The Web Application Hackers Toolchain
- 2. About Me: • Twitter @jhaddix • [email protected] • I blog like I know stuff: • http://www.securityaegis.com • http://www.ethicalhacker.net • Former VA/Netpen turned Webpen • Currently work for HP Application Security Center • Webpen, Netpen, Mobile, etc… • Random Projects • Open Penetration Testers Bookmark Collection • http://code.google.com/p/pentest-bookmarks/ • Nmap Http-enum fingerprints • ghetto Nessus parsers • Burp hacking presentation • No I can’t get you a touchpad • I love talking about hacking, and I like to drink Beer & Gin and Tonics • I don’t know if that’s a girly drink in Brussels =( • You’re welcome to educate me…
- 3. Words for the Wise: “Until a man is twenty-five, he still thinks, every so often, that under the right circumstances he could be the baddest motherfucker in the world. If (he) moved to a martial-arts monastery in China and studied real hard for ten years. If (his) family was wiped out by Colombian drug dealers and (he) swore (himself) to revenge. If (he) got a fatal disease, had one year to live, and devoted it to wiping out street crime. If (he) just dropped out and devoted (his) life to being bad. Hiro used to feel this way, too, but then he ran into Raven. In a way, this was liberating. He no longer has to worry about being the baddest motherfucker in the world. The position is taken.” ― Neal Stephenson, Snow Crash
- 4. Workshop: Done a few conference talks, never done a workshop: • I’m going to move fast, you will get the slides from the con. • Videos for demos available shortly after the conference • If there’s something you want to know just pull me aside sometime or catch me around the con, I’ll do my best to answer all questions. • You’re pretty much getting a whole class converted to a workshop =). • Excuses! • http://code.google.com/p/owaspbwa/ • OK… lets do it.
- 6. • Web Hacking Tool Classes: • OSINT (Passive or Semi-Passive) • Discovery (usually dir brute-forcing or platform identification) • Brute Force (password bruting tools) • Proxies (usually include spider’s) • Fuzzers/Scanners (error or vuln identification tools) • Exploitation (vuln exploitation tools) • Data Aggregation
- 7. • What am I, a script kiddie? •Yes and no, you’re a pentester; Which means you have approximately 40hrs to do what a blackhat has months to do. •We need to identify technologies faster, vulns faster, and speed up the attack process. •We need to identify the best process and tools to use, even for our manual web pentesting.
- 8. GOAL: Gather data to be useful in a web pentest without (or minimally) interacting with the target. Google Hacking: SearchDiggity Metadata: FOCA Email Gathering: TheHarvester Metasploit
- 9. SearchDiggity: The SearchDiggity tools are basically automation of google/bing hacking queries. Think of about a thousand vulnerability checks executed against your target except they are not actually touching your target, only the search engine cache.
- 10. GOAL: Free vulnerability checks aka Google hacking. SearchDiggity: • Requires Ajax Search Query API key • 100 queries per day unless you register a CC • Buy a pre-paid visa for $10 • Find vulns fast
- 11. GOAL: Extract domain usernames, internal pathing, software versions, etc FOCA: FOCA is a windows tool to spider a domain for documents using google/bing/exalead, download them, and then extract relevant metadata and server information. • http://www.informatica64.com/DownloadFOCA/ I always go see these guys at DC: • http://vimeo.com/10602662 • http://vimeo.com/16706893
- 13. GOAL: Extract domain usernames, internal pathing, etc
- 14. GOAL: Gather email addresses for forms based logins, etc. One of the first parts of recon in a pentest is gathering valid login names and emails. We can use these to profile our target, bruteforce authentication systems, send client-side attacks (through phishing), look through social networks for juicy info on platforms and technologies, etc. Where do we get this info? Well without doing a full-blown Open Source Recon (OSINT) style assessment, we can use two simple scripts: • Metasploit's search_email_collector.rb and • theHarvester
