Skiena algorithm 2007 lecture02 asymptotic notation
0 likes691 views
This document contains lecture notes on asymptotic notation for analyzing algorithms. It defines big O, Ω, and Θ notation for describing the worst-case, best-case, and average-case time complexity of algorithms. It explains that these notations describe the upper and lower bounds of the growth rate of an algorithm's run time as the problem size increases. The document also provides examples of using asymptotic notation to classify common functions and discusses properties like how complexity is affected by addition, subtraction, multiplication, and more.
1 of 17
Downloaded 24 times













Ad
Recommended
Time complexity



Time complexityLAKSHMITHARUN PONNAM This document discusses time complexity and big O notation for analyzing the runtime of algorithms. It provides examples of common algorithms like sorting, searching, and matrix multiplication and their time complexities. For example, matrix-vector multiplication runs in O(N2) time, where N is the size of the matrix. The document also explains that big O notation describes the asymptotic worst-case growth rate of an algorithm's runtime as the problem size increases.
02 asymptotic notations



02 asymptotic notationsTarikuDabala1 The document discusses asymptotic notations and analysis. It defines common asymptotic notations like Big-O, Big-Omega, and Theta notation that are used to categorize algorithms based on their asymptotic growth rate (e.g. linear, quadratic, exponential). These notations ignore small constants and inputs, and describe how the running time of an algorithm grows as the input size n approaches infinity. Examples are provided to demonstrate how to determine the asymptotic tight upper and lower bounds of functions using these notations.
Stochastic Assignment Help 



Stochastic Assignment Help Statistics Assignment Help I am Simon M. I am a Statistics Assignment Expert at statisticsassignmenthelp.com. I hold a Masters in Statistics from,Nottingham Trent University,UK
I have been helping students with their homework for the past 6 years. I solve assignments related to Statistics.
Visit statisticsassignmenthelp.com or email [email protected].
You can also call on +1 678 648 4277 for any assistance with Stochastic Assignment Help.
EULER AND FERMAT THEOREM



EULER AND FERMAT THEOREMankita pandey This document discusses Fermat's and Euler's theorems regarding prime numbers and their applications in cryptography. It begins by defining prime numbers, prime factorization, and greatest common divisors. It then explains Fermat's theorem that any integer to the power of a prime number minus one is congruent to one modulo that prime number. Next, it defines Euler's totient function and proves Euler's theorem, which generalizes Fermat's theorem. It concludes by providing an example of how these theorems can be applied to encrypt and decrypt messages in a public-key cryptography system.
Time complexity



Time complexityKartik Chandra Mandal This document discusses recurrence relations and methods for solving recurrences. It introduces recurrence relations and examples. It covers the substitution method, iteration method, and Master Theorem for solving recurrences. The Master Theorem is a technique for solving divide-and-conquer recurrences to determine asymptotic tight bounds. Examples are provided to demonstrate applying these techniques.
Limits And Derivative



Limits And DerivativeAshams kurian The document discusses key concepts in calculus including functions, limits, derivatives, and derivatives of trigonometric functions. It provides examples of calculating derivatives from first principles using the definition of the derivative and common derivative rules like the product rule and quotient rule. Formulas are also derived for the derivatives of the sine, cosine, and tangent functions.
03 convexfunctions



03 convexfunctionsSufyan Sahoo The document discusses convex functions and related concepts. It defines convex functions and provides examples of convex and concave functions on R and Rn, including norms, logarithms, and powers. It describes properties that preserve convexity, such as positive weighted sums and composition with affine functions. The conjugate function and quasiconvex functions are also introduced. Key concepts are illustrated with examples throughout.
Concepts of Maxima And Minima



Concepts of Maxima And MinimaJitin Pillai This document discusses concepts related to finding maximum and minimum values of functions. It provides examples of max-min problems from history involving projectiles and planetary motion. The max-min theorem states that continuous functions on closed intervals attain both maximum and minimum values. A strategy is outlined for solving max-min problems which involves drawing diagrams, writing equations, finding critical points and endpoints, and listing function values to determine local and absolute extrema. An example problem applying the strategy finds the maximum area of a fence enclosure as a 9x9 square.
Numerical analysis convexity, concavity



Numerical analysis convexity, concavitySHAMJITH KM This document discusses the concepts of convexity and concavity for functions of one and two variables. It defines a convex function as one where the line segment between any two points on the graph lies above the graph, and provides tests for determining convexity using derivatives. A function is concave if its derivative is decreasing. Examples are provided to demonstrate these concepts. Conditions for convexity and concavity are extended to functions of two variables, and contour plots are used to illustrate the properties visually.
Linear Algebra



Linear AlgebraMaths Tutoring The document contains solutions to exercises about vector calculus and linear algebra concepts. It shows that the wedge product of two vectors is skew symmetric, that the alpha rotation matrix rotates vectors in R2 by angle alpha and is orthogonal, and that the set of orthogonal 2x2 matrices forms a group. It also analyzes a linear transformation T from R2 to R by finding its kernel and expressing it in terms of a basis.
Pinning and facetting in multiphase LBMs



Pinning and facetting in multiphase LBMsTim Reis This document presents a stochastic sharpening approach for improving the pinning and facetting of sharp phase boundaries in lattice Boltzmann simulations. It summarizes that multiphase lattice Boltzmann models are prone to unphysical pinning and facetting of interfaces. By replacing the deterministic sharpening threshold with a random variable, the approach delays the onset of these issues and better predicts propagation speeds, even with very sharp boundaries. The random projection method preserves the shape of a propagating circular patch, unlike the standard LeVeque model which results in facetting and non-circular shapes at high sharpness ratios.
Ps02 cmth03 unit 1



Ps02 cmth03 unit 1Prakash Dabhi This document defines and provides examples of curves and parametrized curves. It discusses regular and unit-speed curves. The key points are:
i) A parametrized curve is a continuous function from an interval to Rn. Examples of parametrized curves include ellipses, parabolas, and helices.
ii) A regular curve is one where the derivative of the parametrization is never zero. A unit-speed curve has a derivative of constant length 1.
iii) The arc-length of a curve is defined as the integral of the derivative of the parametrization. Any reparametrization of a regular curve is also regular. A curve has a unit-
Application of derivatives 2 maxima and minima



Application of derivatives 2 maxima and minimasudersana viswanathan This document discusses key concepts related to derivatives and their applications:
- It defines increasing and decreasing functions and explains how to determine if a function is increasing or decreasing based on the sign of the derivative.
- It introduces the use of derivatives to find maximum and minimum values, extreme points, and critical points of functions.
- Theorems 1 and 2 provide rules for determining if a critical point represents a maximum or minimum.
- Examples are provided to demonstrate finding the intervals where a function is increasing/decreasing, identifying extrema, and determining the greatest and least function values over an interval.
Limits



Limitsadmercano101 The document discusses the concept of limits. It explains that as the number of sides of a polygon increases, the area of the polygon approximates the area of the circle it is inscribed in, and the limit of the polygon's area is equal to the area of the circle. It also examines the limit of a function as x approaches 2 from both sides, and defines some fundamental rules of limits, such as the constant rule, sum rule, and multiplication rule. Finally, it outlines several techniques that can be used to calculate limits, including direct substitution, factoring, rationalization, and limits involving infinity and trigonometric, exponential and two-sided limits.
Limits, Continuity & Differentiation (Theory)



