TechTalk 2021: Peran IT Security dalam Penerapan DevOps
Di Indonesia, 19,4% perusahaan sudah mulai menggunakan layanan cloud publik. Stapi sering kali saat perusahan sudah mengadopsi cloud, mereka baru menyadari betapa rumitnya penerapan cloud. Akibatnya, banyak perusahaan yang stuck dalam operasional aplikasi yang baru ini. Hadirlah DevOps yang memberi layanan lebih cepat dan mendorong inovasi sekaligus meningkatkan produktivitas, komunikasi, dan keterlibatan karyawan. Tapi hadirnya layanan yang lebih cepat membuat risiko dalam penerapan aplikasi meningkat sebesar 53% upaya pencurian data menyasar aplikasi itu sendiri. Oleh karena itu, sangat penting bagi perusahaan untuk mengubah mindset dari menerapkan keamanan untuk kepatuhan ke metode yang lebih proaktif dengan memanfaatkan prinsip-prinsip DevOps dalam tool dan proses keamanan mereka. Hmm jadi penasaran bagaimana sih memaksimalkan peran keamanan dalam penerapan Devops supaya berjalan dengan lacar? Hal ini akan kita bahas bersama 2 orang pembicara yang expert dibidangnya, yaitu Rei Munisati (Head of IT Security & Risk Compliance, Home Credit Indonesia) dan Taro Lay (Co-Founder Kalama Cyber Security) pada Tech Talk 2021 Live dengan tema "Peran IT Security dalam Penerapan DevOps."




































Recommended




























































More Related Content
What's hot (20)








































Similar to TechTalk 2021: Peran IT Security dalam Penerapan DevOps (20)










































More from DicodingEvent (20)








































Recently uploaded (20)


