- 15. Metasploit, under modules/auxiliary/gather, has search_email_collector.rb and uses search techniques for Google, Bing, and Yahoo. http://www.metasploit.com/modules/auxiliary/gather/search_email_collector ruby /framework3/msfcli auxiliary/gather/search_email_collector DOMAIN=your_target_domain OUTFILE=output_file E Running MSF search_email_collector... [*] Please wait while we load the module tree... [*] Harvesting emails ..... [*] Searching Google for email addresses from defcon.com [*] Extracting emails from Google search results... [*] Searching Bing email addresses from defcon.com [*] Extracting emails from Bing search results... [*] Searching Yahoo for email addresses from defcon.com [*] Extracting emails from Yahoo search results... [*] Located 7 email addresses for defcon.com [*] [email protected] [*] [email protected] [*] [email protected] [*] [email protected] [*] [email protected] [*] [email protected] [*] [email protected]
- 16. theHarvester (just updated to v2.1) has now fixed some of its previous bugs. It supports searching Google, Bing, PGP servers, shodan, dns- bruteforcing, and LinkedIn. https://code.google.com/p/theharvester/ zombie@haktop:/tools/email/theHarvester# ./theHarvester.py -d defcon.com -b google -l 500 Accounts found: =================== [email protected] [email protected] [email protected] [email protected] [email protected] [email protected] [email protected]
- 17. theHarvester:
- 18. There’s also a ton of OSINT sites to help identify server information without ever touching your target yourself: • Netcraft (Uptime Survey, server info) • Domain Tools (Whois Lookup and Domain info) • Centralops.net (traceroute, nslookup, automatic whois lookup, ping, finger) • Hackerfantastic.com ( GeoIP, whois, host, dig, blacklists, ping, traceroute & nmap) • whois.webhosting.info (WHOIS and Reverse IP Service/virtual hosting info) • BING IP Search • SSL Labs – Projects / Public SSL Server Database – SSL Server Test • SHODAN – Computer Search Engine (indexed port scans and banner grabs) • Chris Gates presented on OSINT at Brucon 2009 • http://vimeo.com/6811411 • Other good OSINT resources: • http://www.slideshare.net/agent0x0/enterprise-open-source- intelligence-gathering • http://www.slideshare.net/Laramies/tactical-information-gathering
- 19. Now we need to map the site. Some issues that we need to deal with when mapping the site are poor ajax support for spidering (we go over this later) and finding non-linked resources. To find non linked resources we bruteforce common file/path names, framework paths, etc. Discovery Tools: • Dirbuster & Wfuzz • SVNDigger Lists • FuzzDB and RAFT Lists • (optionally) Nmap HTTP-Enum & CMS Explorer
- 20. Dirbuster is a cross platform directory bruteforcer written in java (GUI app). Tips: • Disable Recursion and Redirects for faster leaner bruting (our spiders will follow redirects later) • We can change threading on the fly • Dirbuster’s built-in lists are from a project that basically spidered the whole internet.
- 21. Wfuzz is a command line equivalent, with a bit more functionality for general web fuzzing (filter by resp code, wc, charc, etc): • http://www.edge-security.com/wfuzz.php Also has some lists!
- 22. 301’s sometimes redirect to very interesting subdomains or promo pages.
- 23. Alright, so for non linked resources and discovery we can use Dirbuster’s lists or Wfuzz’s but they are very generic (that’s not necessarily a bad thing). Like I mentioned before, Dirbuster’s are based off of spidering the net and aggregating the most common directory data and common words (partially). But isn't that finding linked resources? Yes There are some more options for us as far as lists go: SVNDigger – a set of directory lists based of pathing of open source projects on Google Code and SourceForge. RAFT Lists: http://code.google.com/p/fuzzdb/ Within the Discovery/PredictableRes path
- 24. http://www.mavitunasecurity.com/blo g/svn-digger-better-lists-for-forced- browsing/ SourceForge and GoogleCode, 400k words (5000 projects), directories sorted by project: • Type • Extension contained • Context • DB Type Most coverage/success running the “all” lists, pick as you need.
