Splunk for Security: Background & Customer Case Study
Download as PPTX, PDF8 likes1,697 views
Presented at SplunkLive! Denver on August 4, 2015; provides background on the Splunk value proposition for security use cases based on actual experience, a walkthrough of a Splunk engagement at a major national healthcare customer, and examples of three use cases that provided actionable value beyond what was possible with the previous SIEM solution.
1 of 29
Downloaded 81 times



















![22
Use Case: Off-Network Jumping
• Find assets & users jumping from corporate LAN, WLAN to Guest Network
– Detect attempts to bypass security controls
– Detect malware vector of “benign” off-network browsing
1 in 566 websites host malware (Symantec 2014 Internet Security Threat Report)
• Profile jumping behavior to look for patterns and anomalies
– Identify the User, IP address, MAC address
– Identify activity before and after jumping
• Key points to look for include
– Assets and users jumping periodically –
Normal business users should be on corporate network
– Network jumps which don’t appear to be pre-meditated
(i.e. looking for programmatic jumps)
– Volume, periodicity, destination, traffic type can all be
indicators of potential Exfiltration
“40% [of companies] reported
that they had been exposed to a
security threat as a direct
consequence of an off-network
user’s laptop getting compromised
within the last twelve months.”
From Google report, “Off-Network Workers –
The Weakest Link to Corporate Web Security”](https://image.slidesharecdn.com/splunklivedenver-wipro-2015-08-04-150805034546-lva1-app6892/85/Splunk-for-Security-Background-Customer-Case-Study-22-320.jpg)







Ad
Recommended
Gov & Education Day 2015 - User Behavior Analytics



Gov & Education Day 2015 - User Behavior AnalyticsSplunk This document provides an overview of Splunk User Behavior Analytics (UBA). It begins with forward-looking statements and disclaimers. It then introduces the presenter and outlines an agenda covering Splunk's security vision, today's threat landscape, an overview of UBA and machine learning, and a product overview of Splunk UBA. Key use cases of Splunk UBA are described as advanced cyber attacks and malicious insider threats. The document highlights what Splunk UBA does including automated threat detection across various data sources using machine learning. Workflows for threat detection and investigation are outlined. The presentation concludes by inviting the audience to a live demo and providing details on limited-time promotional offers for Splunk UBA and Security bundles
Splunk .conf2011: Splunk for Fraud and Forensics at Intuit



Splunk .conf2011: Splunk for Fraud and Forensics at IntuitErin Sweeney Splunk can help organizations detect security threats and attacks by analyzing patterns in large volumes of machine data. As attacks have evolved beyond simple signatures to target behaviors, a behavioral approach is needed to understand adversary goals and methods. Splunk supports pattern modeling and adaptation to anticipate attack vectors. It detects suspicious patterns and anomalies by establishing baselines of normal behavior and monitoring for deviations. This helps security analysts take an "actor view" to gain insights into persistent threats.
SplunkSummit 2015 - Splunk User Behavioral Analytics



SplunkSummit 2015 - Splunk User Behavioral AnalyticsSplunk The document discusses Splunk User Behavior Analytics (UBA) and its capabilities for detecting advanced cyber attacks and insider threats through behavioral threat detection using machine learning. It notes that traditional threat detection focuses only on known threats, while UBA aims to detect unknown threats through automated security analytics and anomaly detection based on establishing user and entity baselines and identifying deviations from normal behavior. The document provides examples of UBA use cases and the types of data sources it can integrate to perform threat detection and security analytics.
Enterprise Sec + User Bahavior Analytics



Enterprise Sec + User Bahavior AnalyticsSplunk The document provides an overview and update on Splunk's Enterprise Security and User Behavior Analytics solutions. It summarizes the key capabilities of each solution, including advanced threat detection, user activity monitoring, and machine learning-based anomaly detection. It also highlights new features recently added to Enterprise Security 4.0 like breach analysis tools and integration with Splunk UBA.
Splunk for Security-Hands On



Splunk for Security-Hands OnSplunk Learn from our Security Expert on how to use the Splunk App for Enterprise Security (ES) in a live, hands-on session. We'll take a tour through Splunk's award-winning security offering to understand some of the unique capabilities in the product. Then, we'll use ES to work an incident and disrupt an adversary's Kill Chain by finding the Actions on Intent, Exploitation Methods, and Reconnaissance Tactics used against a simulated organization. Data investigated will include threat list intelligence feeds, endpoint activity logs, e-mail logs, and web access logs. This session is a must for all security experts! Please bring your laptop as this is a hands-on session.
Gov Day Sacramento 2015 - User Behavior Analytics



Gov Day Sacramento 2015 - User Behavior AnalyticsSplunk Bob Pratt from Splunk presented on Splunk's User Behavior Analytics (UBA) product. UBA uses machine learning and behavioral analytics to detect cyber threats and insider threats by analyzing user, application, and entity behaviors. It reduces false positives by focusing on anomalies rather than signatures. Splunk collects log data from various sources and uses UBA to detect threats like account takeovers, lateral movement, and malware attacks in a more efficient manner than traditional SIEMs. Pratt demonstrated UBA's threat detection and investigation workflows.
SplunkLive! Splunk for Insider Threats and Fraud Detection



SplunkLive! Splunk for Insider Threats and Fraud DetectionSplunk Splunk can be used to detect insider threats and fraud through monitoring and correlating machine data from various sources. It summarizes use cases where Splunk helped detect disgruntled employees stealing intellectual property, data leakage, and classroom fraud at an education company. It also discusses how Splunk detected millions of dollars in payment fraud at a cash wire transfer company by identifying emerging patterns. Finally, it provides examples of fraud patterns that could be detected at Etsy such as traffic from cloud services or brute force password attempts.
SplunkLive! - Splunk for Security



SplunkLive! - Splunk for SecuritySplunk The document is an agenda for a security session presentation by Splunk. It includes an introduction to Splunk for security use cases, a demo of the Zeus security product, and a discussion of enterprise security and user behavior analytics solutions from Splunk. Key points include how Splunk can provide a unified platform for security data from multiple sources, detect advanced threats that are difficult to find, and help connect related security events to better understand security incidents.
SplunkLive! Stockholm 2015 breakout - Analytics based security



SplunkLive! Stockholm 2015 breakout - Analytics based securitySplunk This document discusses how Splunk can be used for security analytics and threat detection. It describes how Splunk allows organizations to centrally gather and correlate security-related data from various sources like networks, endpoints, applications and threat intelligence feeds. This enables use cases like monitoring for known threats, detecting unknown threats, incident investigation and user behavior analytics. Advanced techniques like machine learning and user/entity behavior analytics are also discussed to help identify anomalous activity that could indicate security incidents or threats.
Splunk for Security



Splunk for SecurityGabrielle Knowles This document discusses how Splunk User Behavior Analytics (UBA) uses machine learning and behavioral analytics to detect threats. It provides an overview of how UBA analyzes logs from various systems to detect anomalies and threats across the kill chain. The document explains that UBA reduces events for SOC analysts to investigate by 99.99% and provides key workflows for threat detection and security analytics/hunting of threats. It provides an example of how UBA could detect a potential insider threat involving a user elevating privileges and potentially exfiltrating sensitive documents.
SplunkLive! Splunk for Security



SplunkLive! Splunk for SecuritySplunk This document provides an overview of Splunk software for security applications. It begins with an agenda for a Splunk security presentation, then discusses challenges facing security teams like advanced threats and limitations of existing security information and event management (SIEM) systems. The document demonstrates how Splunk can collect all types of machine data, perform fast searches and analytics, and be deployed more easily than traditional SIEMs. Use cases shown include incident investigations, compliance reporting, and real-time monitoring of known and unknown threats. The document highlights Splunk's customer base, performance in industry evaluations, and integrations with security vendors. It concludes by inviting the reader to learn more about Splunk on their website or contact sales.
Splunk for Enterprise Security Featuring User Behavior Analytics 



Splunk for Enterprise Security Featuring User Behavior Analytics Splunk This session will review Splunk’s two premium solutions for information security organizations: Splunk for Enterprise Security (ES) and Splunk User Behavior Analytics (UBA). Splunk ES is Splunk's award-winning security intelligence solution that brings immediate value for continuous monitoring across SOC and incident response environments – allowing you to quickly detect and respond to external and internal attacks, simplifying threat management while decreasing risk. Splunk UBA is a new technology that applies unsupervised machine learning and data science to solving one of the biggest problems in information security today: insider threat. You’ll learn how Splunk UBA works in tandem with ES, or third-party data sources, to bring significant automated analytical power to your SOC and Incident Response teams. We’ll discuss each solution and see them integrated and in action through detailed demos.
Splunk conf2014 - Dashboard Fun - Creating an Interactive Transaction Profiler



Splunk conf2014 - Dashboard Fun - Creating an Interactive Transaction ProfilerSplunk Using Simple XML and Splunk Enterprise, learn how to create easy interactive dashboards to explore data. This demo showcases great tools to put ion the hands of Splunk users, help desk users and IT Operations staff.
Enterprise Security Guided Tour



