SSO using CAS + two-factor authentication (PyGrunn 2014 talk)
13 likes7,682 views
Modern authentication techniques in Python web applications. PyGrunn talk by Artur Barseghyan. Year 2014.
1 of 38
Downloaded 119 times




































Ad
Recommended
A Survey on SSO Authentication protocols: Security and Performance



A Survey on SSO Authentication protocols: Security and PerformanceAmin Saqi This document surveys and compares several single sign-on authentication protocols: OAuth 2.0, OpenID Connect 1.0, CAS 3.0, and SAML 2.0. It provides an overview of each protocol, including basic definitions, key components, and sample flows. It then reviews the security and performance of each protocol, comparing their vulnerabilities. The document aims to help understand the security and performance tradeoffs of different authentication protocols.
An Introduction to OAuth2



An Introduction to OAuth2Aaron Parecki Slides from my O'Reilly Webcast on OAuth 2.
Book coming in 2013 http://shop.oreilly.com/product/0636920023531.do
OAuth2 and Spring Security



OAuth2 and Spring SecurityOrest Ivasiv The document discusses OAuth2 and Spring Security. It provides an overview of OAuth2 concepts including the four main roles (resource owner, resource server, client, and authorization server), four common grant types (authorization code, implicit, resource owner password credentials, and client credentials), and how to implement OAuth2 flows in Spring Security. Sample OAuth2 applications using Spring Security are also mentioned.
An Introduction to OAuth 2



An Introduction to OAuth 2Aaron Parecki The document provides an overview of the history and development of OAuth standards for authorization. It describes some of the issues with early implementations that prompted the creation of OAuth 1.0, including services storing user passwords and lack of ability to revoke access. OAuth 1.0 introduced signatures to address these issues. OAuth 2.0 replaced signatures with HTTPS and defines common flows for different use cases, including authorization code, implicit, password, and client credentials grants.
OAuth2 + API Security



OAuth2 + API SecurityAmila Paranawithana The document discusses OAuth 2.0 and how it provides a method for third party applications to access private resources from an API, while allowing the resource owners to authorize access without sharing credentials. It describes the four main roles in OAuth 2.0 - resource owner, client, authorization server, and resource server. It also summarizes the three main authorization flows - authorization code, implicit, and client credentials flows. The document provides details on how each flow works, including the request and response parameters.
OAuth 2.0



OAuth 2.0Uwe Friedrichsen This slide deck gives an introduction to OAuth 2.0, starting with some concepts, explaining the flow plus a few hints. The reminder of the slides are about implementing an OAuth 2.0 server using the Apache Amber library (renamed to Apache Oltu lately). My impression is that many developers shy away as soon as they hear "security" and so I did not only want to talk about the concepts of OAuth 2.0 but also wanted to show how easily you can implement an OAuth 2.0 server ... hope it reduces the fear of contact a bit ... ;-)
Spring security oauth2



Spring security oauth2axykim00 OAuth2 is a protocol for authorization that allows clients limited access to user accounts and specifies four methods for obtaining an access token, including the authorization code flow. The authorization code flow involves a client redirecting a user to an authorization server, the user authorizing access, and the authorization server issuing an authorization code to the client, which can then request an access token to access a resource server on the user's behalf, while avoiding exposing the user's credentials directly.
Token, token... From SAML to OIDC



Token, token... From SAML to OIDCShiu-Fun Poon This document compares and contrasts three token-based authentication and authorization protocols: SAML, OAuth access tokens, and OpenID Connect ID tokens.
SAML uses XML assertions for identity and authorization. Access tokens in OAuth are opaque bearer strings, while ID tokens in OpenID Connect are JSON Web Tokens (JWTs) containing user information. SAML is for web services and uses WS-Security, while access tokens and ID tokens can be used by web and mobile apps via HTTP. Both SAML and ID tokens can be used to represent user identities, while access tokens and SAML assertions can authorize access to protected resources. Security considerations for each include confidentiality, integrity, and replay attacks.
Spring Security



Spring SecurityBoy Tech I did this presentation for one of my java user groups at work.
Basically, this is a mashed up version of various presentations, slides and images that I gathered over the internet.
I've quoted the sources in the end. Feel free to reuse it as you like.
Introduction to Web Application Penetration Testing



Introduction to Web Application Penetration TestingNetsparker These slides give an introduction to all the different things and stages that make a complete web application penetration test. It starts from the very basics, including how to define a Scope of Engagement.
These slides are part of the course Introduction to Web Application Security and Penetration Testing with Netsparker, which can be found here: https://www.netsparker.com/blog/web-security/introduction-web-application-penetration-testing/
Wireless Network Security



Wireless Network SecurityGyana Ranjana The document provides an overview of wireless network security, outlining common issues, threats, and security measures for wireless networks. It discusses standards and protocols like WEP, WPA, and WPA2 and provides practical tips for securing a wireless network, such as enabling encryption, changing default settings, and using firewalls. The document also briefly discusses future trends in wireless network security.
Xss attack



Xss attackManjushree Mashal An XSS attack is a type of vulnerability that allows malicious scripts to be injected into web pages viewed by other users. There are three main types: reflected XSS occurs when a link containing malicious code is clicked; stored XSS injects code directly into a vulnerable website, potentially affecting many users; DOM-based XSS involves injecting code into a website hosted on a user's local system, allowing the attacker to access that user's browser privileges. The document provides examples of how XSS attacks work and can be used to hijack accounts, insert hostile content, steal cookies, and redirect users.
IdP, SAML, OAuth



IdP, SAML, OAuthDan Brinkmann IdP, SAML, OAuth are new acronyms for identity in the cloud. SAML is used for federated authentication between an identity provider (IdP) like Active Directory and a service provider (SP) like Office 365. The IdP authenticates the user and sends a SAML token with claims to the SP. OAuth streamlines authentication for mobile by issuing short-lived access tokens instead of passing full credentials or SAML assertions between each service. It allows authorization without passwords and tokens can be revoked, reducing risks of compromised apps. Office 365 uses Azure Active Directory as an IdP with SAML or OAuth to authenticate users from an on-premises Active Directory via federation or synchronization.
Single Sign On 101



Single Sign On 101Mike Schwartz These slides are supposed to help you understand the basics of application security, and how the latest technologies come together to enable you to reduce the number of times people at your organization need to authenticate.
For more information visit. http://gluu.org
OAuth2 - Introduction



OAuth2 - IntroductionKnoldus Inc. The OAuth 2.0 authorization framework enables a third-party
application to obtain limited access to an HTTP service, either on
behalf of a resource owner by orchestrating an approval interaction
between the resource owner and the HTTP service, or by allowing
the third-party application to obtain access on its own behalf.
How to Unblock an ePass2003 Token



How to Unblock an ePass2003 TokenMyesign The document provides instructions for unblocking an ePass2003 token by downloading and installing an admin password plug-in file. It involves inserting the token, downloading the driver file from a website, extracting the downloaded file, running the admin password plug-in setup, clicking the triangle icon to unblock the token, and entering the default SO PIN and a new user PIN of at least 8 characters when prompted.
Postman tests in jenkins



Postman tests in jenkinsAlex Galkin This document discusses integrating Postman API tests into a Continuous Integration (CI) flow using Jenkins. It describes exporting Postman collections and environment variables to files and pushing them to source control. It then provides steps to install prerequisites like Node.js, NPM, and Newman on the Jenkins server and configure a Jenkins job to run Newman after deployment to execute the Postman tests as part of the CI process.
Implementing WebAuthn & FAPI supports on Keycloak



Implementing WebAuthn & FAPI supports on KeycloakYuichi Nakamura Keycloak supports WebAuthn and FAPI by implementing their features and passing conformance tests. Hitachi contributed WebAuthn support and worked with NRI to add FAPI compliance, addressing issues like supporting newer signature algorithms and the PKCE protocol. Further contributions are welcomed to resolve remaining FAPI test issues.
Developer Tutorial: WebAuthn for Web & FIDO2 for Android



