Ad
Splunk workshop-Threat Hunting
- 1. © 2017 SPLUNK INC.© 2017 SPLUNK INC. Threat Hunting With Splunk Lee Imrey | Splunk Security Specialist August 9, 2017 | Chicago, IL
- 2. © 2017 SPLUNK INC. ▶ Threat Hunting Basics ▶ Threat Hunting Data Sources ▶ Know Your Endpoint ▶ Cyber Kill Chain ▶ Walkthrough of Attack Scenario Using Core Splunk (hands on) ▶ Advanced Threat Hunting Techniques & Tools ▶ Enterprise Security Walkthrough ▶ Applying Machine Learning and Data Science to Security Agenda
- 3. © 2017 SPLUNK INC. Hands On? This Won’t Work.
- 4. © 2017 SPLUNK INC. Some familiarity with… ▶CSIRT/SOC Operations ▶General understanding of Threat Intelligence ▶General understanding of DNS, Proxy, and Endpoint types of data Am I in the right place?
- 5. © 2017 SPLUNK INC. What is Threat Hunting, Why do You Need it? 1 The Who, What, Where, When, Why and How of Effective Threat Hunting, SANS Feb 2016 2 Cyber Threat Hunting - Samuel Alonso blog, Jan 2016 “Threat Hunting is not new, it’s just evolving!” Threat hunting - the act of aggressively intercepting, tracking and eliminating cyber adversaries as early as possible in the Cyber Kill Chain2 What? Threats are human. Focused and funded adversaries will not be countered by security boxes on the network alone. Threat hunters are actively searching for threats to prevent or minimize damage [before it happens] 1 Why?
- 7. © 2017 SPLUNK INC. Threat Hunting With Splunk VS
- 8. © 2017 SPLUNK INC. Human Threat Hunter Objectives > Hypotheses > Expertise Key Building Blocks to Drive Threat Hunting Maturity Ref: The Who, What, Where, When, Why and How of Effective Threat Hunting, SANS Feb 2016 Search & Visualisation Enrichment Data Automation
- 9. © 2017 SPLUNK INC. Henry A. Crumpton The Art of Intelligence: Lessons From a Life in the CIA’s Clandestine Service ““A good intelligence officer cultivates an awareness of what he or she does not know. You need a dose of modesty to acknowledge your own ignorance - even more, to seek out your ignorance.”
- 10. © 2017 SPLUNK INC. SANS Threat Hunting Maturity Ad Hoc Search Statistical Analysis Visualization Techniques Aggregation Machine Learning/ Data Science 85% 55% 50% 48% 32% Source: SANS IR & Threat Hunting Summit 2016
- 11. © 2017 SPLUNK INC. Hypotheses Automated Analytics Data Science & Machine Learning Data & Intelligence Enrichment Data Search Visualisation Maturity How Splunk Helps You Drive Threat Hunting Maturity Human Threat Hunter Threat Hunting Automation Integrated & out of the box automation tooling from artifact query, contextual “swim-lane analysis”, anomaly & time series analysis to advanced data science leveraging machine learning Threat Hunting Data Enrichment Enrich data with context and threat-intel across the stack or time to discern deeper patterns or relationships Search & Visualise Relationships for Faster Hunting Search and correlate data while visually fusing results for faster context, analysis and insight Ingest & Onboard Any Threat Hunting Machine Data Source Enable fast ingestion of any machine data through efficient indexing, a big data real time architecture and ‘schema on the read’ technology Search & Visualisation Enrichment Data Automation
- 12. © 2017 SPLUNK INC. ▶ IP Addresses: threat intelligence, blacklist, whitelist, reputation monitoring Tools: Firewalls, Proxies, Splunk Stream, Bro, IDS ▶ Network Artifacts and Patterns: network flow, packet capture, active network connections, historic network connections, ports and services Tools: Splunk Stream, Bro IDS, FPC, Netflow ▶ DNS: activity, queries and responses, zone transfer activity Tools: Splunk Stream, Bro IDS, OpenDNS ▶ Endpoint – Host Artifacts and Patterns: users, processes, services, drivers, files, registry, hardware, memory, disk activity, file monitoring: hash values, integrity checking and alerts, creation or deletion Tools: Windows/Linux, Carbon Black, Tanium, Tripwire, Active Directory ▶ Vulnerability Management Data Tools: Tripwire IP360, Qualys, Nessus ▶ User Behavior Analytics: TTPs, user monitoring, time of day location, HR watchlist Splunk UBA, (All of the above) Hunting Tools: Internal Data
- 13. © 2017 SPLUNK INC. Typical Data Sources Attacker, know relay/C2 sites, infected sites, IOC, attack/campaign intent and attribution Where they went, who talked to whom, attack transmitted, abnormal traffic, malware download What process is running (malicious, abnormal, etc.) Process owner, registry mods, attack/malware artifacts, patching level, attack susceptibility Access level, privileged users, likelihood of infection, where they might be in kill chain Threat intelligence Network Endpoint Access/Identity • Third-party threat intel • Open-source blacklist • Internal threat intelligence • Endpoint (AV/IPS/FW) • Malware detection • PCLM • DHCP • OS logs • Patching • Active Directory • LDAP • CMDB • Operating system • Database • VPN, AAA, SSO • Firewall, IDS, IPS • DNS • Email • Web proxy • NetFlow • Network
