The Art of Evolutionary Algorithms Programming
- 1. The art of Evolutionary Algorithms programming, by Dr. Juan-Julián Merelo, Esq. Calling from the University of Granada in the Old Continent of Europe
- 2. You suck
- 3. Don't worry I suck too
- 4. This is about sucking less At programming evolutionary algorithms , no less! Or any other, for that matter!
- 5. And about the zen
- 6. And about writing publishable papers painlessly through efficient, maintainable, scientific programming
- 7. 1. Mind your environment
- 8. Tools of the trade Use real operating systems.
- 9. Programmer's editor: kate, emacs, geany (your favorite editor here) + Debugger (gdb, language-specific debugger) Set up macros, syntax-highlighting and -checking, online debugging. IDE: Eclipse, NetBeans Steep learning curve, geared for Java, and too heavy on the resource usage side But worth the while eventually
- 10. 2. Open source your code and data
- 11. Aw, maaaan! Open source first, then program Scientific code should be born free Science must be reproducible
- 12. Easier for others to compare with your approach Increased H Heaven! Manifest hidden assumptions.
- 13. If you don't share, you don't care!
- 14. 3. Minimize bugs via test-driven programming
- 15. Tests before code What do you want your code to do? Mutate a bit string, for instance. Write the test Is the result different from the original? Of course!
- 16. But will it be even if you change an upstream function? Or the representation? Does it change all bits in the same proportion?
- 17. Doest it follow (roughly) the mutation rate?
- 18. Use testing frameworks Unit testing tries to catch bugs in the smallest atom of a program Interface, class, function, decision Every language has its testing framework PHPUnit, jUnit, xUnit, DejaGNU... Write tests for failure , not for success
- 19. 4. Control the source of your power
- 20. Source control systems save the day Source code management systems allow Checkpoints
- 22. Individual responsability over code changes
- 23. Branches Distributed are in : git, mercurial, bazaar
- 24. Centralized are out : subversion, cvs.
- 25. Instant backup!
- 26. Code complete Check out code/Update code
- 27. Make changes
- 28. Commit changes (and push to central repository) Check out code/Update code
- 29. Make changes
- 30. Test your code
- 31. Commit changes (and push to central repository)
- 32. 5. Be language agnostic
- 33. Language shapes thought Don't believe the hype: Compiled languages are faster... NOT Avoid programming in C in every language you use
- 34. Consider DSL: Damn Small Languages
- 35. Python, Perl, Lua, Ruby, Javascript... interpreted languages are faster.
- 36. Language agnoticism at its best Evolving Regular Expressions for GeneChip Probe Performance Prediction http://www.springerlink.com/content/j3x8r108x757876w/ The regular expresions are coded in AWK scripts: Although this may seem complex, gawk (Unix’ free interpreted pattern scanning and processing language) can handle populations of a million individuals.
- 37. Programming speed > program speed 6
- 38. Scientists, not software engineers Our deadlines are for papers – not for software releases
- 39. What should be optimized is speed-to-publish.
- 40. Make no sense to spend 90% time programming – 10 % writing paper
- 41. Scripting languages rock And maximize time-to-publish
- 42. Perl faster than Java? Algorithm::Evolutionary, a flexible Perl module for evolutionary computation http://www.springerlink.com/content/8h025g83j0q68270/ Class-by-class, Perl library much more compact Less code to write In pure EC code, Algorithm::Evolutionary was faster than ECJ
- 43. 10. Become an adept of the chosen language
- 44. Don't teach an old dog new tricks The first language you learn brands you with fire
- 45. But no two languages are the same
- 46. Every language includes very efficient solutions Regular expressions
- 49. 11 Don't assume: measure
- 50. Performance matters Basic measure: CPU time as measured by time jmerelo@penny:~/proyectos/CPAN/Algorithm-Evolutionary/benchmarks$ time perl onemax.pl 0; time: 0.003274 1; time: 0.005438 [...] 498; time: 1.006539 499; time: 1.00884 500; time: 1.010817 real 0m1.349s user 0m1.140s sys 0m0.050s
- 51. Going a bit deeper
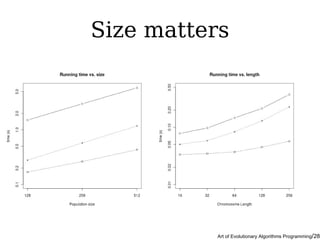
- 52. Size matters
- 53. There's always a better algorithm/ data structure 12
- 54. And differences are huge Sort algorithms are an example Plus, do you need to sort the population? Cache fitness evaluations Cache them permanently in a database? Measure how much fitness evaluation takes Thousand ways of computing fitness How do you compute the MAXONES? $fitness_of{$chromosome} = ($copy_of =~ tr/1/0/); Algorithms and data structures interact
- 55. 13 Learn the tricks of the trade
- 56. Two trades Evolutionary algorithms Become one with your algorithm It does not work, but for a different reason that what you think it does Programming languages What function is better implemented?
