The Cross Site Scripting Guide
- 1. *Introduction........................................................................................................................................... *Cross Site Scripting Attacks................................................................................................................. *Prevention............................................................................................................................................ *Conclusion............................................................................................................................................ Name: Daisuke Dan Website:TheHackersBay.org Twitter: @TheHackersBay
- 3. XSS stands for Cross-Site-Scripting. It is basically an attack, that is used to execute HTML and Javascript on the web-page. This attack can be done by submitting queries into text-boxes, or even into the URL. The results come back reading the text as HTML, so it executes the scripts instead of displaying them in plain text. Many people treat an XSS vulnerability as a low to medium risk vulnerability, when in reality it is a damaging attack that can lead to your users (and you) being compromised. XSS attacks are becoming a big problem and are going to become an extremely big problem if people do not educate them selves about XSS attacks and vulnerabilities, XSS vulnerabilities have been found in all sorts of websites including fbi.gov, yahoo.com, ebay.com and many other popular and important websites, a lot of administrators fail to pay attention to XSS attacks because they either don't know much about them or they do not see them as a threat, an XSS vulnerability when exploited by a skilled attacker or even a novice can be a very powerful attack. This paper details XSS attacks and hopes to educate you on what they are, how attackers use them and of course how you can prevent them from happening. Overview: Cross-site scripting (XSS) is a type of vulnerability commonly found in web applications. This vulnerability makes it possible for attackers to inject malicious code (e.g. JavaScript programs) into victim’s web browser. Using this malicious code, the attackers can steal the victim’s credentials, such as cookies. The access control policies (i.e., the same origin policy) employed by the browser to protect those credentials can be bypassed by exploiting the XSS vulnerability. Vulnerabilities of this kind can potentially lead to large-scale attacks. - HTML HTML is sort of like a programming language. The distinctions between a programming language, and HTML, are not too far apart. They are both languages, that are used to create attributes, and events. HTML is a markup language, which is used mostly to create websites. HTML stands for Hyper-Text Markup Language. You can use HTML to create forms, buttons, and other stuff that can be used in a webpage. I highly doubt you will ever encounter a website that does not contain even a slight amount of HTML. - JavaScript Now, first, let's get one thing straight. There is a HUGE difference between JAVA and JAVASCRIPT. Java, is a language that ressembles to C++, it can be used in games, and applications. Javascript is sort of similar to HTML, but definitely different in many ways. Javascript isn't used NEARLY as much in Webpages than HTML is. Javascript is used, more in applications outside of webpages. Like PDFs. Javascript can be an incredibly useful language along with HTML. They are both fairly simple to learn, and are very dynamic.
- 5. The Cross Site scripting is one of the problem that has plagued a lot of websites. As a web developer, it is important to understand what is cross site scripting and how can we safeguard our site from such attacks. Now the question would be how can a person inject scripts on a running page. This can easily be done using all the various ways a website is collecting inputs. Cross site scripting can be performed by passing scripts in form of: *TextBox *Cookies *Query Strings *Web application variables *Session variables What can you do with Xss Attacks? *Attackers inject JavaScript, ActiveX, or HTML, into a vulnerable application, exploiting XSS holes. *The browser processes the injected code as if it were legitimate content of the web page - with the corresponding security permissions. *Many attack could exploit flaws or vulnerabilities due to bad programming. *Pillage of settings and user sensitive information. Possible Attacks? *Phishing: Criminal fraudulent process of attempting to acquire sensitive information such as usernames, passwords and credit card details, by masque rading as a trustworthy entity in an electronic communication or as a business or individual. *Cookie Stealing: Cookie is used to manage sessions in browsers. Each person logged in gets a unique cookie, it is like a key to the site. *Account hijacking: Term used when malware infiltrates a system without the consent and performs tasks set by its creator in addition to (or instead of) the system's normal duties. *Changing of user settings: A scammer could take information about web sites administrator in order to access to sensitive data or modifying user settings. Basic types of XSS Attacks? STORED XSS: In the “STORED XSS” (persistent XSS),an attacker can inject the malicious code into the page persistently and that means the code will be STORED in the server. And this code will be STORED in the page which will show to the visitors later on. If the visitor goes to the page which is embedded with XSS attacking code, the code will execute on the visitor‟s computer. Hackers usually post these codes into the article in the forum or blog in order to let other users to read in the future and attack more them. Compared with “REFLECTED XSS”, this type of XSS does more serious harm. If the “STORED XSS” vulnerability is successfully exploited by hackers, it will persistently attack the users until administrator remove this vulnerability.