Developer Tutorial: WebAuthn for Web & FIDO2 for AndroidFIDO Alliance This tutorial walks through how to build a website with a simple re-authentication functionality using a fingerprint sensor. Re-authentication is a concept where a user signs into a website once, then authenticate again as they try to enter important sections of the website, or come back after a certain interval, etc in order to protect the account. It also covers how to build an Android app with a simple re-authentication functionality using a fingerprint sensor. "Re-authentication" is a concept where user signs into an app once, then authenticate again when they come back to your app, or trying to access an important section of your app.
Network Programming



Network ProgrammingVinayak Hegde Hey! Socket programming got you down? Is this stuff just a little too difficult to figure out
from the man pages? You want to do cool Internet programming, but you don't have time to wade
through a gob of structs trying to figure out if you have to call bind() before you connect(),
etc., etc.
Well, guess what! I've already done this nasty business, and I'm dying to share the information
with everyone! You've come to the right place. This document should give the average competent C
programmer the edge s/he needs to get a grip on this networking noise.
And check it out: I've finally caught up with the future (just in the nick of time, too!) and have
updated the Guide for IPv6! Enjoy!
Single sign on - benefits, challenges and case study : iFour consultancy



Single sign on - benefits, challenges and case study : iFour consultancyDevam Shah Single sign on - benefits, challenges and case study.
Courtesy : www.ifour-consultancy.com and Symbiosis students
Visio Diagram of a user SSO Flow



Visio Diagram of a user SSO FlowMike Reams Demonstrates a user accessing an SSO provider from Portal as an authenticated/authorized user originating from the IdP
Rest API Security - A quick understanding of Rest API Security



Rest API Security - A quick understanding of Rest API SecurityMohammed Fazuluddin This document discusses REST API security methods. It provides an overview of authentication and authorization and describes common security methods like cookie-based authentication, token-based authentication, OAuth, OpenID, and SAML. It then compares OAuth2, OpenID, and SAML and discusses best practices for securing REST APIs like protecting HTTP methods, validating URLs, using security headers, and encoding JSON input.
Introduction to OpenID Connect 



Introduction to OpenID Connect Nat Sakimura This document summarizes a presentation about OpenID Connect. OpenID Connect is an identity layer on top of the OAuth 2.0 protocol that allows clients to verify the identity of the user based on the authentication performed by an authorization server, as well as to obtain basic profile information about the user. It defines core functionality for modern identity frameworks by standardizing how clients and servers discover and use identity data exposed by identity providers and how clients can verify that identity data. The presenter discusses how OpenID Connect provides a simple yet powerful way to authenticate users and share attributes about them between websites and applications in an interoperable manner.
Azure Key Vault - Getting Started



Azure Key Vault - Getting StartedTaswar Bhatti A description of Azure Key Vault. Why do we need Azure Key Vault where does it fit in a solution. The details of storing keys, secrets and certificate inside of key vault. Using key vault for encryption and decryption of data
Authentication vs authorization



Authentication vs authorizationFrank Victory Authentication verifies a user's identity by validating credentials like a username and password. Authorization then determines what access and permissions an authenticated user has. Authentication methods can include something you know like passwords, something you have like tokens or smartcards, or something you are like biometrics. Common authentication practices for systems include setting password policies, locking accounts after failed logins, and disabling unused accounts. Proper authentication helps implement access controls and security.
Spring security



Spring securitySaurabh Sharma This document provides an overview of Spring Security, including what it is, how it handles authentication and authorization, and how to configure it. Spring Security provides comprehensive security services for Java enterprise applications, including authentication support for databases, LDAP, CAS, and custom authentication. It handles authentication through establishing a user's identity and authorization through controlling user access to resources. The document discusses configuring Spring Security through Java configuration and XML files, and covers topics like security filters, access control patterns, and the basic authentication process.
OWASP Top 10 And Insecure Software Root Causes



OWASP Top 10 And Insecure Software Root CausesMarco Morana This document discusses common web application vulnerabilities and their root causes. It provides an overview of the OWASP Top 10 list of vulnerabilities, describing each vulnerability type, how attackers exploit them, examples of insecure code that enables the vulnerabilities, and recommendations for secure coding practices to prevent the vulnerabilities. Specific vulnerabilities covered include cross-site scripting, SQL injection, malicious file execution, insecure direct object references, cross-site request forgery, and information leakage from error handling. The document emphasizes the importance of following secure coding standards and input validation to prevent vulnerabilities.
Jasig Central Authentication Service in Ten Minutes



Jasig Central Authentication Service in Ten MinutesAndrew Petro CAS (Central Authentication Service) is an open source single sign-on system that allows a user to log in once and gain access to multiple applications without re-authenticating. It acts as a central authentication system and proxy, allowing web applications to avoid directly handling user passwords. CAS provides authentication handlers for LDAP, Active Directory, Kerberos, and other systems. It also supports single sign-out, returning user attributes, clustering, and integrating with portals and other applications through proxy authentication.
Two factor authentication presentation mcit



Two factor authentication presentation mcitmmubashirkhan This document discusses two-factor authentication (2FA) as a method to strengthen user authentication beyond just a username and password. It describes how 2FA uses two different factors, something you know and something you have/are, to verify identity. Specifically, it evaluates using one-time passwords (OTPs) with hard tokens, mobile tokens, and SMS. While hardware tokens are very secure, they are also expensive and inconvenient. Mobile tokens are cheaper but still vulnerable to attacks. The best approach recommends sending the OTP via mobile token while sending transaction details via SMS to separate the factors and prevent SIM swap attacks. The document provides recommendations like using HTTPS and hashing to further improve security with 2FA.
Ad
More Related Content
What's hot (20)
Spring Security



Spring SecurityBoy Tech I did this presentation for one of my java user groups at work.
Basically, this is a mashed up version of various presentations, slides and images that I gathered over the internet.
I've quoted the sources in the end. Feel free to reuse it as you like.
Introduction to Web Application Penetration Testing



Introduction to Web Application Penetration TestingNetsparker These slides give an introduction to all the different things and stages that make a complete web application penetration test. It starts from the very basics, including how to define a Scope of Engagement.
These slides are part of the course Introduction to Web Application Security and Penetration Testing with Netsparker, which can be found here: https://www.netsparker.com/blog/web-security/introduction-web-application-penetration-testing/
Wireless Network Security



Wireless Network SecurityGyana Ranjana The document provides an overview of wireless network security, outlining common issues, threats, and security measures for wireless networks. It discusses standards and protocols like WEP, WPA, and WPA2 and provides practical tips for securing a wireless network, such as enabling encryption, changing default settings, and using firewalls. The document also briefly discusses future trends in wireless network security.
Xss attack



Xss attackManjushree Mashal An XSS attack is a type of vulnerability that allows malicious scripts to be injected into web pages viewed by other users. There are three main types: reflected XSS occurs when a link containing malicious code is clicked; stored XSS injects code directly into a vulnerable website, potentially affecting many users; DOM-based XSS involves injecting code into a website hosted on a user's local system, allowing the attacker to access that user's browser privileges. The document provides examples of how XSS attacks work and can be used to hijack accounts, insert hostile content, steal cookies, and redirect users.
IdP, SAML, OAuth



IdP, SAML, OAuthDan Brinkmann IdP, SAML, OAuth are new acronyms for identity in the cloud. SAML is used for federated authentication between an identity provider (IdP) like Active Directory and a service provider (SP) like Office 365. The IdP authenticates the user and sends a SAML token with claims to the SP. OAuth streamlines authentication for mobile by issuing short-lived access tokens instead of passing full credentials or SAML assertions between each service. It allows authorization without passwords and tokens can be revoked, reducing risks of compromised apps. Office 365 uses Azure Active Directory as an IdP with SAML or OAuth to authenticate users from an on-premises Active Directory via federation or synchronization.
Single Sign On 101



Single Sign On 101Mike Schwartz These slides are supposed to help you understand the basics of application security, and how the latest technologies come together to enable you to reduce the number of times people at your organization need to authenticate.
For more information visit. http://gluu.org
OAuth2 - Introduction



OAuth2 - IntroductionKnoldus Inc. The OAuth 2.0 authorization framework enables a third-party
application to obtain limited access to an HTTP service, either on
behalf of a resource owner by orchestrating an approval interaction
between the resource owner and the HTTP service, or by allowing
the third-party application to obtain access on its own behalf.
How to Unblock an ePass2003 Token



