Ad
Software archiecture lecture05
- 2. Introduction • Functionality often takes not only the front seat in the development scheme but the only seat. • Systems are frequently redesigned not because they are functionally deficient—the replacements are often functionally identical—but because they are difficult to ▫ maintain, port, or scale, or are too slow, or have been compromised by network hackers. • We said that architecture was the first stage in software creation in which quality requirements could be addressed. • It is the mapping of a system's functionality onto software structures that determines the architecture's support for qualities
- 3. Functionality and Architecture • Functionality and quality attributes are orthogonal (independent). • Functionality is the ability of the system to do the work for which it was intended • A task requires that many or most of the system's elements work in a coordinated manner to complete the job. • Software architecture constrains its allocation to structure when other quality attributes are important.
- 4. Architecture and Quality Attributes • Satisfactory results are a matter of getting the big picture (architecture) as well as the details (implementation) correct. • Example: ▫ Usability involves both architectural and nonarchitectural aspects. ▫ Modifiability is determined by how functionality is divided (architectural) and by coding techniques within a module (nonarchitectural). ▫ Performance involves both architectural and nonarchitectural dependencies
- 5. Architecture and Quality Attributes • Within complex systems, quality attributes can never be achieved in isolation. ▫ The achievement of any one will have an effect on the achievement of others (both + , -)
- 6. Quality attributes • We will examine the following three classes: ▫ Qualities of the system. We will focus on availability, modifiability, performance, security, testability, and usability. ▫ Business qualities (such as time to market) that are affected by the architecture. ▫ Qualities, such as conceptual integrity, that are about the architecture itself although they indirectly affect other qualities, such as modifiability.
- 7. System Quality Attributes • There are a variety of published taxonomies and definitions for System Quality Attributes • From an architect's perspective, there are three problems with those definitions: ▫ The definitions provided for an attribute are not operational ▫ A focus of discussion is often on which quality a particular aspect belongs to. ▫ Each attribute community has developed its own vocabulary. • Problem 1 & 2 solve by Quality Attribute Scenarios • Problem 3 solve by provide a brief discussion of each attribute
- 8. Quality Attribute Scenarios • A quality attribute scenario is a quality-attribute- specific requirement. • It consists of six parts. ▫ Source of stimulus ▫ Stimulus ▫ Environment ▫ Artifact ▫ Response ▫ Response measure
- 9. Quality Attribute Scenarios • Source of stimulus. ▫ This is some entity (a human, a computer system, or any other actuator) that generated the stimulus. • Stimulus. ▫ The stimulus is a condition that needs to be considered when it arrives at a system. • Environment. ▫ The stimulus occurs within certain conditions. The system may be in an overload condition or may be running when the stimulus occurs, or some other condition may be true.
- 10. Quality Attribute Scenarios • Artifact. ▫ Some artifact is stimulated. This may be the whole system or some pieces of it. • Response. ▫ The response is the activity undertaken after the arrival of the stimulus. • Response measure. ▫ When the response occurs, it should be measurable in some fashion so that the requirement can be tested.
- 11. General Scenarios VS Concrete Scenarios • General quality attribute scenarios (general scenarios) ▫ those that are system independent and can, potentially, pertain to any system • concrete quality attribute scenarios (concrete scenarios) ▫ those that are specific to the particular system under consideration
- 12. Availability Scenario • Not every system-specific scenario has all of the six parts. • The parts that are necessary are Response & Response Measure
- 13. Quality Attribute Scenarios in Practice • To do Quality Attribute Scenario Generation in a disciplined way ▫ We use the quality-attribute-specific tables to create general scenarios and from these derive system-specific scenario ▫ Not all of the possible general scenarios are created ▫ The tables serve as a checklist to ensure that all possibilities have been considered
- 14. Availability
- 15. Availability • Availability is concerned with system failure and its associated consequences • A system failure occurs when the system no longer delivers a service consistent with its specification. • The availability of a system is calculated by • From this come terms like 99.9% availability • Scheduled downtimes are not considered when calculating availability
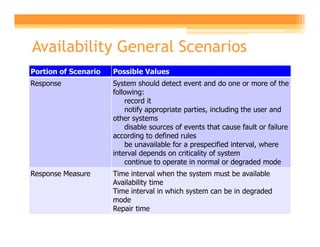
- 16. Availability General Scenarios Portion of Scenario Possible Values Source Internal to the system; external to the system Stimulus Fault: omission, crash, timing, response Artifact System's processors, communication channels, persistent storage, processes Environment Normal operation; degraded mode (i.e., fewer features, a fall back solution)
- 17. Availability General Scenarios Portion of Scenario Possible Values Response System should detect event and do one or more of the following: record it notify appropriate parties, including the user and other systems disable sources of events that cause fault or failure according to defined rules be unavailable for a prespecified interval, where interval depends on criticality of system continue to operate in normal or degraded mode Response Measure Time interval when the system must be available Availability time Time interval in which system can be in degraded mode Repair time
- 18. Sample availability scenario “An external message is received by a process during normal operation. The process informs the operator of the receipt of the message and continues to operate with no downtime.”
