SplunkLive! Frankfurt 2018 - Use Splunk for Incident Response, Orchestration and Automation
Download as PPTX, PDF2 likes474 views
Presented at SplunkLive! Frankfurt 2018: Incident Response Challenge Tools Scale Adaptive Response Customer Success Key Takeaways
1 of 37
Downloaded 62 times




































Ad
Recommended
SplunkLive! Munich 2018: Use Splunk for incident Response, Orchestration and ...



SplunkLive! Munich 2018: Use Splunk for incident Response, Orchestration and ...Splunk Presented at SplunkLive! Munich:
- Incident Response Challenge
- Tools
- Scale
- Adaptive Response
- Customer Success
SplunkLive! Munich 2018: Legacy SIEM to Splunk, How to Conquer Migration and ...



SplunkLive! Munich 2018: Legacy SIEM to Splunk, How to Conquer Migration and ...Splunk Presented at SplunkLive! Munich 2018:
- Splunk as your SIEM
- SIEM Replacement Customer Success
- Next Steps
SplunkLive! Frankfurt 2018 - Intro to Security Analytics Methods



SplunkLive! Frankfurt 2018 - Intro to Security Analytics MethodsSplunk Splunk Security Essentials provides concise summaries in 3 sentences or less that provide the high level and essential information from the document. The document discusses an introductory presentation on security analytics methods. It includes an agenda that covers an introduction to analytics methods, an example scenario, and next steps. It also discusses common security challenges, different analytics methods and types of use cases, and how analytics can be applied to different stages of an attack.
SplunkLive! Munich 2018: Monitoring the End-User Experience with Splunk



SplunkLive! Munich 2018: Monitoring the End-User Experience with SplunkSplunk Presented at SplunkLive! Munich 2018, gaining insight on both the experience, and the "why" behind the experience.
SplunkLive! Munich 2018: Data Onboarding Overview



SplunkLive! Munich 2018: Data Onboarding OverviewSplunk Presented at SplunkLive! Munich 2018:
- Splunk Data Collection Architecture
- Apps & Technology Add-ons
- Demons / Examples
- Best Practices
- Resources
SplunkLive! Munich 2018: Intro to Security Analytics Methods



SplunkLive! Munich 2018: Intro to Security Analytics MethodsSplunk The document provides an introduction and agenda for a presentation on security analytics methods. The agenda includes an intro to analytics methods from 11:40-12:40 followed by a lunch break from 12:40-13:40. The presentation may include forward-looking statements and disclaimers are provided. Information presented is subject to change and any information about product roadmaps is for informational purposes only.
SplunkLive! Frankfurt 2018 - Predictive, Proactive, and Collaborative ML with...



SplunkLive! Frankfurt 2018 - Predictive, Proactive, and Collaborative ML with...Splunk Presented at SplunkLive! Frankfurt 2018:
What data do we need?
We need Machine Learning
Real Use Case Example
Let's Dive Into How it Works
Next Steps
SplunkLive! Munich 2018: Integrating Metrics and Logs



SplunkLive! Munich 2018: Integrating Metrics and LogsSplunk Presented at SplunkLive! Munich 2018, Integrating Metrics and Logs - Enhanced Troubleshooting and Monitoring
SplunkLive! Munich 2018: Predictive, Proactive, and Collaborative ML with IT ...



SplunkLive! Munich 2018: Predictive, Proactive, and Collaborative ML with IT ...Splunk This document discusses how machine learning (ML) can be used with IT service intelligence (ITSI) to enable predictive, proactive, and collaborative IT operations. It describes how ML can be applied to analyze machine data using ITSI to predict failures and other notable events. This allows operations teams to be notified earlier of potential issues. The document provides an example of using ITSI's built-in ML and event analytics to cluster similar alerts from thousands of events into meaningful, actionable alerts to improve response time. It also discusses integrating ITSI with chat tools like Slack to immediately notify teams to further reduce resolution times.
SplunkLive! Zurich 2018: Monitoring the End User Experience with Splunk



SplunkLive! Zurich 2018: Monitoring the End User Experience with SplunkSplunk This document discusses using Splunk to gain insights into end user experience and the factors that influence experience. Splunk provides a platform approach to monitor applications across the full technology stack from networks to databases. It can ingest data from various sources, including APM tools, and provide visibility into both instrumented and non-instrumented applications and environments. Splunk also offers predictive analytics capabilities and allows various stakeholders like operations and business teams to access and analyze data. The document demonstrates how Splunk can help organizations improve user experience, application performance, and collaboration between teams.
SplunkLive! Frankfurt 2018 - Integrating Metrics & Logs



SplunkLive! Frankfurt 2018 - Integrating Metrics & LogsSplunk Presented at SplunkLive! Frankfurt 2018:
Introduction to Splunk for IT Troubleshooting & Monitoring
Metrics Overview
Examples
SplunkLive! Zurich 2018: Use Splunk for Incident Response, Orchestration and ...



SplunkLive! Zurich 2018: Use Splunk for Incident Response, Orchestration and ...Splunk This document discusses using Splunk for incident response, orchestration, and automation. It notes that incident response currently takes significant time, with containment and response phases accounting for 72% of the time spent on incidents. It proposes that security operations need to change through orchestration and automation using adaptive response. Adaptive response aims to accelerate detection, investigation, and response by centrally automating data retrieval, sharing, and response actions across security tools and domains. This improves efficiency and extracts new insights through leveraging shared context and actions.
SplunkLive! Munich 2018: Get More From Your Machine Data Splunk & AI



SplunkLive! Munich 2018: Get More From Your Machine Data Splunk & AISplunk Presented at SplunkLive! Munich 2018:
- Why AI & Machine Learning?
- What is Machine Learning?
- Splunk's Machine Learning Tour
- Use Cases & Customer Stories
SplunkLive! Frankfurt 2018 - Get More From Your Machine Data with Splunk AI



SplunkLive! Frankfurt 2018 - Get More From Your Machine Data with Splunk AISplunk Presented at SpluknLive! Frankfurt 2018:
Why AI & Machine Learning?
What is Machine Learning?
Splunk's Machine Learning Tour
Use Cases & Customer Stories
Wrap Up
SplunkLive! Frankfurt 2018 - Legacy SIEM to Splunk, How to Conquer Migration ...



SplunkLive! Frankfurt 2018 - Legacy SIEM to Splunk, How to Conquer Migration ...Splunk Presented at SplunkLive! Frankfurt 2018:
Introduction
SIEM Migration Methodology
Use Cases
Datasources & Data Onboarding
ES Architecture
Third-Party Integrations
You Got This!
Splunk Discovery: Warsaw 2018 - Intro to Security Analytics Methods



Splunk Discovery: Warsaw 2018 - Intro to Security Analytics MethodsSplunk Presented at Splunk Discovery Warsaw 2018:
Intro to Analytics Methods
Example Scenario
Next Steps
SplunkLive! Zurich 2018: Intro to Security Analytics Methods



SplunkLive! Zurich 2018: Intro to Security Analytics MethodsSplunk Detect Spikes
Data Source: box_logs
Field to Sum: bytes_downloaded
Group By: user, folder
Time Frame: Last 30 days
Alert on Spikes > 3 Standard Deviations
Schedule Alert: Yes
Custom Splunk Search
Let's Build a Custom Search Together
Click "Build Search"
© 2018 SPLUNK INC.
Here is the search we built:
index=box_logs
| stats sum(bytes_downloaded) as bytes
by user, folder
| timechart span=1d
| anomalydetection direction=both
threshold=3
| where folder="Proposals"
|
SplunkLive! Paris 2018: Use Splunk for Incident Response, Orchestration and A...



