Single Sign On Across Drupal 8 - DrupalCon Global 2020
0 likes90 views
In today’s digitally-driven world, connecting multiple systems is a must for any organization. As organizations use different systems, websites and much more, a single authentication mechanism is highly beneficial.
1 of 30
Download to read offline





























Ad
Recommended
Single sign on across drupal 8



Single sign on across drupal 8Iwantha Lekamge Single Sign-On (SSO) is a user authentication service that permits a user to use one set of login credentials (for example, their name and password) to access multiple systems.
Configuring Outbound SSL connection to invoke secured REST



Configuring Outbound SSL connection to invoke secured RESTPradeep Mishra This document outlines the steps to configure an Oracle SOA 12c environment to invoke SSL-secured REST/SOAP web services. It describes verifying the keystore configuration in WebLogic Server, importing SSL certificates into the Oracle keystore, and concluding that following these steps will allow the SOA environment to make SSL calls to exposed web services.
Ossec Lightning



Ossec Lightningwremes A lightning talk prepared for www.brucon.org on the open source host-based intrusion detection system OSSEC (http://www.ossec.net)
Habilitar auditoria no office 365 por usuario



Habilitar auditoria no office 365 por usuarioAndré Luiz Cunha This document describes how to enable auditing for a user in Office 365. It involves running the Windows Azure Active Directory PowerShell module as an administrator, authenticating with Office 365 admin credentials, and using the Set-Mailbox cmdlet to set the AuditEnabled property to true for a specific user's mailbox. This will enable auditing to track actions performed in that user's Office 365 mailbox.
Visual Programming Framework for Unity - UniFlow のご紹介



Visual Programming Framework for Unity - UniFlow のご紹介Mori Tetsuya This document contains code snippets and configuration files related to Unity packages and message handling in a messaging system. It includes a JSON file listing dependencies and scoped package registries, code for connecting a message handler and annotating messages as composable or collectable, and release information for a messaging library called UniFlow.
Architecting Secure and Compliant Applications with MongoDB 



Architecting Secure and Compliant Applications with MongoDB MongoDB High profile security breaches have become embarrassingly common, but ultimately avoidable. Now more than ever, database security is a critical component of any production application. In this talk we'll learn to secure your deployment in accordance with best practices and compliance regulations. We'll explore the MongoDB Enterprise features which ensure HIPAA and PCI compliance, and protect you against attack, data exposure and a damaged reputation.
Open source wso2 identity server sso with drupal 8



Open source wso2 identity server sso with drupal 8Iwantha Lekamge Single sign-on is important for government agencies to maintain a single authentication mechanism among their systems. Open Source WSO2 Identity Server can connect with Drupal 8 and create an SSO environment for government agencies.
Configuration Management Tools on NX-OS



Configuration Management Tools on NX-OSCisco DevNet A session in the DevNet Zone at Cisco Live, Berlin. On Cisco Nexus devices, configuration is performed using command-line interfaces (CLIs) that run only on the device. Configuration Management Tools allow you to automate the network devices configuration in the same way sysadmin have automated the server configuration. These tools include Puppet, Chef and Ansible. We will be introducing the concept of each of them, agent vs agent-less and demoing some use cases.
We will also describe some of the technology enablers like NX-API REST that allows you to enable configurations that would require issuing many CLI commands by combining configuration actions in relatively few HTTP/HTTPS operations."
Expanding your impact with programmability in the data center



Expanding your impact with programmability in the data centerCisco Canada 1) Digital readiness involves embracing automation, operational simplicity through programmability, network disaggregation, and DevOps to drive speed and agility.
2) Programmability allows for more flexibility, innovation, speed, repeatability and fewer mistakes by enabling automated workflows, off-box management via controllers and APIs, and SDKs for application development.
3) Adopting programmability means network operations will need to understand concepts like REST, XML, JSON, and work with developers to automate tasks and integrate the network.
Što danas zamjenjuje Small Business Server?



Što danas zamjenjuje Small Business Server?Tomislav Lulic Jos uvijek je dosta nezadovoljnih zbog nestanka Small Business Servera. No, da li stvarno moraju biti nezadovoljni? Prebacivanjem vecine servisa u Cloud uz pomoc Office 365 korisnik dobiva puno više nego je prije imao. Kroz demo pokazati koji su servisi poboljšani, koje promjene u poslovanju mogu korisnici (u SMB segementu) očekivati. Kroz demo pokazati kako Windows Server 2012 R2 Essential i Office 365 mogu pružiti Enterprise mogućnosti manjim tvrtkama koje nemaju zaposlene IT stručnjake.
Under the Hood 11g Identity Management



Under the Hood 11g Identity ManagementInSync Conference Oracle Identity Management presentation for 2010 Conference presented by Peter McLarty, looks at installation issues, planning and design, overall view of 11g Identity Management, more detailed look at installation and configuration of the Oracle Internet Directory.
11g Identity Management - InSync10



