sqlmap internals
2 likes3,197 views
These are the slides from a talk "sqlmap internals" held at Sec/Admin Resilience 2017 (Sevilla / Spain)
1 of 36
Downloaded 67 times








![SecAdmin, Sevilla (Spain) November 24th, 2017 9
HashDB (1)HashDB (1)
Storage of resumable session data at
centralized place (local SQLite3 database)
Non-ASCII values are being automatically
serialized/deserialized (pickle)
INSERT INTO storage VALUES
(INT(MD5(target_url, uid, MILESTONE_SALT)
[:8]), stored_value)
uid uniquely describes stored_value for a
given target_url (e.g.: KB_INJECTIONS, SELECT
VERSION(), etc.)
MILESTONE_SALT changed whenever there is an
incompatible update of HashDB mechanism](https://image.slidesharecdn.com/secadmin-2017-miroslavstampar-sqlmapinternals-171219013111/85/sqlmap-internals-9-320.jpg)





![SecAdmin, Sevilla (Spain) November 24th, 2017 15
Boolean inference (1)Boolean inference (1)
Binary search using greater-than operator
O(Log2n) complexity compared to sequential
search with O(n)
Faster than bit-by-bit extraction (on average 6
requests compared to 8 requests)
For example:
Sample initial table ['A','B',...'Z']
AND (...) > 'M' → TRUE → ['N',...'Z']
AND (...) > 'S' → FALSE → ['N',...'S']
AND (...) > 'O' → TRUE → ['P', 'R', 'S']
AND (...) > 'R' → FALSE → ['P', 'R']
AND (...) > 'P' → FALSE → 'P' (result)](https://image.slidesharecdn.com/secadmin-2017-miroslavstampar-sqlmapinternals-171219013111/85/sqlmap-internals-15-320.jpg)


















Ad
Recommended
ISO 27005:2022 Overview 221028.pdf



ISO 27005:2022 Overview 221028.pdfAndrey Prozorov, CISM, CIPP/E, CDPSE. LA 27001 This document provides an overview of changes between the 2018 and 2022 versions of ISO 27005, which provides guidance on managing information security risks. Some key changes include aligning terminology with ISO 31000:2018, adjusting the structure to match ISO 27001:2022, introducing risk scenario concepts, revising and restructuring annexes, and providing additional examples and models. The 2022 version contains 62 pages compared to 56 pages previously and has undergone terminology, process, and content updates to align with updated ISO standards and better support organizations in performing information security risk management.
Security Awareness Training



Security Awareness TrainingWilliam Mann This document provides training on cybersecurity best practices for Borough of West Chester personnel. It defines cybersecurity as protecting information and systems from unauthorized access, use, disclosure, disruption or destruction. It outlines common cyber threats like viruses, worms, ransomware, and social engineering. It emphasizes using strong passwords, antivirus software, firewalls, and regular software updates. It also recommends avoiding malicious emails and websites, and backing up important data.
Intro to software development



Intro to software developmentHawkman Academy This document provides an introduction to software development, including:
- An overview of the software development life cycle, from requirements discovery through testing.
- Descriptions of different programming languages from low-level machine languages to high-level languages.
- Factors to consider when choosing a programming language such as the problem domain and available communities.
- The importance of software testing throughout the development process.
- Recommendations for learning software development through practicing with real problems and using online courses and tutorials.
CISA Training - Chapter 2 - 2016



CISA Training - Chapter 2 - 2016Hafiz Sheikh Adnan Ahmed This document provides an overview of topics covered in a CISA review course, including IT governance, corporate governance, governance of enterprise IT, risk management, information security management practices, auditing IT governance structure and implementation, and business continuity planning. The document defines key concepts, best practices, standards, and approaches for each topic. It also outlines the roles and responsibilities of various committees, policies, procedures, and other elements involved in effectively governing enterprise IT.
DEVSECOPS.pptx



DEVSECOPS.pptxMohammadSaif904342
DevSecOps (short for development, security, and operations) is a development practice that integrates security initiatives at every stage of the software development lifecycle to deliver robust and secure applications.
OWASP Top 10 2021 Presentation (Jul 2022)



OWASP Top 10 2021 Presentation (Jul 2022)TzahiArabov The document provides information about the OWASP Top 10 2021 list of web application security risks. It describes the top risk, A01: Broken Access Control, giving its definition, examples of vulnerabilities it can enable, prevention methods, and examples. It also summarizes the second and third top risks, A02: Cryptographic Failures and A03: Injection, in a similar manner.
Python programming



Python programmingAshwin Kumar Ramasamy The document provides an introduction to Python programming. It discusses key concepts like variables, data types, operators, and sequential data types. Python is presented as an interpreted programming language that uses indentation to indicate blocks of code. Comments and documentation are included to explain the code. Various data types are covered, including numbers, strings, booleans, and lists. Operators for arithmetic, comparison, assignment and more are also summarized.
Sqlmap



Sqlmapshamshad9 sqlmap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers. It comes with a powerful detection engine, many niche features for the ultimate penetration tester and a broad range of switches lasting from
database fingerprinting, over data fetching from the database, to accessing the underlying file system and executing commands on the operating system via out-of-band connections.
Heuristic methods used in sqlmap



Heuristic methods used in sqlmapMiroslav Stampar These are the slides from a talk "Heuristic methods
used in sqlmap" held at FSec 2013 conference (Croatia / Varazdin 19th September 2013) by Miroslav Stampar
sqlmap - why (not how) it works?



sqlmap - why (not how) it works?Miroslav Stampar These are the slides from a talk "sqlmap - why (not how) it works?" held at Navaja Negra & ConectaCon 2015 (Albacete / Spain)
sqlmap - Under the Hood



sqlmap - Under the HoodMiroslav Stampar This document summarizes sqlmap, an open source penetration testing tool used for detecting and exploiting SQL injection flaws. It discusses sqlmap's features such as supporting large data dumps, storing session data, XML payload and query formats, multithreading, direct database connections, loading requests from files, form and site crawling, authentication, detection of reflection and dynamic content, and fingerprinting of databases and web servers.
It all starts with the ' (SQL injection from attacker's point of view)



It all starts with the ' (SQL injection from attacker's point of view)Miroslav Stampar These are the slides from a talk "It all starts with the ' (SQL injection from attacker's point of view)" held at FSec 2011 conference (Croatia / Varazdin 22nd September 2011) by Miroslav Stampar
Advanced SQL injection to operating system full control (whitepaper)



Advanced SQL injection to operating system full control (whitepaper)Bernardo Damele A. G. Over ten years have passed since a famous hacker coined the term "SQL injection" and it is still considered one of the major web application threats, affecting over 70% of web application on the Net. A lot has been said on this specific vulnerability, but not all of the aspects and implications have been uncovered, yet.
It's time to explore new ways to get complete control over the database management system's underlying operating system through a SQL injection vulnerability in those over-looked and theoretically not exploitable scenarios: From the command execution on MySQL and PostgreSQL to a stored procedure's buffer overflow exploitation on Microsoft SQL Server. These and much more will be unveiled and demonstrated with my own tool's new version that I will release at the Conference (http://www.blackhat.com/html/bh-europe-09/bh-eu-09-speakers.html#Damele).
SQL injection: Not Only AND 1=1 (updated)



SQL injection: Not Only AND 1=1 (updated)Bernardo Damele A. G. The presentation has a quick preamble on SQL injection definition, sqlmap and its key features.
I will then illustrate into details common and uncommon problems and respective solutions with examples that a penetration tester faces when he wants to take advantage of any kind of web application SQL injection flaw on real world web applications, for instance SQL injection in ORDER BY and LIMIT clauses, single entry UNION query SQL injection, specific web application technologies IDS bypasses and more.
These slides have been presented at the 2nd Digital Security Forum in Lisbon on June 27, 2009.
Updated version of http://www.slideshare.net/inquis/sql-injection-not-only-and-11.
Advanced SQL injection to operating system full control (slides)