Limits, Continuity & Differentiation (Theory)Eduron e-Learning Private Limited The document discusses key concepts related to limits, continuity, and differentiation. It defines what it means for a variable x to approach a finite number a or infinity, and provides the formal definitions of one-sided limits and two-sided limits. It also discusses indeterminate forms when limits take on forms like 0/0, infinity/infinity, or infinity - infinity. The document outlines several properties of limits, including limits of even and odd functions. It distinguishes between the limit of a function as x approaches a, denoted limx→af(x), versus the function value at that point, f(a). Finally, it states standard theorems about limits, such as the sum and product of two functions whose limits exist
Signals Processing Homework Help



Signals Processing Homework HelpMatlab Assignment Experts The document provides homework problems and solutions related to signals processing. It includes problems on determining the frequency and period of signals, properties of even and odd signals, sampling of continuous signals, and periodicity of sums of signals. It also provides detailed solutions and explanations to each problem.
Application of differentiation



Application of differentiationLily Maryati This presentation explains how the differentiation is applied to identify increasing and decreasing functions,identifying the nature of stationary points and also finding maximum or minimum values.
Application of derivatives



Application of derivativesindu thakur The document discusses several key concepts regarding derivatives:
(1) It explains how to use the derivative to determine if a function is increasing, decreasing, or neither on an interval using the signs of the derivative.
(2) It provides theorems and rules for finding local extrema (maxima and minima) of functions using the first and second derivative tests.
(3) It also discusses absolute extrema, monotonic functions, and the Rolle's Theorem and Mean Value Theorem which relate the derivative of a function to values of the function.
Lesson 19: Maximum and Minimum Values



Lesson 19: Maximum and Minimum ValuesMatthew Leingang The closed interval method tells us how to find the extreme values of a continuous function defined on a closed, bounded interval: we check the end points and the critical points.
Limits of functions



Limits of functionsLouie Joy Rosit The document discusses limits of functions and continuity. It defines a limit of a function as approaching a value A as the input x approaches a number a. A function is continuous at a point a if the limit exists and equals the function value at a. A function is discontinuous if it is not continuous at a point. Examples of continuous and discontinuous functions are provided to illustrate the concepts.
application of partial differentiation



application of partial differentiationeteaching This document discusses topics in partial differentiation including:
1) The geometrical meaning of partial derivatives as the slope of the tangent line to a surface.
2) Finding the equation of the tangent plane and normal line to a surface.
3) Taylor's theorem and Maclaurin's theorem for functions with two variables, which can be used to approximate functions and calculate errors.
Dynamical systems solved ex



Dynamical systems solved exMaths Tutoring This document contains exercises related to dynamical systems and periodic points. It includes the following summaries:
1. The doubling map on the circle has 2n-1 periodic points of period n. Its periodic points are dense.
2. The map f(x)=|x-2| has a fixed point at x=1. Other periodic and pre-periodic points are [0,2]\{1\} of period 2 and (-∞,0)∪(2,+∞) which are pre-periodic.
3. Expanding maps of the circle are topologically mixing since intervals get longer under iteration, eventually covering the entire circle.
limits and continuity



limits and continuityElias Dinsa The document discusses limits and continuity of functions. It provides examples of computing one-sided limits, limits at points of discontinuity, and limits involving algebraic, trigonometric, exponential and logarithmic functions. The key rules for limits include the properties of limits, the sandwich theorem, and limits of compositions of functions. Continuity of functions is defined as a function having a limit equal to its value at a point. Polynomials, trigonometric functions and exponentials are shown to be continuous everywhere they are defined.
READ Workshop Appendix



READ Workshop AppendixBan Har Yeap 1. The force of repulsion between two particles is inversely proportional to the square of the distance between them. The formula is given to calculate force based on distance. When the distance is halved, the force doubles.
2. For cones of the same volume, height is inversely proportional to the square of the base radius. The heights and base radii of three cones are given. The heights of the other two cones must be calculated.
3. Several problems are given involving inverse proportions, including calculating unknown variables based on known values and inverse proportional relationships defined by equations.
Introduction to differentiation



Introduction to differentiationShaun Wilson The document introduces differentiation and the concept of the derivative. It discusses how the derivative can be used to find the rate of change of a function and the slope of its tangent line. The main rules covered are:
1) If f(x) = x^n, then the derivative is f'(x) = nx^(n-1).
2) Examples are provided of finding the derivative of functions like f(x) = 6x^3, which is f'(x) = 18x^2.
3) The derivative can be used to find the slope of a tangent line at specific points, like finding the derivative of f(x) = (x + 5)^2 at x
Basic mathematics differentiation application



Basic mathematics differentiation applicationMuhammad Luthfan Materi kuliah tentang Aplikasi Integral. Cari lebih banyak mata kuliah Semester 1 di: http://muhammadhabibielecture.blogspot.com/2014/12/kuliah-semester-1-thp-ftp-ub.html
Workshop presentations l_bworkshop_reis



Workshop presentations l_bworkshop_reisTim Reis The document discusses issues with pinning and facetting in lattice Boltzmann simulations of multiphase flows. It presents a lattice Boltzmann model for propagating sharp interfaces using a phase field approach. Sharpening the phase field interface causes it to become pinned to the lattice or develop facets. Introducing randomness via a random projection method or random threshold prevents pinning and delays facetting, allowing the interface to propagate at the correct speed even for very sharp boundaries.
Limit, Continuity and Differentiability for JEE Main 2014



Limit, Continuity and Differentiability for JEE Main 2014Ednexa The document discusses limits, continuity, and differentiability. It defines the limit of a function, continuity of a function at a point using three conditions, and Cauchy's definition of continuity using delta and epsilon. It also discusses left and right continuity, Heine's definition of continuity using convergent sequences, and the formal definition of continuity. Examples are provided to illustrate calculating limits and determining continuity.
Ad
More Related Content
What's hot (20)
Numerical analysis convexity, concavity



Numerical analysis convexity, concavitySHAMJITH KM This document discusses the concepts of convexity and concavity for functions of one and two variables. It defines a convex function as one where the line segment between any two points on the graph lies above the graph, and provides tests for determining convexity using derivatives. A function is concave if its derivative is decreasing. Examples are provided to demonstrate these concepts. Conditions for convexity and concavity are extended to functions of two variables, and contour plots are used to illustrate the properties visually.
Linear Algebra



Linear AlgebraMaths Tutoring The document contains solutions to exercises about vector calculus and linear algebra concepts. It shows that the wedge product of two vectors is skew symmetric, that the alpha rotation matrix rotates vectors in R2 by angle alpha and is orthogonal, and that the set of orthogonal 2x2 matrices forms a group. It also analyzes a linear transformation T from R2 to R by finding its kernel and expressing it in terms of a basis.
Pinning and facetting in multiphase LBMs



Pinning and facetting in multiphase LBMsTim Reis This document presents a stochastic sharpening approach for improving the pinning and facetting of sharp phase boundaries in lattice Boltzmann simulations. It summarizes that multiphase lattice Boltzmann models are prone to unphysical pinning and facetting of interfaces. By replacing the deterministic sharpening threshold with a random variable, the approach delays the onset of these issues and better predicts propagation speeds, even with very sharp boundaries. The random projection method preserves the shape of a propagating circular patch, unlike the standard LeVeque model which results in facetting and non-circular shapes at high sharpness ratios.
Ps02 cmth03 unit 1



Ps02 cmth03 unit 1Prakash Dabhi This document defines and provides examples of curves and parametrized curves. It discusses regular and unit-speed curves. The key points are:
i) A parametrized curve is a continuous function from an interval to Rn. Examples of parametrized curves include ellipses, parabolas, and helices.
ii) A regular curve is one where the derivative of the parametrization is never zero. A unit-speed curve has a derivative of constant length 1.
iii) The arc-length of a curve is defined as the integral of the derivative of the parametrization. Any reparametrization of a regular curve is also regular. A curve has a unit-
Application of derivatives 2 maxima and minima



