Security testing ?
3 likes889 views
The document discusses the importance of web application security testing. It covers many common vulnerabilities like SQL injection, cross-site scripting, and insecure direct object references. The document provides examples of how to test for these issues and recommends resources like OWASP guides, WebGoat, and DVWA for practicing security testing techniques. It emphasizes that all web inputs should be treated as untrusted to prevent exploits. Overall, the document aims to educate about the prevalence of web app vulnerabilities and the need for thorough security assessments.
1 of 46













































Ad
Recommended
Security Testing



Security TestingKiran Kumar The document discusses integrating security testing into the typical iterative development lifecycle through automated software tests at various stages, including unit tests, integration tests, and acceptance tests. It provides examples of using JUnit for unit testing and tools like Cactus, Selenium, and WATIR for integration and acceptance testing to validate valid/invalid inputs and test for vulnerabilities like SQL injection and cross-site scripting.
Owasp zap



Owasp zapColdFusionConference This document discusses using the OWASP Zed Attack Proxy (ZAP) tool to find vulnerabilities in web applications. ZAP is a free and open-source web application penetration testing tool that can be used to conduct both automated and manual testing of applications. The document provides an overview of ZAP's features, how to install and configure it, how to test applications for vulnerabilities using both automated and direct methods, and how to integrate ZAP with other tools.
Cypress Automation Testing Tutorial (Part 1).pdf



Cypress Automation Testing Tutorial (Part 1).pdfbacancytechnology Learn how to set up an end-to-end testing framework Cypress Automation Testing Tutorial in an angular app. Also, visit the Github code to set up the project.
The OWASP Zed Attack Proxy



The OWASP Zed Attack ProxyAditya Gupta It is a presentation of the work done in a Research and Development Project on the Zed Attack Proxy Tool.
Security testing fundamentals



Security testing fundamentalsCygnet Infotech Security Testing is deemed successful when the below attributes of an application are intact
- Authentication
- Authorization
- Availability
- Confidentiality
- Integrity
- Non-Repudiation
Testing must start early to minimize defects and cost of quality. Security testing must start right from the Requirements Gathering phase to make sure that the quality of end-product is high.
This is to ensure that any intentional/unintentional unforeseen action does not halt or delay the system.
Owasp zap



Owasp zappenetration Tester The document provides information on OWASP ZAP, a free and open source web application security testing tool. It discusses what ZAP is, why it is a good choice for security testing, its key features which include an intercepting proxy, scanners, spiders, and fuzzing. It then describes how to launch and use ZAP, covering its graphical user interface, attacking websites by spidering, scanning and reviewing alerts. Key terms like session and context are also explained. Steps to run a scan are outlined, including crawling the site, creating a session and context, attacking with spider and active scans, and reviewing scan results. Finally, the difference between active and passive scans is summarized.
Bug Bounty 101



Bug Bounty 101Shahee Mirza This document provides an introduction to bug bounty programs. It defines what a bug bounty program is, provides a brief history of major programs, and discusses reasons they are beneficial for both security researchers and companies. Key points covered include popular programs like Google and Facebook, tools used in bug hunting like Burp Suite, and lessons for researchers such as writing quality reports and following each program's rules.
Cypress Automation



Cypress AutomationSusantha Pathirana Cypress is an end-to-end testing framework that focuses on doing testing well through features like time travel debugging, real-time reloads, and automatic waiting. It works on any frontend framework and tests are written in JavaScript alone. Cypress provides an all-in-one solution for developers and QA engineers to set up testing, write Cucumber tests, run and debug tests from a dashboard or command line, and generate reports including screenshots, videos, and JUnit files.
AppSec EU 2016: Automated Mobile Application Security Assessment with MobSF



AppSec EU 2016: Automated Mobile Application Security Assessment with MobSFAjin Abraham Mobile Application market is growing like anything and so is the Mobile Security industry. With lots of frequent application releases and updates happening, conducting the complete security analysis of mobile applications becomes time consuming and cumbersome. In this talk I will introduce an extendable, and scalable web framework called Mobile Security Framework (https://github.com/ajinabraham/YSO-Mobile-Security-Framework) for Security analysis of Mobile Applications. Mobile Security Framework is an intelligent and automated open source mobile application (Android/iOS) pentesting and binary/code analysis framework capable of performing static and dynamic analysis. It supports Android and iOS binaries as well as zipped source code. During the presentation, I will demonstrates some of the issues identified by the tool in real world android applications. The latest Dynamic Analyzer module will be released at OWASP AppSec. Attendees Benefits * An Open Source framework for Automated Mobile Security Assessment. * One Click Report Generation and Security Assessment. * Framework can be deployed at your own environment so that you have complete control of the data. The data/report stays within the organisation and nothing is stored in the cloud. * Supports both Android and iOS Applications. * Semi Automatic Dynamic Analyzer for intelligent application logic based (whitebox) security assessment.
Android Application Penetration Testing - Mohammed Adam



Android Application Penetration Testing - Mohammed AdamMohammed Adam Android Penetration Testing is a process of testing and finding security issues in an android application. It involves decompiling, real-time analyzing and testing android application for security point of view. This Slides covers real-time testing of android applications and some security issues like insecure logging, leaking content providers, insecure data storage and access control issues.
Checkmarx meetup API Security - API Security top 10 - Erez Yalon



Checkmarx meetup API Security - API Security top 10 - Erez YalonAdar Weidman The document summarizes API security topics presented by Erez Yalon at a Checkmarx Meetup event. Yalon discusses how API-based applications are different from traditional apps and deserve their own security focus. He outlines the OWASP API Security Project and the proposed API Security Top 10 risks, including broken object level authorization, excessive data exposure, lack of resources/rate limiting, and improper asset management. Yalon calls for community contributions to further develop the Top 10 and other API security resources.
Secure Code Review 101



Secure Code Review 101Narudom Roongsiriwong, CISSP Secure code review is probably the most effective technique to identify security bugs early in the system development lifecycle.
When used together with automated and manual penetration testing, code review can significantly increase the cost effectiveness of an application security verification effort. This presentation explain how can we start secure code review effectively.
CSSLP & OWASP & WebGoat



CSSLP & OWASP & WebGoatSurachai Chatchalermpun Challenge Web Application Today!!!
Promote CSSLP Certification.
Introduce OWASP 2010 Top 10 Risks?
Practice with Web Goat?
For Education only.
The Game of Bug Bounty Hunting - Money, Drama, Action and Fame



The Game of Bug Bounty Hunting - Money, Drama, Action and FameAbhinav Mishra The document provides an overview of the game of bug bounty hunting, including a brief history of bug bounty programs, the present state of platforms like HackerOne and BugCrowd, tips for getting started, techniques for finding different types of vulnerabilities, examples of famous bounty submissions, and potential drama one may face. It also includes suggestions for resources, tools, blogs, and people to follow to continue learning and developing skills in bug bounty hunting.
Continuous Application Security at Scale with IAST and RASP -- Transforming D...



