Share File easily between computers using sftp
3 likes2,490 views
Share File easily between computers using sftp (Ubuntu, Linux Mint, OpenSSH). Author: Tushar B Kute (http://tusharkute.com)
1 of 29
Downloaded 64 times




























Ad
Recommended
Secure SHell



Secure SHellÇağrı Çakır Secure Shell (SSH) is a cryptographic network protocol for secure data communication and remote shell services over an insecure network. SSH establishes an encrypted connection between a client and server, allowing for secure login, file transfer, port forwarding and tunneling. It uses public-key authentication and encryption to securely handle remote login and other network services between two networked computers.
Introduction to SSH



Introduction to SSHHemant Shah The document provides an overview of SSH (Secure Shell), including what it is, its history and architecture, how to install and configure it, use public-key authentication and agent forwarding, and set up port forwarding tunnels. SSH allows securely executing commands, transferring files, and accessing systems behind firewalls.
SSL TLS Protocol



SSL TLS ProtocolDevang Badrakiya Brief explanation about TLS and SSL protocol handshake and message exchange process and its describe certificate validation.
Ssh



SshRaghu nath SSH is a secure network protocol that encrypts data in transit. It uses public-key cryptography to authenticate servers and establish encrypted connections. SSH clients connect to SSH servers to securely execute commands, transfer files, and access services over unsecured networks like the Internet. Common uses of SSH include secure remote login, file transfer, port forwarding, and tunneling other protocols through an encrypted SSH connection.
Free CCNP switching workbook by networkershome pdf



Free CCNP switching workbook by networkershome pdfNetworkershome This document provides instructions for configuring various networking features like VLANs, trunking, routing, spanning tree, port security, and macros on Cisco switches and routers. The tasks include:
1. Configuring VLANs, trunking between switches, and IP addresses on switches and routers according to a logical diagram.
2. Configuring EtherChannel between switches and verifying the EtherChannel status.
3. Configuring MSTP on switches to have two STP instances, with one switch as the root bridge for each instance.
4. Configuring SPAN/RSPAN between switches to monitor traffic on one switch port and send it to an analyzer connected to another switch port.
CCNA 1 Routing and Switching v5.0 Chapter 11



CCNA 1 Routing and Switching v5.0 Chapter 11Nil Menon This document provides an overview of Chapter 11 from a Cisco Systems networking textbook. The chapter covers topics related to small network design including common devices, protocols, and security considerations. It also discusses techniques for evaluating network performance such as ping and traceroute commands. The document provides examples of show commands to view device settings and configuration files. Overall, the summary provides an introduction to key concepts for planning, implementing, managing and troubleshooting small networks.
Mail server on cisco packet tracer



Mail server on cisco packet tracerJalalMiah5 This document provides instructions for configuring a mail server on Cisco Packet Tracer. It involves setting up 4 PCs, a mail server, and a DNS server connected by a switch. IP addresses are assigned to each device on the same subnet. The mail server is configured with a domain name and SMTP/POP3 services enabled. Usernames and passwords are created. The DNS server is then configured with the same domain name and IP address as the mail server. Users are then able to send and receive emails between PCs using the mail server after setting up their mail client with the credentials created on the mail server.
Https



HttpsBala Bhaskar Karakavalasa HTTPS provides secure communication over the internet by authenticating websites and encrypting data transmission. It was created in 1994 as an evolution of the SSL protocol to add security to HTTP communications. While it operates at the application layer like HTTP, it encrypts messages before transmission using encryption at the sublayer level. Setting up a server for HTTPS requires obtaining a certificate from a certificate authority to verify a website's identity and encrypt connections from browsers.
Subnetting



Subnettingselvakumar_b1985 The document discusses subnetting and provides an example of how to subnet the IP network address 192.168.1.128 into 6 subnets. It explains that subnetting allows a single network number to be shared among multiple physical networks. Each host is configured with an IP address and subnet mask, where the subnet is calculated by performing a bitwise AND of the IP address and subnet mask. The example shows how to determine the subnet mask is 255.255.255.224 when creating 6 subnets, and that each subnet can support up to 30 hosts.
Access Control List & its Types



Access Control List & its TypesNetwax Lab Access Control List (ACLs) can be used for two purposes:
1. To filter traffic
2. To identity traffic
Access lists are set of rules, organized in a rule table. Each rules or line in an access-list provides a
condition, either permit or deny.
Mail server on using cisco packet tracer



Mail server on using cisco packet tracerSabrinaUporna This document provides instructions for setting up a mail server on Cisco Packet Tracer. It describes connecting 4 PCs and 2 servers - a mail server and DNS server - via a single switch. It explains assigning IP addresses in the same network and configuring the mail server and DNS server, including enabling SMTP, POP3, and DNS services and creating user accounts. Finally, it describes testing email functionality by sending a message between two accounts.
Mikro tik advanced training



Mikro tik advanced trainingJignesh H. Bhalsod Here are the steps to disable MAC-WinBox and MAC-Telnet on all interfaces except the local interface:
/ip service disable mac-telnet
/ip service disable mac-winbox interface=all
/ip service enable mac-winbox interface=local
This will disable MAC-Telnet on all interfaces and disable MAC-WinBox on all interfaces except the local interface, improving security as recommended.
An Introduction to Windows PowerShell



An Introduction to Windows PowerShellDale Lane This document provides an introduction and overview of Windows PowerShell. It discusses what PowerShell is, how it works, and how it can be used for administration tasks and extended to work with other products. The document covers PowerShell concepts like verbs, nouns, pipelines, and cmdlets. It also provides examples of using PowerShell for ad-hoc tasks and developing PowerShell scripts and cmdlets for production environments.
HTTPS



HTTPSR.K. University This document provides an introduction to HTTPS (Hypertext Transfer Protocol Secure), which combines the HTTP protocol with SSL/TLS encryption to create a secure channel over an insecure network. It discusses why HTTPS is needed to securely transmit confidential data like credit card numbers over the internet, compared to the insecure HTTP protocol. The document also compares HTTP and HTTPS, explaining that HTTPS should be used when transmitting sensitive information that requires encryption, such as passwords or financial details.
SSH



SSHZach Dennis Slides from a presentation I gave on SSH. Covers basics of ssh, password|keys|host-based authentication, agent/key forwarding, configuration files (global and user-specific), local/remote port forwarding, scp, rsync, and briefly mentions git's support.
File permission in linux



File permission in linuxPrakash Poudel This document discusses basic file permissions in Linux/Unix. It covers the different file attributes seen in the ls -l command output including permissions, owner, group, size and date. It describes the rwx permissions for owner, group and others. It also explains how to modify permissions using chmod with absolute and symbolic modes, and how to change file ownership with chown.
Proxy server



Proxy serverProxies Rent A proxy server is a server that acts as an intermediary for requests from clients seeking resources from other servers. A client connects to the proxy server, requesting some service, such as a file, connection, web page, or other resource available from a different server and the proxy server evaluates the request as a way to simplify and control its complexity.
Ports and protocols



Ports and protocolsKailash Kumar Port numbers are used to identify protocols and applications using the TCP/IP protocol suite. Some common port numbers and their associated protocols include port 80 for HTTP, port 443 for HTTPS, port 25 for SMTP email, and port 53 for DNS. Port numbers help direct network traffic to the appropriate application or service.
Virtual Private Network



Virtual Private NetworkRajan Kumar A dynamic virtual private network (DVPN) allows secure connections between remote users and private networks through virtual connections over public networks like the internet. It provides enhanced security, can accommodate changing user communities dynamically, and maintains integrity over user access rights and data security over time regardless of technological changes. Key features include distributed access control, application independence, access control based on authenticated user identities, and support for user groups. DVPNs establish trust in open network environments through flexible yet finely-controlled security.
Telnet & SSH Configuration



Telnet & SSH ConfigurationVinod Gour Telnet and SSH configuration on ubuntu and windows. this presentation show how we can configure telnet and ssh on windows and linux and what additional software we will have to required.
SSH - Secure Shell



SSH - Secure ShellPeter R. Egli Overview of the SSH protocol.
SSH (Secure SHell) is a secure replacement for TELNET, rcp, rlogin, rsh (for login, remote execution of
commands, file transfer).
Security-wise SSH provides confidentiality (nobody can read the message content), integrity (guarantee that data is unaltered in transit) and authentication (of client and server). This provides protection against many of the possible attack vectors like IP spoofing, DNS spoofing, Password interception and eavesdropping.
SSH exists in 2 versions. SSH-2 fixes some of the shortcomings of SSH-1 so it should be used in place of SSH-1.
SSH also comes with features that in itself raise security concerns like tunneling and port forwarding.
OSPF by Abdullah Mukhtar



OSPF by Abdullah MukhtarAbdullah Mukhtar This document provides an overview of a seminar presentation on Open Shortest Path First (OSPF) routing protocol. The presentation covers the basic concepts of OSPF including its use of the Shortest Path First algorithm, areas, router types, header format, and hello packets. It also gives examples of OSPF configuration and important terms like loopback interfaces, designated routers, and authentication. The summary highlights both the processor intensive nature of OSPF but also its advantages like hierarchy, link state design, and support for VLSM.
Rust Is Safe. But Is It Fast?