Application of derivatives 2 maxima and minimasudersana viswanathan This document discusses key concepts related to derivatives and their applications:
- It defines increasing and decreasing functions and explains how to determine if a function is increasing or decreasing based on the sign of the derivative.
- It introduces the use of derivatives to find maximum and minimum values, extreme points, and critical points of functions.
- Theorems 1 and 2 provide rules for determining if a critical point represents a maximum or minimum.
- Examples are provided to demonstrate finding the intervals where a function is increasing/decreasing, identifying extrema, and determining the greatest and least function values over an interval.
Limits



Limitsadmercano101 The document discusses the concept of limits. It explains that as the number of sides of a polygon increases, the area of the polygon approximates the area of the circle it is inscribed in, and the limit of the polygon's area is equal to the area of the circle. It also examines the limit of a function as x approaches 2 from both sides, and defines some fundamental rules of limits, such as the constant rule, sum rule, and multiplication rule. Finally, it outlines several techniques that can be used to calculate limits, including direct substitution, factoring, rationalization, and limits involving infinity and trigonometric, exponential and two-sided limits.
Limits, Continuity & Differentiation (Theory)



Limits, Continuity & Differentiation (Theory)Eduron e-Learning Private Limited The document discusses key concepts related to limits, continuity, and differentiation. It defines what it means for a variable x to approach a finite number a or infinity, and provides the formal definitions of one-sided limits and two-sided limits. It also discusses indeterminate forms when limits take on forms like 0/0, infinity/infinity, or infinity - infinity. The document outlines several properties of limits, including limits of even and odd functions. It distinguishes between the limit of a function as x approaches a, denoted limx→af(x), versus the function value at that point, f(a). Finally, it states standard theorems about limits, such as the sum and product of two functions whose limits exist
Signals Processing Homework Help



Signals Processing Homework HelpMatlab Assignment Experts The document provides homework problems and solutions related to signals processing. It includes problems on determining the frequency and period of signals, properties of even and odd signals, sampling of continuous signals, and periodicity of sums of signals. It also provides detailed solutions and explanations to each problem.
Application of differentiation



Application of differentiationLily Maryati This presentation explains how the differentiation is applied to identify increasing and decreasing functions,identifying the nature of stationary points and also finding maximum or minimum values.
Application of derivatives



Application of derivativesindu thakur The document discusses several key concepts regarding derivatives:
(1) It explains how to use the derivative to determine if a function is increasing, decreasing, or neither on an interval using the signs of the derivative.
(2) It provides theorems and rules for finding local extrema (maxima and minima) of functions using the first and second derivative tests.
(3) It also discusses absolute extrema, monotonic functions, and the Rolle's Theorem and Mean Value Theorem which relate the derivative of a function to values of the function.
Lesson 19: Maximum and Minimum Values



Lesson 19: Maximum and Minimum ValuesMatthew Leingang The closed interval method tells us how to find the extreme values of a continuous function defined on a closed, bounded interval: we check the end points and the critical points.
Limits of functions



Limits of functionsLouie Joy Rosit The document discusses limits of functions and continuity. It defines a limit of a function as approaching a value A as the input x approaches a number a. A function is continuous at a point a if the limit exists and equals the function value at a. A function is discontinuous if it is not continuous at a point. Examples of continuous and discontinuous functions are provided to illustrate the concepts.
application of partial differentiation



application of partial differentiationeteaching This document discusses topics in partial differentiation including:
1) The geometrical meaning of partial derivatives as the slope of the tangent line to a surface.
2) Finding the equation of the tangent plane and normal line to a surface.
3) Taylor's theorem and Maclaurin's theorem for functions with two variables, which can be used to approximate functions and calculate errors.
Dynamical systems solved ex



Dynamical systems solved exMaths Tutoring This document contains exercises related to dynamical systems and periodic points. It includes the following summaries:
1. The doubling map on the circle has 2n-1 periodic points of period n. Its periodic points are dense.
2. The map f(x)=|x-2| has a fixed point at x=1. Other periodic and pre-periodic points are [0,2]\{1\} of period 2 and (-∞,0)∪(2,+∞) which are pre-periodic.
3. Expanding maps of the circle are topologically mixing since intervals get longer under iteration, eventually covering the entire circle.
limits and continuity



limits and continuityElias Dinsa The document discusses limits and continuity of functions. It provides examples of computing one-sided limits, limits at points of discontinuity, and limits involving algebraic, trigonometric, exponential and logarithmic functions. The key rules for limits include the properties of limits, the sandwich theorem, and limits of compositions of functions. Continuity of functions is defined as a function having a limit equal to its value at a point. Polynomials, trigonometric functions and exponentials are shown to be continuous everywhere they are defined.
READ Workshop Appendix



READ Workshop AppendixBan Har Yeap 1. The force of repulsion between two particles is inversely proportional to the square of the distance between them. The formula is given to calculate force based on distance. When the distance is halved, the force doubles.
2. For cones of the same volume, height is inversely proportional to the square of the base radius. The heights and base radii of three cones are given. The heights of the other two cones must be calculated.
3. Several problems are given involving inverse proportions, including calculating unknown variables based on known values and inverse proportional relationships defined by equations.
Introduction to differentiation



Introduction to differentiationShaun Wilson The document introduces differentiation and the concept of the derivative. It discusses how the derivative can be used to find the rate of change of a function and the slope of its tangent line. The main rules covered are:
1) If f(x) = x^n, then the derivative is f'(x) = nx^(n-1).
2) Examples are provided of finding the derivative of functions like f(x) = 6x^3, which is f'(x) = 18x^2.
3) The derivative can be used to find the slope of a tangent line at specific points, like finding the derivative of f(x) = (x + 5)^2 at x
Basic mathematics differentiation application



Basic mathematics differentiation applicationMuhammad Luthfan Materi kuliah tentang Aplikasi Integral. Cari lebih banyak mata kuliah Semester 1 di: http://muhammadhabibielecture.blogspot.com/2014/12/kuliah-semester-1-thp-ftp-ub.html
Workshop presentations l_bworkshop_reis



Workshop presentations l_bworkshop_reisTim Reis The document discusses issues with pinning and facetting in lattice Boltzmann simulations of multiphase flows. It presents a lattice Boltzmann model for propagating sharp interfaces using a phase field approach. Sharpening the phase field interface causes it to become pinned to the lattice or develop facets. Introducing randomness via a random projection method or random threshold prevents pinning and delays facetting, allowing the interface to propagate at the correct speed even for very sharp boundaries.
Limit, Continuity and Differentiability for JEE Main 2014



Limit, Continuity and Differentiability for JEE Main 2014Ednexa The document discusses limits, continuity, and differentiability. It defines the limit of a function, continuity of a function at a point using three conditions, and Cauchy's definition of continuity using delta and epsilon. It also discusses left and right continuity, Heine's definition of continuity using convergent sequences, and the formal definition of continuity. Examples are provided to illustrate calculating limits and determining continuity.
Similar to Skiena algorithm 2007 lecture02 asymptotic notation (20)
Anlysis and design of algorithms part 1



Anlysis and design of algorithms part 1Deepak John Analyzing Algorithms and problems. Classifying functions by their asymptotic growth rate. Recursive procedures. Recurrence equations - Substitution Method, Changing variables, Recursion Tree, Master Theorem. Design Techniques- Divide and Conquer, Dynamic Programming, Greedy, Backtracking
Unit-1 DAA_Notes.pdf