Continuous Application Security at Scale with IAST and RASP -- Transforming D...Jeff Williams Abstract: SAST, DAST, and WAF have been around for almost 15 years — they’re almost impossible to use, can’t protect modern applications, and aren’t compatible with modern software development. Recent studies have demonstrated that these tools miss the majority of real vulnerabilities and attacks while generating staggering numbers of false positives. To compensate, these tools require huge teams of application security experts that can’t possibly keep up with the size of modern application portfolios. Fortunately, the next generation of application security technology uses dynamic software instrumentation to solve these challenges. Gartner calls these products “Interactive Application Security Testing (IAST)” and “Runtime Application Self-Protection (RASP).” In this talk, you’ll learn how IAST and RASP have revolutionized vulnerability assessment and attack prevention in a massively scalable way.
Bio: A pioneer in application security, Jeff Williams is the founder and CTO of Contrast Security, a revolutionary application security product. Contrast is an application agent that enables software to both report vulnerabilities and prevent attacks. Jeff has over 25 years of security experience, speaks frequently on cutting-edge application security, and has helped secure code at hundreds of major enterprises. Jeff served as the Global Chairman of the OWASP Foundation for eight years, where he created many open-source standards, tools, libraries, and guidelines - including the OWASP Top Ten.
Introduction to E2E in Cypress



Introduction to E2E in CypressFabio Biondi This document discusses Cypress, an open-source JavaScript testing framework for front-end web applications. It highlights key Cypress features like time travel debugging, real-time reloads, and automatic waiting. It provides an overview of how to install Cypress, write tests using an arrange-act-assert structure, query elements, make assertions, and interact with elements. Examples of testing a login flow and cart panel are also presented. The document promotes Cypress and encourages attending live coding sessions to learn more about component testing.
Spring Security 5



Spring Security 5Jesus Perez Franco This document provides an overview of Spring Security including:
I. It distinguishes Spring Framework, Spring Boot, and Spring Security and their relationships.
II. It defines Spring Security as a framework focusing on authentication and authorization for Java applications.
III. It outlines some of the core concepts in Spring Security such as Principal, Authentication, Authorization, GrantedAuthority etc.
The document serves as an introduction to Spring Security fundamentals and architecture.
Pentesting Using Burp Suite



Pentesting Using Burp Suitejasonhaddix This document provides an outline for a presentation on pentesting web applications with Burp Suite. It discusses using Burp Suite to scope a target, map content through spidering and directory bruteforcing, replace automated scanning with manual fuzzing using attack paylists, and test authentication through bruteforcing logins. Specific techniques covered include using the Burp spider, intruder, and engagement tools to discover content and hidden directories, importing wordlists to bruteforce hidden paths, and configuring intruder payloads and grep rules to analyze results from fuzzing and authentication testing.
API Security Fundamentals



API Security FundamentalsJosé Haro Peralta Slides for my webinar "API Security Fundamentals". They cover
👉 𝐎𝐖𝐀𝐒𝐏’𝐬 𝐭𝐨𝐩 𝟏𝟎 API security vulnerabilities with suggestions on how to avoid them, including the 2019 and the 2023 versions.
👉 API authorization and authentication using 𝐎𝐀𝐮𝐭𝐡 and 𝐎𝐈𝐃𝐂
👉 How certain 𝐀𝐏𝐈 𝐝𝐞𝐬𝐢𝐠𝐧𝐬 expose vulnerabilities and how to prevent them
👉 APIs sit within a wider system and therefore API security requires a 𝐡𝐨𝐥𝐢𝐬𝐭𝐢𝐜 𝐚𝐩𝐩𝐫𝐨𝐚𝐜𝐡. I’ll talk about elements “around the API” that also need to be protected
👉 automating API 𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐭𝐞𝐬𝐭𝐢𝐧𝐠
Nullcon Goa 2016 - Automated Mobile Application Security Testing with Mobile ...



Nullcon Goa 2016 - Automated Mobile Application Security Testing with Mobile ...Ajin Abraham Mobile Security Framework (MobSF) is an intelligent, all-in-one open source mobile application (Android/iOS) automated pen-testing framework capable of performing static and dynamic analysis. It can be used for effective and fast security analysis of Android and iOS Applications and supports both binaries (APK & IPA) and zipped source code. MobSF can also perform Web API Security testing with it's API Fuzzer that can do Information Gathering, analyze Security Headers, identify Mobile API specific vulnerabilities like XXE, SSRF, Path Traversal, IDOR, and other logical issues related to Session and API Rate Limiting.
e2e testing with cypress



e2e testing with cypressTomasz Bak Cypress is an e2e testing tool that allows for testing web applications directly in the browser. It provides native access to the browser without using Selenium, making tasks like taking screenshots and recording videos possible. Some limitations are that it only supports single-page applications and one browser tab at a time. Cypress prioritizes developer experience through features like fast testing, intuitive debugging, and integration with continuous integration systems and dashboards. Many large companies have adopted Cypress for their e2e testing needs.
Web Application Security Testing



Web Application Security TestingMarco Morana The document discusses risk-based security testing methodology for web applications. It involves deriving test cases from threat analysis techniques like attack tree analysis and understanding real-world attack vectors. The goal is to simulate real attacker scenarios and test for vulnerabilities, as well as potential abuse of business logic or flaws in the secure architecture. Security testing is integrated into the software development lifecycle to find and fix issues early.
OWASP Mobile Top 10 Deep-Dive



OWASP Mobile Top 10 Deep-DivePrathan Phongthiproek The presentation contains the OWASP Mobile Top 10 2016 information including case study and remediation measures.
Java Source Code Analysis using SonarQube



