Using In-Memory Encrypted Databases on the Cloud
Download as ppt, pdf2 likes980 views
The document proposes using in-memory encrypted databases on the cloud to address privacy issues. It presents an agent-based approach where each user has a local database encrypted with a key only available to a trusted synchronizer. This allows data to be shared securely while minimizing encryption/decryption overhead. A prototype was implemented using HyperSQL. Benchmark results showed the overhead of the proposed solution is low, especially for read operations, making it suitable for privacy-focused applications like professional networks that require frequent data sharing.
1 of 31
Downloaded 29 times
![Using In-Memory Encrypted Databases on the Cloud Francesco (and Davide) Pagano [email_address] Department of Information Technology Università degli Studi di Milano - Italy](https://image.slidesharecdn.com/presentazionepagano1-110906092153-phpapp02/85/Using-In-Memory-Encrypted-Databases-on-the-Cloud-1-320.jpg)





























Ad
Recommended
E031102034039



E031102034039theijes This document summarizes a research paper on secured authorized deduplication in a hybrid cloud system. The system aims to provide data deduplication, differential authorization for access, and confidentiality of data files. It involves a public cloud for storage, a private cloud for managing access tokens, and users who generate keys for files stored on the public cloud. When uploading a file, the user encrypts it and sends it to the public cloud along with the key to the private cloud. To download, the user must provide the correct key to the private cloud to gain access to encrypted files from the public cloud. This hybrid cloud model uses deduplication for storage optimization while controlling access through differential authorization of private keys.
Ieeepro techno solutions 2014 ieee java project -key-aggregate cryptosystem...



Ieeepro techno solutions 2014 ieee java project -key-aggregate cryptosystem...hemanthbbc 2016 - IEEE PROJECT TITLES
www.ieeepro.org
Contact us for LATEST 2016 IEEE TOPICS.
IEEEPRO TECHNO SOLUTIONS,
Near ABOVE KPN TRAVELS
Ashok Nagar, Chennai - 87
Mobile - 8939 964 964, 8939 660 690
Email - [email protected]
LATEST IEEE PROJECTS, 2016 IEEE PROJECTS, IEEE Projects in Chennai, Engineering Projects, Engineering IEEE Projects, Final Year Projects, Final Year IEEE Projects, IEEE Projects 2015 - 2016. 2016 IEEE projects, 2016 IEEE java projects, 2016 IEEE Dotnet projects, 2016 IEEE .net projects,IEEE Projects, IEEE Projects 2016 ,IEEE Academic Projects, IEEE 2016 Projects, IEEE, IEEE Projects, IEEE Software Projects, Latest IEEE Projects,IEEE Student Projects, IEEE Final year Student Projects,Final Year Projects, final year IEEE 2016 projects, final year 2016 projects,ENGINEERING PROJECTS, MCA projects, BE projects, Embedded Projects, JAVA projects, J2EE projects, .NET projects, Students projects,BE projects, B.Tech. projects, ME projects, M.Tech. projects, M.Phil Projects.
2



2srikavitha Cloud computing is a new concept that emerged in the late 1990s involving hosting applications and data over the internet. There are two main types - software as a service where vendors host specific applications, and infrastructure as a service where clients run their own software on vendor machines through virtual machines. Large cloud vendors include Amazon and Google. Cloud databases store and retrieve data for large numbers of users and prioritize availability and scalability over consistency. BigTable is Google's cloud database that stores attribute values as strings using a hierarchical key of record identifier and attribute name to retrieve data.
Secure deduplicaton with efficient and reliable convergent



Secure deduplicaton with efficient and reliable convergentJayakrishnan U This document proposes a new technique called Dekey for secure deduplication in cloud storage. Dekey distributes convergent keys across multiple key servers to reduce key overhead and improve security compared to traditional convergent encryption. The document outlines issues with traditional encryption approaches, describes the baseline convergent encryption approach and issues with it, and then introduces the Dekey approach. Dekey supports both file-level and block-level deduplication while providing cost efficiency, security, and reliability through distributed convergent key management across multiple servers.
Ieeepro techno solutions 2014 ieee java project - query services in cost ef...



Ieeepro techno solutions 2014 ieee java project - query services in cost ef...hemanthbbc 2016 - IEEE PROJECT TITLES
www.ieeepro.org
Contact us for LATEST 2016 IEEE TOPICS.
IEEEPRO TECHNO SOLUTIONS,
Near ABOVE KPN TRAVELS
Ashok Nagar, Chennai - 87
Mobile - 8939 964 964, 8939 660 690
Email - [email protected]
IEEE Projects in Chennai, Engineering Projects, Engineering IEEE Projects, Final Year Projects, Final Year IEEE Projects, IEEE Projects 2015 - 2016. 2014 - 2015 IEEE projects, 2014 - 2015 IEEE java projects, 2014 - 2015 IEEE Dotnet projects, 2014 - 2015 IEEE .net projects,IEEE Projects, IEEE Projects 2014 - 2015 ,IEEE Academic Projects, IEEE 2014 - 2015 Projects, IEEE, IEEE Projects, IEEE Software Projects, Latest IEEE Projects,IEEE Student Projects, IEEE Final year Student Projects,Final Year Projects, final year IEEE 2014 - 2015 projects, final year 2014 - 2015 projects,ENGINEERING PROJECTS, MCA projects, BE projects, Embedded Projects, JAVA projects, J2EE projects, .NET projects, Students projects,BE projects, B.Tech. projects, ME projects, M.Tech. projects, M.Phil Projects.
Panda public auditing for shared data with efficient user revocation in the c...



Panda public auditing for shared data with efficient user revocation in the c...IGEEKS TECHNOLOGIES IGeekS Technologies (Make Final Year Project)
No: 19, MN Complex, 2nd Cross,
Sampige Main Road, Malleswaram
Bangalore- 560003.
Phone No: 080-32487434 /9590544567 / 9739066172
Mail: [email protected] , [email protected]
Land mark : Near to Mantri Mall, Malleswaram Bangalore
A Hybrid Cloud Approach for Secure Authorized Deduplication



A Hybrid Cloud Approach for Secure Authorized DeduplicationSWAMI06 Data deduplication is one of important data compression techniques for eliminating duplicate copies of repeating data,
and has been widely used in cloud storage to reduce the amount of storage space and save bandwidth. To protect the confidentiality
of sensitive data while supporting deduplication, the convergent encryption technique has been proposed to encrypt the data before
outsourcing. To better protect data security, this paper makes the first attempt to formally address the problem of authorized data
deduplication. Different from traditional deduplication systems, the differential privileges of users are further considered in duplicate
check besides the data itself.We also present several new deduplication constructions supporting authorized duplicate check in a hybrid
cloud architecture. Security analysis demonstrates that our scheme is secure in terms of the definitions specified in the proposed
security model. As a proof of concept, we implement a prototype of our proposed authorized duplicate check scheme and conduct
testbed experiments using our prototype. We show that our proposed authorized duplicate check scheme incurs minimal overhead
compared to normal operations.
IRJET- Multiple Keyword Search over Encrypted Cloud Data



