Setting Up .Onion Addresses for your Enterprise, v3.5
0 likes747 views
Onion networking provides an alternative to traditional IP networking by using self-authenticating onion addresses and circuits through the Tor network. Some key aspects of onion networking include: 1) It establishes circuits between clients and servers to transport TCP connections, similar to how IP uses frames and MAC addresses. 2) Onion addresses resolve to introduction points that introduce circuits to rendezvous points for communication, providing redundancy and avoiding single points of failure. 3) While slower than traditional networking due to additional hops, onion networking provides benefits like built-in anonymity, censorship resistance, and lack of single points of control due to its distributed nature.
1 of 79
Download to read offline


















![how do addresses work?
• all these addresses can be typed into a web browser:
• http://192.168.1.1/- ipv4, supported everywhere
• http://[fe80::226:21ff:fed8:fbc2]/ - ipv6, variable
• http://www.foo.com/ - dns, supported everywhere
• http://ylzpu2givhwizoep.onion/ - needs a Tor browser
• …they all connect you to a remote computer](https://image.slidesharecdn.com/settingupanonionaddress-v3-180514082314/85/Setting-Up-Onion-Addresses-for-your-Enterprise-v3-5-20-320.jpg)


























































Ad
Recommended
Why and How to use Onion Networking - #EMFCamp2018



Why and How to use Onion Networking - #EMFCamp2018Alec Muffett Outlining the hows and whys of using Onion Networking to connect apps, devices and tools securely over the Internet, without suffering blocks, NAT issues, or many forms of security woe.
Bh fed-03-kaminsky



Bh fed-03-kaminskyDan Kaminsky Using techniques like ARP spoofing and NAT, it is possible to acquire an IP address and internet access on a network without a DHCP server. By intercepting traffic between an existing node and gateway, one can insert themselves as the "man in the middle" and route traffic through a NAT configuration using the hijacked node's IP address. This allows acquiring internet access without a free IP address by multiplexing sessions through the NAT. Scanrand port scanning observations can also reveal network topology details like firewall locations through analysis of TTL values.
Design Reviewing The Web



Design Reviewing The Webamiable_indian The document summarizes Dan Kaminsky's talk at Black Hat 2007 about exploiting the DNS rebinding vulnerability to bypass firewalls and access internal networks from external web browsers. It describes how DNS rebinding works by abusing the same-origin policy to treat websites with different domain names but the same IP address as coming from the same origin. It then outlines several ways an attacker can force a domain to resolve to different IP addresses and use this to tunnel network traffic over the browser.
Shmoocon Epilogue 2013 - Ruining security models with SSH



Shmoocon Epilogue 2013 - Ruining security models with SSHAndrew Morris This document summarizes how SSH can be used to compromise security in several ways:
1. Authentication can be bypassed by generating a public key on an attacker's machine and transferring it to a victim's machine to allow code execution without a password.
2. SSH allows file transfer and traffic tunneling which can be used to transfer tools, exfiltrate data, and bypass firewalls by tunneling any protocol over an SSH connection.
3. Dynamic tunneling with tools like SOCKS and Proxychains allows running scans, exploits, and other tools through an SSH connection without needing privileged access on the target.
Phreebird Suite 1.0: Introducing the Domain Key Infrastructure



Phreebird Suite 1.0: Introducing the Domain Key InfrastructureDan Kaminsky Phreebird Suite 1.0 introduces the Domain Key Infrastructure through DNSSEC to enable easy and secure authentication across domains. It includes Phreebird, a zero configuration DNSSEC server that can sign responses in real-time without requiring offline key generation or zone signing. It also includes Phreeload, which integrates DNSSEC validation into OpenSSL using LD_PRELOAD to enable end-to-end security for applications. The suite aims to make DNSSEC easy to deploy and leverage its authentication capabilities to enable new secure cross-domain applications.
Flaying the Blockchain Ledger for Fun, Profit, and Hip Hop



Flaying the Blockchain Ledger for Fun, Profit, and Hip HopAndrew Morris This document provides an overview and summary of Andrew Morris' presentation titled "Flaying the Blockchain Ledger for Fun, Profit, and Hip Hop" given at BSides Las Vegas in 2016. The presentation discusses parsing and analyzing the Bitcoin blockchain ledger to find transactions of interest, such as a reported $15 million Bitcoin transaction by Martin Shkreli in early 2016.
The summary is:
1) Andrew Morris discusses parsing the Bitcoin blockchain ledger and loading it into a database to enable queries of transaction attributes like amount, time, and sender/receiver addresses.
2) He explores finding a reported $15 million Bitcoin transaction by Martin Shkreli around February 2016 through queries of the ledger database
Cloudstone - Sharpening Your Weapons Through Big Data



Cloudstone - Sharpening Your Weapons Through Big DataChristopher Grayson These slides were part of a presentation given at HushCon East 2017. The talk covered how we can use big data to improve the effectiveness of offensive security tools.
HTTP/2: What's new? 



HTTP/2: What's new? Piet van Dongen HTTP is dead, long live HTTP! 20 years ago, HTTP/1.1 was born and it has served us well. But a lot has changed since the time a single request was often enough to display a web page. Nowadays, web applications need lots of external resources, forcing us into hacky territory. We can do better!
HTTP/2 is here and you can and should use it. No more domain sharding, resource bundling, convoluted hacks. Instead, you get much better performance and security with less work than before. This talk focuses on HTTP's history and its new features: multiplexing, header compression, server push and more!
About Piet van Dongen
By day, Piet is a software engineer at Luminis, where he keeps himself busy doing the whole full stack thing. By night, he sleeps. The rest of the time, he mostly entertains his kids, wife and vacuum cleaner, sometimes locking himself in the bathroom to read his Twitter feed or a book.
CableTap - Wirelessly Tapping Your Home Network



CableTap - Wirelessly Tapping Your Home NetworkChristopher Grayson These are the slides from Marc Newlin, Logan Lamb, and Christopher Grayson's DEF CON 25 talk "CableTap - Wirelessly Tapping Your Home Network."
Grey H@t - DNS Cache Poisoning



Grey H@t - DNS Cache PoisoningChristopher Grayson This document discusses DNS cache poisoning. It begins by explaining what DNS is and its purpose of mapping domain names to IP addresses. It then discusses how DNS servers implement caching to improve performance and defines DNS cache poisoning as getting unauthorized entries into a DNS server's cache. The document outlines how an attacker could poison a cache to redirect traffic to a machine they control in order to perform man-in-the-middle attacks or install malware. It describes various methods of poisoning caches locally or remotely, such as between end users and nameservers or between nameservers themselves using the Kaminsky attack. Defenses like DNSSEC are mentioned along with encouragement to try cache poisoning in a controlled lab environment.
BlueHat v17 || Disrupting the Mirai Botnet 



BlueHat v17 || Disrupting the Mirai Botnet BlueHat Security Conference Chuck McAuley, Ixia Communications
The Mirai botnet has brought public awareness to the danger of poorly secured embedded devices. Its ability to propagate is fast and reliable. Its impact can be devastating and variants of it will be around for a long time. You need to identify it, stop it, and prevent its spread. I had the opportunity to become familiar with the structure, design, and weaknesses of Mirai and its variants. At this talk you'll learn how to detect members of the botnet, mess with them through various means and setup a safe live fire lab environment for your own amusement. I will demonstrate how to join a C2 server, how to collect new samples for study, and some changes that have occurred since release of the source code. By the end you'll be armed and ready to take the fight to these jerks. Unless you're a botnet operator. Then you'll learn about some of the mistakes you made.
Dmk bo2 k8_bh_fed



Dmk bo2 k8_bh_fedDan Kaminsky DNS is critical infrastructure that everything on the internet relies on, but it is inherently insecure. A significant vulnerability was found in 2008 that allowed cache poisoning attacks. While patching efforts were largely successful, some servers remain unpatched and attacks have been detected in the wild. The vulnerability illustrates how DNS insecurity can undermine higher-level security systems. DNS is difficult to secure due to its need to scale across organizational boundaries, but securing it through technologies like DNSSEC could help address lingering risks.
Dmk blackops2006



Dmk blackops2006Dan Kaminsky The document summarizes Dan Kaminsky's planned talks and demonstrations at Black Hat 2006. Some key points include:
- Enforcing network neutrality through detecting non-neutral networks using techniques like active network probing and analyzing TCP bandwidth.
- Findings from scanning over 2.4 million SSL servers, including many servers responding on port 443 without SSL enabled and variability in certificates served from the same IP.
- Demonstrating ways to securely login to online applications from an insecure home page using iframes to initialize SSL.
Dirty Little Secrets They Didn't Teach You In Pentest Class v2



Dirty Little Secrets They Didn't Teach You In Pentest Class v2Rob Fuller This talk (hopefully) provides some new pentesters tools and tricks. Basically a continuation of last year’s Dirty Little Secrets they didn’t teach you in Pentest class. Topics include; OSINT and APIs, certificate stealing, F**king with Incident Response Teams, 10 ways to psexec, and more. Yes, mostly using metasploit.
Dmk blackops2006 ccc