How to Unblock an ePass2003 TokenMyesign The document provides instructions for unblocking an ePass2003 token by downloading and installing an admin password plug-in file. It involves inserting the token, downloading the driver file from a website, extracting the downloaded file, running the admin password plug-in setup, clicking the triangle icon to unblock the token, and entering the default SO PIN and a new user PIN of at least 8 characters when prompted.
Postman tests in jenkins



Postman tests in jenkinsAlex Galkin This document discusses integrating Postman API tests into a Continuous Integration (CI) flow using Jenkins. It describes exporting Postman collections and environment variables to files and pushing them to source control. It then provides steps to install prerequisites like Node.js, NPM, and Newman on the Jenkins server and configure a Jenkins job to run Newman after deployment to execute the Postman tests as part of the CI process.
Implementing WebAuthn & FAPI supports on Keycloak



Implementing WebAuthn & FAPI supports on KeycloakYuichi Nakamura Keycloak supports WebAuthn and FAPI by implementing their features and passing conformance tests. Hitachi contributed WebAuthn support and worked with NRI to add FAPI compliance, addressing issues like supporting newer signature algorithms and the PKCE protocol. Further contributions are welcomed to resolve remaining FAPI test issues.
Developer Tutorial: WebAuthn for Web & FIDO2 for Android



Developer Tutorial: WebAuthn for Web & FIDO2 for AndroidFIDO Alliance This tutorial walks through how to build a website with a simple re-authentication functionality using a fingerprint sensor. Re-authentication is a concept where a user signs into a website once, then authenticate again as they try to enter important sections of the website, or come back after a certain interval, etc in order to protect the account. It also covers how to build an Android app with a simple re-authentication functionality using a fingerprint sensor. "Re-authentication" is a concept where user signs into an app once, then authenticate again when they come back to your app, or trying to access an important section of your app.
Network Programming



Network ProgrammingVinayak Hegde Hey! Socket programming got you down? Is this stuff just a little too difficult to figure out
from the man pages? You want to do cool Internet programming, but you don't have time to wade
through a gob of structs trying to figure out if you have to call bind() before you connect(),
etc., etc.
Well, guess what! I've already done this nasty business, and I'm dying to share the information
with everyone! You've come to the right place. This document should give the average competent C
programmer the edge s/he needs to get a grip on this networking noise.
And check it out: I've finally caught up with the future (just in the nick of time, too!) and have
updated the Guide for IPv6! Enjoy!
Single sign on - benefits, challenges and case study : iFour consultancy



Single sign on - benefits, challenges and case study : iFour consultancyDevam Shah Single sign on - benefits, challenges and case study.
Courtesy : www.ifour-consultancy.com and Symbiosis students
Visio Diagram of a user SSO Flow



Visio Diagram of a user SSO FlowMike Reams Demonstrates a user accessing an SSO provider from Portal as an authenticated/authorized user originating from the IdP
Rest API Security - A quick understanding of Rest API Security



Rest API Security - A quick understanding of Rest API SecurityMohammed Fazuluddin This document discusses REST API security methods. It provides an overview of authentication and authorization and describes common security methods like cookie-based authentication, token-based authentication, OAuth, OpenID, and SAML. It then compares OAuth2, OpenID, and SAML and discusses best practices for securing REST APIs like protecting HTTP methods, validating URLs, using security headers, and encoding JSON input.
Introduction to OpenID Connect 



Introduction to OpenID Connect Nat Sakimura This document summarizes a presentation about OpenID Connect. OpenID Connect is an identity layer on top of the OAuth 2.0 protocol that allows clients to verify the identity of the user based on the authentication performed by an authorization server, as well as to obtain basic profile information about the user. It defines core functionality for modern identity frameworks by standardizing how clients and servers discover and use identity data exposed by identity providers and how clients can verify that identity data. The presenter discusses how OpenID Connect provides a simple yet powerful way to authenticate users and share attributes about them between websites and applications in an interoperable manner.
Azure Key Vault - Getting Started



Azure Key Vault - Getting StartedTaswar Bhatti A description of Azure Key Vault. Why do we need Azure Key Vault where does it fit in a solution. The details of storing keys, secrets and certificate inside of key vault. Using key vault for encryption and decryption of data
Authentication vs authorization



Authentication vs authorizationFrank Victory Authentication verifies a user's identity by validating credentials like a username and password. Authorization then determines what access and permissions an authenticated user has. Authentication methods can include something you know like passwords, something you have like tokens or smartcards, or something you are like biometrics. Common authentication practices for systems include setting password policies, locking accounts after failed logins, and disabling unused accounts. Proper authentication helps implement access controls and security.
Spring security



Spring securitySaurabh Sharma This document provides an overview of Spring Security, including what it is, how it handles authentication and authorization, and how to configure it. Spring Security provides comprehensive security services for Java enterprise applications, including authentication support for databases, LDAP, CAS, and custom authentication. It handles authentication through establishing a user's identity and authorization through controlling user access to resources. The document discusses configuring Spring Security through Java configuration and XML files, and covers topics like security filters, access control patterns, and the basic authentication process.
OWASP Top 10 And Insecure Software Root Causes



OWASP Top 10 And Insecure Software Root CausesMarco Morana This document discusses common web application vulnerabilities and their root causes. It provides an overview of the OWASP Top 10 list of vulnerabilities, describing each vulnerability type, how attackers exploit them, examples of insecure code that enables the vulnerabilities, and recommendations for secure coding practices to prevent the vulnerabilities. Specific vulnerabilities covered include cross-site scripting, SQL injection, malicious file execution, insecure direct object references, cross-site request forgery, and information leakage from error handling. The document emphasizes the importance of following secure coding standards and input validation to prevent vulnerabilities.
Viewers also liked (20)
Jasig Central Authentication Service in Ten Minutes



Jasig Central Authentication Service in Ten MinutesAndrew Petro CAS (Central Authentication Service) is an open source single sign-on system that allows a user to log in once and gain access to multiple applications without re-authenticating. It acts as a central authentication system and proxy, allowing web applications to avoid directly handling user passwords. CAS provides authentication handlers for LDAP, Active Directory, Kerberos, and other systems. It also supports single sign-out, returning user attributes, clustering, and integrating with portals and other applications through proxy authentication.
Two factor authentication presentation mcit



Two factor authentication presentation mcitmmubashirkhan This document discusses two-factor authentication (2FA) as a method to strengthen user authentication beyond just a username and password. It describes how 2FA uses two different factors, something you know and something you have/are, to verify identity. Specifically, it evaluates using one-time passwords (OTPs) with hard tokens, mobile tokens, and SMS. While hardware tokens are very secure, they are also expensive and inconvenient. Mobile tokens are cheaper but still vulnerable to attacks. The best approach recommends sending the OTP via mobile token while sending transaction details via SMS to separate the factors and prevent SIM swap attacks. The document provides recommendations like using HTTPS and hashing to further improve security with 2FA.
Data-driven Security: Protect APIs from Adaptive Threats



Data-driven Security: Protect APIs from Adaptive ThreatsApigee | Google Cloud This document discusses data-driven security and Apigee's approach. It begins by outlining the challenges posed by adaptive threats to APIs. Then it describes why data-driven security is needed and how current security approaches are not adaptive enough. The document introduces Apigee Sense, a new adaptive API security product that detects threat patterns at the API layer using machine learning algorithms. It analyzes billions of events to identify anomalous behavior patterns and detect bot attacks in order to stop bots and protect APIs from sophisticated threats.
CAS Enhancement



CAS EnhancementGuo Albert - Single Sign-On (SSO) allows a user to log in once and gain access to multiple applications without re-authenticating.
- The Central Authentication Service (CAS) is an open source SSO protocol and server that provides single sign-on for web applications.
- CAS uses tickets instead of transmitting passwords to applications, improving security. It supports many platforms and has a large user base mainly of universities.
Authentication with zend framework



Authentication with zend frameworkGeorge Mihailov Presentation is from http://framework.zend.com/wiki/display/ZFUSER/Authentication+with+Zend+Framework
Central Authentication Service (CAS) SSO for EMC Documentum Rest Services