- 15. © 2017 SPLUNK INC. ▶ TA Available on the App Store ▶ Great blog post to get you started ▶ Increases the fidelity of Microsoft Logging Know Your Endpoint: Microsoft Sysmon Primer Blog Post: http://blogs.splunk.com/2014/11/24/monitoring-network-traffic-with-sysmon-and-splunk/
- 16. © 2017 SPLUNK INC. Log In Credentials January & February https://od-threat-hunting-wrksp-portland-01.splunkoxygen.com March & April https://od-threat-hunting-wrksp-portland-02.splunkoxygen.com May & June https://od-threat-hunting-wrksp-portland-03.splunkoxygen.com July & August https://od-threat-hunting-wrksp-portland-04.splunkoxygen.com September & October https://od-threat-hunting-wrksp-portland-05.splunkoxygen.com November & December https://od-threat-hunting-wrksp-portland-06.splunkoxygen.com User: hunter Password: pr3dat0r Birth Month
- 17. © 2017 SPLUNK INC. Sysmon Event Tags: Optional Search Maps Network Comm to process_id Process_id creation and mapping to parentprocess_id
- 18. © 2017 SPLUNK INC. sourcetype=X* | search tag=communicate
- 19. © 2017 SPLUNK INC. sourcetype=X* | dedup tag| search tag=process
- 20. © 2017 SPLUNK INC. Data Source Mapping Web Email Endpoint Proxy/DNS CMDB and Threat Intelligence Recon Weaponize Deliver Exploit Install Command & Control Action
- 21. © 2017 SPLUNK INC. Web Email Endpoint Proxy/DNS CMDB and Threat Intelligence Recon Weaponize Deliver Exploit Install Command & Control Action Demo Story - Kill Chain Framework Successful brute force – download sensitive pdf document Weaponize the pdf file with Zeus Malware Convincing email sent with weaponized pdf Vulnerable pdf reader exploited by malware. Dropper created on machinea Dropper retrieves and installs the malware Persistence via regular outbound comm Data exfiltration
- 22. © 2017 SPLUNK INC. Servers Storage DesktopsEmail Web Transaction Records Network Flows DHCP/ DNS Hypervisor Custom Apps Physical Access Badges Threat Intelligence Mobile CMDB Stream Investigations – Choose Your Data Wisely Intrusion Detection Firewall Data Loss Prevention Anti-Malware Vulnerability Scans Traditional Authentication
- 23. © 2017 SPLUNK INC. APT Transaction Flow Across Data Sources .pdf executes & unpacks malware overwriting and running “allowed” programs Threat Intelligence Auth - User Roles Host Activity/Security Network Activity/Security Transaction Gain Access to System Create Additional Environment Conduct Business Svchost.exeCalc.exe Attacker hacks website. Steals .pdf files Web Portal Attacker creates malware, embed in .pdf Read email, open attachment Emails to the target EMAIL HTTP (web) session to command & control server Remote control, Steal data, Persist in company, Rent as botnet WEB Our Investigation begins by detecting high risk communications through the proxy, at the endpoint, and even a DNS call.
- 25. © 2017 SPLUNK INC. To begin our investigation, we will start with a quick search to familiarize ourselves with the data sources. In this demo environment, we have a variety of security relevant data including… Web DNS Proxy Firewall Endpoint Email
- 26. © 2017 SPLUNK INC. Take a look at the endpoint data source. We are using the Microsoft Sysmon TA. We have endpoint visibility into all network communication and can map each connection back to a process. } We also have detailed info on each process and can map it back to the user and parent process. } Lets get our day started by looking using threat intel to prioritize our efforts and focus on communication with known high risk entities.
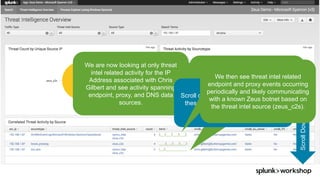
- 27. © 2017 SPLUNK INC. We have multiple source IPs communicating to high risk entities identified by these 2 threat sources. We are seeing high risk communication from multiple data sources. We see multiple threat intel related events across multiple source types associated with the IP Address of Chris Gilbert. Let’s take closer look at the IP Address. We can now see the owner of the system (Chris Gilbert) and that it isn’t a PII or PCI related asset, so there are no immediate business implications that would require informing agencies or external customers within a certain timeframe. This dashboard is based on event data that contains a threat intel based indicator match( IP Address, domain, etc.). The data is further enriched with CMDB based Asset/identity information.
