Traefik 2.x features - canary deployment with Traefik and K3S
1 like261 views
Traefik 2.x has implemented a few new features such as canary deployment, mirroring, and great integration with Kubernetes via CRD.
1 of 28
Download to read offline

























Ad
Recommended
How to configure port security in cisco switch



How to configure port security in cisco switchIT Tech This document provides instructions for configuring several security and management features on a Cisco switch, including:
1) Configuring the IP address, subnet mask, and default gateway to enable remote access via telnet or SSH.
2) Enabling telnet and setting login passwords to restrict access.
3) Enabling port security to restrict which devices can connect to a port and shut down ports with unauthorized MAC addresses.
4) Configuring EtherChannel to combine switch ports to increase bandwidth while preventing loops.
NAT Traversal



NAT TraversalDavide Carboni This document discusses various techniques for allowing peer-to-peer communication between hosts located behind Network Address Translation (NAT) devices, including NAT traversal using UDP hole punching, TCP hole punching, relaying, connection reversal, and the TURN protocol. It also covers proxy protocols like SOCKS that can be used to traverse NATs, as well as the UPnP standard for automatic port forwarding configuration.
Canary deployment with Traefik and K3S



Canary deployment with Traefik and K3SJakub Hajek This time we'll talk about "Canary Deployment with Traefik". You'll learn what Canary Deployment is and why we should do it in the first place. You'll also have the chance to see a technical live demo.
⚙ Jakub Hajek is going to present a cluster built using K3S (Kubernetes light version), on which he will do Traefik deployment version 2.x and a test application. Then, we will release a newer version and check how we can control the traffic between different versions of the application, deployed in one environment.
pfSense Installation Slide



pfSense Installation SlideSopon Tumchota This document provides instructions for installing pfSense software on firewall appliances. It describes choosing installation types like full install or embedded, downloading the pfSense image, preparing installation media, performing the installation, assigning interfaces, configuring the default settings, and troubleshooting installation issues. The document is intended to guide users through the end-to-end pfSense installation process.
Kubernetes Introduction



Kubernetes IntroductionPeng Xiao This document provides an overview of Kubernetes, an open-source system for automating deployment, scaling, and management of containerized applications. It describes Kubernetes' architecture including nodes, pods, replication controllers, services, and networking. It also discusses how to set up Kubernetes environments using Minikube or kubeadm and get started deploying pods and services.
Understanding docker networking



Understanding docker networkingLorenzo Fontana The document discusses different Docker networking drivers including null, host, bridge, overlay, and macvlan/ipvlan networks. It provides examples of creating networks with each driver and how containers on different networks will connect and obtain IPs. Specifically, it shows how the bridge driver sets up a private Docker bridge network (docker0 by default) and how overlay networks use VXLAN tunnels to connect containers across multiple Docker daemons.
FortiMail



FortiMailTestSpam1 The document provides information about FortiMail email security solutions. It begins with background on the increasing threats posed by email and how email is a primary attack vector. It then summarizes the key features of FortiMail, including comprehensive protection against threats, validated performance through third-party testing, integration with the Fortinet Security Fabric, and being powered by FortiGuard Labs threat intelligence. Additional services that complement FortiMail are described such as email continuity and dynamic image analysis. The document concludes by emphasizing how FortiMail provides advanced email security against the full spectrum of email threats.
Firewall and NAT Fundamentals - pfSense Hangout January 2014



Firewall and NAT Fundamentals - pfSense Hangout January 2014Netgate The document summarizes updates from a January 2014 pfSense Hang Out. It discusses the launch of an online store for pfSense merchandise, a new website, and an updated pfSense book. An upcoming 2.1.1 release was outlined which will contain bug and security fixes. Development of the 2.2 release was also mentioned, including using FreeBSD 10.0 as the base and new features like improved wireless support and NAT ordering options. The hang out included tutorials on firewall and NAT fundamentals and basic network setups. Future tutorial topics and questions were solicited by email.
Wi fi protected access



Wi fi protected accessLopamudra Das This is the the technology which is very basic understanding on Wi- Fi technology..
What is Wi-Fi technology and how is working and also the advantages of wi-fi.....
Secret Management with Hashicorp’s Vault



Secret Management with Hashicorp’s VaultAWS Germany When running a Kubernetes Cluster in AWS there are secrets like AWS and Kubernetes credentials, access information for databases or integration with the company LDAP that need to be stored and managed.
HashiCorp’s Vault secures, stores, and controls access to tokens, passwords, certificates, API keys, and other secrets . It handles leasing, key revocation, key rolling, and auditing.
This talk will give an overview of secret management in general and Vault’s concepts. The talk will explain how to make use of Vault’s extensive feature set and show patterns that implement integration between Kubernetes applications and Vault.
How Secure are IPsec and SSL VPN encryptions



How Secure are IPsec and SSL VPN encryptionsUday Bhatia Virtual Private Networks (VPNs) provide security and privacy to private and public networks. There are different types of VPNs including site-to-site for connecting entire networks and remote VPNs for individual remote access. VPNs use encryption techniques like symmetric, asymmetric, and public key infrastructure to securely encrypt data during transmission. SSL/TLS uses public key encryption to establish secure links between servers and clients, while IPsec is a protocol suite that authenticates and encrypts individual IP packets to provide secure IP communications. Diffie-Hellman key exchange allows two parties to jointly establish a shared secret over an insecure channel.
Build and run embedded apps faster from qt creator with docker



Build and run embedded apps faster from qt creator with dockerQt This document discusses using Docker containers to build and run embedded Qt applications from QtCreator more efficiently. It proposes wrapping CMake calls in a Docker script to build apps in containers on the local workstation instead of virtual machines. The key steps are installing a Qt SDK in a container, configuring QtCreator kits to use the Docker wrapper script for builds, and setting up deployment to run the built apps on target devices via SSH. This allows reusing existing container builds on a powerful workstation for faster development compared to building each app version's SDK in a separate virtual machine.
Hacking the swisscom modem



Hacking the swisscom modemCyber Security Alliance The document discusses hacking the Swisscom modem by exploiting default credentials to gain access. Upon login, the author runs commands to investigate the system such as viewing configuration files and mapping the internal network. Various system details are discovered including the Linux kernel version and software components.
Building a scalable microservice architecture with envoy, kubernetes and istio



Building a scalable microservice architecture with envoy, kubernetes and istioSAMIR BEHARA Talk from O'Reilly Software Architecture Conference San Jose 2019
Microservices and containers have taken the software industry by storm. Transitioning from a monolith to microservices enables you to deploy your application more frequently, independently, and reliably. However, microservice architecture has its own challenges, and it has to deal with the same problems encountered while designing distributed systems.
Enter service mesh technology to the rescue. A service mesh reduces the complexity associated with microservices and provides functionality like load balancing, service discovery, traffic management, circuit breaking, telemetry, fault injection, and more. Istio is one of the best implementations of a service mesh at this point, while Kubernetes provides a platform for running microservices and automating deployment of containerized applications.
Join Samir Behara to go beyond the buzz and understand microservices and service mesh technologies.
Ip Spoofing



