Ad
Tutorial 06 - Real-Time Communication on the Internet
- 1. Real-Time Communication on the Internet Communicating in Real-Time and Exploring Wireless Networks Tutorial 6
- 2. Objectives Learn different ways to chat on the Internet. Explore different chat client programs. Find chat rooms devoted to specific topics. Explore businesses that let you create your own chat rooms. Learn about and explore virtual communities and their use in business.
- 3. Objectives Explore the history of the wireless Internet. Learn about different wireless networks. Locate wireless devices that let you access the Internet. Evaluate wireless carriers in the United States. Learn about wireless broadband networks.
- 4. What Is Chat? Chat : a general term for real-time communication that occurs over the Internet. Originally, the term chat described the act of users exchanging typed messages, or a text chat . Voice Chat: where participants speak to each other in real time, much like they would be using a telephone. Video Chat: where participants can see and speak to each other.
- 5. What Is Chat? Private Chat: occurs between individuals who know each other and are invited to participate in the chat. Public Chat: occurs in a public area, sometimes called a chat room , in which people come and go. Chats can be continuous, with participants entering and leaving ongoing discussions or they can be planned for a specific time and to last for a specific duration.
- 6. What Is Chat? Most chat tools allow users to save a transcript of the chat session for future reference. The practice of reading messages and not contributing to the discussion is called lurking . Chatting requires participants to type quickly, therefore, chat participants often omit capitalization and do not worry about proper spelling and grammar.
- 7. Commonly Used Chat Acronyms
- 8. What Is Chat? Flaming: when a participant insults or ridicules another participant. Spamming: when someone or an organization sends unsolicited and irrelevant messages to a chat room. Although many chat rooms don’t enforce the rules of netiquette, as you use the Internet to communicate, you should exercise common courtesy and respect as you would when speaking in person with other people.
- 9. Internet Relay Chat Early UNIX computers included a program called Talk that allowed users to exchange short text messages. In 1988, Jarkko Oikarinen wrote a communications program that extended the capabilities of the Talk program to multi-user. It was called Internet Relay Chat ( IRC ). IRC uses a client-server network model: IRC servers are connected through the internet to form an IRC network. Individual chat participants use IRC clients that connect to the servers in the network.
- 10. Internet Relay Chat The original network was EFNet , which is still one of the largest IRC networks today. Other major IRC networks include IRCNet, Undernet, DALnet, and NewNet. Servers in each of these IRC networks are connected to each other as part of the Internet, but IRC traffic is segregated by network.
- 11. Independent IRC Networks on the Internet New Perspectives on The Internet, Sixth Edition—Comprehensive Tutorial 6
- 12. Internet Relay Chat IRC networks organize their chats by topic. Each topic area is called a channel , and participants who connect to an IRC network join specific channels in which they conduct their chats. Each channel has a name, or a channel heading , that uses the pound sign (#) to indicate the chat’s topic. When a participant creates a new channel, he becomes responsible for managing the channel and is called the channel operator , channel op , or IRCop .
- 13. Internet Relay Chat The channel operator can change the channel’s topic and heading at any time, determines which users may participate in the channel, and can change whether the channel is public or private. Participants select nicknames when they log on to an IRC server. Nicknames must be unique. A channel operator’s nickname is preceded by @. IRC servers run automated programs, called IRC robots or bots, which perform routine services on the IRC network.
- 14. Commonly Used IRC Commands
- 15. Chat in Progress Using ICQ New Perspectives on The Internet, Sixth Edition—Comprehensive Tutorial 6
- 16. Instant Messaging Software Instant messaging software lets two users chat in real time over the Internet. Instant messages usually occur between people who know each other, and are especially popular with friends and families separated by geographic distances. The software has built-in tools that let you identify your friends and alert you when your friends are online.
- 17. Instant Messaging Software Instant messaging is different from e-mail in two important ways: When you send an e-mail message to a user, you do not have a way to determine if that user is online at the time you send your message. When you send an instant message, the instant messaging software identifies whether the intended recipient is online before you send the message.