- 28. © 2017 SPLUNK INC. We are now looking at only threat intel related activity for the IP Address associated with Chris Gilbert and see activity spanning endpoint, proxy, and DNS data sources. These trend lines tell a very interesting visual story. It appears that the asset makes a DNS query involving a threat intel related domain or IP Address. ScrollDown Scroll down the dashboard to examine these threat intel events associated with the IP Address. We then see threat intel related endpoint and proxy events occurring periodically and likely communicating with a known Zeus botnet based on the threat intel source (zeus_c2s).
- 29. © 2017 SPLUNK INC. It’s worth mentioning that at this point you could create a ticket to have someone re- image the machine to prevent further damage as we continue our investigation within Splunk. Within the same dashboard, we have access to very high fidelity endpoint data that allows an analyst to continue the investigation in a very efficient manner. It is important to note that near real-time access to this type of endpoint data is not not common within the traditional SOC. The initial goal of the investigation is to determine whether this communication is malicious or a potential false positive. Expand the endpoint event to continue the investigation. Proxy related threat intel matches are important for helping us to prioritize our efforts toward initiating an investigation. Further investigation into the endpoint is often very time consuming and often involves multiple internal hand-offs to other teams or needing to access additional systems. This encrypted proxy traffic is concerning because of the large amount of data (~1.5MB) being transferred which is common when data is being exfiltrated.
- 30. © 2017 SPLUNK INC. Exfiltration of data is a serious concern and outbound communication to external entity that has a known threat intel indicator, especially when it is encrypted as in this case. Lets continue the investigation. Another clue. We also see that svchost.exe should be located in a Windows system directory but this is being run in the user space. Not good. We immediately see the outbound communication with 115.29.46.99 via https is associated with the svchost.exe process on the windows endpoint. The process id is 4768. There is a great deal more information from the endpoint as you scroll down such as the user ID that started the process and the associated CMDB enrichment information.
- 31. © 2017 SPLUNK INC. We have a workflow action that will link us to a Process Explorer dashboard and populate it with the process id extracted from the event (4768).
- 32. © 2017 SPLUNK INC. This is a standard Windows app, but not in its usual directory, telling us that the malware has again spoofed a common file name. We also can see that the parent process that created this suspicuous svchost.exe process is called calc.exe. This has brought us to the Process Explorer dashboard which lets us view Windows Sysmon endpoint data. Suspected Malware Lets continue the investigation by examining the parent process as this is almost certainly a genuine threat and we are now working toward a root cause. This is very consistent with Zeus behavior. The initial exploitation generally creates a downloader or dropper that will then download the Zeus malware. It seems like calc.exe may be that downloader/dropper. Suspected Downloader/Dropper This process calls itself “svchost.exe,” a common Windows process, but the path is not the normal path for svchost.exe. …which is a common trait of malware attempting to evade detection. We also see it making a DNS query (port 53) then communicating via port 443.
- 33. © 2017 SPLUNK INC. The Parent Process of our suspected downloader/dropper is the legitimate PDF Reader program. This will likely turn out to be the vulnerable app that was exploited in this attack. Suspected Downloader/Dropper Suspected Vulnerable AppWe have very quickly moved from threat intel related network and endpoint activity to the likely exploitation of a vulnerable app. Click on the parent process to keep investigating.
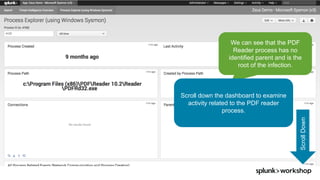
- 34. © 2017 SPLUNK INC. We can see that the PDF Reader process has no identified parent and is the root of the infection. ScrollDown Scroll down the dashboard to examine activity related to the PDF reader process.
- 35. © 2017 SPLUNK INC. Chris opened 2nd_qtr_2014_report.pdf which was an attachment to an email! We have our root cause! Chris opened a weaponized .pdf file which contained the Zeus malware. It appears to have been delivered via email and we have access to our email logs as one of our important data sources. Lets copy the filename 2nd_qtr_2014_report.pdf and search a bit further to determine the scope of this compromise.
- 36. © 2017 SPLUNK INC. Lets dig a little further into 2nd_qtr_2014_report.pdf to determine the scope of this compromise.
- 38. © 2017 SPLUNK INC. Lets search though multiple data sources to quickly get a sense for who else may have have been exposed to this file. We will come back to the web activity that contains reference to the pdf file but lets first look at the email event to determine the scope of this apparent phishing attack.