Central Authentication Service (CAS) SSO for EMC Documentum Rest ServicesEMC This white paper provides an overview of integrating Central Authentication Service (CAS) Single Sign-On with EMC Documentum REST Services, including exploring the CAS architecture and authentication flows, deployment recommendations, and troubleshooting tips for this integration. CAS is an open source single sign-on solution that allows users to authenticate once to access multiple web services, while Documentum REST Services is a multi-layer system that uses CAS proxy authentication to achieve single sign-on across its components. The paper provides details on configuring both the CAS server and Documentum components to enable CAS SSO for the REST API.
Strong Authentication in Web Applications: State of the Art 2011



Strong Authentication in Web Applications: State of the Art 2011Sylvain Maret Sylvain’s talk will focus on risk based authentication, biometry, OTP for smartphones, PKIs, Mobile-OTP, OATH-HOTP, TOTP and the open-source approach to this subjet.
PHP Demo with multiotp class.
3 reasons your business can't ignore Two-Factor Authentication



3 reasons your business can't ignore Two-Factor AuthenticationFortytwo Login security breaches have become commonplace in recent years. We hear about phishing attacks, stolen passwords and malware that collects all of our keystrokes. Once these data breaches would have instigated a call to use stronger and more complex passwords, however research has shown that two-thirds of all breaches are specifically the result of weak or stolen passwords. The one-time reliable password has become the weakest link.
This is where two-factor authentication (2FA) steps in.
Two-factor authentication is a simple yet an extremely powerful way of increasing security via the user logon sequence by simply adding a second factor of authentication to the standard username and password.
Google Authenticator, possible attacks and prevention



Google Authenticator, possible attacks and preventionBoštjan Cigan This presentation describes Google's Time Based One Time Password authentication scheme and its practical implementation Google Authenticator. It also presents possible attacks and their prevention.
"2Fac: Facebook's internal multi-factor authentication". Tim Tickel, Chad Gre...



"2Fac: Facebook's internal multi-factor authentication". Tim Tickel, Chad Gre...Yandex An in-depth look at Facebook's easy-to-use internal multi-factor authentication deployment. We will discuss our motivations, how our solution works, technical and security trade-offs, deployment problems, and outstanding issues.
Bio Chad Greene:
A security manager at Facebook, Chad Greene focuses on security engineering, intrusion detection and incident response at scale. Protecting user data for over 1 billion active users of the social network, his teams are responsible for building creative security solutions that balance rapid growth and innovation with a strong security posture. Prior to Facebook, for more than seven years Chad worked at eBay, where he worked on solving product security and security operations challenges. Chad holds a Bachelor's degree in Management Information Systems from The University of Notre Dame.
2013.devcon3 liferay and google authenticator integration rafik_harabi



2013.devcon3 liferay and google authenticator integration rafik_harabiRafik HARABI Today, with expand of the web portal, many customers are seeking for more secure solutions to access to their web portal outside of their own networks.
For Liferay portal customers, this request has been increased due to the number of portal deployed on Cloud and the increase of deployment of Liferay portal for internet sites (B2C …).
One of the proposed solutions is the use of Multi-factor authentication mechanism.
Google Authenticator is one of the lead open source dual factor authentication systems.
In this presentation, we will explain the integration technical solution of Liferay and Google Authenticator in order to deliver a two-factor authentication system. The presentation will be followed by a live demo.
Two factor authentication-in_your_network_e_guide



Two factor authentication-in_your_network_e_guideNick Owen This document provides instructions for adding two-factor authentication to a corporate network using WiKID as the authentication server. It discusses configuring Radius clients like VPNs from Cisco and Juniper to communicate with an Active Directory server through a Radius server. The Active Directory server would authorize users while the WiKID server authenticates users with two-factor authentication. It provides step-by-step examples of configuring Network Policy Server and WiKID to enable two-factor authentication for remote access to a corporate network.
Two Factor Authentication and You



Two Factor Authentication and YouChris Stone Everyone has at least one password, but that's not enough anymore. When is that not enough? Passwords get out of your hands all the time. You know your password, but what about using something you have in addition to what you know. Let's look at how you can leverage your mobile device for added security, and implement it in your projects. This talk will cover how two factor auth works, how to use it and the ins and outs of rolling your own solution using Time-based One-time Password (TOTP) (and the Google Authenticator app) or a third party service and the pitfalls of both. AWS, Mailchimp, Dropbox and Facebook integrate two factor authentication and you can too! There's no reason not to use it!
Seminar-Two Factor Authentication



Seminar-Two Factor AuthenticationDilip Kr. Jangir This document discusses two-factor authentication and its benefits. It describes two-factor authentication as requiring two different types of evidence, such as something you know (a password) and something you have (a token or mobile device). Hard tokens generate one-time passwords on a physical device while mobile tokens use a mobile app to generate passwords. Using a mobile token is more flexible and cheaper than hard tokens but still vulnerable to active attacks. Sending a one-time password via SMS and requiring the user to enter a code for transactions adds an extra layer of security against man-in-the-middle attacks compared to other methods. The document recommends hashing passwords before sending and mutual authentication between clients and servers to improve security.
Simple Two Factor Authentication



Simple Two Factor AuthenticationJohn Congdon My presentation at SDPHP went well. I definitely could improve on this presentation.
I missed the mark on the general workflow. How the customers and developers are impacted.
I made assumptions that I shouldn't have, such as everyone already knew what Two Factor Authentication (2fa) was.
Securing Your Salesforce Deployment with Two Factor Authentication



Securing Your Salesforce Deployment with Two Factor AuthenticationSalesforce Developers Hackers are seemingly everywhere and we can't escape news droning on about breached companies and lost data. Two Factor Authentication is a critical security process to ensure that only your users gain access to the appropriate information. Join us as we not only walk through why deploying stronger authentication is important, but also demonstrate some of the new technologies and features in the Salesforce Platform that you can deploy today. Finally, get a glimpse of the future as we demonstrate the latest Salesforce Authenticator.
Two-factor Authentication



Two-factor AuthenticationPortalGuard dba PistolStar, Inc. This document describes PortalGuard's two-factor authentication solution. It provides tokenless two-factor authentication through one-time passwords delivered via SMS, email, printer, or transparent token. The summary describes how it works by enrolling user mobile devices, validating credentials through the PortalGuard server, and delivering one-time passwords to grant access to applications.
2 factor authentication 3 [compatibility mode]![2 factor authentication 3 [compatibility mode]](https://cdn.slidesharecdn.com/ss_thumbnails/2factorauthentication3compatibilitymode-130513032050-phpapp01-thumbnail.jpg?width=560&fit=bounds)
![2 factor authentication 3 [compatibility mode]](https://cdn.slidesharecdn.com/ss_thumbnails/2factorauthentication3compatibilitymode-130513032050-phpapp01-thumbnail.jpg?width=560&fit=bounds)
![2 factor authentication 3 [compatibility mode]](https://cdn.slidesharecdn.com/ss_thumbnails/2factorauthentication3compatibilitymode-130513032050-phpapp01-thumbnail.jpg?width=560&fit=bounds)
![2 factor authentication 3 [compatibility mode]](https://cdn.slidesharecdn.com/ss_thumbnails/2factorauthentication3compatibilitymode-130513032050-phpapp01-thumbnail.jpg?width=560&fit=bounds)
2 factor authentication 3 [compatibility mode]Hai Nguyen The document discusses two-factor authentication solutions for the City of High Point, including RSA Authentication Manager for centralized management of multiple authentication methods like hard tokens, soft tokens, certificates, PINs, and biometrics. It describes how the city uses an RSA appliance hosting the main database and managing authentication, with disaster recovery provided by replicating the database to a second appliance. The city also uses Checkpoint and Netmotion with RSA SecurID tokens for two-factor authentication of remote and mobile connections to its network.
Combat the Latest Two-Factor Authentication Evasion Techniques



