T com presentation (error correcting code)
Download as PPTX, PDF5 likes1,412 views
This document discusses error correcting codes, which are used to detect and correct errors that occur during data transmission. It covers different types of block codes like Hamming codes and Reed-Muller codes. Hamming codes can detect and correct single bit errors by adding redundant bits. Reed-Muller codes use a generator matrix to encode data and can detect and correct single bit errors through majority decoding. The document provides examples of encoding and decoding data using Hamming codes and Reed-Muller codes to demonstrate how they can detect and correct errors.
1 of 22
Downloaded 90 times



















Ad
Recommended
Mov instruction



Mov instructionSharma Pavan This document discusses the MOV instruction set for the 8085 microprocessor. It defines the MOV instruction for moving data between registers and memory. The MOV instruction can move data from a source register to a destination register, from memory to a register, or from a register to memory. It provides the mnemonic, operation, number of bytes, machine cycles, addressing mode, and timing for each MOV variation. An example program is given to interchange the values in registers B and C using MOV instructions. Timing diagrams are also included to illustrate the machine cycles for MOV register to register and MOV register to/from memory.
Comprehensive survey on routing protocols for IoT



Comprehensive survey on routing protocols for IoTsulaiman_karim This document provides an overview of routing protocols for the Internet of Things (IoT). It defines IoT and routing protocols, describes common routing algorithms like distance vector and link state, and discusses specific protocols such as RPL, RIP, and OSPF. It also covers clustering in wireless sensor networks and the LEACH clustering protocol.
Bch codes



Bch codesGaurav Thakur This document provides information about BCH codes, including:
1. BCH codes are linear cyclic block codes that can detect and correct errors. They allow flexibility in choosing block length and code rate.
2. Key characteristics of BCH codes include the block length being 2m - 1, error correction ability up to t errors where t<(2m - 1)/2, and minimum distance of at least 2t + 1.
3. Galois fields are finite fields that are important for constructing BCH codes. A generator polynomial is chosen based on the roots in the Galois field and is used to encode messages into codewords.
Gsm signaling



Gsm signalingKannan Selvam The document discusses GSM signaling and mobile signaling. GSM signaling defines communications between the mobile and network using different protocols across interfaces. Mobile signaling involves the mobile searching for frequencies, synchronizing, downloading information, selecting a network, and signaling to the network by sending a service request when a call is made.
narrow Band ISDN



narrow Band ISDNkavitha muneeshwaran This document summarizes narrowband integrated services digital network (ISDN) and broadband ISDN (B-ISDN). It discusses that ISDN provides integrated services for voice, data, and video over digital lines using 64 kbps channels. Narrowband ISDN has a circuit switching orientation while B-ISDN supports higher data rates using packet switching and asynchronous transfer mode (ATM). The document also describes the ISDN protocol architecture including layers 1-3 and channels B and D, and notes that B-ISDN uses an ATM network as the user network interface.
LFSR



LFSRCVR college of Engineering This document presents a mini project on linear feedback shift registers (LFSRs). It describes how an 8-bit LFSR works using 8 D-flip flops connected in a chain with outputs XORed together. The LFSR generates a pseudo-random sequence that repeats after 255 cycles. It discusses the circuit, working, and timing diagrams of the 8-bit LFSR. Applications mentioned include random number generation, error detection/correction, and implementing cyclic redundancy checks for data transmission.
Programmable logic array



Programmable logic arrayHuba Akhtar It Defines what is Programmable Logic Array(PLA) also explains it in easy wording with syntax and Example...
It also cover what is Combinational & Sequential Logic Circuit and the Difference b/w these both. :)
Darshan Dehuniya - Resume - ASIC Verification Engineer (1)



Darshan Dehuniya - Resume - ASIC Verification Engineer (1)Darshan Dehuniya This document contains the resume of Darshan Dehuniya. It summarizes his career objective, qualifications, skills, and experience. He has over 1.4 years of experience as an ASIC Verification Engineer. His skills include SystemVerilog, UVM/OVM methodologies, Bluetooth Low Energy 4.1, AMBA protocols, and FPGA/ASIC design flows. He has a Bachelor's degree in Electronics and Communication Engineering and has worked on projects involving Bluetooth, AMBA, AXI, UART, and SPI verification.
301378156 design-of-sram-in-verilog



301378156 design-of-sram-in-verilogSrinivas Naidu This document provides an overview of the design of a dual port SRAM using Verilog HDL. It begins with an introduction describing the objectives and accomplishments of the project. It then reviews relevant literature on SRAM design. The document describes the FPGA design flow and introduces Verilog. It provides the design and operation of the SRAM, and discusses simulation results and conclusions. The proposed 8-bit dual port SRAM utilizes negative bitline techniques during write operations to improve write ability and reduce power consumption and area compared to conventional designs.
CDMA - USE WALSH TABLE TO GENERATE CHIP SEQUENCE 



CDMA - USE WALSH TABLE TO GENERATE CHIP SEQUENCE 0586umer USE WALSH TABLE TO GENERATE CHIP SEQUENCE FOR EACH OF THE FOLLOWING STATIONS WHICH WANT TO SEND DATA BIT WRITTEN AGAINST EACH
6LoWPAN: An open IoT Networking Protocol



6LoWPAN: An open IoT Networking ProtocolSamsung Open Source Group The document summarizes 6LoWPAN, an open IoT networking protocol specified by the IETF. 6LoWPAN allows IPv6 to be used over low-power wireless personal area networks (LoWPANs) by defining an adaptation layer that compresses IPv6 and UDP headers to accommodate the small packet sizes supported by IEEE 802.15.4 networks. It describes how 6LoWPAN uses header compression techniques like IPHC and NHC to reduce header overhead and enable IPv6 connectivity for constrained IoT devices. The document also provides an overview of the Linux-wpan project, which implements 6LoWPAN and IEEE 802.15.4 support in the Linux kernel.
Design Issues and Challenges in Wireless Sensor Networks



Design Issues and Challenges in Wireless Sensor NetworksKhushbooGupta145 Wireless Sensor Networks (WSNs) are composed self-organized wireless ad hoc networks which comprise of a large number of resource constrained sensor nodes. The major areas of research in WSN is going on hardware, and operating system of WSN, deployment, architecture, localization, synchronization, programming models, data aggregation and dissemination, database querying, architecture, middleware, quality of service and security. This paper study highlights ongoing research activities and issues that affect the design and performance of Wireless Sensor Network.
IPv4 Addressing 



IPv4 Addressing TheGodfather HA This document discusses the Internet Protocol (IP) version 4 and 6. It describes the key tasks of IP including addressing computers and fragmenting packets. IP version 4 uses 32-bit addresses while IP version 6 uses 128-bit addresses and has improvements like larger address space and better security. The document also covers IP address classes, private addressing, subnetting, Classless Inter-Domain Routing (CIDR), and address blocks.
Network Coding



Network CodingKishoj Bajracharya This document presents a simple implementation of network coding using XOR operations. It describes a scenario where two source nodes A and B send messages to an intermediate node C, which performs XOR operations on the messages and broadcasts the coded message. The source nodes are then able to decode the messages from the other source. Diagrams and examples are provided to illustrate how XOR network coding can be implemented on different network topologies, including butterfly networks. Python code demonstrations are also included to show how XOR and random linear network coding can be performed.
Schedule and Contention based MAC protocols



Schedule and Contention based MAC protocolsDarwin Nesakumar Schedule and contention based mac protocols by Mr.Darwin Nesakumar, AP/ECE, R.M.K.Engineering College
Routing protocols