Advanced SQL injection to operating system full control (slides)Bernardo Damele A. G. Over ten years have passed since a famous hacker coined the term "SQL injection" and it is still considered one of the major web application threats, affecting over 70% of web application on the Net. A lot has been said on this specific vulnerability, but not all of the aspects and implications have been uncovered, yet.
It's time to explore new ways to get complete control over the database management system's underlying operating system through a SQL injection vulnerability in those over-looked and theoretically not exploitable scenarios: From the command execution on MySQL and PostgreSQL to a stored procedure's buffer overflow exploitation on Microsoft SQL Server. These and much more will be unveiled and demonstrated with my own tool's new version that I will release at the Conference (http://www.blackhat.com/html/bh-europe-09/bh-eu-09-speakers.html#Damele).
These slides have been presented at Black Hat Euroe conference in Amsterdam on April 16, 2009.
sqlmap - security development in Python



sqlmap - security development in PythonMiroslav Stampar This document provides an overview of sqlmap, an open source penetration testing tool that automates the detection and exploitation of SQL injection vulnerabilities. It discusses the creators and history of the tool, its main features like database enumeration and takeover functionalities, and techniques for detecting different types of SQL injections like blind, error-based, union queries, and time delays. Examples of how each technique works are also provided.
Sql injection with sqlmap



Sql injection with sqlmapHerman Duarte This document discusses SQL injection and the sqlmap tool. It provides an overview of SQL injection, describes how sqlmap can be used to find and exploit SQL injection vulnerabilities, and demonstrates how it can be used to enumerate databases and files systems, and in some cases obtain remote access. It also discusses mitigation techniques like input sanitization and using prepared statements.
Sql Injection - Vulnerability and Security



Sql Injection - Vulnerability and SecuritySandip Chaudhari What is SQL Injection? Why does this problem exist? How it can be exploited? How to secure your app against this vulnerability?
Sql injection



Sql injectionNitish Kumar This document discusses SQL injection attacks and how to mitigate them. It begins by explaining how injection attacks work by tricking applications into executing unintended commands. It then provides examples of how SQL injection can be used to conduct unauthorized access and data modification attacks. The document discusses techniques for finding and exploiting SQL injection vulnerabilities, including through the SELECT, INSERT, UPDATE and UNION commands. It also covers ways to mitigate injection attacks, such as using prepared statements with bound parameters instead of concatenating strings.
SQL INJECTION



SQL INJECTIONMentorcs This document discusses SQL injection (SQLI), which is a code injection technique used to attack data-driven applications. SQLI works by inserting malicious SQL statements into entry fields for execution on the backend database. This allows attackers to read sensitive data, modify database contents, and perform administration tasks. The document outlines common SQLI attack methods like error-based and union-based techniques. It also categorizes SQLI attacks as in-band, inferential/blind, or out-of-band based on how results are returned. Examples are provided to illustrate how SQLI exploits vulnerabilities in dynamic SQL queries.
SQL Injection



SQL InjectionAsish Kumar Rath SQL injection is a code injection technique, used to attack data-driven applications, in which malicious SQL statements are inserted into an entry field for execution (e.g. to dump the database contents to the attacker).
Data Retrieval over DNS in SQL Injection Attacks



Data Retrieval over DNS in SQL Injection AttacksMiroslav Stampar This paper has been made for and it's results were presented at PHDays 2012 conference (Russia / Moscow 30th–31st May 2012) by Miroslav Stampar.
Types of sql injection attacks



Types of sql injection attacksRespa Peter The document discusses different types of SQL injection attacks, including tautologies, illegal/logically incorrect queries, union queries, piggybacked queries, and stored procedures. Tautologies aim to bypass authentication by making conditional statements always true. Illegal queries gather database information by causing syntax or type errors. Union queries extract data by combining results from multiple tables. Piggybacked queries maliciously execute additional queries by abusing query delimiters. Stored procedures can be used to escalate privileges or execute remote commands if vulnerabilities exist. Examples are provided for each type of attack along with potential solutions.
Ppt on sql injection



Ppt on sql injectionashish20012 This document discusses SQL injection, which is a security vulnerability that allows attackers to interfere with how a database operates. SQL injection occurs when user input is not sanitized and is used directly in SQL queries, allowing attackers to alter the structure and meaning of queries. The document provides an example of how an attacker could log in without a password by adding SQL code to the username field. It also lists some common SQL injection techniques like using comments, concatenation, and wildcards. Finally, it points to additional online resources for learning more about SQL injection and database security.
Expanding the control over the operating system from the database



Expanding the control over the operating system from the databaseBernardo Damele A. G. Using a database, either via a SQL injection or via direct connection, as a stepping stone to control the underlying operating system can be achieved.
There is much to say on operating system control by owning a database server: Windows registry access, anti-forensics technique to establish an out-of-band stealth connection, buffer overflow exploitation with memory protections bypass and custom user-defined function injection.
These slides have been presented at SOURCE Conference in Barcelona on September 21, 2009.
Sql injection



Sql injectionZidh The document discusses SQL injection, including its types, methodology, attack queries, and prevention. SQL injection is a code injection technique where a hacker manipulates SQL commands to access a database and sensitive information. It can result in identity spoofing, modifying data, gaining administrative privileges, denial of service attacks, and more. The document outlines the steps of a SQL injection attack and types of queries used. Prevention methods include minimizing privileges, coding standards, and firewalls.
Sqlmap



SqlmapInstitute of Information Security (IIS) sqlmap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers.
seminar report on Sql injection



seminar report on Sql injectionJawhar Ali This document discusses SQL injection, including what it is, how it works, and its impacts. It defines SQL injection as a dangerous web attack that leverages vulnerabilities in web applications to bypass authentication and modify or delete database data. The summary explains that SQL injection works by manipulating SQL queries passed to a backend database, such as by appending additional SQL statements or modifying the structure of the original query. Some impacts of successful SQL injection attacks mentioned are leakage of sensitive information, reputation decline, data loss, and denial of service. Tools for finding SQL injection vulnerabilities like sqlmap and uniscan are also briefly described.
sqlmap internals



sqlmap internalsMiroslav Stampar These are the slides from a talk "sqlmap internals" held at ISACA Croatian Chapter meeting on 09th of April 2018 (Zagreb / Croatia)
Datastax day 2016 : Cassandra data modeling basics



Datastax day 2016 : Cassandra data modeling basicsDuyhai Doan This document discusses data modeling with Apache Cassandra. It covers:
1. The objectives of data modeling like reducing query latency and avoiding disasters
2. Choosing the right partition key which is the main entry point for queries and helps distribute data
3. Using clustering columns to simulate one-to-many relationships and enable sorting and range queries
4. Other critical details like avoiding huge partitions, sub-partitioning techniques, and how deletes create tombstones
Ad
More Related Content
What's hot (20)
Heuristic methods used in sqlmap



Heuristic methods used in sqlmapMiroslav Stampar These are the slides from a talk "Heuristic methods
used in sqlmap" held at FSec 2013 conference (Croatia / Varazdin 19th September 2013) by Miroslav Stampar
sqlmap - why (not how) it works?



sqlmap - why (not how) it works?Miroslav Stampar These are the slides from a talk "sqlmap - why (not how) it works?" held at Navaja Negra & ConectaCon 2015 (Albacete / Spain)
sqlmap - Under the Hood



sqlmap - Under the HoodMiroslav Stampar This document summarizes sqlmap, an open source penetration testing tool used for detecting and exploiting SQL injection flaws. It discusses sqlmap's features such as supporting large data dumps, storing session data, XML payload and query formats, multithreading, direct database connections, loading requests from files, form and site crawling, authentication, detection of reflection and dynamic content, and fingerprinting of databases and web servers.
It all starts with the ' (SQL injection from attacker's point of view)



It all starts with the ' (SQL injection from attacker's point of view)Miroslav Stampar These are the slides from a talk "It all starts with the ' (SQL injection from attacker's point of view)" held at FSec 2011 conference (Croatia / Varazdin 22nd September 2011) by Miroslav Stampar
Advanced SQL injection to operating system full control (whitepaper)