SplunkLive! Paris 2018: Use Splunk for Incident Response, Orchestration and A...Splunk Presented at SplunkLive! Paris 2018:
- Challenges with Security Operations Today
- Overview of Splunk Adaptive Response Initiative
- Technology behind the Adaptive Response Framework
- Demonstrations
- How to build your own AR Action
- Resources
SplunkLive! Munich 2018: Getting Started with Splunk Enterprise



SplunkLive! Munich 2018: Getting Started with Splunk EnterpriseSplunk The document provides an agenda for a SplunkLive! presentation on installing and using Splunk. It includes downloading required files, importing sample data, conducting searches on the data, and exploring various Splunk features through a live demonstration. Common installation problems are also addressed. The presentation aims to provide attendees with the knowledge and skills to get started using Splunk through hands-on learning and a question and answer session.
SplunkLive! Zurich 2018: Legacy SIEM to Splunk, How to Conquer Migration and ...



SplunkLive! Zurich 2018: Legacy SIEM to Splunk, How to Conquer Migration and ...Splunk This document provides an overview of best practices for migrating from a legacy SIEM to Splunk Enterprise Security. It discusses identifying high-value use cases to prioritize for migration. Proper data source onboarding using technologies like the Universal Forwarder and Technology Add-ons is also covered. The presentation recommends planning the target architecture and identifying any necessary third-party integrations. Some preparatory steps customers can take today to get ready for the replacement are also listed.
Splunk Discovery: Warsaw 2018 - Reimagining IT with Service Intelligence



Splunk Discovery: Warsaw 2018 - Reimagining IT with Service IntelligenceSplunk Presented at Splunk Discovery Warsaw 2018:
What's Service Intelligence and Why You Should Care
Introduction to Splunk IT Service Intelligence
IT Service Intelligence Key Concepts
Demo
SplunkLive! Frankfurt 2018 - Monitoring the End User Experience with Splunk



SplunkLive! Frankfurt 2018 - Monitoring the End User Experience with SplunkSplunk Presented at SplunkLive! Frankfurt 2018:
Monitoring App Experience...And the App
Splunk and APM
Demo/Customer Stories
Key Takeaways
SplunkLive! Frankfurt 2018 - Getting Hands On with Splunk Enterprise



SplunkLive! Frankfurt 2018 - Getting Hands On with Splunk EnterpriseSplunk This presentation introduces Splunk software. It provides an overview of Splunk capabilities including indexing and searching machine data from various sources. The presentation demonstrates how to install Splunk, onboard sample data, and perform searches including field extractions, dashboards and alerts. It concludes with information on Splunk documentation, support and community resources.
SplunkLive! Paris 2018: Event Management Is Dead



SplunkLive! Paris 2018: Event Management Is DeadSplunk Presented at SplunkLive! Paris 2018: Event Management is Dead - Splunk IT Service Intelligence (ISTI) for Event Analytics
Splunk for Enterprise Security and User Behavior Analytics



Splunk for Enterprise Security and User Behavior AnalyticsSplunk This session will review Splunk’s two premium solutions for information security organizations: Splunk for Enterprise Security (ES) and Splunk User Behavior Analytics (UBA). Splunk ES is Splunk's award-winning security intelligence solution that brings immediate value for continuous monitoring across SOC and incident response environments – allowing you to quickly detect and respond to external and internal attacks, simplifying threat management while decreasing risk. Splunk UBA is a new technology that applies unsupervised machine learning and data science to solving one of the biggest problems in information security today: insider threat. You’ll learn how Splunk UBA works in tandem with ES, or third-party data sources, to bring significant automated analytical power to your SOC and Incident Response teams. We’ll discuss each solution and see them integrated and in action through detailed demos.
The Splunk AISecOps Initiative - Splunk Security Roundtable: Zurich 2018



The Splunk AISecOps Initiative - Splunk Security Roundtable: Zurich 2018Splunk From event to automated incident response. Presentation by Angelo Brancato, Security Specialist, EMEA and Juerg Fischer, Senior Sales Engineer - Splunk.
SplunkLive! Zurich 2018: Get More From Your Machine Data with Splunk & AI



SplunkLive! Zurich 2018: Get More From Your Machine Data with Splunk & AISplunk This presentation discusses how Splunk and machine learning can help organizations get more value from their machine data. It describes how machine learning can improve decision making, uncover hidden trends, alert on deviations, and forecast incidents. The presentation provides an overview of Splunk's machine learning capabilities, including search, packaged solutions, and the machine learning toolkit. It also showcases several customer use cases that have benefited from Splunk's machine learning offerings, such as network incident detection, security/fraud prevention, and optimizing operations.
SplunkLive! London 2017 - Building an Analytics Driven Security Operation Cen...



SplunkLive! London 2017 - Building an Analytics Driven Security Operation Cen...Splunk This document discusses building an analytics-driven security operations center (SOC). It begins with an overview of traditional SOCs and their limitations, such as focusing primarily on alerts. It then discusses emerging trends in security operations that are driving the need for an analytics-driven SOC, such as the focus on detection and response. The document proposes seven enablers for building an analytics-driven SOC using Splunk, including selecting the right sourcing strategy, adopting an adaptive security architecture, optimizing threat intelligence management, deploying advanced analytics like machine learning, enabling proactive threat hunting, promoting automation and efficiency, and driving broader enterprise insights.
Splunk-Presentation 



Splunk-Presentation PrasadThorat23 The document provides an overview of the Splunk data platform. It discusses how Splunk helps organizations overcome challenges in turning real-time data into action. Splunk provides a single platform to investigate, monitor, and take action on any type of machine data from any source. It enables multiple use cases across IT, security, and business domains. The document highlights some of Splunk's products, capabilities, and customer benefits.
Splunk Discovery Day Dubai 2017 - Security Keynote



Splunk Discovery Day Dubai 2017 - Security KeynoteSplunk This document discusses Splunk's security vision, strategy, and platform. It outlines Splunk's positioning as a leader in security information and event management. It describes Splunk's security portfolio and how the platform can be used to prevent, detect, respond to and predict security threats. It also provides examples of how Splunk has helped customers in various industries improve their security operations and gain insights from security and other machine data.
Ad
More Related Content
What's hot (20)
SplunkLive! Munich 2018: Predictive, Proactive, and Collaborative ML with IT ...



SplunkLive! Munich 2018: Predictive, Proactive, and Collaborative ML with IT ...Splunk This document discusses how machine learning (ML) can be used with IT service intelligence (ITSI) to enable predictive, proactive, and collaborative IT operations. It describes how ML can be applied to analyze machine data using ITSI to predict failures and other notable events. This allows operations teams to be notified earlier of potential issues. The document provides an example of using ITSI's built-in ML and event analytics to cluster similar alerts from thousands of events into meaningful, actionable alerts to improve response time. It also discusses integrating ITSI with chat tools like Slack to immediately notify teams to further reduce resolution times.
SplunkLive! Zurich 2018: Monitoring the End User Experience with Splunk



SplunkLive! Zurich 2018: Monitoring the End User Experience with SplunkSplunk This document discusses using Splunk to gain insights into end user experience and the factors that influence experience. Splunk provides a platform approach to monitor applications across the full technology stack from networks to databases. It can ingest data from various sources, including APM tools, and provide visibility into both instrumented and non-instrumented applications and environments. Splunk also offers predictive analytics capabilities and allows various stakeholders like operations and business teams to access and analyze data. The document demonstrates how Splunk can help organizations improve user experience, application performance, and collaboration between teams.
SplunkLive! Frankfurt 2018 - Integrating Metrics & Logs



SplunkLive! Frankfurt 2018 - Integrating Metrics & LogsSplunk Presented at SplunkLive! Frankfurt 2018:
Introduction to Splunk for IT Troubleshooting & Monitoring
Metrics Overview
Examples
SplunkLive! Zurich 2018: Use Splunk for Incident Response, Orchestration and ...



