Do Design Quality and Code Quality Matter in Merger and Acquisition Tech Due Diligence?
- 1. © 2019 Synopsys, Inc.1 Do Design Quality and Code Quality Matter in M&A Tech Due Diligence? (Spoiler: Yes) Niles Madison, Synopsys Dan Sturtevant, Silverthread
- 2. © 2019 Synopsys, Inc.2 Speakers Niles Madison Senior Manager Black Duck Audits Group Dan Sturtevant Founder/CEO Silverthread
- 3. © 2019 Synopsys, Inc.3 Agenda M&A due diligence and quality risk Understanding code quality Understanding design quality Assessing quality in due diligence Q&A
- 4. © 2019 Synopsys, Inc.4 M&A due diligence and quality risk
- 5. © 2019 Synopsys, Inc.5 Functions of M&A due diligence • Confirm premises for doing the deal • Gather information to plan for integration • Identify unknown risks
- 6. © 2019 Synopsys, Inc.6 Software risk technical due diligence Product / strategy People Process / tools Architecture Code Strategic acquirer performs PE firms may contract out Our focus today is on risks in the software
- 7. © 2019 Synopsys, Inc.7 Architecture Dimensions of software risk Open source and third party Proprietary Software development process Legal Security Quality
- 8. © 2019 Synopsys, Inc.8 Poor-quality software can slow integration and blow the business case for an acquisition • Poor code quality: lots to fix • Poor design quality: fixing is slow (including fixing legal and security issues) Source: Silverthread, Inc. Unhealthy codebase Developer productivity 8 Features/year Developer time fixing bugs 69% Healthy codebase Developer productivity 20 Features/year Developer time fixing bugs 20% Occurrence Severity Description 62.02% BLOCKER High probability of impact on system behavior Must be fixed immediately 85.46% CRITICAL Lower probability of impact on system behavior Must be reviewed immediately 96.14% MAJOR High impact on developer productivity 95.55% MINOR Some impact on developer productivity 72.70% INFO Could be an issue 96.44% Any project with an issue (excluding INFO) Source: Black Duck Quality Audits
- 9. © 2019 Synopsys, Inc.9 Understanding code quality
- 10. © 2019 Synopsys, Inc.10 Quality risk Perhaps not as acute as security and license risk, but insidious • You won’t get sued or breached, but… – Products may: – Be hard to enhance/maintain – Suffer significant technical debt – Not scale – Be buggy – There can be a drag on every fix or feature – You may need to redesign/refactor – You may need to hire more senior developers
- 11. © 2019 Synopsys, Inc.11 Sample of metrics: • File issues vs. complexity • Average and number of high-complexity files/methods • Number of large packages, files, and methods • Amount of duplicated code (i.e., code redundancy/rework)
- 12. © 2019 Synopsys, Inc.12 Understanding design quality
- 13. © 2019 Synopsys, Inc.13 Code quality vs. design quality Individual lines of code or functional parts Architecture of a codebase CODE QUALITY DESIGN QUALITY TECHNICAL HEALTH Good Bad Good Bad vs. vs.
- 14. © 2019 Synopsys, Inc.14 Design quality matters goal • Agility • Predictability • Schedule • Safety • Cloud readiness • Cyber resilience Technical Programmatic Unhealthy codebase Developer productivity 8 Features/year Developer time fixing bugs 69% Healthy codebase Developer productivity 20 Features/year Developer time fixing bugs 20% • Revenue generation • Cost reduction • Optionality for new businesses Economics vs.
- 15. © 2019 Synopsys, Inc.15 Elements of architectural health Layered API Layer compromised API circumvented Cyclicality Healthy architectureUnhealthy architecture Modular Hierarchical dependence Module too big Source: Silverthread, Inc.
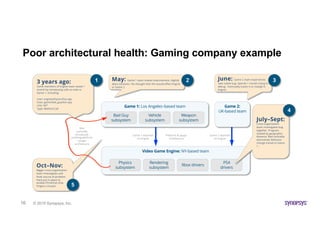
- 16. © 2019 Synopsys, Inc.16 Poor architectural health: Gaming company example Oct–Nov: Bigger cross-organization team investigates and finds source of problem. Hack put in place to enable Christmas ship. Fingers crossed. Video Game Engine: NY-based team Physics subsystem Xbox drivers PS4 drivers Game 1: Los Angeles–based team Vehicle subsystem Bad Guy subsystem Weapon subsystem 3 years ago: Some members of Engine team saved 1 month by introducing calls to code in Game 1, including: User: engine/physics/foo.cpp Uses: game/bad_guy/bar.cpp Line: 407 Type: Method Call Bad cyclicality introduced, violating platform / plugin architecture Platform & plugin architecture May: Game 1 team makes improvement, slightly alters behavior. No thought that this would affect Engine or Game 2. June: Game 2 team experiences new subtle bug. Spends 1 month trying to debug. Eventually traces it to change in Engine. July–Sept: Cross-organization team investigates bug together. Progress slowed by geographic distance. Bad cyclicality discovered. Behavior change traced to Game 1. Game 1 depends on Engine Game 2 depends on Engine 31 2 4 5 Game 2: UK-based team Rendering subsystem
- 17. © 2019 Synopsys, Inc.17 Assessing quality in due diligence
- 18. © 2019 Synopsys, Inc.18 Code quality audit • Method: Automated static code analysis / expert human review • Requires: Access to source code and libraries • Focus: Quality of coding at the file and method level relative to the industry • Evaluates: Coding practices, structure complexity, commenting, errors • Sample of metrics: – File issues vs. complexity – Average and number of high-complexity files/methods – Number of large packages, files, and methods – Amount of duplicated code (i.e., code redundancy/rework) Is the code well-written?
- 19. © 2019 Synopsys, Inc.19 Design quality audit • Method: Automated analysis / expert human review, powered by CodeMRI® from Silverthread • Requires: Access to source code and libraries • Focus: Quality of design at the architectural level • Evaluates: Architecture, modularity, layering, APIs, cyclicality • Sample of metrics: – Economic impact – Size and number of core (tangles) – File interdependencies Is the architecture healthy?
- 20. © 2019 Synopsys, Inc.20 Conclusions • It’s important to understand the holistic risk when evaluating software assets in M&A (and beyond) • Poor-quality design and code can slow integration and impede fixing and improving software • It’s important to assess all aspects of quality
- 21. © 2019 Synopsys, Inc.21 Q&A