, penetration testing, ethical hacking, risk assessment, security auditing, and password cracking. Security testing helps improve security, find loopholes, and ensure systems work properly and protect information.
Application security testing an integrated approach



Application security testing an integrated approachIdexcel Technologies This document discusses application security testing and provides recommendations for a comprehensive testing plan. It begins by outlining common application security vulnerabilities like injection flaws, cross-site scripting, and sensitive data exposure. It then recommends using tools like vulnerability scanning, threat modeling, code analysis, and penetration testing to test for vulnerabilities. The document concludes by describing how to test for issues in specific areas like authentication, authorization, data validation, and payment processing.
Most Common Application Level Attacks



Most Common Application Level AttacksEC-Council What are the most common application level attacks? To find out, take a look at these slides! Click here to learn how CASE can help you create secure applications: http://ow.ly/rARK50BVi4b
Security and information assurance



Security and information assurancebdemchak This document discusses challenges in information assurance and authentication. It introduces common web authentication methods like SAML and Shibboleth that enable single sign-on across domains using federated identity. SAML allows sharing of authentication and authorization data in XML format. Shibboleth is an open source single sign-on system that uses SAML and allows identity federations. OpenID is also discussed as a decentralized authentication standard used by many websites. The document compares and contrasts these different authentication methods.
Software Security Testing



Software Security Testingsrivinayak This document discusses software security testing. It outlines various aspects of secure software like confidentiality, integrity, data security, authentication, and availability. It then describes different types of software that require security testing like operating systems, applications, databases, and network software. Various techniques for security testing are explained in detail, such as vulnerability scanning, penetration testing, firewall rule testing, SQL injection testing, and ethical hacking. The document emphasizes the importance of early security testing and providing recommendations to overcome weaknesses found.
Seminar-Two Factor Authentication



Seminar-Two Factor AuthenticationDilip Kr. Jangir This document discusses two-factor authentication and its benefits. It describes two-factor authentication as requiring two different types of evidence, such as something you know (a password) and something you have (a token or mobile device). Hard tokens generate one-time passwords on a physical device while mobile tokens use a mobile app to generate passwords. Using a mobile token is more flexible and cheaper than hard tokens but still vulnerable to active attacks. Sending a one-time password via SMS and requiring the user to enter a code for transactions adds an extra layer of security against man-in-the-middle attacks compared to other methods. The document recommends hashing passwords before sending and mutual authentication between clients and servers to improve security.
How Does a Data Breach Happen? 



How Does a Data Breach Happen? Claranet UK The document discusses how web application hacking occurs through examples like SQL injection. It explains the basic components of a web application like the database, server, and client. It then covers the steps an attacker may take, like using tools to find hidden content or exploiting vulnerabilities in how user input is handled to access private user data or delete database tables. The document emphasizes that these types of vulnerabilities are common and provides resources for learning about different hacking techniques as well as the company's security assessment services.
Gaining A Foothold



Gaining A FootholdClaranet UK This document discusses various social engineering techniques that can be used by attackers such as phishing and gaining physical access. It provides examples of how phishing emails can appear legitimate but contain subtle signs that reveal the real domain is incorrect. The document also discusses ways attackers may gain physical access such as bypassing security protocols and door locks. It emphasizes the importance of user awareness training to help protect against social engineering attacks.
BAI Security - Brochure - Compromise Assessment



BAI Security - Brochure - Compromise AssessmentPrahlad Reddy The document describes BAI Security's Compromise Assessment service which uses sophisticated forensic analysis, whitelisting, and application profiling to identify advanced malware that may go undetected by traditional antivirus and network security solutions. BAI Security was recognized as one of the top 20 enterprise security companies in 2014 and only uses experienced in-house auditors routinely tested and retrained on the latest methodologies and security tools. The Compromise Assessment process involves an onsite server scan of endpoints, analysis of live memory, disks, and network traffic to distinguish malware and determine the scope of any compromise.
Best Practices for Multi-Factor Authentication: Delivering Stronger Security ...



Best Practices for Multi-Factor Authentication: Delivering Stronger Security ...Sirius This document provides best practices for implementing multi-factor authentication (MFA) for stronger security. It discusses how MFA provides an additional layer of security beyond passwords alone. The document recommends understanding your requirements, evaluating solutions based on integration, user experience and flexibility, assessing users and applications, choosing appropriate authentication factors and distribution methods, taking mobile security measures, and delivering MFA through a risk-based and user-friendly approach to prevent stolen password attacks while balancing security and usability.
Two Factor Authentication



Two Factor AuthenticationNikhil Shaw The document discusses two-factor authentication (2FA) as a more secure alternative to single-factor authentication using just a username and password. 2FA provides an additional layer of security beyond just one credential by requiring two separate factors, such as something you know (a password) plus something you have (a token, smart card, or biometrics). While 2FA is more secure, it can also be slower and require the user to have their second authentication factor available at all times. Popular services like Facebook and Dropbox have implemented 2FA options to better protect user accounts and data.
Asegurarme de la Seguridad?, Un Vistazo al Penetration Testing



Asegurarme de la Seguridad?, Un Vistazo al Penetration TestingSoftware Guru Sesión presentada en SG Virtual 11a. edición.
Por: Gilberto Sánchez.
En esta charla veremos ¿qué es el Penetration Testing?, ¿Porque hacerlo?, los tipos de Pen testing que existen, además veremos el pre-ataque, ataque y el post-ataque así como los estándares que existen en la actualidad..
VAPT - Vulnerability Assessment & Penetration Testing 



VAPT - Vulnerability Assessment & Penetration Testing Netpluz Asia Pte Ltd VAPT (Vulnerability Assessment and Penetration Testing) involves evaluating systems and networks to identify vulnerabilities, configuration issues, and potential routes of unauthorized access. It is recommended for SMEs due to common security issues like phishing and ransomware attacks targeting them. The document outlines the types of VAPT testing, why SMEs need it, example data breaches, and estimated costs of common cyber attacks and security services.
Security-testing presentation



Security-testing presentationEzhilan Elangovan (Eril) This is a detailed presentation of our web security suite - SECURITY-TESTING. It's a cloud based product, providing solutions under 6 modules - SERM, Scanning, Detection, Monitoring, Performance and Inventory. For more details please visit our website www.security-testing.net
Point-Of-Sale Hacking - 2600Thailand#20



Point-Of-Sale Hacking - 2600Thailand#20Prathan Phongthiproek The document discusses vulnerabilities in point-of-sale (POS) systems, including data in memory, data at rest, data in transit, and application code/configuration vulnerabilities. It describes different POS deployment models and their pros and cons in terms of security. A case study examines physical and network security issues found during a pentest of a retail store's POS system, including sensitive data exposure over the network. Recommended protections include minimizing data exposure, encryption of data in memory, in transit, and at rest, and avoiding storage of sensitive data.
How to Become an Ethical Hacker? | Ethical Hacking Career | Ethical Hacker Sa...