- 57. Is there yet another library to do sorting?
- 58. Where should you go if there's a problem? Even a third trade: programming itself.
- 59. Case study: sort Sorting is routinely used in evolutinary algorithms Roulette wheel, rank-based algorithms Faster sorts (in Perl): http://raleigh.pm.org/sorting.html Sorting implies comparing
- 60. Orcish Manoeuver, Schwartzian transform
- 61. Sort::Key, fastest ever http://search.cpan.org/dist/Sort-Key/ Do you even need sorting? Top or bottom n will do nicely sometimes
- 62. Make output processing easy 14
- 63. Avoid drowning in data Every experiment produces megabytes of data Timestamps, vectors, arrays, hashes
- 64. Difficult to understand a time from production Use serialization languages for storing data
- 65. YAML: Yet another markup language
- 66. JSON: Javascript Object Notation
- 67. XML: eXtensible Markup languajge
- 68. Name your own
- 69. Case study: Mastermind Entropy-Driven Evolutionary Approaches to the Mastermind Problem Carlos Cotta et al., http://www.springerlink.com/content/d8414476w2044g2m/ Output uses YAML
- 71. Per-run and per-generation data
- 72. Final population and run time Open source!
- 73. When everything fails visualize
- 74. 15 to 25 backup your data
- 75. Better safe than unpublished Get an old computer, and backup everything there.
- 76. In some cases, create virtual machines to reproduce one paper's environment Do you think gcc 3.2.3 will work on your new one? Use rsync, bacula or simply cp
- 77. It's not if your hard disk will fail, it's when
- 78. Cloud solutions are OK, but backup that too
- 79. 26 Keep stuff together
- 80. Where did I left my keys? Paper: program + data + graphics + experiment logs + text + revisions + referee reports + presentations
- 81. Experiments have to be rerun, graphics replotted, papers rewritten
- 82. Use logs to know which parameters produced which data which produced that graph
- 83. And put them all in the same directory tree
- 84. Get out and smell the air 27
- 85. New is always better Programming paradigms are changing on a daily basis
- 86. NoSQL, cloud computing, internet of things, Google Prediction API, map/reduce, GPGPU
- 87. Keep a balance between following fashions and finding more efficient ways of doing evolutionary algorithms. And by doing I mean publishing
- 88. Nurture your code 28
- 89. A moment of joy, a lifetime of grief Run tests periodically, or when there is a major upgrade of interpreter or upstream library. Can be automated Maintain a roadmap of releases Remember this is free software Get the community involved Your research is for the whole wide world.
- 91. (no cats were harmed doing this presentation) http://geneura.wordpress.com http://twitter.com/geneura Or camels!
Editor's Notes
- #3: CC picture from http://www.flickr.com/photos/torsteinsaltvedt/2459322441/in/photostream/
- #5: Wonderful drawing from http://www.flickr.com/photos/keeki/4264005006/in/photostream/
- #6: Picture from http://www.flickr.com/photos/imsbildarkiv/4962991603/in/photostream/ Zen means totality, and this tutorial is not just about how to write programs, but about the whole process from idea to publishing a paper in a high-impact index journal (and everything in between). So we'll make in the shape of mantras that should be followed when programming evolutionary algorithms (and probably all metaheuristics)
- #7: Picture By MarionVoss http://www.flickr.com/photos/ooocha/2869488840/in/photostream/
- #8: Forge picture from http://www.flickr.com/photos/jamesclay/1396990924/in/photostream/
- #9: You need real operating systems to speed up the gathering of tools to start. It needs to be free and gratis, so that you can have all the libraries you need, and designed for programming, not for desktop and office environment. Programmer's editors speed up coding, allowing you to check the structure of a program at first glance. Every one has his favorite program, but you need to settle for one, since you'll be much more productive with it. Emacs or vi are probably a good choice, since you can live in them and with them. NetBeans and Eclipse are free, and popular, and good, but it's overkill if you want to do small programs and scripts (which is all you need sometimes) There are other IDEs for particular languages, worth checking out.