Advanced SQL injection to operating system full control (whitepaper)Bernardo Damele A. G. Over ten years have passed since a famous hacker coined the term "SQL injection" and it is still considered one of the major web application threats, affecting over 70% of web application on the Net. A lot has been said on this specific vulnerability, but not all of the aspects and implications have been uncovered, yet.
It's time to explore new ways to get complete control over the database management system's underlying operating system through a SQL injection vulnerability in those over-looked and theoretically not exploitable scenarios: From the command execution on MySQL and PostgreSQL to a stored procedure's buffer overflow exploitation on Microsoft SQL Server. These and much more will be unveiled and demonstrated with my own tool's new version that I will release at the Conference (http://www.blackhat.com/html/bh-europe-09/bh-eu-09-speakers.html#Damele).
SQL injection: Not Only AND 1=1 (updated)



SQL injection: Not Only AND 1=1 (updated)Bernardo Damele A. G. The presentation has a quick preamble on SQL injection definition, sqlmap and its key features.
I will then illustrate into details common and uncommon problems and respective solutions with examples that a penetration tester faces when he wants to take advantage of any kind of web application SQL injection flaw on real world web applications, for instance SQL injection in ORDER BY and LIMIT clauses, single entry UNION query SQL injection, specific web application technologies IDS bypasses and more.
These slides have been presented at the 2nd Digital Security Forum in Lisbon on June 27, 2009.
Updated version of http://www.slideshare.net/inquis/sql-injection-not-only-and-11.
Advanced SQL injection to operating system full control (slides)



Advanced SQL injection to operating system full control (slides)Bernardo Damele A. G. Over ten years have passed since a famous hacker coined the term "SQL injection" and it is still considered one of the major web application threats, affecting over 70% of web application on the Net. A lot has been said on this specific vulnerability, but not all of the aspects and implications have been uncovered, yet.
It's time to explore new ways to get complete control over the database management system's underlying operating system through a SQL injection vulnerability in those over-looked and theoretically not exploitable scenarios: From the command execution on MySQL and PostgreSQL to a stored procedure's buffer overflow exploitation on Microsoft SQL Server. These and much more will be unveiled and demonstrated with my own tool's new version that I will release at the Conference (http://www.blackhat.com/html/bh-europe-09/bh-eu-09-speakers.html#Damele).
These slides have been presented at Black Hat Euroe conference in Amsterdam on April 16, 2009.
sqlmap - security development in Python



sqlmap - security development in PythonMiroslav Stampar This document provides an overview of sqlmap, an open source penetration testing tool that automates the detection and exploitation of SQL injection vulnerabilities. It discusses the creators and history of the tool, its main features like database enumeration and takeover functionalities, and techniques for detecting different types of SQL injections like blind, error-based, union queries, and time delays. Examples of how each technique works are also provided.
Sql injection with sqlmap



Sql injection with sqlmapHerman Duarte This document discusses SQL injection and the sqlmap tool. It provides an overview of SQL injection, describes how sqlmap can be used to find and exploit SQL injection vulnerabilities, and demonstrates how it can be used to enumerate databases and files systems, and in some cases obtain remote access. It also discusses mitigation techniques like input sanitization and using prepared statements.
Sql Injection - Vulnerability and Security



Sql Injection - Vulnerability and SecuritySandip Chaudhari What is SQL Injection? Why does this problem exist? How it can be exploited? How to secure your app against this vulnerability?
Sql injection



Sql injectionNitish Kumar This document discusses SQL injection attacks and how to mitigate them. It begins by explaining how injection attacks work by tricking applications into executing unintended commands. It then provides examples of how SQL injection can be used to conduct unauthorized access and data modification attacks. The document discusses techniques for finding and exploiting SQL injection vulnerabilities, including through the SELECT, INSERT, UPDATE and UNION commands. It also covers ways to mitigate injection attacks, such as using prepared statements with bound parameters instead of concatenating strings.
SQL INJECTION



SQL INJECTIONMentorcs This document discusses SQL injection (SQLI), which is a code injection technique used to attack data-driven applications. SQLI works by inserting malicious SQL statements into entry fields for execution on the backend database. This allows attackers to read sensitive data, modify database contents, and perform administration tasks. The document outlines common SQLI attack methods like error-based and union-based techniques. It also categorizes SQLI attacks as in-band, inferential/blind, or out-of-band based on how results are returned. Examples are provided to illustrate how SQLI exploits vulnerabilities in dynamic SQL queries.
SQL Injection



SQL InjectionAsish Kumar Rath SQL injection is a code injection technique, used to attack data-driven applications, in which malicious SQL statements are inserted into an entry field for execution (e.g. to dump the database contents to the attacker).
Data Retrieval over DNS in SQL Injection Attacks



Data Retrieval over DNS in SQL Injection AttacksMiroslav Stampar This paper has been made for and it's results were presented at PHDays 2012 conference (Russia / Moscow 30th–31st May 2012) by Miroslav Stampar.
Types of sql injection attacks



Types of sql injection attacksRespa Peter The document discusses different types of SQL injection attacks, including tautologies, illegal/logically incorrect queries, union queries, piggybacked queries, and stored procedures. Tautologies aim to bypass authentication by making conditional statements always true. Illegal queries gather database information by causing syntax or type errors. Union queries extract data by combining results from multiple tables. Piggybacked queries maliciously execute additional queries by abusing query delimiters. Stored procedures can be used to escalate privileges or execute remote commands if vulnerabilities exist. Examples are provided for each type of attack along with potential solutions.
Ppt on sql injection



Ppt on sql injectionashish20012 This document discusses SQL injection, which is a security vulnerability that allows attackers to interfere with how a database operates. SQL injection occurs when user input is not sanitized and is used directly in SQL queries, allowing attackers to alter the structure and meaning of queries. The document provides an example of how an attacker could log in without a password by adding SQL code to the username field. It also lists some common SQL injection techniques like using comments, concatenation, and wildcards. Finally, it points to additional online resources for learning more about SQL injection and database security.
Expanding the control over the operating system from the database



Expanding the control over the operating system from the databaseBernardo Damele A. G. Using a database, either via a SQL injection or via direct connection, as a stepping stone to control the underlying operating system can be achieved.
There is much to say on operating system control by owning a database server: Windows registry access, anti-forensics technique to establish an out-of-band stealth connection, buffer overflow exploitation with memory protections bypass and custom user-defined function injection.
These slides have been presented at SOURCE Conference in Barcelona on September 21, 2009.
Sql injection



Sql injectionZidh The document discusses SQL injection, including its types, methodology, attack queries, and prevention. SQL injection is a code injection technique where a hacker manipulates SQL commands to access a database and sensitive information. It can result in identity spoofing, modifying data, gaining administrative privileges, denial of service attacks, and more. The document outlines the steps of a SQL injection attack and types of queries used. Prevention methods include minimizing privileges, coding standards, and firewalls.
Sqlmap



SqlmapInstitute of Information Security (IIS) sqlmap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers.
seminar report on Sql injection



seminar report on Sql injectionJawhar Ali This document discusses SQL injection, including what it is, how it works, and its impacts. It defines SQL injection as a dangerous web attack that leverages vulnerabilities in web applications to bypass authentication and modify or delete database data. The summary explains that SQL injection works by manipulating SQL queries passed to a backend database, such as by appending additional SQL statements or modifying the structure of the original query. Some impacts of successful SQL injection attacks mentioned are leakage of sensitive information, reputation decline, data loss, and denial of service. Tools for finding SQL injection vulnerabilities like sqlmap and uniscan are also briefly described.
Similar to sqlmap internals (20)
sqlmap internals



sqlmap internalsMiroslav Stampar These are the slides from a talk "sqlmap internals" held at ISACA Croatian Chapter meeting on 09th of April 2018 (Zagreb / Croatia)
Datastax day 2016 : Cassandra data modeling basics



Datastax day 2016 : Cassandra data modeling basicsDuyhai Doan This document discusses data modeling with Apache Cassandra. It covers:
1. The objectives of data modeling like reducing query latency and avoiding disasters
2. Choosing the right partition key which is the main entry point for queries and helps distribute data
3. Using clustering columns to simulate one-to-many relationships and enable sorting and range queries
4. Other critical details like avoiding huge partitions, sub-partitioning techniques, and how deletes create tombstones
VoxxedDays Luxembourg 2019