How to Become an Ethical Hacker? | Ethical Hacking Career | Ethical Hacker Sa...Edureka! ** Cybersecurity Course: https://www.edureka.co/cybersecurity-certification-training **
This edureka session on "How to become an ethical hacker", covers all the basic aspects of becoming an ethical hacker. It establishes the concepts like roles, responsibilities, skills, salaries and even trends to get you up to speed with hacking. The following topics are going to be discussed throughout the course of this PPT:
1. Who is an ethical hacker?
2. Roadmap to become an Ethical Hacker
3. Pertinent Certifications
4. CEH Exam Overview and Objectives
5. Eligibility Criteria
6. Skills required
7. Job Trends and Companies Hiring
8. Salary
Follow us to never miss an update in the future.
Instagram: https://www.instagram.com/edureka_learning/
Facebook: https://www.facebook.com/edurekaIN/
Twitter: https://twitter.com/edurekain
LinkedIn: https://www.linkedin.com/company/edureka
IRJET- Data Security with Multifactor Authentication



IRJET- Data Security with Multifactor AuthenticationIRJET Journal This document discusses a multi-factor authentication system for improving data security. It proposes using passwords, one-time passwords via QR codes, and encryption/decryption of stored data. The system uses three stages of verification: login with username and password, verification with a randomly generated OTP QR code, and encrypting uploaded data and decrypting downloaded data with keys. By adding multiple layers of authentication and encrypting data, the system aims to minimize unauthorized access to secure systems and stored information.
Two factor authentication 2018



Two factor authentication 2018Will Adams This document summarizes a presentation on two-factor authentication (2FA). It discusses the different types of authentication factors including something you know (e.g. passwords), something you have (e.g. security tokens), and something you are (e.g. biometrics). Software token apps like Google Authenticator and Authy that generate one-time passwords for 2FA are also covered. The document outlines the security issues with passwords and why 2FA is needed based on recent data breaches. It provides an overview of standards like FIDO and implementation recommendations for adding a second authentication factor.
Two factor authentication



Two factor authenticationHai Nguyen Two-factor authentication provides stronger security than single-factor authentication like usernames and passwords alone. It requires two factors: something you know (like a password) and something you have (like a token, smart card, or biometric). This makes hacking accounts more difficult as possessing just a password is not enough. While more secure, two-factor authentication has additional costs and may be inconvenient for users. However, as technology advances, the use of two-factor authentication is growing in industries like banking and online brokerages to better protect customers.
USP SES and the Location Layer: Geolocation for adaptive Access Control and P...



USP SES and the Location Layer: Geolocation for adaptive Access Control and P...United Security Providers AG Discover more about USP`s SES solution : say goodbye to Microsoft’s TMG and Hello to USP`s Smarter Web App Protection and Authentication!
by United Security Providers
Oh, WASP! Security Essentials for Web Apps



Oh, WASP! Security Essentials for Web AppsTechWell The past few years have seen a rapid increase in business efficiency through Web-based applications. Unfortunately, a dramatic increase in the number of web application vulnerabilities has followed. Insecure web applications can be disastrous for mission critical businesses and users' sensitive data. More than 70 percent of security vulnerabilities are due to flaws in the application rather than firewall breaches. Bennie Paul explains how security testing has become an indispensable part of the SDLC for businesses operating online today. OWASP (Open Web Application Security Project) provides open source tools, code, and materials to develop, test, and maintain application security. Monitoring the “OWASP Top 10” web application security flaws is highly recommended as part of an organization’s testing methodology. Vulnerabilities identified are compared against the organization’s security objectives and regulations, and categorized accordingly for remediation. Benny guides you through the OWASP vulnerabilities, technique, framework, and preventive measures that you can adopt for building better software.
Ethical Hacking Services



Ethical Hacking ServicesVirtue Security A short summary of ethical hacking services as well basic information on vulnerability assessments and the types of security tests we offer.
Network Security - Defense Through Layered Information Security



Network Security - Defense Through Layered Information SecurityEryk Budi Pratama My presentation about Defense in Depth and Next Generation Firewall.
Presented for iFest event, held by UHAMKA, Jakarta.
The Ultimate Security Checklist Before Launching Your Android App



The Ultimate Security Checklist Before Launching Your Android AppAppknox Are you an Android developer or an enterprise ready to launch your Android App? Then wait! Did you check for the security risks that your mobile app can is exposed to?
According to a Forbes 2014 report, Android malware rose from 238 threats in 2012 to 2.5 times in 2013.
With the lack of strict security measures, cyber attacks have only increased with each passing year. To avoid being a victim of any malware, enterprises and developers should ensure a complete security check before they launch their Android apps.
In this deck, We have shared 21 most essential security measures that any Android app developer or security professional should follow.
1. penetration-testing-cyber51



1. penetration-testing-cyber51Doree Garcia, CCNA, OSWP Cyber 51 LLC provides penetration testing services to evaluate computer and network security by simulating attacks. They successfully breached 95% of customer systems tested. Penetration testing is recommended for businesses that hold confidential data, want to avoid lawsuits from data theft, must comply with regulations, or understand that proactive security is cheaper than reactive security. Testing should occur every 2-4 times per year depending on business needs. Cyber 51 charges based on the number of IP addresses, machines, or web applications tested and offers various penetration testing services including network, web application, SAP, DDoS, and cloud security testing.
Ad
More Related Content
What's hot (20)
Seminar-Two Factor Authentication



Seminar-Two Factor AuthenticationDilip Kr. Jangir This document discusses two-factor authentication and its benefits. It describes two-factor authentication as requiring two different types of evidence, such as something you know (a password) and something you have (a token or mobile device). Hard tokens generate one-time passwords on a physical device while mobile tokens use a mobile app to generate passwords. Using a mobile token is more flexible and cheaper than hard tokens but still vulnerable to active attacks. Sending a one-time password via SMS and requiring the user to enter a code for transactions adds an extra layer of security against man-in-the-middle attacks compared to other methods. The document recommends hashing passwords before sending and mutual authentication between clients and servers to improve security.
How Does a Data Breach Happen? 