- 6. Example of Stored XSS: guestbook.php Then page guestbook.php lists all entries returned by the previous function, without sanitizing the content of the comments. It is only applied to the names (see function h() in the next section): [---------------------------------------CODE---------------------------------------] <?php if ($guestbook) { foreach ($guestbook as $guest) { ?> <p class="comment"><?= $guest[" XSS SCRIPT "] ?></p> <p> - by <?=h( $guest["name"] ) ?> </p> <?php } ?> [---------------------------------------END CODE---------------------------------------]
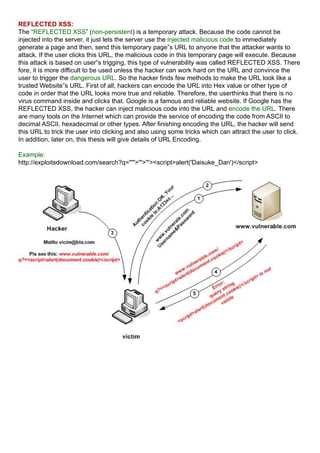
- 7. REFLECTED XSS: The “REFLECTED XSS” (non-persistent) is a temporary attack. Because the code cannot be injected into the server, it just lets the server use the injected malicious code to immediately generate a page and then, send this temporary page‟s URL to anyone that the attacker wants to attack. If the user clicks this URL, the malicious code in this temporary page will execute. Because this attack is based on user‟s trigging, this type of vulnerability was called REFLECTED XSS. There fore, it is more difficult to be used unless the hacker can work hard on the URL and convince the user to trigger the dangerous URL. So the hacker finds few methods to make the URL look like a trusted Website‟s URL. First of all, hackers can encode the URL into Hex value or other type of code in order that the URL looks more true and reliable. Therefore, the userthinks that there is no virus command inside and clicks that. Google is a famous and reliable website. If Google has the REFLECTED XSS, the hacker can inject malicious code into the URL and encode the URL. There are many tools on the Internet which can provide the service of encoding the code from ASCII to decimal ASCII, hexadecimal or other types. After finishing encoding the URL, the hacker will send this URL to trick the user into clicking and also using some tricks which can attract the user to click. In addition, later on, this thesis will give details of URL Encoding. Example: http://exploitsdownload.com/search?q="'">'">'"><script>alert('Daisuke_Dan')</script>
- 8. DOM-Based XSS: The DOM-based XSS attack is another type of XSS vulnerability which is commonly used by hackers as well. What is DOM-based XSS? First of all, we need to know what DOM is. DOM is short for Document Object Model and it is a platform and language - neutral interface which is using scripting or program to modify the content, update the date, structure and style of documents. It is widely used in HTML and XML in Web 2.0. DOM in HTML can generate a tree - structure of HTML documents. However, DOM allows the scripting or program to change the HTML or XML document, the HTML or XML document can be modified by a hackers scripting or program. DOM-based XSS uses DOM's vulnerability to make the XSS come true. This type of XSS vulnerability is totally different from the REFLECTED or STORED XSS attack and it does not inject malicious code into a page. So, it is the problem of the insecure DOM object which can be controlled by the client side in the web page or application. For this reason, hackers can let the attack payload execute in the DOM environment to attack the Victim side.
- 9. The following snippets of HTML demonstrate how to safely render untrusted data in a variety of different contexts.
- 10. Safe HTML Attributes include: align, alink, alt, bgcolor, border, cellpadding, cellspacing, class, color, cols, colspan, coords, dir, face, height, hspace, ismap, lang, marginheight, marginwidth, multiple, nohref, noresize, noshade, nowrap, ref, rel, rev, rows, rowspan, scrolling, shape, span, summary, tabindex, title, usemap, valign, value, vlink, vspace, width. Sanitize the input, all user submitted input anywhere in an application must be treated as hostile and filtered. This should be done by the application code, but can also be performed by a web application firewall (WAF) such as mod_security. The most effective way to prevent this is to do both, use well coded applications and have a WAF or filtering as a second line of defense. A common initial preventative to viral infection is a network level firewall. As HTTP/HTTPS protocols are afforded unfettered access through common firewall configurations, these firewall barriers are ineffectual. A potential remedy to this is an application firewall with the appropriate XSS virus signatures. Whilst unlikely, the most obvious way to prevent XSS viruses is to remove XSS vulnerabilities from web applications. Conclusion? Cross-site scripting (XSS) is one of the most frequent vulnerabilities found in modern web applications. Never-theless, many service providers are either not willing or not able to provide sufficient protection to their users. This paper proposes a novel, client-side solution to this problem. By modifying the popular Firefox web browser, we are able to dynamically track the flow of sensitive values (e.g., user cookies) on the client side. Whenever such a sensitive value is aboutto be transferredto a third party(i.e., the adversary), the user is given the possibility to stop the connection. To censure protection against more subtle types of XSS attacks that try to leak information through non-dynamic control dependencies,we additionallyemploy an auxiliary, efficient static analysis, where necessary. With this combination of dynamic and static techniques, we are able to protect the user against XSS attacks in a reliable and efficient way. To validate our concepts, we automatically tested the enhanced browser on more than one million web pages by means of a crawler that is capable of interpreting JavaScript code. The results of this large-scale evaluation demonstrate that only a small number of false positives is generated, and that our underlying concepts are feasible in practice.





![Example of Stored XSS: guestbook.php
Then page guestbook.php lists all entries returned by the previous function, without sanitizing the
content of the comments. It is only applied to the names (see function h() in the next section):
[---------------------------------------CODE---------------------------------------]
<?php
if ($guestbook)
{
foreach ($guestbook as $guest)
{
?>
<p class="comment"><?= $guest[" XSS SCRIPT "] ?></p>
<p> - by <?=h( $guest["name"] ) ?> </p>
<?php
} ?>
[---------------------------------------END CODE---------------------------------------]](https://image.slidesharecdn.com/16rtalkcs9cdb2jrovc8-140604101932-phpapp01/85/The-Cross-Site-Scripting-Guide-6-320.jpg)