Ip SpoofingDhrumil Shah IP spoofing is when an attacker forges the source IP address in IP packets sent to a computer network to conceal their identity or impersonate another system. It is done by determining the IP address of a trusted system and modifying packet headers to appear to come from that system. Services vulnerable to IP spoofing include RPC, services using IP address authentication, the X Window System, and R services. Types of IP spoofing include blind spoofing, non-blind spoofing, denial of service attacks, and man-in-the-middle attacks. Countermeasures include packet filtering, filtering at routers, and disabling vulnerable commands.
Dell VLT reference architecture v2 0



Dell VLT reference architecture v2 0David Pasek This document explains the dual node VLT deployment strategies with its associated network reference architecture. Various VLT deployment topologies are also explained with emphasis on best practices and recommendations for some of the network scenarios. This document also covers the configuration and troubleshooting of VLT using relevant show commands and different outputs.
Board Support Package Fact Sheet | Manual Guide



Board Support Package Fact Sheet | Manual GuideEmbitel Technologies - A VOLKSWAGEN GROUP COMPANY Board Support Package contains Low level device driver and HAL layer. It is the essential to boot the system. By this virtue, BSP finds its application in almost every automotive ECU software.We offer our Board Support Package (BSP) on a one-time license fee model. This model makes our customers the owner of the entire BSP source code along with the solution IP rights.
VLAN and its implementation 



VLAN and its implementation Mohit Kumar CONTENT
1. Acknowledgement
2. Certificate
3. Certificate of Approval
4. Problem Definition-Defining the problem.
5. Introduction
6. Network and It‘s Types
7. Actual Topic- VLAN
8. VLAN Membership
9. VTP
10. Implementation
11. Conclusion
IS-IS Protocol Introduction



IS-IS Protocol IntroductionNetProtocol Xpert IS-IS is an interior gateway protocol that uses link-state routing and SPF algorithms to calculate the shortest path. It supports both CLNP and IP and has three routing levels - level 1 for intra-area routing, level 2 for inter-area routing, and level 1/2 routers that connect levels 1 and 2. There are three types of IS-IS routers: level 1 that exchange intra-area topology, level 2 that exchange inter-area topology, and level 1/2 that act as border routers between levels 1 and 2.
VoIP and data communication using cisco packet tracer



VoIP and data communication using cisco packet tracerFikri Paramadina From this simulation, we will know how to configure :
Routing and Switching, Vlan for data and telephony, Redistribute between different routing protocols, DHCP IP, and VoIP with the Dial Peer Communication.
LXC, Docker, security: is it safe to run applications in Linux Containers?



LXC, Docker, security: is it safe to run applications in Linux Containers?Jérôme Petazzoni The document discusses the security of running applications in Linux containers. It begins by acknowledging that containers were not originally designed with security in mind. However, it then outlines several techniques that can be used to improve security, such as running containers without root privileges, dropping capabilities, enabling security modules like SELinux, and limiting access to devices and system calls. For the most security-sensitive tasks, it recommends running containers inside virtual machines to isolate them further. In the end, it argues that with the right precautions, containers can be used securely for many applications.
Cisco router basic



Cisco router basicTapan Khilar Routing is the method by which network devices direct messages across networks to arrive at the correct destination. Routers use routing tables containing information about locally-connected networks and remote networks to determine the best path to send packets. The routing table includes details like the destination, mask, gateway, and cost for each route.
Console Menu - pfSense Hangout December 2016



Console Menu - pfSense Hangout December 2016Netgate This document provides instructions for accessing and using the console menu in pfSense. It begins by covering the requirements and setup for the different console access methods like keyboard/video, serial, and SSH. It then describes each of the tasks available in the console menu like assigning interfaces, resetting passwords/defaults, rebooting, and accessing diagnostic tools. Key tasks include interface configuration, resetting passwords, rebooting/shutting down, and accessing shells or logs for troubleshooting. Physical console access requires a keyboard/monitor or serial cable connection while SSH can be used remotely after set up.
wolfSSL and TLS 1.3



wolfSSL and TLS 1.3wolfSSL This document summarizes a talk given by Chris Conlon from wolfSSL on September 15, 2017 in Tokyo, Japan about TLS 1.3. It provides background on Chris Conlon and his role at wolfSSL, an overview of wolfSSL's products and services including their lightweight SSL/TLS library. It also discusses the history and components of the SSL/TLS protocol, common vulnerabilities, and the goals of the new TLS 1.3 specification.
Intrusion Detection And Prevention



Intrusion Detection And PreventionNicholas Davis The document discusses intrusion detection and prevention systems (IDS/IPS). It describes what an IDS is, the components of an IDS, and different types of IDS including network-based, host-based, and hybrid systems. It also covers the differences between passive and reactive IDS, as well as techniques attackers use to evade detection like fragmentation and small packets. The document concludes by discussing intrusion prevention systems and how they differ from IDS in their ability to block threats in real-time.
Secure shell



Secure shellArjun Aj SSH is a protocol for secure remote access and file transfer that replaces insecure protocols like telnet. It uses encryption and authentication to securely transmit data, remote shell access, port forwarding, and file transfers between a client and server. Reasons to use SSH include enabling secure communication channels, arbitrary port redirection, optional compression, and protecting against spoofing and routing attacks.
4. CNCF kubernetes Comparison of-existing-cni-plugins-for-kubernetes



4. CNCF kubernetes Comparison of-existing-cni-plugins-for-kubernetesJuraj Hantak This document compares existing CNI plugins for Kubernetes and provides descriptions of popular plugins like Flannel, Calico, Kube-router, and AWS VPC CNI. It explains that CNI plugins provide the interface between container runtimes and network implementations, and describes the CNI workflow and requirements for pod networking in Kubernetes.
10. th cncf meetup - Routing microservice-architectures-with-traefik-cncfsk



10. th cncf meetup - Routing microservice-architectures-with-traefik-cncfskJuraj Hantak Jakub Hajek gave a presentation on routing microservice architectures with Traefik. Traefik is a cloud native edge router that provides automatic discovery, integrates with major cluster technologies, and includes features like TLS termination, load balancing, and request routing. It can be used to implement canary deployments and traffic mirroring to gradually rollout new versions of services. Hajek demonstrated Traefik's capabilities through a demo environment using K3s and Kubernetes custom resource definitions.
Traefik as an open source edge router for microservice architectures