Unit-1 DAA_Notes.pdfAmayJaiswal4 This document discusses algorithms and their analysis. It begins by defining an algorithm and analyzing its time and space complexity. It then discusses different asymptotic notations used to describe an algorithm's runtime such as Big-O, Omega, and Theta notations. Examples are provided to illustrate how to determine the tight asymptotic bound of functions. The document also covers algorithm design techniques like divide-and-conquer and analyzes merge sort as an example. It concludes by defining recurrences used to describe algorithms and provides an example recurrence for merge sort.
DAA_LECT_2.pdf



DAA_LECT_2.pdfAryanSaini69 The document discusses asymptotic notation, which is used to describe how algorithms scale as the input size increases. It defines Big-O, Big-Omega, and Big-Theta notations to classify functions based on their growth rates. Specifically, it provides the mathematical definitions of O, Ω, and Θ notations and examples of classifying common functions like polynomials, logarithms, and exponentials using this notation. It also covers properties like transitivity and relations between the different notations.
asymptotic notations i



asymptotic notations iAli mahmood This document discusses time complexity analysis of algorithms using asymptotic notations. It defines key notations like O(g(n)) which represents an upper bound, Ω(g(n)) for a lower bound, and Θ(g(n)) for a tight bound. Examples are provided to demonstrate proving classifications like n^2 ∈ O(n^3) and 5n^2 ∈ Ω(n). Limitations of the notations are also noted, such as not capturing variable behavior between even and odd inputs. The notations provide a way to categorize algorithms and compare their growth rates to determine asymptotic efficiency.
Analysis of algorithms



Analysis of algorithmsS.Shayan Daneshvar The document discusses analysis of algorithms and asymptotic notation for analyzing algorithms. It introduces key concepts like analyzing best, worst, and average cases of algorithms; using size of input to analyze resources required; classifying algorithms; and asymptotic notation like Big-O, Big-Omega, and Big-Theta to characterize time and space complexity without small constant factors or lower order terms. It explains how these notations can be used to compare functions and determine upper and lower bounds on resource requirements.
CMSC 56 | Lecture 8: Growth of Functions



CMSC 56 | Lecture 8: Growth of Functionsallyn joy calcaben Growth of Functions
CMSC 56 | Discrete Mathematical Structure for Computer Science
October 6, 2018
Instructor: Allyn Joy D. Calcaben
College of Arts & Sciences
University of the Philippines Visayas
Lecture 3(a) Asymptotic-analysis.pdf



Lecture 3(a) Asymptotic-analysis.pdfShaistaRiaz4 The document discusses asymptotic analysis and asymptotic notation. It defines Big-Oh, Big-Omega, and Theta notation and provides examples. Some key points:
- Asymptotic analysis examines an algorithm's behavior for large inputs by analyzing its growth rate as the input size n approaches infinity.
- Common notations like O(n^2), Ω(n log n), θ(n) describe an algorithm's asymptotic growth in relation to standard functions.
- O notation describes asymptotic upper bounds, Ω describes lower bounds, and θ describes tight bounds between two functions.
- Theorems describe relationships between the notations and how to combine functions when using the notations.
Asymptotic Notation and Complexity



Asymptotic Notation and ComplexityRajandeep Gill The ppt will provide complete detail of different types of complexity and asymptotic notation with suitable example.
Design and analysis of algorithm ppt ppt



Design and analysis of algorithm ppt pptsrushtiivp The document discusses asymptotic analysis and algorithmic complexity. It introduces asymptotic notations like Big O, Omega, and Theta that are used to analyze how an algorithm's running time grows as the input size increases. These notations allow algorithms to be categorized based on their worst-case upper and lower time bounds. Common time complexities include constant, logarithmic, linear, quadratic, and exponential time. The document provides examples of problems that fall into each category and discusses how asymptotic notations are used to prove upper and lower bounds for functions.
Asymptotic Notation



Asymptotic Notationsohelranasweet This document discusses analyzing algorithms and asymptotic notation. It defines running time as the number of primitive operations before termination. Examples are provided to illustrate calculating running time functions and classifying them by order of growth such as constant, logarithmic, linear, quadratic, and exponential time. Asymptotic notation such as Big-O, Big-Omega, and Big-Theta are introduced to classify functions by their asymptotic growth rates. Examples are given to demonstrate determining tight asymptotic bounds between functions. Recurrences are defined as equations describing functions in terms of smaller inputs and base cases, which are useful for analyzing recurrent algorithms.
Asymptotic notation



Asymptotic notationmustafa sarac This document provides an introduction to asymptotic notation, which is used to classify algorithms according to their running time or space requirements. It defines common asymptotic notations like Big-O, Big-Omega, and Big-Theta and provides examples of algorithms that run in constant time (O(1)), linear time (O(n)), logarithmic time (O(log n)), quadratic time (O(n^2)), and other runtimes. The document also compares common growth rates like constant, linear, logarithmic, n log n, quadratic, polynomial, and exponential functions. Overall, it establishes the foundation for discussing the asymptotic efficiency of algorithms.
big_oh



big_ohJonathan (JT) Cho - The document discusses asymptotic analysis and Big-O, Big-Omega, and Big-Theta notation for analyzing the runtime complexity of algorithms.
- It provides examples of using these notations to classify functions as upper or lower bounds of other functions, and explains how to determine if a function is O(g(n)), Ω(g(n)), or Θ(g(n)).
- It also introduces little-o and little-omega notations for strict asymptotic bounds, and discusses properties and caveats of asymptotic analysis.
02 asymp



02 asympaparnabk7 The document discusses asymptotic notation and its use in analyzing algorithms. It introduces big-O, big-Theta, and big-Omega notation to describe the asymptotic growth rates of functions. These notations are defined precisely using limits. Examples are given to illustrate how functions can be classified based on their rate of growth. Properties like transitivity and symmetry of the notations are covered. Common functions like polynomials, logarithms, and exponentials are discussed in terms of asymptotic notation.
lecture 1



lecture 1sajinsc The document discusses algorithms and algorithm analysis. It provides examples to illustrate key concepts in algorithm analysis including worst-case, average-case, and best-case running times. The document also introduces asymptotic notation such as Big-O, Big-Omega, and Big-Theta to analyze the growth rates of algorithms. Common growth rates like constant, logarithmic, linear, quadratic, and exponential functions are discussed. Rules for analyzing loops and consecutive statements are provided. Finally, algorithms for two problems - selection and maximum subsequence sum - are analyzed to demonstrate algorithm analysis techniques.
1_Asymptotic_Notation_pptx.pptx



1_Asymptotic_Notation_pptx.pptxpallavidhade2 The document discusses algorithm analysis and asymptotic notation. It begins by explaining how to analyze algorithms to predict resource requirements like time and space. It defines asymptotic notation like Big-O, which describes an upper bound on the growth rate of an algorithm's running time. The document then provides examples of analyzing simple algorithms and classifying functions based on their asymptotic growth rates. It also introduces common time functions like constant, logarithmic, linear, quadratic, and exponential time and compares their growth.
Asymptotics 140510003721-phpapp02



Asymptotics 140510003721-phpapp02mansab MIRZA The presentation covered time and space complexity, average and worst case analysis, and asymptotic notations. It defined key concepts like time complexity measures the number of operations, space complexity measures memory usage, and worst case analysis provides an upper bound on running time. Common asymptotic notations like Big-O, Omega, and Theta were explained, and how they are used to compare how functions grow relative to each other as input size increases.
Skiena algorithm 2007 lecture09 linear sorting



Skiena algorithm 2007 lecture09 linear sortingzukun - The document discusses linear sorting algorithms like quicksort.
- It provides pseudocode for quicksort and explains its best, average, and worst case time complexities. Quicksort runs in O(n log n) time on average but can be O(n^2) in the worst case if the pivot element is selected poorly.
- Randomized quicksort is discussed as a way to achieve expected O(n log n) time for any input by selecting the pivot randomly.
Ad
More from zukun (20)
My lyn tutorial 2009