Dmk blackops2006 cccDan Kaminsky The document discusses using context-free grammars and symbol discovery techniques to analyze file formats, network protocols, and other data without prior knowledge of the structure or specification. It describes using the Sequitur algorithm to generate hierarchical grammars from arbitrary input data in order to discover meaningful symbols within it. It then suggests using the identified symbols to generate fuzzed or corrupted versions of the data in a structure-preserving manner, rather than simply flipping bits at random. Overall, the document argues that automatically discovering symbolic representations from raw data can enable more effective analysis and fuzzing of file formats, protocols, and other systems.
Confidence web



Confidence webDan Kaminsky The document discusses securing web applications. It argues that traditional approaches like blaming developers or banning third-party cookies are not effective solutions. Adding random tokens manually to URLs is difficult for developers. Using the referer header is unreliable due to inconsistencies across browsers and plugins. The origin header has similar problems. The document proposes an "interpreter suicide" approach where JavaScript detects cross-site navigation and prevents further execution to block attacks. This provides a client-side way to enforce session context without requiring manual token management.
Dmk bo2 k8



Dmk bo2 k8Dan Kaminsky This document summarizes Dan Kaminsky's 2008 talk at Black Hat about a vulnerability he discovered in the Domain Name System (DNS) that allowed attackers to spoof DNS responses. The vulnerability, known as DNS cache poisoning, could allow attackers to redirect traffic to malicious websites by guessing the random transaction ID associated with DNS queries. Kaminsky worked with DNS developers and organizations to coordinate a massive patching effort that updated DNS servers for over 120 million users within a few weeks. His talk analyzed the impact of the patching and discussed the technical details of how the vulnerability worked.
DNS Cache White Paper



DNS Cache White PaperRyan Ellingson 1. The document discusses DNS cache poisoning using a man-in-the-middle attack. It provides details on setting up the attack using Kali Linux, Windows Server 2008, and Windows 7. It clones the Facebook website and poisons the DNS cache so traffic is redirected to the fake site.
2. Testing confirms the attack was successful when pinging the fake Facebook site returns the IP of the Kali machine for both Windows systems. The document also proposes short and long-term solutions to prevent DNS cache poisoning attacks, such as disabling open recursive name servers and implementing DNSSEC.
3. In conclusion, the document notes that while DNS cache poisoning is easy to setup, protection requires more effort but is still important for network
Hot potato Privilege Escalation



Hot potato Privilege EscalationSunny Neo Hot Potato is a tool that combines three vulnerabilities - NetBIOS Name Service spoofing, Web Proxy Auto-Discovery Protocol man-in-the-middle attacks, and HTTP to SMB relaying - to perform privilege escalation on Windows systems. It takes advantage of legacy Windows protocols like NetBIOS and WPAD to trick applications into sending NTLM authentication credentials over HTTP, which are then relayed back over SMB to authenticate at a higher privilege level. Microsoft released patches in 2016 to address issues like local HTTP to SMB relaying and secure WPAD resolution. Disabling vulnerable legacy protocols, requiring SMB signing, and using more secure authentication methods like NTLMv2 or Kerberos can help prevent such privilege escalation attacks.
Using Secure Shell on Linux: What Everyone Should Know



Using Secure Shell on Linux: What Everyone Should KnowNovell Secure Shell, or SSH, is a network protocol that allows data to be exchanged over a secure channel. SSH is much more than just data being passed over the wire. SSH can be used to tunnel traffic and specific ports or applications across multiple servers. SSH is a must for anyone using Linux. If you haven't used SSH, then you have not used Linux!
This session is designed for all technical staff or decision makers curious about great Linux tools and making access to Windows services, remote desktops and remote servers easier and less complicated. During this session, we will demonstrate techniques to tunnel RDP sessions, SOAP sessions and HTTP sessions between remote systems.
Dns tunnelling its all in the name



Dns tunnelling its all in the nameSecurity BSides London BSidesLondon 20Th April 2011 - Arron "finux" Finnon
---------------------------------------------------------------------
The presentations aim is to talk about how simple it is to deploy DNS Tunnelling infrastructure at little or no cost. Also shows how to establish a ssh connection from target to attacker, and act as a taster for peoples further research.
----- for more about @F1nux go to www.finux.co.uk
CNIT 124: Ch 7: Capturing Traffic



CNIT 124: Ch 7: Capturing TrafficSam Bowne Slides for a college course in "Advanced Ethical Hacking" at CCSF. Instructor: Sam Bowne
Course Web page:
https://samsclass.info/124/124_F17.shtml
Based on "Penetration Testing: A Hands-On Introduction to Hacking" by Georgia Weidman -- ISBN-10: 1593275641, No Starch Press; 1 edition (June 8, 2014)
I See You



I See YouAndrew Beard The document summarizes the findings of network monitoring conducted at DEF CON 22. Some key points:
- Passwords and credentials were captured in plaintext for many protocols like POP3, IMAP, SMTP, FTP due to lack of encryption.
- HTTP requests were also intercepted containing usernames, passwords and API keys in the URL query string or HTTP Authorization header.
- Mobile app traffic was analyzed revealing personal user information like location data.
- Email contents were read, including unencrypted attachments containing sensitive personal information.
- With access to email, an attacker could potentially impersonate someone in a financial transaction.
The document warns that failing to use encryption leaves sensitive data vulnerable when on untrusted
Reinventing anon email



Reinventing anon emailantitree Comparison of TAILS vs Liberte and their popularity counterparts Cables and Bitmessage. Presented at Rochester 2600.
Black Ops of TCP/IP 2011 (Black Hat USA 2011)



Black Ops of TCP/IP 2011 (Black Hat USA 2011)Dan Kaminsky The document summarizes vulnerabilities in TCP/IP protocols that can enable spoofing attacks and de-anonymization of Bitcoin transactions. It describes how:
1) UPNP vulnerabilities on home routers can expose nodes running Bitcoin clients to the public internet, allowing identification of IP addresses associated with transactions.
2) IP spoofing techniques can still bypass access control lists (ACLs) due to weaknesses in sequence number generation for TCP connections.
3) SYN cookies used to mitigate SYN floods have limited effectiveness and can be bypassed with a large number of connection attempts.
Introduction to Penetration Testing



Introduction to Penetration TestingAndrew McNicol Introduction to Penetration Testing with a use case of LFI -> Shell. I talk about the mindset required to be a good tester, and show places many testers and automated tools stop and how to go further.
2nd ICANN APAC-TWNIC Engagement Forum: Why RPKI Matters



2nd ICANN APAC-TWNIC Engagement Forum: Why RPKI MattersAPNIC APNIC Product Manager, Registry Services George Michaelson present on why RPKI really matters at the 2nd ICANN APAC-TWNIC Engagement Forum, held from 15 to 16 April 2021.
Practical Malware Analysis Ch 14: Malware-Focused Network Signatures



Practical Malware Analysis Ch 14: Malware-Focused Network SignaturesSam Bowne This document discusses techniques for analyzing malware network signatures and developing effective network countermeasures. It describes using firewalls, proxies, and intrusion detection systems to filter malicious traffic. Deep packet inspection can detect malware beacons hidden in layers like HTTP user-agents. The document advises passively monitoring real infected networks to understand malware without tipping off attackers. It also provides methods for safely investigating attackers online anonymously. Analyzing how malware generates domain names and URLs can reveal signatures to detect similar strains. The goal is to create general signatures that still work if the malware evolves while avoiding false positives.
Setting-up a .Onion address for your Website, v1.5



Setting-up a .Onion address for your Website, v1.5Alec Muffett Setting up an .onion address allows websites to be accessed through the Tor network in order to provide greater privacy, security, and accessibility for users. There are several options for serving content on .onion addresses, including creating a dedicated onion site, configuring content management systems to be onion-aware, or installing an onion shim to rewrite requests and responses between a normal website and its onion domain. Considerations for onionifying a website include certifications, content leakage prevention, and whether to restrict certain features like payments over Tor.
BlueHat v17 || Dyre to Trickbot: An Inside Look at TLS-Encrypted Command-And-...