TechTalk 2021: Peran IT Security dalam Penerapan DevOps
- 1. Security in DevOps Taro Lay (賴天騎) Co-Founder – Kalama Cyber
- 2. Taro Lay (賴天騎) Cyber Security Evangelist Director of Professional Services at PT. Seraphim Digital Technology Founder of Kalama Cyber Foundation Professional penetration tester Digital security consultant Been around in Digital Security arena around 30 years Dedicate 25% his time for digital security research @kalama_security @TaroLay Who Am I
- 3. Security Essentials Security Foundation • Establish a sound security policy as the “foundation” for design • Treat security as an integral part of the overall system design. • Delineate the physical and logical security boundaries governed by associated security policies • Train developers on secure software
- 4. Security Essentials Risk Based • Reduce risk to an acceptable level • Assume external systems are insecure • Implement tailored system security measures to meet goals • Protect information while processed, in transit, and in storage. • Consider custom products to achieve adequate security • Protect against all likely classes of “attacks”
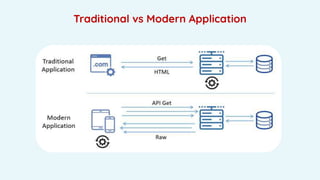
- 6. Traditional vs Modern Application
- 7. Monolithic vs Micro Services
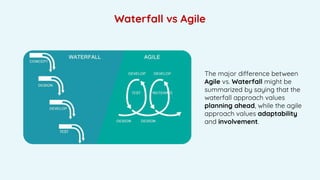
- 8. The major difference between Agile vs. Waterfall might be summarized by saying that the waterfall approach values planning ahead, while the agile approach values adaptability and involvement. Waterfall vs Agile
- 9. Dev-Ops
- 10. Dev- Sec -Ops
- 11. Application Security Layers App level security (libs, code, data) OS / Network / Physical Access Intra-services communication (auth, azn, TLS) Hypervisor, images (VM/Docker)
- 12. Security Testing in SDLC
- 13. Security Testing in SDLC
- 15. OWASP Top 10 - 2021 A1-Broken Access Control A2-Cryptographic Failures A3-Injection A4-Insecure Design A5-Security Misconfiguration A6-Vulnerable and Outdated Components A7-Identification and Authentication Failure A8-Software and Data Integrity Failures A9-Security Logging and Monitoring Failures A10-Server-side Request Forgery (SSRF)
- 16. Bridging the gaps Common goals Streamlined Workflow Integrated Tools ● Security Training ● Lunch and learn ● Lingo and terminology ● Agile development ● Ticketing system ● Continuous integration
- 17. Cost of Flaw
- 18. TOTAL POTENTIAL SECURITY ISSUES ● Null pointer dereference ● Threading issues ● Code quality issues ● Issues in dead code ● Insecure crypto functions ● Issues in back-end application code ● Complex injection issues ● Issues in non-web app code SAST Only ● Environment configuration issues ● Patch level issues ● Runtime privileges issues ● Authentication issues ● Protocol parser issues ● Session management issues ● Issues in 3rd party web components ● Cross-site request forgery ● Malware analysis DAST Only ● SQL Injection ● Cross Site Scripting ● HTTP Response Splitting ● OS Commanding ● LDAP Injection ● XPath Injection ● Path Traversal ● Buffer Overflows ● Format String Issues ● Etc. DAST & SAST Application Security Issues
- 19. Thankyou! Taro Lay, (賴天騎) Cybersecurity Evangelist <[email protected]> @kalama_security @TaroLay
- 21. IT Sec's Role in the Implementation of DevOps Rei Munisati ( Head of IT Security & Risk Compliance – Home Credit Indonesia )
- 22. Let’s Get To Know Each Other Rei Munisati Head of IT Security & Risk Compliance @ Home Credit Indonesia Experienced in Banking, Insurance and Technology industries focusing on Information Security, Data Privacy, GRC, Third Party Security, Audit & Remediation Management roles.
- 23. What is DevSecOps? The main objective of DevSecOps is to automate, monitor and apply security at all phases of the software lifecycle, i.e., plan, develop, build, test, release, deploy, operate and monitor. Applying security at every stage of the software development process enables continuous integration, reducing the cost of compliance and delivering software more rapidly
- 24. DevSecOps: How important is it really? • Agile took us from months to days to deliver software • DevOps took us from months to minutes to deploy software • More applications are mission critical • Now security has become the bottleneck
- 25. The Evolution of Security Tools Duration 2-4 weeks 1-2 weeks Continuous and Real-time Penetration Testing Tools • Port Scanners • Vulnerability Scanner • Exploitation Tools Audience • Security Professionals Secure SDLC Tools • Code Security Scanners • Dynamic Security Scanners • Vulnerability Scanners Audience • Security Professionals in Enterprise Security Teams DeVSecOps Tools • Code Security Scanners • Interactive Security Scanners • Runtime Application Self Protection Audience • Developers in Product Teams
- 26. Phase of DevSecOps • Secret Scanning • Software Composition Analysis (SCA) • Static Analysis Security Testing (SAST) • Dynamic Analysis Security Testing (DAST) • Security in Infrastructure as Code • RunTime Application Self-Protection (RASP) • Vulnerability Management (VA) • Alert and Monitoring in Security For Starter in DevSecOps
- 27. Secret Scanning • Sensitive information such as the access keys, access tokens, SSH keys, etc. • Work on pure Regex-based approach for filtering sensitive data Tools : 1. Detect-Secrets 2. Truffle Hog
- 28. Software Composition Analysis • Software Composition Analysis (SCA) is an application security methodology for managing open-source components. • Disc over all related components, their supporting libraries, and their direct and indirect dependencies Tools : 1. Snyk ( All ) 2. Find-sec-bugs ( Java ) 3. RetireJS ( JavaScript / NodeJS ) 4. Bundler-audit ( Ruby ) 5. Bandit, safety ( Python )
- 29. Static Analysis Security Testing • White-box security testing using automated tools • Useful for weeding out low-hanging fruits like SQL Injection, Cross-Site Scripting, insecure libraries, etc. • Needs manual oversight for managing false-positives Tools : SonarQube
- 30. Dynamic Analysis Security Testing • Black/Grey-box security testing using automated tools • DAST will help in picking out deployment specific issues • Results from DAST and SAST can be compared to weed out false-positives “ We can use tools pentest but must support cmd and export file “ Tools : 1. Nmap 2. Nikto 3. SQLMap 4. Nessus 5. Burpsuite
- 31. Security in Infrastructure Code • Infrastructure as a code allows you to document and version control the infra • It also allows you to perform audit on the infrastructure • Environment is as secure as the base image container • Hardening your server with automation ( Compliance as Code) Tools : 1. Ansible 2. Inspec 3. Clair 4. Anchore 5. Dockscan Infrastructure Code Image Scanning Hardening
- 32. Vulnerability Management • A central dashboard is required to normalize the data • Vulnerability Management System can then be integrated to bug tracking system Tools : 1. Defect Dojo 2. Archery
- 33. Alert and Monitoring Security Monitoring is needed for two end goals • Understand if our security controls are effective • What and where we need to improve "Detect, Mitigation ,and Maintain Continuous Security" Tools : 1. Grafana 2. elk 3. Dynatrace 4. Aqua Security 5. Imperva
- 35. Inject Security in Process DevOps Pre-Commit Hooks IDE Plugins Developer Secrets Management Code Repository SAST SCA Pre-Build DAST Post-Build Manual Web Application Pentesting QA/Staging Sec in IaC Compliance as Code Alerting and Monitoring Production Build Artifact versioning against code commits Artifact Repository CI/CD Server V u l n e r a b i l i t y M a n a g e m e n t
- 36. Sample Pipeline Build Artifactory Deploy Staging Setup Staging Deploy UAT Test PROD Setup PROD Deploy Approval PROD Deploy Start End DevOps Pipeline Build Artifactory Deploy SAST (Dependency Check) Stagin g Setup Staging Deploy UAT Test DAST PROD Setup INFRA Setup INFRA Scan Compliance Scan PROD Deploy Approval PROD Deploy WAF Deploy Start End DevSecOps Pipeline
- 37. Benefits & Conclusions ✔ Integrate Security via Tools ✔ Security as Code ✔ Faster Release Cycles ✔ Prevent Security Bugs in PROD ✔ Shorter Feedback Cycle Developer Secret Management Pre-Build Post-Build Deploy Test Deploy PROD Pre-Commit H. SCA SAST DAST Security in IAC
- 38. THANK YOU