Enterprise Security Guided TourSplunk Join our Security Expert and learn how to use the Splunk App for Enterprise Security (ES) in a live, hands-on session. We'll take a tour through Splunk's award-winning security offering to understand some of the unique capabilities in the product. Then, we'll use ES to work an incident and disrupt an adversary's Kill Chain by finding the Actions on Intent, Exploitation Methods, and Reconnaissance Tactics used against a simulated organization. Data investigated will include threat list intelligence feeds, endpoint activity logs, e-mail logs, and web access logs. This session is a must for all security experts! Please bring your laptop as this is a hands-on session.
Splunk for Enterprise Security featuring User Behavior Analytics



Splunk for Enterprise Security featuring User Behavior AnalyticsSplunk This session will review Splunk’s two premium solutions - Splunk Enterprise Security (ES) is Splunk's award-winning security intelligence solution that brings immediate value for continuous monitoring across SOC and
incident response environments. Splunk UBA is a new technology that applies unsupervised machine learning and data science to solving one of the biggest problems in information security today: insider threat. You’ll learn how Splunk UBA works in tandem with ES, or third-party data sources, to bring significant automated analytical power to your SOC and Incident Response teams.
PPT-Splunk-LegacySIEM-101_FINAL



PPT-Splunk-LegacySIEM-101_FINALRisi Avila This document discusses replacing a legacy security information and event management (SIEM) system with Splunk Enterprise. It outlines 10 common problems with legacy SIEMs, such as an inability to ingest and analyze all relevant log and machine data. Customer case studies show how Splunk can help organizations replace aging SIEMs in a few months to gain scalability, faster security investigations, and the ability to ensure compliance. The presentation covers Splunk's security monitoring and analytics capabilities and migration options from legacy SIEMs to Splunk. Attendees are invited to sign up for a SIEM replacement workshop to discuss their specific needs.
Splunk for Security - Hands-On 



Splunk for Security - Hands-On Splunk Join our Security Expert and learn how to use the Splunk App for Enterprise Security (ES) in a live, hands-on session. We'll take a tour through Splunk's award-winning security offering to understand some of the unique capabilities in the product. Then, we'll use ES to work an incident and disrupt an adversary's Kill Chain by finding the Actions on Intent, Exploitation Methods, and Reconnaissance Tactics used against a simulated organization. Data investigated will include threat list intelligence feeds, endpoint activity logs, e-mail logs, and web access logs. This session is a must for all security experts! Please bring your laptop as this is a hands-on session.
Enterprise Security featuring UBA



Enterprise Security featuring UBASplunk This document provides an overview of Splunk's security products, including Splunk Enterprise Security and Splunk User Behavior Analytics. It discusses the types of threats these products help detect, such as advanced cyber attacks and malicious insider threats. It describes the various data sources that can be analyzed, including network, identity, endpoint, and cloud data. It also lists the over 40 threat and anomaly models included in Splunk UBA to detect issues like reconnaissance, lateral movement, and data exfiltration.
SplunkLive! München 2016 - Splunk für Security



SplunkLive! München 2016 - Splunk für SecuritySplunk This document provides an overview of Splunk's security analytics and user behavior analytics capabilities for detecting threats like cyber attacks and insider threats. It discusses how Splunk uses machine learning and behavioral analytics on large datasets to detect anomalies and threats. Examples are given showing how Splunk can detect suspicious user activities across the cyber kill chain and identify external attacks and insider threats. Key workflows for security analysts and threat hunters using Splunk are also outlined.
Splunk für Security



Splunk für SecuritySplunk Sie haben viel Geld für Ihre Security Infrastruktur ausgegeben. Wie führen Sie nun all die verschiedenen Systeme zusammen, damit Sie Ihre Ziele erreichen: Bedrohungen schnelle entdecken, darauf reagieren und sie zukünftig zu verhindern. Gleichzeitg soll es Ihrem Security Team natürlich möglich sein, im Sinne Ihre Geschäftstätigkeit und Strategie zu handeln. Erfahren Sie hier, wie Sie Ihre Security Ressources am effektivsten einsetzen. Wir zeigen Ihnen das Ganze in einer Live Demo.
Level Up Your Security Skills in Splunk Enterprise



Level Up Your Security Skills in Splunk EnterpriseSplunk During this advanced Splunk webinar, Splunk security experts covered the following security scenarios:
- Automated threat intelligence response
- Behavior profiling
- Anomaly detection
- Tracking an attack against the “kill chain”
You can watch a recording of the webinar here: https://splunkevents.webex.com/splunkevents/lsr.php?RCID=8163d71e6fa0646beb8f8354bfac61a1
Building an Analytics - Enabled SOC Breakout Session 



Building an Analytics - Enabled SOC Breakout Session Splunk This document provides an overview of building an analytics-enabled security operations center (SOC). It discusses the three main components of a SOC - process, people, and technology. For process, it covers threat modeling, playbooks, tier structures, shift rotations, and other operational aspects. For people, it describes the different roles required in a SOC. For technology, it promotes Splunk Enterprise as a security intelligence platform that can power all functions of a SOC. It also provides examples of how Splunk can be used for various SOC use cases and processes.
Enterprise Security and User Behavior Analytics



Enterprise Security and User Behavior AnalyticsSplunk Splunk Enterprise Security 4.5 provides security information and event management (SIEM) and a security intelligence platform. It includes features like adaptive response to extend analytics-driven decisions and automation, and glass tables to enhance visual analytics. Glass tables allow security teams to create custom visualizations that reflect their workflows and gain visibility across their security ecosystem. The update also includes improvements to detection, investigation, and response times through automation and correlation searches.
SplunkLive! Milano 2016 - Splunk Plenary Session



SplunkLive! Milano 2016 - Splunk Plenary SessionSplunk The document provides an agenda for the SplunkLiveMilano2016 event taking place on April 5th, 2016 in Milan. The agenda includes welcome and overview sessions in the morning, followed by use case presentations from Unicredit, Saipem, and Yoox-Net-a-Porter. There will be breakout sessions after lunch on various topics, and a happy hour with sponsors. The document also lists the dedicated Splunk team for Italy and provides information on upcoming Splunk events.
Splunk for Enterprise Security featuring User Behavior Analytics



Splunk for Enterprise Security featuring User Behavior AnalyticsSplunk This session will review Splunk’s two premium solutions for information security organizations: Splunk for Enterprise Security (ES) and Splunk User Behavior Analytics (UBA). Splunk ES is Splunk's award-winning security intelligence solution that brings immediate value for continuous monitoring across SOC and incident response environments – allowing you to quickly detect and respond to external and internal attacks, simplifying threat management while decreasing risk. Splunk UBA is a new technology that applies unsupervised machine learning and data science to solving one of the biggest problems in information security today: insider threat. You’ll learn how Splunk UBA works in tandem with ES, or third-party data sources, to bring significant automated analytical power to your SOC and Incident Response teams. We’ll discuss each solution and see them integrated and in action through detailed demos.
Operational Security Intelligence Breakout Session



Operational Security Intelligence Breakout SessionSplunk This document discusses operationalizing security intelligence through Splunk. It begins with an overview of security intelligence and what it aims to provide organizations. It then discusses requirements for security intelligence like risk-based analytics, context and intelligence, and connecting data and people. The presentation includes two demos of Splunk capabilities for security use cases. It promotes attending future tech talks and Splunk conferences to learn more.
Splunk for Enterprise Security Featuring UBA



Splunk for Enterprise Security Featuring UBASplunk This document provides an overview and summary of Splunk's security products, including Enterprise Security and User Behavior Analytics. It discusses the key capabilities and features of these products, such as detecting advanced cyberattacks, identifying insider threats through machine learning, and integrating UBA with SIEM for improved threat detection. New features in recent versions are highlighted, like custom threat modeling and enhanced visibility into user, device, application, and protocol activity. Customer testimonials praise Splunk UBA's data-science approach to finding hidden threats.
Splunk EMEA Webinar: Scoping infections and disrupting breaches



Splunk EMEA Webinar: Scoping infections and disrupting breachesSplunk This document discusses best practices for scoping infections and disrupting breaches. It outlines the necessary data sources like network endpoint, access/identity, and threat intelligence data. It describes capabilities for monitoring, alerting, investigating incidents, and detecting threats. The document demonstrates investigating a breach example using the attack kill chain. It recommends establishing a security intelligence platform to connect and analyze security-related data from multiple sources. Lastly, it promotes the upcoming Splunk conference and training opportunities.
Splunk conf2014 - Curating User Experience



Splunk conf2014 - Curating User ExperienceSplunk This session shows some of the tricks that make "cookiecutter" app creation a bit easier, reducing development time by admins / data scientists all while providing reusable "code base" for creating more dashboards and content. The presentation focuses on macros, "app virtualization," use of data models to provide an abstraction layer to data, and use of search commands *after* | pivot for more dashboarding win!
Splunk for Online Services Event featuring Groupon