How Does a Data Breach Happen? Claranet UK The document discusses how web application hacking occurs through examples like SQL injection. It explains the basic components of a web application like the database, server, and client. It then covers the steps an attacker may take, like using tools to find hidden content or exploiting vulnerabilities in how user input is handled to access private user data or delete database tables. The document emphasizes that these types of vulnerabilities are common and provides resources for learning about different hacking techniques as well as the company's security assessment services.
Gaining A Foothold



Gaining A FootholdClaranet UK This document discusses various social engineering techniques that can be used by attackers such as phishing and gaining physical access. It provides examples of how phishing emails can appear legitimate but contain subtle signs that reveal the real domain is incorrect. The document also discusses ways attackers may gain physical access such as bypassing security protocols and door locks. It emphasizes the importance of user awareness training to help protect against social engineering attacks.
BAI Security - Brochure - Compromise Assessment



BAI Security - Brochure - Compromise AssessmentPrahlad Reddy The document describes BAI Security's Compromise Assessment service which uses sophisticated forensic analysis, whitelisting, and application profiling to identify advanced malware that may go undetected by traditional antivirus and network security solutions. BAI Security was recognized as one of the top 20 enterprise security companies in 2014 and only uses experienced in-house auditors routinely tested and retrained on the latest methodologies and security tools. The Compromise Assessment process involves an onsite server scan of endpoints, analysis of live memory, disks, and network traffic to distinguish malware and determine the scope of any compromise.
Best Practices for Multi-Factor Authentication: Delivering Stronger Security ...



Best Practices for Multi-Factor Authentication: Delivering Stronger Security ...Sirius This document provides best practices for implementing multi-factor authentication (MFA) for stronger security. It discusses how MFA provides an additional layer of security beyond passwords alone. The document recommends understanding your requirements, evaluating solutions based on integration, user experience and flexibility, assessing users and applications, choosing appropriate authentication factors and distribution methods, taking mobile security measures, and delivering MFA through a risk-based and user-friendly approach to prevent stolen password attacks while balancing security and usability.
Two Factor Authentication



Two Factor AuthenticationNikhil Shaw The document discusses two-factor authentication (2FA) as a more secure alternative to single-factor authentication using just a username and password. 2FA provides an additional layer of security beyond just one credential by requiring two separate factors, such as something you know (a password) plus something you have (a token, smart card, or biometrics). While 2FA is more secure, it can also be slower and require the user to have their second authentication factor available at all times. Popular services like Facebook and Dropbox have implemented 2FA options to better protect user accounts and data.
Asegurarme de la Seguridad?, Un Vistazo al Penetration Testing



Asegurarme de la Seguridad?, Un Vistazo al Penetration TestingSoftware Guru Sesión presentada en SG Virtual 11a. edición.
Por: Gilberto Sánchez.
En esta charla veremos ¿qué es el Penetration Testing?, ¿Porque hacerlo?, los tipos de Pen testing que existen, además veremos el pre-ataque, ataque y el post-ataque así como los estándares que existen en la actualidad..
VAPT - Vulnerability Assessment & Penetration Testing 



VAPT - Vulnerability Assessment & Penetration Testing Netpluz Asia Pte Ltd VAPT (Vulnerability Assessment and Penetration Testing) involves evaluating systems and networks to identify vulnerabilities, configuration issues, and potential routes of unauthorized access. It is recommended for SMEs due to common security issues like phishing and ransomware attacks targeting them. The document outlines the types of VAPT testing, why SMEs need it, example data breaches, and estimated costs of common cyber attacks and security services.
Security-testing presentation



Security-testing presentationEzhilan Elangovan (Eril) This is a detailed presentation of our web security suite - SECURITY-TESTING. It's a cloud based product, providing solutions under 6 modules - SERM, Scanning, Detection, Monitoring, Performance and Inventory. For more details please visit our website www.security-testing.net
Point-Of-Sale Hacking - 2600Thailand#20



Point-Of-Sale Hacking - 2600Thailand#20Prathan Phongthiproek The document discusses vulnerabilities in point-of-sale (POS) systems, including data in memory, data at rest, data in transit, and application code/configuration vulnerabilities. It describes different POS deployment models and their pros and cons in terms of security. A case study examines physical and network security issues found during a pentest of a retail store's POS system, including sensitive data exposure over the network. Recommended protections include minimizing data exposure, encryption of data in memory, in transit, and at rest, and avoiding storage of sensitive data.
How to Become an Ethical Hacker? | Ethical Hacking Career | Ethical Hacker Sa...



How to Become an Ethical Hacker? | Ethical Hacking Career | Ethical Hacker Sa...Edureka! ** Cybersecurity Course: https://www.edureka.co/cybersecurity-certification-training **
This edureka session on "How to become an ethical hacker", covers all the basic aspects of becoming an ethical hacker. It establishes the concepts like roles, responsibilities, skills, salaries and even trends to get you up to speed with hacking. The following topics are going to be discussed throughout the course of this PPT:
1. Who is an ethical hacker?
2. Roadmap to become an Ethical Hacker
3. Pertinent Certifications
4. CEH Exam Overview and Objectives
5. Eligibility Criteria
6. Skills required
7. Job Trends and Companies Hiring
8. Salary
Follow us to never miss an update in the future.
Instagram: https://www.instagram.com/edureka_learning/
Facebook: https://www.facebook.com/edurekaIN/
Twitter: https://twitter.com/edurekain
LinkedIn: https://www.linkedin.com/company/edureka
IRJET- Data Security with Multifactor Authentication



IRJET- Data Security with Multifactor AuthenticationIRJET Journal This document discusses a multi-factor authentication system for improving data security. It proposes using passwords, one-time passwords via QR codes, and encryption/decryption of stored data. The system uses three stages of verification: login with username and password, verification with a randomly generated OTP QR code, and encrypting uploaded data and decrypting downloaded data with keys. By adding multiple layers of authentication and encrypting data, the system aims to minimize unauthorized access to secure systems and stored information.
Two factor authentication 2018



Two factor authentication 2018Will Adams This document summarizes a presentation on two-factor authentication (2FA). It discusses the different types of authentication factors including something you know (e.g. passwords), something you have (e.g. security tokens), and something you are (e.g. biometrics). Software token apps like Google Authenticator and Authy that generate one-time passwords for 2FA are also covered. The document outlines the security issues with passwords and why 2FA is needed based on recent data breaches. It provides an overview of standards like FIDO and implementation recommendations for adding a second authentication factor.
Two factor authentication



Two factor authenticationHai Nguyen Two-factor authentication provides stronger security than single-factor authentication like usernames and passwords alone. It requires two factors: something you know (like a password) and something you have (like a token, smart card, or biometric). This makes hacking accounts more difficult as possessing just a password is not enough. While more secure, two-factor authentication has additional costs and may be inconvenient for users. However, as technology advances, the use of two-factor authentication is growing in industries like banking and online brokerages to better protect customers.
USP SES and the Location Layer: Geolocation for adaptive Access Control and P...