VoxxedDays Luxembourg 2019Cédrick Lunven This document discusses different API options for databases: REST, gRPC, and GraphQL. It begins with an overview of Apache Cassandra and its key features as a distributed database. It then covers an API design methodology, including conceptual and logical data modeling, mapping queries to tables, and creating the physical schema. The document presents criteria for evaluating API choices and provides pros and cons of REST, gRPC, and GraphQL. It concludes that REST is best for CRUD operations, gRPC for high performance services, and GraphQL for discoverability and flexible payloads.
NoSQL



NoSQLAntonio Castellon This document introduces NoSQL and graph databases. It discusses how NoSQL databases can help with complex and dynamic data that is difficult to model. Graph databases are recommended because they provide a flexible data structure and natural query system that closely matches business logic. Neo4j is highlighted as a top graph database due to its ACID compliance, Cypher query language, and large community support. The document provides examples of how graph databases can help with tasks like social network analysis and bioinformatics.
Rattle Graphical Interface for R Language



Rattle Graphical Interface for R LanguageMajid Abdollahi Rattle is Free (as in Libre) Open Source Software and the source code is available from the Bitbucket repository. We give you the freedom to review the code, use it for whatever purpose you like, and to extend it however you like, without restriction, except that if you then distribute your changes you also need to distribute your source code too.
Rattle - the R Analytical Tool To Learn Easily - is a popular GUI for data mining using R. It presents statistical and visual summaries of data, transforms data that can be readily modelled, builds both unsupervised and supervised models from the data, presents the performance of models graphically, and scores new datasets. One of the most important features (according to me) is that all of your interactions through the graphical user interface are captured as an R script that can be readily executed in R independently of the Rattle interface.
Rattle clocks between 10,000 and 20,000 installations per month from the RStudio CRAN node (one of over 100 nodes). Rattle has been downloaded several million times overall.
Unlocking Your Hadoop Data with Apache Spark and CDH5



Unlocking Your Hadoop Data with Apache Spark and CDH5SAP Concur Spark/Mesos Seattle Meetup group shares the latest presentation from their recent meetup event on showcasing real world implementations of working with Spark within the context of your Big Data Infrastructure.
Session are demo heavy and slide light focusing on getting your development environments up and running including getting up and running, configuration issues, SparkSQL vs. Hive, etc.
To learn more about the Seattle meetup: http://www.meetup.com/Seattle-Spark-Meetup/members/21698691/
Structured Query Language (SQL) - Lecture 5 - Introduction to Databases (1007...



Structured Query Language (SQL) - Lecture 5 - Introduction to Databases (1007...Beat Signer The document discusses Structured Query Language (SQL) and its history and components. It notes that SQL is a declarative query language used to define database schemas, manipulate data through queries, and control transactions. The document outlines SQL's data definition language for defining schemas and data manipulation language for querying and modifying data. It also provides examples of SQL statements for creating tables and defining constraints.
Accelerating analytics on the Sensor and IoT Data. 



Accelerating analytics on the Sensor and IoT Data. Keshav Murthy Informix Warehouse Accelerator (IWA) has helped traditional
data warehousing performance to improve dramatically. Now,
IWA accelerates analytics over the sensor data stored in relational and timeseries data.
20180420 hk-the powerofmysql8



20180420 hk-the powerofmysql8Ivan Ma This document discusses new features and enhancements in MySQL 8.0 that enable modern web applications. Key highlights include a transactional data dictionary for improved DDL performance, JSON functions and data types for flexible schema and document store capabilities, window functions and common table expressions for advanced analytics, and performance improvements through invisible indexes, contention handling, and expanded query hints.
How "·$% developers defeat the web vulnerability scanners



How "·$% developers defeat the web vulnerability scannersChema Alonso Share Favorite
Favorited X
Download More...
Favorited! Want to add tags? Have an opinion? Make a quick comment as well. Cancel
Edit your favorites Cancel
Send to your Group / Event Select Group / Event
Add your message Cancel
Post toBlogger WordPress Twitter Facebook Deliciousmore share options .Embed For WordPress.com
Without related presentations
0 commentsPost a comment
Post a comment
..
Embed Video Subscribe to follow-up comments Unsubscribe from followup comments .
Edit your comment Cancel .Notes on slide 1
no notes for slide #1
no notes for slide #1
..Favorites, Groups & Events
more
How "·$% developers defeat the web vulnerability scanners - Presentation Transcript
1.How ?¿$·& developers defeat the most famous web vulnerability scanners …or how to recognize old friends Chema Alonso Informática64 José Parada Microsoft Ibérica
2.Agenda
1.- Introduction
2.- Inverted Queries
3.- Arithmetic Blind SQL Injection
4.- Time-Based Blind SQL Injection using Heavey Queries
5.- Conclusions
3.1.-Introduction
4.SQL Injection is still here among us
5.Web Application Security Consortium: Comparision http://projects.webappsec.org/Web-Application-Security-Statistics 12.186 sites 97.554 bugs
6.Need to Improve Automatic Scanning
Not always a manual scanning is possible
Time
Confidentiality
Money, money, money…
Need to study new ways to recognize old fashion vulnerabilities to improve automatic scanning tools.
7.2.-Inverted Queries
8.
9.Homers, how are they?
Lazy
Bad trainined
Poor Experience in security stuff
Don´t like working
Don´t like computing
Don´t like coding
Don´t like you!
10.Flanders are Left-handed
11.Right
SELECT UID
FROM USERS
WHERE NAME=‘V_NAME’
AND
PASSWORD=‘V_PASSW’;
12.Wrong?
SELECT UID
FROM USERS
WHERE ‘V_NAME’=NAME AND
‘ V_PASSW’=PASSWORD
13.Login Inverted Query
Select uid
From users where ‘v_name’=name and ‘v_pass’=password
http://www.web.com/login.php?v_name=Robert&v_pass=Kubica’ or '1'='1
Select uid
From users where ‘Robert’=name and ‘Kubica’ or ‘1’=‘1’=password
FAIL
14.Login Inverted SQL Injection an example
Select uid
From users where ‘v_name’=name and ‘v_pass’=password
http://www.web.com/login.php?v_name=Robert&v_pass=’=‘’ or ‘1’=‘1’ or ‘Kubica
Select uid
From users where ‘Robert’=name and ’’=‘’ or ‘1’=‘1’ or ‘Kubica’=password
Success
15.Blind Attacks
Attacker injects code but can´t access directly to the data.
However this injection changes the behavior of the web application.
Then the attacker looks for differences between true code injections (1=1) and false code injections (1=2) in the response pages to extract data.
Blind SQL Injection
Biind Xpath Injection
Blind LDAP Injection
16.Blind SQL Injection Attacks
Attacker injects:
“ True where clauses”
“ False where clauses“
Ex:
Program.php?id=1 and 1=1
Program.php?id=1 and 1=2
Program doesn’t return any visible data from database or data in error messages.
The attacker can´t see any data extracted from the database.
17.Blind SQL Injection Attacks
Attacker analyzes the response pages looking for differences between “True-Answer Page” and “False-Answer Page”:
Different hashes
Different html structure
Different patterns (keywords)
Different linear ASCII sums
“ Different behavior”
By example: Response Time
18.Blind SQL Injection Attacks
If any difference exists, then:
Attacker can extract all information from database
How? Using “booleanization”
MySQL:
Program.php?id=1 and 100>(ASCII(Substring(user(),1,1)))
“ True-Answer Page” or “False-Answer Page”?
MSSQL:
Program.php?id=1 and 100>(Select top 1 ASCII(Substring(name,1,1))) from sysusers)
Oracle:
Program.php?id=1 and 100>(Select ASCII(Sub
Cognitive Database: An Apache Spark-Based AI-Enabled Relational Database Syst...