Combat the Latest Two-Factor Authentication Evasion TechniquesIBM Security In the wake of 2005 FFIEC regulation calling for stronger security methods, financial institutions have adopted two-factor authentication (2FA) as a means to mitigate online fraud.
Historically 2FA measures such as security questions, one time passwords, physical tokens, SMS authentications and USB tokens have been able to effectively stop fraud attacks. However, in the fast paced arms race that is the war against financial crime, cybercriminals are starting to take the upper hand by developing increasingly sophisticated techniques that bypass 2FA.
In this presentation, Ori Bach, Senior Security Strategist at IBM Trusteer demonstrates several of the 2FA beating techniques and explains how cybercriminals:
- Highjack authenticated banking sessions by directly taking over victims computers
- Make use fake overlay messages to trick victims to surrender their tokens
- Beat one time passwords sent to mobile devices
- Purchase fraud tool-kits to bypass 2FA
View the on-demand recording: https://attendee.gotowebinar.com/recording/6080887905844019714
Ad
Similar to SSO using CAS + two-factor authentication (PyGrunn 2014 talk) (20)
Two-factor Authentication



Two-factor AuthenticationPortalGuard dba PistolStar, Inc. PortalGuard’s Flexible Two-factor Authentication options are designed as strong authentication methods for securing web applications. PortalGuard leverages a one-time password (OTP) as a factor to further prove a user's identity. The OTP can be delivered via SMS, email, printer, and transparent token. Configurable by user, group or application this is a cost effective approach to stronger authentication security.
Tutorial: http://pg.portalguard.com/flexible_two-factor_tutorial
Authentication without Authentication - AppSec California



Authentication without Authentication - AppSec CaliforniaSoluto Authentication is important, but how do you authenticate when user interaction is not an option? For example, an IoT app without a user interface. We need to authenticate the app ― without any predefined credentials. But how?
SSO IN/With Drupal and Identitiy Management



SSO IN/With Drupal and Identitiy ManagementManish Harsh This presentation is a result of research and evaluation for SSO and IDM majorly focused to Drupal CMS.
Enterprises, corporations and companies with multiple web properties are struggling to provide a better user experience and offer a single "corporate ID" and "Password" as the key for all.
This single ID should be used across all the properties and corporations should still be able to manage the access level and permission of the respective user based on the grants assigned to this ID in each web property.
How to build Simple yet powerful API.pptx



How to build Simple yet powerful API.pptxChanna Ly How to build simple yet powerful API from novice to professional. API for beginners, API for gurus, Enterprise level API, REST API, JWT API, Deep dive.
Serverless Meetup - Getting started with AWS Cognito [Jul 2020]![Serverless Meetup - Getting started with AWS Cognito [Jul 2020]](https://cdn.slidesharecdn.com/ss_thumbnails/serverlessmeetup-gettingstartedwithawscognitojul2020-240904113422-815bf18a-thumbnail.jpg?width=560&fit=bounds)
![Serverless Meetup - Getting started with AWS Cognito [Jul 2020]](https://cdn.slidesharecdn.com/ss_thumbnails/serverlessmeetup-gettingstartedwithawscognitojul2020-240904113422-815bf18a-thumbnail.jpg?width=560&fit=bounds)
![Serverless Meetup - Getting started with AWS Cognito [Jul 2020]](https://cdn.slidesharecdn.com/ss_thumbnails/serverlessmeetup-gettingstartedwithawscognitojul2020-240904113422-815bf18a-thumbnail.jpg?width=560&fit=bounds)
![Serverless Meetup - Getting started with AWS Cognito [Jul 2020]](https://cdn.slidesharecdn.com/ss_thumbnails/serverlessmeetup-gettingstartedwithawscognitojul2020-240904113422-815bf18a-thumbnail.jpg?width=560&fit=bounds)
Serverless Meetup - Getting started with AWS Cognito [Jul 2020]Dhaval Nagar This presentation is Part 1 of the Serverless Application Authentication Series.
Amazon Cognito is a fully managed service that simplifies the process of adding authentication, authorization, and user management to your web and mobile applications. It allows developers to quickly integrate user sign-up, sign-in, and access control without having to build these features from scratch.
Usability vs. Security: Find the Right Balance in Mobile Apps



Usability vs. Security: Find the Right Balance in Mobile AppsJosiah Renaudin Successful mobile apps have two key features: a great user experience and the ability to protect users’ data. Balancing user experience and security—a key aspect of product design and engineering—requires a multidisciplinary approach. According to Levent Gurses, a well-balanced app is designed through a series of informed decisions, meaningful compromises, and research that supports core user behaviors. Based on lessons learned from designing winning mobile apps and securing front- and back-end infrastructure, Levent shares his method for scientifically discovering the most critical aspects of an app and creating user-centric, secure mobile experiences. Join Levent for an interactive session on how to create both the best possible user experience and an app that keeps its users’ data safe and secure. He demonstrates core concepts by borrowing from proven UX design patterns and discovering what drives engagement and data protection. Levent uses the latest science in user behavioral research and cyber analytics to discover pragmatic ways to create engaging and secure mobile apps.
validation of user credentials in social network by using Django backend aut...



validation of user credentials in social network by using Django backend aut...izzatisholehah 1) The document discusses validation of user credentials in social networks using Django backend authentication. It aims to configure a Django framework platform for authentication, integrate token-based authentication, and test the backend authentication in a social network.
2) The problems with traditional username and password authentication are that it increases server overhead with many users authenticating and credentials can be accessed via HTTP requests. Token-based authentication is proposed to address these issues.
3) The proof of concept implements Django authentication with token-based authentication by installing Django/DRF, configuring the backend server, integrating token authentication, and connecting the backend to an API for social network credential validation.
API Security In Cloud Native Era



API Security In Cloud Native EraWSO2 The cloud is rapidly becoming the de-facto standard for deploying enterprise applications. Microservices are at the core of building cloud-native applications due to its proven advantages such as granularity, cloud-native deployment, and scalability. With the exponential growth of the consumer base of these service offerings, enforcing microservice/API security has become one of the biggest challenges to overcome.
In this deck, we discuss:
- The need for API/Microservices Security
- The importance of delegating security enforcement to an API Gateway
- API Authentication and Authorization methodologies
- OAuth2 - The de-facto standard of API Authentication
- Protection against cyber attacks and anomalies
- Security aspects to consider when designing Single Page Applications (SPAs)
Watch the webinar on-demand here - https://wso2.com/library/webinars/2019/11/api-security-in-a-cloud-native-era/
Integration_Architect_-_Study_Group_Part_1.pptx



Integration_Architect_-_Study_Group_Part_1.pptxkathleenwaterworth Session #1 of 5- Integration Architect Certification Prep Study Group
kicking your enterprise security up a notch with adaptive authentication sa...



kicking your enterprise security up a notch with adaptive authentication sa...Sagara Gunathunga This document discusses how adaptive authentication can improve security over traditional passwords and multi-factor authentication. It notes that passwords are often reused or weak, leading to many breaches. While multi-factor authentication adds security, it has low adoption rates due to usability issues. The document proposes that authentication should be dynamic, responsive to context like location, device and application risk level. It outlines how the WSO2 Identity Server supports adaptive authentication through scripting policies, connectivity to machine learning models, and a wide range of authentication connectors. Adaptive authentication can select steps dynamically based on the request, user attributes and behaviors, or a risk score to improve security and usability.
International Journal of Engineering Inventions (IJEI)



International Journal of Engineering Inventions (IJEI)International Journal of Engineering Inventions www.ijeijournal.com This document analyzes single sign-on (SSO) authentication for web applications, specifically using Google as a service provider. It discusses problems with traditional username and password authentication across multiple systems and how SSO solves this by allowing a user to log in once to access all authorized resources. The document then provides details on how SSO authentication works for Google applications using Security Assertion Markup Language (SAML). It describes the steps a user takes to log into a Google application through a partner-operated SSO service, including SAML requests and responses being passed between the partner SSO, user's browser, and Google.
Mobile Enterprise Application Platform



Mobile Enterprise Application PlatformNugroho Gito mobile enterprise application, mobile application development, mobile enterprise, hybrid mobile, mobile security, reverse engineer, obfuscation, ibm, mobilefirst platform, bluemix, api management, mobile backend as a service
Cartes Asia Dem 2010 V2