IRJET- Multiple Keyword Search over Encrypted Cloud DataIRJET Journal This document proposes a system for multi-keyword ranked search over encrypted cloud data. The system consists of four main components: data owners who upload encrypted data to the cloud server, data users who search for and access encrypted files, an administrator server that handles authentication and generates trapdoors for searches, and the cloud server that stores the encrypted data and indexes. When a data user performs a search, the administrator generates an encrypted trapdoor for the keywords to allow searching without revealing the plaintext to the cloud server. Search results are ranked based on factors like download frequency. The proposed system aims to provide secure, authenticated searches over outsourced encrypted data while preserving data privacy.
A hybrid cloud approach for secure authorized deduplication



A hybrid cloud approach for secure authorized deduplicationTmks Infotech TMKS Infotech.
#1510,Sri Gowri Shankara Complex,
2nd Floor,MKK Road,
Near Harishchandra Ghat,
Mariyappanapalya,
Rajajinagar 2nd Stage,
Bangalore - 560021
K.Manjunath - 09535866270
http://www.tmksinfotech.com
http://www.bemtechprojects.com
SECURE AUDITING AND DEDUPLICATING DATA IN CLOUD



SECURE AUDITING AND DEDUPLICATING DATA IN CLOUDNexgen Technology bulk ieee projects in pondicherry,ieee projects in pondicherry,final year ieee projects in pondicherry
Nexgen Technology Address:
Nexgen Technology
No :66,4th cross,Venkata nagar,
Near SBI ATM,
Puducherry.
Email Id: [email protected].
www.nexgenproject.com
Mobile: 9751442511,9791938249
Telephone: 0413-2211159.
NEXGEN TECHNOLOGY as an efficient Software Training Center located at Pondicherry with IT Training on IEEE Projects in Android,IEEE IT B.Tech Student Projects, Android Projects Training with Placements Pondicherry, IEEE projects in pondicherry, final IEEE Projects in Pondicherry , MCA, BTech, BCA Projects in Pondicherry, Bulk IEEE PROJECTS IN Pondicherry.So far we have reached almost all engineering colleges located in Pondicherry and around 90km
Attribute Based Encryption with Privacy Preserving In Clouds 



Attribute Based Encryption with Privacy Preserving In Clouds Swathi Rampur This is a ppt made by shrihari ,in this encryption with privacy preserving in clouds is described!
It will be helpfull for those who are doing projects on cloud!
IEEE 2014 JAVA MOBILE COMPUTING PROJECTS Preserving location privacy in geo s...



IEEE 2014 JAVA MOBILE COMPUTING PROJECTS Preserving location privacy in geo s...IEEEFINALYEARSTUDENTPROJECTS To Get any Project for CSE, IT ECE, EEE Contact Me @ 09666155510, 09849539085 or mail us - [email protected] Our Website: www.finalyearprojects.org
IJSRED-V2I2P10



IJSRED-V2I2P10IJSRED The document proposes a secure client-side deduplication scheme called KeyD that uses identity-based broadcast encryption instead of independent key management to effectively manage convergent keys for deduplication. KeyD ensures data confidentiality and convergent key security while providing ownership privacy. Experimental results show that KeyD achieves better tradeoffs between storage costs, communication overhead, and computation overhead compared to traditional deduplication schemes.
Data deduplication and chunking



Data deduplication and chunkingSanchita Kadambari Data deduplication is a technique to eliminate redundant data and reduce storage needs. It works by identifying identical data chunks using cryptographic hash signatures and storing only one copy of each unique chunk. Chunking refers to dividing files into smaller chunks which are then analyzed to find duplicates. There are different approaches to chunking, including fixed-size, variable content-defined sizes, and frequency-based chunking. Chunk-level deduplication identifies redundancy at a finer granularity than file-level deduplication and is generally more efficient, though it requires an effective chunking algorithm to maximize deduplication benefits.
IJET-V2I6P33



IJET-V2I6P33IJET - International Journal of Engineering and Techniques Privacy preserving is the essential aspect for cloud. In privacy preserving ranked keyword search, data
owner outsource the document in an encrypted form. So for privacy purpose, Reliable ciphertext search technique
is essentially. To design ciphertext search technique which provide encrypted document is critical task. In this
paper, hierarchical clustering method is designed for semantic search and fast ciphertext search within a big data
environment. In hierarchical clustering, documents are based on maximum relevance score and clusters are divided
into sub-clusters.
panda public auditing for shared data with efficient user revocation in the c...



panda public auditing for shared data with efficient user revocation in the c...swathi78 LOGIC SYSTEMS
1st Floor, Reddy Comlex, Opp. SPencers, Near Satyam Theatre, Ameerpet, Hyderabad
9533694296,9703109334
[email protected]
www.logicsystems.org.in
Is2215 lecture7 lecturer_ado_intro



Is2215 lecture7 lecturer_ado_introdannygriff1 This document discusses ADO.NET and how it can be used to interact with databases in Visual Basic.NET. ADO.NET uses a disconnected data model that allows applications to query databases without maintaining an open connection. It keeps a local copy of queried data in a dataset object. The main components of ADO.NET - connection, command, data adapter, and dataset - are introduced. Code examples are provided to demonstrate connecting to an Access database and retrieving, displaying, and navigating records using ADO.NET.
A secure erasure code based cloud storage



A secure erasure code based cloud storageIMPULSE_TECHNOLOGY For further details contact:
N.RAJASEKARAN B.E M.S 9841091117,9840103301.
IMPULSE TECHNOLOGIES,
Old No 251, New No 304,
2nd Floor,
Arcot road ,
Vadapalani ,
Chennai-26.
Final 1st



Final 1stgokulprema The document proposes a system for multi-keyword ranked search over encrypted cloud data while preserving privacy. It addresses limitations in previous systems that allowed single keyword search or did not consider privacy. The proposed system uses asymmetric key encryption, a block-max index, and dynamic key generation to allow efficient retrieval of relevant encrypted data from the cloud without security breaches. It involves three parts: (1) a server that encrypts and stores data in the cloud and sends decryption keys; (2) a cloud server that handles search requests, ranks results, and responds; and (3) users that request data from the cloud server.
Methodology for Optimizing Storage on Cloud Using Authorized De-Duplication –...