My lyn tutorial 2009zukun Mylyn helps address information overload and context loss when multi-tasking. It integrates tasks into the IDE workflow and uses a degree-of-interest model to monitor user interaction and provide a task-focused UI with features like view filtering, element decoration, automatic folding and content assist ranking. This creates a single view of all tasks that are centrally managed within the IDE.
ETHZ CV2012: Tutorial openCV



ETHZ CV2012: Tutorial openCVzukun This document provides an overview of OpenCV, an open source computer vision and machine learning software library. It discusses OpenCV's core functionality for representing images as matrices and directly accessing pixel data. It also covers topics like camera calibration, feature point extraction and matching, and estimating camera pose through techniques like structure from motion and planar homography. Hints are provided for Android developers on required permissions and for planar homography estimation using additional constraints rather than OpenCV's general homography function.
ETHZ CV2012: Information



ETHZ CV2012: Informationzukun This document provides information about the Computer Vision Laboratory 2012 course at the Institute of Visual Computing. The course focuses on computer vision on mobile devices and will involve 180 hours of project work per person. Students will work in groups of 1-2 people on topics like 3D reconstruction from silhouettes or stereo images on mobile devices. Key dates are provided for submitting a work plan, mid-term presentation, and final report. Contact information is given for the lecturers and teaching assistant.
Siwei lyu: natural image statistics



Siwei lyu: natural image statisticszukun This document summarizes a presentation on natural image statistics given by Siwei Lyu at the 2009 CIFAR NCAP Summer School. The presentation covered several key topics:
1) It discussed the motivation for studying natural image statistics, which is to understand representations in the visual system and develop computer vision applications like denoising.
2) It reviewed common statistical properties found in natural images like 1/f power spectra and non-Gaussian distributions.
3) Maximum entropy and Bayesian models were presented as approaches to model these statistics, with Gaussian and independent component analysis discussed as specific examples.
4) Efficient coding principles from information theory were introduced as a framework for understanding neural representations that aim to decorrelate and
Lecture9 camera calibration



Lecture9 camera calibrationzukun Camera calibration involves determining the internal camera parameters like focal length, image center, distortion, and scaling factors that affect the imaging process. These parameters are important for applications like 3D reconstruction and robotics that require understanding the relationship between 3D world points and their 2D projections in an image. The document describes estimating internal parameters by taking images of a calibration target with known geometry and solving the equations that relate the 3D target points to their 2D image locations. Homogeneous coordinates and projection matrices are used to represent the calibration transformations mathematically.
Brunelli 2008: template matching techniques in computer vision



Brunelli 2008: template matching techniques in computer visionzukun The document discusses template matching techniques in computer vision. It begins with an overview that defines template matching and discusses some common computer vision tasks it can be used for, like object detection. It then covers topics like detection as hypothesis testing, training and testing techniques, and provides a bibliography.
Modern features-part-4-evaluation



Modern features-part-4-evaluationzukun The HARVEST Programme evaluates feature detectors and descriptors through indirect and direct benchmarks. Indirect benchmarks measure repeatability and matching scores on the affine covariant testbed to evaluate how features persist across transformations. Direct benchmarks evaluate features on image retrieval tasks using the Oxford 5k dataset to measure real-world performance. VLBenchmarks provides software for easily running these benchmarks and reproducing published results. It allows comparing features and selecting the best for a given application.
Modern features-part-3-software



Modern features-part-3-softwarezukun This document summarizes VLFeat, an open source computer vision library. It provides concise summaries of VLFeat's features, including SIFT, MSER, and other covariant detectors. It also compares VLFeat's performance to other libraries like OpenCV. The document highlights how VLFeat achieves state-of-the-art results in tasks like feature detection, description and matching while maintaining a simple MATLAB interface.
Modern features-part-2-descriptors



Modern features-part-2-descriptorszukun This document summarizes and compares local image descriptors. It begins with an introduction to modern descriptors like SIFT, SURF and DAISY. It then discusses efficient descriptors such as binary descriptors like BRIEF, ORB and BRISK which use comparisons of intensity value pairs. The document concludes with an overview section.
Modern features-part-1-detectors



Modern features-part-1-detectorszukun This document discusses various feature detectors used in computer vision. It begins by describing classic detectors such as the Harris detector and Hessian detector that search scale space to find distinguished locations. It then discusses detecting features at multiple scales using the Laplacian of Gaussian and determinant of Hessian. The document also covers affine covariant detectors such as maximally stable extremal regions and affine shape adaptation. It discusses approaches for speeding up detection using approximations like those in SURF and learning to emulate detectors. Finally, it outlines new developments in feature detection.
Modern features-part-0-intro



Modern features-part-0-introzukun The document discusses modern feature detection techniques. It provides an introduction and agenda for a talk on advances in feature detectors and descriptors, including improvements since a 2005 paper. It also discusses software suites and benchmarks for feature detection. Several application domains are described, such as wide baseline matching, panoramic image stitching, 3D reconstruction, image search, location recognition, and object tracking.
Lecture 02 internet video search



Lecture 02 internet video searchzukun System 1 and System 2 were basic early systems for image matching that used color and texture matching. Descriptor-based approaches like SIFT provided more invariance but not perfect invariance. Patch descriptors like SIFT were improved by making them more invariant to lighting changes like color and illumination shifts. The best performance came from combining descriptors with color invariance. Representing images as histograms of visual word occurrences captured patterns in local image patches and allowed measuring similarity between images. Large vocabularies of visual words provided more discriminative power but were costly to compute and store.
Lecture 01 internet video search



Lecture 01 internet video searchzukun This document summarizes a research paper on internet video search. It discusses several key challenges: [1] the large variation in how the same thing can appear in images/videos due to lighting, viewpoint etc., [2] defining what defines different objects, and [3] the huge number of different things that exist. It also notes gaps in narrative understanding, shared concepts between humans and machines, and addressing diverse query contexts. The document advocates developing powerful yet simple visual features that capture uniqueness with invariance to irrelevant changes.
Lecture 03 internet video search



Lecture 03 internet video searchzukun The document discusses computer vision techniques for object detection and localization. It describes methods like selective search that group image regions hierarchically to propose object locations. Large datasets like ImageNet and LabelMe that provide training examples are also discussed. Performance on object detection benchmarks like PASCAL VOC is shown to improve significantly over time. Evaluation standards for concept detection like those used in TRECVID are presented. The document concludes that results are impressively improving each year but that the number of detectable concepts remains limited. It also discusses making feature extraction more efficient using techniques like SURF that take advantage of integral images.
Icml2012 tutorial representation_learning



Icml2012 tutorial representation_learningzukun This document provides an outline and overview of Yoshua Bengio's 2012 tutorial on representation learning. The key points covered include:
1) The tutorial will cover motivations for representation learning, algorithms such as probabilistic models and auto-encoders, and analysis and practical issues.
2) Representation learning aims to automatically learn good representations of data rather than relying on handcrafted features. Learning representations can help address challenges like exploiting unlabeled data and the curse of dimensionality.
3) Deep learning algorithms attempt to learn multiple levels of increasingly complex representations, with the goal of developing more abstract, disentangled representations that generalize beyond local patterns in the data.
Advances in discrete energy minimisation for computer vision



Advances in discrete energy minimisation for computer visionzukun This document discusses string algorithms and data structures. It introduces the Knuth-Morris-Pratt algorithm for finding patterns in strings in O(n+m) time where n is the length of the text and m is the length of the pattern. It also discusses common string data structures like tries, suffix trees, and suffix arrays. Suffix trees and suffix arrays store all suffixes of a string and support efficient pattern matching and other string operations in linear time or O(m+logn) time where m is the pattern length and n is the text length.
Gephi tutorial: quick start