Routing protocolsshravan kumar upadhayay This document discusses routing protocols RIP and OSPF. It begins with an introduction to routing and defines routing protocols as how routers communicate and share information to select optimal routes. It then provides details on RIP, including its hop count limit of 15, periodic updates every 30 seconds, and versions RIPv1 and RIPv2. The document also covers OSPF, describing how it uses the Dijkstra algorithm and allows for scalability. Configuration examples are given for implementing both RIP and OSPF on sample networks.
Frame Relay



Frame Relaykuldeep singh shishodia Frame Relay is a WAN protocol that operates at the physical and data link layers using packet switching technology. It provides connection-oriented virtual circuits between devices identified by a data-link connection identifier. Frame Relay supports both permanent virtual circuits that are always active and switched virtual circuits that are temporarily established for data transfer. It implements congestion notification using FECN, BECN and discard eligibility bits and uses CRC for error checking but not correction.
Data link layer 



Data link layer Mukesh Chinta This presentation covers the design issues of DLL, Error Correction and detection techniques, Sliding window protocols
Local Area Network – Wired LAN



Local Area Network – Wired LANRaj vardhan A local area network (LAN) uses wired connections to connect devices within a limited geographic area like a building or campus. Ethernet became the dominant wired LAN technology using carrier sense multiple access with collision detection (CSMA/CD) to regulate shared access to the transmission medium. Ethernet has evolved from 10 Mbps to 100 Mbps to 1 Gbps standards to meet increasing bandwidth demands. Key components of wired LANs include network adapters, cabling, connectors, switches/hubs, and software protocols. Other historical wired LAN technologies like Token Ring and Token Bus used token passing for medium access but have been largely replaced by Ethernet.
Energy consumption of wsn



Energy consumption of wsnDeepaDasarathan This document discusses wireless sensor network applications and energy consumption. It provides examples of WSN applications including disaster relief, environment monitoring, healthcare, and more. It then discusses various factors that influence energy consumption in sensor nodes, including operation states, microcontroller usage, radio transceivers, memory, and the relationship between computation and communication. Specific power consumption numbers are given for different components like radios, sensors, and microprocessors. The goals of optimization for WSNs are discussed as quality of service, energy efficiency, scalability, and robustness.
Wlan architecture



Wlan architectureVishal Verma This document provides an overview of wireless local area networks (WLANs), including their architecture and components. It defines key terms like basic service set (BSS), extended service set (ESS), stations, and access points. It describes the two types of BSS architectures - ad-hoc and infrastructure networks. Infrastructure networks use access points to connect stations and form a star topology, while ad-hoc networks connect stations directly without an access point in a peer-to-peer topology. An ESS connects multiple BSSs through a distribution system to increase network coverage.
8086 memory segmentation



8086 memory segmentationmahalakshmimalini
Introduction of memory Segmentation
Segmentation is the process in which the main memory of the computer is logically divided into different segments and each segment has its own base address.
Memory segmentation is the methods where whole memory is divided into the smaller parts called segments of various sizes.
A segment is just an area in memory.
The process of dividing memory this way is called segmentation.
Lambda design rule



Lambda design ruleGowri Kishore The document discusses layout design rules that specify minimum feature sizes and separations between layers for a chip manufacturing process. Design rules are described using either micron or lambda units. Lambda rules specify widths of diffusion and polysilicon layers as well as minimum separations between layers. There are also design rules for metal layers and forming transistors. The document describes three approaches for contact cuts between polysilicon and diffusion layers: using polysilicon to metal to diffusion, buried contacts, and butting contacts using metal.
Counter propagation Network



Counter propagation NetworkAkshay Dhole The document summarizes the counterpropagation neural network algorithm. It consists of an input layer, a Kohonen hidden layer that clusters inputs, and a Grossberg output layer. The algorithm identifies the winning hidden neuron that is most activated by the input. The output is then calculated as the weight between the winning hidden neuron and the output neurons, providing a coarse approximation of the input-output mapping.
Application layer protocols



Application layer protocolsFabMinds The document discusses several application layer protocols used in TCP/IP including HTTP, HTTPS, FTP, and Telnet. HTTP is used to access resources on the world wide web over port 80 and is stateless. HTTPS is a secure version of HTTP that encrypts communications over port 443. FTP is used to transfer files between hosts but sends data and passwords in clear text. Telnet allows users to access programs on remote computers.
System partitioning in VLSI and its considerations



System partitioning in VLSI and its considerationsSubash John System partitioning divides a large circuit into smaller subcircuits. This allows the subcircuits to be designed independently and in parallel, speeding up the design process. Effective partitioning aims to minimize connections between subcircuits. Tool-based partitioning allows constraints to be set to generate a partitioned netlist that balances subcircuit sizes and minimizes connections between top-level blocks.
Chapter 7 8051 programming in c



Chapter 7 8051 programming in cAbdelrahman Elewah 7.1 Data types and time delay in 8051 C
7.2 I/O programming in 8051 C
7.3 Logic operations in 8051 C
7.4 Data conversion programs in 8051 C
7.5 Accessing code ROM space in 8051 C
7.6 Data serialization using 8051 C
Pin Description Of Intel 80386 DX Microprocessor



Pin Description Of Intel 80386 DX MicroprocessorRaunaq Sahni Introduction to 80388 Microprocessor Architecture.
Pin Description Of Intel 80386 DX Microprocessor.
All Signal Groups and Individual Pins Explained.
Error Detection and Correction



Error Detection and CorrectionTechiNerd This document discusses error detection and correction techniques used in data transmission. It covers various types of errors that can occur during transmission and different coding schemes used for error detection and correction, including block coding, linear block coding, cyclic codes, and cyclic redundancy checks (CRCs). Specific examples are provided to illustrate how Hamming codes, parity checks, and CRCs can detect and correct single-bit and burst errors. Key concepts covered include redundancy, minimum Hamming distance, encoding/decoding processes, and the use of polynomials to represent binary words in CRC calculations.
Error detection and correction



Error detection and correctionMaria Akther This document discusses error detection and correction in data transmission. It describes single-bit errors, where one bit is corrupted, and burst errors, where multiple contiguous bits are corrupted. Error detection allows a receiver to detect if errors occurred, while error correction identifies the exact corrupted bits. Redundant bits are added to messages to enable detection and correction. Methods include forward error correction, retransmission, block coding, and convolution coding. Block coding divides messages into blocks with redundant bits added, creating codewords that allow error detection if a codeword is invalid.
Ad
More Related Content
What's hot (20)
301378156 design-of-sram-in-verilog



301378156 design-of-sram-in-verilogSrinivas Naidu This document provides an overview of the design of a dual port SRAM using Verilog HDL. It begins with an introduction describing the objectives and accomplishments of the project. It then reviews relevant literature on SRAM design. The document describes the FPGA design flow and introduces Verilog. It provides the design and operation of the SRAM, and discusses simulation results and conclusions. The proposed 8-bit dual port SRAM utilizes negative bitline techniques during write operations to improve write ability and reduce power consumption and area compared to conventional designs.
CDMA - USE WALSH TABLE TO GENERATE CHIP SEQUENCE 



CDMA - USE WALSH TABLE TO GENERATE CHIP SEQUENCE 0586umer USE WALSH TABLE TO GENERATE CHIP SEQUENCE FOR EACH OF THE FOLLOWING STATIONS WHICH WANT TO SEND DATA BIT WRITTEN AGAINST EACH
6LoWPAN: An open IoT Networking Protocol