Methodology for Optimizing Storage on Cloud Using Authorized De-Duplication –...IRJET Journal This document summarizes a research paper that proposes a methodology for optimizing storage on the cloud using authorized de-duplication. It discusses how de-duplication works to eliminate duplicate data and optimize storage. The key steps are chunking files into blocks, applying secure hash algorithms like SHA-512 to generate unique hashes for each block, and comparing hashes to reference duplicate blocks instead of storing multiple copies. It also discusses using cryptographic techniques like ciphertext-policy attribute-based encryption for authentication and security on public clouds. The proposed approach aims to optimize storage while providing authorized de-duplication functionality.
A Hybrid Cloud Approach for Secure Authorized Deduplication



A Hybrid Cloud Approach for Secure Authorized Deduplication1crore projects - The document proposes a new deduplication system that supports differential or authorized duplicate checking in a hybrid cloud architecture consisting of a public and private cloud. This allows users to securely check for duplicates of files based on their privileges.
- Convergent encryption is used to encrypt files for deduplication while maintaining confidentiality. A new construction is presented that additionally encrypts files with keys derived from user privileges to enforce access control during duplicate checking.
- The system aims to efficiently solve the problem of deduplication with access control in cloud computing. It allows duplicate checking of files marked with a user's corresponding privileges to realize access control while preserving benefits of deduplication.
Access control in decentralized online social networks applying a policy hidi...



Access control in decentralized online social networks applying a policy hidi...IGEEKS TECHNOLOGIES The document proposes a policy-hiding cryptographic scheme for access control in decentralized online social networks that aims to achieve both privacy and performance. Existing DOSNs reveal access policies but some cryptographic variants hide policies at the cost of performance. The proposed scheme uses predicate encryption with a univariate polynomial construction for access policies that drastically improves performance while leaking some policy information. Bloom filters are also used to decrease decryption time and indicate decryptable objects. The goal is to enable privacy-preserving access control without compromising usability in resource-constrained DOSN environments.
In memory databases presentation



In memory databases presentationMichael Keane This document provides an overview of in-memory databases, summarizing different types including row stores, column stores, compressed column stores, and how specific databases like SQLite, Excel, Tableau, Qlik, MonetDB, SQL Server, Oracle, SAP Hana, MemSQL, and others approach in-memory storage. It also discusses hardware considerations like GPUs, FPGAs, and new memory technologies that could enhance in-memory database performance.
In-Memory DataBase



In-Memory DataBasePridhvi Kodamasimham In-memory databases (IMDBs) store data primarily in RAM for faster access than disk-based databases. While an older concept, IMDBs have become more practical due to lower RAM costs, multi-core CPUs, and 64-bit systems allowing more memory. IMDBs have different architectures, data representations, indexing, and query processing optimized for memory versus disk. They also face challenges in providing durability without disk and scaling to very large data sizes.
In-Memory Database Platform for Big Data



In-Memory Database Platform for Big DataSAP Technology SAP HANA is an in-memory database and platform that allows for real-time analytics on large datasets. It utilizes columnar storage, massive parallelization across cores and servers, and in-memory computing to enable interactive queries and analysis of big data without the latency of disk access. SAP HANA provides a single system for both transaction processing and analytics, combining structured and unstructured data on a scalable platform.
Sql Server 2008 Security Enhanments



Sql Server 2008 Security EnhanmentsEduardo Castro This document discusses features and capabilities of SQL Server 2008 including:
- Transparent data encryption to encrypt entire databases
- External key management to consolidate security keys in the data center
- Auditing to monitor data access and modifications
- Declarative management framework to automate administrative tasks
- Server group management to simplify installation, configuration and monitoring across instances
in-memory database system and low latency



in-memory database system and low latencyhyeongchae lee This document discusses in-memory database systems and high performance computing. It begins with an overview of domestic and international in-memory databases like Altibase, Oracle TimesTen, McObject ExtremeDB, and KX Systems KDB+. It then discusses the advantages of in-memory architectures for achieving ultra-low latency. The rest of the document covers technologies that enable high performance like NUMA, SSDs, InfiniBand, message queues, and complex event processing. It concludes by discussing in-memory computing and high performance computing technologies.
Sap technical deep dive in a column oriented in memory database



Sap technical deep dive in a column oriented in memory databaseAlexander Talac The document describes a lecture on column-oriented in-memory databases. The lecture covers the status quo of enterprise computing, database storage techniques like row and column storage layouts, in-memory database operators like scanning and aggregation, and advanced storage techniques like dictionary encoding and tuple reconstruction. The goal is to provide a deep technical understanding of column-oriented in-memory databases and their application in enterprise systems.
In-memory Databases



In-memory DatabasesRobert Friberg This is from a 2 hour talk introducing in-memory databases. First a look at traditional RDBMS architecture and some of it's limitations, then a look at some in-memory products and finally a closer look at OrigoDB, the open source in-memory database toolkit for NET/Mono.
Real World Use Cases and Success Stories for In-Memory Data Grids (TIBCO Acti...



Real World Use Cases and Success Stories for In-Memory Data Grids (TIBCO Acti...Kai Wähner Kai Wähner is a technical lead who discusses in-memory computing and real-world use cases. In-memory computing uses memory for data storage and processing to enable acting in real-time. It offers benefits like eventing, fault tolerance, and high performance beyond traditional caching. Examples where in-memory computing has been applied include personalized customer experiences, routing messages, handling spikes in data, and storing stateful enterprise application data.
Ad
More Related Content
What's hot (14)
A hybrid cloud approach for secure authorized deduplication



A hybrid cloud approach for secure authorized deduplicationTmks Infotech TMKS Infotech.
#1510,Sri Gowri Shankara Complex,
2nd Floor,MKK Road,
Near Harishchandra Ghat,
Mariyappanapalya,
Rajajinagar 2nd Stage,
Bangalore - 560021
K.Manjunath - 09535866270
http://www.tmksinfotech.com
http://www.bemtechprojects.com
SECURE AUDITING AND DEDUPLICATING DATA IN CLOUD



SECURE AUDITING AND DEDUPLICATING DATA IN CLOUDNexgen Technology bulk ieee projects in pondicherry,ieee projects in pondicherry,final year ieee projects in pondicherry
Nexgen Technology Address:
Nexgen Technology
No :66,4th cross,Venkata nagar,
Near SBI ATM,
Puducherry.
Email Id: [email protected].
www.nexgenproject.com
Mobile: 9751442511,9791938249
Telephone: 0413-2211159.
NEXGEN TECHNOLOGY as an efficient Software Training Center located at Pondicherry with IT Training on IEEE Projects in Android,IEEE IT B.Tech Student Projects, Android Projects Training with Placements Pondicherry, IEEE projects in pondicherry, final IEEE Projects in Pondicherry , MCA, BTech, BCA Projects in Pondicherry, Bulk IEEE PROJECTS IN Pondicherry.So far we have reached almost all engineering colleges located in Pondicherry and around 90km
Attribute Based Encryption with Privacy Preserving In Clouds 



Attribute Based Encryption with Privacy Preserving In Clouds Swathi Rampur This is a ppt made by shrihari ,in this encryption with privacy preserving in clouds is described!
It will be helpfull for those who are doing projects on cloud!
IEEE 2014 JAVA MOBILE COMPUTING PROJECTS Preserving location privacy in geo s...



