Ten common mistakes made in Function Java - iSense Java Summit
- 1. Ten common mistakes made with Function Java Brian Vermeer (@BrianVerm)Java Summit
- 6. Doing too much in a single lambda
- 7. Lambda Expression In computer programming, a lambda expression is a function definition that is not bound to an identifier. Anonymous functions are often:[1] • arguments being passed to higher-order functions, or • used for constructing the result of a higher-order function that needs to return a function.
- 8. Lambda in Java Anonymous Inner functions Satisfy a Functional Interface They only exist in runtime Single Line <input> -> <output> or Block <input> -> { function body }
- 9. Example public void execute() { Beer grolsch = new Beer("Grolsche", 4.3); String result = handleBeer(grolsch, beer -> grolsch.getName() + "-" + grolsch.getAlcohol()); System.out.println(result); } private String handleBeer(Beer beer, Function<Beer, String> func) { System.out.println("handling beer " + beer.getName()); return func.apply(beer); } //Output : Grolsche-4.3
- 10. Don’t do Block Lambda beer -> { String name; if (beer.getName().contains(" ")) { name = beer.getName().replace(" ", ""); } else { name = beer.getName(); } try { name += Integer.parseInt(beer.getAlcoholPrecentage().toString()); } catch (NumberFormatException nfe) { name += beer.getAlcoholPrecentage(); } return name; }
- 11. Transform to a methode private String createFullName (Beer beer){ String name; if (beer.getName().contains(" ")) { name = beer.getName().replace(" ", ""); } else { name = beer.getName(); } try { name += Integer.parseInt(beer.getAlcoholPrecentage().toString()); } catch (NumberFormatException nfe) { name += beer.getAlcoholPrecentage(); } return name; } handleBeer(grolsch, this::createFullName);
- 13. A stream is NOT a data structure
- 14. A stream is NOT a data structure A stream is NOT a data structure
- 15. What is Stream ( in Java) Flow of data derived from a Collection Can create a pipeline of function that can be evaluated Intermediate result Lazy evaluated by nature Can transform data, cannot mutate data
- 16. JAVA Streams stringLists.stream() .map(str -> str.toUpperCase()) .collect(Collectors.toList()); Intermediate filter distinct map flatMap Terminal reduce collect toArray count max min limit skip sorted peek findAny findFirst forEach allMatch anyMatch
- 17. List<Beer> beers = getBeers(); Stream<Beer> beerStream = beers.stream(); beerStream.forEach(b ->System.out.println(b.getName())); //1 beerStream.forEach(b ->System.out.println(b.getAlcohol())); //2 Only use a Stream once Line 2 will give: java.lang.IllegalStateException: stream has already been operated upon or closed
- 18. public Stream<Beer> getMeMyBeers() public void execute() { getMeMyBeers() //don’t know if it is consumed yet!!!! … } Don’t return a Stream
- 19. Not Consuming a Stream
- 24. List<Beer> beers = List.of(new Beer("Heineken", 5.2), new Beer("Delirium Tremens", 9.0), new Beer("Amstel", 5.1)); beers.stream() .limit(10) .map(i -> i.getAlcohol()) .peek(i -> { if (i > 7.0) throw new RuntimeException(); }); Consume the stream
- 26. List<Beer> beers = List.of(new Beer("Heineken", 5.2), new Beer("Delirium Tremens", 9.0), new Beer("Amstel", 5.1)); beers.stream() .limit(10) .map(i -> i.getAlcohol()) .peek(i -> { if (i > 7.0) throw new RuntimeException(); }) .forEach(System.out::println); Consume the stream 5.2 Exception in thread "main" java.lang.RuntimeException
- 27. Mutable Object
- 28. Functional Programming In computer science, functional programming is a programming paradigma style of building the structure and elements of computer programs that treats computation as the evaluation of mathematical functions and avoids changing-state and mutable data. It is a declarative programming paradigm, which means programming is done with expressions or declarations instead of statements. — wikipedia
- 30. – Kevlin Henney “Asking a question should not change the answer, nor should asking it twice”
- 31. Immutable objects Less moving parts Easier to reason about code No need to keep a mental map of the state an object is in.