- 39. © 2017 SPLUNK INC. We have access to the email body and can see why this was such a convincing attack. The sender apparently had access to sensitive insider knowledge and hinted at quarterly results. There is our attachment. Hold On! That’s not our Domain Name! The spelling is close but it’s missing a “t”. The attacker likely registered a domain name that is very close to the company domain hoping Chris would not notice. This looks to be a very targeted spear phishing attack as it was sent to only one employee (Chris).
- 40. © 2017 SPLUNK INC. Root Cause Recap .pdf executes & unpacks malware overwriting and running “allowed” programs Threat Intelligence Endpoint Host Activity/Security Network Activity/Security Transaction Gain Access to System Create Additional Environment Conduct Business Svchost.exeCalc.exe Attacker hacks website. Steals .pdf files Web Portal Attacker creates malware, embed in .pdf Read email, open attachment Emails to the target EMAIL HTTP (web) session to command & control server Remote control, Steal data, Persist in company, Rent as botnet WEB We utilized threat intel to detect communication with known high risk indicators and kick off our investigation then worked backward through the kill chain toward a root cause. Key to this investigative process is the ability to associate network communications with endpoint process data. This high value and very relevant ability to work a malware related investigation through to root cause translates into a very streamlined investigative process compared to the legacy SIEM based approach.
- 41. © 2017 SPLUNK INC. Lets revisit the search for additional information on the 2nd_qtr_2014-_report.pdf file. We understand that the file was delivered via email and opened at the endpoint. Why do we see a reference to the file in the access_combined (web server) logs? Click Select the access_combined sourcetype to investigate further.
- 42. © 2017 SPLUNK INC. The results show 54.211.114.134 has accessed this file from the web portal of buttergames.com. There is also a known threat intel association with the source IP Address downloading (HTTP GET) the file.
- 43. © 2017 SPLUNK INC. Select the IP Address, left-click, then select “New search”. We would like to understand what else this IP Address has accessed in the environment.
- 44. © 2017 SPLUNK INC. That’s an abnormally large number of requests sourced from a single IP Address in a ~90 minute window. This looks like a scripted action given the constant high rate of requests over the below window. ScrollDown Scroll down the dashboard to examine other interesting fields to further investigate. Notice the Googlebot useragent string which is another attempt to avoid raising attention..
- 45. © 2017 SPLUNK INC. The requests from 52.211.114.134 are dominated by requests to the login page (wp-login.php). It’s clearly not possible to attempt a login this many times in a short period of time – this is clearly a scripted brute force attack. After successfully gaining access to our website, the attacker downloaded the pdf file, weaponized it with the zeus malware, then delivered it to Chris Gilbert as a phishing email. The attacker is also accessing admin pages which may be an attempt to establish persistence via a backdoor into the web site.
- 46. © 2017 SPLUNK INC. .pdf executes & unpacks malware overwriting and running “allowed” programs Threat Intelligence Endpoint Host Activity/Security Network Activity/Security Transaction Gain Access to System Create Additional Environment Conduct Business Svchost.exeCalc.exe Attacker hacks website. Steals .pdf files Web Portal Attacker creates malware, embed in .pdf Read email, open attachment Emails to the target EMAIL HTTP (web) session to command & control server Remote control, Steal data, Persist in company, Rent as botnet WEB We continued the investigation by pivoting into the endpoint data source and used a workflow action to determine which process on the endpoint was responsible for the outbound communication. We began by reviewing threat intel related events for a particular IP address and observed DNS, Proxy, and Endpoint events for a user in Sales. Investigation complete! Lets get this turned over to Incident Reponse team. We traced the svchost.exe Zeus malware back to it’s parent process ID which was the calc.exe downloader/dropper. Once our root cause analysis was complete, we shifted out focus into the web logs to determine that the sensitive pdf file was obtained via a brute force attack against the company website. We were able to see which file was opened by the vulnerable app and determined that the malicious file was delivered to the user via email. A quick search into the mail logs revealed the details behind the phishing attack and revealed that the scope of the compromise was limited to just the one user. We traced calc.exe back to the vulnerable application PDF Reader. Kill Chain Analysis Across Data Sources
- 48. © 2017 SPLUNK INC. BONUS! - SQLi - DNS Exfilatration - Splunk Security Essentials
- 50. © 2017 SPLUNK INC. ▶ SQL injection ▶ Code injection ▶ OS commanding ▶ LDAP injection ▶ XML injection ▶ XPath injection ▶ SSI injection ▶ IMAP/SMTP injection ▶ Buffer overflow SQL Injection
- 51. © 2017 SPLUNK INC. Imperva Web Attacks Report, 2015
- 53. © 2017 SPLUNK INC. The Anatomy of an SQL Injection Attack SELECT * FROM users WHERE email='[email protected]' OR 1 = 1 -- ' AND password='xxx'; [email protected]' OR 1 = 1 -- ' xxx [email protected] 1234 An attacker might supply:
- 54. © 2017 SPLUNK INC. …and so far this year… 39
- 56. © 2017 SPLUNK INC. Our learning environment consists of: ▶ A bunch of publically-accessible single Splunk servers ▶ Each with ~5.5M events, from real environments but massaged: • Windows Security events • Apache web access logs • Bro DNS & HTTP • Palo Alto traffic logs • Some other various bits What have we here?