Gephi tutorial: quick startzukun This document provides a tutorial on how to use Gephi software to analyze and visualize network graphs. It outlines the basic steps of importing a sample graph file, applying layout algorithms to organize the nodes, calculating metrics, detecting communities, filtering the graph, and exporting/saving the results. The tutorial demonstrates features of Gephi including node ranking, partitioning, and interactive visualization of the graph.
EM algorithm and its application in probabilistic latent semantic analysis



EM algorithm and its application in probabilistic latent semantic analysiszukun The document discusses the EM algorithm and its application in Probabilistic Latent Semantic Analysis (pLSA). It begins by introducing the parameter estimation problem and comparing frequentist and Bayesian approaches. It then describes the EM algorithm, which iteratively computes lower bounds to the log-likelihood function. Finally, it applies the EM algorithm to pLSA by modeling documents and words as arising from a mixture of latent topics.
Object recognition with pictorial structures



Object recognition with pictorial structureszukun This document describes an efficient framework for part-based object recognition using pictorial structures. The framework represents objects as graphs of parts with spatial relationships. It finds the optimal configuration of parts through global minimization using distance transforms, allowing fast computation despite modeling complex spatial relationships between parts. This enables soft detection to handle partial occlusion without early decisions about part locations.
Iccv2011 learning spatiotemporal graphs of human activities 



Iccv2011 learning spatiotemporal graphs of human activities zukun The document presents a new approach for learning spatiotemporal graphs of human activities from weakly supervised video data. The approach uses 2D+t tubes as mid-level features to represent activities as segmentation graphs, with nodes describing tubes and edges describing various relations. A probabilistic graph mixture model is used to model activities, and learning estimates the model parameters and permutation matrices using a structural EM algorithm. The learned models allow recognizing and segmenting activities in new videos through robust least squares inference. Evaluation on benchmark datasets demonstrates the ability to learn characteristic parts of activities and recognize them under weak supervision.
Ad
Recently uploaded (20)
Harmonizing Multi-Agent Intelligence | Open Data Science Conference | Gary Ar...



Harmonizing Multi-Agent Intelligence | Open Data Science Conference | Gary Ar...Gary Arora This deck from my talk at the Open Data Science Conference explores how multi-agent AI systems can be used to solve practical, everyday problems — and how those same patterns scale to enterprise-grade workflows.
I cover the evolution of AI agents, when (and when not) to use multi-agent architectures, and how to design, orchestrate, and operationalize agentic systems for real impact. The presentation includes two live demos: one that books flights by checking my calendar, and another showcasing a tiny local visual language model for efficient multimodal tasks.
Key themes include:
✅ When to use single-agent vs. multi-agent setups
✅ How to define agent roles, memory, and coordination
✅ Using small/local models for performance and cost control
✅ Building scalable, reusable agent architectures
✅ Why personal use cases are the best way to learn before deploying to the enterprise
RTP Over QUIC: An Interesting Opportunity Or Wasted Time?



RTP Over QUIC: An Interesting Opportunity Or Wasted Time?Lorenzo Miniero Slides for my "RTP Over QUIC: An Interesting Opportunity Or Wasted Time?" presentation at the Kamailio World 2025 event.
They describe my efforts studying and prototyping QUIC and RTP Over QUIC (RoQ) in a new library called imquic, and some observations on what RoQ could be used for in the future, if anything.
React Native for Business Solutions: Building Scalable Apps for Success



React Native for Business Solutions: Building Scalable Apps for SuccessAmelia Swank See how we used React Native to build a scalable mobile app from concept to production. Learn about the benefits of React Native development.
for more info : https://www.atoallinks.com/2025/react-native-developers-turned-concept-into-scalable-solution/
AI-proof your career by Olivier Vroom and David WIlliamson



AI-proof your career by Olivier Vroom and David WIlliamsonUXPA Boston This talk explores the evolving role of AI in UX design and the ongoing debate about whether AI might replace UX professionals. The discussion will explore how AI is shaping workflows, where human skills remain essential, and how designers can adapt. Attendees will gain insights into the ways AI can enhance creativity, streamline processes, and create new challenges for UX professionals.
AI’s influence on UX is growing, from automating research analysis to generating design prototypes. While some believe AI could make most workers (including designers) obsolete, AI can also be seen as an enhancement rather than a replacement. This session, featuring two speakers, will examine both perspectives and provide practical ideas for integrating AI into design workflows, developing AI literacy, and staying adaptable as the field continues to change.
The session will include a relatively long guided Q&A and discussion section, encouraging attendees to philosophize, share reflections, and explore open-ended questions about AI’s long-term impact on the UX profession.
論文紹介:"InfLoRA: Interference-Free Low-Rank Adaptation for Continual Learning" ...



論文紹介:"InfLoRA: Interference-Free Low-Rank Adaptation for Continual Learning" ...Toru Tamaki Yan-Shuo Liang, Wu-Jun Li,"Adaptive Plasticity Improvement for Continual Learning" CVPR2023
https://openaccess.thecvf.com/content/CVPR2023/html/Liang_Adaptive_Plasticity_Improvement_for_Continual_Learning_CVPR_2023_paper.html
Yan-Shuo Liang, Wu-Jun Li,"InfLoRA: Interference-Free Low-Rank Adaptation for Continual Learning" CVPR2024
https://openaccess.thecvf.com/content/CVPR2024/html/Liang_InfLoRA_Interference-Free_Low-Rank_Adaptation_for_Continual_Learning_CVPR_2024_paper.html
Refactoring meta-rauc-community: Cleaner Code, Better Maintenance, More Machines



Refactoring meta-rauc-community: Cleaner Code, Better Maintenance, More MachinesLeon Anavi RAUC is a widely used open-source solution for robust and secure software updates on embedded Linux devices. In 2020, the Yocto/OpenEmbedded layer meta-rauc-community was created to provide demo RAUC integrations for a variety of popular development boards. The goal was to support the embedded Linux community by offering practical, working examples of RAUC in action - helping developers get started quickly.
Since its inception, the layer has tracked and supported the Long Term Support (LTS) releases of the Yocto Project, including Dunfell (April 2020), Kirkstone (April 2022), and Scarthgap (April 2024), alongside active development in the main branch. Structured as a collection of layers tailored to different machine configurations, meta-rauc-community has delivered demo integrations for a wide variety of boards, utilizing their respective BSP layers. These include widely used platforms such as the Raspberry Pi, NXP i.MX6 and i.MX8, Rockchip, Allwinner, STM32MP, and NVIDIA Tegra.
Five years into the project, a significant refactoring effort was launched to address increasing duplication and divergence in the layer’s codebase. The new direction involves consolidating shared logic into a dedicated meta-rauc-community base layer, which will serve as the foundation for all supported machines. This centralization reduces redundancy, simplifies maintenance, and ensures a more sustainable development process.
The ongoing work, currently taking place in the main branch, targets readiness for the upcoming Yocto Project release codenamed Wrynose (expected in 2026). Beyond reducing technical debt, the refactoring will introduce unified testing procedures and streamlined porting guidelines. These enhancements are designed to improve overall consistency across supported hardware platforms and make it easier for contributors and users to extend RAUC support to new machines.
The community's input is highly valued: What best practices should be promoted? What features or improvements would you like to see in meta-rauc-community in the long term? Let’s start a discussion on how this layer can become even more helpful, maintainable, and future-ready - together.
DNF 2.0 Implementations Challenges in Nepal