6LoWPAN: An open IoT Networking ProtocolSamsung Open Source Group The document summarizes 6LoWPAN, an open IoT networking protocol specified by the IETF. 6LoWPAN allows IPv6 to be used over low-power wireless personal area networks (LoWPANs) by defining an adaptation layer that compresses IPv6 and UDP headers to accommodate the small packet sizes supported by IEEE 802.15.4 networks. It describes how 6LoWPAN uses header compression techniques like IPHC and NHC to reduce header overhead and enable IPv6 connectivity for constrained IoT devices. The document also provides an overview of the Linux-wpan project, which implements 6LoWPAN and IEEE 802.15.4 support in the Linux kernel.
Design Issues and Challenges in Wireless Sensor Networks



Design Issues and Challenges in Wireless Sensor NetworksKhushbooGupta145 Wireless Sensor Networks (WSNs) are composed self-organized wireless ad hoc networks which comprise of a large number of resource constrained sensor nodes. The major areas of research in WSN is going on hardware, and operating system of WSN, deployment, architecture, localization, synchronization, programming models, data aggregation and dissemination, database querying, architecture, middleware, quality of service and security. This paper study highlights ongoing research activities and issues that affect the design and performance of Wireless Sensor Network.
IPv4 Addressing 



IPv4 Addressing TheGodfather HA This document discusses the Internet Protocol (IP) version 4 and 6. It describes the key tasks of IP including addressing computers and fragmenting packets. IP version 4 uses 32-bit addresses while IP version 6 uses 128-bit addresses and has improvements like larger address space and better security. The document also covers IP address classes, private addressing, subnetting, Classless Inter-Domain Routing (CIDR), and address blocks.
Network Coding



Network CodingKishoj Bajracharya This document presents a simple implementation of network coding using XOR operations. It describes a scenario where two source nodes A and B send messages to an intermediate node C, which performs XOR operations on the messages and broadcasts the coded message. The source nodes are then able to decode the messages from the other source. Diagrams and examples are provided to illustrate how XOR network coding can be implemented on different network topologies, including butterfly networks. Python code demonstrations are also included to show how XOR and random linear network coding can be performed.
Schedule and Contention based MAC protocols



Schedule and Contention based MAC protocolsDarwin Nesakumar Schedule and contention based mac protocols by Mr.Darwin Nesakumar, AP/ECE, R.M.K.Engineering College
Routing protocols



Routing protocolsshravan kumar upadhayay This document discusses routing protocols RIP and OSPF. It begins with an introduction to routing and defines routing protocols as how routers communicate and share information to select optimal routes. It then provides details on RIP, including its hop count limit of 15, periodic updates every 30 seconds, and versions RIPv1 and RIPv2. The document also covers OSPF, describing how it uses the Dijkstra algorithm and allows for scalability. Configuration examples are given for implementing both RIP and OSPF on sample networks.
Frame Relay



Frame Relaykuldeep singh shishodia Frame Relay is a WAN protocol that operates at the physical and data link layers using packet switching technology. It provides connection-oriented virtual circuits between devices identified by a data-link connection identifier. Frame Relay supports both permanent virtual circuits that are always active and switched virtual circuits that are temporarily established for data transfer. It implements congestion notification using FECN, BECN and discard eligibility bits and uses CRC for error checking but not correction.
Data link layer 



Data link layer Mukesh Chinta This presentation covers the design issues of DLL, Error Correction and detection techniques, Sliding window protocols
Local Area Network – Wired LAN



Local Area Network – Wired LANRaj vardhan A local area network (LAN) uses wired connections to connect devices within a limited geographic area like a building or campus. Ethernet became the dominant wired LAN technology using carrier sense multiple access with collision detection (CSMA/CD) to regulate shared access to the transmission medium. Ethernet has evolved from 10 Mbps to 100 Mbps to 1 Gbps standards to meet increasing bandwidth demands. Key components of wired LANs include network adapters, cabling, connectors, switches/hubs, and software protocols. Other historical wired LAN technologies like Token Ring and Token Bus used token passing for medium access but have been largely replaced by Ethernet.
Energy consumption of wsn



Energy consumption of wsnDeepaDasarathan This document discusses wireless sensor network applications and energy consumption. It provides examples of WSN applications including disaster relief, environment monitoring, healthcare, and more. It then discusses various factors that influence energy consumption in sensor nodes, including operation states, microcontroller usage, radio transceivers, memory, and the relationship between computation and communication. Specific power consumption numbers are given for different components like radios, sensors, and microprocessors. The goals of optimization for WSNs are discussed as quality of service, energy efficiency, scalability, and robustness.
Wlan architecture



Wlan architectureVishal Verma This document provides an overview of wireless local area networks (WLANs), including their architecture and components. It defines key terms like basic service set (BSS), extended service set (ESS), stations, and access points. It describes the two types of BSS architectures - ad-hoc and infrastructure networks. Infrastructure networks use access points to connect stations and form a star topology, while ad-hoc networks connect stations directly without an access point in a peer-to-peer topology. An ESS connects multiple BSSs through a distribution system to increase network coverage.
8086 memory segmentation



8086 memory segmentationmahalakshmimalini
Introduction of memory Segmentation
Segmentation is the process in which the main memory of the computer is logically divided into different segments and each segment has its own base address.
Memory segmentation is the methods where whole memory is divided into the smaller parts called segments of various sizes.
A segment is just an area in memory.
The process of dividing memory this way is called segmentation.
Lambda design rule



Lambda design ruleGowri Kishore The document discusses layout design rules that specify minimum feature sizes and separations between layers for a chip manufacturing process. Design rules are described using either micron or lambda units. Lambda rules specify widths of diffusion and polysilicon layers as well as minimum separations between layers. There are also design rules for metal layers and forming transistors. The document describes three approaches for contact cuts between polysilicon and diffusion layers: using polysilicon to metal to diffusion, buried contacts, and butting contacts using metal.
Counter propagation Network



Counter propagation NetworkAkshay Dhole The document summarizes the counterpropagation neural network algorithm. It consists of an input layer, a Kohonen hidden layer that clusters inputs, and a Grossberg output layer. The algorithm identifies the winning hidden neuron that is most activated by the input. The output is then calculated as the weight between the winning hidden neuron and the output neurons, providing a coarse approximation of the input-output mapping.
Application layer protocols



Application layer protocolsFabMinds The document discusses several application layer protocols used in TCP/IP including HTTP, HTTPS, FTP, and Telnet. HTTP is used to access resources on the world wide web over port 80 and is stateless. HTTPS is a secure version of HTTP that encrypts communications over port 443. FTP is used to transfer files between hosts but sends data and passwords in clear text. Telnet allows users to access programs on remote computers.
System partitioning in VLSI and its considerations



System partitioning in VLSI and its considerationsSubash John System partitioning divides a large circuit into smaller subcircuits. This allows the subcircuits to be designed independently and in parallel, speeding up the design process. Effective partitioning aims to minimize connections between subcircuits. Tool-based partitioning allows constraints to be set to generate a partitioned netlist that balances subcircuit sizes and minimizes connections between top-level blocks.
Chapter 7 8051 programming in c



Chapter 7 8051 programming in cAbdelrahman Elewah 7.1 Data types and time delay in 8051 C
7.2 I/O programming in 8051 C
7.3 Logic operations in 8051 C
7.4 Data conversion programs in 8051 C
7.5 Accessing code ROM space in 8051 C
7.6 Data serialization using 8051 C
Pin Description Of Intel 80386 DX Microprocessor



Pin Description Of Intel 80386 DX MicroprocessorRaunaq Sahni Introduction to 80388 Microprocessor Architecture.
Pin Description Of Intel 80386 DX Microprocessor.
All Signal Groups and Individual Pins Explained.
Viewers also liked (20)
Error Detection and Correction