Java Source Code Analysis using SonarQubeAngelin R This document discusses how to set up and use SonarQube to analyze code quality for both Maven and non-Maven projects. It describes installing the SonarQube server and runner, configuring the server, and setting up projects for analysis by adding a sonar-project.properties file. It then explains how to generate a SonarQube report by running the sonar-runner on a project and view results on the SonarQube server dashboard.
Spring Security



Spring SecurityBoy Tech I did this presentation for one of my java user groups at work.
Basically, this is a mashed up version of various presentations, slides and images that I gathered over the internet.
I've quoted the sources in the end. Feel free to reuse it as you like.
SonarQube Presentation.pptx



SonarQube Presentation.pptxSatwik Bhupathi Raju There's no other tool in the market that is as reliable and trustworthy as SonarQube for Static Analysis.
Getting Started with API Security Testing



Getting Started with API Security TestingSmartBear Ole Lensmar, CTO of SmartBear Software, presents the basics of API security and API security testing. From his successful STARWest talk.
Bug bounty



Bug bountyn|u - The Open Security Community This document discusses bug bounty programs (BBPs), which reward security researchers for responsibly disclosing software vulnerabilities. It introduces BBPs, noting they save companies money while improving security. Major companies like Google and Facebook run BBPs. The document outlines prerequisites for BBPs like learning security testing techniques. It provides tips for finding vulnerabilities like understanding a site's scope, tools, and avoiding duplicate reports. Common vulnerability types in BBPs include injection flaws and insecure data storage.
Continuous and Visible Security Testing with BDD-Security



Continuous and Visible Security Testing with BDD-SecurityStephen de Vries This presentation makes the case for adapting security requirements and processes to those used by developers. Specifically, it advocates the use of BDD (Given/When/Then) specifications to create self-verifying security requirements.
You've heard of infrastructure as code, with the BDD-Security framework, we can now write security-processes-as-code.
DevOpsCon 2016 - Continuous Security Testing - Stephan Kaps



DevOpsCon 2016 - Continuous Security Testing - Stephan KapsStephan Kaps Continuous Delivery (CD) ist in aller Munde. Zu Recht, doch wollen wir unsere Software kontinuierlich ausliefern, müssen wir auch kontinuierlich Sicherheitstests durchführen.
Continuous Security Testing bedeutet, statische und dynamische Analysen bereits während der Entwicklung durchzuführen, um frühzeitig und regelmäßig Sicherheitsmaßnahmen umzusetzen, bevor manuelle Prüfungen wie Penetrationstests zum Einsatz kommen. Um eine Anwendung bereits während der Entwicklung auf das Vorhandensein sicherheitskritischer Schwachstellen hin überprüfen zu können, ist eine Integration in den Entwicklungsprozess und somit eine kontinuierliche und am besten automatisierte Prüfung notwendig.
Der Vortrag stellt die praktischen Erfahrungen aus einem Projekt vor, bei dem Sicherheitsrichtlinien (Secure Coding Guide) für die eigene Entwicklung von Java-Webanwendungen aufgestellt und Sicherheitstests in den Softwareentwicklungsprozess integriert wurden. Dabei wird auf die organisatorischen, inhaltlichen und technischen Überlegungen eingegangen.
Ad
More Related Content
What's hot (20)
AppSec EU 2016: Automated Mobile Application Security Assessment with MobSF



AppSec EU 2016: Automated Mobile Application Security Assessment with MobSFAjin Abraham Mobile Application market is growing like anything and so is the Mobile Security industry. With lots of frequent application releases and updates happening, conducting the complete security analysis of mobile applications becomes time consuming and cumbersome. In this talk I will introduce an extendable, and scalable web framework called Mobile Security Framework (https://github.com/ajinabraham/YSO-Mobile-Security-Framework) for Security analysis of Mobile Applications. Mobile Security Framework is an intelligent and automated open source mobile application (Android/iOS) pentesting and binary/code analysis framework capable of performing static and dynamic analysis. It supports Android and iOS binaries as well as zipped source code. During the presentation, I will demonstrates some of the issues identified by the tool in real world android applications. The latest Dynamic Analyzer module will be released at OWASP AppSec. Attendees Benefits * An Open Source framework for Automated Mobile Security Assessment. * One Click Report Generation and Security Assessment. * Framework can be deployed at your own environment so that you have complete control of the data. The data/report stays within the organisation and nothing is stored in the cloud. * Supports both Android and iOS Applications. * Semi Automatic Dynamic Analyzer for intelligent application logic based (whitebox) security assessment.
Android Application Penetration Testing - Mohammed Adam



Android Application Penetration Testing - Mohammed AdamMohammed Adam Android Penetration Testing is a process of testing and finding security issues in an android application. It involves decompiling, real-time analyzing and testing android application for security point of view. This Slides covers real-time testing of android applications and some security issues like insecure logging, leaking content providers, insecure data storage and access control issues.
Checkmarx meetup API Security - API Security top 10 - Erez Yalon



Checkmarx meetup API Security - API Security top 10 - Erez YalonAdar Weidman The document summarizes API security topics presented by Erez Yalon at a Checkmarx Meetup event. Yalon discusses how API-based applications are different from traditional apps and deserve their own security focus. He outlines the OWASP API Security Project and the proposed API Security Top 10 risks, including broken object level authorization, excessive data exposure, lack of resources/rate limiting, and improper asset management. Yalon calls for community contributions to further develop the Top 10 and other API security resources.
Secure Code Review 101



Secure Code Review 101Narudom Roongsiriwong, CISSP Secure code review is probably the most effective technique to identify security bugs early in the system development lifecycle.
When used together with automated and manual penetration testing, code review can significantly increase the cost effectiveness of an application security verification effort. This presentation explain how can we start secure code review effectively.
CSSLP & OWASP & WebGoat



CSSLP & OWASP & WebGoatSurachai Chatchalermpun Challenge Web Application Today!!!
Promote CSSLP Certification.
Introduce OWASP 2010 Top 10 Risks?
Practice with Web Goat?
For Education only.
The Game of Bug Bounty Hunting - Money, Drama, Action and Fame



The Game of Bug Bounty Hunting - Money, Drama, Action and FameAbhinav Mishra The document provides an overview of the game of bug bounty hunting, including a brief history of bug bounty programs, the present state of platforms like HackerOne and BugCrowd, tips for getting started, techniques for finding different types of vulnerabilities, examples of famous bounty submissions, and potential drama one may face. It also includes suggestions for resources, tools, blogs, and people to follow to continue learning and developing skills in bug bounty hunting.
Continuous Application Security at Scale with IAST and RASP -- Transforming D...