Traefik as an open source edge router for microservice architecturesJakub Hajek Traefik is an edge router that can be easily integrated with the common cluster management solutions. The presentation includes features provided in the recent major release of Traefik. The live demo includes presentation of canary deployment, mirroring which are built-in features. The cluster was running on a lightweight version of Kubernets called #k3s.
Ad
More Related Content
What's hot (20)
Firewall and NAT Fundamentals - pfSense Hangout January 2014



Firewall and NAT Fundamentals - pfSense Hangout January 2014Netgate The document summarizes updates from a January 2014 pfSense Hang Out. It discusses the launch of an online store for pfSense merchandise, a new website, and an updated pfSense book. An upcoming 2.1.1 release was outlined which will contain bug and security fixes. Development of the 2.2 release was also mentioned, including using FreeBSD 10.0 as the base and new features like improved wireless support and NAT ordering options. The hang out included tutorials on firewall and NAT fundamentals and basic network setups. Future tutorial topics and questions were solicited by email.
Wi fi protected access



Wi fi protected accessLopamudra Das This is the the technology which is very basic understanding on Wi- Fi technology..
What is Wi-Fi technology and how is working and also the advantages of wi-fi.....
Secret Management with Hashicorp’s Vault



Secret Management with Hashicorp’s VaultAWS Germany When running a Kubernetes Cluster in AWS there are secrets like AWS and Kubernetes credentials, access information for databases or integration with the company LDAP that need to be stored and managed.
HashiCorp’s Vault secures, stores, and controls access to tokens, passwords, certificates, API keys, and other secrets . It handles leasing, key revocation, key rolling, and auditing.
This talk will give an overview of secret management in general and Vault’s concepts. The talk will explain how to make use of Vault’s extensive feature set and show patterns that implement integration between Kubernetes applications and Vault.
How Secure are IPsec and SSL VPN encryptions



How Secure are IPsec and SSL VPN encryptionsUday Bhatia Virtual Private Networks (VPNs) provide security and privacy to private and public networks. There are different types of VPNs including site-to-site for connecting entire networks and remote VPNs for individual remote access. VPNs use encryption techniques like symmetric, asymmetric, and public key infrastructure to securely encrypt data during transmission. SSL/TLS uses public key encryption to establish secure links between servers and clients, while IPsec is a protocol suite that authenticates and encrypts individual IP packets to provide secure IP communications. Diffie-Hellman key exchange allows two parties to jointly establish a shared secret over an insecure channel.
Build and run embedded apps faster from qt creator with docker



Build and run embedded apps faster from qt creator with dockerQt This document discusses using Docker containers to build and run embedded Qt applications from QtCreator more efficiently. It proposes wrapping CMake calls in a Docker script to build apps in containers on the local workstation instead of virtual machines. The key steps are installing a Qt SDK in a container, configuring QtCreator kits to use the Docker wrapper script for builds, and setting up deployment to run the built apps on target devices via SSH. This allows reusing existing container builds on a powerful workstation for faster development compared to building each app version's SDK in a separate virtual machine.
Hacking the swisscom modem



Hacking the swisscom modemCyber Security Alliance The document discusses hacking the Swisscom modem by exploiting default credentials to gain access. Upon login, the author runs commands to investigate the system such as viewing configuration files and mapping the internal network. Various system details are discovered including the Linux kernel version and software components.
Building a scalable microservice architecture with envoy, kubernetes and istio



Building a scalable microservice architecture with envoy, kubernetes and istioSAMIR BEHARA Talk from O'Reilly Software Architecture Conference San Jose 2019
Microservices and containers have taken the software industry by storm. Transitioning from a monolith to microservices enables you to deploy your application more frequently, independently, and reliably. However, microservice architecture has its own challenges, and it has to deal with the same problems encountered while designing distributed systems.
Enter service mesh technology to the rescue. A service mesh reduces the complexity associated with microservices and provides functionality like load balancing, service discovery, traffic management, circuit breaking, telemetry, fault injection, and more. Istio is one of the best implementations of a service mesh at this point, while Kubernetes provides a platform for running microservices and automating deployment of containerized applications.
Join Samir Behara to go beyond the buzz and understand microservices and service mesh technologies.
Ip Spoofing



Ip SpoofingDhrumil Shah IP spoofing is when an attacker forges the source IP address in IP packets sent to a computer network to conceal their identity or impersonate another system. It is done by determining the IP address of a trusted system and modifying packet headers to appear to come from that system. Services vulnerable to IP spoofing include RPC, services using IP address authentication, the X Window System, and R services. Types of IP spoofing include blind spoofing, non-blind spoofing, denial of service attacks, and man-in-the-middle attacks. Countermeasures include packet filtering, filtering at routers, and disabling vulnerable commands.
Dell VLT reference architecture v2 0



Dell VLT reference architecture v2 0David Pasek This document explains the dual node VLT deployment strategies with its associated network reference architecture. Various VLT deployment topologies are also explained with emphasis on best practices and recommendations for some of the network scenarios. This document also covers the configuration and troubleshooting of VLT using relevant show commands and different outputs.
Board Support Package Fact Sheet | Manual Guide



Board Support Package Fact Sheet | Manual GuideEmbitel Technologies - A VOLKSWAGEN GROUP COMPANY Board Support Package contains Low level device driver and HAL layer. It is the essential to boot the system. By this virtue, BSP finds its application in almost every automotive ECU software.We offer our Board Support Package (BSP) on a one-time license fee model. This model makes our customers the owner of the entire BSP source code along with the solution IP rights.
VLAN and its implementation 



VLAN and its implementation Mohit Kumar CONTENT
1. Acknowledgement
2. Certificate
3. Certificate of Approval
4. Problem Definition-Defining the problem.
5. Introduction
6. Network and It‘s Types
7. Actual Topic- VLAN
8. VLAN Membership
9. VTP
10. Implementation
11. Conclusion
IS-IS Protocol Introduction



IS-IS Protocol IntroductionNetProtocol Xpert IS-IS is an interior gateway protocol that uses link-state routing and SPF algorithms to calculate the shortest path. It supports both CLNP and IP and has three routing levels - level 1 for intra-area routing, level 2 for inter-area routing, and level 1/2 routers that connect levels 1 and 2. There are three types of IS-IS routers: level 1 that exchange intra-area topology, level 2 that exchange inter-area topology, and level 1/2 that act as border routers between levels 1 and 2.
VoIP and data communication using cisco packet tracer



VoIP and data communication using cisco packet tracerFikri Paramadina From this simulation, we will know how to configure :
Routing and Switching, Vlan for data and telephony, Redistribute between different routing protocols, DHCP IP, and VoIP with the Dial Peer Communication.
LXC, Docker, security: is it safe to run applications in Linux Containers?



