Using Machine-Learning to Investigate Web Campaigns at Large - HITB 2018
- 1. Using Machine-Learning to Investigate Web Campaigns at Large 2nd Nov 18 JD-HITB PEK Beijing, China Dr. Marco Balduzzi @embyte, madlab.it
- 2. Who am I? ● HITB aficionado ● Computer security geek (since 2002) ● Love research, Ph.D. (in 2011) ● “Community centric” ● Work for Trend Micro
- 3. Web Defacement = Website Compromise + Homepage Hijacking
- 4. 90s 2000 2010 Now “Just-for-fun” era Digital activism Geopolitical factors kick in Dark propaganda Evolution
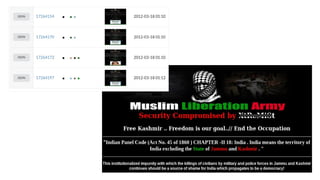
- 8. Coordinated campaigns: From one to many targets ● Death statement is 2nd of May 2011 ● Campaign is 6th-12th of May ● Targets:
- 10. Data Collection
- 12. Others
- 13. THE site :)
- 14. Collected Data Source Name Website URL Acquired Records Zone-H www.zone-h.org 12,303,240 Hack-CN www.hack-cn.com 386,705 Mirror Zone www.mirror-zone.org 195,398 Hack Mirror www.hack-mirror.com 68,980 MyDeface www.mydeface.com 37,843 TOTAL 12,992,166
- 17. Data Trustworthiness Type Attribute Example Trustworthiness Metadata URL http://target.gov High Timestamp 2010-01-02 15:00 Medium Nickname Neo Hacker Medium-Low Webserver; Reason; Hack Mode Nginx; Political; SQLi Low Raw content Main page HTML or TXT file High Embeeded resources Various format High External resources Various format Medium-High
- 18. General Trends
- 19. Topics Over The Years Security Problems Real World Events
- 20. Adoption of Malicious Content
- 21. Adoption of email & Twitter handlers
- 23. Key Observations
- 25. Key Observations 1.Actors cooperate in teams Especially if driven by strong ideologies 2.Defacements are organized around campaigns 3.When a team prepares and runs a campaign, it tends to re-use a common template that each member can customize
- 26. Next Generation* Defacement Explorer (DefPloreX-NG) (*) 1st generation presented at BH Arsenal
- 30. Riga 1 Riga 2 Riga 3 Riga 4 0 2 4 6 8 10 12 Colonna 1 Colonna 2 Colonna 3 Pre-Filtering Search Campaigns Search The Indo-Pakistani conflict
- 33. Features Engineering Visual Features (images) Social Features Structural Features Format of Title Visual Features (colors)
- 34. Features Engineering Multimedia URLs Email Addresses
- 35. Clustering ● BIRCH – Balanced Iterative Reducing and Clustering Hierarchies ● Do not materialize the entire distance matrix – Statistical values are efficient to compute – Quickly find the closest cluster for each new data points
- 36. Clustering ● Scalability of BIRCH vs. DBSCAN (10 runs)
- 37. Labeling ● Each cluster is represented by a succinct report – Time span – Screenshot thumbnails (by perceptual hash) – Name of actors and teams – Keywords used in campaigns (e.g. #opfrance) – Category of targets (e.g, news, governmental sites)
- 38. Findings
- 39. Organization of Actors 43% of actors join one team, at least 70% of campaigns do collaborate Half of joint campaigns are larger than 3
- 40. Geopolitical Real-World Events ● Successfully detected
- 41. The “Charlie Hebdo” case
- 42. The “Charlie Hebdo” case Campaigns Teams Actors
- 44. The Israeli-Palestinian conflict Example of large-scale joint campaigns. While the entire Israeli- Palestinian conflict involves 12 campaigns, opisreal and opsavealaqsa represent the most aggressive and active ones.
- 45. Anonymous Operations Joint campaigns conducted by anonymous-affiliated groups against governmental sites.
- 46. Long-Term vs. Aggressive Campaigns Campaign savegaza reacted to war events in the Gaza Strip
- 47. Example of a long-running campaign named h4ck3rsbr. The horizontal bars represent the different sub-campaigns (60) with their most targeted TLDs and teams (next slide). This is a very generic campaign, with different affiliates.
- 49. Conclusions ● Dark propaganda ● Prevailing phenomenon ● Driven by geopolitical motivations ● Key targets, influencing sites ● Contribute to make the Internet a better world!
- 50. Conclusions ● DefPloreX-NG ● GitHub (old code, new ask): https://github.com/trendmicro/defplorex ● Paper*: https://documents.trendmicro.com/assets/wp/ wp-web-defacement-campaigns-uncovered- gaining-insights-from-deface-pages-using- defplorex-ng.pdf (*) Joint work with Federico Maggi, Ryan Flores, Lion Gu and Vincenzo Ciancaglini
- 51. Thanks! Questions? Dr. Marco Balduzzi @embyte, madlab.it