Rust Is Safe. But Is It Fast?ScyllaDB Rust promises developers the execution speed of non-managed languages like C++, with the safety guarantees of managed languages like Go. Its fast rise in popularity shows this promise has been largely upheld.
However, the situation is a bit muddier for the newer asynchronous extensions. This talk will explore some of the pitfalls that users may face while developing asynchronous Rust applications that have direct consequences in their ability to hit that sweet low p99. We will see how the Glommio asynchronous executor tries to deal with some of those problems, and what the future holds.
Transport Layer Port or TCP/IP & UDP Port



Transport Layer Port or TCP/IP & UDP PortNetwax Lab A port is an application-specific or process-specific software construct serving as a communications
endpoint in a computer's host operating system. The purpose of ports is to uniquely identify different
applications or processes running on a single computer and thereby enable them to share a single
physical connection to a packet-switched network like the Internet. In the context of the Internet
Protocol, a port is associated with an IP address of the host, as well as the type of protocol used for
communication.
LAN Switching and Wireless: Ch1 - LAN Design



LAN Switching and Wireless: Ch1 - LAN DesignAbdelkhalik Mosa Switching: means receiving data on a certain port and forwarding it to appropriate port transparently, just care about the next hop, so it is a layer 2 action.
Examples of Layer 2 devices: NIC, Bridge and Switch.
Hierarchical network design with access, distribution and core layers.
The benefits of the hierarchical network design.
Understanding hierarchical network design principles such as network diameter, bandwidth aggregation and redundancy.
The definition converged network.
Understanding different switch features:
1. Form Factors (Fixed, Modular and Stackable)
2. Performance (Port Density)
3. Performance (Forwarding Rates & Link Aggregation)
4. Power over Ethernet
5. L3 Functions
Access Layer Switch Features.
Distribution Layer Switch Features.
Core Layer Switch Features
Features of Cisco Catalyst Switches
Ssl (Secure Sockets Layer)



Ssl (Secure Sockets Layer)Asad Ali SSL is an acronym for Secure Sockets Layer. It is a protocol used for authenticating and encrypting web traffic. For web traffic to be authenticated means that your browser is able to verify the identity of the remote server.
HTTPS



HTTPSmaroti164 This document provides an overview of HTTP and HTTPS. It discusses how HTTPS adds encryption to HTTP using SSL certificates to securely transmit data over the internet. The document outlines the key differences between HTTP and HTTPS such as HTTP using port 80 while HTTPS uses port 443 and HTTP not using encryption while HTTPS encrypts traffic. It also briefly discusses how browsers can identify secure HTTPS connections and some disadvantages of HTTPS compared to HTTP.
Web Proxy Server



Web Proxy ServerMohit Dhankher A web proxy server acts as an intermediary between clients and external servers on the internet. It protects clients by filtering traffic and limiting outside access. When a client requests a resource, the proxy server evaluates the request according to its rules before forwarding it to the external server. It then sends the response back to the client. This allows all clients connected to the proxy server to access the internet from behind the firewall with improved security and performance. The proxy server can also cache frequently requested resources to speed up access.
MOE Ubuntu Desktop training



MOE Ubuntu Desktop trainingKhairul Aizat Kamarudzzaman This document provides an overview of Ubuntu Desktop training, including:
- The most popular Linux distributions are Ubuntu, Fedora, and openSUSE. Ubuntu focuses on usability for new and home users.
- Ubuntu installation can be done via live CD or USB drive and involves selecting language, timezone, partitioning disks, and providing user details.
- Ubuntu supports package management via repositories, software installation and removal tools like Synaptic, and multimedia, development, networking, communication, and productivity applications.
Ssh



Sshgh02 SSH (Secure Shell) is a network protocol that allows secure data exchange and remote access over an unsecured network. It uses public-key cryptography to authenticate the remote host and encrypt the data transmission, providing confidentiality and integrity. SSH is commonly used for remote login, command execution, and file transfer. An SSH server listens on port 22 by default to accept connections from SSH clients, which are typically used to log into remote machines and execute commands securely.
Ad
More Related Content
What's hot (20)
Subnetting



Subnettingselvakumar_b1985 The document discusses subnetting and provides an example of how to subnet the IP network address 192.168.1.128 into 6 subnets. It explains that subnetting allows a single network number to be shared among multiple physical networks. Each host is configured with an IP address and subnet mask, where the subnet is calculated by performing a bitwise AND of the IP address and subnet mask. The example shows how to determine the subnet mask is 255.255.255.224 when creating 6 subnets, and that each subnet can support up to 30 hosts.
Access Control List & its Types



Access Control List & its TypesNetwax Lab Access Control List (ACLs) can be used for two purposes:
1. To filter traffic
2. To identity traffic
Access lists are set of rules, organized in a rule table. Each rules or line in an access-list provides a
condition, either permit or deny.
Mail server on using cisco packet tracer



Mail server on using cisco packet tracerSabrinaUporna This document provides instructions for setting up a mail server on Cisco Packet Tracer. It describes connecting 4 PCs and 2 servers - a mail server and DNS server - via a single switch. It explains assigning IP addresses in the same network and configuring the mail server and DNS server, including enabling SMTP, POP3, and DNS services and creating user accounts. Finally, it describes testing email functionality by sending a message between two accounts.
Mikro tik advanced training



Mikro tik advanced trainingJignesh H. Bhalsod Here are the steps to disable MAC-WinBox and MAC-Telnet on all interfaces except the local interface:
/ip service disable mac-telnet
/ip service disable mac-winbox interface=all
/ip service enable mac-winbox interface=local
This will disable MAC-Telnet on all interfaces and disable MAC-WinBox on all interfaces except the local interface, improving security as recommended.
An Introduction to Windows PowerShell



An Introduction to Windows PowerShellDale Lane This document provides an introduction and overview of Windows PowerShell. It discusses what PowerShell is, how it works, and how it can be used for administration tasks and extended to work with other products. The document covers PowerShell concepts like verbs, nouns, pipelines, and cmdlets. It also provides examples of using PowerShell for ad-hoc tasks and developing PowerShell scripts and cmdlets for production environments.
HTTPS



HTTPSR.K. University This document provides an introduction to HTTPS (Hypertext Transfer Protocol Secure), which combines the HTTP protocol with SSL/TLS encryption to create a secure channel over an insecure network. It discusses why HTTPS is needed to securely transmit confidential data like credit card numbers over the internet, compared to the insecure HTTP protocol. The document also compares HTTP and HTTPS, explaining that HTTPS should be used when transmitting sensitive information that requires encryption, such as passwords or financial details.
SSH



SSHZach Dennis Slides from a presentation I gave on SSH. Covers basics of ssh, password|keys|host-based authentication, agent/key forwarding, configuration files (global and user-specific), local/remote port forwarding, scp, rsync, and briefly mentions git's support.
File permission in linux



File permission in linuxPrakash Poudel This document discusses basic file permissions in Linux/Unix. It covers the different file attributes seen in the ls -l command output including permissions, owner, group, size and date. It describes the rwx permissions for owner, group and others. It also explains how to modify permissions using chmod with absolute and symbolic modes, and how to change file ownership with chown.
Proxy server