11g Identity Management - InSync10Peter McLarty Presentation on Oracle Identity Management from Insync10 conference in Melbourne August 2010. Looks at OID and some of the potential issues around installation and configuration
Moodle + Adobe Connect 



Moodle + Adobe Connect Takeshi Matsuzaki This document provides instructions for installing and configuring Adobe Connect and integrating it with Moodle. It discusses installing Adobe Connect on-premises or using the SaaS version. It then covers configuring settings in Connect and Moodle to enable single sign-on between the two systems. Troubleshooting tips are also provided for issues with multi-byte user/meeting names and possible bugs. Lastly, using multiple IP addresses with Connect on Amazon EC2 is discussed.
Being HAPI! Reverse Proxying on Purpose



Being HAPI! Reverse Proxying on PurposeAman Kohli Node is used to build a reverse proxy to provide secure access to internal web resources and sites for mobile clients within a large enterprise. Performance testing shows the proxy can handle over 1000 requests per second with latency under 1 second. Code quality analysis tools like Plato and testing frameworks like Jest are useful for maintaining high quality code. Scalability is achieved through auto-scaling virtual machine instances with a load balancer and configuration management.
PSU Security Conference 2015 - LAPS Presentation



PSU Security Conference 2015 - LAPS PresentationDan Barr This document discusses the Local Administrator Password Solution (LAPS) created by Microsoft to securely manage unique local administrator passwords on systems. LAPS uses Active Directory and Group Policy to randomly generate and centrally store administrator passwords, reducing the risk of password sharing attacks. It extends the AD schema, uses a client-side DLL to generate and reset passwords periodically based on Group Policy, and provides tools to configure and manage passwords. LAPS aims to mitigate pass-the-hash attacks while maintaining a simple implementation without additional infrastructure requirements.
Booting Weblogic - OOW14



Booting Weblogic - OOW14Jon Petter Hjulstad This document provides an overview of booting Oracle WebLogic server instances. It discusses the key components involved, including Node Manager and WebLogic Scripting Tool (WLST). It recommends using Node Manager to start the Administration Server and WLST to start managed servers. Sample scripts are provided to start all servers using this approach. The document also covers encrypting credentials, configuring Node Manager as a Windows service, and other tips.
Enterprise Node - Securing Your Environment



Enterprise Node - Securing Your EnvironmentKurtis Kemple This document discusses securing an enterprise Node.js environment. It recommends using Node LTS versions for stability, containerizing applications for isolation, and securing dependencies by whitelisting modules. It also covers authenticating users with JWT, authorizing access with scopes and roles, validating input data, encrypting sensitive data, and ensuring HTTPS is used everywhere. Securing the runtime is important to protect the company from threats, improve confidence, and meet regulations.
Building and Managing your Virtual Datacenter using PowerShell DSC - Florin L...



Building and Managing your Virtual Datacenter using PowerShell DSC - Florin L...ITCamp PowerShell DSC is a configuration management platform that provides the operations team the capability to deploy and manage systems by defining the desired configuration of a machine while having the assurance that whatever happens, the machines configuration will remain the same.
In this session you will learn what is PowerShell DSC, and how it can grant you the power of implementing a DevOps oriented environment by building and managing your infrastructure in an automatic and consistent fashion.
0505 Windows Server 2008 一日精華營 PartI



0505 Windows Server 2008 一日精華營 PartITimothy Chen This document provides an overview of server management in Windows Server 2008, including primary management tools, initial configuration tasks, alternative management tools, and technical background information. It discusses tools like Server Manager Console, Windows PowerShell, and Remote Management. It also covers managing Server Core installations, centralized application access with Terminal Services, and using a Terminal Services Gateway.
OpenIDM: An Introduction



OpenIDM: An IntroductionForgeRock This document summarizes a presentation about OpenIDM. It describes where OpenIDM fits into Open Identity Stack (OIS), common identity management use cases like provisioning and password management that OpenIDM addresses, and OpenIDM features like its REST interface, connectors to external systems, and use of workflows. The architecture of OpenIDM is also summarized, including its components like OSGi, persistence layer, and connectors. Configuration of connectors and potential role management challenges are also briefly outlined.
CertsOut Checkpoint-156-587 exam dumps pdf



CertsOut Checkpoint-156-587 exam dumps pdfDumpcollection CertsOut Checkpoint-156-587
https://www.certsout.com/156-587-test.html
Keycloak SSO basics



Keycloak SSO basicsJuan Vicente Herrera Ruiz de Alejo Red Hat Single Sign-On (RH-SSO) is an identity and access management product based on the open source Keycloak project. The document provides an overview of RH-SSO, including its architecture, core concepts such as authentication, authorization, tokens, and security considerations for deployment. It also discusses clustering, user federation, and identity brokering capabilities.
Securing Your Enterprise Web Apps with MongoDB Enterprise 