LXC, Docker, security: is it safe to run applications in Linux Containers?Jérôme Petazzoni The document discusses the security of running applications in Linux containers. It begins by acknowledging that containers were not originally designed with security in mind. However, it then outlines several techniques that can be used to improve security, such as running containers without root privileges, dropping capabilities, enabling security modules like SELinux, and limiting access to devices and system calls. For the most security-sensitive tasks, it recommends running containers inside virtual machines to isolate them further. In the end, it argues that with the right precautions, containers can be used securely for many applications.
Cisco router basic



Cisco router basicTapan Khilar Routing is the method by which network devices direct messages across networks to arrive at the correct destination. Routers use routing tables containing information about locally-connected networks and remote networks to determine the best path to send packets. The routing table includes details like the destination, mask, gateway, and cost for each route.
Console Menu - pfSense Hangout December 2016



Console Menu - pfSense Hangout December 2016Netgate This document provides instructions for accessing and using the console menu in pfSense. It begins by covering the requirements and setup for the different console access methods like keyboard/video, serial, and SSH. It then describes each of the tasks available in the console menu like assigning interfaces, resetting passwords/defaults, rebooting, and accessing diagnostic tools. Key tasks include interface configuration, resetting passwords, rebooting/shutting down, and accessing shells or logs for troubleshooting. Physical console access requires a keyboard/monitor or serial cable connection while SSH can be used remotely after set up.
wolfSSL and TLS 1.3



wolfSSL and TLS 1.3wolfSSL This document summarizes a talk given by Chris Conlon from wolfSSL on September 15, 2017 in Tokyo, Japan about TLS 1.3. It provides background on Chris Conlon and his role at wolfSSL, an overview of wolfSSL's products and services including their lightweight SSL/TLS library. It also discusses the history and components of the SSL/TLS protocol, common vulnerabilities, and the goals of the new TLS 1.3 specification.
Intrusion Detection And Prevention



Intrusion Detection And PreventionNicholas Davis The document discusses intrusion detection and prevention systems (IDS/IPS). It describes what an IDS is, the components of an IDS, and different types of IDS including network-based, host-based, and hybrid systems. It also covers the differences between passive and reactive IDS, as well as techniques attackers use to evade detection like fragmentation and small packets. The document concludes by discussing intrusion prevention systems and how they differ from IDS in their ability to block threats in real-time.
Secure shell



Secure shellArjun Aj SSH is a protocol for secure remote access and file transfer that replaces insecure protocols like telnet. It uses encryption and authentication to securely transmit data, remote shell access, port forwarding, and file transfers between a client and server. Reasons to use SSH include enabling secure communication channels, arbitrary port redirection, optional compression, and protecting against spoofing and routing attacks.
4. CNCF kubernetes Comparison of-existing-cni-plugins-for-kubernetes



4. CNCF kubernetes Comparison of-existing-cni-plugins-for-kubernetesJuraj Hantak This document compares existing CNI plugins for Kubernetes and provides descriptions of popular plugins like Flannel, Calico, Kube-router, and AWS VPC CNI. It explains that CNI plugins provide the interface between container runtimes and network implementations, and describes the CNI workflow and requirements for pod networking in Kubernetes.
Similar to Traefik 2.x features - canary deployment with Traefik and K3S (20)
10. th cncf meetup - Routing microservice-architectures-with-traefik-cncfsk



10. th cncf meetup - Routing microservice-architectures-with-traefik-cncfskJuraj Hantak Jakub Hajek gave a presentation on routing microservice architectures with Traefik. Traefik is a cloud native edge router that provides automatic discovery, integrates with major cluster technologies, and includes features like TLS termination, load balancing, and request routing. It can be used to implement canary deployments and traffic mirroring to gradually rollout new versions of services. Hajek demonstrated Traefik's capabilities through a demo environment using K3s and Kubernetes custom resource definitions.
Traefik as an open source edge router for microservice architectures



Traefik as an open source edge router for microservice architecturesJakub Hajek Traefik is an edge router that can be easily integrated with the common cluster management solutions. The presentation includes features provided in the recent major release of Traefik. The live demo includes presentation of canary deployment, mirroring which are built-in features. The cluster was running on a lightweight version of Kubernets called #k3s.
Container Orchestration with Traefik 2.x



Container Orchestration with Traefik 2.xJakub Hajek The presentation includes key features of Traefk - a modern reverse proxy and load balancer for micro services that easily integrates with many cluster technology such as Kubernetes and Docker Swarm.
Cloud-native .NET Microservices mit Kubernetes



Cloud-native .NET Microservices mit KubernetesQAware GmbH Mario-Leander Reimer presented on building cloud-native .NET microservices with Kubernetes. He discussed key principles of cloud native applications including designing for distribution, performance, automation, resiliency and elasticity. He also covered containerization with Docker, composing services with Kubernetes and common concepts like deployments, services and probes. Reimer provided examples of Dockerfiles, Kubernetes definitions and using tools like Steeltoe and docker-compose to develop cloud native applications.
JDO 2019: Container orchestration with Docker Swarm - Jakub Hajek



JDO 2019: Container orchestration with Docker Swarm - Jakub HajekPROIDEA This document discusses Docker Swarm and container orchestration. It provides an overview of key Docker Swarm features such as decentralized design, declarative service model, rolling updates, secrets, and configs. It then describes a demonstration environment running on AWS with Docker Swarm, NodeJS, Consul, Traefik, and Let's Encrypt. Diagrams are shown of the overlay networks, architecture, and stacks. The demonstration shows the cluster topology, service scaling, and response time testing. Contact information is provided to learn more about Docker Swarm, container orchestration, and the demonstration environment.
Full stack development best practice and toolset



Full stack development best practice and toolsetReid Lai The document discusses full stack development best practices and toolsets. It defines a full stack developer as someone proficient in both front-end and back-end development. It also discusses how full stack developers fit into scrum teams, the relationship between agile development and DevOps practices like continuous integration, delivery and deployment. Finally, it covers using containers and Docker for DevOps and orchestrating required application services.
Cloud-native .NET-Microservices mit Kubernetes @BASTAcon



Cloud-native .NET-Microservices mit Kubernetes @BASTAconMario-Leander Reimer Cloud-Größen wie Google, Twitter und Netflix haben die Kernbausteine ihrer Infrastruktur quelloffen verfügbar gemacht. Das Resultat aus vielen Jahren Cloud-Erfahrung ist nun frei zugänglich, und jeder kann seine eigenen Cloud-nativen Anwendungen entwickeln – Anwendungen, die in der Cloud zuverlässig laufen und fast beliebig skalieren. Die einzelnen Bausteine wachsen zu einem großen Ganzen zusammen, dem Cloud-Native-Stack. In dieser Session stellen wir die wichtigsten Konzepte und aktuellen Schlüsseltechnologien kurz vor. Anschließend implementieren wir einen einfachen Microservice mit .NET Core und Steeltoe OSS und bringen ihn zusammen mit ausgewählten Bausteinen für Service-Discovery und Konfiguration schrittweise auf einem Kubernetes-Cluster zum Laufen. @BASTAcon #BASTA17 @qaware #CloudNativeNerd
https://basta.net/microservices-services/cloud-native-net-microservices-mit-kubernetes/
Connect Everything with NATS - Cloud Expo Europe