BlueHat v17 || Dyre to Trickbot: An Inside Look at TLS-Encrypted Command-And-...BlueHat Security Conference Andrew Brandt, Symantec
Back in 2014 and 2015, the Dyre (sometimes called Dyreza) Trojan was a distinctive crimeware tool for the simple reason that it appeared to employ, and experiment with, a whole range of sophisticated tactics, techniques and procedures: It was the first Trojan which exclusively employed HTTPS for its C2 traffic; It operated on a modular basis with a small cadre of other malware families, such as the Upatre downloader, which seemed to support it exclusively, as well as email address scraping tools and spam mail relayers; and it was at least as interested in profiling the environment it had infected as it was in exfiltrating any data it could find on the victim's machine. Then it disappeared suddenly, but re-emerged this year in the form of a Trojan now called Trickbot (aka Trickybot), completely rewritten but with many of the same features. In the lab, we permit Trickbot samples to persist on infected machines for days to weeks in order to perform man-in-the-middle SSL decryption on their C2 traffic. In this session, attendees will get a detailed forensic analysis of the content of some of this C2 traffic and the endpoint behavior of various machines (virtual and bare-metal) when left infected for an extended period of time. Finally, we will share what we know about the botnet's C2 infrastructure and its historical reputation. By understanding how Trickbot functions, and to where it communicates, we hope we can help identify infections more rapidly and, maybe, interpret the motives of whoever is operating this shadowy botnet to predict its next course of action.
Ad
More Related Content
What's hot (20)
CableTap - Wirelessly Tapping Your Home Network



CableTap - Wirelessly Tapping Your Home NetworkChristopher Grayson These are the slides from Marc Newlin, Logan Lamb, and Christopher Grayson's DEF CON 25 talk "CableTap - Wirelessly Tapping Your Home Network."
Grey H@t - DNS Cache Poisoning



Grey H@t - DNS Cache PoisoningChristopher Grayson This document discusses DNS cache poisoning. It begins by explaining what DNS is and its purpose of mapping domain names to IP addresses. It then discusses how DNS servers implement caching to improve performance and defines DNS cache poisoning as getting unauthorized entries into a DNS server's cache. The document outlines how an attacker could poison a cache to redirect traffic to a machine they control in order to perform man-in-the-middle attacks or install malware. It describes various methods of poisoning caches locally or remotely, such as between end users and nameservers or between nameservers themselves using the Kaminsky attack. Defenses like DNSSEC are mentioned along with encouragement to try cache poisoning in a controlled lab environment.
BlueHat v17 || Disrupting the Mirai Botnet 



BlueHat v17 || Disrupting the Mirai Botnet BlueHat Security Conference Chuck McAuley, Ixia Communications
The Mirai botnet has brought public awareness to the danger of poorly secured embedded devices. Its ability to propagate is fast and reliable. Its impact can be devastating and variants of it will be around for a long time. You need to identify it, stop it, and prevent its spread. I had the opportunity to become familiar with the structure, design, and weaknesses of Mirai and its variants. At this talk you'll learn how to detect members of the botnet, mess with them through various means and setup a safe live fire lab environment for your own amusement. I will demonstrate how to join a C2 server, how to collect new samples for study, and some changes that have occurred since release of the source code. By the end you'll be armed and ready to take the fight to these jerks. Unless you're a botnet operator. Then you'll learn about some of the mistakes you made.
Dmk bo2 k8_bh_fed



Dmk bo2 k8_bh_fedDan Kaminsky DNS is critical infrastructure that everything on the internet relies on, but it is inherently insecure. A significant vulnerability was found in 2008 that allowed cache poisoning attacks. While patching efforts were largely successful, some servers remain unpatched and attacks have been detected in the wild. The vulnerability illustrates how DNS insecurity can undermine higher-level security systems. DNS is difficult to secure due to its need to scale across organizational boundaries, but securing it through technologies like DNSSEC could help address lingering risks.
Dmk blackops2006



Dmk blackops2006Dan Kaminsky The document summarizes Dan Kaminsky's planned talks and demonstrations at Black Hat 2006. Some key points include:
- Enforcing network neutrality through detecting non-neutral networks using techniques like active network probing and analyzing TCP bandwidth.
- Findings from scanning over 2.4 million SSL servers, including many servers responding on port 443 without SSL enabled and variability in certificates served from the same IP.
- Demonstrating ways to securely login to online applications from an insecure home page using iframes to initialize SSL.
Dirty Little Secrets They Didn't Teach You In Pentest Class v2



Dirty Little Secrets They Didn't Teach You In Pentest Class v2Rob Fuller This talk (hopefully) provides some new pentesters tools and tricks. Basically a continuation of last year’s Dirty Little Secrets they didn’t teach you in Pentest class. Topics include; OSINT and APIs, certificate stealing, F**king with Incident Response Teams, 10 ways to psexec, and more. Yes, mostly using metasploit.
Dmk blackops2006 ccc



Dmk blackops2006 cccDan Kaminsky The document discusses using context-free grammars and symbol discovery techniques to analyze file formats, network protocols, and other data without prior knowledge of the structure or specification. It describes using the Sequitur algorithm to generate hierarchical grammars from arbitrary input data in order to discover meaningful symbols within it. It then suggests using the identified symbols to generate fuzzed or corrupted versions of the data in a structure-preserving manner, rather than simply flipping bits at random. Overall, the document argues that automatically discovering symbolic representations from raw data can enable more effective analysis and fuzzing of file formats, protocols, and other systems.
Confidence web



Confidence webDan Kaminsky The document discusses securing web applications. It argues that traditional approaches like blaming developers or banning third-party cookies are not effective solutions. Adding random tokens manually to URLs is difficult for developers. Using the referer header is unreliable due to inconsistencies across browsers and plugins. The origin header has similar problems. The document proposes an "interpreter suicide" approach where JavaScript detects cross-site navigation and prevents further execution to block attacks. This provides a client-side way to enforce session context without requiring manual token management.
Dmk bo2 k8



Dmk bo2 k8Dan Kaminsky This document summarizes Dan Kaminsky's 2008 talk at Black Hat about a vulnerability he discovered in the Domain Name System (DNS) that allowed attackers to spoof DNS responses. The vulnerability, known as DNS cache poisoning, could allow attackers to redirect traffic to malicious websites by guessing the random transaction ID associated with DNS queries. Kaminsky worked with DNS developers and organizations to coordinate a massive patching effort that updated DNS servers for over 120 million users within a few weeks. His talk analyzed the impact of the patching and discussed the technical details of how the vulnerability worked.
DNS Cache White Paper



DNS Cache White PaperRyan Ellingson 1. The document discusses DNS cache poisoning using a man-in-the-middle attack. It provides details on setting up the attack using Kali Linux, Windows Server 2008, and Windows 7. It clones the Facebook website and poisons the DNS cache so traffic is redirected to the fake site.
2. Testing confirms the attack was successful when pinging the fake Facebook site returns the IP of the Kali machine for both Windows systems. The document also proposes short and long-term solutions to prevent DNS cache poisoning attacks, such as disabling open recursive name servers and implementing DNSSEC.
3. In conclusion, the document notes that while DNS cache poisoning is easy to setup, protection requires more effort but is still important for network
Hot potato Privilege Escalation



Hot potato Privilege EscalationSunny Neo Hot Potato is a tool that combines three vulnerabilities - NetBIOS Name Service spoofing, Web Proxy Auto-Discovery Protocol man-in-the-middle attacks, and HTTP to SMB relaying - to perform privilege escalation on Windows systems. It takes advantage of legacy Windows protocols like NetBIOS and WPAD to trick applications into sending NTLM authentication credentials over HTTP, which are then relayed back over SMB to authenticate at a higher privilege level. Microsoft released patches in 2016 to address issues like local HTTP to SMB relaying and secure WPAD resolution. Disabling vulnerable legacy protocols, requiring SMB signing, and using more secure authentication methods like NTLMv2 or Kerberos can help prevent such privilege escalation attacks.
Using Secure Shell on Linux: What Everyone Should Know



Using Secure Shell on Linux: What Everyone Should KnowNovell Secure Shell, or SSH, is a network protocol that allows data to be exchanged over a secure channel. SSH is much more than just data being passed over the wire. SSH can be used to tunnel traffic and specific ports or applications across multiple servers. SSH is a must for anyone using Linux. If you haven't used SSH, then you have not used Linux!
This session is designed for all technical staff or decision makers curious about great Linux tools and making access to Windows services, remote desktops and remote servers easier and less complicated. During this session, we will demonstrate techniques to tunnel RDP sessions, SOAP sessions and HTTP sessions between remote systems.
Dns tunnelling its all in the name



Dns tunnelling its all in the nameSecurity BSides London BSidesLondon 20Th April 2011 - Arron "finux" Finnon
---------------------------------------------------------------------
The presentations aim is to talk about how simple it is to deploy DNS Tunnelling infrastructure at little or no cost. Also shows how to establish a ssh connection from target to attacker, and act as a taster for peoples further research.
----- for more about @F1nux go to www.finux.co.uk
CNIT 124: Ch 7: Capturing Traffic



CNIT 124: Ch 7: Capturing TrafficSam Bowne Slides for a college course in "Advanced Ethical Hacking" at CCSF. Instructor: Sam Bowne
Course Web page:
https://samsclass.info/124/124_F17.shtml
Based on "Penetration Testing: A Hands-On Introduction to Hacking" by Georgia Weidman -- ISBN-10: 1593275641, No Starch Press; 1 edition (June 8, 2014)
I See You



I See YouAndrew Beard The document summarizes the findings of network monitoring conducted at DEF CON 22. Some key points:
- Passwords and credentials were captured in plaintext for many protocols like POP3, IMAP, SMTP, FTP due to lack of encryption.
- HTTP requests were also intercepted containing usernames, passwords and API keys in the URL query string or HTTP Authorization header.
- Mobile app traffic was analyzed revealing personal user information like location data.
- Email contents were read, including unencrypted attachments containing sensitive personal information.
- With access to email, an attacker could potentially impersonate someone in a financial transaction.
The document warns that failing to use encryption leaves sensitive data vulnerable when on untrusted
Reinventing anon email