Securing Your Enterprise Web Apps with MongoDB Enterprise MongoDB Speaker: Jay Runkel, Principal Solution Architect, MongoDB
Level: 200 (Intermediate)
Track: Operations
When architecting a MongoDB application, one of the most difficult questions to answer is how much hardware (number of shards, number of replicas, and server specifications) am I going to need for an application. Similarly, when deploying in the cloud, how do you estimate your monthly AWS, Azure, or GCP costs given a description of a new application? While there isn’t a precise formula for mapping application features (e.g., document structure, schema, query volumes) into servers, there are various strategies you can use to estimate the MongoDB cluster sizing. This presentation will cover the questions you need to ask and describe how to use this information to estimate the required cluster size or cloud deployment cost.
What You Will Learn:
- How to architect a sharded cluster that provides the required computing resources while minimizing hardware or cloud computing costs
- How to use this information to estimate the overall cluster requirements for IOPS, RAM, cores, disk space, etc.
- What you need to know about the application to estimate a cluster size
[OW2con'21] Hosting Identity in the Cloud with OW2 free softwares![[OW2con'21] Hosting Identity in the Cloud with OW2 free softwares](https://cdn.slidesharecdn.com/ss_thumbnails/ow2con21identitycloud-210623143630-thumbnail.jpg?width=560&fit=bounds)
![[OW2con'21] Hosting Identity in the Cloud with OW2 free softwares](https://cdn.slidesharecdn.com/ss_thumbnails/ow2con21identitycloud-210623143630-thumbnail.jpg?width=560&fit=bounds)
![[OW2con'21] Hosting Identity in the Cloud with OW2 free softwares](https://cdn.slidesharecdn.com/ss_thumbnails/ow2con21identitycloud-210623143630-thumbnail.jpg?width=560&fit=bounds)
![[OW2con'21] Hosting Identity in the Cloud with OW2 free softwares](https://cdn.slidesharecdn.com/ss_thumbnails/ow2con21identitycloud-210623143630-thumbnail.jpg?width=560&fit=bounds)
[OW2con'21] Hosting Identity in the Cloud with OW2 free softwaresWorteks Some notes about Identity and Access Management and how create your IDaaS (Identity as a Service) with free softwares
Service Management Dec 11



Service Management Dec 11clarendonint This is a London Windows Azure Group Presentation for December 11 on the Windows Azure Service Management API
Service management Dec 11



Service management Dec 11Richard Conway The document discusses the Azure Service Management API which allows users to manage Azure services through a RESTful API. It can be used to perform CRUD operations on hosted services, storage accounts, and other Azure resources. The API uses HTTP verbs like GET, PUT, POST, and DELETE and requires an authentication certificate. Tools like Powershell, the management portal, and third party tools can also be used to manage Azure services by interacting with the Service Management API in the background.
Autonomous Transaction Processing (ATP): In Heavy Traffic, Why Drive Stick?



Autonomous Transaction Processing (ATP): In Heavy Traffic, Why Drive Stick?Jim Czuprynski Autonomous Transaction Processing (ATP) - the second in the family of Oracle’s Autonomous Databases – offers Oracle DBAs the ability to apply a force multiplier for their OLTP database application workloads. However, it’s important to understand both the benefits and limitations of ATP before migrating any workloads to that environment. I'll offer a quick but deep dive into how best to take advantage of ATP - including how to load data quickly into the underlying database – and some ideas on how ATP will impact the role of Oracle DBA in the immediate future. (Hint: Think automatic transmission instead of stick-shift.)
Cloud api之應用與實例



Cloud api之應用與實例Simon Su CloudAPI allows users to provision and manage machines as well as perform cloud analysis. It provides APIs, SDKs, and CLIs to create, list, start, stop and delete machines. Users can choose from public datasets and packages to specify machine configurations. CloudAPI also offers instruments and decomposition to monitor infrastructure and obtain metrics for individual machines or zones. Dtrace and JSON tools help further analyze collected data.
Special Meetup Edition - TDX Bengaluru Meetup #52.pptx



Special Meetup Edition - TDX Bengaluru Meetup #52.pptxshyamraj55 We’re bringing the TDX energy to our community with 2 power-packed sessions:
🛠️ Workshop: MuleSoft for Agentforce
Explore the new version of our hands-on workshop featuring the latest Topic Center and API Catalog updates.
📄 Talk: Power Up Document Processing
Dive into smart automation with MuleSoft IDP, NLP, and Einstein AI for intelligent document workflows.
Semantic Cultivators : The Critical Future Role to Enable AI



Semantic Cultivators : The Critical Future Role to Enable AIartmondano By 2026, AI agents will consume 10x more enterprise data than humans, but with none of the contextual understanding that prevents catastrophic misinterpretations.
Ad
More Related Content
Similar to Single Sign On Across Drupal 8 - DrupalCon Global 2020 (20)
Expanding your impact with programmability in the data center



Expanding your impact with programmability in the data centerCisco Canada 1) Digital readiness involves embracing automation, operational simplicity through programmability, network disaggregation, and DevOps to drive speed and agility.
2) Programmability allows for more flexibility, innovation, speed, repeatability and fewer mistakes by enabling automated workflows, off-box management via controllers and APIs, and SDKs for application development.
3) Adopting programmability means network operations will need to understand concepts like REST, XML, JSON, and work with developers to automate tasks and integrate the network.
Što danas zamjenjuje Small Business Server?