SplunkLive! Zurich 2018: Use Splunk for Incident Response, Orchestration and ...Splunk This document discusses using Splunk for incident response, orchestration, and automation. It notes that incident response currently takes significant time, with containment and response phases accounting for 72% of the time spent on incidents. It proposes that security operations need to change through orchestration and automation using adaptive response. Adaptive response aims to accelerate detection, investigation, and response by centrally automating data retrieval, sharing, and response actions across security tools and domains. This improves efficiency and extracts new insights through leveraging shared context and actions.
SplunkLive! Munich 2018: Get More From Your Machine Data Splunk & AI



SplunkLive! Munich 2018: Get More From Your Machine Data Splunk & AISplunk Presented at SplunkLive! Munich 2018:
- Why AI & Machine Learning?
- What is Machine Learning?
- Splunk's Machine Learning Tour
- Use Cases & Customer Stories
SplunkLive! Frankfurt 2018 - Get More From Your Machine Data with Splunk AI



SplunkLive! Frankfurt 2018 - Get More From Your Machine Data with Splunk AISplunk Presented at SpluknLive! Frankfurt 2018:
Why AI & Machine Learning?
What is Machine Learning?
Splunk's Machine Learning Tour
Use Cases & Customer Stories
Wrap Up
SplunkLive! Frankfurt 2018 - Legacy SIEM to Splunk, How to Conquer Migration ...



SplunkLive! Frankfurt 2018 - Legacy SIEM to Splunk, How to Conquer Migration ...Splunk Presented at SplunkLive! Frankfurt 2018:
Introduction
SIEM Migration Methodology
Use Cases
Datasources & Data Onboarding
ES Architecture
Third-Party Integrations
You Got This!
Splunk Discovery: Warsaw 2018 - Intro to Security Analytics Methods



Splunk Discovery: Warsaw 2018 - Intro to Security Analytics MethodsSplunk Presented at Splunk Discovery Warsaw 2018:
Intro to Analytics Methods
Example Scenario
Next Steps
SplunkLive! Zurich 2018: Intro to Security Analytics Methods



SplunkLive! Zurich 2018: Intro to Security Analytics MethodsSplunk Detect Spikes
Data Source: box_logs
Field to Sum: bytes_downloaded
Group By: user, folder
Time Frame: Last 30 days
Alert on Spikes > 3 Standard Deviations
Schedule Alert: Yes
Custom Splunk Search
Let's Build a Custom Search Together
Click "Build Search"
© 2018 SPLUNK INC.
Here is the search we built:
index=box_logs
| stats sum(bytes_downloaded) as bytes
by user, folder
| timechart span=1d
| anomalydetection direction=both
threshold=3
| where folder="Proposals"
|
SplunkLive! Paris 2018: Use Splunk for Incident Response, Orchestration and A...



SplunkLive! Paris 2018: Use Splunk for Incident Response, Orchestration and A...Splunk Presented at SplunkLive! Paris 2018:
- Challenges with Security Operations Today
- Overview of Splunk Adaptive Response Initiative
- Technology behind the Adaptive Response Framework
- Demonstrations
- How to build your own AR Action
- Resources
SplunkLive! Munich 2018: Getting Started with Splunk Enterprise



SplunkLive! Munich 2018: Getting Started with Splunk EnterpriseSplunk The document provides an agenda for a SplunkLive! presentation on installing and using Splunk. It includes downloading required files, importing sample data, conducting searches on the data, and exploring various Splunk features through a live demonstration. Common installation problems are also addressed. The presentation aims to provide attendees with the knowledge and skills to get started using Splunk through hands-on learning and a question and answer session.
SplunkLive! Zurich 2018: Legacy SIEM to Splunk, How to Conquer Migration and ...



SplunkLive! Zurich 2018: Legacy SIEM to Splunk, How to Conquer Migration and ...Splunk This document provides an overview of best practices for migrating from a legacy SIEM to Splunk Enterprise Security. It discusses identifying high-value use cases to prioritize for migration. Proper data source onboarding using technologies like the Universal Forwarder and Technology Add-ons is also covered. The presentation recommends planning the target architecture and identifying any necessary third-party integrations. Some preparatory steps customers can take today to get ready for the replacement are also listed.
Splunk Discovery: Warsaw 2018 - Reimagining IT with Service Intelligence



Splunk Discovery: Warsaw 2018 - Reimagining IT with Service IntelligenceSplunk Presented at Splunk Discovery Warsaw 2018:
What's Service Intelligence and Why You Should Care
Introduction to Splunk IT Service Intelligence
IT Service Intelligence Key Concepts
Demo
SplunkLive! Frankfurt 2018 - Monitoring the End User Experience with Splunk



SplunkLive! Frankfurt 2018 - Monitoring the End User Experience with SplunkSplunk Presented at SplunkLive! Frankfurt 2018:
Monitoring App Experience...And the App
Splunk and APM
Demo/Customer Stories
Key Takeaways
SplunkLive! Frankfurt 2018 - Getting Hands On with Splunk Enterprise



SplunkLive! Frankfurt 2018 - Getting Hands On with Splunk EnterpriseSplunk This presentation introduces Splunk software. It provides an overview of Splunk capabilities including indexing and searching machine data from various sources. The presentation demonstrates how to install Splunk, onboard sample data, and perform searches including field extractions, dashboards and alerts. It concludes with information on Splunk documentation, support and community resources.
SplunkLive! Paris 2018: Event Management Is Dead



SplunkLive! Paris 2018: Event Management Is DeadSplunk Presented at SplunkLive! Paris 2018: Event Management is Dead - Splunk IT Service Intelligence (ISTI) for Event Analytics
Splunk for Enterprise Security and User Behavior Analytics



Splunk for Enterprise Security and User Behavior AnalyticsSplunk This session will review Splunk’s two premium solutions for information security organizations: Splunk for Enterprise Security (ES) and Splunk User Behavior Analytics (UBA). Splunk ES is Splunk's award-winning security intelligence solution that brings immediate value for continuous monitoring across SOC and incident response environments – allowing you to quickly detect and respond to external and internal attacks, simplifying threat management while decreasing risk. Splunk UBA is a new technology that applies unsupervised machine learning and data science to solving one of the biggest problems in information security today: insider threat. You’ll learn how Splunk UBA works in tandem with ES, or third-party data sources, to bring significant automated analytical power to your SOC and Incident Response teams. We’ll discuss each solution and see them integrated and in action through detailed demos.
The Splunk AISecOps Initiative - Splunk Security Roundtable: Zurich 2018



The Splunk AISecOps Initiative - Splunk Security Roundtable: Zurich 2018Splunk From event to automated incident response. Presentation by Angelo Brancato, Security Specialist, EMEA and Juerg Fischer, Senior Sales Engineer - Splunk.
SplunkLive! Zurich 2018: Get More From Your Machine Data with Splunk & AI



SplunkLive! Zurich 2018: Get More From Your Machine Data with Splunk & AISplunk This presentation discusses how Splunk and machine learning can help organizations get more value from their machine data. It describes how machine learning can improve decision making, uncover hidden trends, alert on deviations, and forecast incidents. The presentation provides an overview of Splunk's machine learning capabilities, including search, packaged solutions, and the machine learning toolkit. It also showcases several customer use cases that have benefited from Splunk's machine learning offerings, such as network incident detection, security/fraud prevention, and optimizing operations.
SplunkLive! London 2017 - Building an Analytics Driven Security Operation Cen...