- 18. Instant Messaging Software ICQ Pronounced “I seek you” One of the most popular instant messaging software programs Created by Mirabilis, an Israeli company in 1996 AOL purchased the software in 1998 and offers it as freeware AIM ( AOL Instant Messenger ) Available to anyone, even those without an AOL account. MSN Messenger / Windows Messenger Yahoo! Messenger
- 19. Instant Messaging Software You must use the same instant messaging software to chat with other users. Some instant messaging software programs have options for logging on to your chat account using a Web page so you can use the software when you are away from your primary computer. All instant messaging software programs have some features that work on wireless devices, such as cell phones. All instant messaging software is free and requires an Internet connection, preferably a broadband connection.
- 20. Instant Messaging Software New Perspectives on The Internet, Sixth Edition—Comprehensive Tutorial 6 Windows Messenger
- 21. Instant Messaging Software New Perspectives on The Internet, Sixth Edition—Comprehensive Tutorial 6 Home page of Cerulean Studios, which produces Trillian instant message software. Trillian allows you to chat with people using different IM software.
- 22. Web-Based Chat Sites Web-based chat sites offer the same features as text-based IRC chat networks and instant messaging but are often easier to use and do not require users to download and install any software. In Web-based chat , some users lurk and others have multiple conversations going at the same time. The chat room identifies users as they speak with their user names. Conversations are often open-ended and rarely follow the prescribed topic.
- 23. Web-Based Chat Sites Most Web-based chat sites prohibit spam messages, the use of automated programs, profane and vulgar language, and threats to individuals. Most sites require you to register before using their chat rooms. Although Web sites that provide chat rooms have rules of appropriate conduct, you might encounter conversations taking place that are offensive to you.
- 24. Web-Based Chat Sites New Perspectives on The Internet, Sixth Edition—Comprehensive Tutorial 6
- 25. Finding Web Chat Sites Use a directory that provides an organized list of chat site hyperlinks. The descriptions for each hyperlink might tell you more about the nature of the chat to which it leads. Use a Web search engine and include the word “chat” in the search expression.
- 26. Creating a Chat Room Use the features at a portal site such as Yahoo! Chat to create your own chat room. Easy, inexpensive, and usually includes tools that let you give access to only those people you want to participate in the chat that you create. Several businesses offer services that support the different situations in which an organization might need to conduct a private, moderated chat.
- 27. Sharing Information in Virtual Communities Virtual community : a place on the Internet where people can gather to discuss issues and share information. Types of virtual communities: online social networks online business networks online political networks
- 28. Online Social Networks Virtual communities that exist for the sole purpose of being a community. Useful tools for persons who want to make new local friends, establish acquaintances before moving to a new location, or obtain advice of various kinds. Rely on advertising to generate revenue. Some of the sites charge, or plan in the near future to charge, a monthly membership fee. Other sites plan to charge for specific site features.
- 29. Online Business Networks Focus on business networking. Users log on to seek jobs, find potential business partners, recruit workers, and engage in other business development activities. Users are looking for specific solutions to their problems. Online business networks tend to use categories that reflect specific interests and try to make it easy for business persons to find exactly the connections they need, quickly and efficiently.
- 30. Online Political Networks Used in the 2004 U.S. elections to rally supporters, raise funds, and get their messages out to voters. Provide a place for people interested in a candidate or an issue to communicate with each other. These sites allow people to discuss issues, plan strategies, and arrange in-person meetings called meetups .
- 31. Evolution of Wireless Networks When you connect to your Internet service provider, you’re creating a wired connection . A wireless connection occurs when data, such as a person’s voice, is transferred to another location without the use of any wires. In 1994, carriers created digital networks, or Personal Communication Service (PCS ), where data was carried in bits at a rate of up to 14.4 Kbps.
- 32. Evolution of Wireless Networks The year 1999 saw the introduction of the first “wireless” connections to the Internet. Personal digital assistant (PDA): a handheld computer that can send and receive wireless telephone and fax calls, act as a personal organizer, perform calculations, store notes, and download Web pages formatted for handheld devices. The wireless Internet has expanded to include different hardware devices, networks, and other options.
- 33. Evolution of Wireless Networks Cell phones were one of the first wireless connections to transfer a person’s voice. Text messaging occurs over second-generation wireless systems , or 2G wireless . Short Message Service (SMS) lets you send text messages of up to 160 characters over a 2G wireless network to a wireless phone. SMS is slow and you must have a network connection to receive the data.
