Terraform Unleashed - Crafting Custom Provider Exploits for Ultimate Control
0 likes87 views
Video and presentation on Youtube channel - https://www.youtube.com/cloudvillage_dc
1 of 18
Download to read offline

















Ad
Recommended
Terraform Abstractions for Safety and Power

Terraform Abstractions for Safety and PowerCalvin French-Owen https://www.youtube.com/watch?v=IeweKUdHJc4
My presentation from Hashiconf 2017, discussing our use of Terraform, and our techniques
to help make it safe and accessible.
Linode_eBook_Declarative_Cloud_Infrastructure_Management_with_Terraform.pptx



Linode_eBook_Declarative_Cloud_Infrastructure_Management_with_Terraform.pptxAkwasiBoateng6 This document provides an overview of using Terraform to manage cloud infrastructure. It discusses what infrastructure as code (IaC) is and how Terraform supports IaC principles. Key benefits of Terraform include allowing infrastructure to be version controlled and defined declaratively in code. The document also covers basic Terraform concepts like providers, resources, and the HashiCorp configuration language (HCL). It provides an example of how Terraform can be used to define and provision a web application infrastructure on Linode.
RIMA-Infrastructure as a code with Terraform.pptx



RIMA-Infrastructure as a code with Terraform.pptxMrJustbis RIMA is a project that aims to automate infrastructure using modern DevOps strategies like CI/CD pipelines. It will implement infrastructure as code with Terraform and configure systems with Ansible. The goal is to reduce costs and failures by replacing manual processes with automated solutions for provisioning, configuration management, and code quality checks.
Terraform Definition, Working and Challenges it Overcomes



Terraform Definition, Working and Challenges it OvercomesEyeglass Repair USA Terraform is an infrastructure-as-code tool that allows you to create Cloud and on-prem resources using a format that is readable by humans. Learn about its working and the problems it overcomes.
Terraform Automation in Azure Cloud Online Training in Hyderabad.pptx



Terraform Automation in Azure Cloud Online Training in Hyderabad.pptxsivavisualpath Visualpath provides top-quality Terraform Automation in Azure Cloud Online Training conducted by real-time experts. Our training is available worldwide, and we offer daily recordings and presentations for reference. Call us at +91-9989971070 for a free demo.
WhatsApp: https://www.whatsapp.com/catalog/919989971070/
Visit blog: https://visualpathblogs.com/
Visit: https://www.visualpath.in/terraform-online-training-in-hyderabad.html
Terraform modules and some of best-practices - March 2019



Terraform modules and some of best-practices - March 2019Anton Babenko This document summarizes best practices for using Terraform modules. It discusses:
- Writing resource modules to version infrastructure instead of individual resources
- Using infrastructure modules to enforce tags, standards and preprocessors
- Calling modules in a 1-in-1 structure for smaller blast radii and dependencies
- Using Terragrunt for orchestration to call modules dynamically
- Working with Terraform code by using lists, JSONnet, and preparing for Terraform 0.12
Terraform vs Pulumi



Terraform vs PulumiHoaiNam307 Terraform and Pulumi are both infrastructure as code tools but they differ in key ways. Terraform uses HCL syntax and focuses on infrastructure resources while Pulumi uses regular programming languages to define cloud resources and applications together. Pulumi supports more providers but Terraform is easier to use for developers with system administration experience. Both tools use state files to track infrastructure changes but Pulumi state is managed through its CLI and service while Terraform uses local or remote state files.
Hashicorp-Terraform_Packer_Vault-by Sushil



Hashicorp-Terraform_Packer_Vault-by SushilSushil Kumar This document provides an overview of the HashiCorp toolchain, including Terraform, Packer, and Vault. Terraform allows users to define and provision infrastructure across multiple cloud providers like AWS, Azure, and Google Cloud through configuration files. Packer is used to automate the creation of machine images. Vault securely stores secrets like passwords and API keys that can then be retrieved and injected into apps and infrastructure provisioned by Terraform. The presenter demonstrates deploying resources across providers using Terraform and building a custom AMI with Packer. He emphasizes that the HashiCorp tools allow infrastructure to be automated, versioned, and secured through secrets management.
Introduction to Terraspace Presentation.



Introduction to Terraspace Presentation.Knoldus Inc. Terraspace Is A Terraform Framework that optimizes for infrastructure-as-code happiness. It provides an organized structure, and conventions over configurations, keeps your code DRY, and adds convenient tooling. You can keep your code DRY. Terraspace builds your Terraform project with the common app and config/terraform structure that gets built each deployment.
Introduction to Terra space Presentation



Introduction to Terra space PresentationKnoldus Inc. Terraspace Is A Terraform Framework that optimizes for infrastructure-as-code happiness It provides an organized structure, conventions over configurations, keeps your code DRY, and adds convenient tooling. You can keep your code DRY. Terraspace builds your Terraform project with common app and config/terraform structure that gets built each deploy.
Terraform Automation in Azure Online Training Institute in Hyderabad.pptx



Terraform Automation in Azure Online Training Institute in Hyderabad.pptxsivavisualpath Visualpath provides top-quality Terraform Automation in Azure Cloud Online Training conducted by real-time experts. Our training is available worldwide, and we offer daily recordings and presentations for reference. Call us at +91-9989971070 for a free demo.
WhatsApp: https://www.whatsapp.com/catalog/919989971070/
Visit blog: https://visualpathblogs.com/
Visit: https://www.visualpath.in/terraform-online-training-in-hyderabad.html
Terraform day 1



Terraform day 1Kalkey This document provides an overview and tutorial on using Terraform for DevOps. It introduces Terraform as a tool for defining and managing infrastructure as code. It then covers installing Terraform, deploying AWS infrastructure like EC2 instances using Terraform configurations, managing variables and outputs, using provisioners, organizing code with modules and workspaces, and managing Terraform state. The document aims to help users get started with Terraform for infrastructure as code.
Building infrastructure as code using Terraform - DevOps Krakow



Building infrastructure as code using Terraform - DevOps KrakowAnton Babenko This document provides an overview of a DevOps meetup on building infrastructure as code using Terraform. The agenda includes Terraform basics, frequent questions, and problems. The presenter then discusses Terraform modules, tools, and solutions. He addresses common questions like secrets handling and integration with other tools. Finally, he solicits questions from the audience on Terraform use cases and challenges.
Terraform with OCI



Terraform with OCIJeSam Kim This document provides an introduction and overview of using Terraform with Oracle Cloud Infrastructure (OCI). It discusses installing Terraform, configuring providers and resources, and demonstrates creating an OCI compute instance through Terraform. Key points include:
- Terraform is an infrastructure as code tool that can be used to provision and manage resources across multiple cloud providers, including OCI.
- The document walks through installing Terraform on Oracle Linux, configuring the OCI provider, and defining resources like compute instances in configuration files.
- A demo is shown creating an OCI compute instance named "TEST" through a Terraform plan and apply, validating the infrastructure provisioning.
Terraform - Taming Modern Clouds



Terraform - Taming Modern CloudsNic Jackson Slides form Config Management Camp, looking at how you can take a collaborative GitFlow approach to Terraform using Remote State, Modules and Dynamically Generated Credentials using Vault
OracleBeer_Terraform_soe.pdf



OracleBeer_Terraform_soe.pdfStefan Oehrli Click, click, click and I have already built my infrastructure in the cloud. But do you still know what you have built afterwards? With Infrastructure as Code or Terraform, cloud resources can be built, changed and deleted again relatively easily. This is ideal for dynamically building test and lab environments. But how do you make sure that a wrong command in the Terraform configuration does not dismantle the whole infrastructure again or shoot the costs up to astronomical heights? Where is the boundary between IaC testing and the actual release tests on the generated systems? Using Accenture Lab and training environments as an example, I will show various aspects around deploying cloud based infrastructures with Terraform. This course presentation will be complemented with demos and examples.
Infrastructure as Code with Terraform