Continuous Application Security at Scale with IAST and RASP -- Transforming D...Jeff Williams Abstract: SAST, DAST, and WAF have been around for almost 15 years — they’re almost impossible to use, can’t protect modern applications, and aren’t compatible with modern software development. Recent studies have demonstrated that these tools miss the majority of real vulnerabilities and attacks while generating staggering numbers of false positives. To compensate, these tools require huge teams of application security experts that can’t possibly keep up with the size of modern application portfolios. Fortunately, the next generation of application security technology uses dynamic software instrumentation to solve these challenges. Gartner calls these products “Interactive Application Security Testing (IAST)” and “Runtime Application Self-Protection (RASP).” In this talk, you’ll learn how IAST and RASP have revolutionized vulnerability assessment and attack prevention in a massively scalable way.
Bio: A pioneer in application security, Jeff Williams is the founder and CTO of Contrast Security, a revolutionary application security product. Contrast is an application agent that enables software to both report vulnerabilities and prevent attacks. Jeff has over 25 years of security experience, speaks frequently on cutting-edge application security, and has helped secure code at hundreds of major enterprises. Jeff served as the Global Chairman of the OWASP Foundation for eight years, where he created many open-source standards, tools, libraries, and guidelines - including the OWASP Top Ten.
Introduction to E2E in Cypress



Introduction to E2E in CypressFabio Biondi This document discusses Cypress, an open-source JavaScript testing framework for front-end web applications. It highlights key Cypress features like time travel debugging, real-time reloads, and automatic waiting. It provides an overview of how to install Cypress, write tests using an arrange-act-assert structure, query elements, make assertions, and interact with elements. Examples of testing a login flow and cart panel are also presented. The document promotes Cypress and encourages attending live coding sessions to learn more about component testing.
Spring Security 5



Spring Security 5Jesus Perez Franco This document provides an overview of Spring Security including:
I. It distinguishes Spring Framework, Spring Boot, and Spring Security and their relationships.
II. It defines Spring Security as a framework focusing on authentication and authorization for Java applications.
III. It outlines some of the core concepts in Spring Security such as Principal, Authentication, Authorization, GrantedAuthority etc.
The document serves as an introduction to Spring Security fundamentals and architecture.
Pentesting Using Burp Suite



Pentesting Using Burp Suitejasonhaddix This document provides an outline for a presentation on pentesting web applications with Burp Suite. It discusses using Burp Suite to scope a target, map content through spidering and directory bruteforcing, replace automated scanning with manual fuzzing using attack paylists, and test authentication through bruteforcing logins. Specific techniques covered include using the Burp spider, intruder, and engagement tools to discover content and hidden directories, importing wordlists to bruteforce hidden paths, and configuring intruder payloads and grep rules to analyze results from fuzzing and authentication testing.
API Security Fundamentals



API Security FundamentalsJosé Haro Peralta Slides for my webinar "API Security Fundamentals". They cover
👉 𝐎𝐖𝐀𝐒𝐏’𝐬 𝐭𝐨𝐩 𝟏𝟎 API security vulnerabilities with suggestions on how to avoid them, including the 2019 and the 2023 versions.
👉 API authorization and authentication using 𝐎𝐀𝐮𝐭𝐡 and 𝐎𝐈𝐃𝐂
👉 How certain 𝐀𝐏𝐈 𝐝𝐞𝐬𝐢𝐠𝐧𝐬 expose vulnerabilities and how to prevent them
👉 APIs sit within a wider system and therefore API security requires a 𝐡𝐨𝐥𝐢𝐬𝐭𝐢𝐜 𝐚𝐩𝐩𝐫𝐨𝐚𝐜𝐡. I’ll talk about elements “around the API” that also need to be protected
👉 automating API 𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐭𝐞𝐬𝐭𝐢𝐧𝐠
Nullcon Goa 2016 - Automated Mobile Application Security Testing with Mobile ...



Nullcon Goa 2016 - Automated Mobile Application Security Testing with Mobile ...Ajin Abraham Mobile Security Framework (MobSF) is an intelligent, all-in-one open source mobile application (Android/iOS) automated pen-testing framework capable of performing static and dynamic analysis. It can be used for effective and fast security analysis of Android and iOS Applications and supports both binaries (APK & IPA) and zipped source code. MobSF can also perform Web API Security testing with it's API Fuzzer that can do Information Gathering, analyze Security Headers, identify Mobile API specific vulnerabilities like XXE, SSRF, Path Traversal, IDOR, and other logical issues related to Session and API Rate Limiting.
e2e testing with cypress



e2e testing with cypressTomasz Bak Cypress is an e2e testing tool that allows for testing web applications directly in the browser. It provides native access to the browser without using Selenium, making tasks like taking screenshots and recording videos possible. Some limitations are that it only supports single-page applications and one browser tab at a time. Cypress prioritizes developer experience through features like fast testing, intuitive debugging, and integration with continuous integration systems and dashboards. Many large companies have adopted Cypress for their e2e testing needs.
Web Application Security Testing



Web Application Security TestingMarco Morana The document discusses risk-based security testing methodology for web applications. It involves deriving test cases from threat analysis techniques like attack tree analysis and understanding real-world attack vectors. The goal is to simulate real attacker scenarios and test for vulnerabilities, as well as potential abuse of business logic or flaws in the secure architecture. Security testing is integrated into the software development lifecycle to find and fix issues early.
OWASP Mobile Top 10 Deep-Dive



OWASP Mobile Top 10 Deep-DivePrathan Phongthiproek The presentation contains the OWASP Mobile Top 10 2016 information including case study and remediation measures.
Java Source Code Analysis using SonarQube



Java Source Code Analysis using SonarQubeAngelin R This document discusses how to set up and use SonarQube to analyze code quality for both Maven and non-Maven projects. It describes installing the SonarQube server and runner, configuring the server, and setting up projects for analysis by adding a sonar-project.properties file. It then explains how to generate a SonarQube report by running the sonar-runner on a project and view results on the SonarQube server dashboard.
Spring Security