Reinventing anon emailantitree Comparison of TAILS vs Liberte and their popularity counterparts Cables and Bitmessage. Presented at Rochester 2600.
Black Ops of TCP/IP 2011 (Black Hat USA 2011)



Black Ops of TCP/IP 2011 (Black Hat USA 2011)Dan Kaminsky The document summarizes vulnerabilities in TCP/IP protocols that can enable spoofing attacks and de-anonymization of Bitcoin transactions. It describes how:
1) UPNP vulnerabilities on home routers can expose nodes running Bitcoin clients to the public internet, allowing identification of IP addresses associated with transactions.
2) IP spoofing techniques can still bypass access control lists (ACLs) due to weaknesses in sequence number generation for TCP connections.
3) SYN cookies used to mitigate SYN floods have limited effectiveness and can be bypassed with a large number of connection attempts.
Introduction to Penetration Testing



Introduction to Penetration TestingAndrew McNicol Introduction to Penetration Testing with a use case of LFI -> Shell. I talk about the mindset required to be a good tester, and show places many testers and automated tools stop and how to go further.
2nd ICANN APAC-TWNIC Engagement Forum: Why RPKI Matters



2nd ICANN APAC-TWNIC Engagement Forum: Why RPKI MattersAPNIC APNIC Product Manager, Registry Services George Michaelson present on why RPKI really matters at the 2nd ICANN APAC-TWNIC Engagement Forum, held from 15 to 16 April 2021.
Practical Malware Analysis Ch 14: Malware-Focused Network Signatures



Practical Malware Analysis Ch 14: Malware-Focused Network SignaturesSam Bowne This document discusses techniques for analyzing malware network signatures and developing effective network countermeasures. It describes using firewalls, proxies, and intrusion detection systems to filter malicious traffic. Deep packet inspection can detect malware beacons hidden in layers like HTTP user-agents. The document advises passively monitoring real infected networks to understand malware without tipping off attackers. It also provides methods for safely investigating attackers online anonymously. Analyzing how malware generates domain names and URLs can reveal signatures to detect similar strains. The goal is to create general signatures that still work if the malware evolves while avoiding false positives.
Similar to Setting Up .Onion Addresses for your Enterprise, v3.5 (20)
Setting-up a .Onion address for your Website, v1.5



Setting-up a .Onion address for your Website, v1.5Alec Muffett Setting up an .onion address allows websites to be accessed through the Tor network in order to provide greater privacy, security, and accessibility for users. There are several options for serving content on .onion addresses, including creating a dedicated onion site, configuring content management systems to be onion-aware, or installing an onion shim to rewrite requests and responses between a normal website and its onion domain. Considerations for onionifying a website include certifications, content leakage prevention, and whether to restrict certain features like payments over Tor.
BlueHat v17 || Dyre to Trickbot: An Inside Look at TLS-Encrypted Command-And-...



BlueHat v17 || Dyre to Trickbot: An Inside Look at TLS-Encrypted Command-And-...BlueHat Security Conference Andrew Brandt, Symantec
Back in 2014 and 2015, the Dyre (sometimes called Dyreza) Trojan was a distinctive crimeware tool for the simple reason that it appeared to employ, and experiment with, a whole range of sophisticated tactics, techniques and procedures: It was the first Trojan which exclusively employed HTTPS for its C2 traffic; It operated on a modular basis with a small cadre of other malware families, such as the Upatre downloader, which seemed to support it exclusively, as well as email address scraping tools and spam mail relayers; and it was at least as interested in profiling the environment it had infected as it was in exfiltrating any data it could find on the victim's machine. Then it disappeared suddenly, but re-emerged this year in the form of a Trojan now called Trickbot (aka Trickybot), completely rewritten but with many of the same features. In the lab, we permit Trickbot samples to persist on infected machines for days to weeks in order to perform man-in-the-middle SSL decryption on their C2 traffic. In this session, attendees will get a detailed forensic analysis of the content of some of this C2 traffic and the endpoint behavior of various machines (virtual and bare-metal) when left infected for an extended period of time. Finally, we will share what we know about the botnet's C2 infrastructure and its historical reputation. By understanding how Trickbot functions, and to where it communicates, we hope we can help identify infections more rapidly and, maybe, interpret the motives of whoever is operating this shadowy botnet to predict its next course of action.
NZNOG 2020: DOH



NZNOG 2020: DOHAPNIC APNIC Chief Scientist, Geoff Huston, gives a presentation on DOH and the changing nature of the DNS as infrastructure at NZNOG 2020 in Christchurch, New Zealand, from 28 to 31 January 2020.
The Background Noise of the Internet



The Background Noise of the InternetAndrew Morris The last five to ten years has seen massive advancements in open source Internet-wide mass-scan tooling, on-demand cloud computing, and high speed Internet connectivity. This has lead to a massive influx of different groups mass-scanning all four billion IP address in the IPv4 space on a constant basis. Information security researchers, cyber security companies, search engines, and criminals scan the Internet for various different benign and nefarious reasons (such as the WannaCry ransomware and multiple MongoDB, ElasticSearch, and Memcached ransomware variants). It is increasingly difficult to differentiate between scan/attack traffic targeting your organization specifically and opportunistic mass-scan background radiation packets.
Grey Noise is a system that records and analyzes all the collective omnidirectional background noise of the Internet, performs enrichments and analytics, and makes the data available to researchers for free. Traffic is collected by a large network of geographically and logically diverse “listener” servers distributed around different data centers belonging to different cloud providers and ISPs around the world.
In this talk I will candidly discuss motivations for developing the system, a technical deep dive on the architecture, data pipeline, and analytics, observations and analysis of the traffic collected by the system, business impacts for network operators, pitfalls and lessons learned, and the vision for the system moving forward.
Lares from LOW to PWNED



Lares from LOW to PWNEDChris Gates This document discusses various techniques for finding and exploiting vulnerabilities during a penetration test when vulnerabilities are marked as "low" or "medium" in severity. It argues that penetration testers and clients should not rely solely on vulnerability scanners and should thoroughly investigate even lower severity issues. Specific techniques mentioned include exploiting default credentials on services like VNC, exploiting exposed admin interfaces found through tools like Metasploit, taking advantage of browsable directories with backups or other sensitive files, exploiting SharePoint misconfigurations, exploiting HTTP PUT or WebDAV configurations, exploiting Apple Filing Protocol, and exploiting trace.axd to view request details in .NET applications. The document emphasizes finding overlooked vulnerabilities and keeping "a human in the mix" rather than full reliance
Meek and domain fronting public



Meek and domain fronting publicantitree This document discusses Meek and domain fronting as techniques for circumventing internet censorship. It provides an overview of censorship tools and the arms race between censors and circumvention methods. Meek uses domain fronting to hide proxy traffic by making encrypted requests to CDNs like Google and Cloudflare that appear as normal traffic, making the connections difficult for censors to block without blocking major sites. Meek has been implemented in tools like Psiphon and Tor to provide uncensorable access by tunneling their protocols over domain-fronted connections. While attacks from deep packet inspection are possible, Meek has so far proven very effective at evading censorship.
BSIDES-PR Keynote Hunting for Bad Guys



BSIDES-PR Keynote Hunting for Bad GuysJoff Thyer This document discusses techniques for hunting bad guys on networks, including identifying client-side attacks, malware command and control channels, post-exploitation activities, and hunting artifacts. It provides examples of using DNS logs, firewall logs, HTTP logs, registry keys, installed software inventories, and the AMCache registry hive to look for anomalous behaviors that could indicate security compromises. The goal is to actively hunt for threats rather than just detecting known bad behaviors.
Dmk Bo2 K7 Web



Dmk Bo2 K7 Webroyans This document summarizes Dan Kaminsky's 2007 talk at Black Hat about exploiting vulnerabilities in the DNS system and web browser security policies to enable arbitrary TCP and UDP access from within a web browser. Kaminsky describes how controlling DNS responses allows an attacker to bypass firewalls and access internal networks by manipulating the browser's view of domain names and IP addresses. He then outlines his proof-of-concept attack software called "Slirpie" that implements a VPN-like tunnel using only a compromised web browser.
OFFENSIVE: Exploiting DNS servers changes BlackHat Asia 2014



OFFENSIVE: Exploiting DNS servers changes BlackHat Asia 2014Leonardo Nve Egea This document discusses exploiting changes to DNS server configurations to intercept network traffic. It begins by introducing the speaker and their background in security research. Then it outlines normal exploitation procedures like CSRF, default passwords, and rogue DSLAMs. The document explores using tools like Metasploit, Dnsmasq and Bind to hijack DNS servers and redirect traffic. It discusses obstacles like SSL certificates and ways to improve attacks using features like DNS load balancing. The document demonstrates a proof of concept tool called dns2proxy that can spoof and redirect DNS responses. It also discusses defeating protections like HSTS and exploring attacks using protocols like UDP. In conclusion, the document advocates that improved DNS hijacking using multiple tools can capture more information than
Introduction to Computer Networking