Infrastructure as Code with TerraformPedro J. Molina Session talk presented at Innosoft 2022.11.11 University of Sevilla.
Presented the concept of Infrastructure as Core and its practical approach using Hashicorp Terraform a a tool to provision in the cloud. Examples with AWS are provided in a Guthub repository.
Debasihish da final.ppt



Debasihish da final.pptKalkey This document provides an overview of Terraform including its key features, installation process, and common usage patterns. Terraform allows infrastructure to be defined as code and treated similarly to other code. It generates execution plans to avoid surprises when provisioning resources. Complex changes can be automated while avoiding human errors. The document covers installing Terraform, deploying AWS EC2 instances, variables, outputs, modules, and workspaces. It demonstrates how Terraform can be used to provision and manage infrastructure in a safe, efficient manner.
presentation @ docker meetup



presentation @ docker meetupDaniël van Gils This document discusses Docker and the Docker ecosystem. It provides descriptions of various tools related to Docker including orchestration, service discovery, networking, data management, and monitoring tools. It also discusses some companies and projects that are part of the Docker ecosystem like Docker itself, CoreOS, Kubernetes, Marathon, Consul, etcd, and others.
Hashicorp-Certified-Terraform-Associate_V1



Hashicorp-Certified-Terraform-Associate_V1kodecloud86 Terraform is an open-source Infrastructure as Code (IaC) tool created by HashiCorp that allows users to define and provision data center infrastructure using a declarative configuration language known as HashiCorp Configuration Language (HCL) or JSON.
Key Features of Terraform:
Declarative Configuration: You describe what your infrastructure should look like, and Terraform figures out how to achieve that state.
Execution Plans: Terraform generates an execution plan showing what will happen when you apply your configurations, helping you understand changes before they take effect.
Resource Management: It manages a wide variety of service providers including AWS, Azure, Google Cloud, and many others, allowing for cross-cloud infrastructure management.
State Management: Terraform maintains a state file that helps track the current state of your infrastructure, which is crucial for planning and applying changes.
Modules: These are reusable components that can help encapsulate resources for better organization and sharing.
Provider Ecosystem: Terraform supports a wide range of providers and allows users to write custom providers to extend its capabilities.
Final terraform



Final terraformGourav Varma This document provides an overview of Terraform including its key features and how to install, configure, and use Terraform to deploy infrastructure on AWS. It covers topics such as creating EC2 instances and other AWS resources with Terraform, using variables, outputs, and provisioners, implementing modules and workspaces, and managing the Terraform state.
Terraform Basics



Terraform BasicsMohammed Fazuluddin As part of this presentation we covered basics of Terraform which is Infrastructure as code. It will helps to Devops teams to start with Terraform.
This document will be helpful for the development who wants to understand infrastructure as code concepts and if they want to understand the usability of terrform
Infrastructure as Code with Terraform.pptx



Infrastructure as Code with Terraform.pptxSamuel862293 Terraform is an infrastructure as code tool that allows infrastructure to be provisioned and managed declaratively through code. It aims to streamline operations by automating infrastructure provisioning and management, reducing manual efforts and errors. The document discusses how Terraform works, including defining infrastructure through configuration files, connecting to providers to provision resources, and best practices for using Terraform like version control and remote state management. A demo is also provided to illustrate provisioning an EC2 instance with Terraform.
What are the Benefits of Using Terraform?



What are the Benefits of Using Terraform?Ravendra Singh Terraform is an open-source provisioning mechanism from HashiCorp registered in the Go language. It is utilized for the construction, modification, and versioning of infrastructure, safely and efficiently. Provisioning tools are accountable for the creation of servers and associated assistance.
Deploy resources on Azure using IaC (Azure Terraform)



Deploy resources on Azure using IaC (Azure Terraform)George Grammatikos I introduced Azure Terraform and IAC solutions. As part of the presentation, I demonstrate how to deploy resources to Azure using Azure Terraform.
Infrastructure as code, using Terraform



Infrastructure as code, using TerraformHarkamal Singh This document discusses using Terraform to automate infrastructure provisioning and management. It begins with an introduction to infrastructure as code and Terraform. It then discusses some of the benefits of using Terraform like increased productivity, consistent deployments, and faster iteration. The document provides examples of Terraform configuration files and demonstrates basic Terraform commands like init, plan, apply, and destroy.
Instant download Terraform in Depth (MEAP V01) Robert Hafner pdf all chapter



Instant download Terraform in Depth (MEAP V01) Robert Hafner pdf all chapterakceyohros Obtain Terraform in Depth (MEAP V01) Robert Hafner instantly after payment at https://ebookmeta.com/product/terraform-in-depth-meap-v01-robert-hafner. Check out additional textbooks and ebooks in https://ebookmeta.com Full chapter PDF download.
Devops Columbia October 2020 - Gabriel Alix: A Discussion on Terraform



Devops Columbia October 2020 - Gabriel Alix: A Discussion on TerraformDrew Malone Wonder why you would want to use Terraform vs it competitors? Why not stick with CFNs, you ask? CDK should do the trick right? Come enjoy an opinionated take on using Terraform, for the betterment of your sanity. Also, includes a light intro to Terraform for those who are new to it.
Gabriel is a Cloud Technologist and accomplished Cyber practitioner who has led & built complex workloads across the IC for 20+ years. He's a native New Yorker from Washington Heights, with a boisterous laugh and calm demeanor. Gabriel has built a strong career starting in Federal service and has evolved into CTO and now VP of IC at Applied Insight. In addition to his technical accolades, he's a social leader that believes in building and growing strong teams
Unexpected Leaks in AWS Transit Gateways



Unexpected Leaks in AWS Transit GatewaysCloud Village Abstract:
Engineers can carefully build their networks, designing the traffic flow explicitly through well constructed controls, even following design best practices from the CSP themselves, only to be let down by unexpected subtleties in the exact way certain technologies operate.
In this talk, we will take a look at just such a case study concerning Transit Gateways (TGW) in AWS, where security consultants were able to communicate freely across an apparent network boundary. We will review how TGWs are attached to subnets, and how the documentation implies they should operate. Then we will examine why NACLs appeared to be having no effect on blocking traffic, and allowed an effectively flat network between two peered accounts.
This case study will demonstrate the importance and effectiveness of practical testing, either internally by the developers or with an external reviewer, in confirming – or in many cases quite the opposite – that the operation matches the design aims. It isn’t always easy to find that leak, but if there is a puddle of water on the floor then at least you know you need to start looking for the flaw. This talk will show through the TGW case study and a few other examples how we noticed the puddle, how we found the leak, how it was fixed, and how hopefully the same leak won’t spring twice.
The Rise of the Planet of the Agents: LLM-based AI Agents and Cloud Security ...



The Rise of the Planet of the Agents: LLM-based AI Agents and Cloud Security ...Cloud Village Abstract:
In the rapidly evolving domain of cloud security, the ability to dynamically interact with cloud services is crucial for security teams. Understanding cloud APIs is key to effectively managing everything from administrative tasks to security operations. Security researchers often face the challenge of selecting from numerous API definitions. What if there was a system capable of autonomously selecting the right APIs and intelligently chaining them to achieve specific goals?
In this presentation, I will share insights from my research on LLM-based AI agents. These agents utilize LLMs as reasoning engines, enabling them to handle complex tasks in natural language and autonomously determine their next actions based on user input and previous interactions. I will explain how we can transform Microsoft Graph API definitions into schemas that align with LLM function-calling capabilities. This transformation allows an LLM to select the appropriate tools and supply the correct arguments for an AI agent to execute. By integrating generative AI with cybersecurity, we can automate tasks and discover new ways to chain APIs for various operations, significantly enhancing the capabilities of security researchers to innovate in security operations and automation.
Ad
More Related Content
Similar to Terraform Unleashed - Crafting Custom Provider Exploits for Ultimate Control (20)
Introduction to Terraspace Presentation.