- 57. © 2017 SPLUNK INC. https://splunkbase.splunk.com/app/1528/ Search for possible SQL injection in your events: • looks for patterns in URI query field to see if anyone has injected them with SQL statements • use standard deviations that are 2.5 times greater than the average length of your URI query field ▶ Macros used • sqlinjection_pattern(sourcetype, uri query field) • sqlinjection_stats(sourcetype, uri query field)
- 58. © 2017 SPLUNK INC. Regular Expression FTW sqlinjection_rex is a search macro. It contains: (?<injection>(?i)select.*?from|union.*?select|'$|delete.*?from|update.*?set|alter.*?table|([%27|'](%2 0)*=(%20)*[%27|'])|w*[%27|']or) Which means: In the string we are given, look for ANY of the following matches and put that into the “injection” field. • Anything containing SELECT followed by FROM • Anything containing UNION followed by SELECT • Anything with a ‘ at the end • Anything containing DELETE followed by FROM • Anything containing UPDATE followed by SET • Anything containing ALTER followed by TABLE • A %27 OR a ‘ and then a %20 and any amount of characters then a %20 and then a %27 OR a ‘ • Note: %27 is encoded “’” and %20 is encoded <space> • Any amount of word characters followed by a %27 OR a ‘ and then “or”
- 59. © 2017 SPLUNK INC. Bonus: Try out the SQL Injection app!
- 60. © 2017 SPLUNK INC. ▶ SQL injection provide attackers with easy access to data ▶ Detecting advanced SQL injection is hard – use an app! ▶ Understand where SQLi is happening on your network and put a stop to it. ▶ Augment your WAF with enterprise-wide Splunk searches. Summary: Web Attacks/SQL Injection
- 63. © 2017 SPLUNK INC. DNS exfil tends to be overlooked within an ocean of DNS data. Let’s fix that! DNS Exfiltration
- 64. © 2017 SPLUNK INC. But the big difference is the way how stolen data is exfiltrated: the malware used DNS requests! https://blog.gdatasoftware.com/2014/10/23942-new- frameworkpos-variant-exfiltrates-data-via-dns-requests “ ” … few organizations actually keep detailed logs or records of the DNS traffic traversing their networks — making it an ideal way to siphon data from a hacked network. http://krebsonsecurity.com/2015/05/deconstructing-the-2014-sally-beauty- breach/#more-30872 “ ” ▶ FrameworkPOS: a card-stealing program that exfiltrates data from the target’s network by transmitting it as domain name system (DNS) traffic DNS Exfiltration
- 65. © 2017 SPLUNK INC. https://splunkbase.splunk.com/app/2734/ DNS exfil detection – tricks of the trade ü parse URLs & complicated TLDs (Top Level Domain) ü calculate Shannon Entropy List of provided lookups • ut_parse_simple(url) • ut_parse(url, list) or ut_parse_extended(url, list) • ut_shannon(word) • ut_countset(word, set) • ut_suites(word, sets) • ut_meaning(word) • ut_bayesian(word) • ut_levenshtein(word1, word2)
- 66. © 2017 SPLUNK INC. Layman’s definition: a score reflecting the randomness or measure of uncertainty of a string ▶ Examples • The domain aaaaa.com has a Shannon Entropy score of 1.8 (very low) • The domain google.com has a Shannon Entropy score of 2.6 (rather low) • A00wlkj—(-a.aslkn-C.a.2.sk.esasdfasf1111)-890209uC.4.com has a Shannon Entropy score of 3 (rather high) Shannon Entropy
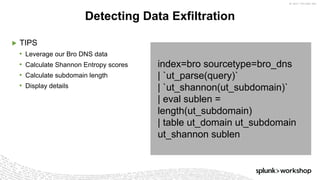
- 67. © 2017 SPLUNK INC. index=bro sourcetype=bro_dns | `ut_parse(query)` | `ut_shannon(ut_subdomain)` | eval sublen = length(ut_subdomain) | table ut_domain ut_subdomain ut_shannon sublen ▶ TIPS • Leverage our Bro DNS data • Calculate Shannon Entropy scores • Calculate subdomain length • Display details Detecting Data Exfiltration
- 68. © 2017 SPLUNK INC. ▶ TIPS • Leverage our Bro DNS data • Calculate Shannon Entropy scores • Calculate subdomain length • Display count, scores, lengths, deviations Detecting Data Exfiltration … | stats count avg(ut_shannon) as avg_sha avg(sublen) as avg_sublen stdev(sublen) as stdev_sublen by ut_domain | search avg_sha>3 avg_sublen>20 stdev_sublen<2
- 69. © 2017 SPLUNK INC. ▶ RESULTS • Exfiltrating data requires many DNS requests – look for high counts • DNS exfiltration to mooo.com and chickenkiller.com Detecting Data Exfiltration
- 70. © 2017 SPLUNK INC. ▶ Exfiltration by DNS and ICMP is a very common technique ▶ Many organizations do not analyze DNS activity – do not be like them! ▶ No DNS logs? No Splunk Stream? Look at FW byte counts Summary: DNS exfiltration
- 72. © 2017 SPLUNK INC. Security Essentials: Free as in Beer
- 73. © 2017 SPLUNK INC. https://splunkbase.splunk.com/app/3435/ Identify bad guys in your environment: ü 45+ use cases common in UEBA products, all free on Splunk Enterprise ü Target external attackers and insider threat ü Scales from small to massive companies ü Save from the app, send results to ES/UBA You can solve use cases today for free, then use Splunk UBA for advanced ML detection.