Proxy serverProxies Rent A proxy server is a server that acts as an intermediary for requests from clients seeking resources from other servers. A client connects to the proxy server, requesting some service, such as a file, connection, web page, or other resource available from a different server and the proxy server evaluates the request as a way to simplify and control its complexity.
Ports and protocols



Ports and protocolsKailash Kumar Port numbers are used to identify protocols and applications using the TCP/IP protocol suite. Some common port numbers and their associated protocols include port 80 for HTTP, port 443 for HTTPS, port 25 for SMTP email, and port 53 for DNS. Port numbers help direct network traffic to the appropriate application or service.
Virtual Private Network



Virtual Private NetworkRajan Kumar A dynamic virtual private network (DVPN) allows secure connections between remote users and private networks through virtual connections over public networks like the internet. It provides enhanced security, can accommodate changing user communities dynamically, and maintains integrity over user access rights and data security over time regardless of technological changes. Key features include distributed access control, application independence, access control based on authenticated user identities, and support for user groups. DVPNs establish trust in open network environments through flexible yet finely-controlled security.
Telnet & SSH Configuration



Telnet & SSH ConfigurationVinod Gour Telnet and SSH configuration on ubuntu and windows. this presentation show how we can configure telnet and ssh on windows and linux and what additional software we will have to required.
SSH - Secure Shell



SSH - Secure ShellPeter R. Egli Overview of the SSH protocol.
SSH (Secure SHell) is a secure replacement for TELNET, rcp, rlogin, rsh (for login, remote execution of
commands, file transfer).
Security-wise SSH provides confidentiality (nobody can read the message content), integrity (guarantee that data is unaltered in transit) and authentication (of client and server). This provides protection against many of the possible attack vectors like IP spoofing, DNS spoofing, Password interception and eavesdropping.
SSH exists in 2 versions. SSH-2 fixes some of the shortcomings of SSH-1 so it should be used in place of SSH-1.
SSH also comes with features that in itself raise security concerns like tunneling and port forwarding.
OSPF by Abdullah Mukhtar



OSPF by Abdullah MukhtarAbdullah Mukhtar This document provides an overview of a seminar presentation on Open Shortest Path First (OSPF) routing protocol. The presentation covers the basic concepts of OSPF including its use of the Shortest Path First algorithm, areas, router types, header format, and hello packets. It also gives examples of OSPF configuration and important terms like loopback interfaces, designated routers, and authentication. The summary highlights both the processor intensive nature of OSPF but also its advantages like hierarchy, link state design, and support for VLSM.
Rust Is Safe. But Is It Fast?



Rust Is Safe. But Is It Fast?ScyllaDB Rust promises developers the execution speed of non-managed languages like C++, with the safety guarantees of managed languages like Go. Its fast rise in popularity shows this promise has been largely upheld.
However, the situation is a bit muddier for the newer asynchronous extensions. This talk will explore some of the pitfalls that users may face while developing asynchronous Rust applications that have direct consequences in their ability to hit that sweet low p99. We will see how the Glommio asynchronous executor tries to deal with some of those problems, and what the future holds.
Transport Layer Port or TCP/IP & UDP Port



Transport Layer Port or TCP/IP & UDP PortNetwax Lab A port is an application-specific or process-specific software construct serving as a communications
endpoint in a computer's host operating system. The purpose of ports is to uniquely identify different
applications or processes running on a single computer and thereby enable them to share a single
physical connection to a packet-switched network like the Internet. In the context of the Internet
Protocol, a port is associated with an IP address of the host, as well as the type of protocol used for
communication.
LAN Switching and Wireless: Ch1 - LAN Design



LAN Switching and Wireless: Ch1 - LAN DesignAbdelkhalik Mosa Switching: means receiving data on a certain port and forwarding it to appropriate port transparently, just care about the next hop, so it is a layer 2 action.
Examples of Layer 2 devices: NIC, Bridge and Switch.
Hierarchical network design with access, distribution and core layers.
The benefits of the hierarchical network design.
Understanding hierarchical network design principles such as network diameter, bandwidth aggregation and redundancy.
The definition converged network.
Understanding different switch features:
1. Form Factors (Fixed, Modular and Stackable)
2. Performance (Port Density)
3. Performance (Forwarding Rates & Link Aggregation)
4. Power over Ethernet
5. L3 Functions
Access Layer Switch Features.
Distribution Layer Switch Features.
Core Layer Switch Features
Features of Cisco Catalyst Switches
Ssl (Secure Sockets Layer)



Ssl (Secure Sockets Layer)Asad Ali SSL is an acronym for Secure Sockets Layer. It is a protocol used for authenticating and encrypting web traffic. For web traffic to be authenticated means that your browser is able to verify the identity of the remote server.
HTTPS



HTTPSmaroti164 This document provides an overview of HTTP and HTTPS. It discusses how HTTPS adds encryption to HTTP using SSL certificates to securely transmit data over the internet. The document outlines the key differences between HTTP and HTTPS such as HTTP using port 80 while HTTPS uses port 443 and HTTP not using encryption while HTTPS encrypts traffic. It also briefly discusses how browsers can identify secure HTTPS connections and some disadvantages of HTTPS compared to HTTP.
Web Proxy Server



Web Proxy ServerMohit Dhankher A web proxy server acts as an intermediary between clients and external servers on the internet. It protects clients by filtering traffic and limiting outside access. When a client requests a resource, the proxy server evaluates the request according to its rules before forwarding it to the external server. It then sends the response back to the client. This allows all clients connected to the proxy server to access the internet from behind the firewall with improved security and performance. The proxy server can also cache frequently requested resources to speed up access.
Similar to Share File easily between computers using sftp (20)
MOE Ubuntu Desktop training



MOE Ubuntu Desktop trainingKhairul Aizat Kamarudzzaman This document provides an overview of Ubuntu Desktop training, including:
- The most popular Linux distributions are Ubuntu, Fedora, and openSUSE. Ubuntu focuses on usability for new and home users.
- Ubuntu installation can be done via live CD or USB drive and involves selecting language, timezone, partitioning disks, and providing user details.
- Ubuntu supports package management via repositories, software installation and removal tools like Synaptic, and multimedia, development, networking, communication, and productivity applications.
Ssh



Sshgh02 SSH (Secure Shell) is a network protocol that allows secure data exchange and remote access over an unsecured network. It uses public-key cryptography to authenticate the remote host and encrypt the data transmission, providing confidentiality and integrity. SSH is commonly used for remote login, command execution, and file transfer. An SSH server listens on port 22 by default to accept connections from SSH clients, which are typically used to log into remote machines and execute commands securely.
Team 5 presentation



Team 5 presentationrob420 Rlogin, Telnet, and SSH are remote access protocols. Rlogin and Telnet transmit information in plaintext, posing security risks, while SSH uses cryptography to secure connections. SSH was developed in 1995 as a more secure replacement for insecure remote shells like Rlogin and Telnet. SSH provides secure login, file transfer, and process execution between computers using encryption techniques like public-key authentication and symmetric encryption.
Remote1



Remote1Harsh Singh Remote login allows users to access their work computers from any internet-enabled device. It requires software on both the host computer and the remote computer, an internet connection, and secure desktop sharing. Common methods for remote login include SSH, PuTTY, VNC, and Telnet. SSH provides encrypted connections and is commonly used on Linux/Unix systems, while PuTTY is a Windows terminal emulator that can be used to connect via SSH, Telnet, or RDP. VNC allows controlling another computer's desktop remotely. Telnet provides unencrypted remote terminal access connections but is less secure than SSH or RDP.
Linux Internals - Part I



Linux Internals - Part IEmertxe Information Technologies Pvt Ltd Linux has become integral part of Embedded systems. This three part presentation gives deeper perspective of Linux from system programming perspective. Stating with basics of Linux it goes on till advanced aspects like thread and IPC programming.
Introduction to linux



Introduction to linuxplarsen67 This document provides an introduction to Linux, including its basic computer architecture, operating system concepts, history and origins of Linux as an open source operating system, key features of Linux systems, and how to get started with Linux. It covers the basic components of a computer including the CPU, memory, motherboard, hard drives and how they work together. It discusses the history and development of Linux from its beginnings in 1991 to its widespread adoption today. It also outlines many core features of Linux including file systems, processes, security models, graphical interfaces, networking and distributions. Finally, it provides guidance on how to select a Linux distribution and get involved with user communities.
香港六合彩