Introduction to Terraspace Presentation.Knoldus Inc. Terraspace Is A Terraform Framework that optimizes for infrastructure-as-code happiness. It provides an organized structure, and conventions over configurations, keeps your code DRY, and adds convenient tooling. You can keep your code DRY. Terraspace builds your Terraform project with the common app and config/terraform structure that gets built each deployment.
Introduction to Terra space Presentation



Introduction to Terra space PresentationKnoldus Inc. Terraspace Is A Terraform Framework that optimizes for infrastructure-as-code happiness It provides an organized structure, conventions over configurations, keeps your code DRY, and adds convenient tooling. You can keep your code DRY. Terraspace builds your Terraform project with common app and config/terraform structure that gets built each deploy.
Terraform Automation in Azure Online Training Institute in Hyderabad.pptx



Terraform Automation in Azure Online Training Institute in Hyderabad.pptxsivavisualpath Visualpath provides top-quality Terraform Automation in Azure Cloud Online Training conducted by real-time experts. Our training is available worldwide, and we offer daily recordings and presentations for reference. Call us at +91-9989971070 for a free demo.
WhatsApp: https://www.whatsapp.com/catalog/919989971070/
Visit blog: https://visualpathblogs.com/
Visit: https://www.visualpath.in/terraform-online-training-in-hyderabad.html
Terraform day 1



Terraform day 1Kalkey This document provides an overview and tutorial on using Terraform for DevOps. It introduces Terraform as a tool for defining and managing infrastructure as code. It then covers installing Terraform, deploying AWS infrastructure like EC2 instances using Terraform configurations, managing variables and outputs, using provisioners, organizing code with modules and workspaces, and managing Terraform state. The document aims to help users get started with Terraform for infrastructure as code.
Building infrastructure as code using Terraform - DevOps Krakow



Building infrastructure as code using Terraform - DevOps KrakowAnton Babenko This document provides an overview of a DevOps meetup on building infrastructure as code using Terraform. The agenda includes Terraform basics, frequent questions, and problems. The presenter then discusses Terraform modules, tools, and solutions. He addresses common questions like secrets handling and integration with other tools. Finally, he solicits questions from the audience on Terraform use cases and challenges.
Terraform with OCI



Terraform with OCIJeSam Kim This document provides an introduction and overview of using Terraform with Oracle Cloud Infrastructure (OCI). It discusses installing Terraform, configuring providers and resources, and demonstrates creating an OCI compute instance through Terraform. Key points include:
- Terraform is an infrastructure as code tool that can be used to provision and manage resources across multiple cloud providers, including OCI.
- The document walks through installing Terraform on Oracle Linux, configuring the OCI provider, and defining resources like compute instances in configuration files.
- A demo is shown creating an OCI compute instance named "TEST" through a Terraform plan and apply, validating the infrastructure provisioning.
Terraform - Taming Modern Clouds



Terraform - Taming Modern CloudsNic Jackson Slides form Config Management Camp, looking at how you can take a collaborative GitFlow approach to Terraform using Remote State, Modules and Dynamically Generated Credentials using Vault
OracleBeer_Terraform_soe.pdf



OracleBeer_Terraform_soe.pdfStefan Oehrli Click, click, click and I have already built my infrastructure in the cloud. But do you still know what you have built afterwards? With Infrastructure as Code or Terraform, cloud resources can be built, changed and deleted again relatively easily. This is ideal for dynamically building test and lab environments. But how do you make sure that a wrong command in the Terraform configuration does not dismantle the whole infrastructure again or shoot the costs up to astronomical heights? Where is the boundary between IaC testing and the actual release tests on the generated systems? Using Accenture Lab and training environments as an example, I will show various aspects around deploying cloud based infrastructures with Terraform. This course presentation will be complemented with demos and examples.
Infrastructure as Code with Terraform



Infrastructure as Code with TerraformPedro J. Molina Session talk presented at Innosoft 2022.11.11 University of Sevilla.
Presented the concept of Infrastructure as Core and its practical approach using Hashicorp Terraform a a tool to provision in the cloud. Examples with AWS are provided in a Guthub repository.
Debasihish da final.ppt



Debasihish da final.pptKalkey This document provides an overview of Terraform including its key features, installation process, and common usage patterns. Terraform allows infrastructure to be defined as code and treated similarly to other code. It generates execution plans to avoid surprises when provisioning resources. Complex changes can be automated while avoiding human errors. The document covers installing Terraform, deploying AWS EC2 instances, variables, outputs, modules, and workspaces. It demonstrates how Terraform can be used to provision and manage infrastructure in a safe, efficient manner.
presentation @ docker meetup



presentation @ docker meetupDaniël van Gils This document discusses Docker and the Docker ecosystem. It provides descriptions of various tools related to Docker including orchestration, service discovery, networking, data management, and monitoring tools. It also discusses some companies and projects that are part of the Docker ecosystem like Docker itself, CoreOS, Kubernetes, Marathon, Consul, etcd, and others.
Hashicorp-Certified-Terraform-Associate_V1



Hashicorp-Certified-Terraform-Associate_V1kodecloud86 Terraform is an open-source Infrastructure as Code (IaC) tool created by HashiCorp that allows users to define and provision data center infrastructure using a declarative configuration language known as HashiCorp Configuration Language (HCL) or JSON.
Key Features of Terraform:
Declarative Configuration: You describe what your infrastructure should look like, and Terraform figures out how to achieve that state.
Execution Plans: Terraform generates an execution plan showing what will happen when you apply your configurations, helping you understand changes before they take effect.
Resource Management: It manages a wide variety of service providers including AWS, Azure, Google Cloud, and many others, allowing for cross-cloud infrastructure management.
State Management: Terraform maintains a state file that helps track the current state of your infrastructure, which is crucial for planning and applying changes.
Modules: These are reusable components that can help encapsulate resources for better organization and sharing.
Provider Ecosystem: Terraform supports a wide range of providers and allows users to write custom providers to extend its capabilities.
Final terraform



Final terraformGourav Varma This document provides an overview of Terraform including its key features and how to install, configure, and use Terraform to deploy infrastructure on AWS. It covers topics such as creating EC2 instances and other AWS resources with Terraform, using variables, outputs, and provisioners, implementing modules and workspaces, and managing the Terraform state.
Terraform Basics



Terraform BasicsMohammed Fazuluddin As part of this presentation we covered basics of Terraform which is Infrastructure as code. It will helps to Devops teams to start with Terraform.
This document will be helpful for the development who wants to understand infrastructure as code concepts and if they want to understand the usability of terrform
Infrastructure as Code with Terraform.pptx



Infrastructure as Code with Terraform.pptxSamuel862293 Terraform is an infrastructure as code tool that allows infrastructure to be provisioned and managed declaratively through code. It aims to streamline operations by automating infrastructure provisioning and management, reducing manual efforts and errors. The document discusses how Terraform works, including defining infrastructure through configuration files, connecting to providers to provision resources, and best practices for using Terraform like version control and remote state management. A demo is also provided to illustrate provisioning an EC2 instance with Terraform.
What are the Benefits of Using Terraform?



What are the Benefits of Using Terraform?Ravendra Singh Terraform is an open-source provisioning mechanism from HashiCorp registered in the Go language. It is utilized for the construction, modification, and versioning of infrastructure, safely and efficiently. Provisioning tools are accountable for the creation of servers and associated assistance.
Deploy resources on Azure using IaC (Azure Terraform)



Deploy resources on Azure using IaC (Azure Terraform)George Grammatikos I introduced Azure Terraform and IAC solutions. As part of the presentation, I demonstrate how to deploy resources to Azure using Azure Terraform.
Infrastructure as code, using Terraform



Infrastructure as code, using TerraformHarkamal Singh This document discusses using Terraform to automate infrastructure provisioning and management. It begins with an introduction to infrastructure as code and Terraform. It then discusses some of the benefits of using Terraform like increased productivity, consistent deployments, and faster iteration. The document provides examples of Terraform configuration files and demonstrates basic Terraform commands like init, plan, apply, and destroy.
Instant download Terraform in Depth (MEAP V01) Robert Hafner pdf all chapter