Error Detection and CorrectionTechiNerd This document discusses error detection and correction techniques used in data transmission. It covers various types of errors that can occur during transmission and different coding schemes used for error detection and correction, including block coding, linear block coding, cyclic codes, and cyclic redundancy checks (CRCs). Specific examples are provided to illustrate how Hamming codes, parity checks, and CRCs can detect and correct single-bit and burst errors. Key concepts covered include redundancy, minimum Hamming distance, encoding/decoding processes, and the use of polynomials to represent binary words in CRC calculations.
Error detection and correction



Error detection and correctionMaria Akther This document discusses error detection and correction in data transmission. It describes single-bit errors, where one bit is corrupted, and burst errors, where multiple contiguous bits are corrupted. Error detection allows a receiver to detect if errors occurred, while error correction identifies the exact corrupted bits. Redundant bits are added to messages to enable detection and correction. Methods include forward error correction, retransmission, block coding, and convolution coding. Block coding divides messages into blocks with redundant bits added, creating codewords that allow error detection if a codeword is invalid.
Error Detection and Correction - Data link Layer



Error Detection and Correction - Data link LayerAbdullaziz Tagawy Networks must be able to transfer data from one device to another with acceptable
accuracy. For most applications, a system must guarantee that the data received are
identical to the data transmitted. Any time data are transmitted from one node to the
next, they can become corrupted in passage. Many factors can alter one or more bits of
a message. Some applications require a mechanism for detecting and correcting errors.
Some applications can tolerate a small level of error. For example, random errors
in audio or video transmissions may be tolerable, but when we transfer text, we expect
a very high level of accuracy.
At the data-link layer, if a frame is corrupted between the two nodes, it needs to be
corrected before it continues its journey to other nodes. However, most link-layer protocols
simply discard the frame and let the upper-layer protocols handle the retransmission
of the frame. Some multimedia applications, however, try to correct the corrupted frame.
This chapter is divided into five sections.
❑ The first section introduces types of errors, the concept of redundancy, and distinguishes
between error detection and correction.
❑ The second section discusses block coding. It shows how error can be detected
using block coding and also introduces the concept of Hamming distance.
❑ The third section discusses cyclic codes. It discusses a subset of cyclic code, CRC,
that is very common in the data-link layer. The section shows how CRC can be
easily implemented in hardware and represented by polynomials.
❑ The fourth section discusses checksums. It shows how a checksum is calculated for
a set of data words. It also gives some other approaches to traditional checksum.
❑ The fifth section discusses forward error correction. It shows how Hamming distance
can also be used for this purpose. The section also describes cheaper methods
to achieve the same goal, such as XORing of packets, interleaving chunks, or
compounding high and low resolutions packets.
Error detection and correction



Error detection and correctionSiddique Ibrahim This document discusses error detection and correction in digital communication. It describes how coding schemes add redundancy to messages through techniques like block coding and convolution coding to detect or correct errors. The encoder adds redundant bits to original messages to create relationships between bits that the decoder can use to check for errors. It also explains the use of modular arithmetic, specifically modulo-2 arithmetic which uses only 1s and 0s, for error detection and correction operations.
Error Detection And Correction



Error Detection And CorrectionRenu Kewalramani The document discusses error detection and correction techniques used in data communication. It describes different types of errors like single bit errors and burst errors. It then explains various error detection techniques like vertical redundancy check (VRC), longitudinal redundancy check (LRC), and cyclic redundancy check (CRC). VRC adds a parity bit, LRC calculates parity bits for each column, and CRC uses a generator polynomial to calculate redundant bits. The document also discusses Hamming code, an error correcting code that uses redundant bits to detect and correct single bit errors.
Lecture 9 dim & rank - 4-5 & 4-6



Lecture 9 dim & rank - 4-5 & 4-6njit-ronbrown The document discusses the dimension of vector spaces. It defines the dimension of a vector space V as the number of vectors in a basis for V. It states that any set containing more vectors than the dimension must be linearly dependent, and that every basis of V must consist of exactly the dimension number of vectors. Examples of finding the dimension of various vector spaces and subspaces are provided.
Computer network



Computer networkSubrata Kumer Paul This document summarizes computer networking concepts including switches, hubs, and the differences between them. It defines a switch as a networking device that connects multiple computers within a local area network and operates at the data link layer. The document describes how switches work by examining destination MAC addresses in packets and updating their MAC address tables to forward packets to the correct port. It also lists characteristics of switches such as using MAC addressing and filtering data. The document then defines a hub as a basic networking device that broadcasts all traffic to all ports without intelligence about destinations. It provides details on how hubs work and compares hubs to switches, noting that switches can selectively forward data while hubs broadcast to all ports.
Galois field



Galois fieldNiaj Morshed This presentation provides an introduction to Galois fields, which are finite fields with a prime number of elements. The objectives are to discuss preliminaries like sets and groups, introduce Galois fields and provide examples, discuss related theorems, and describe the computational approach. A sample computation in FORTRAN verifies the theorem that any element in a Galois field can be expressed as the sum of two squares.
Semantic Compositionality through Recursive Matrix-Vector Spaces (Socher et al.)



Semantic Compositionality through Recursive Matrix-Vector Spaces (Socher et al.)marujirou Slides about introducing a paper "Socher et al. Semantic Compositionality through Recursive Matrix-Vector Spaces" presented at DL reading group at Tokyo Metropolitan University, Japan.
28 networking



28 networkingRavindra Rathore The document discusses Java networking concepts including sockets, TCP, UDP, client-server programming, and key networking classes like InetAddress, ServerSocket, Socket, DatagramSocket, and DatagramPacket. It provides code examples for basic TCP and UDP client-server applications in Java using sockets to demonstrate sending and receiving data over a network.
Ch11 communication



Ch11 communicationadrienne0901 This document summarizes key concepts about communication. It discusses the functions of communication including control, motivation, emotional expression, and information sharing. It outlines the communication process and directions including downward, upward, and lateral. It describes interpersonal communication methods like oral, written, and nonverbal. It also examines organizational communication structures, channels, and barriers. Current issues in communication mentioned include gender differences, political correctness, cross-cultural challenges, and semantics. The overall purpose is to provide an overview of communication concepts.
26 io -ii file handling



26 io -ii file handlingRavindra Rathore The document discusses File Input/Output in Java. It describes FileInputStream and FileOutputStream classes which allow reading and writing of bytes from/to files. FileInputStream can be used to read bytes from a file, while FileOutputStream can be used to write bytes to a file. It also discusses FileReader and FileWriter character stream classes which allow reading and writing of characters from/to files. Examples are provided to demonstrate reading bytes/characters from a file, writing bytes/characters to a file, and copying contents from one file to another using the FileInputStream and FileOutputStream classes.
Introduction of reflection 



Introduction of reflection Ravindra Rathore A boundary is where conditions change, and how a wave interacts with a boundary depends on the boundary conditions. Waves can interact with boundaries in four different ways.
21 multi threading - iii



21 multi threading - iiiRavindra Rathore The document discusses two main ways for a thread to know when another thread has finished:
1. Calling isAlive() on the thread, which returns true if the thread is still running and false if not.
2. Using join(), which waits for the specified thread to terminate before continuing. Additional forms of join() allow specifying a maximum wait time.
The example code starts three threads and uses join() in the main thread to wait for the child threads to finish before exiting, ensuring the main thread finishes last. Without join(), the main thread could exit before the child threads.
22 multi threading iv