- #10: Picture http://www.flickr.com/photos/goldenberg/22276200/in/photostream/ Now it's more important than ever to open source because research topics are more and more narrower and the code is the law
- #12: http://www.flickr.com/photos/wohinauswandern/4146824312/in/photostream/
- #14: http://www.flickr.com/photos/paulwatson/43393028/in/photostream/
- #15: http://www.flickr.com/photos/anotherpioneer/5252749975/
- #18: http://www.flickr.com/photos/youngrobv/2497132840/
- #19: Speed will depend on many factors, and every language is geared for particular features.
- #20: Aho, Weinberger, Kernighan, AWK is a data-driven language included in all Unices. Extremely mature, extremely fast, extremely unknown... and also the best tool for this paper.
- #21: Foto: http://www.flickr.com/photos/gnackgnackgnack/3297936548/in/photostream/
- #23: In fact, test by Kernighan and Pike over Markov chains, back in 99, proved the same. Things have evolved, but in both languages.
- #24: http://www.flickr.com/photos/inoxkrow/1041584485/in/photostream/
- #25: There is a balance between efficiency in programming and efficiency when doing a task. There's a power law: you can be best at one, maybe 3 languages, but at least know the potentialities of several others. Or at least know enough to tell a graduate student where she should look.
- #26: Foto de http://www.flickr.com/photos/marcelgermain/2071204651/in/photostream/
- #28: A profiler, which is available for every computer language but we show here for Perl, allows to know how much time is spent in every function, and then in every line of every function. That allows identification of bottlenecks, and surgically directed optimization.
- #29: Parameters of an evolutionary algorithm really matter, and the two main ones are chromosome and population size. This is, BTW, the first purely evolutionary-algorithmic stuff I introduce here. It can vary in complex ways, and differently depending on implementation, computer languaje, and lots of other factors. In this case what is being measured is the running time of three different implementations. Details in an upcoming paper (from SpringerLink) You probably know this already. But it's good to remember it from time to time.
- #30: How can you optimize? By looking for a better algorithm, like the cat is doing. Picture from http://www.flickr.com/photos/broterham/13140244/in/photostream/
- #31: Instead of sorting, some algorithms just need the max or two max. You have to look for the best implementation in your programming language of choice. A choide of data structure forces using lenguage function and algorithms, which might be slow or the other way round. For instance, if you use a string instead of a bitvector you will be forced to use string operations a language might not be prepared for.
- #32: Image from http://www.flickr.com/photos/adactio/502362353/in/photostream/
- #35: Imagen de http://www.flickr.com/photos/lwr/3462352862/in/photostream/
- #38: De hecho, también lo aconseja en “The practice of programming”: hacer tests estadísticos simples. It's an example of evoluitonary algorithm for MasterMind. It does not work very well: too many copies of a single one in the population. Having a YAML log allowed easy off-linen visualization of the evolution of the population.
- #39: Image from http://www.flickr.com/photos/dacran/2369215001/in/photostream/
- #41: Picture from RealBlades http://www.flickr.com/photos/xtl/3007809619/
- #43: Picture by Fernando Rodríguez, http://www.flickr.com/photos/frodrig/5317382828/
- #45: Picture by 1967geezer http://www.flickr.com/photos/chrisguise/5607158342/in/photostream/
- #47: Picture by doviende from http://www.flickr.com/photos/doviende/77324602/





























































![Golda Meir And Arab Israeli Relations 35 Years After[1]](https://cdn.slidesharecdn.com/ss_thumbnails/golda-meir-and-arabisraeli-relations-35-years-after1-1225750179327982-9-thumbnail.jpg?width=560&fit=bounds)








































