- 32. Stream cannot mutate private final List<Beer> beers = List.of(new Beer("Heineken", 5.2), new Beer("Amstel", 5.1)); public void execute() { List<Beer> beersNew = beers.stream() .map(beer -> beer.setName(“foo”)) //not allowed .collect(Collectors.toList()); }
- 33. Stream should not mutate ! private class Beer { String name; Double alcohol; public Beer setName(String name){ this.name = name; return this; } } private final List<Beer> beers = List.of(new Beer("Heineken", 5.2), new Beer("Amstel", 5.1)); public void execute() { List<Beer> beersNew = beers.stream() .map(beer -> beer.setName("foo")) .collect(Collectors.toList()); System.out.println(beers); System.out.println(beersNew); }
- 34. Stream should not mutate ! private class Beer { String name; Double alcohol; public Beer setName(String name){ this.name = name; return this; } } private final List<Beer> beers = List.of(new Beer("Heineken", 5.2), new Beer("Amstel", 5.1)); public void execute() { List<Beer> beersNew = beers.stream() .map(beer -> beer.setName("foo")) .collect(Collectors.toList()); System.out.println(beers); System.out.println(beersNew); }
- 35. Return a new copy private class Beer { String name; Double alcohol; public Beer withName(String name){ return new Beer(name, this.alcohol); } } private final List<Beer> beers = List.of(new Beer("Heineken", 5.2), new Beer("Amstel", 5.1)); public void execute() { List<Beer> beersNew = beers.stream() .map(beer -> beer.withName("foo")) .collect(Collectors.toList()); System.out.println(beers); System.out.println(beersNew); }
- 37. forEach() Terminal functional on a stream. Takes a consumer. Can be used to apply side effects. for-loop without the external iterator
- 38. simple forEach example List<String> names = List.of("James", "Trisha", "Joshua", "Jessica","Simon", “Heather"); names.stream() .map(String::toUpperCase) .forEach(System.out::println);
- 39. mutation with forEach List<Beer> beers = List.of(new Beer("Heineken", 5.2), new Beer("Amstel", 5.1)); beers.stream() .forEach(beer -> beer.setAlcohol(0.0));
- 40. overusing forEach private class Beer { String name; Double alcohol; List<String> reviews; Integer rating; } List<Beer> beers = List.of(new Beer("Heineken", 5.2), new Beer("Amstel", 5.1)); //enrich with ratings beers.stream().forEach(beer -> beer.setRating(findRating(beer.getName()))); //enrich with reviews beers.stream().forEach(beer -> beer.setReviews(findReviews(beer.getName()))); …
- 42. Assignment Beers -> Brewer -> Country I want the first 3 unique brewers countries from the beer library as comma separated String beerLib.stream() .map(Beer::getBrewer) .distinct() .limit(3) .map(Brewer::getCountry) .map(String::toUpperCase) .collect(Collectors.joining(“,”));
- 43. Assignment Beers -> Brewer -> Country I want the first 3 unique brewers countries from the beer library as comma separated String beerLib.stream() .map(Beer::getBrewer) .distinct() .limit(3) .map(Brewer::getCountry) .map(String::toUpperCase) .collect(Collectors.joining(“,”)); // wrong
- 44. Assignment Beers -> Brewer -> Country I want the first 3 unique brewers countries from the beer library as comma separated String beerLib.stream() .map(Beer::getBrewer) .map(Brewer::getCountry) .map(String::toUpperCase) .distinct() .limit(3) .collect(Collectors.joining(“,”)); // correct
- 45. Infinite stream IntStream.iterate(0, i -> ( i + 1) % 2) .distinct() .limit(10) .forEach(i -> System.out.println(i));
- 46. Infinite stream IntStream.iterate(0, i -> ( i + 1) % 2) .distinct() .limit(10) .forEach(i -> System.out.println(i)); // will run forever IntStream.iterate(0, i -> ( i + 1) % 2) .limit(10) .distinct() .forEach(i -> System.out.println(i)); //will terminate
- 47. Infinite stream IntStream.iterate(0, i -> ( i + 1) % 2) .parallel() .distinct() .limit(10) .forEach(i -> System.out.println(i)); // will run forever on all threads.