22 multi threading ivRavindra Rathore This document discusses synchronization in multithreaded applications in Java. It covers key concepts like monitors, synchronized methods and statements, and inter-thread communication using wait(), notify(), and notifyAll() methods. Synchronized methods ensure only one thread can access a shared resource at a time by acquiring the object's monitor. synchronized statements allow synchronizing access to non-synchronized methods. Inter-thread communication allows threads to wait for notifications from other threads rather than busy waiting.
Lecture 5 phasor notations



Lecture 5 phasor notationsRavindra Rathore Phasors are complex numbers that represent the amplitude and phase of sinusoidal signals and are useful for analyzing linear time-invariant systems. Phasors allow representations of electromagnetic fields, circuit elements, and communication systems as sinusoidal signals. By using phasors, time-domain differential operators can be converted to algebraic operations in the frequency domain, simplifying analyses of linear problems where frequency components do not mix.
Vlsi



VlsiRina Ahire The seminar discussed CAD tools and their use in electronic design automation. CAD tools help partition systems, plan chip layouts, and optimize designs to meet goals like minimizing area and interconnect length. System partitioning was demonstrated using the example of the Sun SPARCstation 1, which was broken into custom ASICs, memory modules, and other components. Power dissipation sources like switching current and short-circuit current were also examined. CAD tools provide advantages like evaluating complex conditions and helping to find optimal solutions.
Fiber optics101



Fiber optics101admercano101 This document provides a 3-paragraph summary of the key concepts of fiber optics:
Fiber optics uses glass or plastic fibers to guide light along its length through the process of total internal reflection. Light is transmitted from a transmitter that converts an electrical signal to light, through the fiber, and received at the other end by a receiver that converts the light back to an electrical signal. Refraction causes light to bend as it passes between materials with different refractive indices, and total internal reflection keeps light confined within the fiber when it encounters a change in index of refraction at the fiber's outer surface.
Basic galois field arithmatics required for error control codes



Basic galois field arithmatics required for error control codesMadhumita Tamhane Knowledge of Galois Fields is must for understanding Error Control Codes. This presentation undertakes concepts of Galois Field required for understanding Error Control Codes in very simple manner, explaining its complex mathematical intricacies in a structured manner.
Spread spectrum



Spread spectrumRina Ahire Miss Rina Ahire presented a seminar on spread spectrum that covered jamming margin, time hopping spread spectrum, the block diagram, synchronization including acquisition and tracking. The key topics were how jamming margin is the ratio of average powers of interference and data signal, how time hopping spread spectrum works, the components in the block diagram, and how synchronization has an initial acquisition phase followed by a tracking phase where acquisition finds coarse synchronization and tracking provides fine synchronization.
Ad
Similar to T com presentation (error correcting code) (20)
linear codes and cyclic codes



linear codes and cyclic codessaigopinadh bodigiri This document provides an introduction to error correcting codes. It discusses key concepts such as channel capacity, error detection and correction, information rate, weight and distance, maximum likelihood decoding, and linear codes. Error correcting codes add redundant bits to messages to facilitate detecting and correcting errors that may occur during transmission or storage. Linear codes allow for simpler encoding and decoding procedures compared to non-linear codes. The generator and parity check matrices are important for encoding and decoding messages using linear codes.
Chapter 10



Chapter 10bheemsain This document summarizes error detection and correction techniques. It discusses types of errors like single-bit errors and burst errors. It covers basic concepts of error detection, including adding redundant bits and using techniques like parity checks. Error correction requires knowing the number and positions of errors. Linear block codes and cyclic codes are introduced. Hamming distance and minimum distance are important metrics for error detection and correction capability. Specific codes like parity codes, Hamming codes, and cyclic redundancy checks (CRCs) are described through examples.
4_Datalink__Error_Detection_and Correction.pdf



4_Datalink__Error_Detection_and Correction.pdfkenilpatel65 The document discusses error detection and correction techniques at the data link layer. It describes how errors can occur during data transmission and the need for reliable communication. Error detection allows a receiver to detect errors while error correction enables identifying and correcting bit errors without retransmission. Common techniques discussed include parity checks, checksums, and cyclic redundancy checks which add redundant bits to detect errors. CRC is based on binary division of data and checksum on addition. Forward error correction and retransmission are compared. Coding schemes use redundancy to detect or correct errors.
Human: Thank you for the summary. Can you provide a 2 sentence summary that captures the key aspects?
Error Detection and correction concepts in Data communication and networks



Error Detection and correction concepts in Data communication and networksNt Arvind single bit , burst error detection and correction in data communication networks , block coding ( hamming code , simple parity check code , Cyclic redundancy check-CRC , checksum , internet checksum etc
Coding theory.pdf



Coding theory.pdf230231060 This document covers the basics of coding theory. It specifically explains the Generator and Parity Check Matrices, and Hamming code.
Ch10 2 v1



Ch10 2 v1Nitesh Singh This document discusses error detection and correction techniques using Hamming codes and cyclic codes. It provides examples of calculating Hamming distance between words and finding the minimum Hamming distance of coding schemes. Linear block codes are introduced where the XOR of two codewords results in another valid codeword. Simple parity check codes that can detect single bit errors are examined. Hamming codes that can detect up to two errors and correct single errors are analyzed. Cyclic codes are discussed as a special type of linear block code where cyclically shifting a codeword results in another valid codeword. Polynomial representations and cyclic redundancy checks are presented.
Ch10 2 v1



Ch10 2 v1bhagavanprasad This document discusses error detection and correction techniques in digital communications. It covers Hamming distance, block codes, linear block codes, cyclic codes, cyclic redundancy checks (CRCs), and checksums. Key points include:
- The Hamming distance between words is the number of differing bits
- Minimum Hamming distance determines a code's error detection/correction capabilities
- CRCs use polynomial division to generate check bits and detect errors
- Cyclic codes have the property that cyclic shifts of codewords are also codewords
- CRC and cyclic codes are often implemented using shift registers and polynomial arithmetic
- Characteristics of good cyclic code generators for detecting various error patterns are discussed
Ch10 2 v1



Ch10 2 v1Vivek Kumar This document discusses error detection and correction techniques in digital communications. It covers Hamming distance, block codes, linear block codes, cyclic codes, cyclic redundancy checks (CRCs), and checksums. Key points include:
- The Hamming distance between words is the number of differing bits
- Minimum Hamming distance determines a code's error detection/correction capability
- Linear block codes allow valid codewords to be created by XORing other codewords
- Cyclic codes maintain codeword validity under cyclic shifts
- CRCs use polynomial division to embed a checksum in transmitted data
- Checksums provide error detection by transmitting a calculated value over transmitted data
Cn lec-06



Cn lec-06M Mudassar Khan This document discusses error detection and correction techniques in digital communications. It covers Hamming distance, block codes, linear block codes, cyclic codes, cyclic redundancy checks (CRCs), and checksums. Key points include:
- The Hamming distance between words is the number of differing bits
- Minimum Hamming distance determines a code's error detection/correction capability
- Linear block codes allow valid codewords to be created by XORing other codewords
- Cyclic codes maintain codeword validity under cyclic shifts
- CRCs use polynomial division to embed a checksum in transmitted data for error detection
- Checksums provide simple error detection by transmitting a sum of message bits
Hamming codes



Hamming codesGIGI JOSEPH Richard Hamming developed Hamming codes in the late 1940s to enable error correction in computing. Hamming codes are perfect 1-error correcting codes that use parity checks to detect and correct single bit errors in binary data. The codes work by encoding k message bits into an n-bit codeword with additional parity check bits such that the minimum distance between any two codewords is 3, allowing correction of single bit errors. Hamming codes see widespread use and can be generalized to non-binary alphabets. Extended Hamming codes provide both single-error correction and double-error detection.
Chapter 10: Error Correction and Detection