- 74. © 2017 SPLUNK INC. ▶ First Time Seen Powered by Stats ▶ Time Series Analysis With Standard Deviation ▶ General Security Analytics Searches Splunk Security Essentials Types of Use Cases
- 75. © 2017 SPLUNK INC. Splunk Security Essentials Data Sources Electronic Medical Records Source Code Repository Firewall EmailLogs
- 76. © 2017 SPLUNK INC. How does the app work? How does the app scale? ▶ Leverages primarily | stats for UEBA ▶ Also implements several advanced Splunk searches (URL Toolbox, etc.) ▶ App automates the utilization of high scale techniques ▶ Summary indexing for Time Series, caching in lookup for First Time
- 78. © 2017 SPLUNK INC. Hypotheses Automated Analytics Data Science & Machine Learning Data & Intelligence Enrichment Data Search Visualisation Maturity Threat Hunting With Splunk 78 Splunk Enterprise - Big Data Analytics Platform - Splunk Enterprise Security - Security Analytics Platform - Threat Hunting Data Enrichment Threat Hunting Automation Ingest & Onboard Any Threat Hunting Machine Data Source Search & Visualise Relationships for Faster Hunting User Behavior Analytics - Security Data Science Platform - Search & Visualization Enrichment Data Automation
- 79. © 2017 SPLUNK INC. Other Items To Note Items to Note Navigation - How to Get Here Description of what to click on Click
- 80. © 2017 SPLUNK INC. Key Security Indicators (build your own!) Sparklines Editable
- 81. © 2017 SPLUNK INC. Various ways to filter data Malware-Specific KSIs and Reports Most Popular Signatures Across All Technologies Security Domains -> Endpoint -> Malware Center
- 82. © 2017 SPLUNK INC. Filterable KSIs specific to Risk Risk assigned to system, user or other Under Advanced Threat, select Risk Analysis
- 83. © 2017 SPLUNK INC. (Scroll Down) Recent Risk Activity Under Advanced Threat, Select Risk Analysis
- 84. © 2017 SPLUNK INC. Filterable, down to IoC KSIs specific to Threat Most active threat source Scroll down… Scroll Under Advanced Threat, Select Threat Activity
- 85. © 2017 SPLUNK INC. Specifics about recent threat matches Under Advanced Threat, Select Threat Activity
- 86. © 2017 SPLUNK INC. To add threat intel go to: Configure -> Data Enrichment -> Threat Intelligence Downloads Click
- 87. © 2017 SPLUNK INC. Click “Threat Artifacts” Under “Advanced Threat” Click
- 88. © 2017 SPLUNK INC. Artifact Categories – click different tabs… STIX feed Custom feed Under Advanced Threat, Select Threat Artifacts
- 89. © 2017 SPLUNK INC. Review the Advanced Threat content Click
- 90. © 2017 SPLUNK INC. Data from asset framework Configurable Swimlanes Darker=more events All happened around same timeChange to “Today” if needed Asset Investigator, enter “192.168.56.102”
- 91. © 2017 SPLUNK INC. Data Science & Machine Learning In Security 91
- 92. © 2017 SPLUNK INC. Disclaimer: I am not a data scientist
- 93. © 2017 SPLUNK INC. BIG DATA vs DATA SCIENCE COLLECTION vs INSIGHT
- 94. © 2017 SPLUNK INC. Security data isn’t just big data It’s morbidly obese data
- 95. © 2017 SPLUNK INC. Computer Science Statistics and Math Machine Learning Security Engineer Security Analyst Cyber Security Expertise Security Data Science
- 96. © 2017 SPLUNK INC. Supervised Machine Learning: Focus is to build models that make predictions based on evidence (labeled data) in the presence of uncertainty. As adaptive algorithms identify patterns in data, it "learns" from the observations. Unsupervised Machine Learning: Used to draw inferences from datasets consisting of input data without labeled responses. Semi-Supervised Machine Learning Types of Machine Learning
- 97. © 2017 SPLUNK INC. Types of Machine Learning Supervised Learning: Generalizing from labeled data