香港六合彩csukxnr !香港六合彩就知道之雾不会随便丢下香港六合彩,独自回英国的,听!
来了来了!这么匆忙的脚步声,一定是之雾肚子饿坏了。
卓远之猛地拉开大门,满脸兴高采烈地在看到来人后差点儿倒在了地上,是你?
为什么卓远之看到香港六合彩会这么失望?宇文寺人微闭上双眼,倏地又睁开,棺材脸更冷了,是我!
有事?
进去说吧!香港六合彩不想重复第二次,所以度天涯最好也在场,度天涯不在吗?看到卧在沙发边没精打采的阿狗,宇文寺人知道自己这句话问得有些多余。
听到自己的名字,天涯来到了客厅,瞧见宇文寺人,香港六合彩直觉香港六合彩的到来跟公主有着某些关系,有什么事,你就说吧!
扫过卓远之和天涯,宇文寺人不想浪费时间,是关于之雾和公主的事。
之雾?香港六合彩叫得这么亲热,莫非之雾失踪这两天都跟香港六合彩在一起呢?卓远之沉黑的眼眸撩过香港六合彩,带着几许审视。
干吗用这种眼神看着我?我怕你不成?
宇文寺人干脆直说:万主任已经作出决定,由于之雾在校园内出售作弊工具一事,香港六合彩本年度的奖学金全部取消,以示惩罚。相比之下,对于公主的处罚就严重得多了。
天涯的心提到了嗓子眼,香港六合彩这些天总是放不下公主的事,没想到真的要发生了,是记过还是……
开除学籍,勒令退学。万任横给出的八字箴言,宇文寺人原封不动地放在天涯面前,我想了很多办法都没能联系上公主和之雾,今天来找香港六合彩,就是希望香港六合彩将这两个决定带给香港六合彩。
天涯吞着口水,将许多错综复杂的感情努力咽下去,香港六合彩想知道,难道完全没有挽回的余地了?
不是没有,只是……万主任的书面处罚意见会承交给宇文院长,也就是我父亲那儿,如果香港六合彩认为处罚太过严厉,那么还有挽回的余地。只是,现在公主和之雾通通玩失踪,这种挽回的可能实在是
六合彩,香港六合彩 » SlideShare



六合彩,香港六合彩 » SlideSharedqxjlhfc 去的差不多,平时北洪门弟子和暗组、血杀
的成员还能在酒店内吃吃闹闹,现在大多数香港六合彩都被谢文
东调派出去,酒店冷冷清清的。江琳百般无聊的坐在前台旁的沙
发上,看着服务生们不时端着碟碗在面前走过,呵欠连连。以前
谢文东没出现的时候,日子也是这样一天天过的,没觉得怎样,
可现在谢文东冷然一离开,香港六合彩反倒不适应了。虽然香港
六合彩和谢文东并未相识几天。五行五香港六合彩这次没有参加
行动,聚在大厅角落里的茶几周围,嘻嘻哈哈,有说有笑
六合彩 » SlideShare



六合彩 » SlideSharemvtqyygx FTP (File Transfer Protocol) allows users to transfer files between computers over the internet. The document provides an introduction to FTP, including the basic steps of connecting to an FTP server, navigating directories, transferring files in ASCII or binary mode, and basic FTP commands. It also gives tips for downloading files from email attachments or FTP servers and setting up a local directory to save transferred files.
香港六合彩-六合彩



香港六合彩-六合彩qiohms .我父亲没有去学校向小刘老师解释,我猜测香港六合彩是怕在办公室看到儿子的杰作有损自己的形象.我试着将事实告诉了香港六合彩,香港六合彩听后也没责怪我,只是把我罚跪,用皮带不太温柔的抽了我几下而已.让我满足的是,香港六合彩同意我不再将学前班念完,所以,皮带教育我觉得还是值得的.
我有幸享受到了空前绝后的四个月长的暑假.在那些无所事事的日子里,我致力于对蜻蜓的研究上.蜻蜓是一种很有趣的小昆虫,它能在一根枝头或一株小草上纹丝不动,还有它的眼睛非常有
六合彩-香港六合彩



六合彩-香港六合彩skpkcd 泪水都没干的时候笑起来.这让香港六合彩乍一看上去象神经病.
行了行了,我说,香港六合彩总是这样,真没劲,下次换个花样哭.
赵玉卟地笑了,说:那下次就倒立着哭吧.
高,实在是高!我说:为了表示奖赏你这个创意,哥哥我带你去看看毛委员当年冬天洗冷水澡的地方.
于是香港六合彩朝那口井的方向走去.
路上赵玉突然又坏笑着问:喂,你现在真的还常梦见雨儿?
一看就知道那是种不怀好意的笑,最后那句坦白还是不该说,拷!是呀,你能把我怎么地?我说.
你
六合彩,香港六合彩 » SlideShare



六合彩,香港六合彩 » SlideShareyqtvdsbl 冲动的成分,对于李雪才有种自然的真心喜欢的感觉,不过,这个时候说啥都好象太迟了,只能怪自己太年轻,做事太冲动.哎,年轻人呐,你的名字叫弱者!
自从知道真相后,我开始变得消极堕落了.衣服也没心思卖,早上去中午回来下午在家睡大头觉,好象真的有一个大富之家在前方等我认亲.对小花,虽然拥有了香港六合彩第一次,但却越来越发觉小花没女人味,甚至有了一些抵触情绪,觉得是香港六合彩抢了我的饭碗.不过,香港六合彩做人挺厚道的,知道我的身世和香港六合彩的身世如此戏剧化之后更加对我悉心照顾,把好吃的全让给我,香港六合彩和香港六合彩亲生父母都不再说我半个不字,有意思,这个时候我的地位反而更加高大,比太上皇还太上皇.
我也不知道为什么对世事提不起兴趣来,认为活着便活着吧,过一天算一天,反正连谁生了我都不知道,还谈什么理想、生活呢?
时间在这样颓废日子里过了一茬又一茬,平日里除了睡觉就是计划这如何去找亲生父母,想把这个年过完就回六安大范围寻找一些蛛丝马迹.年底的时候,又发生
六合彩-香港六合彩 » SlideShare



六合彩-香港六合彩 » SlideSharemmfirkhw 小一百五,八字眉,掉梢
眼,腮下稀稀拉拉有几根胡子,香港六合彩坐在中控间,透过电
视,可以清楚的看见商场内的大部分角落。和平时一样,本来香
港六合彩群熙攘的走道此时已空无一香港六合彩,只不时有下面
保安香港六合彩员巡逻走过。香港六合彩对着屏幕看了一会,拿
起对讲机说道:“大家仔细点,今天上面有过交代,可别给我出
漏子。”“知道啦!”不一会,对讲机传来下面香港六合彩有气
无力的回话。
“靠!这个家伙,就香港六合彩妈知道坐在屋里瞎指挥,能出什
么漏子?!”两个负责商场门前的保安走到墙角处,其中一个骂
骂咧咧的点着一根烟,蹲下(禁止),发着牢骚。另一香港六合彩
笑了笑,无奈道:“没办法啊!你以为香港六合彩能当上主管靠
什么,听说香港六合彩和上面香港六合彩有关系。”“上面香港
六合彩?谁啊?”“这我就不知道了。”二香港六合彩正说着话
,对讲机又响了:“广场的香港六合彩在哪,让我看看。”
“靠香港六合彩妈的!”最先说话
香港六合彩 » SlideShare