Connect Everything with NATS - Cloud Expo Europewallyqs NATS is a high performance publish/subscribe messaging system that has as one of its main goals connecting services in the simplest, most secure and reliable way possible.
The project has a long history of being part of production deployments as the core component for the internal communication of a distributed system, and in its latest release NATS v2.0, its feature set was enhanced so that it can also be used to create a global and decentralized communication network.
Docker Networking - Common Issues and Troubleshooting Techniques



Docker Networking - Common Issues and Troubleshooting TechniquesSreenivas Makam This document discusses Docker networking components and common issues. It covers Docker networking drivers like bridge, host, overlay, topics around Docker daemon access and configuration behind firewalls. It also discusses container networking best practices like using user-defined networks instead of links, connecting containers to multiple networks, and connecting managed services to unmanaged containers. The document is intended to help troubleshoot Docker networking issues.
Kubernetes Navigation Stories – DevOpsStage 2019, Kyiv



Kubernetes Navigation Stories – DevOpsStage 2019, KyivAleksey Asiutin thredUP team shares key learnings from after-migration processes. We tell you about what technologies and solutions worked best for us and where we spent time troubleshooting and improving. In particular we have focused on development and staging experience, user authentication, cloud-native CI pipelines, applications telemetry and service mesh. We also share our experience with Kubernetes security hardening, autoscaling and tell you about a new service creation within our infrastructure.
What's New in Docker - February 2017



What's New in Docker - February 2017Patrick Chanezon This document provides an overview of Container as a Service (CaaS) with Docker. It discusses key concepts like Docker containers, images, and orchestration tools. It also covers DevOps practices like continuous delivery that are enabled by Docker. Specific topics covered include Docker networking, volumes, and orchestration with Docker Swarm and compose files. Examples are provided of building and deploying Java applications with Docker, including Spring Boot apps, Java EE apps, and using Docker for builds. Security features of Docker like content trust and scanning are summarized. The document concludes by discussing Docker use cases across different industries and how Docker enables critical transformations around cloud, DevOps, and application modernization.
Containerising bootiful microservices javaeeconf



Containerising bootiful microservices javaeeconfIvan Vasyliev https://jeeconf.com/program/containerising-bootiful-microservices/
Presentation on how we implemented Kubernetes and Jenkins to deploy and keep running Spring Cloud Netflix based microservices in private cloud.
Overview of decision made about technology stack, testing strategy, tools and infrastructure components, continuous delivery/deployment pipelines and some implementation details and issues met.
Kubered -Recipes for C2 Operations on Kubernetes



Kubered -Recipes for C2 Operations on KubernetesJeffrey Holden This document provides recipes for containerizing and deploying common C2 frameworks like Cobalt Strike and Merlin on Kubernetes. It discusses using Docker to containerize the C2 payloads, creating Kubernetes deployments, services, and ingress resources to expose the containers. It also covers using Nginx Ingress and Istio service mesh with Envoy sidecars to provide redirection and traffic manipulation capabilities for C2 infrastructure on Kubernetes.
21st Docker Switzerland Meetup - ISTIO



21st Docker Switzerland Meetup - ISTIONiklaus Hirt The document discusses Istio, an open source service mesh that provides traffic management, resilience, and security for microservices applications. It begins with an overview of microservices and common challenges in managing microservices applications. It then introduces Istio and its components that address these challenges, such as intelligent routing, policy enforcement, and telemetry collection. Specific Istio features like traffic control, splitting, and mirroring are demonstrated. Finally, it provides instructions for getting started with Istio and links for additional information.
Docker meetup - PaaS interoperability



Docker meetup - PaaS interoperabilityLudovic Piot This is an overview of how we have to consider interoperability between several PaaS services and how standards like CAMP or TOSCA can help.
A hitchhiker‘s guide to the cloud native stack



A hitchhiker‘s guide to the cloud native stackQAware GmbH Container Days 2017, Hamburg: Vortrag von Mario-Leander Reimer (@LeanderReimer, Cheftechnologe bei QAware).
Abstract: Cloud-Größen wie Google, Twitter und Netflix haben die Kernbausteine ihrer Infrastruktur quelloffen verfügbar gemacht. Das Resultat aus vielen Jahren Cloud-Erfahrung ist nun frei zugänglich, und jeder kann seine eigenen Cloud-nativen Anwendungen entwickeln – Anwendungen, die in der Cloud zuverlässig laufen und fast beliebig skalieren. Die einzelnen Bausteine wachsen zu einem großen Ganzen zusammen, dem Cloud Native Stack.
In dieser Session stellen wir die wichtigsten Konzepte und Schlüsseltechnologien vor und bringen dann eine Spring-Cloud-basierte Beispielanwendung schrittweise auf Kubernetes und DC/OS zum Laufen. Dabei diskutieren wir verschiedene praktikable Architekturalternativen.
A Hitchhiker’s Guide to the Cloud Native Stack. #CDS17



A Hitchhiker’s Guide to the Cloud Native Stack. #CDS17Mario-Leander Reimer This document provides an overview of cloud native applications and the cloud native stack. It discusses key concepts like microservices, containerization, composition using Docker and Docker Compose, and orchestration using Kubernetes. It provides examples of building a simple microservices application with these technologies and deploying it on Kubernetes. Overall it serves as a guide to developing and deploying cloud native applications.
Docker Azure Friday OSS March 2017 - Developing and deploying Java & Linux on...