Cartes Asia Dem 2010 V2Donald Malloy The document summarizes the Open Authentication initiative (OATH), which aims to drive adoption of open strong authentication standards. OATH has created standardized authentication algorithms like HOTP and works with members to promote interoperability. Its reference architecture provides guidance for integrating strong authentication into applications while balancing security, usability and choice. OATH also works on credential provisioning standards and certification programs to further authentication adoption.
[WSO2Con EU 2018] Kicking Your Enterprise Security Up a Notch With Adaptive A...![[WSO2Con EU 2018] Kicking Your Enterprise Security Up a Notch With Adaptive A...](https://cdn.slidesharecdn.com/ss_thumbnails/4-181113094708-thumbnail.jpg?width=560&fit=bounds)
![[WSO2Con EU 2018] Kicking Your Enterprise Security Up a Notch With Adaptive A...](https://cdn.slidesharecdn.com/ss_thumbnails/4-181113094708-thumbnail.jpg?width=560&fit=bounds)
![[WSO2Con EU 2018] Kicking Your Enterprise Security Up a Notch With Adaptive A...](https://cdn.slidesharecdn.com/ss_thumbnails/4-181113094708-thumbnail.jpg?width=560&fit=bounds)
![[WSO2Con EU 2018] Kicking Your Enterprise Security Up a Notch With Adaptive A...](https://cdn.slidesharecdn.com/ss_thumbnails/4-181113094708-thumbnail.jpg?width=560&fit=bounds)
[WSO2Con EU 2018] Kicking Your Enterprise Security Up a Notch With Adaptive A...WSO2 Adaptive authentication offers a good balance between security and usability. This presentation discusses the benefits of adaptive authentication and how WSO2 Identity Server can support any adaptive or risk-based authentication use case.
JDD2015: Security in the era of modern applications and services - Bolesław D...



JDD2015: Security in the era of modern applications and services - Bolesław D...PROIDEA This document discusses security challenges with modern applications and services and provides an overview of common standards and approaches. It outlines issues with traditional password-based authentication and session management in today's environment of mobile apps, microservices, and client-side applications. The document then introduces token-based security standards like SAML, JWT, OAuth2, and OpenID Connect, explaining how they address these issues through tokenization, delegation, and flexible authentication. It recommends relying on existing solutions like Keycloak that implement these standards to simplify security implementation and avoid potential vulnerabilities.
ISS SA le presenta IdentityGuard de Entrust



ISS SA le presenta IdentityGuard de EntrustInformation Security Services SA Las organizaciones necesitan evolucionar más allá del nombre de usuario y contraseña básico y asegurar las transacciones en línea con un abanico de opciones de autenticación segura.
[APIdays INTERFACE 2021] Authentication and Authorization Best Practices for ...![[APIdays INTERFACE 2021] Authentication and Authorization Best Practices for ...](https://cdn.slidesharecdn.com/ss_thumbnails/ishara-apidays-interface-june2021-210710185027-thumbnail.jpg?width=560&fit=bounds)
![[APIdays INTERFACE 2021] Authentication and Authorization Best Practices for ...](https://cdn.slidesharecdn.com/ss_thumbnails/ishara-apidays-interface-june2021-210710185027-thumbnail.jpg?width=560&fit=bounds)
![[APIdays INTERFACE 2021] Authentication and Authorization Best Practices for ...](https://cdn.slidesharecdn.com/ss_thumbnails/ishara-apidays-interface-june2021-210710185027-thumbnail.jpg?width=560&fit=bounds)
![[APIdays INTERFACE 2021] Authentication and Authorization Best Practices for ...](https://cdn.slidesharecdn.com/ss_thumbnails/ishara-apidays-interface-june2021-210710185027-thumbnail.jpg?width=560&fit=bounds)
[APIdays INTERFACE 2021] Authentication and Authorization Best Practices for ...WSO2 Modern enterprises are increasingly adopting APIs, exceeding all predictions. With more businesses investing in microservices and the increased consumption of cloud APIs, you need to secure beyond just a handful of well-known APIs. You will need to secure a higher number of internal and external endpoints.
Security itself is a broad area and authentication and authorization is a key element in API security. Vendors implement a number of seemingly similar standards and patterns, making it very difficult for consumers to settle on the best option for securing APIs. The sheer number of options can be very confusing. At the same time, technology stack and industry practices are under a rapid transformation, browsers are enforcing different restrictions, new privacy regulations are in place, and more. That makes the authentication and authorization best practices you relied on a few years ago obsolete now.
These slides we will discuss:
- What is new and what is old in OAuth 2.0
- Mitigate security exploits by understanding the OAuth 2.0 threat landscape
- Pick security standards and protocols to match business needs
- Federated identities to expand business APIs beyond the corporate firewall
- User strong authentication and authorization for API access
- Adaptive and risk-based access control for API
Distributed Authorization with Open Policy Agent.pdf



Distributed Authorization with Open Policy Agent.pdfNordic APIs A talk given by Anders Eknert, Developer Advocate at Styra, at the 2023 Platform Summit in Stockholm.
What is Full Stack with Django and how to start learning It.docx



What is Full Stack with Django and how to start learning It.docxTechnogeeks
Full Stack with Django combines backend development using Django with frontend technologies like HTML, CSS, and JavaScript. Beginners should focus on Python basics, delve into web development fundamentals, and explore Django specifics for hands-on learning and project building.
Making User Authentication More Usable



Making User Authentication More UsableJim Fenton A recent revision to the US Government’s authentication guideline, NIST SP 800-63B "Authentication and Lifecycle Management", puts a greater emphasis on the usability of authentication in its recommendations. This talk will discuss the ways in which it attempts to relieve the users’ burden and shift more responsibility to the services themselves, hopefully improving overall security in the process.
Presentation to BayCHI, December 12, 2017
International Journal of Engineering Inventions (IJEI)



International Journal of Engineering Inventions (IJEI)International Journal of Engineering Inventions www.ijeijournal.com
Ad
Recently uploaded (20)
Complete Guide to Advanced Logistics Management Software in Riyadh.pdf



Complete Guide to Advanced Logistics Management Software in Riyadh.pdfSoftware Company Explore the benefits and features of advanced logistics management software for businesses in Riyadh. This guide delves into the latest technologies, from real-time tracking and route optimization to warehouse management and inventory control, helping businesses streamline their logistics operations and reduce costs. Learn how implementing the right software solution can enhance efficiency, improve customer satisfaction, and provide a competitive edge in the growing logistics sector of Riyadh.
Noah Loul Shares 5 Steps to Implement AI Agents for Maximum Business Efficien...



Noah Loul Shares 5 Steps to Implement AI Agents for Maximum Business Efficien...Noah Loul Artificial intelligence is changing how businesses operate. Companies are using AI agents to automate tasks, reduce time spent on repetitive work, and focus more on high-value activities. Noah Loul, an AI strategist and entrepreneur, has helped dozens of companies streamline their operations using smart automation. He believes AI agents aren't just tools—they're workers that take on repeatable tasks so your human team can focus on what matters. If you want to reduce time waste and increase output, AI agents are the next move.
Increasing Retail Store Efficiency How can Planograms Save Time and Money.pptx



Increasing Retail Store Efficiency How can Planograms Save Time and Money.pptxAnoop Ashok In today's fast-paced retail environment, efficiency is key. Every minute counts, and every penny matters. One tool that can significantly boost your store's efficiency is a well-executed planogram. These visual merchandising blueprints not only enhance store layouts but also save time and money in the process.
#StandardsGoals for 2025: Standards & certification roundup - Tech Forum 2025



#StandardsGoals for 2025: Standards & certification roundup - Tech Forum 2025BookNet Canada Book industry standards are evolving rapidly. In the first part of this session, we’ll share an overview of key developments from 2024 and the early months of 2025. Then, BookNet’s resident standards expert, Tom Richardson, and CEO, Lauren Stewart, have a forward-looking conversation about what’s next.
Link to recording, transcript, and accompanying resource: https://bnctechforum.ca/sessions/standardsgoals-for-2025-standards-certification-roundup/
Presented by BookNet Canada on May 6, 2025 with support from the Department of Canadian Heritage.
AI Changes Everything – Talk at Cardiff Metropolitan University, 29th April 2...