Cognitive Database: An Apache Spark-Based AI-Enabled Relational Database Syst...Databricks We describe design and implementation of Cognitive Database, a Spark-based relational database that demonstrates novel capabilities of AI-enabled SQL queries. A key aspect of our approach is to first view the structured data source as meaningful unstructured text, and then use the text to build an unsupervised neural network model using a Natural Language Processing (NLP) technique called word embedding. We seamlessly integrate the word embedding model into existing SQL query infrastructure and use it to enable a new class of SQL-based analytics queries called cognitive intelligence (CI) queries.
CI queries use the model vectors to enable complex queries such as semantic matching, inductive reasoning queries such as analogies/semantic clustering, predictive queries using entities not present in a database, and, more generally, using knowledge from external sources. We demonstrate unique capabilities of Cognitive Databases using an Apache Spark 2.2.0 based prototype to execute inductive reasoning CI queries over a multi-modal relational database containing text and images from the ImageNet dataset. We illustrate key aspects of the Spark-based implementation, e.g., UDF implementations of various cognitive functions using Spark SQL, Python (via Jupyter notebook) and Scala based interfaces, Distributed Spark implementation, and integration of GPU-enabled nearest neighbor kernels.
We also discuss a variety of real-world use cases from different application domains. Further details of this system can be found in the Arxiv paper: https://arxiv.org/abs/1712.07199
Mini-lab 1: Stochastic Gradient Descent classifier, Optimizing Logistic Regre...



Mini-lab 1: Stochastic Gradient Descent classifier, Optimizing Logistic Regre...Yao Yao https://github.com/yaowser/data_mining_group_project
https://www.kaggle.com/c/zillow-prize-1/data
From the Zillow real estate data set of properties in the southern California area, conduct the following data cleaning, data analysis, predictive analysis, and machine learning algorithms:
Mini-lab 1: Stochastic Gradient Descent classifier, Optimizing Logistic Regression Model Performance, Optimizing Support Vector Machine Classifier, Accuracy of results and efficiency, Logistic Regression Feature Importance, interpretation of support vectors, Density Graph
AWS SSA Webinar 20 - Getting Started with Data Warehouses on AWS



AWS SSA Webinar 20 - Getting Started with Data Warehouses on AWSCobus Bernard In this session, we will take you through setting up an Amazon Redshift cluster and at the ways you can populate it with data. We will start by using AWS DMS to replicate the data as-is as well as doing some ETL on it. This will be followed by AWS Glue where you can do more advanced ETL operations. Lastly, we will look at how you can use Amazon Kinesis Firehose to stream event directly to the Redshift cluster.
ST-Toolkit, a Framework for Trajectory Data Warehousing



ST-Toolkit, a Framework for Trajectory Data WarehousingSimone Campora Presentation of ST-Toolkit: a Framework for trajectory Data warehousing short paper published in AGILE 2011, Utrecht 20th April 2011.
Scylla Summit 2018: From SAP to Scylla - Tracking the Fleet at GPS Insight



Scylla Summit 2018: From SAP to Scylla - Tracking the Fleet at GPS InsightScyllaDB Originally using SAP Adaptive Server Enterprise (ASE), the GPS Insight team soon found that relational databases simply aren’t a match for high volume machine data. To top it off, SAP ASE’s clustering technology proved cumbersome to manage and operate. In this presentation, you’ll learn about GPS Insight’s hybrid Scylla deployment that runs on-premises and on AWS datacenter. GPS Insight relies on Scylla to capture and analyze GPS data, offloading data from RDBMS to Scylla for hybrid analytics approach.
Apache Lens at Hadoop meetup



Apache Lens at Hadoop meetupamarsri Apache Lens is a unified analytics platform that enables multi-dimensional queries over datasets stored in multiple data warehouses like Hadoop and columnar databases. It provides a single metadata layer and OLAP cube abstraction to allow for data discovery and unified access across data sources. Lens uses a distributed architecture and can push queries to where data resides for efficient processing.
6° Sessione - Ambiti applicativi nella ricerca di tecnologie statistiche avan...



6° Sessione - Ambiti applicativi nella ricerca di tecnologie statistiche avan...Jürgen Ambrosi
In questa sessione vedremo, con il solito approccio pratico di demo hands on, come utilizzare il linguaggio R per effettuare analisi a valore aggiunto,
Toccheremo con mano le performance di parallelizzazione degli algoritmi, aspetto fondamentale per aiutare il ricercatore nel raggiungimento dei suoi obbiettivi.
In questa sessione avremo la partecipazione di Lorenzo Casucci, Data Platform Solution Architect di Microsoft.
The State of Stream Processing



The State of Stream Processingconfluent Speaker: Neil Avery, Technologist, Office of the CTO, Confluent
Stream processing is now at the forefront of many company strategies. Over the last couple of years we have seen streaming use cases explode and now proliferate the landscape of any modern business.
Use cases including digital transformation, IoT, real-time risk, payments microservices and machine learning are all built on the fundamental that they need fast data and they need it at scale.
Apache Kafka® has long been the streaming platform of choice, its origins of being dumb pipes for big data have long since been left behind and now it is the goto-streaming platform of choice.
Stream processing beckons as being the vehicle for driving those streams, and along with it brings a world of real-time semantics surrounding windowing, joining, correctness, elasticity, and accessibility. The ‘current state of stream processing’ walks through the origins of stream processing, applicable use cases and then dives into the challenges currently facing the world of stream processing as it drives the next data revolution.
Neil is a Technologist in the Office of the CTO at Confluent, the company founded by the creators of Apache Kafka. He has over 20 years of expertise of working on distributed computing, messaging and stream processing. He has built or redesigned commercial messaging platforms, distributed caching products as well as developed large scale bespoke systems for tier-1 banks. After a period at ThoughtWorks, he went on to build some of the first distributed risk engines in financial services. In 2008 he launched a startup that specialised in distributed data analytics and visualization. Prior to joining Confluent he was the CTO at a fintech consultancy.
Watch the recording: https://videos.confluent.io/watch/rmU6GHrd4EKFaZrRhdTE3s?.
TAO Fayan_Report on Top 10 data mining algorithms applications with R



TAO Fayan_Report on Top 10 data mining algorithms applications with RFayan TAO This document summarizes and demonstrates the top 10 data mining algorithms integrated with R and RStudio. It introduces algorithms like C4.5, k-Means, SVM, Apriori, EM, PageRank, AdaBoost, kNN, Naive Bayes, and CART. It provides examples applying C4.5, k-Means, and SVM to the iris dataset to classify iris flowers. For C4.5 and SVM, it shows they have similar accuracy while k-Means performs worse. It also demonstrates the Apriori algorithm by generating association rules from a census dataset and interpreting the top 5 rules.
MMDS 2014: Myria (and Scalable Graph Clustering with RelaxMap)



MMDS 2014: Myria (and Scalable Graph Clustering with RelaxMap)University of Washington A talk I gave at the MMDS workshop June 2014 on the Myria system as well as some of Seung-Hee Bae's work on scalable graph clustering.
https://mmds-data.org/
Ad
More from Miroslav Stampar (16)
sqlmap - "One Tiny Step At a Time"



sqlmap - "One Tiny Step At a Time"Miroslav Stampar These are the slides from a talk "sqlmap - One Tiny Step At a Time" held at Bsides Chile 2020 (online)
Blind WAF identification



Blind WAF identificationMiroslav Stampar These are the slides from a talk "Blind WAF identification" held at Sh3llCON 2019 (Santander / Spain)
Why everybody should do CTF / Wargames?