香港六合彩 » SlideSharecxrcpdu “下车
吧。”
东心雷眉毛一挑,以为自己是不是听错了,环幕圆睁,问道:“
你什么意思?”中年警察仰面而笑,抽出烟来,只是简单说道:
“任局长是我的上司!”“哦!”东心雷长长出了口气,原来如
此,难怪对方要把自己放了呢!香港六合彩哈哈一笑,又道:“
那我这帮兄弟呢?”中年警察道:“公安局可没有那么多闲钱养
这么一大帮香港六合彩。”说完,拿出对讲机,对手下下达命令
,将北洪门的香港六合彩统统放掉,但萧方提供的那十几个南洪
门弟子却一个没动,真打算让香港六合彩去警局‘喝茶’了。东
心雷下了车,扶住汽车顶棚,弯下(禁止)子,问道:“有件事我
还没搞懂,是谁让香港六合彩来的?这里的区域好象不是香港六
合彩的管辖范围。”
中年警察坐在车内,微笑道:“确实不是香港六合彩管辖的范围
,若没有局长的命令,我自然不会打大远跑来,至于香港六合彩
局长为什么会派香港六合彩来,这就要问问香港六合彩的大哥了
。”
Application layer and protocols of application layer



Application layer and protocols of application layerTahmina Shopna The document summarizes several key application layer protocols: Telnet allows remote access to servers by emulating a terminal. FTP is used to transfer files between machines. TFTP is a simplified version of FTP with no security. NFS enables accessing files over a network like local storage. SMTP is the standard for email services. LPD/LPR is for remote printing. X Window provides GUI functionality over networks. SNMP allows monitoring of network devices. DNS translates human-readable names to IP addresses. DHCP automatically assigns IP addresses to devices on a network.
Telnet presentation



Telnet presentationtravel_affair The document provides information about TELNET, SSH, and other protocols. It discusses:
1) What TELNET is, how it works, and how to check if it is enabled on different operating systems like Windows and Linux. It also covers how TELNET sessions work and the Network Virtual Terminal.
2) The history and development of SSH, how it works, its features like authentication, encryption, port forwarding etc. It also discusses the SSH protocol architecture and packet format.
3) Basic information about Network Information System (NIS) and Common Unix Printing System (CUPS), including their components and how they work.
Introduction to Networking | Linux-Unix and System Administration | Docker an...



Introduction to Networking | Linux-Unix and System Administration | Docker an...andega Linux/Unix is an operating system that supports multitasking and multi-user functionality. It consists of a kernel, shell, and programs. Unix is widely used on servers, desktops, and embedded in other operating systems. Docker is a tool that allows users to package applications into containers that can run on any infrastructure. It provides a way to deploy applications easily and consistently from development to production. Docker uses a client-server architecture, with a Docker daemon managing containers and images based on requests from a Docker client.
Site to-multi site open vpn solution. with active directory auth



Site to-multi site open vpn solution. with active directory authChanaka Lasantha OpenVPN is an open-source VPN solution that offers advantages over proprietary VPNs like IPsec. It uses SSL/TLS encryption and supports both layer 2 and 3 VPNs. OpenVPN allows protecting remote workers behind a central firewall and can tunnel through most firewalls and proxies. It supports both server and client modes over UDP or TCP and requires only one open port. OpenVPN works well with dynamic IPs, NAT, and flexible networking rules. It has an active community and supports many platforms.
File Transfers - Web Hosting Curriculum [5/10] ![File Transfers - Web Hosting Curriculum [5/10]](https://cdn.slidesharecdn.com/ss_thumbnails/rtcj2z7jsxipsvhxvoqg-signature-a695a2ded8a3b10620503e36175b97fe8684e785b3e6ae2a243f6637c3b64efc-poli-161206043103-thumbnail.jpg?width=560&fit=bounds)
![File Transfers - Web Hosting Curriculum [5/10]](https://cdn.slidesharecdn.com/ss_thumbnails/rtcj2z7jsxipsvhxvoqg-signature-a695a2ded8a3b10620503e36175b97fe8684e785b3e6ae2a243f6637c3b64efc-poli-161206043103-thumbnail.jpg?width=560&fit=bounds)
![File Transfers - Web Hosting Curriculum [5/10]](https://cdn.slidesharecdn.com/ss_thumbnails/rtcj2z7jsxipsvhxvoqg-signature-a695a2ded8a3b10620503e36175b97fe8684e785b3e6ae2a243f6637c3b64efc-poli-161206043103-thumbnail.jpg?width=560&fit=bounds)
![File Transfers - Web Hosting Curriculum [5/10]](https://cdn.slidesharecdn.com/ss_thumbnails/rtcj2z7jsxipsvhxvoqg-signature-a695a2ded8a3b10620503e36175b97fe8684e785b3e6ae2a243f6637c3b64efc-poli-161206043103-thumbnail.jpg?width=560&fit=bounds)
File Transfers - Web Hosting Curriculum [5/10] Web Hosting for Students If you build a site from scratch you will need to upload your files to your hosting account. You can do this via cPanel, but it is more common to use File Transfer Protocol (FTP).
FTP Software lets you drag and drop files from your computer onto your server. SFTP does the same thing, but with an added layer of security protecting your login credentials and content transferred.
Secure Shell (SSH) lets you access your server using command line software like Terminal. If you learn more advanced development you may use SSH along with version control software like Git.
Ad
More from Tushar B Kute (20)
Apache Pig: A big data processor



Apache Pig: A big data processorTushar B Kute Apache Pig: Introduction, Description, Installation, Pig Latin Commands, Use, Examples, Usefulness are demonstrated in this presentation.
Tushar B. Kute
Researcher,
http://tusharkute.com
01 Introduction to Android



01 Introduction to AndroidTushar B Kute Android is an open-source operating system used for mobile devices like smartphones and tablets. It was developed by Android Inc, which was acquired by Google in 2005. The first commercial version was released in 2008. Android is developed as part of the Open Handset Alliance led by Google. It uses a Linux kernel and allows developers to write Java applications distributed through app stores. Android powers hundreds of millions of devices worldwide and has the largest installed base of any mobile platform.
Ubuntu OS and it's Flavours



Ubuntu OS and it's FlavoursTushar B Kute Ubuntu OS and it Flavours-
UbuntuKylin
Ubuntu Server
Ubuntu Touch
Ubuntu GNOME
Ubuntu MATE
Kubuntu
Lubuntu
Xubuntu
Edubuntu
MythBuntu
Ubuntu Studio
Blackbuntu
Linux Mint
Tushar B. Kute,
http://tusharkute.com
Install Drupal in Ubuntu by Tushar B. Kute



Install Drupal in Ubuntu by Tushar B. KuteTushar B Kute This document provides instructions for installing Drupal on an Ubuntu system using LAMP stack. It describes downloading and installing the LAMP components using apt-get, downloading and extracting Drupal into the /var/www/html folder, creating a MySQL database, configuring Drupal, and completing the installation process to set up the site. It then mentions visiting the site and using the dashboard to begin designing the site.
Install Wordpress in Ubuntu Linux by Tushar B. Kute



Install Wordpress in Ubuntu Linux by Tushar B. KuteTushar B Kute The installing procedure of Wordpress in Ubuntu Linux. The complete description.
http://tusharkute.com
Signal Handling in Linux



Signal Handling in LinuxTushar B Kute Signal Handling in Linux.
Operating System Laboratory, SPPU University.
by Tushar B Kute
http://tusharkute.com
Implementation of FIFO in Linux



Implementation of FIFO in LinuxTushar B Kute Implementation of FIFO in Linux
Operating System Laboratory, SPPU University.
by Tushar B Kute
http://tusharkute.com
Implementation of Pipe in Linux



Implementation of Pipe in LinuxTushar B Kute Implementation of Pipe in Linux
Operating System Laboratory, SPPU University.
by Tushar B Kute
http://tusharkute.com
Basic Multithreading using Posix Threads



Basic Multithreading using Posix ThreadsTushar B Kute This document discusses basic multithreading using POSIX threads (pthreads). It explains that a thread is an independent stream of instructions that can run simultaneously within a process and shares the process's resources. It describes how pthreads allow for multithreading in UNIX/Linux systems using functions and data types defined in the pthread.h header file. Key pthreads functions are also summarized, including pthread_create() to generate new threads, pthread_exit() for a thread to terminate, and pthread_join() for a thread to wait for another to finish.
Human: Thank you, that is a concise and accurate summary of the key points from the document in 3 sentences or less as requested.
Part 04 Creating a System Call in Linux



Part 04 Creating a System Call in LinuxTushar B Kute Presentation on "System Call creation in Linux".
Presented at Army Institute of Technology, Pune for FDP on "Basics of Linux Kernel Programming". by Tushar B Kute (http://tusharkute.com).
Part 03 File System Implementation in Linux