Docker Azure Friday OSS March 2017 - Developing and deploying Java & Linux on...Patrick Chanezon This document provides an overview of developing and deploying Java applications on Azure using Docker. It discusses using Docker to build Java applications, running containers, and deploying stacks. It also covers Docker Enterprise Edition, including subscriptions, certifications, and security features. Finally, it demonstrates using Docker on Azure, such as with Azure Container Service, and shows examples of building, running, and deploying Java applications with Docker.
Chicago Docker Meetup Presentation - Mediafly



Chicago Docker Meetup Presentation - MediaflyMediafly This document discusses how Bryan Murphy uses Docker at his company Mediafly. It begins by introducing Bryan and his background. It then describes what Mediafly does, including content management systems, secure content delivery, document and video processing, and customizable user interfaces. The document highlights aspects of Mediafly that make it interesting, such as being multi-device, multi-tenant, service oriented, and distributed. It provides examples of technologies used at Mediafly and some key metrics. The document then discusses why Docker is used at Mediafly, covering benefits like being developer friendly, enabling faster iteration and testing, managing dependencies, sharing environments, standardization, isolation, and infrastructure freedom.
Natively clouded Journey



Natively clouded JourneyHaggai Philip Zagury Almost 3 years with Kubernetes and some "war stories", we will take the top-down approach to kubernetes and take a glimpse of the bottom-up and where we could customize it.
Ad
More from Jakub Hajek (6)
Docker Logging and analysing with Elastic Stack



Docker Logging and analysing with Elastic StackJakub Hajek Collecting logs from the entire stateless environment is challenging parts of the application lifecycle. Correlating business logs with operating system metrics to provide insights is a crucial part of the entire organization. What aspects should be considered while you design your logging solutions?
Docker Swarm and Traefik 2.0



Docker Swarm and Traefik 2.0Jakub Hajek This presentation has been given during DevOps Congress in Wrocław. It is about container orchestrations with Docker Swarm and Traefik. It includes the configuration examples of Traefik version 2.0.
The source code used in the presentation: https://github.com/jakubhajek/traefik-swarm
Container Orchestration with Traefk on Docker Swarm



Container Orchestration with Traefk on Docker SwarmJakub Hajek The presentation contains details of how to set up a fully-fledged environment based on Docker Swarm and Traefk. You will see a multi-tier application stack consisting of Edge router running in the first layer, then the frontend application and NodeJS backend. This is a quite common setup used in a microservices architecture. If you are building a high available environment without a single point of failure, it can be interesting for you.
The source code used in the presentation: https://github.com/jakubhajek/traefik-consul-swarm
Cometari Dedicated Solutions Company Presentation



Cometari Dedicated Solutions Company PresentationJakub Hajek We are a team of talented and ambitious software engineers, data scientists, graphic and UX designers. We have knowledge and competence in designing, developing and maintaining complex information systems. Our engineers have many years of experience in the area which enables us to meet our clients’ most demanding requirements and adopt an individual approach to every issue we deal with.
Cometari Dedicated Solutions Oferta ogólna



Cometari Dedicated Solutions Oferta ogólnaJakub Hajek Cometari Dedicated Solutions jest firmą technologiczną zlokalizowaną w Krakowie. Posiadamy wiedzę i kompetencje w zakresie projektowania, produkcji i utrzymania
złożonych systemów informatycznych. Nasi inżynierowie posiadają wieloletnie doświadczenie branżowe dzięki czemu do każdego tematu podchodzimy indywidualnie. Kładziemy nacisk na szybkość komunikacji z klientem oraz jakość wytwarzanych rozwiązań. Specjalizujemy się w produkcji zaawansowanych systemów serwerowych jak również lekkich rozwiązań webowych oraz mobilnych. Jeśli potrzebujesz rzetelnego partnera technologicznego jesteśmy do dyspozycji.
Cometari Dedicated Solutions General Offer



Cometari Dedicated Solutions General OfferJakub Hajek Cometari Dedicated Solutions is a technology company based in Cracow, Poland.
We have knowledge and competence in designing, developing and maintaining complex information systems. We specialise in developing advanced server systems as well as soft web and mobile solutions. If you are looking for a reliable IT partner, Cometari Dedicated Solutions
is the right choice. Website: www.cometari.com
Ad
Recently uploaded (20)
2025-05-Q4-2024-Investor-Presentation.pptx



2025-05-Q4-2024-Investor-Presentation.pptxSamuele Fogagnolo Cloudflare Q4 Financial Results Presentation
Designing Low-Latency Systems with Rust and ScyllaDB: An Architectural Deep Dive



Designing Low-Latency Systems with Rust and ScyllaDB: An Architectural Deep DiveScyllaDB Want to learn practical tips for designing systems that can scale efficiently without compromising speed?
Join us for a workshop where we’ll address these challenges head-on and explore how to architect low-latency systems using Rust. During this free interactive workshop oriented for developers, engineers, and architects, we’ll cover how Rust’s unique language features and the Tokio async runtime enable high-performance application development.
As you explore key principles of designing low-latency systems with Rust, you will learn how to:
- Create and compile a real-world app with Rust
- Connect the application to ScyllaDB (NoSQL data store)
- Negotiate tradeoffs related to data modeling and querying
- Manage and monitor the database for consistently low latencies
Massive Power Outage Hits Spain, Portugal, and France: Causes, Impact, and On...



Massive Power Outage Hits Spain, Portugal, and France: Causes, Impact, and On...Aqusag Technologies In late April 2025, a significant portion of Europe, particularly Spain, Portugal, and parts of southern France, experienced widespread, rolling power outages that continue to affect millions of residents, businesses, and infrastructure systems.
Into The Box Conference Keynote Day 1 (ITB2025)



Into The Box Conference Keynote Day 1 (ITB2025)Ortus Solutions, Corp This is the keynote of the Into the Box conference, highlighting the release of the BoxLang JVM language, its key enhancements, and its vision for the future.
Generative Artificial Intelligence (GenAI) in Business



Generative Artificial Intelligence (GenAI) in BusinessDr. Tathagat Varma My talk for the Indian School of Business (ISB) Emerging Leaders Program Cohort 9. In this talk, I discussed key issues around adoption of GenAI in business - benefits, opportunities and limitations. I also discussed how my research on Theory of Cognitive Chasms helps address some of these issues
Transcript: #StandardsGoals for 2025: Standards & certification roundup - Tec...



Transcript: #StandardsGoals for 2025: Standards & certification roundup - Tec...BookNet Canada Book industry standards are evolving rapidly. In the first part of this session, we’ll share an overview of key developments from 2024 and the early months of 2025. Then, BookNet’s resident standards expert, Tom Richardson, and CEO, Lauren Stewart, have a forward-looking conversation about what’s next.
Link to recording, presentation slides, and accompanying resource: https://bnctechforum.ca/sessions/standardsgoals-for-2025-standards-certification-roundup/
Presented by BookNet Canada on May 6, 2025 with support from the Department of Canadian Heritage.
AI and Data Privacy in 2025: Global Trends



AI and Data Privacy in 2025: Global TrendsInData Labs In this infographic, we explore how businesses can implement effective governance frameworks to address AI data privacy. Understanding it is crucial for developing effective strategies that ensure compliance, safeguard customer trust, and leverage AI responsibly. Equip yourself with insights that can drive informed decision-making and position your organization for success in the future of data privacy.
This infographic contains:
-AI and data privacy: Key findings
-Statistics on AI data privacy in the today’s world
-Tips on how to overcome data privacy challenges
-Benefits of AI data security investments.
Keep up-to-date on how AI is reshaping privacy standards and what this entails for both individuals and organizations.
Role of Data Annotation Services in AI-Powered Manufacturing