AI Changes Everything – Talk at Cardiff Metropolitan University, 29th April 2...Alan Dix Talk at the final event of Data Fusion Dynamics: A Collaborative UK-Saudi Initiative in Cybersecurity and Artificial Intelligence funded by the British Council UK-Saudi Challenge Fund 2024, Cardiff Metropolitan University, 29th April 2025
https://alandix.com/academic/talks/CMet2025-AI-Changes-Everything/
Is AI just another technology, or does it fundamentally change the way we live and think?
Every technology has a direct impact with micro-ethical consequences, some good, some bad. However more profound are the ways in which some technologies reshape the very fabric of society with macro-ethical impacts. The invention of the stirrup revolutionised mounted combat, but as a side effect gave rise to the feudal system, which still shapes politics today. The internal combustion engine offers personal freedom and creates pollution, but has also transformed the nature of urban planning and international trade. When we look at AI the micro-ethical issues, such as bias, are most obvious, but the macro-ethical challenges may be greater.
At a micro-ethical level AI has the potential to deepen social, ethnic and gender bias, issues I have warned about since the early 1990s! It is also being used increasingly on the battlefield. However, it also offers amazing opportunities in health and educations, as the recent Nobel prizes for the developers of AlphaFold illustrate. More radically, the need to encode ethics acts as a mirror to surface essential ethical problems and conflicts.
At the macro-ethical level, by the early 2000s digital technology had already begun to undermine sovereignty (e.g. gambling), market economics (through network effects and emergent monopolies), and the very meaning of money. Modern AI is the child of big data, big computation and ultimately big business, intensifying the inherent tendency of digital technology to concentrate power. AI is already unravelling the fundamentals of the social, political and economic world around us, but this is a world that needs radical reimagining to overcome the global environmental and human challenges that confront us. Our challenge is whether to let the threads fall as they may, or to use them to weave a better future.
HCL Nomad Web – Best Practices and Managing Multiuser Environments



HCL Nomad Web – Best Practices and Managing Multiuser Environmentspanagenda Webinar Recording: https://www.panagenda.com/webinars/hcl-nomad-web-best-practices-and-managing-multiuser-environments/
HCL Nomad Web is heralded as the next generation of the HCL Notes client, offering numerous advantages such as eliminating the need for packaging, distribution, and installation. Nomad Web client upgrades will be installed “automatically” in the background. This significantly reduces the administrative footprint compared to traditional HCL Notes clients. However, troubleshooting issues in Nomad Web present unique challenges compared to the Notes client.
Join Christoph and Marc as they demonstrate how to simplify the troubleshooting process in HCL Nomad Web, ensuring a smoother and more efficient user experience.
In this webinar, we will explore effective strategies for diagnosing and resolving common problems in HCL Nomad Web, including
- Accessing the console
- Locating and interpreting log files
- Accessing the data folder within the browser’s cache (using OPFS)
- Understand the difference between single- and multi-user scenarios
- Utilizing Client Clocking
Into The Box Conference Keynote Day 1 (ITB2025)



Into The Box Conference Keynote Day 1 (ITB2025)Ortus Solutions, Corp This is the keynote of the Into the Box conference, highlighting the release of the BoxLang JVM language, its key enhancements, and its vision for the future.
Quantum Computing Quick Research Guide by Arthur Morgan



Quantum Computing Quick Research Guide by Arthur MorganArthur Morgan This is a Quick Research Guide (QRG).
QRGs include the following:
- A brief, high-level overview of the QRG topic.
- A milestone timeline for the QRG topic.
- Links to various free online resource materials to provide a deeper dive into the QRG topic.
- Conclusion and a recommendation for at least two books available in the SJPL system on the QRG topic.
QRGs planned for the series:
- Artificial Intelligence QRG
- Quantum Computing QRG
- Big Data Analytics QRG
- Spacecraft Guidance, Navigation & Control QRG (coming 2026)
- UK Home Computing & The Birth of ARM QRG (coming 2027)
Any questions or comments?
- Please contact Arthur Morgan at [email protected].
100% human made.
Mobile App Development Company in Saudi Arabia



Mobile App Development Company in Saudi ArabiaSteve Jonas EmizenTech is a globally recognized software development company, proudly serving businesses since 2013. With over 11+ years of industry experience and a team of 200+ skilled professionals, we have successfully delivered 1200+ projects across various sectors. As a leading Mobile App Development Company In Saudi Arabia we offer end-to-end solutions for iOS, Android, and cross-platform applications. Our apps are known for their user-friendly interfaces, scalability, high performance, and strong security features. We tailor each mobile application to meet the unique needs of different industries, ensuring a seamless user experience. EmizenTech is committed to turning your vision into a powerful digital product that drives growth, innovation, and long-term success in the competitive mobile landscape of Saudi Arabia.
Designing Low-Latency Systems with Rust and ScyllaDB: An Architectural Deep Dive



Designing Low-Latency Systems with Rust and ScyllaDB: An Architectural Deep DiveScyllaDB Want to learn practical tips for designing systems that can scale efficiently without compromising speed?
Join us for a workshop where we’ll address these challenges head-on and explore how to architect low-latency systems using Rust. During this free interactive workshop oriented for developers, engineers, and architects, we’ll cover how Rust’s unique language features and the Tokio async runtime enable high-performance application development.
As you explore key principles of designing low-latency systems with Rust, you will learn how to:
- Create and compile a real-world app with Rust
- Connect the application to ScyllaDB (NoSQL data store)
- Negotiate tradeoffs related to data modeling and querying
- Manage and monitor the database for consistently low latencies
tecnologias de las primeras civilizaciones.pdf



tecnologias de las primeras civilizaciones.pdffjgm517 descaripcion detallada del avance de las tecnologias en mesopotamia, egipto, roma y grecia.
Generative Artificial Intelligence (GenAI) in Business



Generative Artificial Intelligence (GenAI) in BusinessDr. Tathagat Varma My talk for the Indian School of Business (ISB) Emerging Leaders Program Cohort 9. In this talk, I discussed key issues around adoption of GenAI in business - benefits, opportunities and limitations. I also discussed how my research on Theory of Cognitive Chasms helps address some of these issues
IEDM 2024 Tutorial2_Advances in CMOS Technologies and Future Directions for C...



IEDM 2024 Tutorial2_Advances in CMOS Technologies and Future Directions for C...organizerofv IEDM 2024 Tutorial2
Linux Support for SMARC: How Toradex Empowers Embedded Developers



Linux Support for SMARC: How Toradex Empowers Embedded DevelopersToradex Toradex brings robust Linux support to SMARC (Smart Mobility Architecture), ensuring high performance and long-term reliability for embedded applications. Here’s how:
• Optimized Torizon OS & Yocto Support – Toradex provides Torizon OS, a Debian-based easy-to-use platform, and Yocto BSPs for customized Linux images on SMARC modules.
• Seamless Integration with i.MX 8M Plus and i.MX 95 – Toradex SMARC solutions leverage NXP’s i.MX 8 M Plus and i.MX 95 SoCs, delivering power efficiency and AI-ready performance.
• Secure and Reliable – With Secure Boot, over-the-air (OTA) updates, and LTS kernel support, Toradex ensures industrial-grade security and longevity.
• Containerized Workflows for AI & IoT – Support for Docker, ROS, and real-time Linux enables scalable AI, ML, and IoT applications.
• Strong Ecosystem & Developer Support – Toradex offers comprehensive documentation, developer tools, and dedicated support, accelerating time-to-market.
With Toradex’s Linux support for SMARC, developers get a scalable, secure, and high-performance solution for industrial, medical, and AI-driven applications.
Do you have a specific project or application in mind where you're considering SMARC? We can help with Free Compatibility Check and help you with quick time-to-market
For more information: https://www.toradex.com/computer-on-modules/smarc-arm-family
Manifest Pre-Seed Update | A Humanoid OEM Deeptech In France



Manifest Pre-Seed Update | A Humanoid OEM Deeptech In Francechb3 The latest updates on Manifest's pre-seed stage progress.
Cybersecurity Identity and Access Solutions using Azure AD



Cybersecurity Identity and Access Solutions using Azure ADVICTOR MAESTRE RAMIREZ Cybersecurity Identity and Access Solutions using Azure AD
Enhancing ICU Intelligence: How Our Functional Testing Enabled a Healthcare I...



