Testing Docker Images Security -All day dev ops 2017
- 3. Introduction to docker security Security best practices Tools for auditing docker images Three Takeaways
- 4. ● “Docker containers wrap up a piece of software in a complete filesystem that contains everything it needs to run: code,runtime, system tools, system libraries –anything you can install on a server. This guarantees that it will always run the same,regardless of the environment it is running in.”
- 6. ● Docker provides an additional layer of isolation, making your infrastructure safer by default. ● Makes the application lifecycle fast and easier, reducing risks in your applications
- 7. ● Docker uses several mechanisms for security: ○ Linux kernel namespaces ○ Linux Control Groups (cgroups) ○ The Docker daemon ○ Linux capabilities (libcap) ○ Linux security mechanisms like AppArmor or SELinux
- 8. ● Namespaces:provides an isolated view of the system where processes cannot see other processes in other containers ● Each container also gets its own network stack. ● A container doesn’t get privileged access to the sockets or interfaces of another container.
- 9. ● Cgroups: kernel feature that limits and isolates the resource usage(CPU,memory,network) of a collection of processes. ● Linux Capabilities: divides the privileges of root into distinct units and smaller groups of privileges.
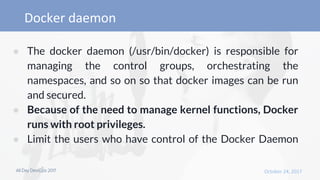
- 10. ● The docker daemon (/usr/bin/docker) is responsible for managing the control groups, orchestrating the namespaces, and so on so that docker images can be run and secured. ● Because of the need to manage kernel functions, Docker runs with root privileges. ● Limit the users who have control of the Docker Daemon
- 11. ● Restrict access to the daemon only to the ones really needing it (users, processes) ● Don’t expose the daemon to the outside your network ● If you do so, make sure you have put this behind a secure proxy, like NGINX
- 18. ● Images are extracted in a chrooted sub process, being the first-step in a wider effort toward privilege separation. ● From Docker 1.10, all images are stored and accessed by the cryptographic checksums of their contents, limiting the possibility of an attacker causing a collision with an existing image Docker Content Trust.
- 20. ● Protects against untrusted images ● Can enable signing checks on every managed host ● Signature verification transparent to users ● Guarantee integrity of your images when pulled ● Provides trust from publisher to consumer ● export DOCKER_CONTENT_TRUST=1 ● ~/.docker/trust/trusted-certificates/
- 21. ● Do not write secrets(users and passwords). ● Remove unnecessary setuid, setgid permissions (Privilege escalation) ● Download packages securely using GPG and certificates ● Try to restrict an image or container to one service
- 22. ● To disable setuid rights, add the following to the Dockerfile of your image
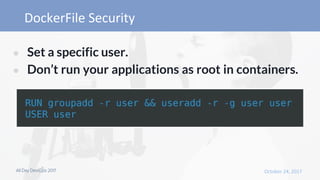
- 23. ● Set a specific user. ● Don’t run your applications as root in containers.
- 24. ● Don’t run containers with --privileged flag ● The --privileged flag gives all capabilities to the container. ● docker run --privileged … ● docker run --cap-drop=ALL --cap-add= CAP_NET_ADMIN ...
- 25. ● Manual management within the container: docker run --cap-add ALL ● Restricted capabilities with root: docker run --cap-drop ALL --cap-add $CAP ● No capabilities: docker run --user
- 28. ● We can verify the integrity of the image ● Checksum validation when pulling image from docker hub ● Pulling by digest to enforce consistent
- 29. ● Pulling by Docker content trust ● $ export DOCKER_CONTENT_TRUST=1 $ docker pull debian:latest Pull (1 of 1): debian:latest@sha256:a25306f38…
- 30. ● Check packages installed in the container
- 31. Docker security is about limiting and controlling the attack surface on the kernel.
- 32. Run filesystems as read-only so that attackers can not overwrite data or save malicious scripts to the image.