Role of Data Annotation Services in AI-Powered ManufacturingAndrew Leo From predictive maintenance to robotic automation, AI is driving the future of manufacturing. But without high-quality annotated data, even the smartest models fall short.
Discover how data annotation services are powering accuracy, safety, and efficiency in AI-driven manufacturing systems.
Precision in data labeling = Precision on the production floor.
HCL Nomad Web – Best Practices und Verwaltung von Multiuser-Umgebungen



HCL Nomad Web – Best Practices und Verwaltung von Multiuser-Umgebungenpanagenda Webinar Recording: https://www.panagenda.com/webinars/hcl-nomad-web-best-practices-und-verwaltung-von-multiuser-umgebungen/
HCL Nomad Web wird als die nächste Generation des HCL Notes-Clients gefeiert und bietet zahlreiche Vorteile, wie die Beseitigung des Bedarfs an Paketierung, Verteilung und Installation. Nomad Web-Client-Updates werden “automatisch” im Hintergrund installiert, was den administrativen Aufwand im Vergleich zu traditionellen HCL Notes-Clients erheblich reduziert. Allerdings stellt die Fehlerbehebung in Nomad Web im Vergleich zum Notes-Client einzigartige Herausforderungen dar.
Begleiten Sie Christoph und Marc, während sie demonstrieren, wie der Fehlerbehebungsprozess in HCL Nomad Web vereinfacht werden kann, um eine reibungslose und effiziente Benutzererfahrung zu gewährleisten.
In diesem Webinar werden wir effektive Strategien zur Diagnose und Lösung häufiger Probleme in HCL Nomad Web untersuchen, einschließlich
- Zugriff auf die Konsole
- Auffinden und Interpretieren von Protokolldateien
- Zugriff auf den Datenordner im Cache des Browsers (unter Verwendung von OPFS)
- Verständnis der Unterschiede zwischen Einzel- und Mehrbenutzerszenarien
- Nutzung der Client Clocking-Funktion
TrsLabs - Fintech Product & Business Consulting



TrsLabs - Fintech Product & Business ConsultingTrs Labs Hybrid Growth Mandate Model with TrsLabs
Strategic Investments, Inorganic Growth, Business Model Pivoting are critical activities that business don't do/change everyday. In cases like this, it may benefit your business to choose a temporary external consultant.
An unbiased plan driven by clearcut deliverables, market dynamics and without the influence of your internal office equations empower business leaders to make right choices.
Getting things done within a budget within a timeframe is key to Growing Business - No matter whether you are a start-up or a big company
Talk to us & Unlock the competitive advantage
What is Model Context Protocol(MCP) - The new technology for communication bw...



What is Model Context Protocol(MCP) - The new technology for communication bw...Vishnu Singh Chundawat The MCP (Model Context Protocol) is a framework designed to manage context and interaction within complex systems. This SlideShare presentation will provide a detailed overview of the MCP Model, its applications, and how it plays a crucial role in improving communication and decision-making in distributed systems. We will explore the key concepts behind the protocol, including the importance of context, data management, and how this model enhances system adaptability and responsiveness. Ideal for software developers, system architects, and IT professionals, this presentation will offer valuable insights into how the MCP Model can streamline workflows, improve efficiency, and create more intuitive systems for a wide range of use cases.
Special Meetup Edition - TDX Bengaluru Meetup #52.pptx



Special Meetup Edition - TDX Bengaluru Meetup #52.pptxshyamraj55 We’re bringing the TDX energy to our community with 2 power-packed sessions:
🛠️ Workshop: MuleSoft for Agentforce
Explore the new version of our hands-on workshop featuring the latest Topic Center and API Catalog updates.
📄 Talk: Power Up Document Processing
Dive into smart automation with MuleSoft IDP, NLP, and Einstein AI for intelligent document workflows.
Technology Trends in 2025: AI and Big Data Analytics



Technology Trends in 2025: AI and Big Data AnalyticsInData Labs At InData Labs, we have been keeping an ear to the ground, looking out for AI-enabled digital transformation trends coming our way in 2025. Our report will provide a look into the technology landscape of the future, including:
-Artificial Intelligence Market Overview
-Strategies for AI Adoption in 2025
-Anticipated drivers of AI adoption and transformative technologies
-Benefits of AI and Big data for your business
-Tips on how to prepare your business for innovation
-AI and data privacy: Strategies for securing data privacy in AI models, etc.
Download your free copy nowand implement the key findings to improve your business.
IEDM 2024 Tutorial2_Advances in CMOS Technologies and Future Directions for C...



IEDM 2024 Tutorial2_Advances in CMOS Technologies and Future Directions for C...organizerofv IEDM 2024 Tutorial2
Cyber Awareness overview for 2025 month of security



Cyber Awareness overview for 2025 month of securityriccardosl1 Cyber awareness training educates employees on risk associated with internet and malicious emails
Heap, Types of Heap, Insertion and Deletion



Heap, Types of Heap, Insertion and DeletionJaydeep Kale This pdf will explain what is heap, its type, insertion and deletion in heap and Heap sort
UiPath Community Berlin: Orchestrator API, Swagger, and Test Manager API



UiPath Community Berlin: Orchestrator API, Swagger, and Test Manager APIUiPathCommunity Join this UiPath Community Berlin meetup to explore the Orchestrator API, Swagger interface, and the Test Manager API. Learn how to leverage these tools to streamline automation, enhance testing, and integrate more efficiently with UiPath. Perfect for developers, testers, and automation enthusiasts!
📕 Agenda
Welcome & Introductions
Orchestrator API Overview
Exploring the Swagger Interface
Test Manager API Highlights
Streamlining Automation & Testing with APIs (Demo)
Q&A and Open Discussion
Perfect for developers, testers, and automation enthusiasts!
👉 Join our UiPath Community Berlin chapter: https://community.uipath.com/berlin/
This session streamed live on April 29, 2025, 18:00 CET.
Check out all our upcoming UiPath Community sessions at https://community.uipath.com/events/.
Quantum Computing Quick Research Guide by Arthur Morgan



Quantum Computing Quick Research Guide by Arthur MorganArthur Morgan This is a Quick Research Guide (QRG).
QRGs include the following:
- A brief, high-level overview of the QRG topic.
- A milestone timeline for the QRG topic.
- Links to various free online resource materials to provide a deeper dive into the QRG topic.
- Conclusion and a recommendation for at least two books available in the SJPL system on the QRG topic.
QRGs planned for the series:
- Artificial Intelligence QRG
- Quantum Computing QRG
- Big Data Analytics QRG
- Spacecraft Guidance, Navigation & Control QRG (coming 2026)
- UK Home Computing & The Birth of ARM QRG (coming 2027)
Any questions or comments?
- Please contact Arthur Morgan at [email protected].
100% human made.
What is Model Context Protocol(MCP) - The new technology for communication bw...