Spring SecurityBoy Tech I did this presentation for one of my java user groups at work.
Basically, this is a mashed up version of various presentations, slides and images that I gathered over the internet.
I've quoted the sources in the end. Feel free to reuse it as you like.
SonarQube Presentation.pptx



SonarQube Presentation.pptxSatwik Bhupathi Raju There's no other tool in the market that is as reliable and trustworthy as SonarQube for Static Analysis.
Getting Started with API Security Testing



Getting Started with API Security TestingSmartBear Ole Lensmar, CTO of SmartBear Software, presents the basics of API security and API security testing. From his successful STARWest talk.
Bug bounty



Bug bountyn|u - The Open Security Community This document discusses bug bounty programs (BBPs), which reward security researchers for responsibly disclosing software vulnerabilities. It introduces BBPs, noting they save companies money while improving security. Major companies like Google and Facebook run BBPs. The document outlines prerequisites for BBPs like learning security testing techniques. It provides tips for finding vulnerabilities like understanding a site's scope, tools, and avoiding duplicate reports. Common vulnerability types in BBPs include injection flaws and insecure data storage.
Viewers also liked (9)
Continuous and Visible Security Testing with BDD-Security



Continuous and Visible Security Testing with BDD-SecurityStephen de Vries This presentation makes the case for adapting security requirements and processes to those used by developers. Specifically, it advocates the use of BDD (Given/When/Then) specifications to create self-verifying security requirements.
You've heard of infrastructure as code, with the BDD-Security framework, we can now write security-processes-as-code.
DevOpsCon 2016 - Continuous Security Testing - Stephan Kaps



DevOpsCon 2016 - Continuous Security Testing - Stephan KapsStephan Kaps Continuous Delivery (CD) ist in aller Munde. Zu Recht, doch wollen wir unsere Software kontinuierlich ausliefern, müssen wir auch kontinuierlich Sicherheitstests durchführen.
Continuous Security Testing bedeutet, statische und dynamische Analysen bereits während der Entwicklung durchzuführen, um frühzeitig und regelmäßig Sicherheitsmaßnahmen umzusetzen, bevor manuelle Prüfungen wie Penetrationstests zum Einsatz kommen. Um eine Anwendung bereits während der Entwicklung auf das Vorhandensein sicherheitskritischer Schwachstellen hin überprüfen zu können, ist eine Integration in den Entwicklungsprozess und somit eine kontinuierliche und am besten automatisierte Prüfung notwendig.
Der Vortrag stellt die praktischen Erfahrungen aus einem Projekt vor, bei dem Sicherheitsrichtlinien (Secure Coding Guide) für die eigene Entwicklung von Java-Webanwendungen aufgestellt und Sicherheitstests in den Softwareentwicklungsprozess integriert wurden. Dabei wird auf die organisatorischen, inhaltlichen und technischen Überlegungen eingegangen.
Security testing



Security testingRihab Chebbah Security testing involves testing software to identify security flaws and vulnerabilities. It is done at various stages of development, including unit testing by developers, integrated system testing of the full application, and functional acceptance testing by quality assurance testers. Security testing techniques include static analysis, dynamic testing, and fuzzing invalid or random inputs to expose unexpected behaviors and potential vulnerabilities. Thorough security testing requires checking for issues like SQL injection, unauthorized access, disclosure of sensitive data, and verifying proper access controls, authentication, encryption, and input validation. Various tools can assist with security testing.
Security testing presentation



Security testing presentationConfiz The document discusses security testing of software and applications. It defines security testing as testing the ability of a system to prevent unauthorized access to resources and data. It outlines common security risks like SQL injection, cross-site scripting, and insecure direct object references. It also describes different types of security testing like black box and white box testing and provides examples of security vulnerabilities like XSS and tools used for security testing.
Software Project Management: Testing Document



Software Project Management: Testing DocumentMinhas Kamal This document outlines the testing plan for an application called ResearchCoLab. It details test items, strategy, required tools, measures, pass/fail criteria, responsibilities, and schedule. Test cases are provided to test database integrity, system response time under load, user access permissions, compatibility across configurations, and implemented features such as user registration and login. The goal is to thoroughly test the application according to best practices before the scheduled submission date.
we45 - Web Application Security Testing Case Study



we45 - Web Application Security Testing Case Studywe45 we45 performed a comprehensive security test of a large messaging gateway's platform over 5 years. They identified deep injection flaws and unauthorized access to web services. we45 presented detailed findings, which were remediated. The client now has an enhanced security program with we45 as a long-term security partner.
Pactera Cybersecurity - Application Security Penetration Testing - Mobile, We...



Pactera Cybersecurity - Application Security Penetration Testing - Mobile, We...Kyle Lai Pactera Technologies North America (NA) Cybersecurity Consulting Services specializes in Cybersecurity Program Development, Application Vulnerability Assessment, Application Security Governance, Secure SDLC, Secure Coding Practice Training, and Third-party supplier security risk management and assessment. We only hire top security consultants that are most qualified for this job. We love to prove ourselves to you!
8 Access Control



8 Access ControlAlfred Ouyang This document provides an overview of access control concepts and topics relevant to the CISSP certification. It defines access control as the mechanisms that grant or revoke the right to access data or perform actions on an information system. The document outlines key access control topics like identification, authentication, authorization, accountability, access control models, and monitoring. It also discusses access control principles such as least privilege and separation of duties.
Audit Checklist for Information Systems



Audit Checklist for Information SystemsAhmad Tariq Bhatti IS - Audit Checklist for all companies. The checklist comprehensively covers audit aspects of management information systems.
Ad
Similar to Security testing ? (9)
No, you be the hacker !