SplunkLive! London 2017 - Building an Analytics Driven Security Operation Cen...Splunk This document discusses building an analytics-driven security operations center (SOC). It begins with an overview of traditional SOCs and their limitations, such as focusing primarily on alerts. It then discusses emerging trends in security operations that are driving the need for an analytics-driven SOC, such as the focus on detection and response. The document proposes seven enablers for building an analytics-driven SOC using Splunk, including selecting the right sourcing strategy, adopting an adaptive security architecture, optimizing threat intelligence management, deploying advanced analytics like machine learning, enabling proactive threat hunting, promoting automation and efficiency, and driving broader enterprise insights.
Similar to SplunkLive! Frankfurt 2018 - Use Splunk for Incident Response, Orchestration and Automation (20)
Splunk-Presentation 



Splunk-Presentation PrasadThorat23 The document provides an overview of the Splunk data platform. It discusses how Splunk helps organizations overcome challenges in turning real-time data into action. Splunk provides a single platform to investigate, monitor, and take action on any type of machine data from any source. It enables multiple use cases across IT, security, and business domains. The document highlights some of Splunk's products, capabilities, and customer benefits.
Splunk Discovery Day Dubai 2017 - Security Keynote



Splunk Discovery Day Dubai 2017 - Security KeynoteSplunk This document discusses Splunk's security vision, strategy, and platform. It outlines Splunk's positioning as a leader in security information and event management. It describes Splunk's security portfolio and how the platform can be used to prevent, detect, respond to and predict security threats. It also provides examples of how Splunk has helped customers in various industries improve their security operations and gain insights from security and other machine data.
Splunk for Enterprise Security featuring User Behavior Analytics



Splunk for Enterprise Security featuring User Behavior AnalyticsSplunk This session will review Splunk’s two premium solutions - Splunk Enterprise Security (ES) is Splunk's award-winning security intelligence solution that brings immediate value for continuous monitoring across SOC and
incident response environments. Splunk UBA is a new technology that applies unsupervised machine learning and data science to solving one of the biggest problems in information security today: insider threat. You’ll learn how Splunk UBA works in tandem with ES, or third-party data sources, to bring significant automated analytical power to your SOC and Incident Response teams.
Splunk for Enterprise Security featuring UBA Breakout Session



Splunk for Enterprise Security featuring UBA Breakout SessionSplunk Splunk User Behavior Analytics (UBA) 2.2 provides enhanced security analytics and detection capabilities. It uses machine learning to establish baseline behaviors and detect anomalies. UBA analyzes activities across users, hosts, networks, applications and data to identify potential threats. The latest version features expanded visibility metrics, custom threat modeling capabilities, and improved context enrichment through integrations with additional security technologies.
Splunk Discovery: Warsaw 2018 - Legacy SIEM to Splunk, How to Conquer Migrati...



Splunk Discovery: Warsaw 2018 - Legacy SIEM to Splunk, How to Conquer Migrati...Splunk Presented at Splunk Discovery Warsaw 2018:
SIEM Replacement Methodology
Use Cases
Data Sources & Data Onboarding
Architecture
Third Party Integration
You Got This!
Exploring Frameworks of Splunk Enterprise Security



Exploring Frameworks of Splunk Enterprise SecuritySplunk This document discusses Splunk Enterprise Security and its frameworks for addressing security operations challenges. It provides an overview of Splunk's security portfolio and how it can help with issues like slow investigations, limited data ingestion, and inflexible deployments faced by legacy SIEMs. Key frameworks covered include the Notable Events framework for streamlining incident management across the entire lifecycle from detection to remediation. It also discusses the Asset and Identity framework for automatically enriching incidents with relevant context to help with rapid qualification and situational awareness.
Splunk Enterprise Security



Splunk Enterprise SecuritySplunk This document discusses Splunk Enterprise Security and its frameworks for analyzing security data. It provides an overview of Splunk's security portfolio and how it addresses challenges with legacy SIEM solutions. Key frameworks covered include Notable Events for streamlining incident management, Asset and Identity for enriching incidents with contextual data, Risk Analysis for prioritizing incidents based on quantitative risk scores, and Threat Intelligence for detecting indicators of compromise in machine data. Interactive dashboards and incident review interfaces are highlighted as ways to investigate threats and monitor the security posture.
Exploring Frameworks of Splunk Enterprise Security 



Exploring Frameworks of Splunk Enterprise Security Splunk This document discusses Splunk Enterprise Security and its frameworks for analyzing security data. It begins with an introduction and agenda. It then discusses Splunk's analytics-driven security information and event management (SIEM) capabilities. The main part of the presentation covers Splunk's frameworks for enterprise security, including the Notable Events framework for streamlining incident management and the Asset and Identity framework for automatically mapping context to incidents. It provides examples of how these frameworks enable faster incident review and investigation.
Accelerate Incident Response with Orchestration & Automation



Accelerate Incident Response with Orchestration & AutomationSplunk Daily IT security operations processes have not changed significantly over the past decade, but that all stands to change now that a new technology has arrived—enabling security teams to work smarter, respond faster, and improve their defenses. With Security Orchestration, Automation and Response (SOAR) technology, mundane processes can be handled by computers, allowing the SOC team to focus on identifying and responding to the real threats and attacks. This session examines traditional SOC processes and what becomes possible with a SOAR platform like Splunk Phantom. Whether it's a two-person security operation or a full complement SOC, learn to identify the processes that computers can handle on your behalf, and how to go beyond simple use cases and leverage all of the available security tools in your arsenal to the max.
Power the SOC of the Future with scale, speed and choice - Splunk Public Sect...



Power the SOC of the Future with scale, speed and choice - Splunk Public Sect...Splunk EMEA Power the SOC of the Future with scale, speed and choice - Splunk Public Sector Summit 2024
Sprecher:
Matthias Maier (Security Market Advisor, EMEA CEH, CISSP, CISM)
Splunk Webinar: Webinar: Die Effizienz Ihres SOC verbessern mit neuen Funktio...



Splunk Webinar: Webinar: Die Effizienz Ihres SOC verbessern mit neuen Funktio...Splunk Splunk Webinar: Webinar: Die Effizienz Ihres SOC verbessern mit neuen Funktionalitäten in Splunk Enterprise Security und UBA
24. Juni 2016
Accelerate incident Response Using Orchestration and Automation 



Accelerate incident Response Using Orchestration and Automation Splunk This document discusses how orchestration and automation can accelerate incident response. It notes that incident response currently takes a significant amount of time, with the majority of time spent on containment and remediation. It also states that most organizations use too many security tools that are not integrated. The document promotes the use of security orchestration and automation response (SOAR) to help coordinate security actions across tools. It describes Splunk's security portfolio including the Splunk Phantom product, which allows users to automate repetitive tasks, execute automated actions quickly, and coordinate complex workflows to strengthen defenses and accelerate incident response.
Accelerate incident Response Using Orchestration and Automation 



Accelerate incident Response Using Orchestration and Automation Splunk This document discusses how orchestration and automation can accelerate incident response. It notes that incident response currently takes a significant amount of time, with the majority of time spent on containment and remediation. It also states that most organizations use too many security tools that are not integrated. The document promotes the use of security orchestration and automation response (SOAR) to help coordinate security actions across tools. It describes Splunk's security portfolio, including the Splunk Phantom product, which allows organizations to automate repetitive tasks, execute actions more quickly, and strengthen defenses by integrating various security tools.
SplunkLive! London 2017 - Travis Perkins



SplunkLive! London 2017 - Travis PerkinsSplunk The document discusses building a lean security operations center (SOC) at Travis Perkins Group. It describes challenges with their complex IT environment and the need for a flexible security information and event management (SIEM) solution. An initial "big bang" SIEM implementation was unsuccessful. The new approach takes an incremental, lean approach using Splunk Cloud to provide flexible alerting and meet multiple stakeholder needs. This has helped improve security incident response and provided benefits like reduced infrastructure management. Future plans include expanding the use of Splunk analytics and machine learning.
SplunkLive! Paris 2018: Intro to Security Analytics Methods



SplunkLive! Paris 2018: Intro to Security Analytics MethodsSplunk Presented at SplunkLive! Paris 2018:
- Intro to Analytics Methods
- Example Scenario
- Next Steps
Splunk Discovery: Warsaw 2018 - Solve Your Security Challenges with Splunk En...