Instant download Terraform in Depth (MEAP V01) Robert Hafner pdf all chapterakceyohros Obtain Terraform in Depth (MEAP V01) Robert Hafner instantly after payment at https://ebookmeta.com/product/terraform-in-depth-meap-v01-robert-hafner. Check out additional textbooks and ebooks in https://ebookmeta.com Full chapter PDF download.
Devops Columbia October 2020 - Gabriel Alix: A Discussion on Terraform



Devops Columbia October 2020 - Gabriel Alix: A Discussion on TerraformDrew Malone Wonder why you would want to use Terraform vs it competitors? Why not stick with CFNs, you ask? CDK should do the trick right? Come enjoy an opinionated take on using Terraform, for the betterment of your sanity. Also, includes a light intro to Terraform for those who are new to it.
Gabriel is a Cloud Technologist and accomplished Cyber practitioner who has led & built complex workloads across the IC for 20+ years. He's a native New Yorker from Washington Heights, with a boisterous laugh and calm demeanor. Gabriel has built a strong career starting in Federal service and has evolved into CTO and now VP of IC at Applied Insight. In addition to his technical accolades, he's a social leader that believes in building and growing strong teams
More from Cloud Village (18)
Unexpected Leaks in AWS Transit Gateways



Unexpected Leaks in AWS Transit GatewaysCloud Village Abstract:
Engineers can carefully build their networks, designing the traffic flow explicitly through well constructed controls, even following design best practices from the CSP themselves, only to be let down by unexpected subtleties in the exact way certain technologies operate.
In this talk, we will take a look at just such a case study concerning Transit Gateways (TGW) in AWS, where security consultants were able to communicate freely across an apparent network boundary. We will review how TGWs are attached to subnets, and how the documentation implies they should operate. Then we will examine why NACLs appeared to be having no effect on blocking traffic, and allowed an effectively flat network between two peered accounts.
This case study will demonstrate the importance and effectiveness of practical testing, either internally by the developers or with an external reviewer, in confirming – or in many cases quite the opposite – that the operation matches the design aims. It isn’t always easy to find that leak, but if there is a puddle of water on the floor then at least you know you need to start looking for the flaw. This talk will show through the TGW case study and a few other examples how we noticed the puddle, how we found the leak, how it was fixed, and how hopefully the same leak won’t spring twice.
The Rise of the Planet of the Agents: LLM-based AI Agents and Cloud Security ...



The Rise of the Planet of the Agents: LLM-based AI Agents and Cloud Security ...Cloud Village Abstract:
In the rapidly evolving domain of cloud security, the ability to dynamically interact with cloud services is crucial for security teams. Understanding cloud APIs is key to effectively managing everything from administrative tasks to security operations. Security researchers often face the challenge of selecting from numerous API definitions. What if there was a system capable of autonomously selecting the right APIs and intelligently chaining them to achieve specific goals?
In this presentation, I will share insights from my research on LLM-based AI agents. These agents utilize LLMs as reasoning engines, enabling them to handle complex tasks in natural language and autonomously determine their next actions based on user input and previous interactions. I will explain how we can transform Microsoft Graph API definitions into schemas that align with LLM function-calling capabilities. This transformation allows an LLM to select the appropriate tools and supply the correct arguments for an AI agent to execute. By integrating generative AI with cybersecurity, we can automate tasks and discover new ways to chain APIs for various operations, significantly enhancing the capabilities of security researchers to innovate in security operations and automation.
Creating Azure Policy Compliant Backdoor



Creating Azure Policy Compliant BackdoorCloud Village Abstract:
Azure Policy is a built-on service that helps creating security and compliance policies to enforce organizational standards in the cloud environment. It evaluates resources by comparing the properties of the resources and with the help of remediation tasks, it can fix or remediate any issues with those resources. Have you ever wondered if you could abuse or bend these policies? Can you do more than just listing the storage accounts with public access and not be in the logs? How about creating a backdoor?
In this talk I will answer these questions by talking about what Azure Policy is, how to write one, what the logs contain, what permission you need, what does resource enumeration could look like etc. At the end I will present a proof-of-concept solution to bend the Azure Policy and create a backdoor account in Azure.
Kicking in the Door to the Cloud: Exploiting Cloud Provider Vulnerabilities f...



Kicking in the Door to the Cloud: Exploiting Cloud Provider Vulnerabilities f...Cloud Village Abstract:
In this talk we will explore vulnerabilities in Amazon Web Services (AWS) products which allowed us to gain access to cloud environments.
Traditionally, adversaries have abused misconfigurations and leaked credentials to gain access to AWS workloads. Things like exposed long-lived access keys and exploiting the privileges of virtual machines have allowed adversaries to breach cloud resources. However, these mistakes are on the customer side of the shared responsibility model. In this session, we will cover vulnerabilities in AWS services that have been fixed and that previously allowed us to access cloud resources.
We will start with an exploration of how Identity and Access Management (IAM) roles establish trust with AWS services. Covering how roles associated with Amazon Cognito and GitHub Actions could be misconfigured to allow anyone in the world to access them. From here, we’ll cover a vulnerability we found in AWS Amplify which exposed IAM roles associated with the service to takeover, allowing anyone the ability to assume these roles.
Finally, we will also look at a worst-case scenario: what happens when an attacker finds a confused deputy vulnerability and is able to assume roles in other accounts? Sounds far-fetched? We’ll cover a real world example of a vulnerability we found in AWS AppSync that lets us do just that. We’ll also discuss how security practitioners can secure their environments, even against a zero-day like this one.
Join us to learn how attackers search for and exploit vulnerabilities in AWS services to gain access to cloud environments.
Cloud Tripwires: fighting stealth with stealth



Cloud Tripwires: fighting stealth with stealthCloud Village Abstract:
Cloud attacks continue to evolve e.g., AWS enumeration without logging (Fourchette), Azure OAuth tokens used for EoP and persistence (Blizzard), Cloud Shell backdoors, code abuse in GSuite scripting (Bryant), and tool evolution (Rhinolabs pacu), with current defensive approaches of lagging further and further behind.
This talk covers research and tooling to improve cloud defenses in AWS, Azure, and GCP, using more stealthy measures which complement existing techniques. We call the approach cloud tripwires, which involves stealthy defensive techniques that can provide low-FP detections of malicious actors.
Through analysis of cloud provider IAM design, published attack techniques and common attack tools, we show multiple stealthy detection techniques such as: restricted admin roles that are not used by valid users; seeding of the restricted admin roles in regular user policies; honey resources (buckets, files) with detections to flag access; seeding of honey resources within user policies; cached honey credentials seeded in CLI installations in external client environments, EC2 instances, and Cloud Shells; unrestricted cross-account roles to restricted accounts; metadata proxy/iptables config on EC2 instances that issue restricted temporary tokens; and full CRUD/reporting/auditing functionality.
Connecting the Dots - Mastering Alert Correlation for Proactive Defense in th...



Connecting the Dots - Mastering Alert Correlation for Proactive Defense in th...Cloud Village Abstract:
Interpret the vast amount of alerts (from different sources) received with a comprehensive, hands-on autonomous attack correlation & false positive detection workshop designed to enhance your proactive defense in the cloud. The workshop aims to demystify the process of identifying coordinated attacks amidst this noise, empowering attendees to improve their efficacy & utilize the cloud cost-effectiveness.
No data science expertise is required. Little cloud & secops expertise is required.
Intro:
- The session begins with a foundational overview of event analysis challenges and state of the art.
- Participants will learn about the ATT&CK framework, focusing on its Flows, Tactics, & Techniques to standardize threat detection.
AI & Data:
- A deep dive into accessible open-source AI tools will follow, featuring clustering algorithms, natural language processing, & Markov chains.
- Guidance on importing, cleaning, & normalizing data will ensure accuracy in subsequent analyses.
- Participants will have access to a demo environment to apply these tools interactively.
Mapping Alerts:
- Techniques for automated mapping of alerts to ATT&CK will be demonstrated.
- Attendees will engage in mapping exercises using AI.
Clustering Alerts:
- The workshop will cover clustering methods based on temporal, spatial, & technical attributes.
- Participants will engage in clustering sample alerts to form contextualized attack steps.
Correlating Alerts:
- The importance of killchains in cybersecurity will be highlighted, with methods to link attack steps into cohesive killchains.
- Participants are guided in creating & analyzing killchains to identify coordinated attacks.
Tickets:
- Criteria for creating FP Tickets, Incident Tickets, & Attack Story Tickets will be outlined.
- Participants will engage in generating sample tickets, ensuring each type is comprehensive & actionable.
Integrating & QA:
- The session will cover integration into existing SOC setups & automation using scripts & tools.
- Demonstrations will show how to maintain & update the system for continuous improvement, emphasizing cost-effective cloud automation.
- QA, troubleshooting, & further resources.
By the end of this interactive workshop, participants will have experience with AI tools mapping alerts to Techniques, clustering them into contextualized attack steps, & constructing comprehensive killchains to uncover coordinated attacks. Additionally, they will learn to generate actionable tickets for immediate response & long-term improvements in their security posture, all without needing advanced data science knowledge. This session encourages practical application in participants' environments & further exploration of the vast capabilities of open-source AI in cybersecurity, & showcases the power of cloud cost-effectiveness in big data analytics (sagemaker, s3, lambda, etc.).
Runtime Reachability: Prioritizing Vulnerabilities with eBPF & Continuous Pro...