Chapter 10: Error Correction and DetectionJeoffnaRuth This document discusses error detection and correction techniques. It defines single-bit and burst errors and explains how redundancy is used to detect or correct errors by adding extra bits. It describes the differences between error detection and correction. Various error correction methods are presented, including forward error correction, retransmission, and the use of modular arithmetic and cyclic redundancy checks. Hardware implementations of cyclic redundancy checks are also summarized.
error control coding 



error control coding Suhad Malayshi The document discusses error control coding, which detects and corrects errors in received symbols. It defines error control coding and describes how it works by segmenting the bit stream into blocks and mapping blocks to codewords. The channel decoder detects and possibly corrects errors. It discusses ARQ and FEC techniques for error control. Specific coding techniques covered include Hamming distance, linear block coding, syndrome coding, and block vs convolutional coding. Applications of error control coding include aerospace, cellular networks, and security systems.
Computer Representation of Numbers and.pptx



Computer Representation of Numbers and.pptxTemesgen Geta - Computers use binary to represent numbers, where each digit is either a 1 or 0. Real numbers are approximated using floating point representation with sign, mantissa, and exponent fields.
- Integers can be stored by reserving bits for the magnitude and using the first bit to indicate sign (sign-magnitude representation) or by using two's complement representation where the most significant bit indicates sign.
- When storing numbers in memory, multiple bytes are typically used to represent integers or floating point values to support a wider range of numbers.
Encoder for (7,3) cyclic code using matlab



Encoder for (7,3) cyclic code using matlabSneheshDutta This document provides an overview of cyclic codes including:
- What cyclic codes are and their properties of error detection and correction.
- The method of generating cyclic codes by multiplying message polynomials by a generator polynomial.
- How to systematically encode cyclic codes in three steps.
- The encoding and decoding circuits including Meggitt decoder.
- An example of a (7,3) cyclic code implemented in Matlab showing the encoding, corruption with errors, and decoding.
- How cyclic codes can detect errors through syndrome computation and lookup tables.
- Applications of cyclic codes in message identification.
New error-detection (2)



New error-detection (2)Nitesh Singh This document discusses various techniques for error detection and correction in digital communications. It begins by describing common types of errors like single-bit and burst errors. It then explains error detection methods like parity checks and cyclic redundancy checks (CRCs). CRCs use cyclic codes and polynomial division to detect errors. Block codes like Hamming codes can detect and correct errors by ensuring a minimum Hamming distance between codewords. Checksums are also discussed as a simpler error detection technique than CRCs. The document provides examples to illustrate how these different error control methods work.
New error-detection



New error-detectionNitesh Singh This document discusses various techniques for error detection and correction in digital communications. It describes common types of errors like single-bit and burst errors. It then explains different coding schemes for error detection and correction including block coding, linear block codes like parity codes and Hamming codes, and cyclic redundancy checks (CRCs). Key concepts covered are redundancy, minimum Hamming distance requirements for detection and correction capabilities, and encoders and decoders for different coding schemes.
GROUP03_AMAK:ERROR DETECTION AND CORRECTION PPT



GROUP03_AMAK:ERROR DETECTION AND CORRECTION PPTKrishbathija This document discusses error detection and correction techniques. It introduces concepts like redundancy, forward error correction, retransmission, linear block coding, Hamming codes, and cyclic redundancy checks (CRC). Specific error correction codes covered include Hamming codes, which use modulo-2 arithmetic to add redundant bits to detect and correct single bit errors. CRC codes are also discussed, which use cyclic codes and polynomial representations to detect errors by computing a syndrome value. The document provides information on generating and detecting errors for different codes.
5(1)crc-chechsum-hamming.ppt



5(1)crc-chechsum-hamming.pptprashant513130 This document discusses error detection and correction techniques using Hamming codes and cyclic redundancy checks (CRCs). It explains key concepts like Hamming distance, minimum distance, linear block codes, and cyclic codes. Examples are provided to illustrate how Hamming codes can detect up to two errors and correct one error using a minimum distance of 3. CRC codes are also examined, showing how they use polynomial division to detect errors. The advantages of cyclic codes for hardware implementation are noted.
hamming code detailed



hamming code detailedIKhait This document discusses error detection and correction techniques using Hamming codes and cyclic redundancy checks (CRCs). It explains key concepts like Hamming distance, minimum distance, linear block codes, and cyclic codes. Examples are provided to illustrate how Hamming codes can detect up to two errors and correct one error using a minimum distance of 3. CRC codes are also examined, showing how they use polynomial division to detect errors. The advantages of cyclic codes for hardware implementation are noted.
Ad
Recently uploaded (20)
How to track Cost and Revenue using Analytic Accounts in odoo Accounting, App...



How to track Cost and Revenue using Analytic Accounts in odoo Accounting, App...Celine George Analytic accounts are used to track and manage financial transactions related to specific projects, departments, or business units. They provide detailed insights into costs and revenues at a granular level, independent of the main accounting system. This helps to better understand profitability, performance, and resource allocation, making it easier to make informed financial decisions and strategic planning.
One Hot encoding a revolution in Machine learning



One Hot encoding a revolution in Machine learningmomer9505 A brief introduction to ONE HOT encoding a way to communicate with machines
Understanding P–N Junction Semiconductors: A Beginner’s Guide



Understanding P–N Junction Semiconductors: A Beginner’s GuideGS Virdi Dive into the fundamentals of P–N junctions, the heart of every diode and semiconductor device. In this concise presentation, Dr. G.S. Virdi (Former Chief Scientist, CSIR-CEERI Pilani) covers:
What Is a P–N Junction? Learn how P-type and N-type materials join to create a diode.
Depletion Region & Biasing: See how forward and reverse bias shape the voltage–current behavior.
V–I Characteristics: Understand the curve that defines diode operation.
Real-World Uses: Discover common applications in rectifiers, signal clipping, and more.
Ideal for electronics students, hobbyists, and engineers seeking a clear, practical introduction to P–N junction semiconductors.
K12 Tableau Tuesday - Algebra Equity and Access in Atlanta Public Schools



K12 Tableau Tuesday - Algebra Equity and Access in Atlanta Public Schoolsdogden2 Algebra 1 is often described as a “gateway” class, a pivotal moment that can shape the rest of a student’s K–12 education. Early access is key: successfully completing Algebra 1 in middle school allows students to complete advanced math and science coursework in high school, which research shows lead to higher wages and lower rates of unemployment in adulthood.
Learn how The Atlanta Public Schools is using their data to create a more equitable enrollment in middle school Algebra classes.
World war-1(Causes & impacts at a glance) PPT by Simanchala Sarab(BABed,sem-4...