IEEE 2014 JAVA MOBILE COMPUTING PROJECTS Preserving location privacy in geo s...IEEEFINALYEARSTUDENTPROJECTS To Get any Project for CSE, IT ECE, EEE Contact Me @ 09666155510, 09849539085 or mail us - [email protected] Our Website: www.finalyearprojects.org
IJSRED-V2I2P10



IJSRED-V2I2P10IJSRED The document proposes a secure client-side deduplication scheme called KeyD that uses identity-based broadcast encryption instead of independent key management to effectively manage convergent keys for deduplication. KeyD ensures data confidentiality and convergent key security while providing ownership privacy. Experimental results show that KeyD achieves better tradeoffs between storage costs, communication overhead, and computation overhead compared to traditional deduplication schemes.
Data deduplication and chunking



Data deduplication and chunkingSanchita Kadambari Data deduplication is a technique to eliminate redundant data and reduce storage needs. It works by identifying identical data chunks using cryptographic hash signatures and storing only one copy of each unique chunk. Chunking refers to dividing files into smaller chunks which are then analyzed to find duplicates. There are different approaches to chunking, including fixed-size, variable content-defined sizes, and frequency-based chunking. Chunk-level deduplication identifies redundancy at a finer granularity than file-level deduplication and is generally more efficient, though it requires an effective chunking algorithm to maximize deduplication benefits.
IJET-V2I6P33



IJET-V2I6P33IJET - International Journal of Engineering and Techniques Privacy preserving is the essential aspect for cloud. In privacy preserving ranked keyword search, data
owner outsource the document in an encrypted form. So for privacy purpose, Reliable ciphertext search technique
is essentially. To design ciphertext search technique which provide encrypted document is critical task. In this
paper, hierarchical clustering method is designed for semantic search and fast ciphertext search within a big data
environment. In hierarchical clustering, documents are based on maximum relevance score and clusters are divided
into sub-clusters.
panda public auditing for shared data with efficient user revocation in the c...



panda public auditing for shared data with efficient user revocation in the c...swathi78 LOGIC SYSTEMS
1st Floor, Reddy Comlex, Opp. SPencers, Near Satyam Theatre, Ameerpet, Hyderabad
9533694296,9703109334
[email protected]
www.logicsystems.org.in
Is2215 lecture7 lecturer_ado_intro



Is2215 lecture7 lecturer_ado_introdannygriff1 This document discusses ADO.NET and how it can be used to interact with databases in Visual Basic.NET. ADO.NET uses a disconnected data model that allows applications to query databases without maintaining an open connection. It keeps a local copy of queried data in a dataset object. The main components of ADO.NET - connection, command, data adapter, and dataset - are introduced. Code examples are provided to demonstrate connecting to an Access database and retrieving, displaying, and navigating records using ADO.NET.
A secure erasure code based cloud storage



A secure erasure code based cloud storageIMPULSE_TECHNOLOGY For further details contact:
N.RAJASEKARAN B.E M.S 9841091117,9840103301.
IMPULSE TECHNOLOGIES,
Old No 251, New No 304,
2nd Floor,
Arcot road ,
Vadapalani ,
Chennai-26.
Final 1st



Final 1stgokulprema The document proposes a system for multi-keyword ranked search over encrypted cloud data while preserving privacy. It addresses limitations in previous systems that allowed single keyword search or did not consider privacy. The proposed system uses asymmetric key encryption, a block-max index, and dynamic key generation to allow efficient retrieval of relevant encrypted data from the cloud without security breaches. It involves three parts: (1) a server that encrypts and stores data in the cloud and sends decryption keys; (2) a cloud server that handles search requests, ranks results, and responds; and (3) users that request data from the cloud server.
Methodology for Optimizing Storage on Cloud Using Authorized De-Duplication –...



Methodology for Optimizing Storage on Cloud Using Authorized De-Duplication –...IRJET Journal This document summarizes a research paper that proposes a methodology for optimizing storage on the cloud using authorized de-duplication. It discusses how de-duplication works to eliminate duplicate data and optimize storage. The key steps are chunking files into blocks, applying secure hash algorithms like SHA-512 to generate unique hashes for each block, and comparing hashes to reference duplicate blocks instead of storing multiple copies. It also discusses using cryptographic techniques like ciphertext-policy attribute-based encryption for authentication and security on public clouds. The proposed approach aims to optimize storage while providing authorized de-duplication functionality.
A Hybrid Cloud Approach for Secure Authorized Deduplication



A Hybrid Cloud Approach for Secure Authorized Deduplication1crore projects - The document proposes a new deduplication system that supports differential or authorized duplicate checking in a hybrid cloud architecture consisting of a public and private cloud. This allows users to securely check for duplicates of files based on their privileges.
- Convergent encryption is used to encrypt files for deduplication while maintaining confidentiality. A new construction is presented that additionally encrypts files with keys derived from user privileges to enforce access control during duplicate checking.
- The system aims to efficiently solve the problem of deduplication with access control in cloud computing. It allows duplicate checking of files marked with a user's corresponding privileges to realize access control while preserving benefits of deduplication.
Access control in decentralized online social networks applying a policy hidi...



Access control in decentralized online social networks applying a policy hidi...IGEEKS TECHNOLOGIES The document proposes a policy-hiding cryptographic scheme for access control in decentralized online social networks that aims to achieve both privacy and performance. Existing DOSNs reveal access policies but some cryptographic variants hide policies at the cost of performance. The proposed scheme uses predicate encryption with a univariate polynomial construction for access policies that drastically improves performance while leaking some policy information. Bloom filters are also used to decrease decryption time and indicate decryptable objects. The goal is to enable privacy-preserving access control without compromising usability in resource-constrained DOSN environments.
IEEE 2014 JAVA MOBILE COMPUTING PROJECTS Preserving location privacy in geo s...



IEEE 2014 JAVA MOBILE COMPUTING PROJECTS Preserving location privacy in geo s...IEEEFINALYEARSTUDENTPROJECTS
Viewers also liked (9)
In memory databases presentation



In memory databases presentationMichael Keane This document provides an overview of in-memory databases, summarizing different types including row stores, column stores, compressed column stores, and how specific databases like SQLite, Excel, Tableau, Qlik, MonetDB, SQL Server, Oracle, SAP Hana, MemSQL, and others approach in-memory storage. It also discusses hardware considerations like GPUs, FPGAs, and new memory technologies that could enhance in-memory database performance.
In-Memory DataBase



In-Memory DataBasePridhvi Kodamasimham In-memory databases (IMDBs) store data primarily in RAM for faster access than disk-based databases. While an older concept, IMDBs have become more practical due to lower RAM costs, multi-core CPUs, and 64-bit systems allowing more memory. IMDBs have different architectures, data representations, indexing, and query processing optimized for memory versus disk. They also face challenges in providing durability without disk and scaling to very large data sizes.
In-Memory Database Platform for Big Data



In-Memory Database Platform for Big DataSAP Technology SAP HANA is an in-memory database and platform that allows for real-time analytics on large datasets. It utilizes columnar storage, massive parallelization across cores and servers, and in-memory computing to enable interactive queries and analysis of big data without the latency of disk access. SAP HANA provides a single system for both transaction processing and analytics, combining structured and unstructured data on a scalable platform.
Sql Server 2008 Security Enhanments