Splunk Discovery: Warsaw 2018 - Solve Your Security Challenges with Splunk En...Splunk This document summarizes how Splunk Enterprise Security can help organizations strengthen their security posture and operationalize security processes. It discusses how Splunk ES allows organizations to centralize analysis of endpoint, network, identity, and threat data for improved visibility. It also emphasizes developing an investigative mindset when handling alerts to efficiently determine the root cause. Finally, it explains how Splunk ES can operationalize security processes by providing a single source of truth and integrating security technologies to automate responses.
Splunk for Enterprise Security Featuring UBA



Splunk for Enterprise Security Featuring UBASplunk This document provides an overview and summary of Splunk's security products, including Enterprise Security and User Behavior Analytics. It discusses the key capabilities and features of these products, such as detecting advanced cyberattacks, identifying insider threats through machine learning, and integrating UBA with SIEM for improved threat detection. New features in recent versions are highlighted, like custom threat modeling and enhanced visibility into user, device, application, and protocol activity. Customer testimonials praise Splunk UBA's data-science approach to finding hidden threats.
Splunk Discovery Köln - 17-01-2020 - Accelerate Incident Response



Splunk Discovery Köln - 17-01-2020 - Accelerate Incident ResponseSplunk The document discusses Splunk Incident Response, orchestration and automation capabilities. It notes that incident response currently takes significant time, from months for detection to days for containment and remediation. Splunk aims to accelerate this process through automation, orchestration and its security operations platform to integrate tools, streamline workflows and automate repetitive tasks. The presentation demonstrates Splunk's Phantom security orchestration product and how it can automate security tasks like malware investigations to reduce response times.
Splunk for Enterprise Security featuring UBA Breakout Session



Splunk for Enterprise Security featuring UBA Breakout SessionSplunk This document provides an overview of a presentation given by Dave Herrald, a security architect at Splunk, on Splunk's Enterprise Security and User Behavior Analytics solutions. The presentation covered new features in Splunk Enterprise Security 4.1, including enhanced threat intelligence integration, risk-based searching and incident review, and integration with Splunk User Behavior Analytics. It also reviewed capabilities in Splunk User Behavior Analytics 2.2 like custom threat modeling, expanded attack coverage, and context enrichment.
Splunk Phantom SOAR Roundtable



Splunk Phantom SOAR RoundtableSplunk A presentation from the Splunk Phantom roundtable on Security Orchestration, Automation, & Response (SOAR) Security. September 2018
Ad
More from Splunk (20)
Splunk Security Update | Public Sector Summit Germany 2025



Splunk Security Update | Public Sector Summit Germany 2025Splunk Splunk Security Update
Sprecher: Marcel Tanuatmadja
Building Resilience with Energy Management for the Public Sector



Building Resilience with Energy Management for the Public SectorSplunk Splunk Public Sector Summit Germany April 2025
Präsentation: Building Resilience
with Energy
Management for
the Public Sector
IT-Lagebild: Observability for Resilience (SVA)



IT-Lagebild: Observability for Resilience (SVA)Splunk Splunk Public Sector Summit Germany April 2025
Präsentation: IT-Lagebild:
Observability for
Resilience
Sprecher:
Giscard Venn -
Fachvertrieb Big Data & AI
Sebastian Kramp - Team Lead Technical Business Analytics
Nach dem SOC-Aufbau ist vor der Automatisierung (OFD Baden-Württemberg)



Nach dem SOC-Aufbau ist vor der Automatisierung (OFD Baden-Württemberg)Splunk Splunk Public Sector Summit Germany April 2025
Präsentation: Nach dem SOC-Aufbau ist vor der Automatisierung
Sprecher: Sven Beisel, Fachreferent SOC, Oberfinanzdirektion Baden-Württemberg
Monitoring einer Sicheren Inter-Netzwerk Architektur (SINA)



Monitoring einer Sicheren Inter-Netzwerk Architektur (SINA)Splunk Splunk Public Sector Summit Germany April 2025
Präsentation: Monitoring einer
Sicheren Inter-Netzwerk Architektur
(SINA)
Sprecher: Alexander Hauptner -
Senior Technical Consultant, NetDescribe
Praktische Erfahrungen mit dem Attack Analyser (gematik)



Praktische Erfahrungen mit dem Attack Analyser (gematik)Splunk Splunk Public Sector Summit Germany April 2025
Präsentation: Praktische
Erfahrungen mit dem
Attack Analyser
Cisco XDR & Splunk SIEM - stronger together (DATAGROUP Cyber Security)



Cisco XDR & Splunk SIEM - stronger together (DATAGROUP Cyber Security)Splunk Splunk Public Sector Summit Germany April 2025
Präsentation: DATAGROUP Cyber Security
Cisco XDR & Splunk SIEM - stronger together
Sprecher: Uwe Northmann - Advisor bei DATATGROUP Cybersecurity GmbH
Security - Mit Sicherheit zum Erfolg (Telekom)



Security - Mit Sicherheit zum Erfolg (Telekom)Splunk Splunk Public Sector Summit 2025
Präsentation von der Telekom: "Security - Mit Sicherheit zum Erfolg"
Sprecher:
Thomas Beinke - Senior Sales Expert
Lars Fürle - Senior Sales Expert
One Cisco - Splunk Public Sector Summit Germany April 2025



One Cisco - Splunk Public Sector Summit Germany April 2025Splunk Splunk Public Sector Summit Germany April 2025
Präsentation: Cisco & Splunk Stronger Together ...gemeinsam noch stärker
Sprecher: Philipp Behre - Field CTO & Strategic Advisor, Technology & Innovation, Splunk
.conf Go 2023 - Data analysis as a routine



.conf Go 2023 - Data analysis as a routineSplunk .conf Go 2023 presentation: Data analysis as a routine
Speaker: Markus Gustafsson - Senior Development Lead, Posti Group
.conf Go 2023 - How KPN drives Customer Satisfaction on IPTV



.conf Go 2023 - How KPN drives Customer Satisfaction on IPTVSplunk .conf Go 2023 presentation: How KPN drives Customer Satisfaction on IPTV
Speaker: Alain de Lannoy - Senior DevOps Engineer | KPN – iTV
.conf Go 2023 - Navegando la normativa SOX (Telefónica)



.conf Go 2023 - Navegando la normativa SOX (Telefónica)Splunk .conf Go 2023 - Navegando la normativa SOX (Telefónica)
Speakers:
Miguel Castillo - CyberSecurity Engineer - SIEM (Telefónica)
Manuel Iniesta - CyberSecurity Engineer - SIEM (Telefónica)
.conf Go 2023 - Raiffeisen Bank International



.conf Go 2023 - Raiffeisen Bank InternationalSplunk This document discusses standardizing security operations procedures (SOPs) to increase efficiency and automation. It recommends storing SOPs in a code repository for versioning and referencing them in workbooks which are lists of standard tasks to follow for investigations. The goal is to have investigation playbooks in the security orchestration, automation and response (SOAR) tool perform the predefined investigation steps from the workbooks to automate incident response. This helps analysts automate faster without wasting time by having standard, vendor-agnostic procedures.
.conf Go 2023 - På liv og død Om sikkerhetsarbeid i Norsk helsenett 



.conf Go 2023 - På liv og død Om sikkerhetsarbeid i Norsk helsenett Splunk .conf Go 2023 presentation:
"På liv og død
Om sikkerhetsarbeid i Norsk helsenett"
Speaker: Jostein Jensen -Sikkerhetsdirektør
.conf Go 2023 - Many roads lead to Rome - this was our journey (Julius Bär)



.conf Go 2023 - Many roads lead to Rome - this was our journey (Julius Bär)Splunk .conf Go 2023 presentation: "Many roads lead to Rome - this was our journey"
Speakers:
Bruno Domingos (Julius Bär)
Stefan Meier (Julius Bär)
.conf Go 2023 - Das passende Rezept für die digitale (Security) Revolution zu...