- 37. ● You can scan your images for known vulnerabilities ● There are tools for that, like Docker Security Scanning, Docker Bench Security and CoreOS Clair ● Find known vulnerable binaries
- 38. ● Checks based on best practices for hosts and containers ● Find Common Vulnerabilities and Exposures (CVEs) https://docs.docker.com/docker-cloud/builds/image-scan/
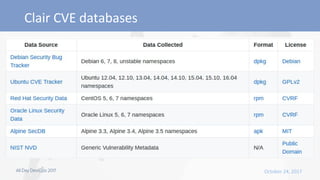
- 39. ● Checks against CVE database for image layers ● Binary scanning of all components in the image ● Performs binary scan to pick up on statically linked binaries ● Analyses libraries statically compiled in the image ● Generates a reports that shows if there are CVE in the libraries inside the image
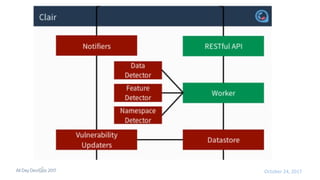
- 45. ● Vulnerability Static Analysis for Containers ● https://github.com/coreos/clair
- 46. ● You've found an image by searching the internet and want to determine if it's safe enough for you to use in production. ● You're regularly deploying into a containerized production environment and want operations to alert or block deployments on insecure software.
- 49. ● Checks based on best practices for hosts and containers ● https://github.com/docker/docker-bench-security ● Open-source tool for running automated tests ● Inspired by the CIS Docker 1.11 benchmark ● Runs against containers currently running on same host ● Checks for AppArmor, read-only volumes, etc...
- 51. ● The host configuration ● The Docker daemon configuration ● The Docker daemon configuration files ● Container images and build files ● Container runtime ● Docker security operations
- 52. ● The Docker daemon configuration ● [WARN] 2.1- Restrict network traffic between containers ● [WARN] 4.1 - Create a user for the container ● [WARN] * Running as root: ● [WARN] 5.4 - Restrict Linux Kernel Capabilities within containers ● [WARN] * Capabilities added: CapAdd=[audit_control] ● [WARN] 5.13 - Mount container's root filesystem as readonly ● [WARN] * Container running with root FS mounted R/W:
- 54. ● Lynis ● Dagda ● Anchore
- 55. ● https://github.com/CISOfy/lynis-docker ● Lynis is a Linux, Mac and Unix security auditing and system hardening tool that includes a module to audit Dockerfiles. ● lynis audit dockerfile <file>
- 57. ● https://github.com/eliasgranderubio/dagda ● Static analysis of known vulnerabilities on Docker containers ● Allows monitoring Docker containers for detecting anomalous activities
- 59. ● python3 dagda.py check --docker_image <image_name> ● python3 dagda.py history <image_name> --id <Id_Scan>
- 71. Signing ● Secure & sign your source Dependences ● Pin & verify your dependencies Content Trust ● Sign your artifacts with Docker Content Trust Privileges ● Least Privilege configurations
- 72. ● https://docs.docker.com/engine/security ● http://www.oreilly.com/webops-perf/free/files/dock er-security.pdf ● http://container-solutions.com/content/uploads/201 5/06/15.06.15_DockerCheatSheet_A2.pdf ● https://www.openshift.com/promotions/docker-sec urity.html
- 73. ● Docker Content Trust https://docs.docker.com/engine/security/trust/cont ent_trust ● Docker Security Scanning https://docs.docker.com/docker-cloud/builds/image-scan https://blog.docker.com/2016/04/docker-security http://softwaretester.info/docker-audit
- 79. bit.ly/addo-slack Find me on slack, right now!
















































![● The Docker daemon configuration
● [WARN] 2.1- Restrict network traffic between containers
● [WARN] 4.1 - Create a user for the container
● [WARN] * Running as root:
● [WARN] 5.4 - Restrict Linux Kernel Capabilities within
containers
● [WARN] * Capabilities added: CapAdd=[audit_control]
● [WARN] 5.13 - Mount container's root filesystem as readonly
● [WARN] * Container running with root FS mounted R/W:](https://image.slidesharecdn.com/alldaydevops2017-171024200558/85/Testing-Docker-Images-Security-All-day-dev-ops-2017-52-320.jpg)


