No, you be the hacker !Maikel Ninaber The document outlines a plan to teach hacking skills, including an introduction to FristiLeaks 1.3, web application security, web crawling, reverse shells, and limitations of hacking. It discusses the architecture of web applications and important concepts for a workshop, including web crawling, reverse shells, and limitations under computer fraud laws. The document concludes with sources for further information.
Once upon a time... before UX became relevant



Once upon a time... before UX became relevantMichael Van der Gaag User Experience is the result of the evolution of a discipline based on Frederick Taylor’s turn-of-the-20th-century book, The Principles of Scientific Management (1911).
My story tells,
1) How User Experience has evolved as the integration of multiple disciplines
2) How user’s needs and expectations are the keystones of successful projects and products.
3) What we can all do to make UX even better
ION Hangzhou - Keynote: Collaborative Security and an Open Internet



ION Hangzhou - Keynote: Collaborative Security and an Open InternetDeploy360 Programme (Internet Society) 14 July 2016, ION Hangzhou (China). Afternoon Keynote on Collaborative Security and an Open Internet by Internet Society CITO Olaf Kolkman.
Summit 2016 Wrap-up for eVar7



Summit 2016 Wrap-up for eVar7Keisuke Anzai The document appears to be a report from Adobe on their 2016 activities in Japan. However, most of the content is redacted copyright notices. Therefore, the document does not provide any substantive information that can be summarized.
Webinar: A deep dive on phishing, today's #1 business threat



Webinar: A deep dive on phishing, today's #1 business threatCyren, Inc Learn about the anatomy of a phishing site in this slide deck. To view the corresponding on-demand webinar, click here: http://bit.ly/2ii2hZf
Webinar: A deep dive on ransomware



Webinar: A deep dive on ransomwareCyren, Inc Learn about how ransomware works in this slide deck. To view the on-demand webinar in its entirety, click here: http://bit.ly/2jBhYXF
Nrf 2016 - Observations and reflections



Nrf 2016 - Observations and reflectionsCapgemini The document discusses observations and reflections from the NRF 2016 conference. Key topics discussed include personalization and relevancy in customer experiences, the rise of data scientists in retail, and creating frictionless shopping experiences through improved payment and ordering technologies. Trust and security, network collaboration, and the role of mobility and integrated cloud solutions are also covered.
State of NetBeans



State of NetBeansGeertjan Wielenga This document outlines plans for the NetBeans IDE to transition to an open governance model under the Apache foundation. It discusses moving NetBeans from Oracle's proprietary model to a community-driven model where developers from different companies and organizations can contribute code transparently. The new model aims to expand NetBeans' support for newer technologies like Java 9, Android, Gradle, Spring Boot and programming languages including Kotlin, Scala and R. Research projects and education uses are also discussed. The proposal to incubate NetBeans under Apache is currently in the initial stages.
[CB16] Background Story of "Operation neutralizing banking malware" and highl...![[CB16] Background Story of "Operation neutralizing banking malware" and highl...](https://cdn.slidesharecdn.com/ss_thumbnails/cb16takadaen-161109045319-thumbnail.jpg?width=560&fit=bounds)
![[CB16] Background Story of "Operation neutralizing banking malware" and highl...](https://cdn.slidesharecdn.com/ss_thumbnails/cb16takadaen-161109045319-thumbnail.jpg?width=560&fit=bounds)
![[CB16] Background Story of "Operation neutralizing banking malware" and highl...](https://cdn.slidesharecdn.com/ss_thumbnails/cb16takadaen-161109045319-thumbnail.jpg?width=560&fit=bounds)
![[CB16] Background Story of "Operation neutralizing banking malware" and highl...](https://cdn.slidesharecdn.com/ss_thumbnails/cb16takadaen-161109045319-thumbnail.jpg?width=560&fit=bounds)
[CB16] Background Story of "Operation neutralizing banking malware" and highl...CODE BLUE Financial damages caused by remittance fraud in Japan has been increasing since year 2013, and this has become a critical problem in our society.
In April 2015, Tokyo Metropolitan Police Department conducted its very first unique takedown operation called "Operation Banking Malware Takedown”.
Tokyo Metropolitan Police Department had asked us to cooporate with this operation, so we developed a technology that would takedown the banking malware called "VAWTRAK".
In this presentation, I will give an overview of the operation and a background of our involvement.
Then, I will introduce and demonstrate the technology that we developed to takedown “VAWTRAK”.
I will also provide a description of ongoing banking malware attacks this year based on our investigation.
--- Kazuki Takada
He works at SecureBrain Corporation and belongs to Advanced Research Center and Security Response Team. Senior Software Engineer. 2014, He joined SecureBrain Corporation. As a software engineer, he works on the software development while doing security research. Mainly he focused on the analysis of the cyber crimes caused by financial Malware and phishing and its developing its technological countermeasures.
Major lectures in the past
2015/2016 Practical Anti-Phishing Guideline Seminar Lecturer
2016 IEICE requested symposium “Analysis methods and the results from Malware Long-term observation and taint analysis”.
ION Hangzhou - Keynote: Collaborative Security and an Open Internet



ION Hangzhou - Keynote: Collaborative Security and an Open InternetDeploy360 Programme (Internet Society)
Ad
Recently uploaded (19)
APNIC Update, presented at NZNOG 2025 by Terry Sweetser



APNIC Update, presented at NZNOG 2025 by Terry SweetserAPNIC Terry Sweetser, Training Delivery Manager (South Asia & Oceania) at APNIC presented an APNIC update at NZNOG 2025 held in Napier, New Zealand from 9 to 11 April 2025.
Reliable Vancouver Web Hosting with Local Servers & 24/7 Support



Reliable Vancouver Web Hosting with Local Servers & 24/7 Supportsteve198109 Looking for powerful and affordable web hosting in Vancouver? 4GoodHosting offers premium Canadian web hosting solutions designed specifically for individuals, startups, and businesses across British Columbia. With local data centers in Vancouver and Toronto, we ensure blazing-fast website speeds, superior uptime, and enhanced data privacy—all critical for your business success in today’s competitive digital landscape.
Our Vancouver web hosting plans are packed with value—starting as low as $2.95/month—and include secure cPanel management, free domain transfer, one-click WordPress installs, and robust email support with anti-spam protection. Whether you're hosting a personal blog, business website, or eCommerce store, our scalable cloud hosting packages are built to grow with you.
Enjoy enterprise-grade features like daily backups, DDoS protection, free SSL certificates, and unlimited bandwidth on select plans. Plus, our expert Canadian support team is available 24/7 to help you every step of the way.
At 4GoodHosting, we understand the needs of local Vancouver businesses. That’s why we focus on speed, security, and service—all hosted on Canadian soil. Start your online journey today with a reliable hosting partner trusted by thousands across Canada.
Top Vancouver Green Business Ideas for 2025 Powered by 4GoodHosting