.conf Go 2023 - Das passende Rezept für die digitale (Security) Revolution zu...Splunk .conf Go 2023 presentation:
"Das passende Rezept für die digitale (Security) Revolution zur Telematik Infrastruktur 2.0 im Gesundheitswesen?"
Speaker: Stefan Stein -
Teamleiter CERT | gematik GmbH M.Eng. IT-Sicherheit & Forensik,
doctorate student at TH Brandenburg & Universität Dresden
.conf go 2023 - Cyber Resilienz – Herausforderungen und Ansatz für Energiever...



.conf go 2023 - Cyber Resilienz – Herausforderungen und Ansatz für Energiever...Splunk .conf Go 2023 presentation:
"Cyber Resilienz – Herausforderungen und Ansatz für Energieversorger"
Speaker: Dr. Michael Ebner - CISO EnBW
.conf go 2023 - De NOC a CSIRT (Cellnex)



.conf go 2023 - De NOC a CSIRT (Cellnex)Splunk El documento describe la transición de Cellnex de un Centro de Operaciones de Seguridad (SOC) a un Equipo de Respuesta a Incidentes de Seguridad (CSIRT). La transición se debió al crecimiento de Cellnex y la necesidad de automatizar procesos y tareas para mejorar la eficiencia. Cellnex implementó Splunk SIEM y SOAR para automatizar la creación, remediación y cierre de incidentes. Esto permitió al personal concentrarse en tareas estratégicas y mejorar KPIs como tiempos de resolución y correos electrónicos anal
conf go 2023 - El camino hacia la ciberseguridad (ABANCA)



conf go 2023 - El camino hacia la ciberseguridad (ABANCA)Splunk Este documento resume el recorrido de ABANCA en su camino hacia la ciberseguridad con Splunk, desde la incorporación de perfiles dedicados en 2016 hasta convertirse en un centro de monitorización y respuesta con más de 1TB de ingesta diaria y 350 casos de uso alineados con MITRE ATT&CK. También describe errores cometidos y soluciones implementadas, como la normalización de fuentes y formación de operadores, y los pilares actuales como la automatización, visibilidad y alineación con MITRE ATT&CK. Por último, señala retos
Splunk - BMW connects business and IT with data driven operations SRE and O11y



Splunk - BMW connects business and IT with data driven operations SRE and O11ySplunk BMW is defining the next level of mobility - digital interactions and technology are the backbone to continued success with its customers. Discover how an IT team is tackling the journey of business transformation at scale whilst maintaining (and showing the importance of) business and IT service availability. Learn how BMW introduced frameworks to connect business and IT, using real-time data to mitigate customer impact, as Michael and Mark share their experience in building operations for a resilient future.
Ad
Recently uploaded (20)
Dev Dives: Automate and orchestrate your processes with UiPath Maestro



Dev Dives: Automate and orchestrate your processes with UiPath MaestroUiPathCommunity This session is designed to equip developers with the skills needed to build mission-critical, end-to-end processes that seamlessly orchestrate agents, people, and robots.
📕 Here's what you can expect:
- Modeling: Build end-to-end processes using BPMN.
- Implementing: Integrate agentic tasks, RPA, APIs, and advanced decisioning into processes.
- Operating: Control process instances with rewind, replay, pause, and stop functions.
- Monitoring: Use dashboards and embedded analytics for real-time insights into process instances.
This webinar is a must-attend for developers looking to enhance their agentic automation skills and orchestrate robust, mission-critical processes.
👨🏫 Speaker:
Andrei Vintila, Principal Product Manager @UiPath
This session streamed live on April 29, 2025, 16:00 CET.
Check out all our upcoming Dev Dives sessions at https://community.uipath.com/dev-dives-automation-developer-2025/.
Transcript: #StandardsGoals for 2025: Standards & certification roundup - Tec...



Transcript: #StandardsGoals for 2025: Standards & certification roundup - Tec...BookNet Canada Book industry standards are evolving rapidly. In the first part of this session, we’ll share an overview of key developments from 2024 and the early months of 2025. Then, BookNet’s resident standards expert, Tom Richardson, and CEO, Lauren Stewart, have a forward-looking conversation about what’s next.
Link to recording, presentation slides, and accompanying resource: https://bnctechforum.ca/sessions/standardsgoals-for-2025-standards-certification-roundup/
Presented by BookNet Canada on May 6, 2025 with support from the Department of Canadian Heritage.
Complete Guide to Advanced Logistics Management Software in Riyadh.pdf



Complete Guide to Advanced Logistics Management Software in Riyadh.pdfSoftware Company Explore the benefits and features of advanced logistics management software for businesses in Riyadh. This guide delves into the latest technologies, from real-time tracking and route optimization to warehouse management and inventory control, helping businesses streamline their logistics operations and reduce costs. Learn how implementing the right software solution can enhance efficiency, improve customer satisfaction, and provide a competitive edge in the growing logistics sector of Riyadh.
Technology Trends in 2025: AI and Big Data Analytics



Technology Trends in 2025: AI and Big Data AnalyticsInData Labs At InData Labs, we have been keeping an ear to the ground, looking out for AI-enabled digital transformation trends coming our way in 2025. Our report will provide a look into the technology landscape of the future, including:
-Artificial Intelligence Market Overview
-Strategies for AI Adoption in 2025
-Anticipated drivers of AI adoption and transformative technologies
-Benefits of AI and Big data for your business
-Tips on how to prepare your business for innovation
-AI and data privacy: Strategies for securing data privacy in AI models, etc.
Download your free copy nowand implement the key findings to improve your business.
Procurement Insights Cost To Value Guide.pptx



Procurement Insights Cost To Value Guide.pptxJon Hansen Procurement Insights integrated Historic Procurement Industry Archives, serves as a powerful complement — not a competitor — to other procurement industry firms. It fills critical gaps in depth, agility, and contextual insight that most traditional analyst and association models overlook.
Learn more about this value- driven proprietary service offering here.
Heap, Types of Heap, Insertion and Deletion



Heap, Types of Heap, Insertion and DeletionJaydeep Kale This pdf will explain what is heap, its type, insertion and deletion in heap and Heap sort
How Can I use the AI Hype in my Business Context?



How Can I use the AI Hype in my Business Context?Daniel Lehner 𝙄𝙨 𝘼𝙄 𝙟𝙪𝙨𝙩 𝙝𝙮𝙥𝙚? 𝙊𝙧 𝙞𝙨 𝙞𝙩 𝙩𝙝𝙚 𝙜𝙖𝙢𝙚 𝙘𝙝𝙖𝙣𝙜𝙚𝙧 𝙮𝙤𝙪𝙧 𝙗𝙪𝙨𝙞𝙣𝙚𝙨𝙨 𝙣𝙚𝙚𝙙𝙨?
Everyone’s talking about AI but is anyone really using it to create real value?
Most companies want to leverage AI. Few know 𝗵𝗼𝘄.
✅ What exactly should you ask to find real AI opportunities?
✅ Which AI techniques actually fit your business?
✅ Is your data even ready for AI?
If you’re not sure, you’re not alone. This is a condensed version of the slides I presented at a Linkedin webinar for Tecnovy on 28.04.2025.
tecnologias de las primeras civilizaciones.pdf



tecnologias de las primeras civilizaciones.pdffjgm517 descaripcion detallada del avance de las tecnologias en mesopotamia, egipto, roma y grecia.
Cybersecurity Identity and Access Solutions using Azure AD



Cybersecurity Identity and Access Solutions using Azure ADVICTOR MAESTRE RAMIREZ Cybersecurity Identity and Access Solutions using Azure AD
Increasing Retail Store Efficiency How can Planograms Save Time and Money.pptx



Increasing Retail Store Efficiency How can Planograms Save Time and Money.pptxAnoop Ashok In today's fast-paced retail environment, efficiency is key. Every minute counts, and every penny matters. One tool that can significantly boost your store's efficiency is a well-executed planogram. These visual merchandising blueprints not only enhance store layouts but also save time and money in the process.
AI EngineHost Review: Revolutionary USA Datacenter-Based Hosting with NVIDIA ...