Sql Server 2008 Security EnhanmentsEduardo Castro This document discusses features and capabilities of SQL Server 2008 including:
- Transparent data encryption to encrypt entire databases
- External key management to consolidate security keys in the data center
- Auditing to monitor data access and modifications
- Declarative management framework to automate administrative tasks
- Server group management to simplify installation, configuration and monitoring across instances
in-memory database system and low latency



in-memory database system and low latencyhyeongchae lee This document discusses in-memory database systems and high performance computing. It begins with an overview of domestic and international in-memory databases like Altibase, Oracle TimesTen, McObject ExtremeDB, and KX Systems KDB+. It then discusses the advantages of in-memory architectures for achieving ultra-low latency. The rest of the document covers technologies that enable high performance like NUMA, SSDs, InfiniBand, message queues, and complex event processing. It concludes by discussing in-memory computing and high performance computing technologies.
Sap technical deep dive in a column oriented in memory database



Sap technical deep dive in a column oriented in memory databaseAlexander Talac The document describes a lecture on column-oriented in-memory databases. The lecture covers the status quo of enterprise computing, database storage techniques like row and column storage layouts, in-memory database operators like scanning and aggregation, and advanced storage techniques like dictionary encoding and tuple reconstruction. The goal is to provide a deep technical understanding of column-oriented in-memory databases and their application in enterprise systems.
In-memory Databases



In-memory DatabasesRobert Friberg This is from a 2 hour talk introducing in-memory databases. First a look at traditional RDBMS architecture and some of it's limitations, then a look at some in-memory products and finally a closer look at OrigoDB, the open source in-memory database toolkit for NET/Mono.
Real World Use Cases and Success Stories for In-Memory Data Grids (TIBCO Acti...



Real World Use Cases and Success Stories for In-Memory Data Grids (TIBCO Acti...Kai Wähner Kai Wähner is a technical lead who discusses in-memory computing and real-world use cases. In-memory computing uses memory for data storage and processing to enable acting in real-time. It offers benefits like eventing, fault tolerance, and high performance beyond traditional caching. Examples where in-memory computing has been applied include personalized customer experiences, routing messages, handling spikes in data, and storing stateful enterprise application data.
Open API and API Management - Introduction and Comparison of Products: TIBCO ...



Open API and API Management - Introduction and Comparison of Products: TIBCO ...Kai Wähner In October 2014, I had a talk at Jazoon in Zurich, Switzerland: "A New Front for SOA: Open API and API Management as Game Changer"
Open API represent the leading edge of a new business model, providing innovative ways for companies to expand brand value and routes to market, and create new value chains for intellectual property. In the past, SOA strategies mostly targeted internal users. Open APIs target mostly external partners.
This session introduces the concepts of Open API, its challenges and opportunities. API Management will become important in many areas, no matter if business-to-business (B2B) or business-to-customer (B2C) communication. Several real world use cases will discuss how to gain leverage due to API Management. The end of the session shows and compares API management products from different vendors such as TIBCO API Exchange, IBM, Apigee, 3scale, WSO2, MuleSoft, Mashery, Layer 7, Vordel
Ad
Similar to Using In-Memory Encrypted Databases on the Cloud (20)
IRJET - A Secure Access Policies based on Data Deduplication System



IRJET - A Secure Access Policies based on Data Deduplication SystemIRJET Journal This document summarizes a research paper on a secure access policies based data deduplication system. The system uses attribute-based encryption and a hybrid cloud model with a private cloud for deduplication and a public cloud for storage. It allows defining access policies for encrypted data files. When a user uploads a duplicate file, the system checks for a matching file and replaces it with a reference to the existing copy to save storage. The system provides file and block-level deduplication for efficient storage and uses cryptographic techniques like MD5, 3DES and RSA for encryption, tagging and access control of encrypted duplicate data across clouds.
cloud computing preservity



cloud computing preservitychennuruvishnu This document discusses preserving data integrity in cloud computing through third party auditing. It introduces an effective third party auditor that can perform multiple auditing tasks simultaneously using the technique of bilinear aggregate signature. This reduces computation costs and storage overhead for integrity verification. The system supports dynamic data operations through techniques like fragment structure, random sampling and an index-hash table. It also allows efficient scheduling of audit activities in an audit period and assigns each third party auditor to audit a batch of files to save time. The system provides advantages like improved performance and reduced extra storage requirements.
Off-Label Data Mesh: A Prescription for Healthier Data



Off-Label Data Mesh: A Prescription for Healthier DataHostedbyConfluent "Data mesh is a relatively recent architectural innovation, espoused as one of the best ways to fix analytic data. We renegotiate aged social conventions by focusing on treating data as a product, with a clearly defined data product owner, akin to that of any other product. In addition, we focus on building out a self-service platform with integrated governance, letting consumers safely access and use the data they need to solve their business problems.
Data mesh is prescribed as a solution for _analytical data_, so that conventionally analytical results (think weekly sales or monthly revenue reports) can be more accurately and predictably computed. But what about non-analytical business operations? Would they not also benefit from data products backed by self-service capabilities and dedicated owners? If you've ever provided a customer with an analytical report that differed from their operational conclusions, then this talk is for you.
Adam discusses the resounding successes he has seen from applying data mesh _off-label_ to both analytical and operational domains. The key? Event streams. Well-defined, incrementally updating data products that can power both real-time and batch-based applications, providing a single source of data for a wide variety of application and analytical use cases. Adam digs into the common areas of success seen across numerous clients and customers and provides you with a set of practical guidelines for implementing your own minimally viable data mesh.
Finally, Adam covers the main social and technical hurdles that you'll encounter as you implement your own data mesh. Learn about important data use cases, data domain modeling techniques, self-service platforms, and building an iteratively successful data mesh."
My Other Computer is a Data Center: The Sector Perspective on Big Data



My Other Computer is a Data Center: The Sector Perspective on Big DataRobert Grossman This is a keynote I gave on July 25, 2010 at the 2nd Workshop on Large-scale Data Mining: Theory and Applications (LDMTA 2010).
EXPLORING WOMEN SECURITY BY DEDUPLICATION OF DATA



EXPLORING WOMEN SECURITY BY DEDUPLICATION OF DATAIRJET Journal The document proposes a new deduplication system that supports endorsed duplicate check and separates the record structure and substance. It utilizes AES calculation to encrypt information for security. MD5 and sha1 calculations are utilized to recognize duplicate records. The private cloud is outfitted with mystery validation to give more prominent security. The proposed framework separates record structure and substance and underpins endorsed duplicate check to give proficient deduplication while ensuring information security in the cloud.
Evolution from EDA to Data Mesh: Data in Motion



Evolution from EDA to Data Mesh: Data in Motionconfluent Thoughtworks Zhamak Dehghani observations on these traditional approaches’s failure modes, inspired her to develop an alternative big data management architecture that she aptly named the Data Mesh. This represents a paradigm shift that draws from modern distributed architecture and is founded on the principles of domain-driven design, self-serve platform, and product thinking with Data. In the last decade Apache Kafka has established a new category of data management infrastructure for data in motion that has been leveraged in modern distributed data architectures.
Implementing a Data Mesh with Apache Kafka with Adam Bellemare | Kafka Summit...