- 48. Solution 1. Look closely at the order of operations - prevent incorrect answers 2. Only use infinite streams when absolutely necessary. rather use: IntStream.range(0,10); IntStream.rangeClosed(0,10); IntStream.iterate(0, i -> i < 10, i -> i + 1); //java 9 and up
- 50. Optional Java’s implementation of the Maybe Monad Encapsulation to handle possible null value Consider it a wrapper where a value can be absent Force the user to unpack the Optional before using it.
- 51. Optional Optional<String> c = null //please avoid this
- 52. public void execute() { Optional<String> maybeString = getText(); String unpacked = maybeString.get(); } Unpack Optional
- 53. public void execute() { Optional<String> maybeString = getText(); String unpacked = maybeString.get(); } Unpack Optional NoSuchElementException
- 54. public void execute() { Optional<String> maybeString = getText(); String unpacked = maybeString.get(); } Unpack Optional public void execute() { Optional<String> maybeString = getText(); if (maybeString.isPresent()) { String unpacked = maybeString.get(); } } NoSuchElementException
- 55. Unpack Optional public void execute() { Optional<String> maybeString = getText(); maybeString.ifPresent( str -> /* doSomething */ ); } public void execute() { Optional<String> maybeString = getText(); maybeString.map(str -> str + “."); }
- 56. What else ..??
- 57. Alternative flow - orElse() - orElseGet() - orElseThrow()
- 58. orElseThrow public void execute() { Optional<String> maybeString = Optional.empty(); maybeString .map(this::runIfExist) .orElseThrow(() -> new RuntimeException("Optional was empty")); }
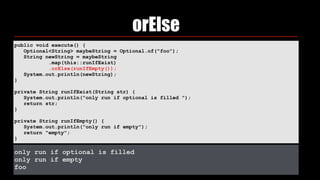
- 59. orElse public void execute() { Optional<String> maybeString = Optional.of("foo"); String newString = maybeString .map(this::runIfExist) .orElse(runIfEmpty()); System.out.println(newString); } private String runIfExist(String str) { System.out.println("only run if optional is filled "); return str; } private String runIfEmpty() { System.out.println("only run if empty"); return "empty"; }
- 60. orElse public void execute() { Optional<String> maybeString = Optional.of("foo"); String newString = maybeString .map(this::runIfExist) .orElse(runIfEmpty()); System.out.println(newString); } private String runIfExist(String str) { System.out.println("only run if optional is filled "); return str; } private String runIfEmpty() { System.out.println("only run if empty"); return "empty"; } only run if optional is filled only run if empty foo
- 61. orElseGet public void execute() { Optional<String> maybeString = Optional.of("foo"); String newString = maybeString .map(this::runIfExist) .orElseGet(() -> runIfEmpty()); System.out.println(newString); } private String runIfExist(String str) { System.out.println("only run if optional is filled "); return str; } private String runIfEmpty() { System.out.println("only run if empty"); return "empty"; }
- 62. orElseGet public void execute() { Optional<String> maybeString = Optional.of("foo"); String newString = maybeString .map(this::runIfExist) .orElseGet(() -> runIfEmpty()); System.out.println(newString); } private String runIfExist(String str) { System.out.println("only run if optional is filled "); return str; } private String runIfEmpty() { System.out.println("only run if empty"); return "empty"; } only run if optional is filled foo
- 63. what else? - When using orElse(x), make sure x doesn’t contain any side effects - Only use orElse() to assign a default value - Use orElseGet() to run an alternative flow
- 64. Exceptions
- 65. Checked Exceptions & Lambda public Beer doSomething(Beer beer) throws IsEmptyException { …} Function <Beer,Beer> fBeer = beer -> doSomething(beer)
