Ad
User Account Access Graphs
- 1. User Account Access Graphs ACM CCS 2019 Sven Hammann, Saša Radomirović, Ralf Sasse and David Basin 林彥賓 2020/11/25
- 2. Outline Introduction Contribution Graph model Access Sets SECURITY SCORING SCHEMES Account importance 2
- 3. Introduction How save is your account? 3
- 4. Contribution evulate security that could allow an attacker to compromise an account evulate recoverability that could result in a user being permanently locked out of an accoun 4
- 5. Graph model Definition: An account access graph is a directed graph , where are vertices, are colors, and are directed colored edges. model account same color : all needed to access the account (i.e., multi-factor authentication) different colors : alternative access methods credentials : an account provides access to the credential G = (V , E , C )G G G VG CG E ⊆G V ×G V ×G CG v e e v e 5
- 6. example A webshop account acc_shop that can be accessed with password pwd_shop or recovered from the e-mail account acc_mail. The e-mail account requires two- factor authentication with password pwd_mail and a code. The code is generated by an authentication app on a device. The device can be unlocked using either a fingerprint (finger) or a PIN. 6
- 7. Access Sets Definition: the set of all vertices that have a c-colored edge to v. Formally, for an account access graph In (v) :c = {v′ ∈ V ∣e =G (v′, v, c) ∈ E }G Definition: the set of vertices that can directly or transitively be accessed from a set of vertices V the set for a vertex set is the smallest set that satisfies and is closed under the rule v ∈ accessFrom(V ) ∃c ∈ C : ∅ ⊊ In (v) ⊆ accessFrom(V )G c In (v)c G = (V , E , C )G G G accessFrom(v) accessFrom(V ) V ⊆ VG V ⊆ accessFrom(V ) 7
- 8. Definition: the set of all sets of vertices that provide access to a vertex , that is AccessTo(v) := {V ⊆ V ∣v ∈G accessFrom(V )} Definition: The minimal access sets of a vertex v are all minimal sets that provide access to v. MinAccessTo(v) := {V ⊆ V ∣V ∈G AccessTo(v) ∧ (∀V ⊊′ V : V ∈′ / AccessTo(v))} AccessTo(v) v MinAccessTo(v) 8
- 9. Definition: the set of all leaves in the graph Definition: A vertex with respect to a set of initial vertices consists of the minimal access sets V that only contain vertices from AccessBase(v) := {V ∈ MinAccessTo(v)∣V ⊆ V }init Vinit AccessBase(v, V )init v Vinit Vinit 9
- 10. Example accessFrom(pwd , device, PIN) =mail {pwd , device, PIN, code, acc , acc }mail mail shop AccessTo(acc ) =mail {{acc }, {pwd , code}, {pwd , device, finger}, {pwd , device, PIN}}mail mail mail mail AccessBace(acc , V ) =shop init {{pwd }, {pwd , device, finger}, {pwd , device, PIN}}shop mail mail 10
- 11. SECURITY SCORING SCHEMES main idea Whenever we can access , we can also access . Therefore, is at least as secure as V =init {pwd , device}acc AccessBace(acc , V ) =basic init {pwd }acc AccessBace(acc , V ) =full init {pwd , device}acc accfull accbasic accfull accbasic 11
- 12. Requirements : Domain over which scores are defined is a partial order relating elements in : the set of initial vertices : maps a multiset of initial scores (of vertices in an access set) to an intermediate score (for that access set) : maps a set of intermediate scores (of access sets in a vertex’s access base) to a score (for that vertex D ⪯ D V ∈init VG Eval : P (D) →M D Combine : P(D) → D EvalSet(S) := Eval({Init(v′)∣v′ ∈ S}) Score(v) := Combine({EvalSet(S)∣S ∈ AccessBase(v, V init)}) 12
- 13. Definition: Let be vertices in an account access graph . An access base for a vertex is at least as secure as that for if and only if any set of vertices that provides access to also provides access to AccessBase(v , V ) ⪯A init AccessBase(v , V ) :B init ⟺ ∀V ⊆ V :init v ∈B accessFrom(V ) → v ∈A accessFrom(V ) Theorem: Let be vertices in an account access graph and let be given. Let and (∀B ∈i B∃A ∈j A : A ⊆j B ) ⟺i A ⪯ B v , vA B G vB vA V vB vA v , vA B G V ⊆init VG A := AccessBase(v , V )A init B := AccessBase(v , V )B init 13