Top Vancouver Green Business Ideas for 2025 Powered by 4GoodHostingsteve198109 Vancouver in 2025 is more than scenic views, yoga studios, and oat milk lattes—it’s a thriving hub for eco-conscious entrepreneurs looking to make a real difference. If you’ve ever dreamed of launching a purpose-driven business, now is the time. Whether it’s urban mushroom farming, upcycled furniture sales, or vegan skincare sold online, your green idea deserves a strong digital foundation.
The 2025 Canadian eCommerce landscape is being shaped by trends like sustainability, local innovation, and consumer trust. To stay ahead, eco-startups need reliable hosting that aligns with their values. That’s where 4GoodHosting.com comes in—one of the top-rated Vancouver web hosting providers of 2025. Offering secure, sustainable, and Canadian-based hosting solutions, they help green entrepreneurs build their brand with confidence and conscience.
As eCommerce in Canada embraces localism and environmental responsibility, choosing a hosting provider that shares your vision is essential. 4GoodHosting goes beyond just hosting websites—they champion Canadian businesses, sustainable practices, and meaningful growth.
So go ahead—start that eco-friendly venture. With Vancouver web hosting from 4GoodHosting, your green business and your values are in perfect sync.
DNS Resolvers and Nameservers (in New Zealand)



DNS Resolvers and Nameservers (in New Zealand)APNIC Geoff Huston, Chief Scientist at APNIC, presented on 'DNS Resolvers and Nameservers in New Zealand' at NZNOG 2025 held in Napier, New Zealand from 9 to 11 April 2025.
Perguntas dos animais - Slides ilustrados de múltipla escolha



Perguntas dos animais - Slides ilustrados de múltipla escolhasocaslev Slides ilustrados de múltipla escolha
Understanding the Tor Network and Exploring the Deep Web



Understanding the Tor Network and Exploring the Deep Webnabilajabin35 While the Tor network, Dark Web, and Deep Web can seem mysterious and daunting, they are simply parts of the internet that prioritize privacy and anonymity. Using tools like Ahmia and onionland search, users can explore these hidden spaces responsibly and securely. It’s essential to understand the technology behind these networks, as well as the risks involved, to navigate them safely. Visit https://torgol.com/
Smart Mobile App Pitch Deck丨AI Travel App Presentation Template



Smart Mobile App Pitch Deck丨AI Travel App Presentation Templateyojeari421237 🚀 Smart Mobile App Pitch Deck – "Trip-A" | AI Travel App Presentation Template
This professional, visually engaging pitch deck is designed specifically for developers, startups, and tech students looking to present a smart travel mobile app concept with impact.
Whether you're building an AI-powered travel planner or showcasing a class project, Trip-A gives you the edge to impress investors, professors, or clients. Every slide is cleanly structured, fully editable, and tailored to highlight key aspects of a mobile travel app powered by artificial intelligence and real-time data.
💼 What’s Inside:
- Cover slide with sleek app UI preview
- AI/ML module implementation breakdown
- Key travel market trends analysis
- Competitor comparison slide
- Evaluation challenges & solutions
- Real-time data training model (AI/ML)
- “Live Demo” call-to-action slide
🎨 Why You'll Love It:
- Professional, modern layout with mobile app mockups
- Ideal for pitches, hackathons, university presentations, or MVP launches
- Easily customizable in PowerPoint or Google Slides
- High-resolution visuals and smooth gradients
📦 Format:
- PPTX / Google Slides compatible
- 16:9 widescreen
- Fully editable text, charts, and visuals
Mobile database for your company telemarketing or sms marketing campaigns. Fr...



Mobile database for your company telemarketing or sms marketing campaigns. Fr...DataProvider1 Why Mobile Database Services are Important: Powering the Future of Mobile Applications
Best web hosting Vancouver 2025 for you business



Best web hosting Vancouver 2025 for you businesssteve198109 Vancouver in 2025 is more than scenic views, yoga studios, and oat milk lattes—it’s a thriving hub for eco-conscious entrepreneurs looking to make a real difference. If you’ve ever dreamed of launching a purpose-driven business, now is the time. Whether it’s urban mushroom farming, upcycled furniture sales, or vegan skincare sold online, your green idea deserves a strong digital foundation.
The 2025 Canadian eCommerce landscape is being shaped by trends like sustainability, local innovation, and consumer trust. To stay ahead, eco-startups need reliable hosting that aligns with their values. That’s where 4GoodHosting.com comes in—one of the top-rated Vancouver web hosting providers of 2025. Offering secure, sustainable, and Canadian-based hosting solutions, they help green entrepreneurs build their brand with confidence and conscience.
As eCommerce in Canada embraces localism and environmental responsibility, choosing a hosting provider that shares your vision is essential. 4GoodHosting goes beyond just hosting websites—they champion Canadian businesses, sustainable practices, and meaningful growth.
So go ahead—start that eco-friendly venture. With Vancouver web hosting from 4GoodHosting, your green business and your values are in perfect sync.
APNIC -Policy Development Process, presented at Local APIGA Taiwan 2025



APNIC -Policy Development Process, presented at Local APIGA Taiwan 2025APNIC Joyce Chen, Senior Advisor, Strategic Engagement at APNIC, presented on 'APNIC Policy Development Process' at the Local APIGA Taiwan 2025 event held in Taipei from 19 to 20 April 2025.
IT Services Workflow From Request to Resolution



IT Services Workflow From Request to Resolutionmzmziiskd IT Services Workflow From Request to Resolution
highend-srxseries-services-gateways-customer-presentation.pptx