- 98. © 2017 SPLUNK INC. ▶ Regression: A regression problem is when the output variable is a real value, such as “authorizations over time”. ▶ Classification: A classification problem is when the output variable is a category, such as “malicious” or “non-malicious.” or “authorized” and “not authorized”. ▶ Anomaly Detection: Identify unusual activity, learn what normal looks like. Example: A history of normal web authorizations to then identify anything significantly different. Supervised Machine Learning
- 99. © 2017 SPLUNK INC. ▶ Regression is used for predictive modeling to investigate the relationship between a dependent (target) and independent variables (predictors). ▶ Examples of regression algorithms: • Linear Regression • Logistic Regression • Stepwise Regression • Multivariate Adaptive Regression Splines (MARS) • Locally Estimated Scatterplot Smoothing (LOESS) • Ordinary Least Squares Regression (OLSR) Supervised Machine Learning Regression
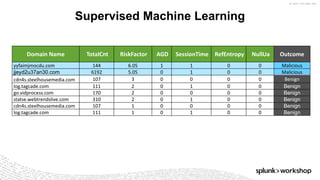
- 101. © 2017 SPLUNK INC. Supervised Machine Learning Domain Name TotalCnt RiskFactor AGD SessionTime RefEntropy NullUa Outcome yyfaimjmocdu.com 144 6.05 1 1 0 0 Malicious jjeyd2u37an30.com 6192 5.05 0 1 0 0 Malicious cdn4s.steelhousemedia.com 107 3 0 0 0 0 Benign log.tagcade.com 111 2 0 1 0 0 Benign go.vidprocess.com 170 2 0 0 0 0 Benign statse.webtrendslive.com 310 2 0 1 0 0 Benign cdn4s.steelhousemedia.com 107 1 0 0 0 0 Benign log.tagcade.com 111 1 0 1 0 0 Benign
- 102. © 2017 SPLUNK INC. Test Raw Security Data Production Supervised Machine Learning Process Algorithm Product Sample Pre/Train/Model Verification
- 103. © 2017 SPLUNK INC. Unsupervised Learning: Generalizing from unlabeled data
- 104. © 2017 SPLUNK INC. ▶ No tuning ▶ Programmatically finds trends Unsupervised Machine Learning Raw Security Data Automated Clustering ▶UBA is primarily unsupervised ▶Rigorously tested for fit Algorithm
- 105. © 2017 SPLUNK INC. Supervised vs. Unsupervised Supervised Learning Unsupervised Learning
- 108. © 2017 SPLUNK INC. ▶ Splunk Supported framework for building ML Apps • Get it for free: http://tiny.cc/splunkmlapp ▶ Leverages Python for Scientific Computing (PSC) add-on: • Open-source Python data science ecosystem • NumPy, SciPy, scitkit-learn, pandas, statsmodels ▶ Showcase use cases: Predict Hard Drive Failure, Server Power Consumption, Application Usage, Customer Churn & more ▶ Standard algorithms out of the box: • Supervised: Logistic Regression, SVM, Linear Regression, Random Forest, etc. • Unsupervised: KMeans, DBSCAN, Spectral Clustering, PCA, KernelPCA, etc. ▶ Implement one of 300+ algorithms by editing Python scripts ML Toolkit & Showcase ML Toolkit and Showcase
- 110. © 2017 SPLUNK INC. Splunk for Analytics and Data Science
- 112. © 2017 SPLUNK INC. Hypotheses Automated Analytics Data Science & Machine Learning Data & Intelligence Enrichment Data Search Visualisation Maturity Threat Hunting With Splunk 112 Splunk Enterprise - Big Data Analytics Platform - Splunk Enterprise Security - Security Analytics Platform - Threat Hunting Data Enrichment Threat Hunting Automation Ingest & Onboard Any Threat Hunting Machine Data Source Search & Visualise Relationships for Faster Hunting User Behavior Analytics - Security Data Science Platform - Search & Visualization Enrichment Data Automation
- 113. © 2017 SPLUNK INC. Machine Learning Security Use Cases 113 MachineLearningUseCases Polymorphic Attack Analysis Behavioral Peer Group Analysis User & Entity Behavior Baseline Entropy/Rare Event Detection Cyber Attack / External Threat Detection Reconnaissance, Botnet and C&C Analysis Lateral Movement Analysis Statistical Analysis Data Exfiltration Models IP Reputation Analysis Insider Threat Detection User/Device Dynamic Fingerprinting
- 114. © 2017 SPLUNK INC. Insider Treats External Threats ▶ Account Takeover • Privileged account compromise • Data exfiltration ▶ Lateral Movement • Pass-the-hash kill chain • Privilege escalation ▶ Suspicious Activity • Misuse of credentials • Geo-location anomalies ▶ Malware Attacks • Hidden malware activity ▶ Botnet, Command & Control • Malware beaconing • Data leakage ▶ User & Entity Behavior Analytics • Suspicious behavior by accounts or devices Splunk UBA Use Cases