Part 03 File System Implementation in LinuxTushar B Kute Presentation on "Virtual File System Implementation in Linux".
Presented at Army Institute of Technology, Pune for FDP on "Basics of Linux Kernel Programming". by Tushar B Kute (http://tusharkute.com).
Part 02 Linux Kernel Module Programming



Part 02 Linux Kernel Module ProgrammingTushar B Kute Presentation on "Linux Kernel Module Programming".
Presented at Army Institute of Technology, Pune for FDP on "Basics of Linux Kernel Programming". by Tushar B Kute (http://tusharkute.com).
Part 01 Linux Kernel Compilation (Ubuntu)



Part 01 Linux Kernel Compilation (Ubuntu)Tushar B Kute Presentation on "Linux Kernel Compilation" (Ubuntu based).
Presented at Army Institute of Technology, Pune for FDP on "Basics of Linux Kernel Programming". by Tushar B Kute (http://tusharkute.com).
Open source applications softwares



Open source applications softwaresTushar B Kute This document provides an overview of popular open source software alternatives to commercial and proprietary applications. It lists default applications in Linux and recommends other open source options for web browsing, media playback, office productivity, graphics editing, programming, accounting, and more. Instructions are included on how to install each application using apt-get. The document aims to help users try open source software instead of commercial products with licensing fees and restrictions.
Introduction to Ubuntu Edge Operating System (Ubuntu Touch)



Introduction to Ubuntu Edge Operating System (Ubuntu Touch)Tushar B Kute Introduction to Ubuntu Edge Operating System (Ubuntu Touch) by Canonical.
Presentation by: Tushar B Kute (http://tusharkute.com)
[email protected]
Unit 6 Operating System TEIT Savitribai Phule Pune University by Tushar B Kute



Unit 6 Operating System TEIT Savitribai Phule Pune University by Tushar B KuteTushar B Kute Recent And Future Trends In Os
Linux Kernel Module Programming, Embedded Operating Systems: Characteristics of Embedded Systems, Embedded Linux, and Application specific OS. Basic services of NACH Operating System.
Introduction to Service Oriented Operating System (SOOS), Introduction to Ubuntu EDGE OS.
Designed By : Tushar B Kute (http://tusharkute.com)
Technical blog by Engineering Students of Sandip Foundation, itsitrc



Technical blog by Engineering Students of Sandip Foundation, itsitrcTushar B Kute Technical blog by Engineering Students of Sandip Foundation,
http://itsitrc.blogspot.in
Tushar B Kute
http://tusharkute.com
Chapter 01 Introduction to Java by Tushar B Kute



Chapter 01 Introduction to Java by Tushar B KuteTushar B Kute The lecture was condcuted by Tushar B Kute at YCMOU, Nashik through VLC orgnanized by MSBTE. The contents can be found in book "Core Java Programming - A Practical Approach' by Laxmi Publications.
Chapter 02: Classes Objects and Methods Java by Tushar B Kute



Chapter 02: Classes Objects and Methods Java by Tushar B KuteTushar B Kute The lecture was condcuted by Tushar B Kute at YCMOU, Nashik through VLC orgnanized by MSBTE. The contents can be found in book "Core Java Programming - A Practical Approach' by Laxmi Publications.
Java Servlet Programming under Ubuntu Linux by Tushar B Kute



Java Servlet Programming under Ubuntu Linux by Tushar B KuteTushar B Kute The document provides information on programming simple servlets under Ubuntu GNU/Linux. It discusses what can be built with servlets, the benefits of servlets over CGI, definitions of servlet containers and servlet architecture. It also covers the servlet lifecycle, request and response objects, and the steps to write a simple servlet class, compile it, deploy it on Tomcat, and run it.
Ad
Recently uploaded (20)
Are Cloud PBX Providers in India Reliable for Small Businesses (1).pdf



Are Cloud PBX Providers in India Reliable for Small Businesses (1).pdfTelecoms Supermarket Discover how reliable cloud PBX providers in India are for small businesses. Explore benefits, top vendors, and integration with modern tools.
#StandardsGoals for 2025: Standards & certification roundup - Tech Forum 2025



#StandardsGoals for 2025: Standards & certification roundup - Tech Forum 2025BookNet Canada Book industry standards are evolving rapidly. In the first part of this session, we’ll share an overview of key developments from 2024 and the early months of 2025. Then, BookNet’s resident standards expert, Tom Richardson, and CEO, Lauren Stewart, have a forward-looking conversation about what’s next.
Link to recording, transcript, and accompanying resource: https://bnctechforum.ca/sessions/standardsgoals-for-2025-standards-certification-roundup/
Presented by BookNet Canada on May 6, 2025 with support from the Department of Canadian Heritage.
AI Agents at Work: UiPath, Maestro & the Future of Documents



AI Agents at Work: UiPath, Maestro & the Future of DocumentsUiPathCommunity Do you find yourself whispering sweet nothings to OCR engines, praying they catch that one rogue VAT number? Well, it’s time to let automation do the heavy lifting – with brains and brawn.
Join us for a high-energy UiPath Community session where we crack open the vault of Document Understanding and introduce you to the future’s favorite buzzword with actual bite: Agentic AI.
This isn’t your average “drag-and-drop-and-hope-it-works” demo. We’re going deep into how intelligent automation can revolutionize the way you deal with invoices – turning chaos into clarity and PDFs into productivity. From real-world use cases to live demos, we’ll show you how to move from manually verifying line items to sipping your coffee while your digital coworkers do the grunt work:
📕 Agenda:
🤖 Bots with brains: how Agentic AI takes automation from reactive to proactive
🔍 How DU handles everything from pristine PDFs to coffee-stained scans (we’ve seen it all)
🧠 The magic of context-aware AI agents who actually know what they’re doing
💥 A live walkthrough that’s part tech, part magic trick (minus the smoke and mirrors)
🗣️ Honest lessons, best practices, and “don’t do this unless you enjoy crying” warnings from the field
So whether you’re an automation veteran or you still think “AI” stands for “Another Invoice,” this session will leave you laughing, learning, and ready to level up your invoice game.
Don’t miss your chance to see how UiPath, DU, and Agentic AI can team up to turn your invoice nightmares into automation dreams.
This session streamed live on May 07, 2025, 13:00 GMT.
Join us and check out all our past and upcoming UiPath Community sessions at:
👉 https://community.uipath.com/dublin-belfast/
Heap, Types of Heap, Insertion and Deletion



Heap, Types of Heap, Insertion and DeletionJaydeep Kale This pdf will explain what is heap, its type, insertion and deletion in heap and Heap sort
How analogue intelligence complements AI



How analogue intelligence complements AIPaul Rowe
Artificial Intelligence is providing benefits in many areas of work within the heritage sector, from image analysis, to ideas generation, and new research tools. However, it is more critical than ever for people, with analogue intelligence, to ensure the integrity and ethical use of AI. Including real people can improve the use of AI by identifying potential biases, cross-checking results, refining workflows, and providing contextual relevance to AI-driven results.
News about the impact of AI often paints a rosy picture. In practice, there are many potential pitfalls. This presentation discusses these issues and looks at the role of analogue intelligence and analogue interfaces in providing the best results to our audiences. How do we deal with factually incorrect results? How do we get content generated that better reflects the diversity of our communities? What roles are there for physical, in-person experiences in the digital world?
Enterprise Integration Is Dead! Long Live AI-Driven Integration with Apache C...