Splunk for Online Services Event featuring GrouponSplunk Groupon uses Splunk for API management, security, DevOps, business analytics, mobile app monitoring and more.
Watch the presentation live here: http://bit.ly/xAHcgI
Ad
More Related Content
What's hot (20)
SplunkLive! Stockholm 2015 breakout - Analytics based security



SplunkLive! Stockholm 2015 breakout - Analytics based securitySplunk This document discusses how Splunk can be used for security analytics and threat detection. It describes how Splunk allows organizations to centrally gather and correlate security-related data from various sources like networks, endpoints, applications and threat intelligence feeds. This enables use cases like monitoring for known threats, detecting unknown threats, incident investigation and user behavior analytics. Advanced techniques like machine learning and user/entity behavior analytics are also discussed to help identify anomalous activity that could indicate security incidents or threats.
Splunk for Security



Splunk for SecurityGabrielle Knowles This document discusses how Splunk User Behavior Analytics (UBA) uses machine learning and behavioral analytics to detect threats. It provides an overview of how UBA analyzes logs from various systems to detect anomalies and threats across the kill chain. The document explains that UBA reduces events for SOC analysts to investigate by 99.99% and provides key workflows for threat detection and security analytics/hunting of threats. It provides an example of how UBA could detect a potential insider threat involving a user elevating privileges and potentially exfiltrating sensitive documents.
SplunkLive! Splunk for Security



SplunkLive! Splunk for SecuritySplunk This document provides an overview of Splunk software for security applications. It begins with an agenda for a Splunk security presentation, then discusses challenges facing security teams like advanced threats and limitations of existing security information and event management (SIEM) systems. The document demonstrates how Splunk can collect all types of machine data, perform fast searches and analytics, and be deployed more easily than traditional SIEMs. Use cases shown include incident investigations, compliance reporting, and real-time monitoring of known and unknown threats. The document highlights Splunk's customer base, performance in industry evaluations, and integrations with security vendors. It concludes by inviting the reader to learn more about Splunk on their website or contact sales.
Splunk for Enterprise Security Featuring User Behavior Analytics 



Splunk for Enterprise Security Featuring User Behavior Analytics Splunk This session will review Splunk’s two premium solutions for information security organizations: Splunk for Enterprise Security (ES) and Splunk User Behavior Analytics (UBA). Splunk ES is Splunk's award-winning security intelligence solution that brings immediate value for continuous monitoring across SOC and incident response environments – allowing you to quickly detect and respond to external and internal attacks, simplifying threat management while decreasing risk. Splunk UBA is a new technology that applies unsupervised machine learning and data science to solving one of the biggest problems in information security today: insider threat. You’ll learn how Splunk UBA works in tandem with ES, or third-party data sources, to bring significant automated analytical power to your SOC and Incident Response teams. We’ll discuss each solution and see them integrated and in action through detailed demos.
Splunk conf2014 - Dashboard Fun - Creating an Interactive Transaction Profiler



Splunk conf2014 - Dashboard Fun - Creating an Interactive Transaction ProfilerSplunk Using Simple XML and Splunk Enterprise, learn how to create easy interactive dashboards to explore data. This demo showcases great tools to put ion the hands of Splunk users, help desk users and IT Operations staff.
Enterprise Security Guided Tour



Enterprise Security Guided TourSplunk Join our Security Expert and learn how to use the Splunk App for Enterprise Security (ES) in a live, hands-on session. We'll take a tour through Splunk's award-winning security offering to understand some of the unique capabilities in the product. Then, we'll use ES to work an incident and disrupt an adversary's Kill Chain by finding the Actions on Intent, Exploitation Methods, and Reconnaissance Tactics used against a simulated organization. Data investigated will include threat list intelligence feeds, endpoint activity logs, e-mail logs, and web access logs. This session is a must for all security experts! Please bring your laptop as this is a hands-on session.
Splunk for Enterprise Security featuring User Behavior Analytics



Splunk for Enterprise Security featuring User Behavior AnalyticsSplunk This session will review Splunk’s two premium solutions - Splunk Enterprise Security (ES) is Splunk's award-winning security intelligence solution that brings immediate value for continuous monitoring across SOC and
incident response environments. Splunk UBA is a new technology that applies unsupervised machine learning and data science to solving one of the biggest problems in information security today: insider threat. You’ll learn how Splunk UBA works in tandem with ES, or third-party data sources, to bring significant automated analytical power to your SOC and Incident Response teams.
PPT-Splunk-LegacySIEM-101_FINAL



PPT-Splunk-LegacySIEM-101_FINALRisi Avila This document discusses replacing a legacy security information and event management (SIEM) system with Splunk Enterprise. It outlines 10 common problems with legacy SIEMs, such as an inability to ingest and analyze all relevant log and machine data. Customer case studies show how Splunk can help organizations replace aging SIEMs in a few months to gain scalability, faster security investigations, and the ability to ensure compliance. The presentation covers Splunk's security monitoring and analytics capabilities and migration options from legacy SIEMs to Splunk. Attendees are invited to sign up for a SIEM replacement workshop to discuss their specific needs.
Splunk for Security - Hands-On 



Splunk for Security - Hands-On Splunk Join our Security Expert and learn how to use the Splunk App for Enterprise Security (ES) in a live, hands-on session. We'll take a tour through Splunk's award-winning security offering to understand some of the unique capabilities in the product. Then, we'll use ES to work an incident and disrupt an adversary's Kill Chain by finding the Actions on Intent, Exploitation Methods, and Reconnaissance Tactics used against a simulated organization. Data investigated will include threat list intelligence feeds, endpoint activity logs, e-mail logs, and web access logs. This session is a must for all security experts! Please bring your laptop as this is a hands-on session.
Enterprise Security featuring UBA



Enterprise Security featuring UBASplunk This document provides an overview of Splunk's security products, including Splunk Enterprise Security and Splunk User Behavior Analytics. It discusses the types of threats these products help detect, such as advanced cyber attacks and malicious insider threats. It describes the various data sources that can be analyzed, including network, identity, endpoint, and cloud data. It also lists the over 40 threat and anomaly models included in Splunk UBA to detect issues like reconnaissance, lateral movement, and data exfiltration.
SplunkLive! München 2016 - Splunk für Security



SplunkLive! München 2016 - Splunk für SecuritySplunk This document provides an overview of Splunk's security analytics and user behavior analytics capabilities for detecting threats like cyber attacks and insider threats. It discusses how Splunk uses machine learning and behavioral analytics on large datasets to detect anomalies and threats. Examples are given showing how Splunk can detect suspicious user activities across the cyber kill chain and identify external attacks and insider threats. Key workflows for security analysts and threat hunters using Splunk are also outlined.
Splunk für Security



Splunk für SecuritySplunk Sie haben viel Geld für Ihre Security Infrastruktur ausgegeben. Wie führen Sie nun all die verschiedenen Systeme zusammen, damit Sie Ihre Ziele erreichen: Bedrohungen schnelle entdecken, darauf reagieren und sie zukünftig zu verhindern. Gleichzeitg soll es Ihrem Security Team natürlich möglich sein, im Sinne Ihre Geschäftstätigkeit und Strategie zu handeln. Erfahren Sie hier, wie Sie Ihre Security Ressources am effektivsten einsetzen. Wir zeigen Ihnen das Ganze in einer Live Demo.
Level Up Your Security Skills in Splunk Enterprise



Level Up Your Security Skills in Splunk EnterpriseSplunk During this advanced Splunk webinar, Splunk security experts covered the following security scenarios:
- Automated threat intelligence response
- Behavior profiling
- Anomaly detection
- Tracking an attack against the “kill chain”
You can watch a recording of the webinar here: https://splunkevents.webex.com/splunkevents/lsr.php?RCID=8163d71e6fa0646beb8f8354bfac61a1
Building an Analytics - Enabled SOC Breakout Session 



Building an Analytics - Enabled SOC Breakout Session Splunk This document provides an overview of building an analytics-enabled security operations center (SOC). It discusses the three main components of a SOC - process, people, and technology. For process, it covers threat modeling, playbooks, tier structures, shift rotations, and other operational aspects. For people, it describes the different roles required in a SOC. For technology, it promotes Splunk Enterprise as a security intelligence platform that can power all functions of a SOC. It also provides examples of how Splunk can be used for various SOC use cases and processes.
Enterprise Security and User Behavior Analytics



Enterprise Security and User Behavior AnalyticsSplunk Splunk Enterprise Security 4.5 provides security information and event management (SIEM) and a security intelligence platform. It includes features like adaptive response to extend analytics-driven decisions and automation, and glass tables to enhance visual analytics. Glass tables allow security teams to create custom visualizations that reflect their workflows and gain visibility across their security ecosystem. The update also includes improvements to detection, investigation, and response times through automation and correlation searches.
SplunkLive! Milano 2016 - Splunk Plenary Session