- 14. Definition A security scoring scheme with score function is sound if, for any two vertices and AccessBase(v , V ) ⪯A init AccessBase(v , V ) ⟹B init Score (v ) ⪯S A S Score (v )S B Theorem A security scoring scheme is sound if the following two conditions hold (D, ⪯S , V , Init, Eval, Combine)init ScoreS vA vB (D, ⪯S , V , Init, Eval, Combine)init 14
- 16. The sum-then-min scoring scheme: example: D = N, ⪯=≤, Eval(M) = m, Combine(S) =∑m∈M min (s)s∈S 16
- 17. Multiset-based Scoring Scheme Set ⦃1, 1⦄ denotes an access method that requires two credentials with value 1 each a score of {⦃1, 1⦄, ⦃2⦄} denotes that the account can (transitively) be accessed either by two credentials with value 1 each, or a single credential with value 2. Definition for comparing scores: For two multisets and over if and only if , and there exists an indexing of their elements such that , and Example: and , but and are incomparable M N N, M ⪯ N k = ∣M∣ ≤ ∣N∣ = n M = {[m , ..., m ]}, N =1 k {[n , ..., n ]}1 n ∀1 ≤ i ≤ k : m ≤i ni {[1, 1]} ≺ {[1, 2]} {[1, 2]} ≺ {[1, 1, 2]} {[1, 2]} {[1, 1, 1]} 17
- 18. Definition 12: For two sets of multisets if and only if Example: , but and are incomparable S , S , S ⪯1 2 1 S2 ∀N ∈ S ∃M ∈2 S :1 M ⪯ N {{[1, 1]}, {[1, 2]}} ≺ {{[1, 2]}, {[1, 1, 2]}} {{[1, 2]}} {{[1, 1]}, {[1, 1, 1]}} 18
- 19. : for sets where Definition: The distributed product of two sets of multisets is defined as S ⊕1 S =2 {M ⊎ N∣M ∈ S , N ∈1 S }2 Example: ⊎ A ∪ B A, B A ∩ B = ∅ S , S1 2 ⊕{[{{[1]}}, {{[2, 2]}}, {{[3]}, {[4]}}]} = {{[1, 2, 2, 3]}, {[1, 2, 2, 4]}} 19
- 20. Multisets Scoring Scheme : the sets of multisets over : Definition 12 Eval = Combine( ) = minimal( ), minimal := D = P (N)M N ⪯ ⊕ S S∪ S :∪ = ∪ SS ∈Si i {M∣M ∈ S ∧∪ ¬(∃M ∈′ S :∪ M ≺′ M)} 20
- 21. Example {⦃1, 1⦄} and {⦃2⦄} are incomparable Score(acc ) =A Combine(EvalSet({pwd , pwd })) =A B {{[1, 1]}} Score(acc ) =B Combine(EvalSet({device})) = {{[2]}} 21
- 22. Attacker attribute sets: Location = {rem, loc}, with rem < loc a local attacker has more capabilities than a remote one Skill = {none, some, exp}, with none < some < exp none: The attacker has no special skills some: The attacker he has special skills can exploit known vulnerabilities exp: An expert hacker An account with a score of {(rem, some), (loc, none)} could be compromised by a remote attacker with special skills or by a local attacker without any special skills. (rem, exp), (loc, some), could also compromise the account. 22
- 23. Definition 16: For if and only if Consider a set of attacker tuples . Another set . is smaller or equal to if and only if for each attacker tuple in , there is a tuple representing a weaker (or equal) attacker, in Any attacker that could compromise the account with score S2 could also compromise the account with score S1 S , S ∈1 2 P(A ×1 ... × A ), S ⪯n 1 S2 ∀u ∈ S ∃t ∈2 S :1 t ⪯ u S2 S1 S1 S2 S2 S1 23
- 24. Aattacker model scoring scheme Let be totally ordered attribute sets : sets of attribute tuples. : Definition 16. is a singleton set that contains the component-wise maximum of tuple set A , ..., A1 n D = P(A , ..., A )1 n ⪯ Eval(M) = compMax(M )∪ M :∪ = ∪ MM ∈Mi i compMax M∪ Combine(S) = minimal(S )∪ S :∪ = ∪ SS ∈Si i minimal(S ) :∪ = {t∣t ∈ S ∧∪ ¬(∃t ∈ S :∪ t′ ≺ t)} 24
- 25. Score(accshop) = Combine(EvalSet({pwdshop}), EvalSet({pwdmail, device, finger}), EvalSet({pwdmail, device, PIN})) = Combine({(rem, some)}, {(loc, exp)}, {(loc, some)}) = minimal({(rem, some), (loc, exp), (loc, some)}) = {(rem, some)} 25
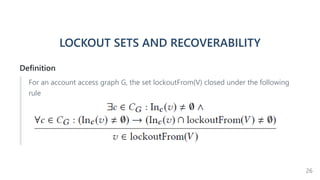
- 26. LOCKOUT SETS AND RECOVERABILITY Definition For an account access graph G, the set lockoutFrom(V) closed under the following rule 26
- 27. Example: lockoutFrom({pwdshop, device}) = {pwdshop, device, code, accmail, accshop} 27