- 25. RAFT is a recent proxy project released at BHUSA 2011, with a set of wordlists for content discovery based upon spidering 1.7 million “robots.txt” disallows and contextual framework paths. There’s some overlap with SVNDigger. The lists themselves are downloadable from the RAFT site but they are also contained in the FuzzDB Discovery/PredictableRes directory which we’ll be seeing in the tactical fuzzing section later. Broken down into directories, words, and files which takes us to smarter recursive content discovery…
- 26. 1. Use raft-large-directories in Dirbuster or Burp 2. Take the successful output and add it to a Burp Intruder setup (clusterbomb) as payload set 1 3. Add raft-large-files.txt as 2nd payload set
- 28. Storytime
- 29. Hopefully at this point we have some logins or emails to try and bruteforce authentication from the OSINT section. I prefer Burp Suite’s Intruder Module for bruteforcing authentication. 1. Attempt Login 2. Go to Proxy History Tab 3. Find the POST request 4. Send to Intruder 5. Use Cluster Bomb payload 6. Clear all payload positions 7. Mark username and password fields as payload positions 8. Goto “payloads” tab 9. Set “payload set” 1 to your username list 10. Set “payload set” 2 to your password list 11. Click on the intruder Menu 12. Start Attack 13. Look for different lengths or grep possible successful auth messages under options
- 30. With some valid usernames we want to up our chances of bruting a valid password. Ron Bowes (@iagox86) has some fantastic password research and has archived many of the lists that have been leaked on the web. http://www.skullsecurity.org/blog/2010/the-ultimate-faceoff-between- password-lists Huge password repository. Actual user data from hacked sites: • RockYou (Rockyou 75 is a winner) • Phpbb • Myspace • Hotmail • Hak5 • Facebook • More…
- 31. Just a few…
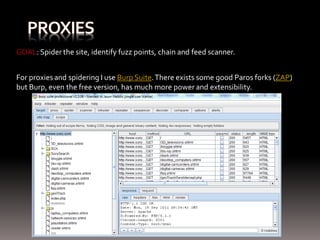
- 32. GOAL: Spider the site, identify fuzz points, chain and feed scanner. For proxies and spidering I use Burp Suite. There exists some good Paros forks (ZAP) but Burp, even the free version, has much more power and extensibility.
- 33. Fiddler is a unique and powerful option as well due to some great plugins such as Watcher (for passively identifying user controllable )and x5s (for identifying possible xss insertion points). These can help us later when we want to start tacitly fuzzing.
- 35. Proxies sit between you and the browser but they can also enhance your testing by chaining them with your other tools. This is great if your scanner has a proxy mode, this way we get walk through the functionality of the site and hit it with two different spider engines and finally attack it with our scanner. Additionally, chaining proxies and scanners can help us deal with auth/session issues in hard to scan environments (NTLM/Kerberos). If you’re sticking with open source tools or non-proxy mode scanners you can export your spider results as links and import them into you scanner. Browser -> Burp -> Scanner (in proxy mode) -> Site 1. Walk app, executing all Ajax and rich functionality (snaplinks is handy) 2. Browse to anything from the discovery stage to populate proxy and scanner 3. Spider with Proxy of choice 4. (optional, this might pollute your site tree) Fuzz with fuzzer/proxy of choice 5. Run Scan This all gets fed to the scanner sitemap/tree. Now the scanner has the best chance of finding all fuzz points and vulns.
- 36. You said scanners! Which ones?! Shay Chen has some excellent research on the accuracy of open source and commercial scanners. Only covers XSS and SQLi atm
- 37. Now that you have the blanket stuff out of the way, its time to interpret the proxy and scanner data for tactical fuzzing points. Does this functionality display something back to the user? Fuzz for XSS Does it interact with a database? Fuzz for SQLi or other injections Does it call on the server file system? Fuzz for LFI/PT Does it call on a URL or external/internal site/domain? Fuzz for RFI Tactical Fuzzing? Wtf?
- 38. Now we can fully utilize the project we mentioned a few times earlier, the Fuzz Database: “ The fuzzdb aggregates known attack patterns, predictable resource names, server response messages, and other resources like web shells into the most comprehensive Open Source database of malicious and malformed input test cases.”
- 39. 1. Use Fuzzdb strings on all the afore mentioned forms and parameters 2. Re-fuzz all parameters that gave errors on the spidering/scanning results. 3. After concretely identifying the platform, re-fuzz/content discover with that platforms specific lists.