SplunkLive! Milano 2016 - Splunk Plenary SessionSplunk The document provides an agenda for the SplunkLiveMilano2016 event taking place on April 5th, 2016 in Milan. The agenda includes welcome and overview sessions in the morning, followed by use case presentations from Unicredit, Saipem, and Yoox-Net-a-Porter. There will be breakout sessions after lunch on various topics, and a happy hour with sponsors. The document also lists the dedicated Splunk team for Italy and provides information on upcoming Splunk events.
Splunk for Enterprise Security featuring User Behavior Analytics



Splunk for Enterprise Security featuring User Behavior AnalyticsSplunk This session will review Splunk’s two premium solutions for information security organizations: Splunk for Enterprise Security (ES) and Splunk User Behavior Analytics (UBA). Splunk ES is Splunk's award-winning security intelligence solution that brings immediate value for continuous monitoring across SOC and incident response environments – allowing you to quickly detect and respond to external and internal attacks, simplifying threat management while decreasing risk. Splunk UBA is a new technology that applies unsupervised machine learning and data science to solving one of the biggest problems in information security today: insider threat. You’ll learn how Splunk UBA works in tandem with ES, or third-party data sources, to bring significant automated analytical power to your SOC and Incident Response teams. We’ll discuss each solution and see them integrated and in action through detailed demos.
Operational Security Intelligence Breakout Session



Operational Security Intelligence Breakout SessionSplunk This document discusses operationalizing security intelligence through Splunk. It begins with an overview of security intelligence and what it aims to provide organizations. It then discusses requirements for security intelligence like risk-based analytics, context and intelligence, and connecting data and people. The presentation includes two demos of Splunk capabilities for security use cases. It promotes attending future tech talks and Splunk conferences to learn more.
Splunk for Enterprise Security Featuring UBA



Splunk for Enterprise Security Featuring UBASplunk This document provides an overview and summary of Splunk's security products, including Enterprise Security and User Behavior Analytics. It discusses the key capabilities and features of these products, such as detecting advanced cyberattacks, identifying insider threats through machine learning, and integrating UBA with SIEM for improved threat detection. New features in recent versions are highlighted, like custom threat modeling and enhanced visibility into user, device, application, and protocol activity. Customer testimonials praise Splunk UBA's data-science approach to finding hidden threats.
Splunk EMEA Webinar: Scoping infections and disrupting breaches



Splunk EMEA Webinar: Scoping infections and disrupting breachesSplunk This document discusses best practices for scoping infections and disrupting breaches. It outlines the necessary data sources like network endpoint, access/identity, and threat intelligence data. It describes capabilities for monitoring, alerting, investigating incidents, and detecting threats. The document demonstrates investigating a breach example using the attack kill chain. It recommends establishing a security intelligence platform to connect and analyze security-related data from multiple sources. Lastly, it promotes the upcoming Splunk conference and training opportunities.
Viewers also liked (20)
Splunk conf2014 - Curating User Experience



Splunk conf2014 - Curating User ExperienceSplunk This session shows some of the tricks that make "cookiecutter" app creation a bit easier, reducing development time by admins / data scientists all while providing reusable "code base" for creating more dashboards and content. The presentation focuses on macros, "app virtualization," use of data models to provide an abstraction layer to data, and use of search commands *after* | pivot for more dashboarding win!
Splunk for Online Services Event featuring Groupon



Splunk for Online Services Event featuring GrouponSplunk Groupon uses Splunk for API management, security, DevOps, business analytics, mobile app monitoring and more.
Watch the presentation live here: http://bit.ly/xAHcgI
Splunk in Target: Internet of Things (Robot Analytics)



Splunk in Target: Internet of Things (Robot Analytics)Timur Bagirov This document discusses how Target is using machine data from robots in their distribution centers to provide data-driven insights and decisions for robotics analytics. It provides examples of how Splunk is helping Target better manage their equipment by analyzing machine data and providing predictive analytics to identify performance trends and predict future issues. The vision is to expand this approach to more distribution centers and further integrate Splunk with their asset management systems.
Легкие мобильные приложения – альтернатива традиционной экосистемной модели?



Легкие мобильные приложения – альтернатива традиционной экосистемной модели?CEE-SEC(R) Валентин Оносовский, UbiqMobile
SplunkLive! London 2016 - BBC Worldwide



SplunkLive! London 2016 - BBC WorldwideSplunk Splunk was used by BBC Worldwide to provide end-to-end visibility into the customer journey on BBC Store, a new digital service for audiences to buy, enjoy and keep BBC programmes. Splunk provided dashboards and visualizations to monitor key parts of the customer journey like login, browsing, purchase and playback that involved different suppliers. This allowed non-technical users to monitor performance, authentication errors, payment issues and marketing reports to ensure a great customer experience and translate insights into operational impact ahead of the BBC Store launch.
Splunk Cloud



Splunk CloudSplunk If you are looking to gain all the benefits of Splunk software with all the benefits of a cloud-service, this is a must-attend session. In this session learn why Splunk Cloud is the industry-leading SaaS platform for operational intelligence and hear how Splunk Cloud customers use Splunk software with zero operational overhead. You will also learn how Splunk Cloud offers the full feature set of Splunk Enterprise, access to 500+ apps and single pane-of-glass visibility across Splunk Cloud and Splunk Enterprise deployments.
Splunk live! Italy 2015



Splunk live! Italy 2015Georg Knon Splunk is used by John Lewis, a major UK retailer, to gain insights from machine data across their operations. Splunk collects and indexes log and event data from various systems like web servers, applications, and devices. This data is analyzed using Splunk to provide real-time visibility, troubleshoot issues, model customer behavior, and make business decisions. Splunk helps John Lewis improve their online customer experience and resolve issues more quickly by analyzing data from their ecommerce platform and various systems.
SplunkLive! London 2016 - John Lewis



SplunkLive! London 2016 - John LewisSplunk Presentation on how John Lewis uses Splunk Enterprise and Splunk Enterprise Security as a security platform.
SplunkLive! London 2016 - Shazam



SplunkLive! London 2016 - ShazamSplunk This document discusses how Shazam, a mobile app for identifying music, TV, and other media, uses Splunk for analytics. It describes how Shazam ingests beacon and other log data into Splunk to power dashboards for A/B testing, music charts, and other analytics. It also outlines how Shazam has scaled up its use of Splunk over time to support more data, queries, and new types of insights like predicting music popularity trends. The document envisions future uses of Splunk at Shazam for DevOps monitoring and anomaly detection.
SplunkLive! London 2016 - HSCIC / NHS Digital / Spine 2



SplunkLive! London 2016 - HSCIC / NHS Digital / Spine 2Splunk The document discusses how Splunk software is used by the Health and Social Care Information Centre (HSCIC) to index and analyze log data from the NHS SPINE CORE system. It provides an overview of HSCIC and SPINE CORE, outlines requirements for log indexing and search, and describes the performance monitoring platform architecture and key use cases including 24/7 operational monitoring, performance monitoring, and incident investigation for both technical and business issues.
Periodo de entreguerras



Periodo de entreguerrasMaria Portarrieu El documento resume los principales acontecimientos políticos en varios países europeos e internacionales después de la Primera Guerra Mundial. Trata sobre el Tratado de Versalles, el ascenso del fascismo en Italia bajo Mussolini, los gobiernos de entreguerras en Inglaterra, la guerra civil en Irlanda, y los conflictos en el Medio Oriente, India, España y China. También habla sobre la creación y fracasos de la Liga de Naciones.
Leveraging Compliance for Security with SIEM and Log Management



Leveraging Compliance for Security with SIEM and Log ManagementTripwire With the fast changing regulatory and threat landscape, organizations need to gain quick knowledge of how log management and SIEM solutions help them meet their compliance and security needs. The 2010 Data Breach Investigations Report highlights this issue, revealing that 86 percent of organizations breached had evidence of the breach in their logs. Had they found this evidence in a timely manner, they likely could have prevented much of the damage associated with a breach from occurring.
In this webcast, security and compliance expert Anton Chuvakin and Tripwire's Cindy Valladares offer practical strategies organizations can apply to meet their compliance needs and improve security with log management and SIEM solutions.
The difference between log management and SIEM solutions and why you need both.
How defining the problem you are trying to solve helps you choose the right solution.
A pragmatic approach to SIEM that ensures a successful compliance audit, but also improves security.
How SIEM and log management requirements tie in to various regulations and standards like PCI, HIPAA and NERC.
Additional steps organizations can take to improve security through the solutions they use for compliance.
Mistakes organizations make that undermine the organization's security.
Learn how solutions in the Tripwire VIA suite are a perfect fit for this pragmatic approach.
SplunkLive! Customer Presentation - FINRA



SplunkLive! Customer Presentation - FINRASplunk This document discusses log centralization in cloud environments. It describes FINRA's role as an independent financial industry regulator and how it monitors the stock market and registered brokers. It then discusses challenges of collecting logs from various cloud services (SaaS, IaaS, PaaS) and providers (AWS, Cisco, etc.). It provides examples of using AWS services like CloudTrail, CloudWatch, and Elastic MapReduce with Hadoop to collect and analyze logs and metrics in the cloud.
Security Information Event Management - nullhyd