- 66. Checked Exceptions & Lambda public Beer doSomething(Beer beer) throws IsEmptyException { …} Function <Beer,Beer> fBeer = beer -> doSomething(beer)
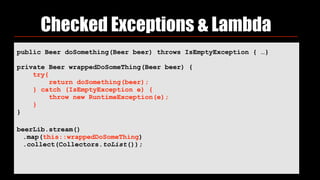
- 67. Checked Exceptions & Lambda public Beer doSomething(Beer beer) throws IsEmptyException { …} beerLib.stream() .map(beer -> { try{ return doSomething(beer); } catch (IsEmptyException e) { throw new RuntimeException(e); } };) .collect(Collectors.toList()); //not very pretty
- 68. Checked Exceptions & Lambda public Beer doSomething(Beer beer) throws IsEmptyException { …} private Beer wrappedDoSomeThing(Beer beer) { try{ return doSomething(beer); } catch (IsEmptyException e) { throw new RuntimeException(e); } } beerLib.stream() .map(this::wrappedDoSomeThing) .collect(Collectors.toList());
- 69. Exception Utility @FunctionalInterface public interface CheckedFunction<T, R> { public R apply(T t) throws Throwable; } public static <T, R> Function<T, R> wrap(CheckedFunction<T, R> function) { return t -> { try { return function.apply(t); } catch (Throwable ex) { throw new RuntimeException(ex); } }; }; beerLib.stream() .map(beer -> wrap(doSomething(beer))) .collect(Collectors.toList());
- 70. Either type public class Either<L, R> { private final L left; private final R right; private Either(L left, R right) { this.left = left; this.right = right; } public static <L,R> Either<L,R> Left( L value) { return new Either(value, null); } public static <L,R> Either<L,R> Right( R value) { return new Either(null, value); } … }
- 71. Either type private Either<Exception, String> canGoWrong(Integer input) { if (input > 10) { return Either.Left(new RuntimeException("larger then 10")); } return Either.Right("["+input+"]"); } List<Either<Exception, String>> canGoWrongs = IntStream.range(0,12) .mapToObj(i -> canGoWrong(i)) .collect(Collectors.toList());
- 72. Either type private Either<Exception, String> canGoWrong(Integer input) { if (input > 10) { return Either.Left(new RuntimeException("larger then 10")); } return Either.Right(“["+input+"]"); } List<Either<Exception, String>> canGoWrongs = IntStream.range(0,12) .mapToObj(i -> canGoWrong(i)) .collect(Collectors.toList()); canGoWrongs.stream() .map(e -> e.mapRight(s -> s.toUpperCase())) .flatMap(o -> o.map(Stream::of).orElseGet(Stream::empty)) .forEach(System.out::println);
- 74. //java 9 List myList = List.of(1,2,3,4,5) //pre Java9 List myList = Arrays.asList(new String[] {“a”,"b","c"}); Creating collections
- 75. //java 9 List myList = List.of(1,2,3,4,5) //pre Java9 List myList = Arrays.asList(new String[] {"a","b","c"}); // since Java 8 List myList = Stream.of("a","b","c","d").collect(Collectors.toList()); Creating collections
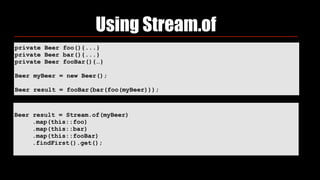
- 76. private Beer foo(){...} private Beer bar(){...} private Beer fooBar(){…} Beer myBeer = new Beer(); Beer result = fooBar(bar(foo(myBeer))); Using Stream.of
- 77. private Beer foo(){...} private Beer bar(){...} private Beer fooBar(){…} Beer myBeer = new Beer(); Beer result = fooBar(bar(foo(myBeer))); Using Stream.of Beer result = Stream.of(myBeer) .map(this::foo) .map(this::bar) .map(this::fooBar) .findFirst().get();
- 78. String sentence = "The quick fox jumps over the lazy dog. "; String[] words = sentence .trim() .toUpperCase() .split(" "); for(String word : words) { System.out.println(word); } Using Stream.of
- 79. String sentence = "The quick fox jumps over the lazy dog. "; String[] words = sentence .trim() .toUpperCase() .split(" "); for(String word : words) { System.out.println(word); } Stream.of(sentence) .map(String::trim) .map(String::toUpperCase) .map(str -> str.split(" ")) .flatMap(array -> Arrays.stream(array)) .forEach(System.out::println); Using Stream.of