USP SES and the Location Layer: Geolocation for adaptive Access Control and P...United Security Providers AG Discover more about USP`s SES solution : say goodbye to Microsoft’s TMG and Hello to USP`s Smarter Web App Protection and Authentication!
by United Security Providers
Oh, WASP! Security Essentials for Web Apps



Oh, WASP! Security Essentials for Web AppsTechWell The past few years have seen a rapid increase in business efficiency through Web-based applications. Unfortunately, a dramatic increase in the number of web application vulnerabilities has followed. Insecure web applications can be disastrous for mission critical businesses and users' sensitive data. More than 70 percent of security vulnerabilities are due to flaws in the application rather than firewall breaches. Bennie Paul explains how security testing has become an indispensable part of the SDLC for businesses operating online today. OWASP (Open Web Application Security Project) provides open source tools, code, and materials to develop, test, and maintain application security. Monitoring the “OWASP Top 10” web application security flaws is highly recommended as part of an organization’s testing methodology. Vulnerabilities identified are compared against the organization’s security objectives and regulations, and categorized accordingly for remediation. Benny guides you through the OWASP vulnerabilities, technique, framework, and preventive measures that you can adopt for building better software.
Ethical Hacking Services



Ethical Hacking ServicesVirtue Security A short summary of ethical hacking services as well basic information on vulnerability assessments and the types of security tests we offer.
Network Security - Defense Through Layered Information Security



Network Security - Defense Through Layered Information SecurityEryk Budi Pratama My presentation about Defense in Depth and Next Generation Firewall.
Presented for iFest event, held by UHAMKA, Jakarta.
The Ultimate Security Checklist Before Launching Your Android App



The Ultimate Security Checklist Before Launching Your Android AppAppknox Are you an Android developer or an enterprise ready to launch your Android App? Then wait! Did you check for the security risks that your mobile app can is exposed to?
According to a Forbes 2014 report, Android malware rose from 238 threats in 2012 to 2.5 times in 2013.
With the lack of strict security measures, cyber attacks have only increased with each passing year. To avoid being a victim of any malware, enterprises and developers should ensure a complete security check before they launch their Android apps.
In this deck, We have shared 21 most essential security measures that any Android app developer or security professional should follow.
1. penetration-testing-cyber51



1. penetration-testing-cyber51Doree Garcia, CCNA, OSWP Cyber 51 LLC provides penetration testing services to evaluate computer and network security by simulating attacks. They successfully breached 95% of customer systems tested. Penetration testing is recommended for businesses that hold confidential data, want to avoid lawsuits from data theft, must comply with regulations, or understand that proactive security is cheaper than reactive security. Testing should occur every 2-4 times per year depending on business needs. Cyber 51 charges based on the number of IP addresses, machines, or web applications tested and offers various penetration testing services including network, web application, SAP, DDoS, and cloud security testing.
USP SES and the Location Layer: Geolocation for adaptive Access Control and P...



USP SES and the Location Layer: Geolocation for adaptive Access Control and P...United Security Providers AG
Viewers also liked (20)
Ericsson ConsumerLab: Privacy, security and safety online



Ericsson ConsumerLab: Privacy, security and safety onlineEricsson This report is the third installment from Ericsson ConsumerLab investigating matters of user privacy, integrity and security online.
JavaScript Object Notation (JSON)



JavaScript Object Notation (JSON)BOSS Webtech JSON (JavaScript Object Notation) is an independent data exchange format. It is a lightweight data-interchange format. It is easy for humans to read and write. It is easy for machines to parse and generate. In JSON, a data structure is a key / value pair. It is a subset of the JavaScript Specification (ECME-Script) and is therefore directly in JavaScript.
ALMOUNKEZ Diwani , Manage your documents with ease



ALMOUNKEZ Diwani , Manage your documents with easeKamal Al Mounajed This document describes a windows application called Diwani that allows users to organize documents in one central location. Key features include:
- Storing documents like bills, receipts, photos in one place and attaching an information card with fields to help sort and search documents.
- All documents are stored in a database so they do not need to be located on the hard disk and can be printed or viewed from the database.
- Documents can be assigned statuses, employees, customers or offices and reports can list documents by these attributes.
- Built-in templates allow standard documents like bills or offers to be easily created with pre-defined formats.
- The system uses Microsoft SQL server for the
Ikatan phi



Ikatan phiLusi Padma Dokumen tersebut membahas tentang ikatan phi (π) yang merupakan ikatan kovalen yang terbentuk dari pertumpangtindahan dua orbital atom yang masing-masing memiliki satu elektron. Ikatan phi lebih lemah dari ikatan sigma karena densitas elektronnya lebih jauh dari inti atom. Walaupun demikian, ikatan phi seringkali merupakan komponen penting dari ikatan rangkap.
Innovative systems icdl lesson 01 arabic



Innovative systems icdl lesson 01 arabicKamal Al Mounajed Arabic Lessons in ICDL 5 in arabic Unit 01 - 01
Innovative systems icdl lesson 02 arabic



Innovative systems icdl lesson 02 arabicKamal Al Mounajed Arabic Lessons in ICDL 5 in arabic Unit 01 - 02
arabic icdl unit 1



arabic icdl unit 1Kamal Al Mounajed This document provides an overview of key concepts in information and communication technology (ICT). It covers hardware components, input/output devices, system units, processors, memory, storage, ports, and computer performance. It also discusses operating systems, application software, networks, internet, telecommunications, and the use of ICT in everyday life. Finally, it outlines important considerations around health and safety, data protection, security, software licensing, and relevant legislation.
نظام المنقذ لتقييم الموظفين من انتاج شركة الانظمة المتجددة



نظام المنقذ لتقييم الموظفين من انتاج شركة الانظمة المتجددةKamal Al Mounajed software for evaluation employees and assessments it can help management in moving , rewarding and make decision for any employee ,
simple actions and helpful
Online Safety and Security 



Online Safety and Security Arah Louise It is about the different threats that can be obtained through accessing the internet, the different government provisions and how to stay safe online.
Cluster Computing



Cluster ComputingBOSS Webtech Cluster computing involves linking multiple computers together to act as a single system. There are three main types of computer clusters: high availability clusters which maintain redundant backup nodes for reliability, load balancing clusters which distribute workloads efficiently across nodes, and high-performance clusters which exploit parallel processing across nodes. Clusters offer benefits like increased processing power, cost efficiency, expandability, and high availability.
Online Ethics and Etiquette 