Security Information Event Management - nullhydn|u - The Open Security Community SIEM systems provide security event monitoring and log management by collecting security data from across an organization's network and systems. The first SIEM was developed in 1996 and major players today include IBM QRadar, HP ArcSight, and McAfee Nitro. SIEMs aggregate logs from various sources, use correlation engines to identify related security events, and generate alerts when multiple events indicate a higher risk threat. They provide visibility across an organization's security infrastructure and help with compliance, operations, and forensic investigations. SIEM is important for threat detection, compliance, and gaining insights from security event data.
Leveraging your hadoop cluster better - running performant code at scale



Leveraging your hadoop cluster better - running performant code at scaleMichael Kopp Somebody once said that hadoop is a way of running highly unperformant code at scale. In this talk I want to show how we can change that and make map reduce jobs more performant. I will show how to analyze them at scale and optimize the job itself, instead of just tinkering with hadoop options. The result is a much better utilized cluster and jobs that run in a fraction of the original time running performant code at scale! Most of the time when speaking about Hadoop people only consider scale, however, when looking at it it very often runs highly unperformant jobs. By actually looking at the performance characteristics of the jobs themselves and optimizing and tuning those far better results can be achieved. Examples include small changes that cut jobs down from 15 hours to 2 hours without adding any more hardware. The concepts and techniques explained in the talk will be applicable regardless which tool is used to identify the performance characteristics, what is important is that by applying performance analysis and optimization techniques that we have used on other applications for a long time we can make hadoop jobs much more effective and performant! The attendees will be able to understand those techniques and apply them to their map/reduce/PIG/hive or other mapreduce jobs.
SIEM evolution



SIEM evolutionStijn Vande Casteele Stijn Vande Casteele is a security architect who provides solutions to underpin SIEM services. His responsibilities include engineering infrastructure to deliver security monitoring services to customers, integrating new technologies, and advising on pre-sales and security questions. He aims to create a center of excellence for SIEM within his company. The presentation discusses the evolution of SIEM, different SIEM architectures, use cases, and concludes with recommendations around carefully planning SIEM migrations and centralizing security monitoring efforts.
Security Monitoring using SIEM null bangalore meet april 2015



Security Monitoring using SIEM null bangalore meet april 2015n|u - The Open Security Community This document discusses security information and event management (SIEM) systems. It defines log files and events, and explains that SIEM systems allow organizations to monitor security events and write correlation rules to detect patterns of attacks. The document outlines typical SIEM architectures and notes that SIEM systems present detailed information about attack scenarios by correlating disparate security-related events from various sources.
Tableau AWS EC2 integration architecture diagram



Tableau AWS EC2 integration architecture diagramVaidy Krishnan Tableau offers a suite of business intelligence and data visualization software including Tableau Desktop for data preparation and visualization, Tableau Server for deploying visualizations to teams, and Tableau Online for hosting visualizations on the web and mobile. The software integrates with data sources through Tableau Data Engine and enables management, presentation, and automation capabilities through additional modules.
Big data performance management thesis



Big data performance management thesisAhmad Muammar The document is a thesis submitted by Ahmad Muammar to the University of Strathclyde Business School for the degree of Master of Business Administration. It contains 14,903 words excluding appendices and tables of contents. The thesis explores big data and proposes a framework to guide big data analytics. It includes a literature review on big data definitions, value, and characteristics. Case studies of big data implementation at companies like Procter & Gamble, Obama's election campaign, GE, and Walmart are also reviewed. The author aims to understand big data thoroughly and differentiate realities from myths to suggest a practical framework for organizations to evaluate and guide their performance with big data.
SIEM Surelog Arcsight Qradar LogRhythm Alienvault Solarwinds LEM Performance...



SIEM Surelog Arcsight Qradar LogRhythm Alienvault Solarwinds LEM Performance...Ertugrul Akbas The SIEM products and the performance analyses of these products are very important in terms of evaluation.
The running performance of SIEM products, the resources which they require (CPU, RAM, DISK) and how they will show performance in the EPS value needed is very important.
Ad
Similar to Splunk for Security: Background & Customer Case Study (20)
Wipro Customer Presentation



Wipro Customer PresentationSplunk This document discusses Wipro's experience helping a customer transition from their existing SIEM platform to Splunk for security monitoring and analytics. It describes how Wipro guided the customer through a two-phase implementation: first standing up a hybrid on-premise/cloud Splunk deployment to address immediate needs, and now expanding that deployment to 500GB/day in Splunk Cloud and 200GB/day on-premise to accommodate growing data and use cases. The transition yielded significant improvements in search performance, data ingestion and parsing flexibility, and enhanced security visualization and analytics capabilities.
New Splunk Management Solutions Update: Splunk MINT and Splunk App for Stream 



New Splunk Management Solutions Update: Splunk MINT and Splunk App for Stream Splunk Learn what is new in Splunk App for Stream and how it can help you utilize wire/network data analytics to proactively resolve applications and IT operational issues and to efficiently analyze security threats in real-time, across your cloud and on-premises infrastructures. Additionally, you will learn about Splunk MINT, which allows you to gain operational intelligence on the availability, performance, and usage of your mobile apps. You’ll learn how to instrument your mobile apps for operational insight, and how you can build the dashboards, alerts, and searches you need to gain real-time insight on your mobile apps.
Splunk MINT for Mobile Intelligence and Splunk App for Stream for Enhanced Op...



Splunk MINT for Mobile Intelligence and Splunk App for Stream for Enhanced Op...Splunk Learn what is new in Splunk App for Stream and how it can help you utilize wire/network data analytics to proactively resolve applications and IT operational issues and to efficiently analyze security threats in real-time, across your cloud and on-premises infrastructures. Additionally, you will learn about Splunk MINT, which allows you to gain operational intelligence on the availability, performance, and usage of your mobile apps. You’ll learn how to instrument your mobile apps for operational insight, and how you can build the dashboards, alerts, and searches you need to gain real-time insight on your mobile apps.
Splunk MINT and Stream Breakout



Splunk MINT and Stream BreakoutSplunk This document discusses new capabilities in Splunk's App for Stream and Splunk MINT products. It begins with an introduction and overview of each product. It then discusses key benefits like real-time insights, efficient cloud data collection, and fast time to value. Example use cases are provided for IT operations, security, and applications visibility. Supported protocols, platforms, and architecture options are also outlined. The document concludes by discussing challenges in mobile app delivery and how Splunk MINT addresses them through mobile data collection and correlation with other data sources.
CSA SV Threat detection and prediction



CSA SV Threat detection and predictionVishwas Manral The document discusses cloud security challenges and threat detection and prediction techniques. It describes how cloud services like SaaS, PaaS, and IaaS present different security risks. It then discusses a multi-step process for cloud security involving gaining visibility, detecting anomalies and threats using techniques like supervised rules, machine learning, and user behavior analytics, and then remediating incidents. Specific techniques are described like detecting risky users based on anomalous IP addresses, usage patterns, and administrator activities. The summary emphasizes the importance of visibility, automated threat detection, and securing clouds through continuous monitoring.
What’s New: Splunk App for Stream and Splunk MINT



What’s New: Splunk App for Stream and Splunk MINTSplunk Join us to learn what is new in Splunk App for Stream and how it can help you utilize wire/network data analytics to proactively resolve applications and IT operational issues and to efficiently analyze security threats in real-time, across your cloud and on-premises infrastructures. Additionally, you will learn about Splunk MINT, which allows you to gain operational intelligence on the availability, performance, and usage of your mobile apps. You’ll learn how to instrument your mobile apps for operational insight, and how you can build the dashboards, alerts, and searches you need to gain real-time insight on your mobile apps.
FINAL_SCFm50000_JonPapp_CAA_The_Practical_Benefits_of_a_Behavioral_Solution_f...