DNF 2.0 Implementations Challenges in NepalICT Frame Magazine Pvt. Ltd. A national workshop bringing together government, private sector, academia, and civil society to discuss the implementation of Digital Nepal Framework 2.0 and shape the future of Nepal’s digital transformation.
Building Connected Agents: An Overview of Google's ADK and A2A Protocol



Building Connected Agents: An Overview of Google's ADK and A2A ProtocolSuresh Peiris Google's Agent Development Kit (ADK) provides a framework for building AI agents, including complex multi-agent systems. It offers tools for development, deployment, and orchestration.
Complementing this, the Agent2Agent (A2A) protocol is an open standard by Google that enables these AI agents, even if from different developers or frameworks, to communicate and collaborate effectively. A2A allows agents to discover each other's capabilities and work together on tasks.
In essence, ADK helps create the agents, and A2A provides the common language for these connected agents to interact and form more powerful, interoperable AI solutions.
Cybersecurity Threat Vectors and Mitigation



Cybersecurity Threat Vectors and MitigationVICTOR MAESTRE RAMIREZ Cybersecurity Threat Vectors and Mitigation
ICDCC 2025: Securing Agentic AI - Eryk Budi Pratama.pdf



ICDCC 2025: Securing Agentic AI - Eryk Budi Pratama.pdfEryk Budi Pratama Title: Securing Agentic AI: Infrastructure Strategies for the Brains Behind the Bots
As AI systems evolve toward greater autonomy, the emergence of Agentic AI—AI that can reason, plan, recall, and interact with external tools—presents both transformative potential and critical security risks.
This presentation explores:
> What Agentic AI is and how it operates (perceives → reasons → acts)
> Real-world enterprise use cases: enterprise co-pilots, DevOps automation, multi-agent orchestration, and decision-making support
> Key risks based on the OWASP Agentic AI Threat Model, including memory poisoning, tool misuse, privilege compromise, cascading hallucinations, and rogue agents
> Infrastructure challenges unique to Agentic AI: unbounded tool access, AI identity spoofing, untraceable decision logic, persistent memory surfaces, and human-in-the-loop fatigue
> Reference architectures for single-agent and multi-agent systems
> Mitigation strategies aligned with the OWASP Agentic AI Security Playbooks, covering: reasoning traceability, memory protection, secure tool execution, RBAC, HITL protection, and multi-agent trust enforcement
> Future-proofing infrastructure with observability, agent isolation, Zero Trust, and agent-specific threat modeling in the SDLC
> Call to action: enforce memory hygiene, integrate red teaming, apply Zero Trust principles, and proactively govern AI behavior
Presented at the Indonesia Cloud & Datacenter Convention (IDCDC) 2025, this session offers actionable guidance for building secure and trustworthy infrastructure to support the next generation of autonomous, tool-using AI agents.
Dark Dynamism: drones, dark factories and deurbanization



Dark Dynamism: drones, dark factories and deurbanizationJakub Šimek Startup villages are the next frontier on the road to network states. This book aims to serve as a practical guide to bootstrap a desired future that is both definite and optimistic, to quote Peter Thiel’s framework.
Dark Dynamism is my second book, a kind of sequel to Bespoke Balajisms I published on Kindle in 2024. The first book was about 90 ideas of Balaji Srinivasan and 10 of my own concepts, I built on top of his thinking.
In Dark Dynamism, I focus on my ideas I played with over the last 8 years, inspired by Balaji Srinivasan, Alexander Bard and many people from the Game B and IDW scenes.
accessibility Considerations during Design by Rick Blair, Schneider Electric



accessibility Considerations during Design by Rick Blair, Schneider ElectricUXPA Boston as UX and UI designers, we are responsible for creating designs that result in products, services, and websites that are easy to use, intuitive, and can be used by as many people as possible. accessibility, which is often overlooked, plays a major role in the creation of inclusive designs. In this presentation, you will learn how you, as a designer, play a major role in the creation of accessible artifacts.
Slack like a pro: strategies for 10x engineering teams



Slack like a pro: strategies for 10x engineering teamsNacho Cougil You know Slack, right? It's that tool that some of us have known for the amount of "noise" it generates per second (and that many of us mute as soon as we install it 😅).
But, do you really know it? Do you know how to use it to get the most out of it? Are you sure 🤔? Are you tired of the amount of messages you have to reply to? Are you worried about the hundred conversations you have open? Or are you unaware of changes in projects relevant to your team? Would you like to automate tasks but don't know how to do so?
In this session, I'll try to share how using Slack can help you to be more productive, not only for you but for your colleagues and how that can help you to be much more efficient... and live more relaxed 😉.
If you thought that our work was based (only) on writing code, ... I'm sorry to tell you, but the truth is that it's not 😅. What's more, in the fast-paced world we live in, where so many things change at an accelerated speed, communication is key, and if you use Slack, you should learn to make the most of it.
---
Presentation shared at JCON Europe '25
Feedback form:
http://tiny.cc/slack-like-a-pro-feedback
Agentic Automation - Delhi UiPath Community Meetup



Agentic Automation - Delhi UiPath Community MeetupManoj Batra (1600 + Connections) Original presentation of Delhi Community Meetup with the following topics
▶️ Session 1: Introduction to UiPath Agents
- What are Agents in UiPath?
- Components of Agents
- Overview of the UiPath Agent Builder.
- Common use cases for Agentic automation.
▶️ Session 2: Building Your First UiPath Agent
- A quick walkthrough of Agent Builder, Agentic Orchestration, - - AI Trust Layer, Context Grounding
- Step-by-step demonstration of building your first Agent
▶️ Session 3: Healing Agents - Deep dive
- What are Healing Agents?
- How Healing Agents can improve automation stability by automatically detecting and fixing runtime issues
- How Healing Agents help reduce downtime, prevent failures, and ensure continuous execution of workflows
Google DeepMind’s New AI Coding Agent AlphaEvolve.pdf



Google DeepMind’s New AI Coding Agent AlphaEvolve.pdfderrickjswork In a landmark announcement, Google DeepMind has launched AlphaEvolve, a next-generation autonomous AI coding agent that pushes the boundaries of what artificial intelligence can achieve in software development. Drawing upon its legacy of AI breakthroughs like AlphaGo, AlphaFold and AlphaZero, DeepMind has introduced a system designed to revolutionize the entire programming lifecycle from code creation and debugging to performance optimization and deployment.
May Patch Tuesday



May Patch TuesdayIvanti Ivanti’s Patch Tuesday breakdown goes beyond patching your applications and brings you the intelligence and guidance needed to prioritize where to focus your attention first. Catch early analysis on our Ivanti blog, then join industry expert Chris Goettl for the Patch Tuesday Webinar Event. There we’ll do a deep dive into each of the bulletins and give guidance on the risks associated with the newly-identified vulnerabilities.
DevOpsDays SLC - Platform Engineers are Product Managers.pptx



DevOpsDays SLC - Platform Engineers are Product Managers.pptxJustin Reock Platform Engineers are Product Managers: 10x Your Developer Experience
Discover how adopting this mindset can transform your platform engineering efforts into a high-impact, developer-centric initiative that empowers your teams and drives organizational success.
Platform engineering has emerged as a critical function that serves as the backbone for engineering teams, providing the tools and capabilities necessary to accelerate delivery. But to truly maximize their impact, platform engineers should embrace a product management mindset. When thinking like product managers, platform engineers better understand their internal customers' needs, prioritize features, and deliver a seamless developer experience that can 10x an engineering team’s productivity.
In this session, Justin Reock, Deputy CTO at DX (getdx.com), will demonstrate that platform engineers are, in fact, product managers for their internal developer customers. By treating the platform as an internally delivered product, and holding it to the same standard and rollout as any product, teams significantly accelerate the successful adoption of developer experience and platform engineering initiatives.
Integrating FME with Python: Tips, Demos, and Best Practices for Powerful Aut...