Online Ethics and Etiquette JessamenTino21 Online ethics and etiquette are very important in an online community so that there is a peace and order among us.
XML Document Object Model (DOM)



XML Document Object Model (DOM)BOSS Webtech The document discusses the XML DOM (Document Object Model). It defines the DOM as a standard for accessing and manipulating XML documents through a tree structure representation. The DOM defines all elements in an XML document as nodes that can be traversed and modified. It outlines DOM properties and methods for navigating and manipulating the node tree. Advantages of the DOM include its traversable and modifiable tree structure, while disadvantages include higher resource usage compared to SAX parsing.
Ad
Similar to Security Testing (20)
Top 20 certified ethical hacker interview questions and answer



Top 20 certified ethical hacker interview questions and answerShivamSharma909 The technique of discovering vulnerabilities in a software, website, or agency’s structure that a hacker might exploit is known as ethical hacking. They employ this method to avoid cyberattacks and security breaches by legitimately hacking into systems and looking for flaws. CEH was designed to include a hands-on environment and a logical procedure across each ethical hacking area and technique. This is to provide you the opportunity to work towards proving the knowledge and skills to earn the CEH certificate and perform the tasks of an ethical hacker.
Read more: https://www.infosectrain.com/blog/top-20-certified-ethical-hacker-interview-questions-and-answer/
Introduction to security testing raj



Introduction to security testing rajRajakrishnan S, MCA,MBA,MA Phil,PMP,CSM,ISTQB-Test Mgr,ITIL Security testing is the process of identifying vulnerabilities in a system to protect data and ensure intended functionality. It involves testing confidentiality, integrity, authentication, availability, authorization, and non-repudiation. The security testing process includes planning, vulnerability scanning, assessment, penetration testing, and reporting. Types of security testing include static application, dynamic application, and penetration testing. The OWASP Top 10 list identifies the most critical web application security risks.
Best Security Practices for Web Application Development.pdf



Best Security Practices for Web Application Development.pdfDigital Auxilio Technologies Discover essential security practices for robust web application development. Learn how to safeguard your projects effectively.
Domain 5 of the CEH Web Application Hacking.pptx



Domain 5 of the CEH Web Application Hacking.pptxInfosectrain3 The document discusses Domain 5 of the Certified Ethical Hacker (CEH) exam, which is web application hacking. It defines a web application as a software program that performs tasks by running on any web browser without needing to be downloaded. Common hacking methods like SQL injection, cross-site scripting, and fuzzing are described. The document also outlines vulnerabilities like unvalidated inputs and directory traversal attacks, and defenses against web application hacking such as authentication, secure coding, and auditing.
Module 6.pdf



Module 6.pdfSitamarhi Institute of Technology The document discusses several topics related to cyber security including biometrics, mobile device hardening, web application security, identity management for web services, authorization patterns, security considerations, and challenges. Specifically, it provides best practices for securing evolving technologies, mobile devices, web servers, web services, implementing identity management, common authorization patterns, important security considerations, and challenges related to implementing security.
Module 6.Security in Evolving Technology



Module 6.Security in Evolving TechnologySitamarhi Institute of Technology Module 6 Lectures 8 hrs.
Security in Evolving Technology: Biometrics, Mobile Computing and Hardening on
android and ios, IOT Security, Web server configuration and Security. Introduction,
Basic security for HTTP Applications and Services, Basic Security for Web Services
like SOAP, REST etc., Identity Management and Web Services, Authorization Patterns,
Security Considerations, Challenges.
Open Source/ Free/ Trial Tools: adb for android, xcode for ios, Implementation of REST/
SOAP web services and Security implementations.
21CSB02T UNIT 1 NOTES. FOR WEB APPLICATION SECURITY VERTICAL COURSES



21CSB02T UNIT 1 NOTES. FOR WEB APPLICATION SECURITY VERTICAL COURSESRajkumars275092 WEB APPLICATION SECURITY NOTES
Security Testing Approach for Web Application Testing.pdf



Security Testing Approach for Web Application Testing.pdfAmeliaJonas2 There are numerous web security testing tools available to aid in the process. One such tool is Astra's Pentest Solution. Astra offers a comprehensive suite of Security Testing Services, including vulnerability scanning, penetration testing, and code reviews. It provides automated scanning and analysis of web applications to identify vulnerabilities and suggest remediation measures.
What is penetration testing and why is it important for a business to invest ...



What is penetration testing and why is it important for a business to invest ...Alisha Henderson A penetration test is also called a pen test, and a penetration tester is also referred to as an ethical hacker. We can figure out the vulnerable loopholes of a network, a web app or a network through penetration testing services.https://bit.ly/2Zq44xn
AW-Infs201101067.pptx



AW-Infs201101067.pptxAnonymousDevil2 Abdul Wahab's presentation covers topics related to common cybersecurity vulnerabilities and exploits including cross-site scripting, cross-site request forgery, session management, SQL injection, secure software testing, and replicating vulnerabilities. It discusses these topics in detail providing examples of each vulnerability type and strategies to prevent exploits such as input validation, output encoding, secure cookies, penetration testing, and security awareness training. The presentation aims to educate audiences on how these vulnerabilities work and best practices for secure development.
Top Interview Questions Asked to a Penetration Tester.pdf



Top Interview Questions Asked to a Penetration Tester.pdfinfosec train 𝐔𝐧𝐥𝐨𝐜𝐤 𝐘𝐨𝐮𝐫 𝐏𝐞𝐧𝐞𝐭𝐫𝐚𝐭𝐢𝐨𝐧 𝐓𝐞𝐬𝐭𝐢𝐧𝐠 𝐏𝐨𝐭𝐞𝐧𝐭𝐢𝐚𝐥: 𝐃𝐨𝐰𝐧𝐥𝐨𝐚𝐝 𝐎𝐮𝐫 𝐕𝐢𝐫𝐚𝐥 𝐖𝐡𝐢𝐭𝐞 𝐏𝐚𝐩𝐞𝐫!
As the demand for Penetration Testers skyrockets, stand out in interviews with our **𝐓𝐨𝐩 𝐈𝐧𝐭𝐞𝐫𝐯𝐢𝐞𝐰 𝐐𝐮𝐞𝐬𝐭𝐢𝐨𝐧𝐬 𝐟𝐨𝐫 𝐏𝐞𝐧𝐞𝐭𝐫𝐚𝐭𝐢𝐨𝐧 𝐓𝐞𝐬𝐭𝐞𝐫𝐬** white paper!
🌐 Get the insider tips and tactics you need to tackle the toughest questions and impress employers.
👉 Download now and elevate your career!
Top Interview Questions for Penetration Testers.pdf