Introduction to Computer NetworkingAmit Saha This slide deck was used for a 2-day short course at IIT Gandhinagar in Spring 2015. Being a 2-day course, it focuses more on a qualitative description of how we access the Internet.
Part 6 : Internet applications



Part 6 : Internet applicationsOlivier Bonaventure Slides supporting the "Computer Networking: Principles, Protocols and Practice" ebook. The slides can be freely reused to teach an undergraduate computer networking class using the open-source ebook.
Workshop on Network Security



Workshop on Network SecurityUC San Diego @skeptic_fx (Ahamed Nafeez) and I conducted a National Level Workshop on Network and Web Security on August 11th, 2010 during our third year BE CSE.
P2P Lecture.ppt



P2P Lecture.pptJohnRebenRequinto1 P2P systems utilize the resources of nodes at the edge of the internet in a decentralized way. Each node acts as both a client and server. An overlay network forms the virtual connections between peers. Structured overlays arrange peers in a restrictive structure to enable efficient lookup, while unstructured overlays connect peers randomly. Popular applications include file sharing with BitTorrent maximizing bandwidth usage, and communications with Skype utilizing direct peer connections. Management of these dynamic networks under high churn is an ongoing challenge.
Trick or XFLTReaT a.k.a. Tunnel All The Things



Trick or XFLTReaT a.k.a. Tunnel All The ThingsBalazs Bucsay XFLTReaT presentation from RuxCon 2017
This presentation will sum up how to do tunnelling with different protocols and will have different perspectives detailed. For example, companies are fighting hard to block exfiltration from their network: they use http(s) proxies, DLP, IPS technologies to protect their data, but are they protected against tunnelling? There are so many interesting questions to answer for users, abusers, companies and malware researchers. Mitigation and bypass techniques will be shown you during this presentation, which can be used to filter any tunnelling on your network or to bypass misconfigured filters.
Our new tool XFLTReaT is an open-source tunnelling framework that handles all the boring stuff and gives users the capability to take care of only the things that matter. It provides significant improvements over existing tools. From now on there is no need to write a new tunnel for each and every protocol or to deal with interfaces and routing. Any protocol can be converted to a module, which works in a plug-and-play fashion; authentication and encryption can be configured and customised on all traffic and it is also worth mentioning that the framework was designed to be easy to configure, use and develop. In case there is a need to send packets over ICMP type 0 or HTTPS TLS v1.2 with a special header, then this can be done in a matter of minutes, instead of developing a new tool from scratch. The potential use (or abuse) cases are plentiful, such as bypassing network restrictions of an ISP, the proxy of a workplace or obtaining Internet connectivity through bypassing captive portals in the middle of the Atlantic Ocean or at an altitude of 33000ft on an airplane.
This framework is not just a tool; it unites different technologies in the field of tunnelling. While we needed to use different tunnels and VPNs for different protocols in the past like OpenVPN for TCP and UDP, ptunnel for ICMP or iodined for DNS tunnelling, it changes now. After taking a look at these tools it was easy to see some commonality, all of them are doing the same things only the means of communication are different. We simplified the whole process and created a framework that is responsible for everything but the communication itself, we rethought the old way of tunnelling and tried to give something new to the community. After the initial setup the framework takes care of everything. With the check functionality we can even find out, which module can be used on the network, there is no need for any low-level packet fu and hassle. I guarantee that you won’t be disappointed with the tool and the talk, actually you will be richer with an open-source tool.
Basic computers for DIU laptop project students



Basic computers for DIU laptop project studentsAlauddin Azad The workshop aims to provide career awareness to DIU students by covering basic computer skills and careers. Topics include computer hardware, software, the internet, networks and careers. It will discuss components like the motherboard, CPU, RAM, hard drive and operating systems. Applications like Microsoft Office will be demonstrated. The internet, protocols, websites and search engines will be introduced. Networking concepts such as topologies, devices and addressing will be explained. The workshop aims to help students understand computer fundamentals and apply online for jobs.
DEF CON 27 - ORANGE TSAI and MEH CHANG - infiltrating corporate intranet like...



DEF CON 27 - ORANGE TSAI and MEH CHANG - infiltrating corporate intranet like...Felipe Prado DEF CON 27 - ORANGE TSAI and MEH CHANG - infiltrating corporate intranet like nsa pre auth rce on leading ssl vpns
SIP trunking in Janus @ Kamailio World 2024



SIP trunking in Janus @ Kamailio World 2024Lorenzo Miniero Slides for my "Am I sober or am I trunk? A Janus story" presentation at Kamailio World 2024.
They describe my prototype efforts to add an option to create a trunk between a Janus instance and a SIP server, with the related implementation challenges and the interesting opportunities it opens.
Distributed "Web Scale" Systems



Distributed "Web Scale" SystemsRicardo Vice Santos Ricardo Vice Santos discusses distributed, web-scale systems used at Spotify. He explains that Spotify uses a decentralized architecture with services that are decoupled and horizontally scalable. Key services are read-only for scalability and use techniques like DNS lookups, sharding via consistent hashing, and eventual consistency across replicas to distribute load. This allows Spotify to provide fast, reliable music streaming at a massive scale.
XFLTReaT: a new dimension in tunnelling (BruCON 0x09 2017)



XFLTReaT: a new dimension in tunnelling (BruCON 0x09 2017)Balazs Bucsay XFLTReaT presentation from BruCON 0x09 2017
https://www.youtube.com/watch?v=0hnxgu8lkfc
This presentation will sum up how to do tunnelling with different protocols and will have different perspectives detailed. For example, companies are fighting hard to block exfiltration from their network: they use http(s) proxies, DLP, IPS technologies to protect their data, but are they protected against tunnelling? There are so many interesting questions to answer for users, abusers, companies and malware researchers. Mitigation and bypass techniques will be shown you during this presentation, which can be used to filter any tunnelling on your network or to bypass misconfigured filters.
Our new tool XFLTReaT is an open-source tunnelling framework that handles all the boring stuff and gives users the capability to take care of only the things that matter. It provides significant improvements over existing tools. From now on there is no need to write a new tunnel for each and every protocol or to deal with interfaces and routing. Any protocol can be converted to a module, which works in a plug-and-play fashion; authentication and encryption can be configured and customised on all traffic and it is also worth mentioning that the framework was designed to be easy to configure, use and develop. In case there is a need to send packets over ICMP type 0 or HTTPS TLS v1.2 with a special header, then this can be done in a matter of minutes, instead of developing a new tool from scratch. The potential use (or abuse) cases are plentiful, such as bypassing network restrictions of an ISP, the proxy of a workplace or obtaining Internet connectivity through bypassing captive portals in the middle of the Atlantic Ocean or at an altitude of 33000ft on an airplane.
This framework is not just a tool; it unites different technologies in the field of tunnelling. While we needed to use different tunnels and VPNs for different protocols in the past like OpenVPN for TCP and UDP, ptunnel for ICMP or iodined for DNS tunnelling, it changes now. After taking a look at these tools it was easy to see some commonality, all of them are doing the same things only the means of communication are different. We simplified the whole process and created a framework that is responsible for everything but the communication itself, we rethought the old way of tunnelling and tried to give something new to the community. After the initial setup the framework takes care of everything. With the check functionality we can even find out, which module can be used on the network, there is no need for any low-level packet fu and hassle. I guarantee that you won’t be disappointed with the tool and the talk, actually you will be richer with an open-source tool.
Burp suite



Burp suiteYashar Shahinzadeh This document provides an overview of Burp Suite and how to use its features to perform vulnerability assessments. It discusses Burp Suite's key components like the proxy, scanner, intruder, repeater, collaborator, and extender. It also covers techniques like bypassing filters, server-side request forgery, XML external entities, and common vulnerabilities to target like open redirects, insufficient entropy, and insecure deserialization.
BlueHat v17 || Dyre to Trickbot: An Inside Look at TLS-Encrypted Command-And-...