Što danas zamjenjuje Small Business Server?Tomislav Lulic Jos uvijek je dosta nezadovoljnih zbog nestanka Small Business Servera. No, da li stvarno moraju biti nezadovoljni? Prebacivanjem vecine servisa u Cloud uz pomoc Office 365 korisnik dobiva puno više nego je prije imao. Kroz demo pokazati koji su servisi poboljšani, koje promjene u poslovanju mogu korisnici (u SMB segementu) očekivati. Kroz demo pokazati kako Windows Server 2012 R2 Essential i Office 365 mogu pružiti Enterprise mogućnosti manjim tvrtkama koje nemaju zaposlene IT stručnjake.
Under the Hood 11g Identity Management



Under the Hood 11g Identity ManagementInSync Conference Oracle Identity Management presentation for 2010 Conference presented by Peter McLarty, looks at installation issues, planning and design, overall view of 11g Identity Management, more detailed look at installation and configuration of the Oracle Internet Directory.
11g Identity Management - InSync10



11g Identity Management - InSync10Peter McLarty Presentation on Oracle Identity Management from Insync10 conference in Melbourne August 2010. Looks at OID and some of the potential issues around installation and configuration
Moodle + Adobe Connect 



Moodle + Adobe Connect Takeshi Matsuzaki This document provides instructions for installing and configuring Adobe Connect and integrating it with Moodle. It discusses installing Adobe Connect on-premises or using the SaaS version. It then covers configuring settings in Connect and Moodle to enable single sign-on between the two systems. Troubleshooting tips are also provided for issues with multi-byte user/meeting names and possible bugs. Lastly, using multiple IP addresses with Connect on Amazon EC2 is discussed.
Being HAPI! Reverse Proxying on Purpose



Being HAPI! Reverse Proxying on PurposeAman Kohli Node is used to build a reverse proxy to provide secure access to internal web resources and sites for mobile clients within a large enterprise. Performance testing shows the proxy can handle over 1000 requests per second with latency under 1 second. Code quality analysis tools like Plato and testing frameworks like Jest are useful for maintaining high quality code. Scalability is achieved through auto-scaling virtual machine instances with a load balancer and configuration management.
PSU Security Conference 2015 - LAPS Presentation



PSU Security Conference 2015 - LAPS PresentationDan Barr This document discusses the Local Administrator Password Solution (LAPS) created by Microsoft to securely manage unique local administrator passwords on systems. LAPS uses Active Directory and Group Policy to randomly generate and centrally store administrator passwords, reducing the risk of password sharing attacks. It extends the AD schema, uses a client-side DLL to generate and reset passwords periodically based on Group Policy, and provides tools to configure and manage passwords. LAPS aims to mitigate pass-the-hash attacks while maintaining a simple implementation without additional infrastructure requirements.
Booting Weblogic - OOW14



Booting Weblogic - OOW14Jon Petter Hjulstad This document provides an overview of booting Oracle WebLogic server instances. It discusses the key components involved, including Node Manager and WebLogic Scripting Tool (WLST). It recommends using Node Manager to start the Administration Server and WLST to start managed servers. Sample scripts are provided to start all servers using this approach. The document also covers encrypting credentials, configuring Node Manager as a Windows service, and other tips.
Enterprise Node - Securing Your Environment



Enterprise Node - Securing Your EnvironmentKurtis Kemple This document discusses securing an enterprise Node.js environment. It recommends using Node LTS versions for stability, containerizing applications for isolation, and securing dependencies by whitelisting modules. It also covers authenticating users with JWT, authorizing access with scopes and roles, validating input data, encrypting sensitive data, and ensuring HTTPS is used everywhere. Securing the runtime is important to protect the company from threats, improve confidence, and meet regulations.
Building and Managing your Virtual Datacenter using PowerShell DSC - Florin L...