Top Interview Questions for Penetration Testers.pdfinfosecTrain Unlock Your Penetration Testing Potential: Download Our Viral White Paper!
As the demand for Penetration Testers skyrockets, stand out in interviews with our Top Interview Questions for Penetration Testers white paper!
Infosectrain.com
Get the insider tips and tactics you need to tackle the toughest questions and impress employers.
Download now and elevate your career!
Appsec2013 assurance tagging-robert martin



Appsec2013 assurance tagging-robert martindrewz lin The document discusses engineering software systems to be more secure against attacks. It notes that reducing a system's attack surface alone is not enough, as software and networks are too complex and it is impossible to know all vulnerabilities. It then discusses characteristics of advanced persistent threats, including that the initial attack may go unnoticed and adversaries cannot be fully kept out. Finally, it argues that taking a threat-driven perspective beyond just operational defense can help balance mitigation with detection and response.
C01461422



C01461422IOSR Journals This document discusses secure web application development and preventing common vulnerabilities. It begins with an introduction on why web applications are often vulnerable and the importance of secure development. It then provides details on secure development lifecycles and practices, describes top vulnerabilities like injection flaws and cross-site scripting, and provides guidance on how to prevent each vulnerability through practices like input validation, output encoding, and access controls. The goal is to help developers understand security risks and how to build more robust applications through secure coding and threat modeling.
Security Testing



Security TestingISsoft This document discusses the importance of security testing. It defines key security concepts like confidentiality, integrity, and availability. It describes common security testing methods like vulnerability scanning and penetration testing. It also provides examples of specific vulnerabilities like SQL injection, cross-site scripting, and social engineering attacks. The document seeks to demonstrate why organizations should invest in security testing now rather than just responding to attacks after they occur.
Exploring the Seven Key Attributes of Security Testing.pdf



Exploring the Seven Key Attributes of Security Testing.pdfAmeliaJonas2 Security Testing Service is a crucial process that evaluates the resilience of an organization's digital assets against potential cyberattacks. In this blog, we will delve into the seven key attributes of security testing and understand their significance in safeguarding our digital world.
Best Practices for Secure Web Application Development by Site Invention.pdf



Best Practices for Secure Web Application Development by Site Invention.pdfsiteseo In the era of digital transformation, web applications have become an essential part of business operations. However, there is a greater chance of security breaches as web apps become more and more reliant upon. This comprehensive guide will explore the best practices for secure web application development, with insights specifically tailored for web application development in Mumbai by the leading experts at Site Invention.
Top Cybersecurity Interview Questions.pdf



Top Cybersecurity Interview Questions.pdfinfosec train In today’s fast-paced digital landscape, staying ahead in cybersecurity is more crucial than ever. Understanding the **𝐓𝐨𝐩 𝐂𝐲𝐛𝐞𝐫𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐈𝐧𝐭𝐞𝐫𝐯𝐢𝐞𝐰 𝐐𝐮𝐞𝐬𝐭𝐢𝐨𝐧𝐬** can make all the difference for candidates and hiring managers alike.
Master Your next Cyber security Interview Questions.pdf



Master Your next Cyber security Interview Questions.pdfInfosecTrain In today’s fast-paced digital landscape, staying ahead in cybersecurity is more crucial than ever. Understanding the **𝐓𝐨𝐩 𝐂𝐲𝐛𝐞𝐫𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐈𝐧𝐭𝐞𝐫𝐯𝐢𝐞𝐰 𝐐𝐮𝐞𝐬𝐭𝐢𝐨𝐧𝐬** can make all the difference for candidates and hiring managers alike.
For more info to Checkout :- https://www.infosectrain.com/blog/top-cyber-security-interview-questions/
👉 **𝐃𝐨𝐰𝐧𝐥𝐨𝐚𝐝 𝐨𝐮𝐫 𝐠𝐮𝐢𝐝𝐞 𝐭𝐨𝐝𝐚𝐲** to equip yourself with the knowledge needed to stand out in your cybersecurity interviews!
Comment below with your favorite interview question or share your interview experiences! Let’s learn from each other!
InfosecTrain Top Cybersecurity Interview Questions



InfosecTrain Top Cybersecurity Interview Questionspriyanshamadhwal2 In today’s fast-paced digital landscape, staying ahead in cybersecurity is more crucial than ever. Understanding the 𝐓𝐨𝐩 𝐂𝐲𝐛𝐞𝐫𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐈𝐧𝐭𝐞𝐫𝐯𝐢𝐞𝐰 𝐐𝐮𝐞𝐬𝐭𝐢𝐨𝐧𝐬 can make all the difference for candidates and hiring managers alike.
View more: https://www.infosectrain.com/category/cybersecurity/
Ad
Recently uploaded (20)
Into The Box Conference Keynote Day 1 (ITB2025)



Into The Box Conference Keynote Day 1 (ITB2025)Ortus Solutions, Corp This is the keynote of the Into the Box conference, highlighting the release of the BoxLang JVM language, its key enhancements, and its vision for the future.
TrsLabs - Fintech Product & Business Consulting



TrsLabs - Fintech Product & Business ConsultingTrs Labs Hybrid Growth Mandate Model with TrsLabs
Strategic Investments, Inorganic Growth, Business Model Pivoting are critical activities that business don't do/change everyday. In cases like this, it may benefit your business to choose a temporary external consultant.
An unbiased plan driven by clearcut deliverables, market dynamics and without the influence of your internal office equations empower business leaders to make right choices.
Getting things done within a budget within a timeframe is key to Growing Business - No matter whether you are a start-up or a big company
Talk to us & Unlock the competitive advantage
Procurement Insights Cost To Value Guide.pptx



Procurement Insights Cost To Value Guide.pptxJon Hansen Procurement Insights integrated Historic Procurement Industry Archives, serves as a powerful complement — not a competitor — to other procurement industry firms. It fills critical gaps in depth, agility, and contextual insight that most traditional analyst and association models overlook.
Learn more about this value- driven proprietary service offering here.
How Can I use the AI Hype in my Business Context?