- 28. Definition Definition minimal lockout sets of a vertex v: Definition V_{init}$ denotes the vertices that a user might directly get locked out of Lockout(v) := {V ∈ V ∣v ∈G lockoutFrom(V )} MinLockout(v) := {V ∈ V ∣V ∈G Lockout(v) ∧ (∀V ′(V : V ′ < Lockout(v))} LockoutBase(v, V ) :init = {V ∈ MinLockout(v)∣V ⊆ V }init 28
- 29. Example Let Vinit be the set of all leaves in the graph LockoutBase(acc , V ) = shop init {pwd , pwd }, {pwd , device},shop mail shop 29
- 31. Inherent lockout risk There is an account with a service that provides single sign-on, and an account with a web shop using this single sign-on. accSSO accshop V :init = {pwd , acc }SSO SSO AccessBase(acc , V ) =shop init LockoutBase(acc , V ) =shop init {{pwd }, {acc }}SSO SSO 31
- 32. Recovery paths and backdoors Backdoor: An account can be accessed more easily using recovery access methods than using its primary authentication method Recoverability point of view: If there is no backdoors in an access account graph, it's ineffective recovery. Definition S: security scoring scheme with scoring function Score be a set of edges used in recovery methods : the graph obtained from G by removing the edges in HasBackdoorS, E (v) :rec = Score (v) ≺G Score (v)G′ E ⊊rec EG G′ := (V , EG G E , C )rec G Erec 32
- 33. let Thus, E :rec = {(acc , acc , red),mailA bank (acc , acc , red)}mailB mailA AccessBase (acc , V ) =G bank init {{pwd , device},bank {pwd , device}, {pwd }}mailA mailB AccessBase (acc , V ) =G′ bank init {{pwd , device}}bank Score (acc ) =G bank 1 < 3 = Score (acc )G′ bank HasBackdoor (acc )S,Erec bank 33
- 34. Account importance Definition: let be a function that assigns to a vertex an importance value from a partially ordered domain Inconsistent (v , v ) :S,I 1 2 = I(v ) ≺1 I(v ) ∧2 Score(v ) ⪯1 Score(v )2 That is, represents a more important account than , but receives the same or a lower score value. I : V → DI DI v1 v2 34
- 35. Example = {low, med, high} with the expected ordering Thus, DI I(acc ) =bank high ≻ med = I(acc )shop Score(acc ) =bank {(rem, some)} ≻ {(loc, some)} = Score(acc )shop Inconsistent (acc , acc )S,I bank shop 35

















![Multiset-based Scoring Scheme
Set ⦃1, 1⦄ denotes an access method that requires two credentials with value 1
each
a score of {⦃1, 1⦄, ⦃2⦄} denotes that the account can (transitively) be accessed either
by two credentials with value 1 each, or a single credential with value 2.
Definition for comparing scores:
For two multisets and over if and only if
, and there exists an indexing of their elements such that
, and
Example:
and , but and are
incomparable
M N N, M ⪯ N k = ∣M∣ ≤ ∣N∣ = n
M =
{[m , ..., m ]}, N =1 k {[n , ..., n ]}1 n ∀1 ≤ i ≤ k : m ≤i ni
{[1, 1]} ≺ {[1, 2]} {[1, 2]} ≺ {[1, 1, 2]} {[1, 2]} {[1, 1, 1]}
17](https://image.slidesharecdn.com/useraccessgraph-201129053945/85/User-Account-Access-Graphs-17-320.jpg)
![Definition 12:
For two sets of multisets if and only if
Example:
, but and
are incomparable
S , S , S ⪯1 2 1 S2 ∀N ∈ S ∃M ∈2 S :1
M ⪯ N
{{[1, 1]}, {[1, 2]}} ≺ {{[1, 2]}, {[1, 1, 2]}} {{[1, 2]}} {{[1, 1]}, {[1, 1, 1]}}
18](https://image.slidesharecdn.com/useraccessgraph-201129053945/85/User-Account-Access-Graphs-18-320.jpg)
![: for sets where
Definition:
The distributed product of two sets of multisets is defined as
S ⊕1 S =2 {M ⊎ N∣M ∈ S , N ∈1 S }2
Example:
⊎ A ∪ B A, B A ∩ B = ∅
S , S1 2
⊕{[{{[1]}}, {{[2, 2]}}, {{[3]}, {[4]}}]} = {{[1, 2, 2, 3]}, {[1, 2, 2, 4]}}
19](https://image.slidesharecdn.com/useraccessgraph-201129053945/85/User-Account-Access-Graphs-19-320.jpg)

![Example
{⦃1, 1⦄} and {⦃2⦄} are incomparable
Score(acc ) =A Combine(EvalSet({pwd , pwd })) =A B {{[1, 1]}}
Score(acc ) =B Combine(EvalSet({device})) = {{[2]}}
21](https://image.slidesharecdn.com/useraccessgraph-201129053945/85/User-Account-Access-Graphs-21-320.jpg)










































![Lec 9 05_sept [compatibility mode]](https://cdn.slidesharecdn.com/ss_thumbnails/lec905septcompatibilitymode-130917013819-phpapp01-thumbnail.jpg?width=560&fit=bounds)

















