Building and Managing your Virtual Datacenter using PowerShell DSC - Florin L...ITCamp PowerShell DSC is a configuration management platform that provides the operations team the capability to deploy and manage systems by defining the desired configuration of a machine while having the assurance that whatever happens, the machines configuration will remain the same.
In this session you will learn what is PowerShell DSC, and how it can grant you the power of implementing a DevOps oriented environment by building and managing your infrastructure in an automatic and consistent fashion.
0505 Windows Server 2008 一日精華營 PartI



0505 Windows Server 2008 一日精華營 PartITimothy Chen This document provides an overview of server management in Windows Server 2008, including primary management tools, initial configuration tasks, alternative management tools, and technical background information. It discusses tools like Server Manager Console, Windows PowerShell, and Remote Management. It also covers managing Server Core installations, centralized application access with Terminal Services, and using a Terminal Services Gateway.
OpenIDM: An Introduction



OpenIDM: An IntroductionForgeRock This document summarizes a presentation about OpenIDM. It describes where OpenIDM fits into Open Identity Stack (OIS), common identity management use cases like provisioning and password management that OpenIDM addresses, and OpenIDM features like its REST interface, connectors to external systems, and use of workflows. The architecture of OpenIDM is also summarized, including its components like OSGi, persistence layer, and connectors. Configuration of connectors and potential role management challenges are also briefly outlined.
CertsOut Checkpoint-156-587 exam dumps pdf



CertsOut Checkpoint-156-587 exam dumps pdfDumpcollection CertsOut Checkpoint-156-587
https://www.certsout.com/156-587-test.html
Keycloak SSO basics



Keycloak SSO basicsJuan Vicente Herrera Ruiz de Alejo Red Hat Single Sign-On (RH-SSO) is an identity and access management product based on the open source Keycloak project. The document provides an overview of RH-SSO, including its architecture, core concepts such as authentication, authorization, tokens, and security considerations for deployment. It also discusses clustering, user federation, and identity brokering capabilities.
Securing Your Enterprise Web Apps with MongoDB Enterprise 



Securing Your Enterprise Web Apps with MongoDB Enterprise MongoDB Speaker: Jay Runkel, Principal Solution Architect, MongoDB
Level: 200 (Intermediate)
Track: Operations
When architecting a MongoDB application, one of the most difficult questions to answer is how much hardware (number of shards, number of replicas, and server specifications) am I going to need for an application. Similarly, when deploying in the cloud, how do you estimate your monthly AWS, Azure, or GCP costs given a description of a new application? While there isn’t a precise formula for mapping application features (e.g., document structure, schema, query volumes) into servers, there are various strategies you can use to estimate the MongoDB cluster sizing. This presentation will cover the questions you need to ask and describe how to use this information to estimate the required cluster size or cloud deployment cost.
What You Will Learn:
- How to architect a sharded cluster that provides the required computing resources while minimizing hardware or cloud computing costs
- How to use this information to estimate the overall cluster requirements for IOPS, RAM, cores, disk space, etc.
- What you need to know about the application to estimate a cluster size
[OW2con'21] Hosting Identity in the Cloud with OW2 free softwares![[OW2con'21] Hosting Identity in the Cloud with OW2 free softwares](https://cdn.slidesharecdn.com/ss_thumbnails/ow2con21identitycloud-210623143630-thumbnail.jpg?width=560&fit=bounds)
![[OW2con'21] Hosting Identity in the Cloud with OW2 free softwares](https://cdn.slidesharecdn.com/ss_thumbnails/ow2con21identitycloud-210623143630-thumbnail.jpg?width=560&fit=bounds)
![[OW2con'21] Hosting Identity in the Cloud with OW2 free softwares](https://cdn.slidesharecdn.com/ss_thumbnails/ow2con21identitycloud-210623143630-thumbnail.jpg?width=560&fit=bounds)
![[OW2con'21] Hosting Identity in the Cloud with OW2 free softwares](https://cdn.slidesharecdn.com/ss_thumbnails/ow2con21identitycloud-210623143630-thumbnail.jpg?width=560&fit=bounds)
[OW2con'21] Hosting Identity in the Cloud with OW2 free softwaresWorteks Some notes about Identity and Access Management and how create your IDaaS (Identity as a Service) with free softwares
Service Management Dec 11



Service Management Dec 11clarendonint This is a London Windows Azure Group Presentation for December 11 on the Windows Azure Service Management API
Service management Dec 11



Service management Dec 11Richard Conway The document discusses the Azure Service Management API which allows users to manage Azure services through a RESTful API. It can be used to perform CRUD operations on hosted services, storage accounts, and other Azure resources. The API uses HTTP verbs like GET, PUT, POST, and DELETE and requires an authentication certificate. Tools like Powershell, the management portal, and third party tools can also be used to manage Azure services by interacting with the Service Management API in the background.
Autonomous Transaction Processing (ATP): In Heavy Traffic, Why Drive Stick?