BlueHat v17 || Dyre to Trickbot: An Inside Look at TLS-Encrypted Command-And-...BlueHat Security Conference
Ad
More from Alec Muffett (6)
How To Think Clearly About Cybersecurity v2



How To Think Clearly About Cybersecurity v2Alec Muffett The document discusses the concept of "cybersecurity" and argues that it is an unsuitable model for describing challenges related to information and network security. It notes that the word "cybersecurity" implies a virtual space or domain that functions similarly to the real world, but that this is an inaccurate analogy. Several examples are given to illustrate how aspects like theft work differently in a digital context versus the physical world. The thesis being defended is that the "cybersecurity" model tends to promote misguided strategies, excessive costs, and illiberal policies if not supplemented with other perspectives.
Sex, Lies & Instant Messenger v3



Sex, Lies & Instant Messenger v3Alec Muffett The document discusses the risks of using various communication methods like instant messengers and social media for private conversations. It recommends avoiding using Skype, XMPP-based chat, and Twitter for intimate discussions as the messages could be seen by unintended recipients due to features of the platforms. The document instead suggests using simple web-based chat systems and exercising caution to avoid typos or accidental oversharing of private content.
You and Your Phone are Huge Threats to the Net



You and Your Phone are Huge Threats to the NetAlec Muffett The document discusses how smartphones and their users unintentionally threaten network openness through their acceptance of network address translation (NAT) and firewalling. This isolation allows easier censorship and control of the network compared to direct communication. However, NAT is implemented on smartphones not for security but because it is expected by users. New technologies like IPv6, alternative DNS systems, and Tor could help promote more open connectivity.
How To Think Clearly About Cybersecurity v1



How To Think Clearly About Cybersecurity v1Alec Muffett The document discusses the concept of "cybersecurity" and argues that the common model of viewing cyberspace as a physical space is flawed and has been adopted by states in a way that is misguided. It asserts that this model promotes expensive and illiberal security strategies and greater state control over communication if not balanced with other perspectives. The document aims to critique the dominant metaphor of "cybersecurity" and suggest alternative ways of thinking about information and network security.
Sex, Lies and Instant Messenger v1



Sex, Lies and Instant Messenger v1Alec Muffett Adultery is one of the oldest of human preoccupations, but the modern world of social networking and instant messaging is ill-suited to discreet and deniable infidelities. In this talk we will describe what can go wrong with your intra-affair communications, how to avoid such mistakes, and what lessons can be learned.
Ad
Recently uploaded (20)
Big Data Analytics Quick Research Guide by Arthur Morgan



Big Data Analytics Quick Research Guide by Arthur MorganArthur Morgan This is a Quick Research Guide (QRG).
QRGs include the following:
- A brief, high-level overview of the QRG topic.
- A milestone timeline for the QRG topic.
- Links to various free online resource materials to provide a deeper dive into the QRG topic.
- Conclusion and a recommendation for at least two books available in the SJPL system on the QRG topic.
QRGs planned for the series:
- Artificial Intelligence QRG
- Quantum Computing QRG
- Big Data Analytics QRG
- Spacecraft Guidance, Navigation & Control QRG (coming 2026)
- UK Home Computing & The Birth of ARM QRG (coming 2027)
Any questions or comments?
- Please contact Arthur Morgan at [email protected].
100% human made.
AI EngineHost Review: Revolutionary USA Datacenter-Based Hosting with NVIDIA ...



AI EngineHost Review: Revolutionary USA Datacenter-Based Hosting with NVIDIA ...SOFTTECHHUB I started my online journey with several hosting services before stumbling upon Ai EngineHost. At first, the idea of paying one fee and getting lifetime access seemed too good to pass up. The platform is built on reliable US-based servers, ensuring your projects run at high speeds and remain safe. Let me take you step by step through its benefits and features as I explain why this hosting solution is a perfect fit for digital entrepreneurs.
The Evolution of Meme Coins A New Era for Digital Currency ppt.pdf



The Evolution of Meme Coins A New Era for Digital Currency ppt.pdfAbi john Analyze the growth of meme coins from mere online jokes to potential assets in the digital economy. Explore the community, culture, and utility as they elevate themselves to a new era in cryptocurrency.
DevOpsDays Atlanta 2025 - Building 10x Development Organizations.pptx



DevOpsDays Atlanta 2025 - Building 10x Development Organizations.pptxJustin Reock Building 10x Organizations with Modern Productivity Metrics
10x developers may be a myth, but 10x organizations are very real, as proven by the influential study performed in the 1980s, ‘The Coding War Games.’
Right now, here in early 2025, we seem to be experiencing YAPP (Yet Another Productivity Philosophy), and that philosophy is converging on developer experience. It seems that with every new method we invent for the delivery of products, whether physical or virtual, we reinvent productivity philosophies to go alongside them.
But which of these approaches actually work? DORA? SPACE? DevEx? What should we invest in and create urgency behind today, so that we don’t find ourselves having the same discussion again in a decade?
Quantum Computing Quick Research Guide by Arthur Morgan



Quantum Computing Quick Research Guide by Arthur MorganArthur Morgan This is a Quick Research Guide (QRG).
QRGs include the following:
- A brief, high-level overview of the QRG topic.
- A milestone timeline for the QRG topic.
- Links to various free online resource materials to provide a deeper dive into the QRG topic.
- Conclusion and a recommendation for at least two books available in the SJPL system on the QRG topic.
QRGs planned for the series:
- Artificial Intelligence QRG
- Quantum Computing QRG
- Big Data Analytics QRG
- Spacecraft Guidance, Navigation & Control QRG (coming 2026)
- UK Home Computing & The Birth of ARM QRG (coming 2027)
Any questions or comments?
- Please contact Arthur Morgan at [email protected].
100% human made.
What is Model Context Protocol(MCP) - The new technology for communication bw...



What is Model Context Protocol(MCP) - The new technology for communication bw...Vishnu Singh Chundawat The MCP (Model Context Protocol) is a framework designed to manage context and interaction within complex systems. This SlideShare presentation will provide a detailed overview of the MCP Model, its applications, and how it plays a crucial role in improving communication and decision-making in distributed systems. We will explore the key concepts behind the protocol, including the importance of context, data management, and how this model enhances system adaptability and responsiveness. Ideal for software developers, system architects, and IT professionals, this presentation will offer valuable insights into how the MCP Model can streamline workflows, improve efficiency, and create more intuitive systems for a wide range of use cases.
Linux Support for SMARC: How Toradex Empowers Embedded Developers



Linux Support for SMARC: How Toradex Empowers Embedded DevelopersToradex Toradex brings robust Linux support to SMARC (Smart Mobility Architecture), ensuring high performance and long-term reliability for embedded applications. Here’s how:
• Optimized Torizon OS & Yocto Support – Toradex provides Torizon OS, a Debian-based easy-to-use platform, and Yocto BSPs for customized Linux images on SMARC modules.
• Seamless Integration with i.MX 8M Plus and i.MX 95 – Toradex SMARC solutions leverage NXP’s i.MX 8 M Plus and i.MX 95 SoCs, delivering power efficiency and AI-ready performance.
• Secure and Reliable – With Secure Boot, over-the-air (OTA) updates, and LTS kernel support, Toradex ensures industrial-grade security and longevity.
• Containerized Workflows for AI & IoT – Support for Docker, ROS, and real-time Linux enables scalable AI, ML, and IoT applications.
• Strong Ecosystem & Developer Support – Toradex offers comprehensive documentation, developer tools, and dedicated support, accelerating time-to-market.
With Toradex’s Linux support for SMARC, developers get a scalable, secure, and high-performance solution for industrial, medical, and AI-driven applications.
Do you have a specific project or application in mind where you're considering SMARC? We can help with Free Compatibility Check and help you with quick time-to-market
For more information: https://www.toradex.com/computer-on-modules/smarc-arm-family
AI Changes Everything – Talk at Cardiff Metropolitan University, 29th April 2...



AI Changes Everything – Talk at Cardiff Metropolitan University, 29th April 2...Alan Dix Talk at the final event of Data Fusion Dynamics: A Collaborative UK-Saudi Initiative in Cybersecurity and Artificial Intelligence funded by the British Council UK-Saudi Challenge Fund 2024, Cardiff Metropolitan University, 29th April 2025
https://alandix.com/academic/talks/CMet2025-AI-Changes-Everything/
Is AI just another technology, or does it fundamentally change the way we live and think?
Every technology has a direct impact with micro-ethical consequences, some good, some bad. However more profound are the ways in which some technologies reshape the very fabric of society with macro-ethical impacts. The invention of the stirrup revolutionised mounted combat, but as a side effect gave rise to the feudal system, which still shapes politics today. The internal combustion engine offers personal freedom and creates pollution, but has also transformed the nature of urban planning and international trade. When we look at AI the micro-ethical issues, such as bias, are most obvious, but the macro-ethical challenges may be greater.
At a micro-ethical level AI has the potential to deepen social, ethnic and gender bias, issues I have warned about since the early 1990s! It is also being used increasingly on the battlefield. However, it also offers amazing opportunities in health and educations, as the recent Nobel prizes for the developers of AlphaFold illustrate. More radically, the need to encode ethics acts as a mirror to surface essential ethical problems and conflicts.
At the macro-ethical level, by the early 2000s digital technology had already begun to undermine sovereignty (e.g. gambling), market economics (through network effects and emergent monopolies), and the very meaning of money. Modern AI is the child of big data, big computation and ultimately big business, intensifying the inherent tendency of digital technology to concentrate power. AI is already unravelling the fundamentals of the social, political and economic world around us, but this is a world that needs radical reimagining to overcome the global environmental and human challenges that confront us. Our challenge is whether to let the threads fall as they may, or to use them to weave a better future.
#StandardsGoals for 2025: Standards & certification roundup - Tech Forum 2025