![Lambda Expression
In computer programming, a lambda expression is a function definition
that is not bound to an identifier. Anonymous functions are often:[1]
• arguments being passed to higher-order functions, or
• used for constructing the result of a higher-order function that
needs to return a function.](https://image.slidesharecdn.com/tenmistakesfunctionaljavaisensejavasummit-180517061150/85/Ten-common-mistakes-made-in-Function-Java-iSense-Java-Summit-7-320.jpg)




























































![Either type
private Either<Exception, String> canGoWrong(Integer input) {
if (input > 10) {
return Either.Left(new RuntimeException("larger then 10"));
}
return Either.Right("["+input+"]");
}
List<Either<Exception, String>> canGoWrongs = IntStream.range(0,12)
.mapToObj(i -> canGoWrong(i))
.collect(Collectors.toList());](https://image.slidesharecdn.com/tenmistakesfunctionaljavaisensejavasummit-180517061150/85/Ten-common-mistakes-made-in-Function-Java-iSense-Java-Summit-71-320.jpg)
![Either type
private Either<Exception, String> canGoWrong(Integer input) {
if (input > 10) {
return Either.Left(new RuntimeException("larger then 10"));
}
return Either.Right(“["+input+"]");
}
List<Either<Exception, String>> canGoWrongs = IntStream.range(0,12)
.mapToObj(i -> canGoWrong(i))
.collect(Collectors.toList());
canGoWrongs.stream()
.map(e -> e.mapRight(s -> s.toUpperCase()))
.flatMap(o -> o.map(Stream::of).orElseGet(Stream::empty))
.forEach(System.out::println);](https://image.slidesharecdn.com/tenmistakesfunctionaljavaisensejavasummit-180517061150/85/Ten-common-mistakes-made-in-Function-Java-iSense-Java-Summit-72-320.jpg)

![//java 9
List myList = List.of(1,2,3,4,5)
//pre Java9
List myList = Arrays.asList(new String[] {“a”,"b","c"});
Creating collections](https://image.slidesharecdn.com/tenmistakesfunctionaljavaisensejavasummit-180517061150/85/Ten-common-mistakes-made-in-Function-Java-iSense-Java-Summit-74-320.jpg)
![//java 9
List myList = List.of(1,2,3,4,5)
//pre Java9
List myList = Arrays.asList(new String[] {"a","b","c"});
// since Java 8
List myList = Stream.of("a","b","c","d").collect(Collectors.toList());
Creating collections](https://image.slidesharecdn.com/tenmistakesfunctionaljavaisensejavasummit-180517061150/85/Ten-common-mistakes-made-in-Function-Java-iSense-Java-Summit-75-320.jpg)

![String sentence = "The quick fox jumps over the lazy dog. ";
String[] words = sentence
.trim()
.toUpperCase()
.split(" ");
for(String word : words) {
System.out.println(word);
}
Using Stream.of](https://image.slidesharecdn.com/tenmistakesfunctionaljavaisensejavasummit-180517061150/85/Ten-common-mistakes-made-in-Function-Java-iSense-Java-Summit-78-320.jpg)
![String sentence = "The quick fox jumps over the lazy dog. ";
String[] words = sentence
.trim()
.toUpperCase()
.split(" ");
for(String word : words) {
System.out.println(word);
}
Stream.of(sentence)
.map(String::trim)
.map(String::toUpperCase)
.map(str -> str.split(" "))
.flatMap(array -> Arrays.stream(array))
.forEach(System.out::println);
Using Stream.of](https://image.slidesharecdn.com/tenmistakesfunctionaljavaisensejavasummit-180517061150/85/Ten-common-mistakes-made-in-Function-Java-iSense-Java-Summit-79-320.jpg)















































![Progecad 2025 Professional Cracked [Latest]](https://cdn.slidesharecdn.com/ss_thumbnails/1-250523110414-1ac543c0-250523121349-2f0f5a8d-thumbnail.jpg?width=560&fit=bounds)