- 19. Modifiability
- 20. Modifiability • Modifiability is about the cost of change ▫ What can change ? (the artifact) ▫ When is the change made and who makes it ? (the environment)
- 21. Modifiability General Scenarios Portion of Scenario Possible Values Source End user, developer, system administrator Stimulus Wishes to add/delete/modify/vary functionality, quality attribute, capacity Artifact System user interface, platform, environment; system that interoperates with target system Environment At runtime, compile time, build time, design time Response Locates places in architecture to be modified; makes modification without affecting other functionality; tests modification; deploys modification Response Measure Cost in terms of number of elements affected, effort, money; extent to which this affects other functions or quality attributes
- 22. Sample modifiability scenario "A developer wishes to change the user interface to make a screen's background color blue. This change will be made to the code at design time. It will take less than three hours to make and test the change and no side effect changes will occur in the behavior."
- 23. Performance
- 24. Performance • Performance is about timing. • Basically performance is concerned with how long it takes the system to respond when an event occurs. • One of the things that make performance complicated is the number of event sources and arrival patterns.
- 25. Performance General Scenarios Portion of Scenario Possible Values Source One of a number of independent sources, possibly from within system Stimulus Periodic events arrive; sporadic events arrive; stochastic events arrive Artifact System Environment Normal mode; overload mode Response Processes stimuli; changes level of service Response Measure Latency, deadline, throughput, jitter, miss rate, data loss
- 26. Sample performance scenario “Users initiate 1,000 transactions per minute stochastically under normal operations, and these transactions are processed with an average latency of two seconds."
- 27. Security
- 28. Security • Security is a measure of the system's ability to resist unauthorized usage while still providing its services to legitimate users • Security can be characterized as a system providing nonrepudiation, confidentiality, integrity, assurance, availability, and auditing
- 29. Security General Scenarios Portion of Possible Values Scenario Source Individual or system that is correctly identified, identified incorrectly, of unknown identity who is internal/external, authorized/not authorized with access to limited resources, vast resources Stimulus Tries to display data, change/delete data, access system services, reduce availability to system services Artifact System services; data within system Environment Either online or offline, connected or disconnected, firewalled or open
- 30. Security General Scenarios Portion of Possible Values Scenario Response Authenticates user; hides identity of the user; blocks access to data and/or services; allows access to data and/or services; grants or withdraws permission to access data and/or services; records access/modifications or attempts to access/modify data/services by identity; stores data in an unreadable format; recognizes an unexplainable high demand for services, and informs a user or another system, and restricts availability of services Response Time/effort/resources required to circumvent security measures Measure with probability of success; probability of detecting attack; probability of identifying individual responsible for attack or access/modification of data and/or services; percentage of services still available under denial-of-services attack; restore data/services; extent to which data/services damaged and/or legitimate access denied
- 31. Sample security scenario • A correctly identified individual tries to modify system data from an external site; system maintains an audit trail and the correct data is restored within one day.
- 32. Testability
- 33. Testability • Software testability refers to the ease with which software can be made to demonstrate its faults through testing • At least 40% of the cost of developing well- engineered systems is taken up by testing • Testing is done by various developers, testers, verifiers, or users • The response measures for testability deal with ▫ how effective the tests are in discovering faults ▫ how long it takes to perform the tests to some desired level of coverage.