Enhancing ICU Intelligence: How Our Functional Testing Enabled a Healthcare I...Impelsys Inc. Impelsys provided a robust testing solution, leveraging a risk-based and requirement-mapped approach to validate ICU Connect and CritiXpert. A well-defined test suite was developed to assess data communication, clinical data collection, transformation, and visualization across integrated devices.
What is Model Context Protocol(MCP) - The new technology for communication bw...



What is Model Context Protocol(MCP) - The new technology for communication bw...Vishnu Singh Chundawat The MCP (Model Context Protocol) is a framework designed to manage context and interaction within complex systems. This SlideShare presentation will provide a detailed overview of the MCP Model, its applications, and how it plays a crucial role in improving communication and decision-making in distributed systems. We will explore the key concepts behind the protocol, including the importance of context, data management, and how this model enhances system adaptability and responsiveness. Ideal for software developers, system architects, and IT professionals, this presentation will offer valuable insights into how the MCP Model can streamline workflows, improve efficiency, and create more intuitive systems for a wide range of use cases.
What is Model Context Protocol(MCP) - The new technology for communication bw...



What is Model Context Protocol(MCP) - The new technology for communication bw...Vishnu Singh Chundawat
SSO using CAS + two-factor authentication (PyGrunn 2014 talk)
- 1. Modern authentication techniques in Python web applications Artur Barseghyan Goldmund, Wyldebeast & Wunderliebe http://www.goldmund-wyldebeast-wunderliebe.nl/ [email protected] https://github.com/barseghyanartur
- 2. Part 1 Single Sign-on using Central Authentication Service
- 3. A single framework/application User base Framework/application Authentication system Other importants parts not related to this talk
- 4. Typical framework/application authentication flow User requests content requiring authentication User gets the content requested Is user authenticated? Authenticate user User provides credentials (login page) Are credentials correct? Yes No Yes No
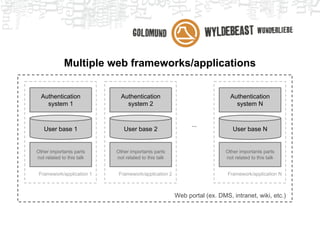
- 5. Multiple web frameworks/applications User base 1 Framework/application 1 Authentication system 1 Other importants parts not related to this talk User base 2 Framework/application 2 Authentication system 2 Other importants parts not related to this talk User base N Framework/application N Authentication system N Other importants parts not related to this talk ... Web portal (ex. DMS, intranet, wiki, etc.)
- 6. Without Single Sign-on... ● Use a single framework/application and write lots of apps OR ● Use multiple frameworks/applications and: ○ Hack their authentication systems OR ○ Expect users to login into each of them OR ○ Make them communicate via customly built API ● More (bad) ideas?
- 7. With Single Sign-on... ● User logs in once and gains access to all systems without being prompted to log in again.
- 8. (JaSig) CAS Enterprise Single Sign-on solution ● Open source ● Well documented ● Scalable ● Modular and highly pluggable (MySQL, PostgreSQL, Oracle, LDAP, SPINEGO, RADIUS, etc.) ● Lots of ready-to-use clients and plugins
- 9. (JaSig) CAS CAS involves at least three parties: ● A client web browser ● Web application requesting authentication ● The CAS server It also optionally may involve: ● Back-end service, such as a database server
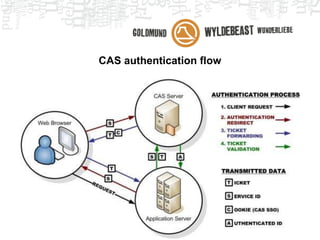
- 11. CAS authentication schema User requests content which requires authentication User is asked to provide credentials (login page) Create SSO token and redirect User gets the content requested No Yes No Yes Is user authenticated into app? No Yes Authenticate user (CAS) CAS server Authenticate user (locally) Are credentials correct? Is user authenticated into CAS? CAS client (web application)
- 12. Pros of CAS Pros ● Centralised authentication for all frameworks/applications. ● Actively maintained and developed. Large community. ● Modular and highly pluggable (MySQL, PostgreSQL, Oracle, Active Directory, LDAP, SPINEGO, RADIUS, etc.). ● Lots of ready-to-use packages for many frameworks/applications. ● Less passwords to retype, remember and recover. ● More of your own code is reusable. ● Happier end-users. ● REST API.
- 13. Cons of CAS Cons ● SSO availability becomes critical. ● SSO security becomes critical.
- 14. Our use case Dashboard app ● Django Server A CAS server Server C User base ● Active Directory Server D VPN ● Apache ● Tomcat ● Debian ● Java ● CAS ● OpenVPN ● AJP ● Python ● Django ● Plone More to come Server X DMS ● Plone Server B
- 15. Conclusion
- 16. CAS alternatives 1 / n JOSSO http://www.josso.org OpenAM (formerly known as OpenSSO) http://openam.forgerock.org Pubcookie http://www.pubcookie.org CoSign http://weblogin.org
- 17. Linkodrome 1 / n Software packages JaSig CAS http://www.jasig.org/cas Django CAS client https://github.com/Goldmund-Wyldebeast-Wunderliebe/django-cas-consumer Plone CAS client https://github.com/collective/anz.casclient Detailed installation instructions http://bit.ly/1uuk2BS
- 18. Part 2 Two-step verification (Two-factor authentication)
- 19. Standard authentication flow User requests content requiring authentication User gets the content requested Is user authenticated? Authenticate user User provides credentials (login page) Are credentials correct? Yes Yes No No
- 20. ● Knowledge factor ("something only the user knows"): a password or a PIN. ● Possession factor ("something only the user has"): ATM card, smart card, mobile phone. ● Inherence factor ("something only the user is"): Fingerprint or voiceprint. Standard authentication factors
- 21. Common advises on remembering many passwords ● Use complex passwords and have them saved in password managers. ● Use complex passwords, write them on paper and carry them in your wallet. Passwords aren’t enough!
- 22. Two-factor authentication ● Knowledge factor ("something only the user knows"): a password or a PIN. ● Possession factor ("something only the user has"): ATM card, smart card, mobile phone. ● Inherence factor ("something only the user is"): Fingerprint or voiceprint.
- 23. Standard authentication flow User requests content requiring authentication User provides credentials No Yes Is user authenticated ? Authenticate user Yes No Are credentials correct? User gets the content requested
- 24. Two-factor authentication flow User requests content requiring authentication User provides credentials No Yes User provides second factor token Is token correct ? Yes No Second factor Is user authenticated ? Authenticate user Yes No Are credentials correct? User gets the content requested
- 25. (Common) solutions ● SMS authentication ● Google Authenticator (mobile app) ● Hardware token generators
- 28. Our use cases ● collective.googleauthenticator (uses Google Authenticator app) ● collective.smsauthenticator (login codes sent by SMS)
- 31. Authenticate
- 32. Verify
- 33. Conclusion
- 34. Alternatives ● Risk-based authentication (based on behavioral biometrics, keystroke dynamics, etc.) ● Strong authentication ● Reliance authentication
- 35. Linkodrome Plone ● collective.googleauthenticator (two-factor authentication using Google Authenticator app) https://pypi.python.org/pypi/collective.googleauthenticator ● collective.smsauthenticator (two-factor authentication using login codes sent by SMS) https://pypi.python.org/pypi/collective.smsauthenticator Django ● django-two-factor-auth (two-factor authentication using Google Authenticator or login codes sent by SMS) https://pypi.python.org/pypi/django-two-factor-auth ● django-otp (pluggable framework for adding two-factor authentication using OTP.) https://pypi.python.org/pypi/django-otp
- 36. Questions?
- 37. Thank you! Artur Barseghyan Goldmund, Wyldebeast & Wunderliebe [email protected] https://github.com/barseghyanartur