FINAL_SCFm50000_JonPapp_CAA_The_Practical_Benefits_of_a_Behavioral_Solution_f...Jon Papp This document provides an overview of adopting Splunk User Behavior Analytics (UBA) to help mitigate security risks. It discusses challenges like increased attack surfaces from cloud migrations and mergers & acquisitions. It recommends preparing data in Splunk and identifying users/devices before implementing UBA models. UBA can detect anomalies and threats by analyzing 40 behavioral models over time. Real-life examples showed UBA discovering compromised accounts and external malware activity. UBA helps prioritize risks by separating true threats from false positives.
Splunk Discovery Day Düsseldorf 2016 - Splunk für Security



Splunk Discovery Day Düsseldorf 2016 - Splunk für SecuritySplunk Splunk Enterprise Security is an advanced security information and event management (SIEM) and security intelligence platform that allows organizations to monitor, detect, investigate, and respond to cyberattacks and threats. It provides risk-based analytics, security intelligence, continuous monitoring of security domains, and incident response capabilities through features like alerts and dashboards, pre-built searches, threat intelligence integration, and an investigation timeline. The platform helps connect data from various sources to gain security insights and identify unknown threats.
Splunk App for Stream for Enhanced Operational Intelligence from Wire Data



Splunk App for Stream for Enhanced Operational Intelligence from Wire DataSplunk The Splunk App for Stream provides concise summaries of wire data in 3 sentences or less:
The Splunk App for Stream enables capturing and analyzing wire data from public, private, and hybrid cloud infrastructures for real-time operational insights. It delivers rapid deployment and scalability along with efficient wire data collection. The app captures critical events not found in logs to enhance operational intelligence through wire data analysis.
How to Access and Make Use of “Trapped” Cyber Data to Reduce Your Risk



How to Access and Make Use of “Trapped” Cyber Data to Reduce Your RiskSurfWatch Labs Today’s business world is online and as such is inherently chock full of cyber risks. Cybercriminals continue to take advantage of system vulnerabilities and social engineering to target personally identifiable information, credit card numbers, trade secrets and more. Although there are hundreds of security solutions, products and consultants that claim to solve and address data breaches, the traditional, tactical approach to security is not working. Evaluated cyber intelligence is trapped in your systems, applications and employees – and making that intelligence easily available and quickly understood can help your organization significantly reduce the cyber risks it faces and improve its business resilience.
This presentation examines how to reduce your cyber risks by unlocking the door to evaluated intelligence. Learn:
• Why the traditional threat intelligence approach is not addressing the problem
• Why it’s not just about adding on more security layers, but shifting your cybersecurity approach
• How to mine both your tactical and strategic cyber data for improved operational intelligence
• How to derive immediate visual insights of relevant trending cyber problems through security analytics
CyberCrime in the Cloud and How to defend Yourself 



CyberCrime in the Cloud and How to defend Yourself Alert Logic The document discusses cybercrime threats in the cloud and how to defend against them. It notes that traditional on-premises threats are moving to the cloud, with web application attacks and brute force attacks being most common. Honeypots are used to gather intelligence on attacks by simulating vulnerable systems. Analysis of honeypot data found increases in brute force attacks and vulnerability scans in cloud environments. The document recommends best practices like secure coding, access management, patch management, log review, and tools like firewalls and intrusion detection to help secure cloud environments.
Using Data Science for Cybersecurity



Using Data Science for CybersecurityVMware Tanzu Watch the video: https://content.pivotal.io/webinars/using-data-science-for-cybersecurity
Enterprise networks are under constant threat. While perimeter security can help keep some bad actors out, we know from experience that there is no 100%, foolproof way to prevent unwanted intrusions. In many cases, bad actors come from within the enterprise, meaning perimeter security methods are ineffective.
Enterprises, therefore, must enhance their cybersecurity efforts to include data science-driven methods for identifying anomalous and potentially nefarious user behavior taking place inside their networks and IT infrastructure.
Join Pivotal’s Anirudh Kondaveeti and Jeff Kelly in this live webinar on data science for cybersecurity. You’ll learn how to perform data-science driven anomalous user behavior using a two-stage framework, including using principal components analysis to develop user specific behavioral models. Anirudh and Jeff will also share examples of successful real-world cybersecurity efforts and tips for getting started.
About the Speakers:
Anirudh Kondaveeti is a Principal Data Scientist at Pivotal with a focus on Cybersecurity and spatio-temporal data mining. He has developed statistical models and machine learning algorithms to detect insider and external threats and "needle-in-the-hay-stack" anomalies in machine generated network data for leading industries.
Jeff Kelly is a Principal Product Marketing Manager at Pivotal.
SplunkLive! London - Splunk App for Stream & MINT Breakout



SplunkLive! London - Splunk App for Stream & MINT BreakoutSplunk The document discusses new features in Splunk's App for Stream and Splunk MINT. It introduces the Splunk App for Stream, which enables real-time insights into private, public and hybrid cloud infrastructures through efficient wire data capture. It also discusses Splunk for Mobile Intelligence (MINT), which provides mobile analytics capabilities. The document promotes these products as enhancing operational intelligence through efficient and cloud-ready wire data collection.
Delivering User Behavior Analytics at Apache Hadoop Scale : A new perspective...



Delivering User Behavior Analytics at Apache Hadoop Scale : A new perspective...Cloudera, Inc. Learn how to:
* Detect threats automatically and accurately
* Reduce threat response times from 7 days to 4 hour
* Ingest and process 100+TB per day for automated machine learning and behavior-based detection
Network traffic analysis with cyber security



Network traffic analysis with cyber securityKAMALI PRIYA P We are students from SRM University pursuing B.TECH in Computer Science Department. We took a small initiative to make a PPT about how network traffic can be analyzed through Cyber Security. We have also mentioned the known network analyzers and future scope for network traffic analysis with cyber security.
Security Delivery Platform: Best practices



Security Delivery Platform: Best practicesMihajlo Prerad Security Delivery Platform: Best practices
The traditional Security model was one that operated under simple assumptions. Those assumptions led to deployment models which in todays’ world of cyber security have been proven to be quite vulnerable and inadequate to growing amount and diversity of threats.
A Security Delivery Platform addresses the above considerations and provides a powerful solution for deploying a diverse set of security solutions, as well as scaling each security solution beyond traditional deployments. Such platform delivers visibility into the lateral movement of malware, accelerate the detection of ex-filtration activity, and could significantly reduce the overhead, complexity and costs associated with such security deployments.
In today’s world of industrialized and well-organized cyber threats, it is no longer sufficient to focus on the security applications exclusively. Focusing on how those solutions get deployed together and how they get consistent access to relevant data is a critical piece of the solution. A Security Delivery Platform in this sense is a foundational building block of any cyber security strategy.
Soc analyst course content v3



Soc analyst course content v3ShivamSharma909 The SOC analyst training program is meticulously designed by the subject matter experts at Infosec Train. The training program offers a deep insight into the SOC operations and workflows. It is an excellent opportunity for aspiring and current SOC analysts (L1/L2/L3) to level up their skills to mitigate business risks by effectively handling and responding to security threats.
https://www.infosectrain.com/courses/soc-analyst-expert-training/
Soc analyst course content



Soc analyst course contentShivamSharma909 The SOC analyst training program is meticulously designed by the subject matter experts at Infosec Train. The training program offers a deep insight into the SOC operations and workflows. It is an excellent opportunity for aspiring and current SOC analysts (L1/L2/L3) to level up their skills to mitigate business risks by effectively handling and responding to security threats.
https://www.infosectrain.com/courses/soc-analyst-expert-training/
Elevate your Splunk Deployment by Better Understanding your Value Breakfast S...



Elevate your Splunk Deployment by Better Understanding your Value Breakfast S...Splunk This document discusses how to better understand the value of a Splunk deployment through assessing data sources. It presents a data source assessment tool to map data sources to use cases and organizational groups to identify opportunities. The tool shows which data sources are indexed and overlap between groups. It aims to maximize benefits from machine data by supporting business objectives and enabling broader impact.
Presentacion de solucion cloud de navegacion segura



Presentacion de solucion cloud de navegacion seguraRogerChaucaZea Solucion de seguridad de navegacion WEb con controles dobre trafico http y https, ademas de DLP y control de amenazas, CASB
Ad
Recently uploaded (20)
What is Model Context Protocol(MCP) - The new technology for communication bw...



What is Model Context Protocol(MCP) - The new technology for communication bw...Vishnu Singh Chundawat The MCP (Model Context Protocol) is a framework designed to manage context and interaction within complex systems. This SlideShare presentation will provide a detailed overview of the MCP Model, its applications, and how it plays a crucial role in improving communication and decision-making in distributed systems. We will explore the key concepts behind the protocol, including the importance of context, data management, and how this model enhances system adaptability and responsiveness. Ideal for software developers, system architects, and IT professionals, this presentation will offer valuable insights into how the MCP Model can streamline workflows, improve efficiency, and create more intuitive systems for a wide range of use cases.
Special Meetup Edition - TDX Bengaluru Meetup #52.pptx



Special Meetup Edition - TDX Bengaluru Meetup #52.pptxshyamraj55 We’re bringing the TDX energy to our community with 2 power-packed sessions:
🛠️ Workshop: MuleSoft for Agentforce
Explore the new version of our hands-on workshop featuring the latest Topic Center and API Catalog updates.
📄 Talk: Power Up Document Processing
Dive into smart automation with MuleSoft IDP, NLP, and Einstein AI for intelligent document workflows.
AI and Data Privacy in 2025: Global Trends



AI and Data Privacy in 2025: Global TrendsInData Labs In this infographic, we explore how businesses can implement effective governance frameworks to address AI data privacy. Understanding it is crucial for developing effective strategies that ensure compliance, safeguard customer trust, and leverage AI responsibly. Equip yourself with insights that can drive informed decision-making and position your organization for success in the future of data privacy.
This infographic contains:
-AI and data privacy: Key findings
-Statistics on AI data privacy in the today’s world
-Tips on how to overcome data privacy challenges
-Benefits of AI data security investments.
Keep up-to-date on how AI is reshaping privacy standards and what this entails for both individuals and organizations.
Build Your Own Copilot & Agents For Devs



Build Your Own Copilot & Agents For DevsBrian McKeiver May 2nd, 2025 talk at StirTrek 2025 Conference.
Linux Professional Institute LPIC-1 Exam.pdf



Linux Professional Institute LPIC-1 Exam.pdfRHCSA Guru Introduction to LPIC-1 Exam - overview, exam details, price and job opportunities
Massive Power Outage Hits Spain, Portugal, and France: Causes, Impact, and On...