#StandardsGoals for 2025: Standards & certification roundup - Tech Forum 2025BookNet Canada Book industry standards are evolving rapidly. In the first part of this session, we’ll share an overview of key developments from 2024 and the early months of 2025. Then, BookNet’s resident standards expert, Tom Richardson, and CEO, Lauren Stewart, have a forward-looking conversation about what’s next.
Link to recording, transcript, and accompanying resource: https://bnctechforum.ca/sessions/standardsgoals-for-2025-standards-certification-roundup/
Presented by BookNet Canada on May 6, 2025 with support from the Department of Canadian Heritage.
Rusty Waters: Elevating Lakehouses Beyond Spark



Rusty Waters: Elevating Lakehouses Beyond Sparkcarlyakerly1 Spark is a powerhouse for large datasets, but when it comes to smaller data workloads, its overhead can sometimes slow things down. What if you could achieve high performance and efficiency without the need for Spark?
At S&P Global Commodity Insights, having a complete view of global energy and commodities markets enables customers to make data-driven decisions with confidence and create long-term, sustainable value. 🌍
Explore delta-rs + CDC and how these open-source innovations power lightweight, high-performance data applications beyond Spark! 🚀
Technology Trends in 2025: AI and Big Data Analytics



Technology Trends in 2025: AI and Big Data AnalyticsInData Labs At InData Labs, we have been keeping an ear to the ground, looking out for AI-enabled digital transformation trends coming our way in 2025. Our report will provide a look into the technology landscape of the future, including:
-Artificial Intelligence Market Overview
-Strategies for AI Adoption in 2025
-Anticipated drivers of AI adoption and transformative technologies
-Benefits of AI and Big data for your business
-Tips on how to prepare your business for innovation
-AI and data privacy: Strategies for securing data privacy in AI models, etc.
Download your free copy nowand implement the key findings to improve your business.
How Can I use the AI Hype in my Business Context?



How Can I use the AI Hype in my Business Context?Daniel Lehner 𝙄𝙨 𝘼𝙄 𝙟𝙪𝙨𝙩 𝙝𝙮𝙥𝙚? 𝙊𝙧 𝙞𝙨 𝙞𝙩 𝙩𝙝𝙚 𝙜𝙖𝙢𝙚 𝙘𝙝𝙖𝙣𝙜𝙚𝙧 𝙮𝙤𝙪𝙧 𝙗𝙪𝙨𝙞𝙣𝙚𝙨𝙨 𝙣𝙚𝙚𝙙𝙨?
Everyone’s talking about AI but is anyone really using it to create real value?
Most companies want to leverage AI. Few know 𝗵𝗼𝘄.
✅ What exactly should you ask to find real AI opportunities?
✅ Which AI techniques actually fit your business?
✅ Is your data even ready for AI?
If you’re not sure, you’re not alone. This is a condensed version of the slides I presented at a Linkedin webinar for Tecnovy on 28.04.2025.
Transcript: #StandardsGoals for 2025: Standards & certification roundup - Tec...



Transcript: #StandardsGoals for 2025: Standards & certification roundup - Tec...BookNet Canada Book industry standards are evolving rapidly. In the first part of this session, we’ll share an overview of key developments from 2024 and the early months of 2025. Then, BookNet’s resident standards expert, Tom Richardson, and CEO, Lauren Stewart, have a forward-looking conversation about what’s next.
Link to recording, presentation slides, and accompanying resource: https://bnctechforum.ca/sessions/standardsgoals-for-2025-standards-certification-roundup/
Presented by BookNet Canada on May 6, 2025 with support from the Department of Canadian Heritage.
Drupalcamp Finland – Measuring Front-end Energy Consumption



Drupalcamp Finland – Measuring Front-end Energy ConsumptionExove How to measure web front-end energy consumption using Firefox Profiler. Presented in DrupalCamp Finland on April 25th, 2025.
Designing Low-Latency Systems with Rust and ScyllaDB: An Architectural Deep Dive



Designing Low-Latency Systems with Rust and ScyllaDB: An Architectural Deep DiveScyllaDB Want to learn practical tips for designing systems that can scale efficiently without compromising speed?
Join us for a workshop where we’ll address these challenges head-on and explore how to architect low-latency systems using Rust. During this free interactive workshop oriented for developers, engineers, and architects, we’ll cover how Rust’s unique language features and the Tokio async runtime enable high-performance application development.
As you explore key principles of designing low-latency systems with Rust, you will learn how to:
- Create and compile a real-world app with Rust
- Connect the application to ScyllaDB (NoSQL data store)
- Negotiate tradeoffs related to data modeling and querying
- Manage and monitor the database for consistently low latencies
Splunk Security Update | Public Sector Summit Germany 2025



Splunk Security Update | Public Sector Summit Germany 2025Splunk Splunk Security Update
Sprecher: Marcel Tanuatmadja
HCL Nomad Web – Best Practices und Verwaltung von Multiuser-Umgebungen



HCL Nomad Web – Best Practices und Verwaltung von Multiuser-Umgebungenpanagenda Webinar Recording: https://www.panagenda.com/webinars/hcl-nomad-web-best-practices-und-verwaltung-von-multiuser-umgebungen/
HCL Nomad Web wird als die nächste Generation des HCL Notes-Clients gefeiert und bietet zahlreiche Vorteile, wie die Beseitigung des Bedarfs an Paketierung, Verteilung und Installation. Nomad Web-Client-Updates werden “automatisch” im Hintergrund installiert, was den administrativen Aufwand im Vergleich zu traditionellen HCL Notes-Clients erheblich reduziert. Allerdings stellt die Fehlerbehebung in Nomad Web im Vergleich zum Notes-Client einzigartige Herausforderungen dar.
Begleiten Sie Christoph und Marc, während sie demonstrieren, wie der Fehlerbehebungsprozess in HCL Nomad Web vereinfacht werden kann, um eine reibungslose und effiziente Benutzererfahrung zu gewährleisten.
In diesem Webinar werden wir effektive Strategien zur Diagnose und Lösung häufiger Probleme in HCL Nomad Web untersuchen, einschließlich
- Zugriff auf die Konsole
- Auffinden und Interpretieren von Protokolldateien
- Zugriff auf den Datenordner im Cache des Browsers (unter Verwendung von OPFS)
- Verständnis der Unterschiede zwischen Einzel- und Mehrbenutzerszenarien
- Nutzung der Client Clocking-Funktion
What is Model Context Protocol(MCP) - The new technology for communication bw...