Runtime Reachability: Prioritizing Vulnerabilities with eBPF & Continuous Pro...Cloud Village Abstract:
As security engineers, managing risk means making informed decisions about which vulnerabilities to address first. We are often too time constrained, and the signal-to-noise ratio of current SAST/SCA tooling is too low.
This talk introduces "Runtime Reachability," a novel approach that leverages Continuous Profiling via eBPF to quantify how often a vulnerable method/codepath is called, in actual production usage. By understanding the runtime behavior of applications, security teams can effectively filter out low-likelihood vulnerabilities, prioritize fixes more effectively, reduce toil & the overall risk to their organization.
Revealing Choke Points - Practical Tactics for Boosting Cloud Security



Revealing Choke Points - Practical Tactics for Boosting Cloud SecurityCloud Village Abstract:
During this presentation, we will address the critical importance of permission management in Cloud Native integrations and how an inadequate permissions model can create significant advantages for attackers. We will demonstrate how an attacker can exploit standard permissions to achieve privilege escalation, explain what Choke Points are, and illustrate Attack Paths in practice, showing how an attacker can progress towards success in their objectives. As the ultimate goal of this talk, we will present practical actions to enhance the security of your environment in this context and mitigate these threats.
Finding Holes in Conditional Access Policies



Finding Holes in Conditional Access PoliciesCloud Village Abstract:
Microsoft Entra Conditional Access sits at the forefront of organization's security boundaries. The ever-changing climate of conditional access continues to give administrators more and more security controls. The tradeoff of which is increased complexity when attempting to balance security and productivity. The more policies deployed in a tenant, the greater the chance for misconfigurations that create opportunities for exploitation. Whether you're a cloud administrator, security consultant, or adversary, the goal remains the same: to find the holes in conditional access.
This talk discusses lessons learned from real-life engagements and identifies multiple strategies for evaluating conditional access. Topics and tooling are explored that view conditional access from several different angles. First, understanding PowerShell and Graph API is vital when combing through policies, finding gaps in user, group, role, location, application, or device configuration. Second, simulation of logon criteria and reporting on authentication events helps to understand where policies fall short. Finally, creating a visual representation of each policy is helpful to better see policy details or build executive reports. Each of these provides an important piece of the puzzle when attempting to identify methods to bypass security controls. Audience members should expect to leave with an arsenal of new tools and techniques to continuously monitor conditional access for risk.
One Click, Six Services - Abusing The Dangerous Multi-service Orchestration P...



One Click, Six Services - Abusing The Dangerous Multi-service Orchestration P...Cloud Village Abstract:
Cloud providers build their services a little like Jenga towers. They use their core services as the foundation of more popular customer-facing offerings. You may think you’re just creating a GCP cloud function in an empty account. In reality, with one click, you’re creating resources in six different services: a Cloud Build instance, a Storage Bucket, an Artifact Registry or a Container Registry, and possibly a Cloud Run instance and Eventarc triggers. The security of the entire stack is only as strong as the weakest link.
By looking at the entire stack, we can find privilege escalation techniques and even vulnerabilities that are hidden behind the stack. In my research, I was able to find a novel privilege escalation vulnerability and several privilege escalation techniques in GCP.
The talk will showcase a key concept, sometimes not discussed enough: cloud services are built on top of each other, and one click in the console can cause many things to happen behind the scenes. More services mean more risks and a larger attack surface.
The next part will dive deep into the vulnerable GCP cloud functions deployment flow. I will showcase the vulnerability I found in this flow, which enables an attacker to run code as the default Cloud Build service account by exploiting the deployment flow and the flawed trust between services resulting in a large fix and change in GCP IAM and Cloud Functions. This would grant an attacker high privileges to key services such as Storage, Artifact Registry, and Cloud Build.
However, this talk is about more than just a vulnerability. By understanding cross-service dependency, we can reveal a broad attack surface for many possible privilege escalation vectors between services. I will demo a simple tool I wrote to find the hidden APIs that are called by the CSP when performing an action.
By the end of this talk, the audience will learn the dangers of treating cloud services like a black box. The talk explains the hidden deployment flow behind one important stack, and provides the tools to uncover the risks of many more.
Workshop: Hands-On Container Image Security Mastering Sigstore for Unbreachab...



Workshop: Hands-On Container Image Security Mastering Sigstore for Unbreachab...Cloud Village Abstract:
In the ever-evolving landscape of containerized applications, ensuring the integrity and security of your container images is paramount. Join us for an immersive, hands-on workshop titled "Hands-On Container Image Security: Mastering Sigstore for Unbreachable Integrity," where we'll dive deep into securing your container images using the cutting-edge open-source tools Cosign and Rekor from the Sigstore project.
This workshop will provide a comprehensive, practical introduction to Sigstore tools, demonstrating how they can be seamlessly integrated into your DevOps workflows. We'll begin with a brief overview of the common security challenges associated with container images and how Sigstore addresses these issues by providing automated and tamper-proof signing and verification processes.
Participants will then engage in hands-on exercises, where they'll:
1. Learn to sign container images and verify their integrity using Cosign. We'll guide you through setting up Cosign, signing your first image, and verifying its signature, ensuring you have a solid understanding of this powerful tool.
2. Delve into using Rekor, Sigstore's transparency log, to record and verify signed image metadata. You'll experience firsthand how Rekor enhances security by providing an immutable log of all signed images, ensuring accountability and traceability.
3. Discover how to seamlessly integrate these tools into your existing DevOps pipelines, automating the signing and verification process, and ensuring that only trusted and verified images make it to production environments.
By the end of this workshop, you'll have gained hands-on experience with Sigstore tools and a deep understanding of how to implement them in your own environment. This session is tailored for DevOps engineers, security professionals, and software developers who are committed to enhancing their container security practices.
Don't miss this unique opportunity to acquire practical knowledge and skills in securing your container images. Join us and learn how to leverage Sigstore's powerful tools to ensure your container images are secure, verified, and trustworthy, safeguarding your applications from potential threats.
DC 32: Epyon - Attacking DevOps environments



DC 32: Epyon - Attacking DevOps environmentsCloud Village Abstract:
A CI/CD pipeline is a sequence of steps designed to automate the software delivery process. DevOps environments consist of multiple systems that collaborate to facilitate CI/CD pipelines. However, DevOps systems are significant targets for attackers due to their possession of credentials and access keys for various components, including domain accounts, databases, and cloud assets.
Epyon is a versatile tool for red teamers to target common DevOps systems. It is open source and written entirely in Golang. Moreover, it features multiple modules, such as GitLab, SonarQube, and Azure DevOps.
During this demonstration, I will present examples (based on real project experiences) of how to utilize Epyon for privilege escalation and lateral movement within a DevOps environment.
Exploit K8S via Misconfiguration .YAML in CSP environments