Why everybody should do CTF / Wargames?Miroslav Stampar The document discusses Capture the Flag (CTF) competitions and wargames and why everyone should participate in them. It notes that CTFs are legal hacking games or puzzles that help people improve their information security skills. Wargames are similar but always online and have no time limits. The document outlines different categories of challenges people may encounter in CTFs and wargames, including programming, cryptography, steganography, forensics, reverse engineering, and web challenges. It argues that participating provides free training, is fun, helps improve skills, allows competitive testing of skills, and can help with recruitment and stress testing teams.
Improving Network Intrusion Detection with Traffic Denoise



Improving Network Intrusion Detection with Traffic DenoiseMiroslav Stampar This document discusses improving network intrusion detection systems by filtering out "noise" from real threats. It proposes collecting data from multiple sensors on different IP ranges to identify traffic that is seen across many networks, which is likely noise rather than targeted attacks. By ignoring or lowering the severity of events originating from noisy IP addresses found on public blacklists or seen across different sensor networks, the system could focus alerts on real adversaries and reduce the number of false alarms. An experimental system using these techniques saw a 35-37% reduction in total events and threats after filtering noise. Further development could help security teams prioritize real network threats.
APT Attacks on Critical Infrastructure



APT Attacks on Critical InfrastructureMiroslav Stampar These are the slides from a talk "APT Attacks on
Critical Infrastructure" held at Cyber Defense Symposium 2017 (Mali Losinj / Croatia)
WARNING: Do Not Feed the Bears



WARNING: Do Not Feed the BearsMiroslav Stampar These are the slides from a talk "WARNING:
Do Not Feed the Bears" held at BSidesLjubljana 2017 (Ljubljana / Slovenia)
Non-Esoteric XSS Tips & Tricks



Non-Esoteric XSS Tips & TricksMiroslav Stampar These are the slides from a talk "Non-Esoteric XSS Tips & Tricks" held at FSec 2016 (Croatia / Varazdin 15th September 2016) by Miroslav Stampar
2014 – Year of Broken Name Generator(s)



2014 – Year of Broken Name Generator(s)Miroslav Stampar These are the slides from a guest talk "2014 – Year of Broken Name Generator(s)" held at Faculty of Electrical Engineering and Computing 2015 (Croatia / Zagreb 16th January 2015) by Miroslav Stampar
Smashing the Buffer



Smashing the BufferMiroslav Stampar These are the slides from a talk "Smashing the Buffer" held at BSidesVienna 2014 (Austria / Vienna 22nd November 2014) by Miroslav Stampar
Riding the Overflow - Then and Now



Riding the Overflow - Then and NowMiroslav Stampar These are the slides from a talk "Riding the Overflow - Then and Now" held at FSec 2014 (Croatia / Varazdin 17th September 2014) by Miroslav Stampar
Riding the Overflow - Then and Now



Riding the Overflow - Then and NowMiroslav Stampar This document discusses the history and techniques of buffer overflow exploits. It begins with an overview of stack-based and heap-based buffer overflows and vulnerable code. It then details the history of buffer overflow exploitation from 1961 to present day. The rest of the document explains techniques used to exploit buffer overflows such as DEP/NX, ASLR, stack canaries, NOP sleds, return-to-libc, egg hunting, heap spraying, and return-oriented programming. It also discusses defenses implemented by operating systems like SEHOP, SafeSEH, and safe functions.
Hash DoS Attack



Hash DoS AttackMiroslav Stampar These are the slides from a guest talk "Hash DoS Attack" held at Faculty of Electrical Engineering and Computing 2014 (Croatia / Zagreb 17th January 2014) by Miroslav Stampar
Curious Case of SQLi



Curious Case of SQLiMiroslav Stampar This document describes a case study of discovering and exploiting a SQL injection vulnerability. Over the course of three days, the researcher tested various parameters of a web application using sqlmap and custom payloads. After initial failures, the researcher realized the application was using Windows Search and leveraged its Advanced Query Syntax to conduct file queries and infer file contents. This allowed retrieving a local web.config file containing a SQL Server password. The researcher concluded that thorough manual analysis is needed to fully understand vulnerabilities beyond just using automated scanners.
Spot the Web Vulnerability



Spot the Web VulnerabilityMiroslav Stampar These are the slides from a talk "Spot the Web Vulnerability" held at Hacktivity 2012 conference (Hungary / Budapest 12th–13th October 2012) by Miroslav Stampar.
Analysis of mass SQL injection attacks



Analysis of mass SQL injection attacksMiroslav Stampar These are the slides from a talk "Analysis of mass SQL injection attacks" held at FSec 2012 conference (Croatia / Varazdin 21st September 2012) by Miroslav Stampar
DNS exfiltration using sqlmap



DNS exfiltration using sqlmapMiroslav Stampar These are the slides from a talk "DNS exfiltration using sqlmap" held at PHDays 2012 conference (Russia / Moscow 30th–31st May 2012) by Miroslav Stampar.
Ad
Recently uploaded (19)
Best web hosting Vancouver 2025 for you business



Best web hosting Vancouver 2025 for you businesssteve198109 Vancouver in 2025 is more than scenic views, yoga studios, and oat milk lattes—it’s a thriving hub for eco-conscious entrepreneurs looking to make a real difference. If you’ve ever dreamed of launching a purpose-driven business, now is the time. Whether it’s urban mushroom farming, upcycled furniture sales, or vegan skincare sold online, your green idea deserves a strong digital foundation.
The 2025 Canadian eCommerce landscape is being shaped by trends like sustainability, local innovation, and consumer trust. To stay ahead, eco-startups need reliable hosting that aligns with their values. That’s where 4GoodHosting.com comes in—one of the top-rated Vancouver web hosting providers of 2025. Offering secure, sustainable, and Canadian-based hosting solutions, they help green entrepreneurs build their brand with confidence and conscience.
As eCommerce in Canada embraces localism and environmental responsibility, choosing a hosting provider that shares your vision is essential. 4GoodHosting goes beyond just hosting websites—they champion Canadian businesses, sustainable practices, and meaningful growth.
So go ahead—start that eco-friendly venture. With Vancouver web hosting from 4GoodHosting, your green business and your values are in perfect sync.
Mobile database for your company telemarketing or sms marketing campaigns. Fr...



Mobile database for your company telemarketing or sms marketing campaigns. Fr...DataProvider1 Why Mobile Database Services are Important: Powering the Future of Mobile Applications
Smart Mobile App Pitch Deck丨AI Travel App Presentation Template



Smart Mobile App Pitch Deck丨AI Travel App Presentation Templateyojeari421237 🚀 Smart Mobile App Pitch Deck – "Trip-A" | AI Travel App Presentation Template
This professional, visually engaging pitch deck is designed specifically for developers, startups, and tech students looking to present a smart travel mobile app concept with impact.
Whether you're building an AI-powered travel planner or showcasing a class project, Trip-A gives you the edge to impress investors, professors, or clients. Every slide is cleanly structured, fully editable, and tailored to highlight key aspects of a mobile travel app powered by artificial intelligence and real-time data.
💼 What’s Inside:
- Cover slide with sleek app UI preview
- AI/ML module implementation breakdown
- Key travel market trends analysis
- Competitor comparison slide
- Evaluation challenges & solutions
- Real-time data training model (AI/ML)
- “Live Demo” call-to-action slide
🎨 Why You'll Love It:
- Professional, modern layout with mobile app mockups
- Ideal for pitches, hackathons, university presentations, or MVP launches
- Easily customizable in PowerPoint or Google Slides
- High-resolution visuals and smooth gradients
📦 Format:
- PPTX / Google Slides compatible
- 16:9 widescreen
- Fully editable text, charts, and visuals
Understanding the Tor Network and Exploring the Deep Web



Understanding the Tor Network and Exploring the Deep Webnabilajabin35 While the Tor network, Dark Web, and Deep Web can seem mysterious and daunting, they are simply parts of the internet that prioritize privacy and anonymity. Using tools like Ahmia and onionland search, users can explore these hidden spaces responsibly and securely. It’s essential to understand the technology behind these networks, as well as the risks involved, to navigate them safely. Visit https://torgol.com/
APNIC Update, presented at NZNOG 2025 by Terry Sweetser



APNIC Update, presented at NZNOG 2025 by Terry SweetserAPNIC Terry Sweetser, Training Delivery Manager (South Asia & Oceania) at APNIC presented an APNIC update at NZNOG 2025 held in Napier, New Zealand from 9 to 11 April 2025.
Top Vancouver Green Business Ideas for 2025 Powered by 4GoodHosting