How Can I use the AI Hype in my Business Context?Daniel Lehner 𝙄𝙨 𝘼𝙄 𝙟𝙪𝙨𝙩 𝙝𝙮𝙥𝙚? 𝙊𝙧 𝙞𝙨 𝙞𝙩 𝙩𝙝𝙚 𝙜𝙖𝙢𝙚 𝙘𝙝𝙖𝙣𝙜𝙚𝙧 𝙮𝙤𝙪𝙧 𝙗𝙪𝙨𝙞𝙣𝙚𝙨𝙨 𝙣𝙚𝙚𝙙𝙨?
Everyone’s talking about AI but is anyone really using it to create real value?
Most companies want to leverage AI. Few know 𝗵𝗼𝘄.
✅ What exactly should you ask to find real AI opportunities?
✅ Which AI techniques actually fit your business?
✅ Is your data even ready for AI?
If you’re not sure, you’re not alone. This is a condensed version of the slides I presented at a Linkedin webinar for Tecnovy on 28.04.2025.
HCL Nomad Web – Best Practices and Managing Multiuser Environments



HCL Nomad Web – Best Practices and Managing Multiuser Environmentspanagenda Webinar Recording: https://www.panagenda.com/webinars/hcl-nomad-web-best-practices-and-managing-multiuser-environments/
HCL Nomad Web is heralded as the next generation of the HCL Notes client, offering numerous advantages such as eliminating the need for packaging, distribution, and installation. Nomad Web client upgrades will be installed “automatically” in the background. This significantly reduces the administrative footprint compared to traditional HCL Notes clients. However, troubleshooting issues in Nomad Web present unique challenges compared to the Notes client.
Join Christoph and Marc as they demonstrate how to simplify the troubleshooting process in HCL Nomad Web, ensuring a smoother and more efficient user experience.
In this webinar, we will explore effective strategies for diagnosing and resolving common problems in HCL Nomad Web, including
- Accessing the console
- Locating and interpreting log files
- Accessing the data folder within the browser’s cache (using OPFS)
- Understand the difference between single- and multi-user scenarios
- Utilizing Client Clocking
Massive Power Outage Hits Spain, Portugal, and France: Causes, Impact, and On...



Massive Power Outage Hits Spain, Portugal, and France: Causes, Impact, and On...Aqusag Technologies In late April 2025, a significant portion of Europe, particularly Spain, Portugal, and parts of southern France, experienced widespread, rolling power outages that continue to affect millions of residents, businesses, and infrastructure systems.
Linux Professional Institute LPIC-1 Exam.pdf



Linux Professional Institute LPIC-1 Exam.pdfRHCSA Guru Introduction to LPIC-1 Exam - overview, exam details, price and job opportunities
Special Meetup Edition - TDX Bengaluru Meetup #52.pptx



Special Meetup Edition - TDX Bengaluru Meetup #52.pptxshyamraj55 We’re bringing the TDX energy to our community with 2 power-packed sessions:
🛠️ Workshop: MuleSoft for Agentforce
Explore the new version of our hands-on workshop featuring the latest Topic Center and API Catalog updates.
📄 Talk: Power Up Document Processing
Dive into smart automation with MuleSoft IDP, NLP, and Einstein AI for intelligent document workflows.
#StandardsGoals for 2025: Standards & certification roundup - Tech Forum 2025



#StandardsGoals for 2025: Standards & certification roundup - Tech Forum 2025BookNet Canada Book industry standards are evolving rapidly. In the first part of this session, we’ll share an overview of key developments from 2024 and the early months of 2025. Then, BookNet’s resident standards expert, Tom Richardson, and CEO, Lauren Stewart, have a forward-looking conversation about what’s next.
Link to recording, transcript, and accompanying resource: https://bnctechforum.ca/sessions/standardsgoals-for-2025-standards-certification-roundup/
Presented by BookNet Canada on May 6, 2025 with support from the Department of Canadian Heritage.
Mobile App Development Company in Saudi Arabia



Mobile App Development Company in Saudi ArabiaSteve Jonas EmizenTech is a globally recognized software development company, proudly serving businesses since 2013. With over 11+ years of industry experience and a team of 200+ skilled professionals, we have successfully delivered 1200+ projects across various sectors. As a leading Mobile App Development Company In Saudi Arabia we offer end-to-end solutions for iOS, Android, and cross-platform applications. Our apps are known for their user-friendly interfaces, scalability, high performance, and strong security features. We tailor each mobile application to meet the unique needs of different industries, ensuring a seamless user experience. EmizenTech is committed to turning your vision into a powerful digital product that drives growth, innovation, and long-term success in the competitive mobile landscape of Saudi Arabia.
Semantic Cultivators : The Critical Future Role to Enable AI



Semantic Cultivators : The Critical Future Role to Enable AIartmondano By 2026, AI agents will consume 10x more enterprise data than humans, but with none of the contextual understanding that prevents catastrophic misinterpretations.
Cybersecurity Identity and Access Solutions using Azure AD



Cybersecurity Identity and Access Solutions using Azure ADVICTOR MAESTRE RAMIREZ Cybersecurity Identity and Access Solutions using Azure AD
The Evolution of Meme Coins A New Era for Digital Currency ppt.pdf



The Evolution of Meme Coins A New Era for Digital Currency ppt.pdfAbi john Analyze the growth of meme coins from mere online jokes to potential assets in the digital economy. Explore the community, culture, and utility as they elevate themselves to a new era in cryptocurrency.
Complete Guide to Advanced Logistics Management Software in Riyadh.pdf



Complete Guide to Advanced Logistics Management Software in Riyadh.pdfSoftware Company Explore the benefits and features of advanced logistics management software for businesses in Riyadh. This guide delves into the latest technologies, from real-time tracking and route optimization to warehouse management and inventory control, helping businesses streamline their logistics operations and reduce costs. Learn how implementing the right software solution can enhance efficiency, improve customer satisfaction, and provide a competitive edge in the growing logistics sector of Riyadh.
Cyber Awareness overview for 2025 month of security



Cyber Awareness overview for 2025 month of securityriccardosl1 Cyber awareness training educates employees on risk associated with internet and malicious emails
Linux Support for SMARC: How Toradex Empowers Embedded Developers



Linux Support for SMARC: How Toradex Empowers Embedded DevelopersToradex Toradex brings robust Linux support to SMARC (Smart Mobility Architecture), ensuring high performance and long-term reliability for embedded applications. Here’s how:
• Optimized Torizon OS & Yocto Support – Toradex provides Torizon OS, a Debian-based easy-to-use platform, and Yocto BSPs for customized Linux images on SMARC modules.
• Seamless Integration with i.MX 8M Plus and i.MX 95 – Toradex SMARC solutions leverage NXP’s i.MX 8 M Plus and i.MX 95 SoCs, delivering power efficiency and AI-ready performance.
• Secure and Reliable – With Secure Boot, over-the-air (OTA) updates, and LTS kernel support, Toradex ensures industrial-grade security and longevity.
• Containerized Workflows for AI & IoT – Support for Docker, ROS, and real-time Linux enables scalable AI, ML, and IoT applications.
• Strong Ecosystem & Developer Support – Toradex offers comprehensive documentation, developer tools, and dedicated support, accelerating time-to-market.
With Toradex’s Linux support for SMARC, developers get a scalable, secure, and high-performance solution for industrial, medical, and AI-driven applications.
Do you have a specific project or application in mind where you're considering SMARC? We can help with Free Compatibility Check and help you with quick time-to-market
For more information: https://www.toradex.com/computer-on-modules/smarc-arm-family
Transcript: #StandardsGoals for 2025: Standards & certification roundup - Tec...