Autonomous Transaction Processing (ATP): In Heavy Traffic, Why Drive Stick?Jim Czuprynski Autonomous Transaction Processing (ATP) - the second in the family of Oracle’s Autonomous Databases – offers Oracle DBAs the ability to apply a force multiplier for their OLTP database application workloads. However, it’s important to understand both the benefits and limitations of ATP before migrating any workloads to that environment. I'll offer a quick but deep dive into how best to take advantage of ATP - including how to load data quickly into the underlying database – and some ideas on how ATP will impact the role of Oracle DBA in the immediate future. (Hint: Think automatic transmission instead of stick-shift.)
Cloud api之應用與實例



Cloud api之應用與實例Simon Su CloudAPI allows users to provision and manage machines as well as perform cloud analysis. It provides APIs, SDKs, and CLIs to create, list, start, stop and delete machines. Users can choose from public datasets and packages to specify machine configurations. CloudAPI also offers instruments and decomposition to monitor infrastructure and obtain metrics for individual machines or zones. Dtrace and JSON tools help further analyze collected data.
Recently uploaded (20)
Special Meetup Edition - TDX Bengaluru Meetup #52.pptx



Special Meetup Edition - TDX Bengaluru Meetup #52.pptxshyamraj55 We’re bringing the TDX energy to our community with 2 power-packed sessions:
🛠️ Workshop: MuleSoft for Agentforce
Explore the new version of our hands-on workshop featuring the latest Topic Center and API Catalog updates.
📄 Talk: Power Up Document Processing
Dive into smart automation with MuleSoft IDP, NLP, and Einstein AI for intelligent document workflows.
Semantic Cultivators : The Critical Future Role to Enable AI



Semantic Cultivators : The Critical Future Role to Enable AIartmondano By 2026, AI agents will consume 10x more enterprise data than humans, but with none of the contextual understanding that prevents catastrophic misinterpretations.
AI and Data Privacy in 2025: Global Trends



AI and Data Privacy in 2025: Global TrendsInData Labs In this infographic, we explore how businesses can implement effective governance frameworks to address AI data privacy. Understanding it is crucial for developing effective strategies that ensure compliance, safeguard customer trust, and leverage AI responsibly. Equip yourself with insights that can drive informed decision-making and position your organization for success in the future of data privacy.
This infographic contains:
-AI and data privacy: Key findings
-Statistics on AI data privacy in the today’s world
-Tips on how to overcome data privacy challenges
-Benefits of AI data security investments.
Keep up-to-date on how AI is reshaping privacy standards and what this entails for both individuals and organizations.
Complete Guide to Advanced Logistics Management Software in Riyadh.pdf



Complete Guide to Advanced Logistics Management Software in Riyadh.pdfSoftware Company Explore the benefits and features of advanced logistics management software for businesses in Riyadh. This guide delves into the latest technologies, from real-time tracking and route optimization to warehouse management and inventory control, helping businesses streamline their logistics operations and reduce costs. Learn how implementing the right software solution can enhance efficiency, improve customer satisfaction, and provide a competitive edge in the growing logistics sector of Riyadh.
Transcript: #StandardsGoals for 2025: Standards & certification roundup - Tec...



Transcript: #StandardsGoals for 2025: Standards & certification roundup - Tec...BookNet Canada Book industry standards are evolving rapidly. In the first part of this session, we’ll share an overview of key developments from 2024 and the early months of 2025. Then, BookNet’s resident standards expert, Tom Richardson, and CEO, Lauren Stewart, have a forward-looking conversation about what’s next.
Link to recording, presentation slides, and accompanying resource: https://bnctechforum.ca/sessions/standardsgoals-for-2025-standards-certification-roundup/
Presented by BookNet Canada on May 6, 2025 with support from the Department of Canadian Heritage.
tecnologias de las primeras civilizaciones.pdf



tecnologias de las primeras civilizaciones.pdffjgm517 descaripcion detallada del avance de las tecnologias en mesopotamia, egipto, roma y grecia.
Role of Data Annotation Services in AI-Powered Manufacturing



Role of Data Annotation Services in AI-Powered ManufacturingAndrew Leo From predictive maintenance to robotic automation, AI is driving the future of manufacturing. But without high-quality annotated data, even the smartest models fall short.
Discover how data annotation services are powering accuracy, safety, and efficiency in AI-driven manufacturing systems.
Precision in data labeling = Precision on the production floor.
Drupalcamp Finland – Measuring Front-end Energy Consumption



Drupalcamp Finland – Measuring Front-end Energy ConsumptionExove How to measure web front-end energy consumption using Firefox Profiler. Presented in DrupalCamp Finland on April 25th, 2025.
#StandardsGoals for 2025: Standards & certification roundup - Tech Forum 2025



#StandardsGoals for 2025: Standards & certification roundup - Tech Forum 2025BookNet Canada Book industry standards are evolving rapidly. In the first part of this session, we’ll share an overview of key developments from 2024 and the early months of 2025. Then, BookNet’s resident standards expert, Tom Richardson, and CEO, Lauren Stewart, have a forward-looking conversation about what’s next.
Link to recording, transcript, and accompanying resource: https://bnctechforum.ca/sessions/standardsgoals-for-2025-standards-certification-roundup/
Presented by BookNet Canada on May 6, 2025 with support from the Department of Canadian Heritage.
Cyber Awareness overview for 2025 month of security