Implementing a Data Mesh with Apache Kafka with Adam Bellemare | Kafka Summit...HostedbyConfluent Have you heard about Data Mesh but never really understood how you actually build one? Data mesh is a relatively recent term that describes a set of principles that good modern data systems uphold. Although the data mesh is not a technology specific pattern, it requires that organizations make choices and investments into specific technologies and operational policies when implementing the mesh. Establishing ""paved roads"" for creating, publishing, evolving, deprecating, and discovering data products is essential for bringing the benefits of the mesh to those who would use it.
In this talk, Adam covers implementing a self-service data mesh with events streams in Apache Kafka®. Event streams as a data product are an essential part of a real-world data mesh, as they enable both operational and analytical workloads from a common source of truth. Event streams provide full historical data along with realtime updates, letting each individual data product consumer decide what to consume, how to remodel it, and where to store it to best suit their needs.
Adam structures this talk by seeking to answer a hypothetical SaaS business question of ""what is the relationship between feature usage and user retention?"" This example explores each team's role in the data mesh, including the data products they would (and wouldn't) publish, how other teams could use the products, and the organizational dynamics and principles underpinning it all.
Apache Kafka and the Data Mesh | Ben Stopford and Michael Noll, Confluent



Apache Kafka and the Data Mesh | Ben Stopford and Michael Noll, ConfluentHostedbyConfluent The document discusses the principles of a data mesh architecture using Apache Kafka for event streaming. It describes a data mesh as having four key principles: 1) domain-driven decentralization where each domain owns the data it creates, 2) treating data as a first-class product, 3) providing a self-serve data platform for easy access to real-time and historical data, and 4) establishing federated governance with global standards. Event streaming is presented as a good fit for data meshing due to its scalability, ability to handle real-time and historical data, and immutability. The document provides examples and recommendations for implementing each principle in a data mesh.
Computing Outside The Box September 2009



Computing Outside The Box September 2009Ian Foster Keynote talk at Parco 2009 in Lyon, France. An updated version of http://www.slideshare.net/ianfoster/computing-outside-the-box-june-2009.
Nhibernate Part 1



Nhibernate Part 1guest075fec The document discusses NHibernate, an open source object-relational mapping framework for .NET. It begins by describing some of the limitations of using ADO.NET datasets for data access and how NHibernate provides a more object-oriented approach. It then provides steps to get started with NHibernate, including configuring NHibernate, defining a domain model, mapping the domain model to database tables, and generating the necessary code.
Ensuring d.s



Ensuring d.skarthi j Cloud computing moves application software and databases to large data centers where management may not be fully trustworthy, posing security challenges. The article focuses on cloud data storage security and proposes a scheme using erasure-coded data with distributed verification and error localization to identify misbehaving servers. Unlike prior works, the scheme supports secure dynamic operations like update, delete and append. Extensive analysis shows it efficiently protects against attacks while supporting data dependencies and dynamics.
ISBG 2015 - Infrastructure Assessment - Analyze, Visualize and Optimize



ISBG 2015 - Infrastructure Assessment - Analyze, Visualize and OptimizeChristoph Adler This document summarizes a presentation on assessing and optimizing IBM Notes infrastructures. It discusses analyzing user activity data to understand infrastructure usage and prioritize optimization efforts. Key factors like network setup, hardware, applications, and security are reviewed. Specific optimization techniques for client landscapes are presented, like migrating to newer On Disk Structure formats, using multi-user installs, and automating workspace directory setup. Visualizing infrastructure and activity data is presented as an effective way to make informed decisions about consolidation and transformation projects. The presentation aims to provide best practices for assessing Notes infrastructures holistically to support strategic planning.
Secured Authorized Deduplication Based Hybrid Cloud



Secured Authorized Deduplication Based Hybrid Cloudtheijes The International Journal of Engineering & Science is aimed at providing a platform for researchers, engineers, scientists, or educators to publish their original research results, to exchange new ideas, to disseminate information in innovative designs, engineering experiences and technological skills. It is also the Journal's objective to promote engineering and technology education. All papers submitted to the Journal will be blind peer-reviewed. Only original articles will be published.
The papers for publication in The International Journal of Engineering& Science are selected through rigorous peer reviews to ensure originality, timeliness, relevance, and readability.
Theoretical work submitted to the Journal should be original in its motivation or modeling structure. Empirical analysis should be based on a theoretical framework and should be capable of replication. It is expected that all materials required for replication (including computer programs and data sets) should be available upon request to the authors.
The International Journal of Engineering & Science would take much care in making your article published without much delay with your kind cooperation
DATA SECURITY IN CLOUD USING BLOWFISH ALGORITHM



DATA SECURITY IN CLOUD USING BLOWFISH ALGORITHMijsrd.com Cloud computing is computing in which large groups of remote servers are networked to allow centralized data storage and online access to computer services or resources. The strives of environment is dynamic, customizable and reliable with the quality of services. Security issues in the cloud as it is anywhere else. Lots of people share different point of views in cloud computing. Some of the people believe that it is unsafe to use Cloud Computing .Clouds can be classified as public, private or hybrid. This paper handle security issue in cloud using blowfish algorithm.
Mongodb



MongodbThiago Veiga MongoDB is an open-source document database that provides high performance, high availability, and automatic scaling. It stores data in flexible, JSON-like documents, enabling storage of data with complex relationships easily and supporting polyglot persistence. MongoDB can be used for applications such as content management systems, user profiles, logs, and more. It provides indexing, replication, load balancing and aggregation capabilities.
Designing a Scalable Twitter - Patterns for Designing Scalable Real-Time Web ...



Designing a Scalable Twitter - Patterns for Designing Scalable Real-Time Web ...Nati Shalom Twitter is a good example for next generation real-time web applications, but building such an application imposes challenges such as handling an every growing volume of tweets and responses, as well as a large number of concurrent users, who continually *listen* for tweets from users (or topics) they follow. During this session we will review some of the key design principles addressing these challenges, including alternatives *NoSQL* alternatives and blackboard patterns. We will be using Twitter as a use case, while learning how to apply these to any real-time we application
Google Cloud Computing on Google Developer 2008 Day



Google Cloud Computing on Google Developer 2008 Dayprogrammermag The document discusses the evolution of computing models from clusters and grids to cloud computing. It describes how cluster computing involved tightly coupled resources within a LAN, while grids allowed for resource sharing across domains. Utility computing introduced an ownership model where users leased computing power. Finally, cloud computing allows access to services and data from any internet-connected device through a browser.
Essay On Active Directory