- 34. Evolution of Wireless Networks Some handheld computers use Infrared technology to “ beam ” information from one source to another without the use of wired connections. Over 60 major U.S. markets have new 3G wireless systems (third-generation wireless) in place. Some European countries are building and licensing 3G wireless systems. 3G wireless systems offer data transfer rates of up to 2 Mbps and constant connections. Bandwidth and cost are two obstacles for getting 3G wireless systems going in the United States.
- 35. Evolution of Wireless Networks The conversion from 2G to 3G wireless requires the carriers to invest in technology to make the change. Many carriers have transformed and upgraded their existing networks by creating 2.5G wireless systems. There isn’t a single network standard. A wireless device is manufactured to work only on a single type of network, because different networks use different frequencies in the radio spectrum. If you choose a wireless carrier with a 2.5G network, for example, you will not be able to receive a signal in an area with only a 2G or a 3G network because your device operates on a different frequency.
- 36. Evolution of Wireless Networks 3.5G wireless networks use a new network protocol called Universal Mobile Telephone Service (UMTS), which is an extension of the existing W-CDMA network, to provide network connections of up to 10 Mbps. Fourth-generation wireless networks ( 4G wireless ) also called 3G wireless and beyond networks 4G technology is expected to bring network connection speeds of up to 100 Mbps and deliver high quality audio and video to connected devices
- 37. Wireless Local Area Networking Wireless fidelity ( Wi-Fi ): a trademarked name of the Wireless Ethernet Compatibility Alliance (WECA) that specifies the interface between a wireless client and a base station or between two wireless clients. Wireless local area network ( WLAN ): a network in which devices use high frequency radio waves instead of wires to communicate. Wi-Fi operates in the 2.4 GHz radio spectrum, which is the same spectrum used by cordless phones, garage door openers, microwave ovens, and other devices. because this spectrum is unlicensed, it is free the 3G wireless spectrum needs to be licensed
- 38. Wireless Local Area Networking New Perspectives on The Internet, Sixth Edition—Comprehensive Tutorial 6 wired local area network wireless local area network
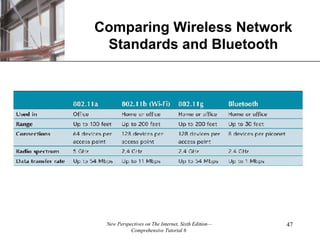
- 39. Wireless Local Area Networking Three of the most widely used standards for WLANs are 802.11a, 802.11b, and 802.11g. Transfer rate: the speed at which data is transmitted from an access point (or base station) to the wireless device. Access point: a hardware device with one or more antennae that permits communication between wired and wireless networks so wireless clients can send and receive data. Range: physical distance between the access point and the wireless device.
- 40. Wireless Local Area Networking Wi-Fi usually refers to the 802.11b specification which is the specification on which most Wi-Fi devices operate. Dual access point: a new device that makes the 802.11a and 802.11b wireless standards and the 802.11b and 802.11 g wireless standards interoperable. Wi-Fi is often used as an alternative in an office building or other area in which you might find a traditional wired local area network. It can be used where wiring cannot be installed.
- 41. Wireless Local Area Networking Laptop computers and other devices must have Wi-Fi compatible hardware installed in them to send and receive data with the network. Once you have a network interface card or other Wi-Fi compatible device, you can connect to the WLAN via that device, provided that it is physically within the area covered by the network. If you position enough access points within the appropriate range of each other, the WLAN can grow to cover an entire office complex or geographic area.
- 42. Personal Area Networking Personal area networking : refers to the wireless network that you use to connect personal devices to each other. There are two major types of personal area networks: Infrared and Bluetooth.
- 43. Infrared Technology The Infrared Data Association ( IrDA ): a group dedicated to developing low-cost, high-speed wireless connectivity solutions. Using infrared technology, you can wirelessly beam information from one device to another compatible device using Infrared light waves. This technology is used with PDAs, notebook computers, printers, phones, and other peripheral devices. A disadvantage is the lack of software products that can handle the transfer. The devices and the software that runs them must be compatible with each other.