Cyber Awareness overview for 2025 month of securityriccardosl1 Cyber awareness training educates employees on risk associated with internet and malicious emails
Manifest Pre-Seed Update | A Humanoid OEM Deeptech In France



Manifest Pre-Seed Update | A Humanoid OEM Deeptech In Francechb3 The latest updates on Manifest's pre-seed stage progress.
Cybersecurity Identity and Access Solutions using Azure AD



Cybersecurity Identity and Access Solutions using Azure ADVICTOR MAESTRE RAMIREZ Cybersecurity Identity and Access Solutions using Azure AD
How analogue intelligence complements AI



How analogue intelligence complements AIPaul Rowe
Artificial Intelligence is providing benefits in many areas of work within the heritage sector, from image analysis, to ideas generation, and new research tools. However, it is more critical than ever for people, with analogue intelligence, to ensure the integrity and ethical use of AI. Including real people can improve the use of AI by identifying potential biases, cross-checking results, refining workflows, and providing contextual relevance to AI-driven results.
News about the impact of AI often paints a rosy picture. In practice, there are many potential pitfalls. This presentation discusses these issues and looks at the role of analogue intelligence and analogue interfaces in providing the best results to our audiences. How do we deal with factually incorrect results? How do we get content generated that better reflects the diversity of our communities? What roles are there for physical, in-person experiences in the digital world?
Build Your Own Copilot & Agents For Devs



Build Your Own Copilot & Agents For DevsBrian McKeiver May 2nd, 2025 talk at StirTrek 2025 Conference.
2025-05-Q4-2024-Investor-Presentation.pptx



2025-05-Q4-2024-Investor-Presentation.pptxSamuele Fogagnolo Cloudflare Q4 Financial Results Presentation
DevOpsDays Atlanta 2025 - Building 10x Development Organizations.pptx



DevOpsDays Atlanta 2025 - Building 10x Development Organizations.pptxJustin Reock Building 10x Organizations with Modern Productivity Metrics
10x developers may be a myth, but 10x organizations are very real, as proven by the influential study performed in the 1980s, ‘The Coding War Games.’
Right now, here in early 2025, we seem to be experiencing YAPP (Yet Another Productivity Philosophy), and that philosophy is converging on developer experience. It seems that with every new method we invent for the delivery of products, whether physical or virtual, we reinvent productivity philosophies to go alongside them.
But which of these approaches actually work? DORA? SPACE? DevEx? What should we invest in and create urgency behind today, so that we don’t find ourselves having the same discussion again in a decade?
TrsLabs - Fintech Product & Business Consulting



TrsLabs - Fintech Product & Business ConsultingTrs Labs Hybrid Growth Mandate Model with TrsLabs
Strategic Investments, Inorganic Growth, Business Model Pivoting are critical activities that business don't do/change everyday. In cases like this, it may benefit your business to choose a temporary external consultant.
An unbiased plan driven by clearcut deliverables, market dynamics and without the influence of your internal office equations empower business leaders to make right choices.
Getting things done within a budget within a timeframe is key to Growing Business - No matter whether you are a start-up or a big company
Talk to us & Unlock the competitive advantage
Linux Support for SMARC: How Toradex Empowers Embedded Developers