Integrating FME with Python: Tips, Demos, and Best Practices for Powerful Aut...Safe Software FME is renowned for its no-code data integration capabilities, but that doesn’t mean you have to abandon coding entirely. In fact, Python’s versatility can enhance FME workflows, enabling users to migrate data, automate tasks, and build custom solutions. Whether you’re looking to incorporate Python scripts or use ArcPy within FME, this webinar is for you!
Join us as we dive into the integration of Python with FME, exploring practical tips, demos, and the flexibility of Python across different FME versions. You’ll also learn how to manage SSL integration and tackle Python package installations using the command line.
During the hour, we’ll discuss:
-Top reasons for using Python within FME workflows
-Demos on integrating Python scripts and handling attributes
-Best practices for startup and shutdown scripts
-Using FME’s AI Assist to optimize your workflows
-Setting up FME Objects for external IDEs
Because when you need to code, the focus should be on results—not compatibility issues. Join us to master the art of combining Python and FME for powerful automation and data migration.
Skiena algorithm 2007 lecture02 asymptotic notation
- 1. Lecture 2: Asymptotic Notation Steven Skiena Department of Computer Science State University of New York Stony Brook, NY 11794–4400 http://www.cs.sunysb.edu/∼skiena
- 2. Problem of the Day The knapsack problem is as follows: given a set of integers S = {s1, s2, . . . , sn}, and a given target number T , find a subset of S which adds up exactly to T . For example, within S = {1, 2, 5, 9, 10} there is a subset which adds up to T = 22 but not T = 23. Find counterexamples to each of the following algorithms for the knapsack problem. That is, give an S and T such that the subset is selected using the algorithm does not leave the knapsack completely full, even though such a solution exists.
- 3. Solution • Put the elements of S in the knapsack in left to right order if they fit, i.e. the first-fit algorithm? • Put the elements of S in the knapsack from smallest to largest, i.e. the best-fit algorithm? • Put the elements of S in the knapsack from largest to smallest?
- 4. The RAM Model of Computation Algorithms are an important and durable part of computer science because they can be studied in a machine/language independent way. This is because we use the RAM model of computation for all our analysis. • Each “simple” operation (+, -, =, if, call) takes 1 step. • Loops and subroutine calls are not simple operations. They depend upon the size of the data and the contents of a subroutine. “Sort” is not a single step operation.
- 5. • Each memory access takes exactly 1 step. We measure the run time of an algorithm by counting the number of steps, where: This model is useful and accurate in the same sense as the flat-earth model (which is useful)!
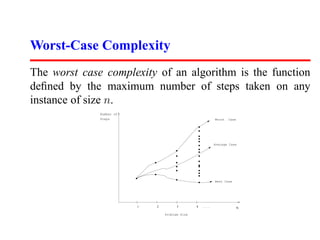
- 6. Worst-Case Complexity The worst case complexity of an algorithm is the function defined by the maximum number of steps taken on any instance of size n. Number of Steps Worst Case Average Case . . Best Case 1 2 3 4 ...... N Problem Size
- 7. Best-Case and Average-Case Complexity The best case complexity of an algorithm is the function defined by the minimum number of steps taken on any instance of size n. The average-case complexity of the algorithm is the function defined by an average number of steps taken on any instance of size n. Each of these complexities defines a numerical function: time vs. size!
- 8. Exact Analysis is Hard! Best, worst, and average are difficult to deal with precisely because the details are very complicated: 1 2 3 4 ...... It easier to talk about upper and lower bounds of the function. Asymptotic notation (O, Θ, Ω) are as well as we can practically deal with complexity functions.
- 9. Names of Bounding Functions • g(n) = O(f (n)) means C × f (n) is an upper bound on g(n). • g(n) = Ω(f (n)) means C ×f (n) is a lower bound on g(n). • g(n) = Θ(f (n)) means C1 × f (n) is an upper bound on g(n) and C2 × f (n) is a lower bound on g(n). C, C1, and C2 are all constants independent of n.
- 10. O, Ω, and Θ c1*g(n) c*g(n) f(n) f(n) f(n) c*g(n) c2*g(n) n n n n0 n0 n0 (a) (b) (c) The definitions imply a constant n0 beyond which they are satisfied. We do not care about small values of n.
- 11. Formal Definitions • f (n) = O(g(n)) if there are positive constants n0 and c such that to the right of n0, the value of f (n) always lies on or below c · g(n). • f (n) = Ω(g(n)) if there are positive constants n0 and c such that to the right of n0, the value of f (n) always lies on or above c · g(n). • f (n) = Θ(g(n)) if there exist positive constants n0 , c1, and c2 such that to the right of n0 , the value of f (n) always lies between c1 · g(n) and c2 · g(n) inclusive.
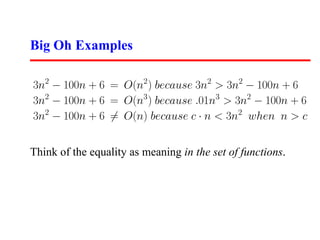
- 12. Big Oh Examples 3n2 − 100n + 6 = O(n2 ) because 3n2 > 3n2 − 100n + 6 3n2 − 100n + 6 = O(n3 ) because .01n3 > 3n2 − 100n + 6 3n2 − 100n + 6 = O(n) because c · n < 3n2 when n > c Think of the equality as meaning in the set of functions.
- 13. Big Omega Examples 3n2 − 100n + 6 = Ω(n2 ) because 2.99n2 < 3n2 − 100n + 6 3n2 − 100n + 6 = Ω(n3 ) because 3n2 − 100n + 6 < n3 1010 3n − 100n + 6 = Ω(n) because 10 n < 3n2 − 100 + 6 2
- 14. Big Theta Examples 3n2 − 100n + 6 = Θ(n2 ) because O and Ω 3n2 − 100n + 6 = Θ(n3 ) because O only 3n2 − 100n + 6 = Θ(n) because Ω only
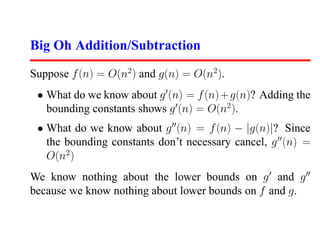
- 15. Big Oh Addition/Subtraction Suppose f (n) = O(n2 ) and g(n) = O(n2 ). • What do we know about g (n) = f (n) + g(n)? Adding the bounding constants shows g (n) = O(n2 ). • What do we know about g (n) = f (n) − |g(n)|? Since the bounding constants don’t necessary cancel, g (n) = O(n2 ) We know nothing about the lower bounds on g and g because we know nothing about lower bounds on f and g.
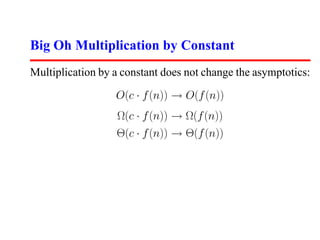
- 16. Big Oh Multiplication by Constant Multiplication by a constant does not change the asymptotics: O(c · f (n)) → O(f (n)) Ω(c · f (n)) → Ω(f (n)) Θ(c · f (n)) → Θ(f (n))
- 17. Big Oh Multiplication by Function But when both functions in a product are increasing, both are important: O(f (n)) ∗ O(g(n)) → O(f (n) ∗ g(n)) Ω(f (n)) ∗ Ω(g(n)) → Ω(f (n) ∗ g(n)) Θ(f (n)) ∗ Θ(g(n)) → Θ(f (n) ∗ g(n))