Exploit K8S via Misconfiguration .YAML in CSP environmentsCloud Village Abstract:
In this presentation, we researched vulnerable security configurations that enable attacks on Kubernetes (K8s) clusters and examined how these settings can be exploited in CNCF projects. Kubernetes (K8s) uses YAML files to manage various security settings, leading to potential attacks such as information leakage, excessive permission acquisition, and container escape.
Initially, this study focused on three security configuration areas in K8s: RBAC, HostPID, and Security Context. We explained the threats present if vulnerable settings are included.
- RBAC: Excessive permission in K8s resources allows sensitive information theft or access to other nodes
- HostPID: Access to node process information enables container escape attacks
- Security Context: Incorrect security settings enable node escape and host access
Next, we created patterns for identifying weak security settings through YAML files. To do this, we conducted a literature review and expanded the vulnerable patterns centered on RBAC proposed in various papers. Additionally, we included other security settings (HostPID, Security Context).
[Our Pattern vs Paper Pattern]
1. RBAC:
- Our: Daemonset, Deployment SA > node Patch and Secret Get/List
- Paper: Daemonset > node Patch and Secret Get/List
2. Kind:
Our: Cluster Role, Role, Role Binding
Paper: Cluster Role
3. Other Security configurations:
- Our: HostPID, SecurityContext
- Paper: X
Utilizing these patterns, we examined over 150 widely-used 3rd-party CNCF projects in K8s, discovering more than 50 instances of vulnerable patterns.
We provide detailed demonstrations of three scenarios for seizing nodes or clusters by using the discovered patterns to set Base Attack conditions.
[Base Attack Conditions]
- RBAC > Demonset / Deployment > Service Account > Secret (Get/List) or Node(Patch)
[Exploit Scenario]
- Stealing Tokens using Pods with excessive privileges
- Node Take over via 1 Day (CVE-2022-42889) or hostPID: True or Security Context
- Take over of another node or cluster using the Service Account Token on the deodorized node
Additionally, we are aware that 3rd-Party CNCF projects are widely used for convenience when operating K8S in CSPs (AWS, Azure, GCP). Since scenarios can occur in a CSP environment, we demonstrate in more detail.
Finally, based on these research results, we share vulnerable patterns with project owners to collaborate on patching and issue tracking. Before the presentation, we plan to share any reporting on CVEs and patch notes.
Cloud Offensive Breach and Risk Assessment (COBRA)



Cloud Offensive Breach and Risk Assessment (COBRA)Cloud Village Abstract:
Cloud Offensive Breach and Risk Assessment (COBRA) is an open-source tool designed to empower users to simulate attacks within multi-cloud environments, offering a comprehensive evaluation of security controls. By automating the testing of various threat vectors including external and insider threats, lateral movement, and data exfiltration, COBRA enables organizations to gain insights into their security posture vulnerabilities. COBRA is designed to conduct simulated attacks to assess an organization's ability to detect and respond to security threats effectively.
It facilitates Proof of Concept (POC) evaluations, assesses security controls, measures maturity levels, and generates comprehensive reports, enabling organizations to enhance their cloud security resilience through lifelike threat scenarios.
COBRA Features:
---
Seamless Integration for POC and Tool Evaluation: COBRA provides seamless integration for Proof of Concept (POC) and tool evaluation purposes. Whether you're exploring new cloud-native applications or evaluating existing solutions, COBRA offers a user-friendly interface and flexible deployment options to facilitate effortless testing and assessment.
Comprehensive Assessment of Cloud-Native Security Posture: Gain unparalleled insights into your organization's existing cloud-native security posture with COBRA. Our advanced assessment capabilities enable you to identify vulnerabilities, assess security controls, and pinpoint areas for improvement. By understanding your current security posture, you can proactively address gaps and strengthen your defenses against emerging threats.
Benchmarking Against Industry Standards and Best Practices: COBRA enables you to benchmark your cloud security controls against industry standards and best practices. With our comprehensive benchmarking framework, you can compare your security posture against established benchmarks, identify areas of strength and weakness, and prioritize remediation efforts accordingly.
Actionable Insights and Recommendations: COBRA goes beyond providing insights by providing a report delivering actionable recommendations tailored to your organization's specific needs. Whether it's optimizing security configurations, implementing additional controls, or enhancing incident response processes, COBRA equips you with the tools and guidance needed to bolster your cloud security defenses.
Continuous Threat Simulation: COBRA offers a modular and templatized approach for users to easily integrate additional modules, allowing for continuous threat simulation and adaptability, by providing a flexible framework for adding modules, COBRA ensures that users can tailor their threat simulation capabilities according to evolving security needs, making it an ideal platform for continuous threat simulation.
One Port to Serve Them All - Google GCP Cloud Shell Abuse



One Port to Serve Them All - Google GCP Cloud Shell AbuseCloud Village Abstract:
The Cloud Shell feature from cloud service providers offers a convenient way to access resources within the cloud, significantly improving the user experience for both administrators and developers. However, even though the spawned instance has a short lifespan, granting excessive permissions could still pose security risks to users. This talk reveals an abuse methodology that leverages an unexpected, public-facing port in GCP Cloud Shell discovered during recon. Through manipulation in Linux Netfilter's NAT table, it serves various internally running services such as HTTP, SOCKS, and SSH within the Cloud Shell container to the public. This configuration could be exploited by adversaries to bypass the Google authentication needed in its Web Preview feature to leak data, to deliver malicious content, or to pivot attack traffic through the Google network.
Bio:
Hubert Lin is an offensive security expert, specializing in remote vulnerability exploitation, honeypots, and penetration testing. He previously led the signature team for network threat defense and was a senior staff engineer on the Red Team at Trend Micro. In his roles, he assessed network intrusion prevention systems and conducted sanctioned red team exercises to enhance corporate security. Hubert holds certifications as a Red Hat Certified Engineer (RHCE) and an Offensive Security Certified Professional (OSCP). Currently, he works at Netskope as a Sr. Staff Researcher.
The Oracle Awakens: Demystifying Privilege Escalation in the cloud



The Oracle Awakens: Demystifying Privilege Escalation in the cloudCloud Village In this talk, we explore privilege escalation mechanisms and paths within Oracle Cloud. Privilege escalation, the process by which an attacker gains elevated access and permissions beyond those intended by the cloud administrator, poses a significant threat in cloud environments and can significantly aid an attacker or pentester.
Our discussion will focus on identifying privilege escalation paths, understanding how cloud administrators can misconfigure policies, and the methods attackers can use to exploit these vulnerabilities. Through carefully designed scenarios and real-world examples, attendees will learn to recognize signs of privilege escalation, thereby enhancing their security posture.
Catch them all! Detection engineering and purple teaming in the cloud



Catch them all! Detection engineering and purple teaming in the cloudCloud Village Where to start looking for attackers in a cloud environment? In a world where cloud providers have hundreds of services and thousands of API calls, getting started can feel overwhelming.
In this talk, we lay out the foundations of a modern detection engineering program built and tailored for the cloud, such as threat-informed defense based on real-world attacker activity, emulating common attacker behavior, shortening feedback loops to validate telemetry, and continuous end-to-end testing of threat detection rules. Additionally, we introduce a new open-source project, Grimoire, which allows leveraging pre-built datasets of AWS CloudTrail logs for common attacks.
You'll gain a hands-on, actionable understanding of how to start identifying threats in your cloud environment, or improve your existing process.
Gone in 60 Seconds… How Azure AD/Entra ID Tenants are Compromise



Gone in 60 Seconds… How Azure AD/Entra ID Tenants are CompromiseCloud Village 60 seconds. 1 minute.
That's all it takes for an attacker to compromise an account with access.
And the account doesn't even need to have obvious privileged rights for the attacker to own the cloud environment.
Then, once they get Global Admin rights to Azure AD/Entra ID, it's game over since they have full admin rights, access to all data, and can easily pivot to control all Azure subscription services and content.
This talk walks through the most common ways that attackers compromise the Microsoft Cloud, specifically Azure AD/Entra ID and how to mitigate these attack techniques.
Join me in this journey of attacker methods involving account compromise of admin and user accounts, including interesting pairing of role rights, application permissions, and Conditional Access gaps.
So go beyond Global Administrator to better understand the Entra ID roles that really matter in the tenant and how application permissions provide attacker opportunity in most environments!
Attendees will learn both Azure AD/Entra ID attack and defense during this session.
Ad
Recently uploaded (20)
UiPath Community Berlin: Orchestrator API, Swagger, and Test Manager API