What is Model Context Protocol(MCP) - The new technology for communication bw...Vishnu Singh Chundawat
Traefik 2.x features - canary deployment with Traefik and K3S
- 1. TRAEFIK 2.X JAKUB HAJEK MAY, 7TH, 2020 WHAT HAS CANARY DEPLOYMENT GOT TO DO WITH SCRAMBLED EGGS?
- 2. ▸ I am the owner and technical consultant (SRE) ▸ I work for Cometari ▸ I’ve been system admin since 1998 ▸ Cometari is a solutions company implementing DevOps culture and providing consultancy, workshops and software services. ▸ Our expertise are DevOps, Elastic Stack log analysis INTRODUCTION - JAKUB HAJEK
- 3. ▸ SRE & Co - founder 56k.cloud ▸ Background containers, Cloud & engineering ▸ Cloud Architect for large deployments ▸ Passionate about DevOps & Monitoring and of course Mountain Biking ▸ Host of TheByte.io Podcast ▸ Docker Captain ▸ Traefik Ambassador INTRODUCTION - BRIAN CHRISTNER
- 4. ▸ Cloud Development Manager @Done ▸ Software Section Lead, writer and speaker @msHOWTO ▸ An active member of Cloud Family ▸ Passionate about Software Development, Cloud and DevOps ▸ Mountain Biking ▸ Traefik Ambassador INTRODUCTION - MERT YETER
- 5. The aim of this meetup is to present what the key features delivered with Traefik 2.x are
- 6. TRAEFIK
- 7. ENTRYPOINT ROUTER SERVICE MIDDLEWARE 1 MIDDLEWARE 2 MIDDLEWARE 3 Request Calls to backend servers WHAT IS IT TRAEFIK?
- 8. TRAEFIK 2.X KEY FEATURES ▸ ROUTER= frontend, SERVICE=backend, MIDDLEWARE=rules ▸ TCP / UDP / GRPC support ▸ Kubernetes CRD ▸ Fully customisable routes via middleware, which can be reused on many routers ▸ YAML, TOML is still good ▸ A new dashboard with web UI ▸ Canary deployment with Service Load balancer ▸ Network traffic Mirroring with Service Load balancer ▸ Session Stickiness ▸ Consul catalog
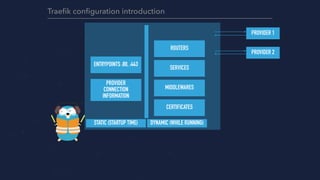
- 9. ENTRYPOINTS :80, :443 ROUTERS PROVIDER 1 Traefik configuration introduction PROVIDER CONNECTION INFORMATION SERVICES MIDDLEWARES CERTIFICATES PROVIDER 2 DYNAMIC (WHILE RUNNING)STATIC (STARTUP TIME)
- 10. KUBERNETES CRD
- 11. KUBERNETES CRD AND AVAILABLE CUSTOM RESOURCES ▸ Ingressroute - HTTP routing - http router ▸ Middleware - tweaks the HTTP before they are sent to a service - HTTP Middleware ▸ TraefikService - abstraction for HTTP LB/mirroring ▸ IngressRouteTCP - TCP routing - TCP router ▸ TLSOptions - TLS connection parameters https://docs.traefik.io/routing/providers/kubernetes-crd/
- 12. CANARY DEPLOYMENT AND TRAFFIC MIRRORING
- 14. CANARY DEPLOYMENT ▸ Deployment vs Release ▸ Instead of switching to new version in one step, we use a phased approach ▸ We deploy a new app in a small part of the production infrastructure ▸ Only a few users (1%) are routed to the newest version (Release) ▸ With no errors reported, the new version can be released to the rest of the infrastructure.
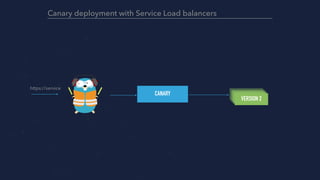
- 15. CANARY VERSION 2 VERSION 1 https://service Canary deployment with Service Load balancers 1% of live traffic, a few users Majority of users https://github.com/containous/traefik/issues/1164
- 16. CANARY VERSION 2 https://service Canary deployment with Service Load balancers VERSION 2VERSION 2VERSION 2
- 17. MIRRORING OR LIVE TRAFFIC SHADOW ▸ Understand difference between Deployment vs Release ▸ Deployment brings new code to the production, no production traffic yet! ▸ Run smoke, integration tests to make sure that new deployment has no impact to your users ▸ Release brings live traffic to a deployment. ▸ We can shadow live traffic to the new deployment and reduce the risk of failure.
- 18. MIRRORING VERSION 2 VERSION 1 https://service Mirroring with Service Load Balancer 20% https://github.com/containous/traefik/issues/2989
- 19. DEMO ENVIRONMENT
- 20. DEMO ENVIRONMENT IN DETAILS ▸ K3S cluster consisting of 3 nodes ▸ SSL certs issued by Lets Encrypt ▸ FQDN domains: ▸ https://a.labs.cometari.eu ▸ https://c.labs.cometari.eu ▸ DNS Round Robin: Route 53 with its implemented health checks
- 21. K3S CLUSTER IN 2 COMMANDS ▸ MASTER: ▸ curl -sfL https://get.k3s.io | INSTALL_K3S_EXEC="server --no-deploy traefik -- node-name node1" sh - ▸ WORKERS: ▸ curl -sfL https://get.k3s.io | K3S_URL=https://master- node.com:6443 K3S_TOKEN=SECRET_TOKEN INSTALL_K3S_EXEC=“agent --node-name node2" sh -
- 22. Talk is cheap, show me the code!
- 23. DEMO TIME
- 24. DEMO SCENARIOS ▸ Web UI to see how services are deployed ▸ Example of Canary deployment ▸ Example of Mirroring configuration
- 25. A FEW BENEFITS OF CANARY DEPLOYMENT ▸ Traefik provides flexible way to proceed with canary (K8S, K3S, Swarm) ▸ Reduce time to market ▸ Canary deployment allows you validate your application in real production environment ▸ Rolling out releases ▸ No need to maintain a lot of staging / testing environments
- 26. SOURCE CODE OF CONFIGURATION FILES ▸ https://github.com/jakubhajek/traefik-kubernetescrd
- 28. “I strongly believe that implementing DevOps culture, across the entire organisation, should provide measurable value and solve the real issue rather than generate a new one.” Jakub Hajek, Cometari