Essay On Active DirectoryTammy Moncrief Active Directory (AD) is a database management system created by Microsoft that stores information about network components. It allows administrators to manage policies, accounts, programs and updates across a network. AD replaced Windows NT's domain model and provided greater scalability than previous Windows versions. The LDAP directory service protocol was developed to provide a standard way to access directories over a network. It led to the development of directory server software like Microsoft Active Directory that could be implemented by various clients and vendors. Windows NT was a powerful and secure operating system that supported multiple file systems and architectures. It provided user accounts and identity-based security where users could only access resources with the proper authenticated password for their account. Database security involves restricting access to tables and authenticating
Database-management-system-dbms-ppt.pptx



Database-management-system-dbms-ppt.pptxsqlserver4 A database management system (or DBMS) is essentially nothing more than a computerized data-keeping system. Users of the system are given facilities to perform several kinds of operations on such a system for either manipulation of the data in the database or the management of the database structure itself.
Cloud C



Cloud CRamin Rastin ✮✮✮✮✮ Despite rumours to the contrary, a private cloud model offers a secure data repository that is protected by cast iron service guarantees (and if your service provider can’t provide them – consider looking elsewhere), which can either be used as a standalone option or integrated within existing client infrastructure to form a hybrid solution
Ad
Recently uploaded (20)
How to Create A Todo List In Todo of Odoo 18



How to Create A Todo List In Todo of Odoo 18Celine George In this slide, we’ll discuss on how to create a Todo List In Todo of Odoo 18. Odoo 18’s Todo module provides a simple yet powerful way to create and manage your to-do lists, ensuring that no task is overlooked.
pulse ppt.pptx Types of pulse , characteristics of pulse , Alteration of pulse



pulse ppt.pptx Types of pulse , characteristics of pulse , Alteration of pulsesushreesangita003 what is pulse ?
Purpose
physiology and Regulation of pulse
Characteristics of pulse
factors affecting pulse
Sites of pulse
Alteration of pulse
for BSC Nursing 1st semester
for Gnm Nursing 1st year
Students .
vitalsign
How to Configure Public Holidays & Mandatory Days in Odoo 18



How to Configure Public Holidays & Mandatory Days in Odoo 18Celine George In this slide, we’ll explore the steps to set up and manage Public Holidays and Mandatory Days in Odoo 18 effectively. Managing Public Holidays and Mandatory Days is essential for maintaining an organized and compliant work schedule in any organization.
Ajanta Paintings: Study as a Source of History



Ajanta Paintings: Study as a Source of HistoryVirag Sontakke This Presentation is prepared for Graduate Students. A presentation that provides basic information about the topic. Students should seek further information from the recommended books and articles. This presentation is only for students and purely for academic purposes. I took/copied the pictures/maps included in the presentation are from the internet. The presenter is thankful to them and herewith courtesy is given to all. This presentation is only for academic purposes.
Bridging the Transit Gap: Equity Drive Feeder Bus Design for Southeast Brooklyn



Bridging the Transit Gap: Equity Drive Feeder Bus Design for Southeast Brooklyni4jd41bk Group presentation of a feasibility and cost benefit study for a proposed bus service in Southeastern Brooklyn, New York.
Myopathies (muscle disorders) for undergraduate



Myopathies (muscle disorders) for undergraduateMohamed Rizk Khodair herediatary myopthies
myotonia
inflammatory myopthies
How to Create Kanban View in Odoo 18 - Odoo Slides



How to Create Kanban View in Odoo 18 - Odoo SlidesCeline George The Kanban view in Odoo is a visual interface that organizes records into cards across columns, representing different stages of a process. It is used to manage tasks, workflows, or any categorized data, allowing users to easily track progress by moving cards between stages.
Form View Attributes in Odoo 18 - Odoo Slides



Form View Attributes in Odoo 18 - Odoo SlidesCeline George Odoo is a versatile and powerful open-source business management software, allows users to customize their interfaces for an enhanced user experience. A key element of this customization is the utilization of Form View attributes.
Herbs Used in Cosmetic Formulations .pptx



Herbs Used in Cosmetic Formulations .pptxRAJU THENGE The content is for the educational purpose for Pharmacy and Cosmetic students.
PHYSIOLOGY MCQS By DR. NASIR MUSTAFA (PHYSIOLOGY)



PHYSIOLOGY MCQS By DR. NASIR MUSTAFA (PHYSIOLOGY)Dr. Nasir Mustafa PHYSIOLOGY MCQS By DR. NASIR MUSTAFA (PHYSIOLOGY)
SCI BIZ TECH QUIZ (OPEN) PRELIMS XTASY 2025.pptx



SCI BIZ TECH QUIZ (OPEN) PRELIMS XTASY 2025.pptxRonisha Das SCI BIZ TECH QUIZ (OPEN) PRELIMS - XTASY 2025
spinal cord disorders (Myelopathies and radiculoapthies)



spinal cord disorders (Myelopathies and radiculoapthies)Mohamed Rizk Khodair Myelopathies
Radiculopathies
Real GitHub Copilot Exam Dumps for Success



Real GitHub Copilot Exam Dumps for SuccessMark Soia Download updated GitHub Copilot exam dumps to boost your certification success. Get real exam questions and verified answers for guaranteed performance
How to Add Customer Note in Odoo 18 POS - Odoo Slides



How to Add Customer Note in Odoo 18 POS - Odoo SlidesCeline George In this slide, we’ll discuss on how to add customer note in Odoo 18 POS module. Customer Notes in Odoo 18 POS allow you to add specific instructions or information related to individual order lines or the entire order.
How to Configure Scheduled Actions in odoo 18



How to Configure Scheduled Actions in odoo 18Celine George Scheduled actions in Odoo 18 automate tasks by running specific operations at set intervals. These background processes help streamline workflows, such as updating data, sending reminders, or performing routine tasks, ensuring smooth and efficient system operations.
APGAR SCORE BY sweety Tamanna Mahapatra MSc Pediatric



APGAR SCORE BY sweety Tamanna Mahapatra MSc PediatricSweetytamannaMohapat Learn about the APGAR SCORE , a simple yet effective method to evaluate a newborn's physical condition immediately after birth ....this presentation covers .....
what is apgar score ?
Components of apgar score.
Scoring system
Indications of apgar score........
All About the 990 Unlocking Its Mysteries and Its Power.pdf



All About the 990 Unlocking Its Mysteries and Its Power.pdfTechSoup In this webinar, nonprofit CPA Gregg S. Bossen shares some of the mysteries of the 990, IRS requirements — which form to file (990N, 990EZ, 990PF, or 990), and what it says about your organization, and how to leverage it to make your organization shine.
Ranking_Felicidade_2024_com_Educacao_Marketing Educacional_V2.pdf