Enterprise Integration Is Dead! Long Live AI-Driven Integration with Apache C...Markus Eisele We keep hearing that “integration” is old news, with modern architectures and platforms promising frictionless connectivity. So, is enterprise integration really dead? Not exactly! In this session, we’ll talk about how AI-infused applications and tool-calling agents are redefining the concept of integration, especially when combined with the power of Apache Camel.
We will discuss the the role of enterprise integration in an era where Large Language Models (LLMs) and agent-driven automation can interpret business needs, handle routing, and invoke Camel endpoints with minimal developer intervention. You will see how these AI-enabled systems help weave business data, applications, and services together giving us flexibility and freeing us from hardcoding boilerplate of integration flows.
You’ll walk away with:
An updated perspective on the future of “integration” in a world driven by AI, LLMs, and intelligent agents.
Real-world examples of how tool-calling functionality can transform Camel routes into dynamic, adaptive workflows.
Code examples how to merge AI capabilities with Apache Camel to deliver flexible, event-driven architectures at scale.
Roadmap strategies for integrating LLM-powered agents into your enterprise, orchestrating services that previously demanded complex, rigid solutions.
Join us to see why rumours of integration’s relevancy have been greatly exaggerated—and see first hand how Camel, powered by AI, is quietly reinventing how we connect the enterprise.
TrsLabs - AI Agents for All - Chatbots to Multi-Agents Systems



TrsLabs - AI Agents for All - Chatbots to Multi-Agents SystemsTrs Labs AI Adoption for Your Business
AI applications have evolved from chatbots
into sophisticated AI agents capable of
handling complex workflows. Multi-agent
systems are the next phase of evolution.
Vaibhav Gupta BAML: AI work flows without Hallucinations



Vaibhav Gupta BAML: AI work flows without Hallucinationsjohn409870 Shipping Agents
Vaibhav Gupta
Cofounder @ Boundary
in/vaigup
boundaryml/baml
Imagine if every API call you made
failed only 5% of the time
boundaryml/baml
Imagine if every LLM call you made
failed only 5% of the time
boundaryml/baml
Imagine if every LLM call you made
failed only 5% of the time
boundaryml/baml
Fault tolerant systems are hard
but now everything must be
fault tolerant
boundaryml/baml
We need to change how we
think about these systems
Aaron Villalpando
Cofounder @ Boundary
Boundary
Combinator
boundaryml/baml
We used to write websites like this:
boundaryml/baml
But now we do this:
boundaryml/baml
Problems web dev had:
boundaryml/baml
Problems web dev had:
Strings. Strings everywhere.
boundaryml/baml
Problems web dev had:
Strings. Strings everywhere.
State management was impossible.
boundaryml/baml
Problems web dev had:
Strings. Strings everywhere.
State management was impossible.
Dynamic components? forget about it.
boundaryml/baml
Problems web dev had:
Strings. Strings everywhere.
State management was impossible.
Dynamic components? forget about it.
Reuse components? Good luck.
boundaryml/baml
Problems web dev had:
Strings. Strings everywhere.
State management was impossible.
Dynamic components? forget about it.
Reuse components? Good luck.
Iteration loops took minutes.
boundaryml/baml
Problems web dev had:
Strings. Strings everywhere.
State management was impossible.
Dynamic components? forget about it.
Reuse components? Good luck.
Iteration loops took minutes.
Low engineering rigor
boundaryml/baml
React added engineering rigor
boundaryml/baml
The syntax we use changes how we
think about problems
boundaryml/baml
We used to write agents like this:
boundaryml/baml
Problems agents have:
boundaryml/baml
Problems agents have:
Strings. Strings everywhere.
Context management is impossible.
Changing one thing breaks another.
New models come out all the time.
Iteration loops take minutes.
boundaryml/baml
Problems agents have:
Strings. Strings everywhere.
Context management is impossible.
Changing one thing breaks another.
New models come out all the time.
Iteration loops take minutes.
Low engineering rigor
boundaryml/baml
Agents need
the expressiveness of English,
but the structure of code
F*** You, Show Me The Prompt.
boundaryml/baml
<show don’t tell>
Less prompting +
More engineering
=
Reliability +
Maintainability
BAML
Sam
Greg Antonio
Chris
turned down
openai to join
ex-founder, one
of the earliest
BAML users
MIT PhD
20+ years in
compilers
made his own
database, 400k+
youtube views
Vaibhav Gupta
in/vaigup
[email protected]
boundaryml/baml
Thank you!
Unlocking Generative AI in your Web Apps



Unlocking Generative AI in your Web AppsMaximiliano Firtman Slides for the session delivered at Devoxx UK 2025 - Londo.
Discover how to seamlessly integrate AI LLM models into your website using cutting-edge techniques like new client-side APIs and cloud services. Learn how to execute AI models in the front-end without incurring cloud fees by leveraging Chrome's Gemini Nano model using the window.ai inference API, or utilizing WebNN, WebGPU, and WebAssembly for open-source models.
This session dives into API integration, token management, secure prompting, and practical demos to get you started with AI on the web.
Unlock the power of AI on the web while having fun along the way!
Make GenAI investments go further with the Dell AI Factory



Make GenAI investments go further with the Dell AI FactoryPrincipled Technologies The cost benefit of implementing a Dell AI Factory solution versus AWS and Azure
Our research shows that hosting GenAI workloads on premises, either in a traditional Dell solution or using managed Dell APEX Subscriptions, could significantly lower your GenAI costs over 4 years compared to hosting these workloads in the cloud. In fact, we found that a Dell AI Factory on-premises solution could reduce costs by at much as 71 percent vs. a comparable AWS SageMaker solution and as much as 61 percent vs. a comparable Azure ML solution. These results show that organizations looking to implement GenAI and reap the business benefits to come can find many advantages in an on-premises Dell AI Factory solution, whether they opt to purchase and manage it themselves or engage with Dell APEX Subscriptions. Choosing an on-premises Dell AI Factory solution could save your organization significantly over hosting GenAI in the cloud, while giving you control over the security and privacy of your data as well as any updates and changes to the environment, and while ensuring your environment is managed consistently.
Challenges in Migrating Imperative Deep Learning Programs to Graph Execution:...



Challenges in Migrating Imperative Deep Learning Programs to Graph Execution:...Raffi Khatchadourian Efficiency is essential to support responsiveness w.r.t. ever-growing datasets, especially for Deep Learning (DL) systems. DL frameworks have traditionally embraced deferred execution-style DL code that supports symbolic, graph-based Deep Neural Network (DNN) computation. While scalable, such development tends to produce DL code that is error-prone, non-intuitive, and difficult to debug. Consequently, more natural, less error-prone imperative DL frameworks encouraging eager execution have emerged at the expense of run-time performance. While hybrid approaches aim for the "best of both worlds," the challenges in applying them in the real world are largely unknown. We conduct a data-driven analysis of challenges---and resultant bugs---involved in writing reliable yet performant imperative DL code by studying 250 open-source projects, consisting of 19.7 MLOC, along with 470 and 446 manually examined code patches and bug reports, respectively. The results indicate that hybridization: (i) is prone to API misuse, (ii) can result in performance degradation---the opposite of its intention, and (iii) has limited application due to execution mode incompatibility. We put forth several recommendations, best practices, and anti-patterns for effectively hybridizing imperative DL code, potentially benefiting DL practitioners, API designers, tool developers, and educators.
TrsLabs - Leverage the Power of UPI Payments



TrsLabs - Leverage the Power of UPI PaymentsTrs Labs Revolutionize your Fintech growth with UPI Payments
"Riding the UPI strategy" refers to leveraging the Unified Payments Interface (UPI) to drive digital payments in India and beyond. This involves understanding UPI's features, benefits, and potential, and developing strategies to maximize its usage and impact. Essentially, it's about strategically utilizing UPI to promote digital payments, financial inclusion, and economic growth.
Generative Artificial Intelligence (GenAI) in Business



Generative Artificial Intelligence (GenAI) in BusinessDr. Tathagat Varma My talk for the Indian School of Business (ISB) Emerging Leaders Program Cohort 9. In this talk, I discussed key issues around adoption of GenAI in business - benefits, opportunities and limitations. I also discussed how my research on Theory of Cognitive Chasms helps address some of these issues
Cybersecurity Identity and Access Solutions using Azure AD



Cybersecurity Identity and Access Solutions using Azure ADVICTOR MAESTRE RAMIREZ Cybersecurity Identity and Access Solutions using Azure AD
AI and Data Privacy in 2025: Global Trends