Massive Power Outage Hits Spain, Portugal, and France: Causes, Impact, and On...Aqusag Technologies In late April 2025, a significant portion of Europe, particularly Spain, Portugal, and parts of southern France, experienced widespread, rolling power outages that continue to affect millions of residents, businesses, and infrastructure systems.
Splunk Security Update | Public Sector Summit Germany 2025



Splunk Security Update | Public Sector Summit Germany 2025Splunk Splunk Security Update
Sprecher: Marcel Tanuatmadja
Enhancing ICU Intelligence: How Our Functional Testing Enabled a Healthcare I...



Enhancing ICU Intelligence: How Our Functional Testing Enabled a Healthcare I...Impelsys Inc. Impelsys provided a robust testing solution, leveraging a risk-based and requirement-mapped approach to validate ICU Connect and CritiXpert. A well-defined test suite was developed to assess data communication, clinical data collection, transformation, and visualization across integrated devices.
Heap, Types of Heap, Insertion and Deletion



Heap, Types of Heap, Insertion and DeletionJaydeep Kale This pdf will explain what is heap, its type, insertion and deletion in heap and Heap sort
HCL Nomad Web – Best Practices und Verwaltung von Multiuser-Umgebungen



HCL Nomad Web – Best Practices und Verwaltung von Multiuser-Umgebungenpanagenda Webinar Recording: https://www.panagenda.com/webinars/hcl-nomad-web-best-practices-und-verwaltung-von-multiuser-umgebungen/
HCL Nomad Web wird als die nächste Generation des HCL Notes-Clients gefeiert und bietet zahlreiche Vorteile, wie die Beseitigung des Bedarfs an Paketierung, Verteilung und Installation. Nomad Web-Client-Updates werden “automatisch” im Hintergrund installiert, was den administrativen Aufwand im Vergleich zu traditionellen HCL Notes-Clients erheblich reduziert. Allerdings stellt die Fehlerbehebung in Nomad Web im Vergleich zum Notes-Client einzigartige Herausforderungen dar.
Begleiten Sie Christoph und Marc, während sie demonstrieren, wie der Fehlerbehebungsprozess in HCL Nomad Web vereinfacht werden kann, um eine reibungslose und effiziente Benutzererfahrung zu gewährleisten.
In diesem Webinar werden wir effektive Strategien zur Diagnose und Lösung häufiger Probleme in HCL Nomad Web untersuchen, einschließlich
- Zugriff auf die Konsole
- Auffinden und Interpretieren von Protokolldateien
- Zugriff auf den Datenordner im Cache des Browsers (unter Verwendung von OPFS)
- Verständnis der Unterschiede zwischen Einzel- und Mehrbenutzerszenarien
- Nutzung der Client Clocking-Funktion
Cybersecurity Identity and Access Solutions using Azure AD



Cybersecurity Identity and Access Solutions using Azure ADVICTOR MAESTRE RAMIREZ Cybersecurity Identity and Access Solutions using Azure AD
TrustArc Webinar: Consumer Expectations vs Corporate Realities on Data Broker...



TrustArc Webinar: Consumer Expectations vs Corporate Realities on Data Broker...TrustArc Most consumers believe they’re making informed decisions about their personal data—adjusting privacy settings, blocking trackers, and opting out where they can. However, our new research reveals that while awareness is high, taking meaningful action is still lacking. On the corporate side, many organizations report strong policies for managing third-party data and consumer consent yet fall short when it comes to consistency, accountability and transparency.
This session will explore the research findings from TrustArc’s Privacy Pulse Survey, examining consumer attitudes toward personal data collection and practical suggestions for corporate practices around purchasing third-party data.
Attendees will learn:
- Consumer awareness around data brokers and what consumers are doing to limit data collection
- How businesses assess third-party vendors and their consent management operations
- Where business preparedness needs improvement
- What these trends mean for the future of privacy governance and public trust
This discussion is essential for privacy, risk, and compliance professionals who want to ground their strategies in current data and prepare for what’s next in the privacy landscape.
2025-05-Q4-2024-Investor-Presentation.pptx



2025-05-Q4-2024-Investor-Presentation.pptxSamuele Fogagnolo Cloudflare Q4 Financial Results Presentation
TrsLabs - Fintech Product & Business Consulting



TrsLabs - Fintech Product & Business ConsultingTrs Labs Hybrid Growth Mandate Model with TrsLabs
Strategic Investments, Inorganic Growth, Business Model Pivoting are critical activities that business don't do/change everyday. In cases like this, it may benefit your business to choose a temporary external consultant.
An unbiased plan driven by clearcut deliverables, market dynamics and without the influence of your internal office equations empower business leaders to make right choices.
Getting things done within a budget within a timeframe is key to Growing Business - No matter whether you are a start-up or a big company
Talk to us & Unlock the competitive advantage
Cyber Awareness overview for 2025 month of security



Cyber Awareness overview for 2025 month of securityriccardosl1 Cyber awareness training educates employees on risk associated with internet and malicious emails
AI EngineHost Review: Revolutionary USA Datacenter-Based Hosting with NVIDIA ...



AI EngineHost Review: Revolutionary USA Datacenter-Based Hosting with NVIDIA ...SOFTTECHHUB I started my online journey with several hosting services before stumbling upon Ai EngineHost. At first, the idea of paying one fee and getting lifetime access seemed too good to pass up. The platform is built on reliable US-based servers, ensuring your projects run at high speeds and remain safe. Let me take you step by step through its benefits and features as I explain why this hosting solution is a perfect fit for digital entrepreneurs.
Complete Guide to Advanced Logistics Management Software in Riyadh.pdf



Complete Guide to Advanced Logistics Management Software in Riyadh.pdfSoftware Company Explore the benefits and features of advanced logistics management software for businesses in Riyadh. This guide delves into the latest technologies, from real-time tracking and route optimization to warehouse management and inventory control, helping businesses streamline their logistics operations and reduce costs. Learn how implementing the right software solution can enhance efficiency, improve customer satisfaction, and provide a competitive edge in the growing logistics sector of Riyadh.
Designing Low-Latency Systems with Rust and ScyllaDB: An Architectural Deep Dive



Designing Low-Latency Systems with Rust and ScyllaDB: An Architectural Deep DiveScyllaDB Want to learn practical tips for designing systems that can scale efficiently without compromising speed?
Join us for a workshop where we’ll address these challenges head-on and explore how to architect low-latency systems using Rust. During this free interactive workshop oriented for developers, engineers, and architects, we’ll cover how Rust’s unique language features and the Tokio async runtime enable high-performance application development.
As you explore key principles of designing low-latency systems with Rust, you will learn how to:
- Create and compile a real-world app with Rust
- Connect the application to ScyllaDB (NoSQL data store)
- Negotiate tradeoffs related to data modeling and querying
- Manage and monitor the database for consistently low latencies
Andrew Marnell: Transforming Business Strategy Through Data-Driven Insights



Andrew Marnell: Transforming Business Strategy Through Data-Driven InsightsAndrew Marnell With expertise in data architecture, performance tracking, and revenue forecasting, Andrew Marnell plays a vital role in aligning business strategies with data insights. Andrew Marnell’s ability to lead cross-functional teams ensures businesses achieve sustainable growth and operational excellence.
What is Model Context Protocol(MCP) - The new technology for communication bw...