- 115. © 2017 SPLUNK INC. ▶ ~100% of breaches involve valid credentials (Mandiant Report) ▶ Need to understand normal & anomalous behaviors for ALL users ▶ UBA detects Advanced Cyberattacks and Malicious Insider Threats ▶ Lots of ML under the hood: • Behavior Baselining & Modeling • Anomaly Detection (30+ models) • Advanced Threat Detection ▶ E.g., Data Exfil Threat: • “Saw this strange login & data transferfor user kwestin at 3am in China…” • Surface threat to SOC Analysts Splunk User Behavior Analytics (UBA)
- 116. © 2017 SPLUNK INC. Raw Security Events Anomalies Anomaly Chains (Threats) Machine Learning Graph Mining Threat Models Lateral Movement Beaconing Land-Speed Violation HCI Anomalies graph Entity relationship graph Kill chain sequence Forensic artifacts Threat/Risk scoring Feedback
- 117. © 2017 SPLUNK INC. Overall Architecture Real-Time Infra (Storm-based) Filter Events Drop Events Model Execution & Online Training Runtime Topologies Threat and Anomaly Review Hadoop/HDFS Data Receivers (flume, REST, etc.) Real-Time Updates/Noti fications App/SaaS Connectors Core + ES Network Data Push/Pull Model Persistence Layer DataDistributed Kafka ETL IR Model Parsers Filters Attribution Control Path –Resource/Health Monitoring HBase/HDFS Direct Access Façade GraphDB SQL Access Layer Node.js Socket.io server SQL Store (Threats/ Anomalies) Time-Series DBModel Registry Model Store HBase Model N Data Model 1 Model N Model 1 Model N Neo4J (Graph visualizations) Rules Engine Anomalies + Threats Analytics Store Syslog and Other Data
- 118. © 2017 SPLUNK INC. Data Flow and System Requirements API CONNECTOR SYSLOG FORWARDER Explore Visualize ShareAnalyze Dashboards Results THREAT & ANOMALY DATA Query UBA Request for additional details Threats Results Query Notable events Risk scoring framework Workflow management VM Search head Standard RT Query VM specs: - Ubuntu/RHEL - 16 cores - 64 GB RAM - Local and network disks - GigE connectivity Performance/scale: - UBA v2.3 - E.g., 5-nodes - 25K EPS - Add nodes for near-linear scale Splunk Enterprise: - RT search capability - 8-10 concurrent searches - REST API port (8089) - SA-LDAPSEARCH Shared network storage
- 120. © 2017 SPLUNK INC. ▶Security Readiness Workshop ▶Data Science Workshop ▶Enterprise Security Benchmark Assessment ▶Boss of the SOC More Security Workshops!





![© 2017 SPLUNK INC.
What is Threat Hunting, Why do You Need it?
1 The Who, What, Where, When, Why and How of Effective Threat Hunting, SANS Feb 2016
2 Cyber Threat Hunting - Samuel Alonso blog, Jan 2016
“Threat Hunting is not new, it’s
just evolving!”
Threat hunting - the act of
aggressively intercepting,
tracking and eliminating cyber
adversaries as early as possible
in the Cyber Kill Chain2
What?
Threats are human. Focused and
funded adversaries will not be
countered by security boxes on
the network alone. Threat
hunters are actively searching for
threats to prevent or minimize
damage [before it happens] 1
Why?](https://image.slidesharecdn.com/ppt-splunkworkshop-threathunting-170811151520/85/Splunk-workshop-Threat-Hunting-5-320.jpg)


















































*=(%20)*[%27|'])|w*[%27|']or)
Which means: In the string we are given, look for ANY of the following matches and put that into the
“injection” field.
• Anything containing SELECT followed by FROM
• Anything containing UNION followed by SELECT
• Anything with a ‘ at the end
• Anything containing DELETE followed by FROM
• Anything containing UPDATE followed by SET
• Anything containing ALTER followed by TABLE
• A %27 OR a ‘ and then a %20 and any amount of characters then a %20 and then a %27 OR a ‘
• Note: %27 is encoded “’” and %20 is encoded <space>
• Any amount of word characters followed by a %27 OR a ‘ and then “or”](https://image.slidesharecdn.com/ppt-splunkworkshop-threathunting-170811151520/85/Splunk-workshop-Threat-Hunting-58-320.jpg)