- 40. The fuzzdb also has an excellent error /vuln grep file for import into Burp:
- 41. When it comes to exploitation tools mostly we need some automagic tools to exploit different forms of SQL injection or file include vulnerabilities. For manual testing we also need a set of web shells. Our standards are SQLmap, Havij, SQLninja for sql injection fimap and metasploit for file include vulnerabilities. and a common set of web shells from the fuzzdb .
- 42. SQLmap is a comprehensive SQL injection tool with the ability to do many forms of injection. SQLmap Tips: -l can import Burp logs to test your hosts (when saving in Burp use only your targets in scope) ./sqlmap -l /root/sqli.txt Often we want to force POST parameters ,setting –data will force POST: -- data=userid=test&pass=test We can specify parameters with -p : ./sqlmap –u TARGET-p userid,pass --level=LEVEL Level of tests to perform (1-5, default 1) has to do with insertion points. --risk=RISK Risk of tests to perform (0-3, default 1) has to do with test cases. ./sqlmap -l /root/sqli.txt --level=5 --risk=3 You can max out speed at threads=10 --forms will parse and test all forms on target --os-pwn for possible meterpreter shell
- 43. Other tools mentioned help us in edge cases: Havij for very up to date WAF evasion (modsec) Use at your own risk. http://itsecteam.com/en/projects/project1.htm SQLNinja when SQLmap will not exploit http://sqlninja.sourceforge.net/ Fimap for file include exploitation http://code.google.com/p/fimap/ Metasploit for remote file includes exploit/unix/webapp/php_include
- 45. We also need some stand alone shells in several different languages for upload vulns. Luckily the FuzzDB has these as well.
- 46. What about taking XSS beyond alert(‘xss’)? BeEF is the best tool for javascript attacks. It’s more extensible now that it integrates with metasploit. We now can: Hook the browser with invisible iframes Inject/change content on the fly Footprint the internal network Sniff keystrokes Deliver browser based exploits or metasploit meterpreter java payloads for full control of the target
- 47. Video
- 48. What about web services, SOAP, XML? With a wsdl and SOAPui proxied through Burp and tactically fuzzing with the Fuzzdb test cases we can do more than any script or tool I’ve seen released.
- 49. I don’t have a fancy portal to put my data =( The Dradis framework has been revamped to accept a ton for tool outputs allowing us to import data and keep working faster. Imports: Nmap Burp Nessus Metasploit Netsparker Openvas w3af Mindmapping software works well too.
- 51. With all this out of the way semi-quickly we can now take more time to tactically fuzz and test for logic and more obscure manual checks!
- 52. Special thanks go out to: Andre Gironda Chris Gates, Armando Romeo, Joe McCray, James Fitts, Bernardo Damele, Daniel Miessler, Ferruh Mavituna, Shay Chen, Ron Bowes, Adam Muntner, and all tool authors.















![Metasploit, under modules/auxiliary/gather, has search_email_collector.rb and
uses search techniques for Google, Bing, and Yahoo.
http://www.metasploit.com/modules/auxiliary/gather/search_email_collector
ruby /framework3/msfcli auxiliary/gather/search_email_collector DOMAIN=your_target_domain OUTFILE=output_file E
Running MSF search_email_collector...
[*] Please wait while we load the module tree...
[*] Harvesting emails .....
[*] Searching Google for email addresses from defcon.com
[*] Extracting emails from Google search results...
[*] Searching Bing email addresses from defcon.com
[*] Extracting emails from Bing search results...
[*] Searching Yahoo for email addresses from defcon.com
[*] Extracting emails from Yahoo search results...
[*] Located 7 email addresses for defcon.com
[*] headsets@defcon.com
[*] info@defcon.com
[*] jobs@defcon.com
[*] nick.s@defcon.com
[*] nick@defcon.com
[*] robert@defcon.com
[*] spr@defcon.com](https://image.slidesharecdn.com/waht-130113230113-phpapp01/85/The-Web-Application-Hackers-Toolchain-15-320.jpg)