UiPath Community Berlin: Orchestrator API, Swagger, and Test Manager APIUiPathCommunity Join this UiPath Community Berlin meetup to explore the Orchestrator API, Swagger interface, and the Test Manager API. Learn how to leverage these tools to streamline automation, enhance testing, and integrate more efficiently with UiPath. Perfect for developers, testers, and automation enthusiasts!
📕 Agenda
Welcome & Introductions
Orchestrator API Overview
Exploring the Swagger Interface
Test Manager API Highlights
Streamlining Automation & Testing with APIs (Demo)
Q&A and Open Discussion
Perfect for developers, testers, and automation enthusiasts!
👉 Join our UiPath Community Berlin chapter: https://community.uipath.com/berlin/
This session streamed live on April 29, 2025, 18:00 CET.
Check out all our upcoming UiPath Community sessions at https://community.uipath.com/events/.
Special Meetup Edition - TDX Bengaluru Meetup #52.pptx



Special Meetup Edition - TDX Bengaluru Meetup #52.pptxshyamraj55 We’re bringing the TDX energy to our community with 2 power-packed sessions:
🛠️ Workshop: MuleSoft for Agentforce
Explore the new version of our hands-on workshop featuring the latest Topic Center and API Catalog updates.
📄 Talk: Power Up Document Processing
Dive into smart automation with MuleSoft IDP, NLP, and Einstein AI for intelligent document workflows.
Big Data Analytics Quick Research Guide by Arthur Morgan



Big Data Analytics Quick Research Guide by Arthur MorganArthur Morgan This is a Quick Research Guide (QRG).
QRGs include the following:
- A brief, high-level overview of the QRG topic.
- A milestone timeline for the QRG topic.
- Links to various free online resource materials to provide a deeper dive into the QRG topic.
- Conclusion and a recommendation for at least two books available in the SJPL system on the QRG topic.
QRGs planned for the series:
- Artificial Intelligence QRG
- Quantum Computing QRG
- Big Data Analytics QRG
- Spacecraft Guidance, Navigation & Control QRG (coming 2026)
- UK Home Computing & The Birth of ARM QRG (coming 2027)
Any questions or comments?
- Please contact Arthur Morgan at [email protected].
100% human made.
AI Changes Everything – Talk at Cardiff Metropolitan University, 29th April 2...



AI Changes Everything – Talk at Cardiff Metropolitan University, 29th April 2...Alan Dix Talk at the final event of Data Fusion Dynamics: A Collaborative UK-Saudi Initiative in Cybersecurity and Artificial Intelligence funded by the British Council UK-Saudi Challenge Fund 2024, Cardiff Metropolitan University, 29th April 2025
https://alandix.com/academic/talks/CMet2025-AI-Changes-Everything/
Is AI just another technology, or does it fundamentally change the way we live and think?
Every technology has a direct impact with micro-ethical consequences, some good, some bad. However more profound are the ways in which some technologies reshape the very fabric of society with macro-ethical impacts. The invention of the stirrup revolutionised mounted combat, but as a side effect gave rise to the feudal system, which still shapes politics today. The internal combustion engine offers personal freedom and creates pollution, but has also transformed the nature of urban planning and international trade. When we look at AI the micro-ethical issues, such as bias, are most obvious, but the macro-ethical challenges may be greater.
At a micro-ethical level AI has the potential to deepen social, ethnic and gender bias, issues I have warned about since the early 1990s! It is also being used increasingly on the battlefield. However, it also offers amazing opportunities in health and educations, as the recent Nobel prizes for the developers of AlphaFold illustrate. More radically, the need to encode ethics acts as a mirror to surface essential ethical problems and conflicts.
At the macro-ethical level, by the early 2000s digital technology had already begun to undermine sovereignty (e.g. gambling), market economics (through network effects and emergent monopolies), and the very meaning of money. Modern AI is the child of big data, big computation and ultimately big business, intensifying the inherent tendency of digital technology to concentrate power. AI is already unravelling the fundamentals of the social, political and economic world around us, but this is a world that needs radical reimagining to overcome the global environmental and human challenges that confront us. Our challenge is whether to let the threads fall as they may, or to use them to weave a better future.
tecnologias de las primeras civilizaciones.pdf



tecnologias de las primeras civilizaciones.pdffjgm517 descaripcion detallada del avance de las tecnologias en mesopotamia, egipto, roma y grecia.
How analogue intelligence complements AI



How analogue intelligence complements AIPaul Rowe
Artificial Intelligence is providing benefits in many areas of work within the heritage sector, from image analysis, to ideas generation, and new research tools. However, it is more critical than ever for people, with analogue intelligence, to ensure the integrity and ethical use of AI. Including real people can improve the use of AI by identifying potential biases, cross-checking results, refining workflows, and providing contextual relevance to AI-driven results.
News about the impact of AI often paints a rosy picture. In practice, there are many potential pitfalls. This presentation discusses these issues and looks at the role of analogue intelligence and analogue interfaces in providing the best results to our audiences. How do we deal with factually incorrect results? How do we get content generated that better reflects the diversity of our communities? What roles are there for physical, in-person experiences in the digital world?
Drupalcamp Finland – Measuring Front-end Energy Consumption



Drupalcamp Finland – Measuring Front-end Energy ConsumptionExove How to measure web front-end energy consumption using Firefox Profiler. Presented in DrupalCamp Finland on April 25th, 2025.
#StandardsGoals for 2025: Standards & certification roundup - Tech Forum 2025



#StandardsGoals for 2025: Standards & certification roundup - Tech Forum 2025BookNet Canada Book industry standards are evolving rapidly. In the first part of this session, we’ll share an overview of key developments from 2024 and the early months of 2025. Then, BookNet’s resident standards expert, Tom Richardson, and CEO, Lauren Stewart, have a forward-looking conversation about what’s next.
Link to recording, transcript, and accompanying resource: https://bnctechforum.ca/sessions/standardsgoals-for-2025-standards-certification-roundup/
Presented by BookNet Canada on May 6, 2025 with support from the Department of Canadian Heritage.
IEDM 2024 Tutorial2_Advances in CMOS Technologies and Future Directions for C...



IEDM 2024 Tutorial2_Advances in CMOS Technologies and Future Directions for C...organizerofv IEDM 2024 Tutorial2
Technology Trends in 2025: AI and Big Data Analytics



Technology Trends in 2025: AI and Big Data AnalyticsInData Labs At InData Labs, we have been keeping an ear to the ground, looking out for AI-enabled digital transformation trends coming our way in 2025. Our report will provide a look into the technology landscape of the future, including:
-Artificial Intelligence Market Overview
-Strategies for AI Adoption in 2025
-Anticipated drivers of AI adoption and transformative technologies
-Benefits of AI and Big data for your business
-Tips on how to prepare your business for innovation
-AI and data privacy: Strategies for securing data privacy in AI models, etc.
Download your free copy nowand implement the key findings to improve your business.
Cybersecurity Identity and Access Solutions using Azure AD



Cybersecurity Identity and Access Solutions using Azure ADVICTOR MAESTRE RAMIREZ Cybersecurity Identity and Access Solutions using Azure AD
Designing Low-Latency Systems with Rust and ScyllaDB: An Architectural Deep Dive



Designing Low-Latency Systems with Rust and ScyllaDB: An Architectural Deep DiveScyllaDB Want to learn practical tips for designing systems that can scale efficiently without compromising speed?
Join us for a workshop where we’ll address these challenges head-on and explore how to architect low-latency systems using Rust. During this free interactive workshop oriented for developers, engineers, and architects, we’ll cover how Rust’s unique language features and the Tokio async runtime enable high-performance application development.
As you explore key principles of designing low-latency systems with Rust, you will learn how to:
- Create and compile a real-world app with Rust
- Connect the application to ScyllaDB (NoSQL data store)
- Negotiate tradeoffs related to data modeling and querying
- Manage and monitor the database for consistently low latencies
Massive Power Outage Hits Spain, Portugal, and France: Causes, Impact, and On...