Linux Support for SMARC: How Toradex Empowers Embedded DevelopersToradex Toradex brings robust Linux support to SMARC (Smart Mobility Architecture), ensuring high performance and long-term reliability for embedded applications. Here’s how:
• Optimized Torizon OS & Yocto Support – Toradex provides Torizon OS, a Debian-based easy-to-use platform, and Yocto BSPs for customized Linux images on SMARC modules.
• Seamless Integration with i.MX 8M Plus and i.MX 95 – Toradex SMARC solutions leverage NXP’s i.MX 8 M Plus and i.MX 95 SoCs, delivering power efficiency and AI-ready performance.
• Secure and Reliable – With Secure Boot, over-the-air (OTA) updates, and LTS kernel support, Toradex ensures industrial-grade security and longevity.
• Containerized Workflows for AI & IoT – Support for Docker, ROS, and real-time Linux enables scalable AI, ML, and IoT applications.
• Strong Ecosystem & Developer Support – Toradex offers comprehensive documentation, developer tools, and dedicated support, accelerating time-to-market.
With Toradex’s Linux support for SMARC, developers get a scalable, secure, and high-performance solution for industrial, medical, and AI-driven applications.
Do you have a specific project or application in mind where you're considering SMARC? We can help with Free Compatibility Check and help you with quick time-to-market
For more information: https://www.toradex.com/computer-on-modules/smarc-arm-family
Ad
Single Sign On Across Drupal 8 - DrupalCon Global 2020
- 1. SSO .SINGLE SIGN ON ACROSS DRUPAL 8. I w a n t h a L e k a m g e | A s s o c i a t e T e c h n i c a l L e a d | W S O 2
- 2. In today’s digitized world, connecting its systems is a must for any organization. DIGITALLY DRIVEN WORLD
- 4. Given the number of systems, websites, and more, having a single authentication mechanism across all systems is highly beneficial. AUTHENTICATION
- 5. Single Sign-On (SSO) is a user authentication service that permits a user to use one set of login credentials (for example, their name and password) to access multiple systems. WHAT IS SSO?
- 7. ● Same user credentials used for multiple systems to simplify login benefits ● Automatic login to federated systems ● Single logout system (SLO) BENEFITS
- 8. ● Centralized system to manage users and roles ● Lower operational costs ● Easy migration and configuration with a new system WHY ORGANIZATIONS NEED SSO
- 9. ● SAML 2.0 ● WS-Federation ● WS-Trust ● OAuth 2.0 ● OpenID Connect ● SCIM SSO STANDARDS
- 10. Security Assertion Markup Language (SAML) is an XML-based data format for exchanging authentication and authorization data between an identity provider and a service provider. SAML
- 11. ● Identity Provider (IdP) The SAML authority that provides the identity assertion to authenticate a user ● Service Provider (SP) The SAML consumer that provides the service for users PROVIDERS
- 12. HOW SAML WORKS
- 13. STEPS INVOLVED IN SAML
- 14. ● SimpleSAMLphp Library ● Drupal 8 instances ● SimpleSAMLphp_auth Drupal module REQUIREMENTS
- 15. ● Two Drupal instances ● One instance as SP ● Other instance as IdP SETTING UP SP AND IDP
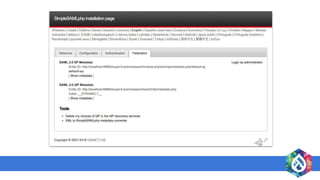
- 16. ● Set up a SimpleSAMLphp library inside the docroot of the Drupal ● Create a symlink and update the .htaccess file ● Configure config.php ● Generate certificates (Run this command inside cert folder) openssl req -new -x509 -days 3652 -nodes -out saml.crt -keyout saml.pem SERVICE PROVIDER CONFIGURATIONS
- 18. ● Set up SimpleSAMLphp library inside the docroot of the Drupal ● Create a symlink and update the .htaccess file ● Update config.php 'enable.saml20-idp' => true ● Enable exampleauth module cd modules/exampleauth touch enable ● Configure authsources.php IDP CONFIGURATIONS
- 20. ● Generate certificates (Run this command inside cert folder) cd cert openssl req -newkey rsa:3072 -new -x509 -days 3652 -nodes -out server.crt -keyout server.pem ● SAML 2.0 IdP needs to be configured by the metadata stored in metadata/saml20-idp-hosted.php metadata/saml20-idp-hosted.php VERIFYING THE IDP
- 22. ● Copy IdP metadata to the metadata/saml20-idp-remote.php file of the SP ● Copy SP metadata to the metadata/saml20-sp-remote.php file of the IdP ● Configure Service Provider with the IdP name METADATA
- 23. TEST CONFIGURED AUTHENTICATION RESOURCES
- 24. ● Download and install the module ● Check ‘Activate authenticate via SimpleSAMLphp’ (Basic settings) ● Change ‘User info and Syncing’ ○ uid as the unique identifier for the user ○ uid as the username for the user ○ email as the email address for the user SIMPLESAMLPHP_AUTH MODULE
- 25. FEDERATED LOGIN
- 26. OPEN SOURCE SSO ● Aerobase ● CAS ● Keycloak ● Shibboleth ● WSO2 Identity Server
- 27. CONNECT WITH WSO2 IDENTITY SERVER ● Download WSO2 Identity Server ● Run/bin/wso2server.sh on terminal ● Open https://localhost:9443/carbon/ in web browser ● Login to the system ○ Username: admin ○ Password: admin
- 28. SSO .SINGLE SIGN ON ACROSS DRUPAL 8. DEMONSTRATION
- 29. ● https://medium.com/@iwantha/single-sign-on-across-drupal-8-e42db6a2e7f ● https://medium.com/@iwantha/wso2-identity-server-sso-with-drupal-8-4bb8ae915c20 ● https://github.com/simplesamlphp/simplesamlphp ● https://www.drupal.org/project/simplesamlphp_auth ● https://wso2.com/identity-and-access-management RESOURCES
- 30. .THANK YOU. I w a n t h a L e k a m g e | A s s o c i a t e T e c h n i c a l L e a d | W S O 2 E m a i l : i w a n t h a @ w s o 2 . c o m https://medium.com/@iwantha https://www.linkedin.com/in/iwantha-lekamge-5b90b629/ https://twitter.com/IwanthaLekamge