World war-1(Causes & impacts at a glance) PPT by Simanchala Sarab(BABed,sem-4...larencebapu132 This is short and accurate description of World war-1 (1914-18)
It can give you the perfect factual conceptual clarity on the great war
Regards Simanchala Sarab
Student of BABed(ITEP, Secondary stage)in History at Guru Nanak Dev University Amritsar Punjab 🙏🙏
Quality Contril Analysis of Containers.pdf



Quality Contril Analysis of Containers.pdfDr. Bindiya Chauhan Quality control test for containers, rubber closures and secondary packing materials.
GDGLSPGCOER - Git and GitHub Workshop.pptx



GDGLSPGCOER - Git and GitHub Workshop.pptxazeenhodekar This presentation covers the fundamentals of Git and version control in a practical, beginner-friendly way. Learn key commands, the Git data model, commit workflows, and how to collaborate effectively using Git — all explained with visuals, examples, and relatable humor.
Biophysics Chapter 3 Methods of Studying Macromolecules.pdf



Biophysics Chapter 3 Methods of Studying Macromolecules.pdfPKLI-Institute of Nursing and Allied Health Sciences Lahore , Pakistan. This chapter provides an in-depth overview of the viscosity of macromolecules, an essential concept in biophysics and medical sciences, especially in understanding fluid behavior like blood flow in the human body.
Key concepts covered include:
✅ Definition and Types of Viscosity: Dynamic vs. Kinematic viscosity, cohesion, and adhesion.
⚙️ Methods of Measuring Viscosity:
Rotary Viscometer
Vibrational Viscometer
Falling Object Method
Capillary Viscometer
🌡️ Factors Affecting Viscosity: Temperature, composition, flow rate.
🩺 Clinical Relevance: Impact of blood viscosity in cardiovascular health.
🌊 Fluid Dynamics: Laminar vs. turbulent flow, Reynolds number.
🔬 Extension Techniques:
Chromatography (adsorption, partition, TLC, etc.)
Electrophoresis (protein/DNA separation)
Sedimentation and Centrifugation methods.
YSPH VMOC Special Report - Measles Outbreak Southwest US 5-3-2025.pptx



YSPH VMOC Special Report - Measles Outbreak Southwest US 5-3-2025.pptxYale School of Public Health - The Virtual Medical Operations Center (VMOC) A measles outbreak originating in West Texas has been linked to confirmed cases in New Mexico, with additional cases reported in Oklahoma and Kansas. The current case count is 817 from Texas, New Mexico, Oklahoma, and Kansas. 97 individuals have required hospitalization, and 3 deaths, 2 children in Texas and one adult in New Mexico. These fatalities mark the first measles-related deaths in the United States since 2015 and the first pediatric measles death since 2003.
The YSPH Virtual Medical Operations Center Briefs (VMOC) were created as a service-learning project by faculty and graduate students at the Yale School of Public Health in response to the 2010 Haiti Earthquake. Each year, the VMOC Briefs are produced by students enrolled in Environmental Health Science Course 581 - Public Health Emergencies: Disaster Planning and Response. These briefs compile diverse information sources – including status reports, maps, news articles, and web content– into a single, easily digestible document that can be widely shared and used interactively. Key features of this report include:
- Comprehensive Overview: Provides situation updates, maps, relevant news, and web resources.
- Accessibility: Designed for easy reading, wide distribution, and interactive use.
- Collaboration: The “unlocked" format enables other responders to share, copy, and adapt seamlessly. The students learn by doing, quickly discovering how and where to find critical information and presenting it in an easily understood manner.
CURRENT CASE COUNT: 817 (As of 05/3/2025)
• Texas: 688 (+20)(62% of these cases are in Gaines County).
• New Mexico: 67 (+1 )(92.4% of the cases are from Eddy County)
• Oklahoma: 16 (+1)
• Kansas: 46 (32% of the cases are from Gray County)
HOSPITALIZATIONS: 97 (+2)
• Texas: 89 (+2) - This is 13.02% of all TX cases.
• New Mexico: 7 - This is 10.6% of all NM cases.
• Kansas: 1 - This is 2.7% of all KS cases.
DEATHS: 3
• Texas: 2 – This is 0.31% of all cases
• New Mexico: 1 – This is 1.54% of all cases
US NATIONAL CASE COUNT: 967 (Confirmed and suspected):
INTERNATIONAL SPREAD (As of 4/2/2025)
• Mexico – 865 (+58)
‒Chihuahua, Mexico: 844 (+58) cases, 3 hospitalizations, 1 fatality
• Canada: 1531 (+270) (This reflects Ontario's Outbreak, which began 11/24)
‒Ontario, Canada – 1243 (+223) cases, 84 hospitalizations.
• Europe: 6,814
To study Digestive system of insect.pptx



To study Digestive system of insect.pptxArshad Shaikh Education is one thing no one can take away from you.”
Marie Boran Special Collections Librarian Hardiman Library, University of Gal...



Marie Boran Special Collections Librarian Hardiman Library, University of Gal...Library Association of Ireland Phoenix – A Collaborative Renewal of Children’s and Young People’s Services Clare Doyle - Cork City Libraries
Presentation of the MIPLM subject matter expert Erdem Kaya



Presentation of the MIPLM subject matter expert Erdem KayaMIPLM Presentation of the MIPLM subject matter expert Erdem Kaya
Exploring-Substances-Acidic-Basic-and-Neutral.pdf



Exploring-Substances-Acidic-Basic-and-Neutral.pdfSandeep Swamy Exploring Substances:
Acidic, Basic, and
Neutral
Welcome to the fascinating world of acids and bases! Join siblings Ashwin and
Keerthi as they explore the colorful world of substances at their school's
National Science Day fair. Their adventure begins with a mysterious white paper
that reveals hidden messages when sprayed with a special liquid.
In this presentation, we'll discover how different substances can be classified as
acidic, basic, or neutral. We'll explore natural indicators like litmus, red rose
extract, and turmeric that help us identify these substances through color
changes. We'll also learn about neutralization reactions and their applications in
our daily lives.
by sandeep swamy
Geography Sem II Unit 1C Correlation of Geography with other school subjects



Geography Sem II Unit 1C Correlation of Geography with other school subjectsProfDrShaikhImran The correlation of school subjects refers to the interconnectedness and mutual reinforcement between different academic disciplines. This concept highlights how knowledge and skills in one subject can support, enhance, or overlap with learning in another. Recognizing these correlations helps in creating a more holistic and meaningful educational experience.
Metamorphosis: Life's Transformative Journey



Metamorphosis: Life's Transformative JourneyArshad Shaikh *Metamorphosis* is a biological process where an animal undergoes a dramatic transformation from a juvenile or larval stage to a adult stage, often involving significant changes in form and structure. This process is commonly seen in insects, amphibians, and some other animals.
Social Problem-Unemployment .pptx notes for Physiotherapy Students



Social Problem-Unemployment .pptx notes for Physiotherapy StudentsDrNidhiAgarwal Unemployment is a major social problem, by which not only rural population have suffered but also urban population are suffered while they are literate having good qualification.The evil consequences like poverty, frustration, revolution
result in crimes and social disorganization. Therefore, it is
necessary that all efforts be made to have maximum.
employment facilities. The Government of India has already
announced that the question of payment of unemployment
allowance cannot be considered in India
Biophysics Chapter 3 Methods of Studying Macromolecules.pdf



Biophysics Chapter 3 Methods of Studying Macromolecules.pdfPKLI-Institute of Nursing and Allied Health Sciences Lahore , Pakistan.
YSPH VMOC Special Report - Measles Outbreak Southwest US 5-3-2025.pptx



YSPH VMOC Special Report - Measles Outbreak Southwest US 5-3-2025.pptxYale School of Public Health - The Virtual Medical Operations Center (VMOC)
Marie Boran Special Collections Librarian Hardiman Library, University of Gal...