Top Vancouver Green Business Ideas for 2025 Powered by 4GoodHostingsteve198109 Vancouver in 2025 is more than scenic views, yoga studios, and oat milk lattes—it’s a thriving hub for eco-conscious entrepreneurs looking to make a real difference. If you’ve ever dreamed of launching a purpose-driven business, now is the time. Whether it’s urban mushroom farming, upcycled furniture sales, or vegan skincare sold online, your green idea deserves a strong digital foundation.
The 2025 Canadian eCommerce landscape is being shaped by trends like sustainability, local innovation, and consumer trust. To stay ahead, eco-startups need reliable hosting that aligns with their values. That’s where 4GoodHosting.com comes in—one of the top-rated Vancouver web hosting providers of 2025. Offering secure, sustainable, and Canadian-based hosting solutions, they help green entrepreneurs build their brand with confidence and conscience.
As eCommerce in Canada embraces localism and environmental responsibility, choosing a hosting provider that shares your vision is essential. 4GoodHosting goes beyond just hosting websites—they champion Canadian businesses, sustainable practices, and meaningful growth.
So go ahead—start that eco-friendly venture. With Vancouver web hosting from 4GoodHosting, your green business and your values are in perfect sync.
APNIC -Policy Development Process, presented at Local APIGA Taiwan 2025



APNIC -Policy Development Process, presented at Local APIGA Taiwan 2025APNIC Joyce Chen, Senior Advisor, Strategic Engagement at APNIC, presented on 'APNIC Policy Development Process' at the Local APIGA Taiwan 2025 event held in Taipei from 19 to 20 April 2025.
Reliable Vancouver Web Hosting with Local Servers & 24/7 Support



Reliable Vancouver Web Hosting with Local Servers & 24/7 Supportsteve198109 Looking for powerful and affordable web hosting in Vancouver? 4GoodHosting offers premium Canadian web hosting solutions designed specifically for individuals, startups, and businesses across British Columbia. With local data centers in Vancouver and Toronto, we ensure blazing-fast website speeds, superior uptime, and enhanced data privacy—all critical for your business success in today’s competitive digital landscape.
Our Vancouver web hosting plans are packed with value—starting as low as $2.95/month—and include secure cPanel management, free domain transfer, one-click WordPress installs, and robust email support with anti-spam protection. Whether you're hosting a personal blog, business website, or eCommerce store, our scalable cloud hosting packages are built to grow with you.
Enjoy enterprise-grade features like daily backups, DDoS protection, free SSL certificates, and unlimited bandwidth on select plans. Plus, our expert Canadian support team is available 24/7 to help you every step of the way.
At 4GoodHosting, we understand the needs of local Vancouver businesses. That’s why we focus on speed, security, and service—all hosted on Canadian soil. Start your online journey today with a reliable hosting partner trusted by thousands across Canada.
DNS Resolvers and Nameservers (in New Zealand)



DNS Resolvers and Nameservers (in New Zealand)APNIC Geoff Huston, Chief Scientist at APNIC, presented on 'DNS Resolvers and Nameservers in New Zealand' at NZNOG 2025 held in Napier, New Zealand from 9 to 11 April 2025.
IT Services Workflow From Request to Resolution



IT Services Workflow From Request to Resolutionmzmziiskd IT Services Workflow From Request to Resolution
highend-srxseries-services-gateways-customer-presentation.pptx



highend-srxseries-services-gateways-customer-presentation.pptxelhadjcheikhdiop Juniper High End Series
Perguntas dos animais - Slides ilustrados de múltipla escolha



