Ad
SolarWinds Patch Manager - How does it compare to SCCM Patch Management?
- 1. Author Jennifer Kuvlesky SolarWinds Patch Manager Compared to SCCM Patch Management Keep Patching Simple & Affordable SOLARWINDS PATCH MANAGER COMPARED TO SCCM PATCH MANAGEMENT 1
- 2. Agenda » Patching Simplified – SolarWinds Patch Manager » SolarWinds Patch Manager High Points » SolarWinds Patch Survey » SCCM Vs. SolarWinds Patch Manager Comparison » Dashboard » What IT Pros say about Patch Manager » Helpful Resources SOLARWINDS PATCH MANAGER COMPARED TO SCCM PATCH MANAGEMENT 2
- 3. Patching simplified with SolarWinds Patch Manager At SolarWinds, we keep things super simple right from: Download Install to Purchase Daily Use Our newly updated product, SolarWinds Patch Manager, has all these characteristics. If your goal is to Keep Patching Simple and affordable choose: SolarWinds Patch Manager, the champion solution for patching SOLARWINDS PATCH MANAGER COMPARED TO SCCM PATCH MANAGEMENT 3
- 4. SolarWinds Patch Manager High Points » Reduce time from weeks to minutes for patching physical & virtual Windows® desktops & servers with pre-built, tested patches from vendors such as Adobe®, Apple®, Google®, Mozilla®, Oracle® & others » Decrease security risks & service performance degradation by controlling when & where patches are applied » Pass audits & demonstrate compliance with out-of-the-box reports & dashboard views » Turn your WSUS or System Center Configuration Manager environment into a powerful patch management solution » Patch Manager provides the best ROI with agentless architecture, mass scale, and ease of use – no scripting or professional services needed SOLARWINDS PATCH MANAGER COMPARED TO SCCM PATCH MANAGEMENT 4
- 5. SolarWinds Patch Survey We recently surveyed the patch management community and got some interesting data back regarding what applications users patch with different tools. The majority of respondents patch Microsoft with WSUS, and secondly System Center Configuration Manager. SOLARWINDS PATCH MANAGER COMPARED TO SCCM PATCH MANAGEMENT 5
- 6. SCCM Users Patching 3rd Party Application ConfigMgr users perform 3rd party application patching more frequently. »Only 11% of SCCM users do not patch 3rd party apps at all However, System Center users are still spending a lot of time patching 3 rd party apps. »Only 30% are using a tool that provides automated 3rd party pre-built packages, like Patch Manager. SOLARWINDS PATCH MANAGER COMPARED TO SCCM PATCH MANAGEMENT 6
- 7. SCCM - 3rd Party Applications Patching There is a misconception that System Center Configuration manager is very effective at patching 3rd party applications. The SCCM users patching 3rd party applications spend on average 3.8 hours researching, scripting, publishing and testing each 3rd party update, and spend an average of 3 days deploying the update. »On average, Patch Manager customers surveyed spend 2.5 hours patching 3rd party updates. SOLARWINDS PATCH MANAGER COMPARED TO SCCM PATCH MANAGEMENT 7
- 8. SCCM – SolarWinds Patch Manager Comparison SolarWinds Capability SCCM Patch Manager Yes, via WSUS & SCCM. Centralized & automated Patch Manager Yes, Microsoft & SCUP software installation leverages this robust feature of these tools. On Demand Patching N/A YES For System Center Essentials (SCE) environments, which Application Inventory use WSUS natively, they enable the use of Microsoft & 3rd party applications, hardware the WSUS/WUAgent. inventory, disk space & The Extended other metrics Inventory collection tool, includes software and hardware inventory. SOLARWINDS PATCH MANAGER COMPARED TO SCCM PATCH MANAGEMENT 8
- 9. SCCM – SolarWinds Patch Manager Comparison SolarWinds Capability SCCM Patch Manager Requires some Reporting – visibility into knowledge of SQL Yes. Custom reporting what needs to be programming as well as requires no SQL patched/what has been administration of SQL programming or patched. Server Reporting scripting Services (SSRS). Filtered Views N/A YES Scheduled Approvals YES N/A SOLARWINDS PATCH MANAGER COMPARED TO SCCM PATCH MANAGEMENT 9
- 10. SCCM – SolarWinds Patch Manager Comparison SolarWinds Capability SCCM Patch Manager Yes. Provides Notification of failed information via the updates N/A client log file as to why the update failed. Yes, push patches at discrete times to accommodate different time zones Patch Scheduling YES and network impacts of patching large numbers of endpoints. SOLARWINDS PATCH MANAGER COMPARED TO SCCM PATCH MANAGEMENT 10
- 11. SCCM – SolarWinds Patch Manager Comparison SolarWinds Capability SCCM Patch Manager 3rd party pre-built & Only for catalogued Yes. for most common tested packages patches applications Wizard driven. Includes PackageBoot™ for Custom package creation Requires SCUP complex before and after deployment scenarios (Java). Client health diagnosis & Repair WMI, WUAgent, Client health data and Configuration remediation Manager Agent. SOLARWINDS PATCH MANAGER COMPARED TO SCCM PATCH MANAGEMENT 11