Marie Boran Special Collections Librarian Hardiman Library, University of Gal...Library Association of Ireland
T com presentation (error correcting code)
- 2. How Is Data Transmitted ?
- 3. Occurrence of Error Causes of Error (Noise): o Multi-path propagation of the signal. o Interference from other communication devices
- 4. Contd..
- 6. Block Codes ● Divide the message into blocks each of k bits called data words. ● Add r redundant bits to each blocks to make the length n = k+r. ● Examples : Hamming Codes, Reed-Muller Codes
- 7. Redundancy Coding ● In n-redundancy coding, each data bit is encoded in n bits. ● In a 3-redundancy coding scheme, a ‘0’ data bit is encoded as ‘000’ and a ‘1’ data bit is encoded as ‘111’.
- 8. How does it reduce the error? ❏ The decoder is taking blocks of n bits. ❏ The decoder expects all n bits to have the same value ❏ When the n bits in a block do not have the same value, the decoder detects an error ❏ n-redundancy coding can correct up to (n-1)/2 bits in a code
- 9. Correction Abilities of Codes
- 11. Hamming Code ❏ Hamming codes can correct one-bit errors ❏ 2r >= n + r + 1 , r=redundancy bits n=data bits
- 12. Redundancy bits calculation r1 will take care of these bits r2 will take care of these bits r4 will take care of these bits r8 will take care of these bits
- 14. Error Correction using hamming code
- 15. Reed Muller Code:R(1,3) One of the interesting things about these codes is that there are several ways to describe them and we shall look at one of these- 1st order Reed Muller R(1,3) which can correct one bit error.
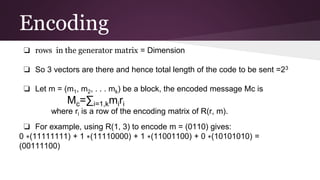
- 16. Contd.. Need a Generator matrix Dimension is
- 17. Encoding ❏ rows in the generator matrix = Dimension ❏ So 3 vectors are there and hence total length of the code to be sent =23 ❏ Let m = (m1, m2, . . . mk) be a block, the encoded message Mc is Mc=∑i=1,kmiri where ri is a row of the encoding matrix of R(r, m). ❏ For example, using R(1, 3) to encode m = (0110) gives: 0 ∗(11111111) + 1 ∗(11110000) + 1 ∗(11001100) + 0 ∗(10101010) = (00111100)
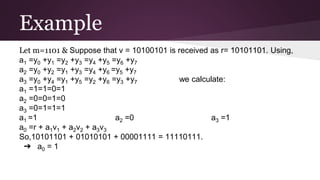
- 18. Decoding ❏ The rows of this matrix are basis vectors for the code v0, v1,v2 and v3. ❏ Any vector v of the code is a linear combination of these v = a0v0+a1v1+a2v2 + a3v3 ❏ If no errors occur, a received vector r = (y0, y1, y2, y3, y4, y5, y6,y7) a1 =y0 +y1 =y2 +y3 =y4 +y5 =y6 +y7 a2 =y0 +y2 =y1 +y3 =y4 +y6 =y5 +y7 a3 =y0 +y4 =y1 +y5 =y2 +y6 =y3 +y7 ❏ If one error has occurred in r, then when all the calculations above are made, 3 of the 4 values will agree for each ai, so the correct value will be obtained by majority decoding. a0 =r + a1v1 + a2v2 + a3v3
- 19. Example Let m=1101 & Suppose that v = 10100101 is received as r= 10101101. Using, a1 =y0 +y1 =y2 +y3 =y4 +y5 =y6 +y7 a2 =y0 +y2 =y1 +y3 =y4 +y6 =y5 +y7 a3 =y0 +y4 =y1 +y5 =y2 +y6 =y3 +y7 we calculate: a1 =1=1=0=1 a2 =0=0=1=0 a3 =0=1=1=1 a1 =1 a2 =0 a3 =1 a0 =r + a1v1 + a2v2 + a3v3 So,10101101 + 01010101 + 00001111 = 11110111. ➔ a0 = 1
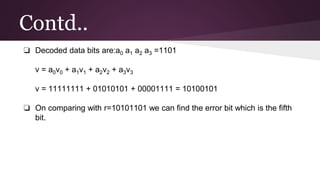
- 20. Contd.. ❏ Decoded data bits are:a0 a1 a2 a3 =1101 v = a0v0 + a1v1 + a2v2 + a3v3 v = 11111111 + 01010101 + 00001111 = 10100101 ❏ On comparing with r=10101101 we can find the error bit which is the fifth bit.
- 21. References ❏ Reed-Muller Error Correcting Codes by Ben Cooke: ❏ http://citeseerx.ist.psu.edu/viewdoc/download?doi=10. 1.1.208.440&rep=rep1&type=pdf ❏ Error Correction Code by Todd K Moon ❏ Hamming Block Codes: http://web.udl.es/usuaris/carlesm/docencia/xc1/Treba lls/Hamming.Treball.pdf
- 22. End of the presentation ThankYou Akshit Jain 2013124 Nitin Varun 2013070
Editor's Notes
- #3: This topic is motivated by the problem of communicating reliably over noisy chan- nels — where the data sent over the channel may come out corrupted on the other end, butbut the receiver wasn’t able to correct the errors and recover the original message. The data is transmitted in the form of binary bits 1’s and 0’s.The encoder converts the message in binary and is transmitted by the transmitter.
- #4: During the transmission the data due to noise or multipath propogation may get corrupted i.e the bits may flip or lost.
- #5: These are the basically the forms of data transmitted and the errors
- #6: The solution to the problem is chanel coding i.e error correction by encoding the message with some redundant bits and making the receiver side decode the message.This will prevent the continuous call to retransmission and hence save bandwidth and time and cost.
- #7: Block codes are one of the kind of methods of error correction.In these methods we divide our message into equally sized blocks which is called data words. And in it we also add extra bits which is called redundant bits to the original data which will be used later to correct errors in the message.we will discuss two block codes methods Hamming codes and Reed Muller.
- #8: Before discussing humming and reed muller let’s first discuss one of the simplest block codes Redundancy coding.In it we send each bits multiple times depending upon redundancy level. As we can see from given example we want to send 100 and we encoded our message by repeating each bit 3 times
- #9: Now how does it reduces error. the decoder will take blocks of n bits depending upon our redundancy level. and will check bits in each block if all the bits are not same in a block then there is an error and it will check for the majority bits in the block and select that bit. So basically we know that for n bits the majority bit will be that bit which occurs more than n -1 /2 times.if there are less than or equal to n-1 /2 errors in a block then it can correct that errors.
- #11: here we can see how redundant coding is useful in reducing errors in received messages.
- #12: the hamming code can correct upto one bit errors.Suppose we want to send n bits then according to this equation we can detect the number of redundancy bits required to detect and correct that error. From the figure We arrange all these bits in a pattern and the redundancy bits are arranged on the 2^ positions.This is till the no. of redundancy bits gets completed and then we arrange the data bits at remaining positions.
- #13: [Look at the figure] the parity bits are calculated using the data bits and they are used in some order and here it is explain for each parity bit.
- #14: Lets see an example
- #15: Suppose the code received is erroraneous and we know the error is at bit 7 but the receiver doesn’t know that.So,how will it find it.Let’s see. Calculate the check bits using the parity bits [sort of C0,C1,C2] .Arrange it like this and Take these calculated check bits together and get the number.That bit will be corrupted.
- #16: Now lets see the last code which is reed muller and it is the most interesting and the complex one. here we are explain only first order reed muller code of block size of 2 ^ 3 bits which can correct one bit error.
- #17: this is a generation matrix and this the dimension equation which are required in generating the code
- #18: the encoding matrix is created by putting the first row as one and then adding k-1 rows. k is the dimension of reed muller code and which also specify the amount of data bits which sent in one block.
- #19: The rows of the matrix are represented as v0,v1,v2,v3. The block of bits which we will send is called a vecotr and is represented as [equation] Suppose the received vector is r as shown Then we will decode this vector using an algorithm.These are the equations and they are formed basically by using the characterstic equations and these are--- Now these bits are calculated using the majority bits in the four characterstic equations for each bit a0 to a3 Now this is the reason the code detects only one error.As if only one bit wrong then only one equation is affected for each data bit and hence can find the majority. a0 is calculated using the majorith in the a0 equation
- #20: a0 is