Perguntas dos animais - Slides ilustrados de múltipla escolhasocaslev Slides ilustrados de múltipla escolha
sqlmap internals
- 1. sqlmap internalssqlmap internals Miroslav Stampar ([email protected]; [email protected]) sqlmap internalssqlmap internals Miroslav Stampar ([email protected]; [email protected])
- 2. SecAdmin, Sevilla (Spain) November 24th, 2017 2 IntroductionIntroduction Free and open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database server(s) Written in Python (2) 11 years old (July 25th 2006) 2 authors / core developers (Bernardo Damele and Miroslav Stampar) 65K LoC (Lines of Code) 100% accuracy and 0% false-positives by WAVSEP benchmark of 64 Web Application Scanners (sectoolmarket.com)
- 3. SecAdmin, Sevilla (Spain) November 24th, 2017 3 CapabilitiesCapabilities 78 switches (e.g. --tor) and 91 options (e.g. --url=”...”) in 15 categories (Target, Request, Optimization, Injection, etc.) Full coverage for (relational DBMS-es): MySQL, Oracle, PostgreSQL, Microsoft SQL Server, Microsoft Access, IBM DB2, SQLite, Firebird, Sybase, SAP MaxDB, HSQLDB and Informix Full support for SQLi techniques: boolean- based blind, time-based blind, error-based, UNION query-based and stacked queries Database enumeration, file-system manipulation, out-of-band communication, etc.
- 4. SecAdmin, Sevilla (Spain) November 24th, 2017 4 Sample runSample run
- 5. SecAdmin, Sevilla (Spain) November 24th, 2017 5 Socket pre-connect (1)Socket pre-connect (1) TCP three-way handshake (SYN, SYN-ACK, ACK) is inherently slow (“necessary evil”) Each HTTP request requires a completed TCP handshake procedure sqlmap runs a “pre-connect” thread in background filling a pool of (e.g. 3) connections with TCP handshake done Overrides Python’s socket.connect() 25% speed-up of a program’s run on average
- 6. SecAdmin, Sevilla (Spain) November 24th, 2017 6 Socket pre-connect (2)Socket pre-connect (2)
- 7. SecAdmin, Sevilla (Spain) November 24th, 2017 7 NULL connection (1)NULL connection (1) In boolean-based blind SQLi response sizes should suffice (e.g. >1000 bytes → TRUE) “NULL” naming because of skipping the retrieval of complete HTTP response Range: bytes=-1 Content-Range: bytes 4789-4789/4790 HEAD /search.aspx HTTP/1.1 Content-Length: 4790 Both are resulting (if applicable) with empty HTTP body (faster retrieval of responses) By looking into “length” headers we can differentiate TRUE from FALSE answers
- 8. SecAdmin, Sevilla (Spain) November 24th, 2017 8 NULL connection (2)NULL connection (2)
- 9. SecAdmin, Sevilla (Spain) November 24th, 2017 9 HashDB (1)HashDB (1) Storage of resumable session data at centralized place (local SQLite3 database) Non-ASCII values are being automatically serialized/deserialized (pickle) INSERT INTO storage VALUES (INT(MD5(target_url, uid, MILESTONE_SALT) [:8]), stored_value) uid uniquely describes stored_value for a given target_url (e.g.: KB_INJECTIONS, SELECT VERSION(), etc.) MILESTONE_SALT changed whenever there is an incompatible update of HashDB mechanism
- 10. SecAdmin, Sevilla (Spain) November 24th, 2017 10 HashDB (2)HashDB (2)
- 11. SecAdmin, Sevilla (Spain) November 24th, 2017 11 BigArray (1)BigArray (1) Support for huge table dumps (e.g. millions of rows) Raw data needs to be held somewhere before being processed (and eventually stored) In memory storage was a good enough choice until user appetites went bigger (!) Memory mapping into smaller chunks (1MB) – memory pages Temporary files store (compressed) chunks In-memory caching of currently used chunk O(1) read/write access
- 12. SecAdmin, Sevilla (Spain) November 24th, 2017 12 BigArray (2)BigArray (2)
- 13. SecAdmin, Sevilla (Spain) November 24th, 2017 13 Heuristics (1)Heuristics (1) “Educational shortcuts to ease the cognitive load of making a decision” Resulting with a solution which is not guaranteed to be optimal (though very helpful) Type casting (e.g. ?id=1foobar) DBMS error reporting (e.g. ?id=1())'”(”') Character filtering (e.g. ?id=1 AND 7=(7)) Length constraining (e.g. id=1 AND 3182= 3182) (quick) DBMS detection (e.g. ?id=1 AND (SELECT 0x73716c)=0x73716c)
- 14. SecAdmin, Sevilla (Spain) November 24th, 2017 14 Heuristics (2)Heuristics (2)
- 15. SecAdmin, Sevilla (Spain) November 24th, 2017 15 Boolean inference (1)Boolean inference (1) Binary search using greater-than operator O(Log2n) complexity compared to sequential search with O(n) Faster than bit-by-bit extraction (on average 6 requests compared to 8 requests) For example: Sample initial table ['A','B',...'Z'] AND (...) > 'M' → TRUE → ['N',...'Z'] AND (...) > 'S' → FALSE → ['N',...'S'] AND (...) > 'O' → TRUE → ['P', 'R', 'S'] AND (...) > 'R' → FALSE → ['P', 'R'] AND (...) > 'P' → FALSE → 'P' (result)
- 16. SecAdmin, Sevilla (Spain) November 24th, 2017 16 Boolean inference (2)Boolean inference (2)
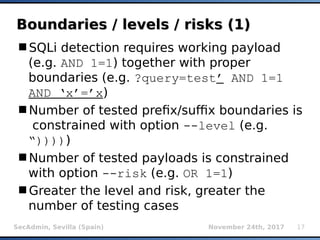
- 17. SecAdmin, Sevilla (Spain) November 24th, 2017 17 Boundaries / levels / risks (1)Boundaries / levels / risks (1) SQLi detection requires working payload (e.g. AND 1=1) together with proper boundaries (e.g. ?query=test’ AND 1=1 AND ‘x’=’x) Number of tested prefix/suffix boundaries is constrained with option --level (e.g. “))))) Number of tested payloads is constrained with option --risk (e.g. OR 1=1) Greater the level and risk, greater the number of testing cases
- 18. SecAdmin, Sevilla (Spain) November 24th, 2017 18 Boundaries / levels / risks (2)Boundaries / levels / risks (2)
- 19. SecAdmin, Sevilla (Spain) November 24th, 2017 19 Statistics (1)Statistics (1) Network latency (or lagging) is the main problem of time-based blind technique For example, used deliberate delay is 1 sec, normal response times are >0.5 and <2.0 secs, what we can conclude for 1.5 sec response? sqlmap learns what's normal and what's not from non-delay based payload responses (e.g. boolean-based blind payloads) Normal distribution is being calculated (Gaussian bell-shaped curve) Everything inside is considered as “normal”, outside as “not normal”
- 20. SecAdmin, Sevilla (Spain) November 24th, 2017 20 Statistics (2)Statistics (2) Everything that's normal (i.e. not deliberately delayed) should fit under the curve μ(t) represents a mean, while σ(t) represents a standard deviation of response times 99.99% of normal response times fall under the upper border value μ(t) + 7σ(t)
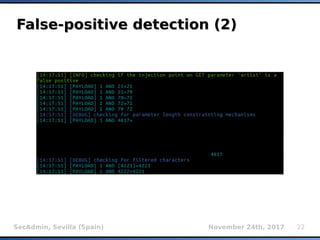
- 21. SecAdmin, Sevilla (Spain) November 24th, 2017 21 False-positive detection (1)False-positive detection (1) Detection of “error” in SQLi detection engine Giving false sense of certainty while in reality there is nothing exploitable at the other side Almost exclusive to boolean-based blind and time-based blind cases Simple tests are being done after the detection Comparing responses to boolean operations with expected results (e.g. id=1 AND 95=27) If any of results is contrary to the expected value, SQLi is discarded as a false-positive (or unexploitable)
- 22. SecAdmin, Sevilla (Spain) November 24th, 2017 22 False-positive detection (2)False-positive detection (2)
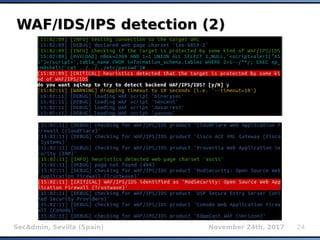
- 23. SecAdmin, Sevilla (Spain) November 24th, 2017 23 WAF/IDS/IPS detection (1)WAF/IDS/IPS detection (1) Sending deliberately suspicious payloads and checking response(s) for unique characteristics (e.g.) ?id=1&bwXY=5253 AND 1=1 UNION ALL SELECT 1,NULL,'<script>alert("XSS") </script>',table_name FROM information_schema.tables WHERE 2>1--/**/; EXEC xp_cmdshell('cat ../../ ../etc/passwd')# ModSecurity returns HTTP error code 501 on detected attack, F5 BIG-IP adds its own X- Cnection HTTP header, etc. Fingeprinting 59 different WAF/IDS/IPS products
- 24. SecAdmin, Sevilla (Spain) November 24th, 2017 24 WAF/IDS/IPS detection (2)WAF/IDS/IPS detection (2)
- 25. SecAdmin, Sevilla (Spain) November 24th, 2017 25 Tamper scripts (1)Tamper scripts (1) Auxiliary python scripts modifying the payload before being sent (e.g. ?id=1 AND 2>1 to ?id=1 AND 2 NOT BETWEEN 0 AND 1) Currently 54 tamper scripts (between.py, space2randomblank.py, versionedkeywords.py, etc.) User has to choose appropriate one(s) based on collected knowledge of target's behavior and/or detected WAF/IDS/IPS product Chain of tamper scripts (if required) can be used (e.g. --tamper=”between, ifnull2ifisnull”)
- 26. SecAdmin, Sevilla (Spain) November 24th, 2017 26 Tamper scripts (2)Tamper scripts (2)
- 27. SecAdmin, Sevilla (Spain) November 24th, 2017 27 Brute-forcing identifiers (1)Brute-forcing identifiers (1) In some cases system tables are unreadable (e.g. because of lack of permissions) Hence, no way to retrieve identifier names (tables and columns) sqlmap does guessing by brute-forcing availability of most common identifiers (e.g. ?id=1 AND EXISTS(SELECT 123 FROM users)) Identifiers (3369 table and 2601 column names) have been collected and frequency- sorted by retrieving and parsing thousands of online SQL scripts
- 28. SecAdmin, Sevilla (Spain) November 24th, 2017 28 Brute-forcing identifiers (2)Brute-forcing identifiers (2)
- 29. SecAdmin, Sevilla (Spain) November 24th, 2017 29 Hash cracking (1)Hash cracking (1) Automatic recognition and dictionary cracking of 30 different hash algorithms (e.g. mysql, mssql, md5_generic, sha1_generic, etc.) Included dictionary with 1.4 million wordlist entries (RockYou, MySpace, Gawker, etc.) Multiprocessing (# of cores) Blazing fast (e.g. under 10 seconds for whole dictionary pass with mysql routine) Stores uncracked hashes to file for eventual further processing (with other tools)
- 30. SecAdmin, Sevilla (Spain) November 24th, 2017 30 Hash cracking (2)Hash cracking (2)
- 31. SecAdmin, Sevilla (Spain) November 24th, 2017 31 Stagers / backdoors (1)Stagers / backdoors (1) Stager uploaded in a first (dirty) stage (e.g. possibility of a query junk in case of INTO OUTFILE method) Stager has a functionality of uploading arbitrary files Backdoor (or any binary) uploaded in second (clean) stage by using stager Backdoor has a functionality of executing arbitrary OS commands Supported platforms: PHP, ASP, ASPX, JSP
- 32. SecAdmin, Sevilla (Spain) November 24th, 2017 32 Stagers / backdoors (2)Stagers / backdoors (2)
- 33. SecAdmin, Sevilla (Spain) November 24th, 2017 33 DNS exfiltration (1)DNS exfiltration (1) In some cases it's possible to incorporate SQL (sub)query results into DNS resolution requests Microsoft SQL Server, Oracle, MySQL and PostgreSQL Dozens of resulting characters can be transferred per single request (compared to boolean-based blind and time-based blind) Domain name server entry (e.g. ns1.attacker.com) has to point to IP address of machine running sqlmap
- 34. SecAdmin, Sevilla (Spain) November 24th, 2017 34 DNS exfiltration (2)DNS exfiltration (2)
- 35. SecAdmin, Sevilla (Spain) November 24th, 2017 35 DNS exfiltration (3)DNS exfiltration (3)
- 36. SecAdmin, Sevilla (Spain) November 24th, 2017 36 Questions?Questions?