Ranking_Felicidade_2024_com_Educacao_Marketing Educacional_V2.pdfRafael Villas B Marketing Educacional
Using In-Memory Encrypted Databases on the Cloud
- 1. Using In-Memory Encrypted Databases on the Cloud Francesco (and Davide) Pagano [email_address] Department of Information Technology Università degli Studi di Milano - Italy
- 2. Agenda Privacy issue on the cloud An agent based approach Database encryption In Memory Databases and HyperSql Our solution Benchmarking Conclusion Question time
- 3. Access control problem Cloud Platform Desktop Desktop controlled accesses for external users uncensored access for cloud provider
- 4. Privacy within the cloud: on the same side of the wall Presentation Layer privacy Data Layer performance
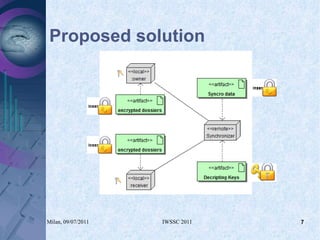
- 5. An agent-based approach Untrusted Synchronizer never holds plaintext data Local agent with local db
- 6. The model
- 8. Database encryption * L. Bouganim and Y. Guo, “Database encryption,” in Encyclopedia of Cryptography and Security, Springer, 2010, 2nd Edition
- 9. Granularity in database-level encryption database tables columns rows
- 10. In Memory Databases “ An in-memory database (IMDB also known as main memory database system or MMDB and as real-time database or RTDB) is a database management system that primarily relies on main memory for computer data storage.” * Wikipedia
- 11. HyperSql
- 12. Loader
- 13. Insert
- 14. Serializer
- 15. .script file of a sample database CREATE SCHEMA PUBLIC AUTHORIZATION DBA CREATE MEMORY TABLE DOSSIER(ID INTEGER GENERATED BY DEFAULT AS IDENTITY(START WITH 0) NOT NULL PRIMARY KEY,NAME CHAR(80)) CREATE MEMORY TABLE STUDENTS(ID INTEGER GENERATED BY DEFAULT AS IDENTITY(START WITH 0) NOT NULL PRIMARY KEY,NAME CHAR(80)) ALTER TABLE DOSSIER ALTER COLUMN ID RESTART WITH 0 ALTER TABLE STUDENTS ALTER COLUMN ID RESTART WITH 32 CREATE USER SA PASSWORD "" GRANT DBA TO SA SET WRITE_DELAY 10 SET SCHEMA PUBLIC INSERT INTO STUDENTS VALUES(12,'Alice') INSERT INTO STUDENTS VALUES(31,'Bob')
- 16. Implemented solution: client side On the client side, using IMDBs, we have only two interactions between each local agent and the Synchronizer
- 17. The modified .script file INSERT INTO students(id,name) VALUES(12,'Alice'); INSERT INTO students(id,name) VALUES(31,'Bob'); $27@5F3C25EE5738DAAAED5DA06A80F305A93C95A $45@5DA67ADA06AAED580FA914BF3C953057D387F INSERT INTO students(id,name) VALUES(23,'Carol'); Encrypted rows id_pending_row
- 20. The synchronizer
- 21. Performances In contrast to the usual row-level encryption, which needs encryption/decryption at every data access, our solution uses these heavy operations only when communicating with Synchronizer, with a clear advantage, especially in the case of rarely modified databases.
- 22. Performances: read operations The system uses decryption only at start time, when records are loaded from the disk into the main memory. Each row is decrypted none (if it is owned by local node) or just once (if it is owned by a remote node), so this is optimal for read operations. Each decryption implies an access to the remote Synchronizer to download the related decrypting key and, eventually, the modified row.
- 23. Performances: write operations Write operations occur when a record is inserted / updated into the db, with no overload until the client, when online, explicitly synchronizes data with the central server. At this moment, for each modified record, the client needs to: • generate a new (symmetric) key • encrypt the record • dispatch the encrypted data and the decrypting key to the remote synchronizer
- 24. Benchmark (1) Creation of database and sample tables Population of tables with sample values Sharing of a portion of data with another user Receipt of shared dossiers from other users Opening of the newly created (and populated) database
- 25. Benchmark (2) To minimize communication delay, the central Synchronizer and the clients ran on the same computer. For testing purpose, it was sufficient to use only two clients (to enable data sharing). The application was compared with an equivalent one having the following differences: • It uses the unmodified HyperSQL driver • It doesn’t share data with other clients • When populating the database, it creates the same number of dossiers than the previous application; after benchmarking, however, it adds the number of shared dossiers, resulting in the same final number of dossiers.
- 26. Benchmark (3) We benchmarked the system using single-table dossiers of about 200 bytes, in two batteries of tests; the first with 20%, and the second with 40% of shared dossiers, which numbered from 1,000 to 500,000.
- 27. Results (1) Overhead when 20% of dossiers are shared
- 28. Results (2) Overhead when 40% of dossiers are shared
- 29. Results (3) Total delay
- 30. Conclusion In this paper, using IMDBs, we presented a simple solution to row-level encryption of databases. It can be used in the cloud to manage very granular access rights in a highly distributed database. This allows for stronger confidence in the privacy of shared sensitive data. An interesting field of application is the use in (business) cooperative environments, e.g. professional networks. In these environments, privacy is a priority, but low computing resources don't allow the use of slow and complex algorithms. IMDBs and our smart encryption, instead, achieve the goal in a more effective way.
- 31. Questions
Editor's Notes
- #2: My name is Francesco Pagano and I come from University of Milan – Italy. Today, I present the paper “Handling Confidential Data on the Untrusted Cloud: an agent-based approach”, written with Prof. Ernesto Damiani from the same university.
- #3: The agenda of my speech: First, I'll analyze the issue of privacy in cloud computing, showing some classical solutions from literature. Then, I'll show an intrinsic problem that clears the effort of those solutions. Followed by a detailed presentation of our solution. Finally, it will be “question time”.
- #4: In cloud computing there is a clear distinction between the Platform, hosted in the cloud, and the clients, distributed in Internet. The clients access the outsourced data, stored in the Platform via applications, in the Cloud too. External user identification and access control are very well studied and diffused, so that EXTERNAL malicious users are easily stopped. But what about internal access? We don't want that Cloud Providers have access to our sensitive data!
- #5: The previous techniques ensure outsourced data integrity, but this is not enough since the data has a long way to go after the data layer. In a Java application, for example, it passes through JDBC, Hibernate, and so on, up to presentation layer. And at that level, certainly, data is clear text. An attacker can attack one of the weakest levels, for example, using aspect programming. <Click> So, for privacy, we have to move “presentation layer” to client side <click> but now data and presentation are divided. If we want performance <click> we have to move also data to client side <click>.
- #6: And this is our proposal. We suggest to atomize the couple application/database, providing a copy per user. Every instance runs locally, and maintains only authorized data that is replicated and synchronized among all authorized users. A centralized node hosts an untrusted Synchronizer which never holds plain-text data.
- #7: Each user has a local copy of his data. We use the term dossier to indicate a group of correlated informations such as a medical record or a court file. If 2 users can access the same dossier, each of them has a copy of the dossier. We suppose that only one user (called “the owner”) can modify the dossier.
- #8: The local nodes synchronize that data by a central repository that stores the updated records. To prevent this synchronizer to access the data, it is encrypted. The decryption keys, protected in the way that we will see later, are also stored into the synchronizer.
- #32: This is all. If you have any question...


