The real incident of stealing a droid app+data
- 1. The Real Incident of Stealing a Droid App & Data Akash Mahajan and Ankur Bhargava @ DroidCon Bangalore 2012
- 2. What we stole The Android Application Package File All the encrypted files found in the external storage © Akash Mahajan DroidCon Bangalore 2012 2
- 3. Not only we successfully the app + data we it on another device which was rooted © Akash Mahajan DroidCon Bangalore 2012 3
- 4. Them devs made it more secure? A device ID check was added We reversed the applications added our device ID and compiled it again. Able to execute again, yay! © Akash Mahajan DroidCon Bangalore 2012 4
- 5. THE DROID JOB A standard Chinese made Tablet running Android 4.0 (Indian Brand) The application contained encrypted data along with other resources. © Akash Mahajan DroidCon Bangalore 2012 5
- 6. We had written permission to steal! © Akash Mahajan DroidCon Bangalore 2012 6
- 7. All your data are belong to us All the encrypted data was with us We didn’t have the encryption key But we had the device with the key in internal storage © Akash Mahajan DroidCon Bangalore 2012 7
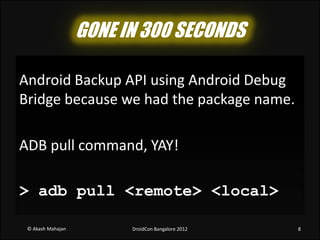
- 8. GONE IN 300 SECONDS Android Backup API using Android Debug Bridge because we had the package name. ADB pull command, YAY! > adb pull <remote> <local> © Akash Mahajan DroidCon Bangalore 2012 8
- 9. DISCLAIMER It is not Rocket Science Simple common security testing © Akash Mahajan DroidCon Bangalore 2012 9
- 10. The Simple Hack We knew find an exploit to root the device might take some time and skill Application written for the same version of Android will run in all devices © Akash Mahajan DroidCon Bangalore 2012 10
- 11. If the device having the application can’t be rooted, let us take the application to the rooted device. © Akash Mahajan DroidCon Bangalore 2012 11
- 12. The Simple Hack Once copied to the rooted device we could see what the application was doing using DDMS. Dalvik Debug Monitor Server provides among other things process information about apps running on a device connected in USB debug mode. © Akash Mahajan DroidCon Bangalore 2012 12
- 13. The key to everything In this particular case, the encryption key was required to decrypt the data. We didn’t have file permissions to reach the key. We decided not to go after the key. We weren’t being paid enough for that. © Akash Mahajan DroidCon Bangalore 2012 13
- 14. The Encryption Conundrum If you give away your device, the only way you can ensure safety of the data is by ensuring that the symmetric encryption key isn’t stolen. At any given point depending on the application the key might be available in memory, temp file/storage or on the chip itself. © Akash Mahajan DroidCon Bangalore 2012 14
- 15. The Encryption Conundrum But because the device is with the thieves, they have all the time in the world to find it. If nothing works, they can always break open the device and steal the key from the storage. © Akash Mahajan DroidCon Bangalore 2012 15
- 16. FREE CONSULTING /Checklist Disable USB debugging port Disable USB itself Don’t give internet access in the device. Obfuscate the source code. Provide a unique key for each device. © Akash Mahajan DroidCon Bangalore 2012 16
- 17. SUCCESS KIDZ Client felt assured about their device security Dev had a more secure solution We get to pretend that we are Android security experts. We are not, just love the challenge. © Akash Mahajan DroidCon Bangalore 2012 17
- 18. WANTED DROID CHORS @ankurbhargava87 @makash © Akash Mahajan DroidCon Bangalore 2012 18