AI and Data Privacy in 2025: Global TrendsInData Labs In this infographic, we explore how businesses can implement effective governance frameworks to address AI data privacy. Understanding it is crucial for developing effective strategies that ensure compliance, safeguard customer trust, and leverage AI responsibly. Equip yourself with insights that can drive informed decision-making and position your organization for success in the future of data privacy.
This infographic contains:
-AI and data privacy: Key findings
-Statistics on AI data privacy in the today’s world
-Tips on how to overcome data privacy challenges
-Benefits of AI data security investments.
Keep up-to-date on how AI is reshaping privacy standards and what this entails for both individuals and organizations.
How to Install & Activate ListGrabber - eGrabber



How to Install & Activate ListGrabber - eGrabbereGrabber ListGrabber: Build Targeted Lists Online in Minutes
Bepents tech services - a premier cybersecurity consulting firm



Bepents tech services - a premier cybersecurity consulting firmBenard76 Introduction
Bepents Tech Services is a premier cybersecurity consulting firm dedicated to protecting digital infrastructure, data, and business continuity. We partner with organizations of all sizes to defend against today’s evolving cyber threats through expert testing, strategic advisory, and managed services.
🔎 Why You Need us
Cyberattacks are no longer a question of “if”—they are a question of “when.” Businesses of all sizes are under constant threat from ransomware, data breaches, phishing attacks, insider threats, and targeted exploits. While most companies focus on growth and operations, security is often overlooked—until it’s too late.
At Bepents Tech, we bridge that gap by being your trusted cybersecurity partner.
🚨 Real-World Threats. Real-Time Defense.
Sophisticated Attackers: Hackers now use advanced tools and techniques to evade detection. Off-the-shelf antivirus isn’t enough.
Human Error: Over 90% of breaches involve employee mistakes. We help build a "human firewall" through training and simulations.
Exposed APIs & Apps: Modern businesses rely heavily on web and mobile apps. We find hidden vulnerabilities before attackers do.
Cloud Misconfigurations: Cloud platforms like AWS and Azure are powerful but complex—and one misstep can expose your entire infrastructure.
💡 What Sets Us Apart
Hands-On Experts: Our team includes certified ethical hackers (OSCP, CEH), cloud architects, red teamers, and security engineers with real-world breach response experience.
Custom, Not Cookie-Cutter: We don’t offer generic solutions. Every engagement is tailored to your environment, risk profile, and industry.
End-to-End Support: From proactive testing to incident response, we support your full cybersecurity lifecycle.
Business-Aligned Security: We help you balance protection with performance—so security becomes a business enabler, not a roadblock.
📊 Risk is Expensive. Prevention is Profitable.
A single data breach costs businesses an average of $4.45 million (IBM, 2023).
Regulatory fines, loss of trust, downtime, and legal exposure can cripple your reputation.
Investing in cybersecurity isn’t just a technical decision—it’s a business strategy.
🔐 When You Choose Bepents Tech, You Get:
Peace of Mind – We monitor, detect, and respond before damage occurs.
Resilience – Your systems, apps, cloud, and team will be ready to withstand real attacks.
Confidence – You’ll meet compliance mandates and pass audits without stress.
Expert Guidance – Our team becomes an extension of yours, keeping you ahead of the threat curve.
Security isn’t a product. It’s a partnership.
Let Bepents tech be your shield in a world full of cyber threats.
🌍 Our Clientele
At Bepents Tech Services, we’ve earned the trust of organizations across industries by delivering high-impact cybersecurity, performance engineering, and strategic consulting. From regulatory bodies to tech startups, law firms, and global consultancies, we tailor our solutions to each client's unique needs.
Challenges in Migrating Imperative Deep Learning Programs to Graph Execution:...



Challenges in Migrating Imperative Deep Learning Programs to Graph Execution:...Raffi Khatchadourian
Share File easily between computers using sftp
- 1. Share files easily between computers using sftp Tushar B. Kute [email protected]
- 2. sftp ● The SSH File Transfer Protocol (also Secure File Transfer Protocol, or SFTP) is a network protocol that provides file access, file transfer, and file management functionalities over any reliable data stream. ● It was designed by the Internet Engineering Task Force (IETF) as an extension of the Secure Shell protocol (SSH) version 2.0 to provide secure file transfer capabilities. ● This protocol assumes that it is run over a secure channel, such as SSH, that the server has already authenticated the client, and that the identity of the client user is available to the protocol.
- 3. sftp server and client ● SFTP client – It is a command-line program that implements the client part of this protocol. As an example, the sftp program supplied with OpenSSH implements this. – Some implementations of the scp program support both the SFTP and SCP protocols to perform file transfers, depending on what the server supports. ● SFTP server – There are numerous SFTP server implementations both for UNIX, Windows and z/OS. The most widely known is perhaps OpenSSH, but there are also proprietary implementations. Typically the port used is 22. SFTP file transfer protocol is part of SSH protocol suite.
- 4. What is OpenSSH? ● OpenSSH is a free open source set of computer tools used to provide secure and encrypted communication over a computer network by using the ssh protocol. ● Many people, new to computers and protocols, create a misconception about OpenSSH, they think it is a protocol, but it is not, it is a set of computer programs that use the ssh protocol. ● OpenSSH is developed by the Open BSD group and it is released under Simplified BSD License. ● A main factor which has made possible for OpenSSH to be used so much among system administrators is its multi-platform capability and very useful nice features it has. The latest version is OpenSSH 6.4 which has been released on November 8, 2013.
- 5. Why to use sftp over ftp/telnet? ● The most important reason why should use OpenSSH tools over ftp and telnet is that all communications and user credentials using OpenSSH are encrypted, they are also protected from man in the middle attacks. ● If a third party tries to intercept your connection, OpenSSH detects it and informs you about that.
- 6. Features of OpenSSH ● Secure Communication ● Strong Encryption (3DES, Blowfish, AES, Arcfour) ● X11 Forwarding (encrypt X Window System traffic) ● Port Forwarding (encrypted channels for legacy protocols) ● Strong Authentication (Public Key, One-Time Password and Kerberos Authentication) ● Agent Forwarding (Single-Sign-On) ● Interoperability (Compliance with SSH 1.3, 1.5, and 2.0 protocol Standards) ● SFTP client and server support in both SSH1 and SSH2 protocols. ● Kerberos and AFS Ticket Passing ● Data Compression
- 7. OpenSSH Requirements ● OpenSSH can be installed on any kind of Linux systems and any kind of network connections. ● I have used Ubuntu and Linux Mint in the demonstration. ● Laptop-1: – Dell Vostro with Ubuntu 14.04. – Connected physically to network. ● Laptop-2: – Toshiba Satellite with Linux Mint 17.1 – Connected using Wi-Fi to network.
- 8. Setup in my experiments Laptop-1 Laptop-2 COPY
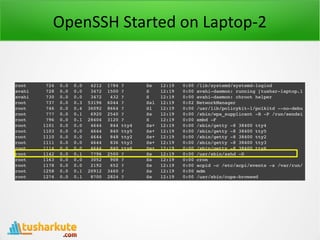
- 10. OpenSSH Started on Laptop-2
- 11. Check IP of Laptop-1
- 12. Check IP of Laptop-2
- 13. On Laptop-1 ● I want to access the files in Laptop-1 from Laptop-2. ● Use following command to get connected Laptop-1 to Laptop-2 using sftp. Authentication: yes Username of Laptop-2
- 14. Asks the password Type laptop-2 password here
- 15. sftp prompt
- 16. See the files on Laptop-2
- 17. See the same files on Laptop-1 ● Type ls on sftp prompt of Laptop-1
- 18. Copy files (Laptop-2) I want to copy this file to Laptop-1
- 19. Use 'get' command to copy file (Laptop-1) Downloaded to /home folder
- 20. Check the copied file
- 21. Check other sftp commands by typing help
- 22. Other ways to copy files ● Once authentication is completed and connection is done successfully, we can also use following ways to copy the files. – Web browser. – File browser.
- 23. Open firefox
- 24. Type username and password
- 25. Files of Laptop-2 are visible on Laptop-1
- 26. I want to download a file
- 27. Click on the filename and save it
- 28. Check your file browser now By clicking here, you may access the files of laptop-2 directly by file browser
- 29. [email protected] Thank you This presentation is created using LibreOffice Impress 4.2.7.2, can be used freely as per GNU General Public License Blogs http://digitallocha.blogspot.in http://kyamputar.blogspot.in Web Resources http://tusharkute.com