Transcript: #StandardsGoals for 2025: Standards & certification roundup - Tec...BookNet Canada Book industry standards are evolving rapidly. In the first part of this session, we’ll share an overview of key developments from 2024 and the early months of 2025. Then, BookNet’s resident standards expert, Tom Richardson, and CEO, Lauren Stewart, have a forward-looking conversation about what’s next.
Link to recording, presentation slides, and accompanying resource: https://bnctechforum.ca/sessions/standardsgoals-for-2025-standards-certification-roundup/
Presented by BookNet Canada on May 6, 2025 with support from the Department of Canadian Heritage.
Dev Dives: Automate and orchestrate your processes with UiPath Maestro



Dev Dives: Automate and orchestrate your processes with UiPath MaestroUiPathCommunity This session is designed to equip developers with the skills needed to build mission-critical, end-to-end processes that seamlessly orchestrate agents, people, and robots.
📕 Here's what you can expect:
- Modeling: Build end-to-end processes using BPMN.
- Implementing: Integrate agentic tasks, RPA, APIs, and advanced decisioning into processes.
- Operating: Control process instances with rewind, replay, pause, and stop functions.
- Monitoring: Use dashboards and embedded analytics for real-time insights into process instances.
This webinar is a must-attend for developers looking to enhance their agentic automation skills and orchestrate robust, mission-critical processes.
👨🏫 Speaker:
Andrei Vintila, Principal Product Manager @UiPath
This session streamed live on April 29, 2025, 16:00 CET.
Check out all our upcoming Dev Dives sessions at https://community.uipath.com/dev-dives-automation-developer-2025/.
Security Testing
- 1. S ECURITY T ESTING FOR W EB AND M OBILE D EVELOPMENT Prepared by: Jyothi Venugopalan (QA Team Member) BOSS Webtech Private Limited www.bosswebtech.com
- 2. S ECURITY T ESTING The security testing is performed to check whether there is any information leakage in the sense by encrypting the application. Security testing is a process to determine that an information system protects data and maintains functionality as intended.
- 3. S ECURITY T ESTING The six basic security concepts: Authentication - It allows a receiver to have confidence that information it receives originated from a specific known source. Authorization - Determining that a requester is allowed to receive a service or perform an operation. Confidentiality - A security measure which protects the disclosure of data or information to parties other than the intended. Integrity – Whether the intended receiver receives the information or data which is not altered in transmission. Non-repudiation - Interchange of authentication information with some form of provable time stamp e.g. with session id etc. Availability - Assuring information and communications services will be ready for use when expected.
- 4. N EED OF S ECURITY T ESTING Security test helps in finding out loopholes that can cause loss of important information and allow any intruder enter into the systems. Security Testing helps in improving the current system. Ensures that the system will work for longer time. Ensures that people in your organization understand and obey security policies.
- 5. D IFFERENT T YPES OF S ECURITY T ESTING Security Auditing: Security Auditing includes direct inspection of the application developed and Operating Systems. This also involves code walk-through. Security Scanning: It is all about scanning and verification of the system and applications. Vulnerability Scanning: Vulnerability scanning involves scanning of the application for all known vulnerabilities. Risk Assessment: Risk assessment is a method of analyzing and deciding the risk that depends upon the type of loss and the possibility of loss occurrence. Penetration Testing: In this type of testing, a tester tries to forcibly access and enter the application under test. Ethical Hacking: It’s a forced intrusion of an external element into the system & applications that are under Security Testing.
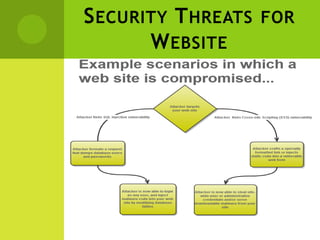
- 6. S ECURITY T HREATS FOR W EBSITE SQL Injection - Insertion of the SQL query into the web application which can directly interact with the backend database on server to reveal information stored in it. Cross Site Scripting- Insertion of the scripting code into client browser. So when client send data to server database, scripting code on client side get stored into the server database.
- 7. S ECURITY T HREATS FOR W EBSITE
- 8. S ECURITY T ESTING A PPROACH FOR W EBSITE Password cracking: In order to log in to the private areas of the application, one can either guess a username/ password or use some password cracker tool for the same. URL manipulation through HTTP GET methods: The tester should check if the application passes important information in the querystring. SQL Injection: Entering a single quote (‘) in any textbox should be rejected by the application. Cross Site Scripting (XSS): Any HTML e.g. <HTML> or any script e.g. <SCRIPT> should not be accepted by the application.
- 9. S ECURITY T HREATS FOR M OBILE A PPLICATION Mobile malware and viruses: A mobile virus is an electronic virus that targets mobile phones or wireless- enabled PDAs. Eavesdropping: Eavesdropping is the unauthorized real-time interception of a private communication, such as a phone call, instant message etc. Unauthorized access: careful attention needs to be paid to AAA – authentication, authorization, and accounting. Physical security: While many notebook computers are indeed lost or stolen every year, it's a lot easier to simply misplace a mobile device.
- 10. S ECURITY T ESTING A PPROACH FOR M OBILE A PPLICATION Authentication checks Input Validation checks Session Management checks Encryption checks Application checks SQL injection checks LDAP injection checks XPATH injection checks
- 11. S ECURITY T ESTING TOOLS Netsparker Community Edition Websecurify Wapiti N-Stalker skipfish Scrawler Watcher x5s Exploit-Me WebScarab
- 12. S UMMARY No Website is 100% Secure. Prevention is the better way to secure the website. Security Vulnerability arise on different ways which up on risks. The Critical risk is attacking the website and stealing the data.
- 14. A BOUT BOSS W EBTECH BOSS Webtech is a process oriented design house specializing in web design, web development, backend web programming, mobile application development and other web and mobile related design and support services. Recently launched BizPlus – Mobile based survey software. Check it more here http://bizplusonline.com/ More products here http://www.bosswebtech.com/products/products.html CONTACT BOSS WEBTECH Call 831-998-9121 at US EST/CST/MST/PST Zone or email [email protected]