- 12. Complexity Reduction with SolarWinds Patch Manager Patch Manager is a great add-on for any SCCM environment. The top Patch Manager features which have benefited customers patching Microsoft applications include Scheduling Reporting and Filtering capabilities Customers patching 3rd party applications appreciate the pre-tested & pre-built 3rd party applications as well as the ability to create custom packages and perform pre-and post deployment scenarios. Patch Manager has native integration with System Center Configuration Manager 2012. Check out this short video to see 3rd party updates directly from the Software Library page of the Configuration Manager 2012 console. SOLARWINDS PATCH MANAGER COMPARED TO SCCM PATCH MANAGEMENT 12
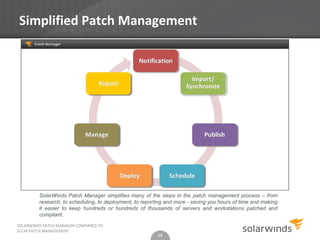
- 13. Simplified Patch Management SolarWinds Patch Manager simplifies many of the steps in the patch management process – from research, to scheduling, to deployment, to reporting and more - saving you hours of time and making it easier to keep hundreds or hundreds of thousands of servers and workstations patched and compliant. SOLARWINDS PATCH MANAGER COMPARED TO SCCM PATCH MANAGEMENT 13
- 14. Centralized Patching of Microsoft Servers and Third-Party Apps SolarWinds Patch Manager enables you to deploy and manage both third-party applications and Microsoft patches, from a central point of control, across tens of thousands of servers and workstations. Microsoft SCUP and complicated scripting NOT required. SOLARWINDS PATCH MANAGER COMPARED TO SCCM PATCH MANAGEMENT 14
- 15. Pre-Tested, Pre-Built Packages for Common Apps A full suite of package management tools: Create, Duplicate, Edit, Publish, Delete, Export to Catalog and Import from Catalog rd 3 party updates accessible in the Configuration Manager 2012 console ready for publishing to your Software Update Point Client health, monitoring and management tools available in Assets and Compliance SolarWinds builds, tests and automatically delivers packages for common third-party applications which can then be quickly and easily deployed using Microsoft SCCM. Visualize 3 rd party updates available right in the Configuration Manager 2012 console. SOLARWINDS PATCH MANAGER COMPARED TO SCCM PATCH MANAGEMENT 15
- 16. Advanced Before-and-After Package Deployment Actions SolarWinds Patch Manager’s PackageBoot™ allows you to create advanced before and after package deployment scenarios to ensure that even the most complicated patches (such as Oracle Java) get deployed successfully – without complicated scripting. SOLARWINDS PATCH MANAGER COMPARED TO SCCM PATCH MANAGEMENT 16
- 17. Flexible Patch Scheduling Schedule patch approvals and deployment of updates within maintenance windows. SOLARWINDS PATCH MANAGER COMPARED TO SCCM PATCH MANAGEMENT 17
- 18. Extends Microsoft® SCCM In addition to providing ready-to-deploy patches for third-party apps, SolarWinds Patch Manager helps you get more out of Microsoft SCCM with enhanced client health diagnostics and remediation, expanded collections views, and WMI repair. SOLARWINDS PATCH MANAGER COMPARED TO SCCM PATCH MANAGEMENT 18
- 19. What IT Pros say about SolarWinds Patch Manager “It used to take four hours per patch for packaging and testing and about a week to deploy each patch,” said Jay. “Now with Patch Manager, it takes an hour tops - It is incredible.” - Jay Harper - IT Network Administrator, Terminix Service, Inc. “I’m very happy with this software and the support services offered. I’m not sure how Solar Winds taking over will affect the company. In the short term, though, I’ve seen that there has been a large price decrease (almost 50%!) and a couple discounts added on. This will definitely decrease some headaches I’ve gotten from working with other products that either require an agent, or haven’t been updated since 1998. The key thing for me with this software is the third-party packages, but I’m not going to complain about better reporting and more granular control” - Lauren Malhoit, TechRepublic “What I especially liked about Patch Manager was that it is a big time saver. The software didn’t have a steep learning curve and it didn’t require third party patches to be manually packaged like some competing solutions do.” - Brien M. Posey, WindowsNetworking.com SOLARWINDS PATCH MANAGER COMPARED TO SCCM PATCH MANAGEMENT 19
- 20. Helpful Resources We invite you to learn more about SolarWinds Patch Manager Watch Video Test Drive Live Demo Ask Our Community Download 30-day Free Trial Whitepaper Top 10 Diagnostics Tips for Explore Features Client Troubleshooting with SCCM Click any of the links above SOLARWINDS PATCH MANAGER COMPARED TO SCCM PATCH MANAGEMENT 20
- 21. Thank You! 21