- 34. Testability General Scenarios Portion of Possible Values Scenario Source Unit developer Increment integrator System verifier Client acceptance tester System user Stimulus Analysis, architecture, design, class, subsystem integration completed; system delivered Artifact Piece of design, piece of code, complete application Environment At design time, at development time, at compile time, at deployment time Response Provides access to state values; provides computed values; prepares test environment Response Measure Percent executable statements executed Probability of failure if fault exists Time to perform tests Length of longest dependency chain in a test Length of time to prepare test environment
- 35. Sample Testability scenario • A unit tester performs a unit test on a completed system component that provides an interface for controlling its behavior and observing its output; 85% path coverage is achieved within three hours.
- 36. Usability
- 37. Usability • Usability is concerned with ▫ how easy it is for the user to accomplish a desired task ▫ the kind of user support the system provides • It can be broken down into following areas: ▫ Learning system features ▫ Using a system efficiently ▫ Minimizing the impact of errors ▫ Adapting the system to user needs ▫ Increasing confidence and satisfaction • The normal development process detects usability problems through building prototypes and user testing
- 38. Usability General Scenarios Portion of Possible Values Scenario Source End user Stimulus Wants to learn system features; use system efficiently; minimize impact of errors; adapt system; feel comfortable Artifact System Environment At runtime or configure time Response System provides one or more of the following responses: to support "learn system features" help system is sensitive to context; interface is familiar to user; interface is usable in an unfamiliar context to "adapt system": customizability; internationalization
- 39. Usability General Scenarios Portion of Possible Values Scenario Response to support "use system efficiently": aggregation of data and/or commands; re-use of already entered data and/or commands; support for efficient navigation within a screen; distinct views with consistent operations; comprehensive searching; multiple simultaneous activities to "minimize impact of errors": undo, cancel, recover from system failure, recognize and correct user error, retrieve forgotten password, verify system resources to "feel comfortable": display system state; work at the user's pace Response Task time, number of errors, number of problems solved, user Measure satisfaction, gain of user knowledge, ratio of successful operations to total operations, amount of time/data lost
- 40. Sample Usability scenario • A user, wanting to minimize the impact of an error, wishes to cancel a system operation at runtime; cancellation takes place in less than one second
- 41. Communicating Concepts Using General Scenarios • We use general scenarios to enable stakeholders to communicate. • Facilitating the understanding of vocabulary aids discussions of architectural decisions • The problem for the architect is to understand which of these stimuli represent the same occurrence, which are aggregates of other stimuli, and which are independent • Once the relations are clear, the architect can communicate them to the various stakeholders using language that each understand.
- 42. Communicating Concepts Using General Scenarios Quality Stimulus Attribute Availability Unexpected event, nonoccurrence of expected event Modifiability Request to add/delete/change/vary functionality, platform, quality attribute, or capacity Performance Periodic, stochastic, or sporadic Security Tries to display, modify, change/delete information, access, or reduce availability to system services Testability Completion of phase of system development Usability Wants to learn system features, use a system efficiently, minimize the impact of errors, adapt the system, feel comfortable
- 43. Other System Quality Attributes • A number of other attributes can be found in the attribute taxonomies in the research literature and in standard software engineering textbooks ▫ Scalability ▫ Portability ▫ Interoperability • If some quality is important to your organization, it is reasonable to create your own general scenario for it
- 44. Business Qualities • A number of business quality goals frequently shape a system's architecture • They need to be made specific with scenarios in order to make them suitable for influencing the design process and to be made testable • Business Qualities ▫ Time to market ▫ Cost and benefit ▫ Projected lifetime of the system ▫ Targeted market ▫ Rollout schedule ▫ Integration with legacy systems
- 45. Architecture Qualities • There are also qualities directly related to the architecture itself that are important to achieve ▫ Conceptual integrity is the underlying theme or vision that unifies the design of the system at all levels ▫ Correctness and completeness are essential for the architecture to allow for all of the system's requirements and runtime resource constraints to be met ▫ Buildability It refers to the ease of constructing a desired system and is achieved architecturally by paying careful attention to the decomposition into modules
- 46. Summary • The qualities presented in this chapter represent those most often the goals of software architects. • Since their definitions overlap, we chose to characterize them with general scenarios. • We saw that qualities can be divided into ▫ those that apply to the system ▫ those that apply to the business environment ▫ those that apply to the architecture itself