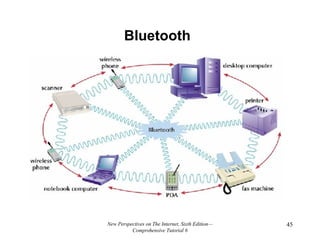
- 44. Bluetooth Bluetooth : a technology that provides short-range radio links between personal computers, handheld devices, wireless phones, headsets, printers, and other electronic devices. For devices without chipsets that enable them to receive Bluetooth radio waves you can purchase an adapter to enable use with other Bluetooth devices. Bluetooth doesn’t need an access point for communication; devices communicate with each other automatically. Bluetooth isn’t really “owned” by any specific manufacturer or group.
- 45. Bluetooth New Perspectives on The Internet, Sixth Edition—Comprehensive Tutorial 6
- 46. Bluetooth Using Bluetooth technology, you can synchronize and share data between as many as eight Bluetooth compatible devices within the specified range at a rate of up to 1 Mbps. A collection of devices connected via Bluetooth technology is called a piconet . A piconet can connect to eight devices at a time. You can use Bluetooth-enabled devices to transfer files, listen to music playing on a computer through a headset, print documents, or connect your notebook computer to the Internet using a wireless phone that is in your desk drawer or briefcase.
- 47. Comparing Wireless Network Standards and Bluetooth
- 48. Wireless Wide Area Networking Wireless device connections let you access the Internet on a PDA, wireless phone, or notebook computer from anywhere in the world without a wired connection. A WLAN provides a wireless connection to a network, but devices must be within the stated boundary of the WLAN. In 2.5G and 3G wireless systems, wireless wide area networking ( WWAN ) makes it possible to access the Internet from anywhere within the boundaries of the wireless network to which you are connected.
- 49. Creating a Wireless Wide Area Network New Perspectives on The Internet, Sixth Edition—Comprehensive Tutorial 6
- 50. Using Wireless Devices to Access the Internet The technology and standards that dictate what you can accomplish with a wireless device change on a daily basis. New standards emerge, new hardware is created, and new ways of connectivity arrive. Select a wireless solution that has the locations in which the technology will be used in its network coverage area and that supports the features you plan to use.
- 51. Metropolitan Area Networking: WiMAX WiMAX ( Worldwide Interoperability for Microwave Access ): uses 802.16 wireless network standard being developed for use in metropolitan areas. Metropolitan area network ( MAN ): provides wireless broadband Internet access via radio signals in the 2 to 11 GHz and 10 to 66 GHz radio spectrum with a range of up to 31 miles and speeds of up to 70 Mbps. When multiple WiMAX towers are connected to each other, WiMAX has the potential to solve some of the geographical and speed limitations of wired networks and other wireless networks, including Wi-Fi.
- 52. Metropolitan Area Networking: WiMAX WiMAX provides broadband Internet connections at the same speed as DSL and cable, but through wireless radio connections. WiMAX works by connecting a WiMAX tower to an ISP that provides the Internet service. The WiMAX towers are connected to each other via radio signals. WiMAX transmitters, which can be located up to 31 miles from the towers, send the signal to homes and businesses that have WiMAX receivers. Businesses can plug the WiMAX receiver into their existing local area networks to provide high-speed Internet access to all of their connected devices.
- 53. Metropolitan Area Networking: WiMAX New Perspectives on The Internet, Sixth Edition—Comprehensive Tutorial 6
- 54. Metropolitan Area Networking: WiMAX VoIP ( Voice over Internet Protocol ): converts audio signals to digital packets so that you can use a broadband wired or wireless Internet connection to make local and long distance telephone calls. Because WiMAX can support many types of data transmissions, it is also used for VoIP. Most experts predict that all new desktop and notebook computers and wireless devices will have built-in 802.16 cards by 2007.
- 55. Summary There are different Internet resources to chat in real time with friends and business associates There are different types of wireless networks, wireless network standards, and wireless devices. When selecting a wireless device, make sure that you understand the features of the network on which that wireless device operates. Carefully examine the network’s geographic coverage area, pricing options, and the provider’s future expansion plans before selecting the device that most closely matches the functions that you need it to perform.