highend-srxseries-services-gateways-customer-presentation.pptxelhadjcheikhdiop Juniper High End Series
Security testing ?
- 1. Maikel Ninaber 19/04/2016 How serious is Web Apps Security Testing ?
- 2. 2Copyright © 2016 Maikel Ninaber. All Rights Reserved Security testing | May 2016 Known facts
- 3. 3Copyright © 2016 Maikel Ninaber. All Rights Reserved Security testing | May 2016 Known facts
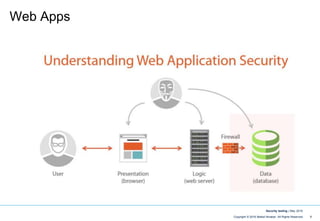
- 4. 4Copyright © 2016 Maikel Ninaber. All Rights Reserved Security testing | May 2016 Web Apps
- 5. 5Copyright © 2016 Maikel Ninaber. All Rights Reserved Security testing | May 2016 Web Apps
- 6. 6Copyright © 2016 Maikel Ninaber. All Rights Reserved Security testing | May 2016 Web Apps
- 7. 7Copyright © 2016 Maikel Ninaber. All Rights Reserved Security testing | May 2016 Web Apps
- 8. 8Copyright © 2016 Maikel Ninaber. All Rights Reserved Security testing | May 2016 Web Apps
- 9. 9Copyright © 2016 Maikel Ninaber. All Rights Reserved Security testing | May 2016 Web Apps
- 10. 10Copyright © 2016 Maikel Ninaber. All Rights Reserved Security testing | May 2016 Web Apps
- 11. 11Copyright © 2016 Maikel Ninaber. All Rights Reserved Security testing | May 2016 Query strings
- 12. 12Copyright © 2016 Maikel Ninaber. All Rights Reserved Security testing | May 2016 Query strings
- 13. 13Copyright © 2016 Maikel Ninaber. All Rights Reserved Security testing | May 2016 Query strings
- 14. 14Copyright © 2016 Maikel Ninaber. All Rights Reserved Security testing | May 2016 Query strings
- 15. 15Copyright © 2016 Maikel Ninaber. All Rights Reserved Security testing | May 2016 Routing
- 16. 16Copyright © 2016 Maikel Ninaber. All Rights Reserved Security testing | May 2016 Routing
- 17. 17Copyright © 2016 Maikel Ninaber. All Rights Reserved Security testing | May 2016 Routing
- 18. 18Copyright © 2016 Maikel Ninaber. All Rights Reserved Security testing | May 2016 HTTP verbs
- 19. 19Copyright © 2016 Maikel Ninaber. All Rights Reserved Security testing | May 2016 HTTP verbs
- 20. 20Copyright © 2016 Maikel Ninaber. All Rights Reserved Security testing | May 2016 HTTP verbs
- 21. 21Copyright © 2016 Maikel Ninaber. All Rights Reserved Security testing | May 2016 HTTP verbs
- 22. 22Copyright © 2016 Maikel Ninaber. All Rights Reserved Security testing | May 2016 Browser protection
- 23. 23Copyright © 2016 Maikel Ninaber. All Rights Reserved Security testing | May 2016 Browser protection
- 24. 24Copyright © 2016 Maikel Ninaber. All Rights Reserved Security testing | May 2016 Browser protection
- 25. 25Copyright © 2016 Maikel Ninaber. All Rights Reserved Security testing | May 2016 Browser protection
- 26. 26Copyright © 2016 Maikel Ninaber. All Rights Reserved Security testing | May 2016 What the browser can’t defend against
- 27. 27Copyright © 2016 Maikel Ninaber. All Rights Reserved Security testing | May 2016 What the browser can’t defend against
- 28. 28Copyright © 2016 Maikel Ninaber. All Rights Reserved Security testing | May 2016 What the browser can’t defend against
- 29. 29Copyright © 2016 Maikel Ninaber. All Rights Reserved Security testing | May 2016 OWASP top 10
- 30. 30Copyright © 2016 Maikel Ninaber. All Rights Reserved Security testing | May 2016 No SQL injection today
- 31. 31Copyright © 2016 Maikel Ninaber. All Rights Reserved Security testing | May 2016 Understanding Untrusted Data
- 32. 32Copyright © 2016 Maikel Ninaber. All Rights Reserved Security testing | May 2016 Understanding Untrusted Data
- 33. 33Copyright © 2016 Maikel Ninaber. All Rights Reserved Security testing | May 2016 Understanding Untrusted Data
- 34. 34Copyright © 2016 Maikel Ninaber. All Rights Reserved Security testing | May 2016 Understanding Untrusted Data
- 35. 35Copyright © 2016 Maikel Ninaber. All Rights Reserved Security testing | May 2016 Understanding Untrusted Data
- 36. 36Copyright © 2016 Maikel Ninaber. All Rights Reserved Security testing | May 2016 Understanding Untrusted Data
- 37. 37Copyright © 2016 Maikel Ninaber. All Rights Reserved Security testing | May 2016 Understanding Untrusted Data
- 38. 38Copyright © 2016 Maikel Ninaber. All Rights Reserved Security testing | May 2016 Demo
- 39. 39Copyright © 2016 Maikel Ninaber. All Rights Reserved Security testing | May 2016 Defending Against Tampering
- 40. 40Copyright © 2016 Maikel Ninaber. All Rights Reserved Security testing | May 2016 Defending Against Tampering
- 41. 41Copyright © 2016 Maikel Ninaber. All Rights Reserved Security testing | May 2016 Defending Against Tampering
- 42. 42Copyright © 2016 Maikel Ninaber. All Rights Reserved Security testing | May 2016 Defending Against Tampering
- 43. 43Copyright © 2016 Maikel Ninaber. All Rights Reserved Security testing | May 2016 Where to practice
- 44. 44Copyright © 2016 Maikel Ninaber. All Rights Reserved Security testing | May 2016 Limitations Computer Fraud and Abuse Act • Using a computer to intrude upon or steal something from another computer is illegal Unintended consequences, such as damaging hijacked computers belonging to innocent individuals, while real criminals remain hidden several layers back on the Internet (e.g., TOR) The only kind of hacking that's considered tolerable is what you might enact defensively within your own computer or network. What’s clearly illegal are offensive hacks, where you leave your territory and actively pursue an assailant online.
- 45. 45Copyright © 2016 Maikel Ninaber. All Rights Reserved Security testing | May 2016 Another Hacker goes to jail !
- 46. 46Copyright © 2016 Maikel Ninaber. All Rights Reserved Security testing | May 2016 Sources http://www.telerik.com/fiddler https://www.troyhunt.com/ https://www.owasp.org/index.php/Web_Application_Security_Testing_Cheat_Sh eet https://www.owasp.org/index.php/Category:OWASP_WebGoat_Project http://www.dvwa.co.uk/ https://hackyourselffirst.troyhunt.com/ https://nl.linkedin.com/in/maikelninaber http://cookiecontroller.com/internet-cookies/secure-cookies/ http://stackoverflow.com/questions/1442863/how-can-i-set-the-secure-flag-on- an-asp-net-session-cookie