What is Model Context Protocol(MCP) - The new technology for communication bw...Vishnu Singh Chundawat
Setting Up .Onion Addresses for your Enterprise, v3.5
- 1. setting up .onion addresses …for your website enterprise v3.5 - @alecmuffett 2018
- 2. hi!
- 3. BBC Radio 4, circa 2012 <cyber type="ominous"/>
- 4. "awesome!"
- 5. "dark net" not as scary as advertised
- 6. <years n=2/>
- 8. <years n=2/>
- 9. <downshift/>
- 10. <bored/>
- 13. why .onion? • you have a community, or you have an audience • for some, ability to access content is hampered • for some, risk of fake websites, credential theft, or political repercussions for accessing content • for some, privacy, assurance & trust is paramount
- 14. social value of .onion? • greater assurance • facebookcorewwwi.onion => genuine facebook • greater availability & privacy • .onion => hard to block/surveil (if sometimes a little flaky) • fewer digital footprints • people using onions are perforce using tor browser • tor browser is generally better at data "hygiene"
- 15. tech value of .onion? <see second half of presentation>
- 16. desktop? mobile? both? • Mac / Win / Linux • tor browser (integrated tor + custom-tuned firefox) • Android • orbot (tor) + orfox (browser) • iOS • onion browser (integrated) • other iOS in progress
- 18. what is .onion? "the top level domain name for the onion namespace"
- 19. what is a namespace? • namespace is "an address + what it means/looks like" • ipv4 addresses look like: 192.168.1.1 • ipv6 addresses look like: fe80::226:21ff:fed8:fbc2 • dns addresses look like: www.foo.com • onion addresses look like: ylzpg2givhwizoep.onion
- 20. how do addresses work? • all these addresses can be typed into a web browser: • http://192.168.1.1/- ipv4, supported everywhere • http://[fe80::226:21ff:fed8:fbc2]/ - ipv6, variable • http://www.foo.com/ - dns, supported everywhere • http://ylzpu2givhwizoep.onion/ - needs a Tor browser • …they all connect you to a remote computer
- 21. how is .onion unusual? • "under the bonnet", an onion is a raw network address • …just like 192.168.1.1 or fe80::226:21ff:fed8:fbc2 • but: formatted like a traditional dns domain name • ".onion" looks like ".com" or ".co.uk" • this means browsers treat the addresses equitably • including subdomains: www.facebookcorewwwi.onion
- 22. “subdomains” on a network address?!? • yes! this would never work with ipv4 … • www.192.168.1.1 would not mean anything sensible • but www.facebookcorewwwi.onion is meaningful to HTTP • …still means facebookcorewwwi.onion • …the "www." bit is transported in the Host: header • thus: standard HTTP/HTML/browser behaviour
- 23. how do you choose addresses? • ipv4 addresses: you take what you are given (eg: DHCP) • ipv6 addresses: ditto (mostly) • dns addresses: you choose a name, & register it • …unless someone beats you to it… • onion addresses: get a random one, or else "mine" one • more mining => "better quality"
- 24. howto: arbitrary traffic? HiddenServiceDir /var/lib/tor/onion-1 # => random onion address in "hostname" file HiddenServicePort 22 127.0.0.1:22 Server: /etc/tor/torrc Host my-onion HostName xxxxxxxxxxxxxxxx.onion ProxyCommand= nc -x localhost:9150 %h %p # 9150 => builtin SOCKS5 in local TorBrowser Client: ~/.ssh/config software-defined listening port number
- 25. howto: password-protect onion network interfaces? Server: /etc/tor/torrc …yields: the following hostname file
- 26. how to serve .onion websites? 3 options…
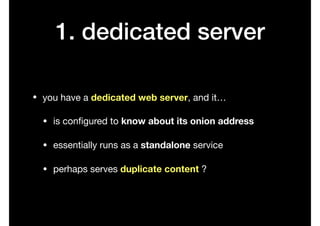
- 27. 1. dedicated server • you have a dedicated web server, and it… • is configured to know about its onion address • essentially runs as a standalone service • perhaps serves duplicate content ?
- 28. 2. onion-aware CMS • you have a web server, and it… • serves content to .com, .co.uk, .in, … • why not just add yet another domain name? • tag requests arriving from .onion reverse proxy • ensure that tagged requests are consistently responded-to, citing only your onion address(es)
- 29. 3. onion shim • you have a web server, and it… • primarily serves content as (say) nytimes.com • install a shim between it and the tor reverse proxy… • shim bidirectionally rewrites requests & responses • nytimes.com <=> nytimes3xbfgragh.onion • custom engineering, or EOTK / Enterprise Onion Toolkit open-source shim for enterprise onions
- 30. examples (or: implement a blend…) 1. dedicated onion server (eg: various SecureDrop sites) • use-case dependent, probably involves anonymity 2. onion-aware CMS (eg: Facebook) • excellent for primarily-dynamically-generated content • modest engineering, ongoing commitment, can be 100% solution 3. onion shim EOTK (eg: NYT) • onionifies all content, including static or static/dynamic mix • minimal/zero engineering, some edge cases, 95..99%+ solution
- 31. implementation tips • don't forget to onionify your CDNs where possible • try to avoid content-leakage between domains • accidentally wandering-off to the cleartext/.com site • e.g. OAuth redirects, tracker embeds… • use horizontal load-balancing for scale • free solution: OnionBalance (EOTK supports) • onions (even via shim) are generally faster for Tor
- 32. nits • you will almost certainly need to buy a special HTTPS cert • cost: probably from mid $$$ to low $$$$ • plus: associated paperwork & faff • if you take payments / subscriptions? • you may want to restrict access to payments over tor? • payment providers often block tor, this can sometimes lead to poor user experiences…
- 33. TECH?
- 34. Onion Networking as a Layer-3 Network
- 35. How IP→Ethernet Works • Server: publishes mapping of IP to MAC address • Gratuitous ARP → populate ARP tables • Client: resolves mapping of IP to MAC address • Checks local ARP table (or makes ARP query) • Client: issues Ethernet frames to MAC address • Frames transport packets yielding TCP connections
- 36. How Onion→IP Works • Server: publishes mapping of Onion to IP address • Descriptor Publication → populate HSDir DHT Ring • Client: resolves mapping of Onion to IP address • Checks HSDir DHT Ring (source of truth) • Client: issues TCP connection to Tor relay • Connections transport Tor cells yielding Tor circuits
- 38. 1) TCP/IP is the L2 "data-link layer" of Onionspace
- 39. # OSI Name Internet Onion 7 Application https, ssh, etc… https, ssh, etc… 6 Presentation socket* socks5 proxy 5 Session tcp/udp socket* tcp socket via socks5 4 Transport tcp/udp protocol tcp circuit 3 Network packet to IP addr cell to Onion addr 2 Data Link frames/MAC/LLC cells over tcp 1 Physical bit bit
- 40. 2) Onionspace is flat
- 41. Onion-flattyness • NAT/Firewalls are not an issue • Connections pretend to be direct, local-network TCP. • Services & Ports are published, not ad-hoc/promiscuous • Onionspace port-scanning is restricted to services and ports which are published by the owners: • HiddenServicePort 44422 localhost:22 • "consent-based networking", cf: NSAPs in X.25 ?
- 42. (2018 - 1994) + 13 = 37
- 43. Returning to the disintermediated end-to-end Internet
- 45. Circuit-switchyness • Long-term circuits between client/server are established • Traffic tunnels over circuits • A bit like X.25 Networking • sometimes circuits break • but then, so does TCP (i.e.: RST) • Circuits may carry multiple TCP/IP streams, be reused • Presentation: as a SOCKS5 relay
- 47. 1 server sets up introduction point 2 server publishes descriptor 3 client looks-up descriptor / intro-point 4a client sets up rendez-point 4b client tells server "meet me at rendez-point" 5 data exchanged via circuit via rendez "Rendezvous", a safer "Client-Server" Server HSDir DHT Ring Client Introduction Point Tor "Cloud" 2 1 4b 3 4a5 Rendezvous Point nb: all connections established "outbound" through the firewall(s); server can live in "enclave" firewallfirewall
- 48. "Rendezvous" at L7? • All this is hidden behind SOCKS5 for app presentation • Your app thinks that it is talking to a TCP/IP stream • Truth = more complex
- 49. 5) Introduction points have redundancy, transience and migrate globally, leading to…
- 50. high-availabilityness (H/A) • DDoS Resistance • Harder to hit a moving target, key resources "at 1+ remove" • Built-in "GSLB" (global server load balancing) • You have little control of where Introduction, or Rendezvous Points are created, but they are distributed globally • Servers can be replicated globally, too; flatness = simpler • "DNSRR" equivalent (DNS Round Robin) • "OnionBalance" enables recombination of descriptors, shares load over servers like DSR (direct server return); or full H/A replicas
- 52. self-authenticatingness • Onion addresses are literally cryptographically-trustable layer-3 network addresses • If you type the address correctly, you are guaranteed to be communicating with someone who has the private key • Built-in IPsec ESP and AH • No PSK hassle • No CA hassle • No revocation, no X.509, no OpenSSL, no faff…
- 53. 7) …and finally…
- 54. BGP-Hijack Resistance • Tor is an over-the-top meta-network • It doesn't much care what's happening at the IP layer
- 55. If you remember one thing: • Tor "treats censorship as damage, and routes around it" • literally its raison d'être… • …with all these hostile actors it's actually pretty good at (eventually) routing around damage of any kind. • Wasn't the Internet supposed to do this anyway? • Maybe we just got too used to reliable networks?
- 56. The Downsides?
- 57. Downside 1: latency, lag, circuit drops
- 58. "good enough for the right kinds of workload"
- 59. Four Major Types Of Established Tor Connection Rendezvous Rendezvous TorBrowser MiddleGuard WebsiteExit Rendezvous TorBrowser MiddleGuard Middle1 Guard Onion OnionMiddle1 GuardBrowser Tor2web TorBrowser MiddleGuard Onion Browsing Normal Web Over Tor Browsing Onion Site Over Tor Browsing Onion Site From Normal Client Using Tor2web (bad idea) Browsing Single-Hop Onion Site (Facebook, NYT, …) single hop single hophttp Protected only by HTTPS, if that... Middle2 Middle2 Chosen by Client Chosen by Server nb:TorBrowser is simply a normal browser with embedded Tor software nb: Onion site is simply a normal website with bonded Tor software
- 60. Tor as Web CDN: Normal vs Onion TorBrowser MiddleGuard WebsiteExit RendezvousTorBrowser MiddleGuard Onion CDN Normal Web Over Tor CDN Single-Hop Onion Site Chosen by Client Chosen by Server Website X: exit node to webserver Y: onion to rendezvous Z: link to webserver → congestion shim / revproxyfast Generally: (Y+Z) < X (less is better)
- 61. Downside 2: Learning New Stuff
- 62. Learning New Stuff • Tor is not TCP/IP (but feels similar) • Tor is not an in-kernel network • userspace daemons • config files, not ifconfig • Tor is evolving • Just like TCP/IP was in 1992
- 66. eotk config file
- 72. <code/>
- 74. fixed (enough)
- 75. Wikipedia Experiment • Why? • Short-term test to prove the concept • Cheap, low resource-usage, borrowed hardware • Was DoS'd by <some asshole with bots> • Sustained few-hundreds of hits per second • Hardly noticeable impact on single quad-core server
- 77. tip: long video, questions welcome…
- 78. onion Tor vs: plain Tor
- 79. for deck PDF, twitter search: from:alecmuffett "nluug slides" ...will be posted later today