What is Model Context Protocol(MCP) - The new technology for communication bw...Vishnu Singh Chundawat
Splunk for Security: Background & Customer Case Study
- 1. Copyright © 2015 Splunk Inc. Splunk for Security: Background & Customer Case Study
- 3. 3 Agenda Background Why Splunk for Security Customer Case Study • Build out and architecture • Phased approach • Hybrid Cloud/on-premise solution Example Security Use Cases Roadmap & Key Takeaways
- 4. 4 Wipro Overview • Wipro Ltd. (NYSE:WIT) is a global information technology, consulting, and outsourcing company • 158,000+ employees in 175 cities+ across 6 continents • Revenues of $7.5 billion for the financial year ended March 31, 2015 • Wipro uses and supports Splunk in many areas for our customers, including: • transaction analysis • fraud detection • business & IT operations monitoring • process improvement • information security
- 5. 5 Speaker Bio Andrew Gerber: Architect & Consultant, Enterprise Security Solutions, Wipro – Discovered Splunk about 4 years ago My mission is to help customers manage their security requirements efficiently and effectively, and to provide meaningful and measurable benefits while improving their security posture.
- 6. 6 Why Splunk for Security • Slow SIEM platform • Limited capabilities and limited customization options • Data source integration and parsing challenges • Lots of effort to create workarounds instead of creating new capabilities Customer challenges • Great user interface and straightforward/flexible SPL • Fast results • Ability to scale flexibly and affordably • Rapid value realization • Late-binding schema • API and extensibility • Higher ROI potential with a competitive TCO Key reasons we often see Splunk selected for Security use cases over other SIEM tools:
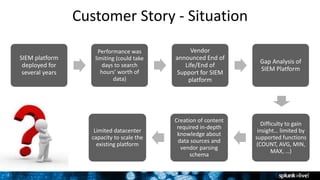
- 7. 7 Customer Story - Situation SIEM platform deployed for several years Performance was limiting (could take days to search hours’ worth of data) Vendor announced End of Life/End of Support for SIEM platform Gap Analysis of SIEM Platform Difficulty to gain insight… limited by supported functions (COUNT, AVG, MIN, MAX, …) Creation of content required in-depth knowledge about data sources and vendor parsing schema Limited datacenter capacity to scale the existing platform
- 8. 8 Splunk – Phase 1 Hybrid POC/Pilot over only 12 weeks! Partnered with Splunk PS 200GB/day On-Premise Deployment Growing to 400GB/day Identified key security data sources to integrate Initial Content Development Dashboards & Demos for stakeholders at all levels, including Executives
- 9. 9 Splunk – Phase 1 Architecture Handled 200GB/day & 10 users comfortably Grew to 400GB/day while still providing sufficient performance >300 Universal Forwarder instances deployed On-Premise Cluster Master Deployment Server 300+ Forwarders Syslog-NG NAS
- 10. 10 Splunk – Phase 1 Results Speed •Searching performance – went from days to seconds to get results •Integrating data sources – ingest first, parse later as needed •Creating searches/dashboards – powerful and straightforward, fast to create Power •SPL, stats, subsearches, graphical reporting, mapping, API, Apps Use cases transformed •Went from listing top machines by # of malware detection alerts to mapping out trends and identifying effective points of intervention/remediation •Went from seeing a list of failed VPN login attempts by user to mapping VPN authentication activity and identifying anomalous activity for further investigation Ability to demo dashboards all the way up to executive leadership
- 11. 11 Scaling successfully: Enter Splunk Cloud Dynamic business context Rapid pace of acquisitions Datacenter transformation project underway Cloud strategy evolving Flexibility of Splunk Cloud was key Availability, capacity, retention, scalability Safeguards & security – beyond the basics Extensive review with Splunk and customer Enterprise Architecture & Security teams Audited Security: Splunk SOC 2 Type 1 & 2 in addition to AWS controls & attestations Flexibility to specify geographic restrictions on where data travels/resides Ability to configure encryption on data at rest Hybrid search heads – can have indexes reside entirely on-prem as needed, on-prem search heads can search cloud
- 12. 12 Splunk – Phase 2 (in progress) Added capacity: 500GB/day Splunk Cloud + 200GB/day on-premise Increasing data source variety, adding apps and integrations (i.e. Remedy for ticketing) Accommodate data center capacity constraints (transformation project underway) Add and integrate users across business units Create processes around security monitoring and SOC operations Deploying Splunk App for Enterprise Security +
- 13. 13 Splunk Phase 2 Architecture On-Premise AWS Cluster Master Deployment Server 500+ Forwarders Syslog-NG ~30% NAS S3
- 14. 14 Example Use Cases Use Case 1 - VPN Activity Profiling • Detect inappropriate or malicious remote access • Profiling of employees, contractors, vendors, and other insiders Use Case 2 – Malware Analysis • Detect new signatures & hashes seen • Enhance information with threat intelligence • Profile activity by host and user • Monitor time to resolution Use Case 3 – Off-Network Jumping • Detect attempted and actual bypass of network controls • Detect network jumping and off-network activity
- 15. 15 Use Case: VPN Activity Profiling • Find abnormal remote access usage pattern in remote access – VPN access with valid credentials used in major attacks, including recent healthcare industry breach • Profile remote usage by employees, contractors, vendors, and other insiders • Look for: – Indicators of Delivery, C2, Exfiltration, as well as employee or insider FTA – Identify potentially compromised credentials • Key points to look for: – Increase in login frequency – Odd times/locations – Improbable travel distance between logins or login attempts (velocity requirements between consecutive geographical login locations too high)
- 16. 16 Use Case: VPN Activity Profiling User level VPN Trends • Multiple login failures by count and over time and successful logins provide insight into VPN behavior. • Identify repeat VPN login failure trends by user Easy to spot outlier and clustered events Geographic & Network VPN Trends • At-a-glance profiling of VPN login success and failures • Geolocation and domain charting identify normal vs. abnormal access • Top Level Domains and other domain names to find anomalies, i.e. connections from .edu TLD or external VPN services
- 17. 17 Use Case: VPN Activity Profiling Geographic Analysis with “Traveler” identification • Per-country trends & users with multiple locations in a given time period • Also identify relative distances for users from a relevant fixed location “Traveler” mapping & improbable behavior analysis • Determine unlikely distance/time combinations between VPN logins • Identify credential theft and/or sharing
- 18. 18 Use Case: Malware Analysis • Understand malware persistence and activity levels – Identify duration of malware persistence – Identify malware by activity levels • Further prioritize remediation – Identifying hosts of interest • Review new signatures and hashes – Understand new threats – Include data enrichment via threat feeds
- 19. 19 Use Case: Malware Analysis Max Malware File Duration • Malware File Duration reflects length of time between first malware message about a specific file and the last malware message (a combination of automated and manual resolution is reflected in this) Max Malware File Events • Malware File Events reflects # of events referencing a specific file (highlights high-activity files)
- 20. 20 Use Case: Malware Analysis Identifying Outliers • Mapping # of malware indicators against timeline and duration of indicator presence allows for easy profiling and identification of hosts
- 21. 21 Use Case: Malware Analysis Tracking new signatures & hashes seen • Understand new threats • Data enrichment with threat intelligence feeds
- 22. 22 Use Case: Off-Network Jumping • Find assets & users jumping from corporate LAN, WLAN to Guest Network – Detect attempts to bypass security controls – Detect malware vector of “benign” off-network browsing 1 in 566 websites host malware (Symantec 2014 Internet Security Threat Report) • Profile jumping behavior to look for patterns and anomalies – Identify the User, IP address, MAC address – Identify activity before and after jumping • Key points to look for include – Assets and users jumping periodically – Normal business users should be on corporate network – Network jumps which don’t appear to be pre-meditated (i.e. looking for programmatic jumps) – Volume, periodicity, destination, traffic type can all be indicators of potential Exfiltration “40% [of companies] reported that they had been exposed to a security threat as a direct consequence of an off-network user’s laptop getting compromised within the last twelve months.” From Google report, “Off-Network Workers – The Weakest Link to Corporate Web Security”
- 23. 23 Key event: Guest network DHCP request Key search to identify this activity • Look at guest network firewall logs which logs DHCP requests (IP MAC hostname) • Look at DHCP requests using IP address of one of our corporate networks, and the MAC address. • Eliminate mobile devices, limit results to our corporate hostname naming convention • Database of internal IP space, hostnames, and associated MAC addresses is being built to further refine this. Use Case: Off-Network Jumping
- 24. 24 Use Case: Off-Network Jumping Selection to lookup user Selection determines drill down Long/Short Term Off-Net Jumping Trends • Visual analysis to determine what looks abnormal • At-a-glance profiling of corporate resources used on guest network – activity for today, 7-days, etc. Rapid investigation to identify users of interest • Selection enables deep investigation via drilldown into user activity details • Dynamic drilldown is a key Splunk feature for effective investigation dashboards
- 25. 25 Use Case: Off-Network Jumping Behavior Investigation – Longitudinal Trending • Patterns identify potential repeat offender, or possible C2/exfiltration • Compare to guest network activity trend to identify likely scenario Having quickly found a user of interest, we can now dig into the details of their activity…
- 26. 26 Use Case: Off-Network Jumping Overview of behavior before/during/after the jump • Looking back in time from the jump • User activity on the corporate network preceding the jump • Looking at the jump • User device mapping to IP address of jumper • Looking in time after the jump • User activity on the guest network after the jump Behavior Investigation – Pre-Jump Activity • Does the jump make sense? – driven by business logic or “benign” behavior • Does the jump look like attacker trying to get out? – more “random” patterns • Does the jump look like insider threat? – exfiltration, etc.
- 27. 27 What’s Next • SOC Operations with Splunk as core tool • Splunk Enterprise Security App • Extreme Search • D3.js • Endpoint • Stream What excites us about future projects we are planning to leverage our data and Splunk products?
- 28. 28 Top Takeaways You can get value out of Splunk quickly Splunk Cloud is a flexible option for growth Basics matter! Process, People, Technology in Balance
- 29. Thank You