AI EngineHost Review: Revolutionary USA Datacenter-Based Hosting with NVIDIA ...SOFTTECHHUB I started my online journey with several hosting services before stumbling upon Ai EngineHost. At first, the idea of paying one fee and getting lifetime access seemed too good to pass up. The platform is built on reliable US-based servers, ensuring your projects run at high speeds and remain safe. Let me take you step by step through its benefits and features as I explain why this hosting solution is a perfect fit for digital entrepreneurs.
AI Changes Everything – Talk at Cardiff Metropolitan University, 29th April 2...



AI Changes Everything – Talk at Cardiff Metropolitan University, 29th April 2...Alan Dix Talk at the final event of Data Fusion Dynamics: A Collaborative UK-Saudi Initiative in Cybersecurity and Artificial Intelligence funded by the British Council UK-Saudi Challenge Fund 2024, Cardiff Metropolitan University, 29th April 2025
https://alandix.com/academic/talks/CMet2025-AI-Changes-Everything/
Is AI just another technology, or does it fundamentally change the way we live and think?
Every technology has a direct impact with micro-ethical consequences, some good, some bad. However more profound are the ways in which some technologies reshape the very fabric of society with macro-ethical impacts. The invention of the stirrup revolutionised mounted combat, but as a side effect gave rise to the feudal system, which still shapes politics today. The internal combustion engine offers personal freedom and creates pollution, but has also transformed the nature of urban planning and international trade. When we look at AI the micro-ethical issues, such as bias, are most obvious, but the macro-ethical challenges may be greater.
At a micro-ethical level AI has the potential to deepen social, ethnic and gender bias, issues I have warned about since the early 1990s! It is also being used increasingly on the battlefield. However, it also offers amazing opportunities in health and educations, as the recent Nobel prizes for the developers of AlphaFold illustrate. More radically, the need to encode ethics acts as a mirror to surface essential ethical problems and conflicts.
At the macro-ethical level, by the early 2000s digital technology had already begun to undermine sovereignty (e.g. gambling), market economics (through network effects and emergent monopolies), and the very meaning of money. Modern AI is the child of big data, big computation and ultimately big business, intensifying the inherent tendency of digital technology to concentrate power. AI is already unravelling the fundamentals of the social, political and economic world around us, but this is a world that needs radical reimagining to overcome the global environmental and human challenges that confront us. Our challenge is whether to let the threads fall as they may, or to use them to weave a better future.
IEDM 2024 Tutorial2_Advances in CMOS Technologies and Future Directions for C...



IEDM 2024 Tutorial2_Advances in CMOS Technologies and Future Directions for C...organizerofv IEDM 2024 Tutorial2
Massive Power Outage Hits Spain, Portugal, and France: Causes, Impact, and On...



Massive Power Outage Hits Spain, Portugal, and France: Causes, Impact, and On...Aqusag Technologies In late April 2025, a significant portion of Europe, particularly Spain, Portugal, and parts of southern France, experienced widespread, rolling power outages that continue to affect millions of residents, businesses, and infrastructure systems.
HCL Nomad Web – Best Practices and Managing Multiuser Environments



HCL Nomad Web – Best Practices and Managing Multiuser Environmentspanagenda Webinar Recording: https://www.panagenda.com/webinars/hcl-nomad-web-best-practices-and-managing-multiuser-environments/
HCL Nomad Web is heralded as the next generation of the HCL Notes client, offering numerous advantages such as eliminating the need for packaging, distribution, and installation. Nomad Web client upgrades will be installed “automatically” in the background. This significantly reduces the administrative footprint compared to traditional HCL Notes clients. However, troubleshooting issues in Nomad Web present unique challenges compared to the Notes client.
Join Christoph and Marc as they demonstrate how to simplify the troubleshooting process in HCL Nomad Web, ensuring a smoother and more efficient user experience.
In this webinar, we will explore effective strategies for diagnosing and resolving common problems in HCL Nomad Web, including
- Accessing the console
- Locating and interpreting log files
- Accessing the data folder within the browser’s cache (using OPFS)
- Understand the difference between single- and multi-user scenarios
- Utilizing Client Clocking
Manifest Pre-Seed Update | A Humanoid OEM Deeptech In France



Manifest Pre-Seed Update | A Humanoid OEM Deeptech In Francechb3 The latest updates on Manifest's pre-seed stage progress.
UiPath Community Berlin: Orchestrator API, Swagger, and Test Manager API



UiPath Community Berlin: Orchestrator API, Swagger, and Test Manager APIUiPathCommunity Join this UiPath Community Berlin meetup to explore the Orchestrator API, Swagger interface, and the Test Manager API. Learn how to leverage these tools to streamline automation, enhance testing, and integrate more efficiently with UiPath. Perfect for developers, testers, and automation enthusiasts!
📕 Agenda
Welcome & Introductions
Orchestrator API Overview
Exploring the Swagger Interface
Test Manager API Highlights
Streamlining Automation & Testing with APIs (Demo)
Q&A and Open Discussion
Perfect for developers, testers, and automation enthusiasts!
👉 Join our UiPath Community Berlin chapter: https://community.uipath.com/berlin/
This session streamed live on April 29, 2025, 18:00 CET.
Check out all our upcoming UiPath Community sessions at https://community.uipath.com/events/.
DevOpsDays Atlanta 2025 - Building 10x Development Organizations.pptx