Massive Power Outage Hits Spain, Portugal, and France: Causes, Impact, and On...Aqusag Technologies In late April 2025, a significant portion of Europe, particularly Spain, Portugal, and parts of southern France, experienced widespread, rolling power outages that continue to affect millions of residents, businesses, and infrastructure systems.
Quantum Computing Quick Research Guide by Arthur Morgan



Quantum Computing Quick Research Guide by Arthur MorganArthur Morgan This is a Quick Research Guide (QRG).
QRGs include the following:
- A brief, high-level overview of the QRG topic.
- A milestone timeline for the QRG topic.
- Links to various free online resource materials to provide a deeper dive into the QRG topic.
- Conclusion and a recommendation for at least two books available in the SJPL system on the QRG topic.
QRGs planned for the series:
- Artificial Intelligence QRG
- Quantum Computing QRG
- Big Data Analytics QRG
- Spacecraft Guidance, Navigation & Control QRG (coming 2026)
- UK Home Computing & The Birth of ARM QRG (coming 2027)
Any questions or comments?
- Please contact Arthur Morgan at [email protected].
100% human made.
Increasing Retail Store Efficiency How can Planograms Save Time and Money.pptx



Increasing Retail Store Efficiency How can Planograms Save Time and Money.pptxAnoop Ashok In today's fast-paced retail environment, efficiency is key. Every minute counts, and every penny matters. One tool that can significantly boost your store's efficiency is a well-executed planogram. These visual merchandising blueprints not only enhance store layouts but also save time and money in the process.
The Evolution of Meme Coins A New Era for Digital Currency ppt.pdf



The Evolution of Meme Coins A New Era for Digital Currency ppt.pdfAbi john Analyze the growth of meme coins from mere online jokes to potential assets in the digital economy. Explore the community, culture, and utility as they elevate themselves to a new era in cryptocurrency.
Complete Guide to Advanced Logistics Management Software in Riyadh.pdf



Complete Guide to Advanced Logistics Management Software in Riyadh.pdfSoftware Company Explore the benefits and features of advanced logistics management software for businesses in Riyadh. This guide delves into the latest technologies, from real-time tracking and route optimization to warehouse management and inventory control, helping businesses streamline their logistics operations and reduce costs. Learn how implementing the right software solution can enhance efficiency, improve customer satisfaction, and provide a competitive edge in the growing logistics sector of Riyadh.
Build Your Own Copilot & Agents For Devs



Build Your Own Copilot & Agents For DevsBrian McKeiver May 2nd, 2025 talk at StirTrek 2025 Conference.
Ad
Terraform Unleashed - Crafting Custom Provider Exploits for Ultimate Control
- 1. Terraform Unleashed: Crafting custom Provider exploits for Ultimate control
- 2. Rupali Dash brings over 8 years of cybersecurity experience, specializing in penetration testing and red teaming. Currently a Lead Security Architect at Axl.net Security, she oversees cloud security and penetration testing engagements. Her credentials include notable certifications like OSCP, OSWE, AWS Security Specialist, and GCPN. She has presented at prominent conferences like Black Hat Asia, DevSecCon, and CoCon. Alex Foley is a broadly experienced security professional with over 25 years of experience in IT and cybersecurity. He is the founder and CEO of Axl.net Security. He has operated and continues to operate as the vCISO of multiple startup companies with the support of the team from Axl.net Security. Throughout his career, he's had the opportunity to wear many hats and do "all the things" within product development, operations, and security. This broad experience has enabled Alex to bring this depth of understanding to the CISO roles. Alex's skill set focuses on blue team operations, which complements Rupali's expertise in red team activities. Who Are We ??
- 3. Who Does The Talk Cater To Pen testers and Red-teamers who will be testing an cloud infrastructure. Security Architects managing the security posture of the cloud infrastructure.
- 4. Terraform Enterprise Deployment Architecture
- 6. ► - In-order to provision this code the user logs in to the terraform enterprise first and provides the AWS Credentials of the account for the resource provisioning . ► Upon Terraform Init the TFE Spins up the worker container in the TFE AWS account and Downloads the required provides specified in the provider block. ► During Terraform Plan, The Terraform API zips the IAC code and the Provided authentication credentials along with the terraform binary and stores it over the worker container. ► It also performs a state lock using dynamo DB for that specific workspace so that no two TFE plan can run simultaneously for a specific workspace and it ques the job. ► It also downloads the Sentinel policies associated with the workspace on to the worker container. ► During the Terraform plan once the sentinel policies are validated against the TFE plan out out, Terraform generates a newer set of credentials using the provided AWS credentials in the terraform file which will be used to provision the resource in the clients AWS account. ► Once the Apply is completed the worker container stores the generated terraform state file over the s3 bucket and destroyes the container.
- 7. Terraform Provider ►A terraform provider is a binary written in go that interacts with terraform binary over RPC & enables interaction with the provider API. This includes Cloud providers and Software-as-a-service providers. The providers are specified in the Terraform configuration code. They tell Terraform which services it needs to interact with.
- 8. Key-RISK Terraform binaries are executables which will be downloaded into the emphiral container during terraform init. Terraform Provider runs with the highest privilege on the worker container and hence have access to all the mounted file system as well as the AWS STS credentials. The TFE worker container needs to have the read access to the s3 and RDS instance where the TFE state file gets stored as a part of application. In a scenario where multiple providers are invoked for a specific Terraform Plan, Both the providers will have access to the TFE environment variables and the host file system.
- 9. Attack-1: Custom provider with filesystem access to gain access to the host file system ● In Golang Import os/exec and import syscall modules enables the binary to interact with the host file system. ● Create the data source to read an environment variable & register this new data source in your provider.go file. ● Use “go build” command to build the provider.
- 10. Exploit ( System File Read) Create a Terraform configuration file that uses the new data source to read the /etc/passwd file on the host.
- 11. Attack-2: Custom provider with Code Execution feature Terraform-provider-cmdexec is a custom built provider that provides command execution capability through Terraform Configuration. Below is the example of the main.tf file used to leverage the provider to execute the command. https://github.com/rung/terraform-provider-cmdexec https://alex.kaskaso.li/post/terraform-plan-rce
- 12. ► Execute Commands on the Terraform container ► Provision highly privileged roles / resources by Bypassing sentinel policies to gain persistence. ► Exfiltrate Vaulted secrets from the TFE container. ► Manipulate state files resulting in deleting resources in the existing cloud accounts. ► Gain access to PII data in Production accounts. ► Supply chain threats to organizations using the malicious providers.
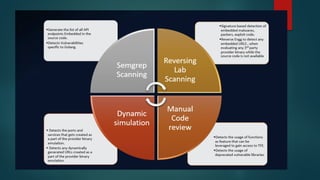
- 13. Why the Terraform Provider and not the Provisioners ? ►Terraform Provisioner has local_exec() and remote_exec() capability which helps to execute commands on the TFE infrastructure as a part of terraform apply. ►Terraform Provisioners are called only after a successful plan and prior to the Terraform Apply. Hence usage of sentinel policy can be leveraged to block those attacks. ►Terraform Provider block executes during the terraform plan and hence It cannot be blocked/restricted through Sentinel
- 14. Provider Security Risks ►1: Malevolence of the Binary: This is to ensure that the provider binary doesn’t contain any malware , packers or custom exploits. ►2: Impact on the TFE infrastructure: This will provide insight on the different functionalities and access level of the provider in the TFE infrastructure. ►3: Out bound Network communication: This will provide insight on the different end points/APIs embedded into the binary
- 17. Conclusions ● Provider Attack Types ○ Third Party Providers ○ Insider Threat ● Defense ○ Updated Training ○ Updated Detection Technology ○ Updated Processes