DevOpsDays Atlanta 2025 - Building 10x Development Organizations.pptxJustin Reock Building 10x Organizations with Modern Productivity Metrics
10x developers may be a myth, but 10x organizations are very real, as proven by the influential study performed in the 1980s, ‘The Coding War Games.’
Right now, here in early 2025, we seem to be experiencing YAPP (Yet Another Productivity Philosophy), and that philosophy is converging on developer experience. It seems that with every new method we invent for the delivery of products, whether physical or virtual, we reinvent productivity philosophies to go alongside them.
But which of these approaches actually work? DORA? SPACE? DevEx? What should we invest in and create urgency behind today, so that we don’t find ourselves having the same discussion again in a decade?
SplunkLive! Frankfurt 2018 - Use Splunk for Incident Response, Orchestration and Automation
- 1. Use Splunk for Incident Response, Orchestration and Automation Kai Seidenschnur | Staff Security Engineer
- 2. During the course of this presentation, we may make forward-looking statements regarding future events or the expected performance of the company. We caution you that such statements reflect our current expectations and estimates based on factors currently known to us and that actual events or results could differ materially. For important factors that may cause actual results to differ from those contained in our forward-looking statements, please review our filings with the SEC. The forward-looking statements made in this presentation are being made as of the time and date of its live presentation. If reviewed after its live presentation, this presentation may not contain current or accurate information. We do not assume any obligation to update any forward looking statements we may make. In addition, any information about our roadmap outlines our general product direction and is subject to change at any time without notice. It is for informational purposes only and shall not be incorporated into any contract or other commitment. Splunk undertakes no obligation either to develop the features or functionality described or to include any such feature or functionality in a future release. Splunk, Splunk>, Listen to Your Data, The Engine for Machine Data, Splunk Cloud, Splunk Light and SPL are trademarks and registered trademarks of Splunk Inc. in the United States and other countries. All other brand names, product names, or trademarks belong to their respective owners. ©2018 Splunk Inc. All rights reserved. Forward-Looking Statements
- 3. Incident Response Slow Alert Noise Tools Problem Many tools Disparate tools Skills Lack of skills Retention Training Scale Horizontal and Vertical Orchestration Automation Security Operations Need to Change
- 5. Incident Response Takes Significant Time 5 Source: SANS 2017 Incident Response Survey
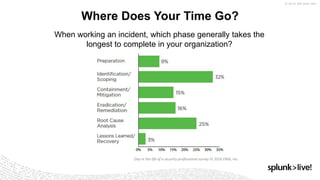
- 6. Where Does Your Time Go? When working an incident, which phase generally takes the longest to complete in your organization? Day in the life of a security professional survey © 2016 EMA, Inc.
- 7. Time-to-Contain + Time-to-Respond = 72% When working an incident, which phase generally takes the longest to complete in your organization? Day in the life of a security professional survey © 2016 EMA, Inc.
- 8. Time = Risk => The Need for Speed!
- 9. Tools
- 10. Tools and Technologies Galore Source: CyberSecurity Analytics and Analytics in Transition, ESG, 2017
- 12. Let us define these terms first.
- 13. Orchestration ▶ Brings together or integrates different technologies and tools ▶ Security-specific or non-security-specific ▶ Provides the ability to coordinate informed decision-making, formalize and automate responsive actions Orchestration vs. Automation
- 14. Automation & Orchestration Adoption Growing Source: CyberSecurity Analytics and Analytics in Transition, ESG, 2017
- 16. Adaptive Response Identity and Access Internal Network Security Endpoints OrchestrationWAF & App Security Threat Intelligence Network Web Proxy FirewallMission Deeper integrations across the best security technologies to help combat advanced attacks together. Approach Gather/analyze, share, take action based on end-to-end context, across security domains.
- 17. Cloud Security Endpoints Orchestration WAF & App Security Threat Intelligence Network Web Proxy Firewall Identity and Access
- 19. ▶ Leverages Existing Splunk Common Action Model • A CIM for alert actions • Not a data model ▶ Existing Actions • Information: Give/Get (i.e., additional context) • Permission: Grant/Revoke (e.g., user, host, etc.) • Control: Change (e.g., firewall rules) ▶ Metadata • Category – Information gathering, Information conveyance, Permissions control • Task – Create, Update, Delete, Allow, Block • Subject – What will be acted upon (network, endpoint, etc.) • Vendor – Providing the action Adaptive Response Framework (Within ES)
- 20. How To Interact With AR Suggest Next StepsAutomatically With Notables Run Ad-Hoc
- 21. Adaptive Response Actions (Examples) AUTOMATIO N Automatically With Notables
- 22. Adaptive Response Actions (Examples) AUTOMATIO NCategory – Information gathering, Information conveyance, Permissions control Task – Create, Update, Delete, Allow, Block Subject – What will be acted upon (network, endpoint, etc.) Vendor – Providing the action. Ex.: Splunk, Ziften, Palo Alto Networks, etc.
- 23. Adaptive Response Actions (Examples) AUTOMATIO N Run Ad-Hoc
- 24. ▶ Catalog of latest AR Actions ▶ Categorized by Use Case and Security Domain ▶ Auto-update from Splunkbase.com ▶ Showcase of key AR actions (AWS, PAN, etc.) Adaptive Response Actions Showcase App
- 26. ▶ Centrally automate retrieval, sharing and response action, resulting in improved detection, investigation and remediation times ▶ Improve operational efficiency using workflow-based context with automated and human-assisted decisions; Measure efficacy ▶ Extract new insight by leveraging context, sharing data and taking actions between Enterprise Security and Adaptive Response partners Adaptive Response Benefits
- 27. Accelerate Detection, Investigation & Response ▶ Use the correlation search builder to configure, automate and attach the results to notable events ▶ In incident review, configure and execute ad-hoc responses and queries across the security ecosystem ▶ Use the actions dashboard to search and review responses taken and their results
- 28. Cloud Security Endpoints Orchestration WAF & App Security Threat Intelligence Network Web Proxy Firewall Identity and Access
- 30. © 2018 SPLUNK INC. ▶ Blocked over two million security threats ▶ Orchestrated threat intelligence across 20 security technologies sitting within its internal Threat Intelligence System ▶ Automated threat detection, response and 90% of its security metrics process in just two months Automating Threat Detection With Splunk Adaptive Response “Since implementing Splunk ES as the brain in our security nerve center have found Splunk to be the right solution to quickly and effectively , we create and implement security analytics across a wide array of data sources and security use cases.” – Senior Vice President, Chief Global Security Officer, Aflac
- 31. Sample of Symantec AR Actions*: • Isolate Endpoint • Rejoin Endpoint • Query File for Disposition Case Study: Symantec Symantec ATP helps detect and remediate complex attacks across endpoint, email, network, and web from a single console “Splunk Adaptive Response has the power to help reduce workload on customer SOC teams by speeding up decision-making and associated actions through automation.” - Peter Doggart, Vice President of Business Development, Symantec
- 32. Sample of ForeScout AR Actions*: • Redirect endpoint to specific web browser • Send email messages to users • Kill peer-to-peer application Case Study: Brown-Forman “Leveraging the ForeScout Extended Module for Splunk via Adaptive Response will enable us to minimize the time and resources needed to respond to emerging threats.” - Clayton Colwell, Associate Security Engineer, Brown-Forman Corporation ForeScout CounterACT enables its customers to monitor real-time NAC events and respond to security threats at endpoints
- 33. © 2018 SPLUNK INC. 1. Adaptive Response helps accelerate Incident Detection, Investigation and Response 2. Use Adaptive Response framework for multi-vendor security workflow orchestration and automation 3. Use with IT and Security domains to solve a range of security use cases Mitigate Incident Response Challenges With Orchestration and Automation Key Takeaways
- 34. Search and Investigate Analytics-Driven Security Index Untapped Data: Any Source, Type, Volume On- Premises Private Cloud Public Cloud Storage Online Shopping Cart Telecoms Desktops Security Web Services Networks Containers Web Clickstreams RFID Smartphones and Devices Servers Messaging GPS Location Packaged Applications Custom Applications Online Services DatabasesCall Detail Records Energy Meters Firewall Intrusion Prevention Splunk Enterprise Security 600+ Security Apps Splunk User Behavior Analytics Monitoring, Correlations, Alerts Dashboards and Reports Analytics and Virtualization Adaptive Response Employee Info Asset and CMDB Threat Intelligence Applications Data Stores External Lookups Platform for Operational Intelligence
- 35. Q&A Thank you Join: Our Community, with Apps, ask questions or join a SplunkLive! event https://www.splunk.com/en_us/community.html Try: Splunk Security Online Experience (No download) https://www.splunk.com/en_us/solutions/solution- areas/security-and-fraud/security- investigation/getting-started.html Explore: Download the CIS Critical Security Controls App https://splunkbase.splunk.com/app/3064/
- 36. ORLANDO FLORIDA Walt Disney World Swan and Dolphin Hotels .conf18: Monday, October 1 – Thursday, October 4 Splunk University: Saturday, September 29 – Monday, October 1 Save the Date 2018
- 37. © 2018 SPLUNK INC. Don't forget to rate this session in the SplunkLive! mobile app THANK YOU https://ponypoll.com/frankfurt


