Synopsys Security Event Israel Presentation: Value Driven Threat Modeling
1 like185 views
Avi Douglen, Software Security Advisor, Bounce Security presented at the Synopsys Security Event - Israel. For more information please visit us at www.synopsys.com/software
1 of 40
Download to read offline







































Ad
Recommended
Value-driven threat modeling: Security by design - Avi Douglen - DevOpsDays T...



Value-driven threat modeling: Security by design - Avi Douglen - DevOpsDays T...DevOpsDays Tel Aviv Threat Modeling is a great method to identify potential security flaws, part of any secure design. But instead of investing time + budget in a top-heavy, big-model-up-front threat modeling methodology, we can use a lightweight value-driven approach to embed security right into the agile dev process!
DevSecCon Tel Aviv 2018 - Value driven threat modeling by Avi Douglen



DevSecCon Tel Aviv 2018 - Value driven threat modeling by Avi DouglenDevSecCon This document discusses value-driven threat modeling, a lightweight approach to threat modeling that prioritizes security based on business value. It advocates for developers to integrate threat modeling into their workflow by focusing on the core questions of what is being built, what could go wrong, how to address issues, and ensuring quality. Specific techniques discussed include using acceptance criteria, security unit tests, abuser stories, and a threat pyramid. The approach aims to make threat modeling quicker and more natural for developers while still addressing important security risks. Some limitations are that it may miss threats and relies on developer experience, requiring an embedded security champion for complex systems.
Managing Application Security Risk in Enterprises - Thoughts and recommendations



Managing Application Security Risk in Enterprises - Thoughts and recommendationsThierry Zoller Application risk management in enterprises - thoughts and recommendations. Privacy by Design, Security by Design
Threat modelling(system + enterprise)



Threat modelling(system + enterprise)abhimanyubhogwan Link to Youtube video: https://youtu.be/OJMqMWnxlT8
You can contact me at [email protected]
My linkdin id : https://www.linkedin.com/in/abhimanyu-bhogwan-cissp-ctprp-98978437/
Threat Modeling(system+ enterprise)
What is Threat Modeling?
Why do we need Threat Modeling?
6 Most Common Threat Modeling Misconceptions
Threat Modelling Overview
6 important components of a DevSecOps approach
DevSecOps Security Best Practices
Threat Modeling Approaches
Threat Modeling Methodologies for IT Purposes
STRIDE
Threat Modelling Detailed Flow
System Characterization
Create an Architecture Overview
Decomposing your Application
Decomposing DFD’s and Threat-Element Relationship
Identify possible attack scenarios mapped to S.T.R.I.D.E. model
Identifying Security Controls
Identify possible threats
Report to Developers and Security team
DREAD Scoring
My Opinion on implementing Threat Modeling at enterprise level
The Principles of Secure Development - BSides Las Vegas 2009



The Principles of Secure Development - BSides Las Vegas 2009Security Ninja The Principles of Secure Development by David Rook at the SecurityBSides Las Vegas conference in 2009.
BlueHat v18 || Go build a tool - best practices for building a robust & e...



BlueHat v18 || Go build a tool - best practices for building a robust & e...BlueHat Security Conference Everett Maus, Microsoft
As shipping cycles accelerate, the only way that security teams will be able to continue to enforce a consistent security bar on shipping code and prevent obvious (or less obvious) regressions is writing tools that can detect security issues--in short, security tools are key part of DevSecOps. However, there are plenty of common pitfalls that hamper security tool rollouts, preventing them from being successful.
In this talk, we'll cover types of tools you can build to help developers ship secure code, and then dig into best practices (and worst practices) for shipping tools to large developer organizations--referencing industry papers, academic studies, and experiences from various successful (and less successful) Microsoft tooling efforts.
This talk is aimed at security experts curious about tool development or considering developing their first tools. Existing security tool developers may find some parts of it interesting, but much of it rudimentary--we won't be covering new techniques for static analysis or revolutionary new fuzzing strategies.
Threat Modeling to Reduce Software Security Risk



Threat Modeling to Reduce Software Security RiskSecurity Innovation Learn about threat modeling from our CTO and co-creator of the DREAD threat modeling classification, Jason Taylor. Understand more about what threat modeling is, dive into real life examples, and use techniques you can leverage at every phase of the SDLC.
DevSecCon London 2017: Threat modeling in a CI environment by Steven Wierckx



DevSecCon London 2017: Threat modeling in a CI environment by Steven WierckxDevSecCon Threat modeling can be challenging in agile environments where processes need to be lightweight and adaptable. The presentation discusses the OWASP STAYPUFT methodology for integrating threat modeling into agile development. It involves three phases - ascertain threats from user stories, identify threats to components, and select mitigations from common controls. Examples are given for how threat modeling can be incorporated into scrum and kanban processes by updating diagrams and assumptions during planning and reviews. The goal is to perform threat modeling iteratively to keep security risks understood and addressed throughout development.
Threat Modeling - Locking the Door to Vulnerabilities



Threat Modeling - Locking the Door to VulnerabilitiesSecurity Innovation Did you lock the door before leaving your house this morning? If you did, you threat modeled without even realizing it. Threat modeling is identifying potential threats (house robbery) and implementing measures to mitigate the risk (locking your door).
Protecting valuable assets, no matter if personal assets or business-related assets such as the software you are developing, threat modeling should become an instinctual and necessary part of your process.
Our talk highlights how nearly 50% of security flaws can be mitigated through threat modeling. We help you prevent and mitigate risks by utilizing a reliable and hard-hitting analysis technique that can be applied to individual applications or across an entire portfolio. We show you how to effectively apply these techniques at the start of the design phase and throughout every phase of the development lifecycle so you can maximize the ROI of your security efforts.
Topics covered include:
• Threat Modeling 101
• The propagating effect of poor design
• Tabletop exercise – a world with and without threat modeling
• Best practices and metrics for every stakeholder
OWASP based Threat Modeling Framework



OWASP based Threat Modeling FrameworkChaitanya Bhatt Creating a custom Threat Modeling feedback model in an agile environment.
Youtube : https://www.youtube.com/watch?v=pXr75ufG1uM
Ryan Elkins - Simple Security Defense to Thwart an Army of Cyber Ninja Warriors



Ryan Elkins - Simple Security Defense to Thwart an Army of Cyber Ninja WarriorsRyan Elkins The document provides guidance on implementing simple yet effective security defenses to thwart cyber attacks. It recommends building security programs with key components like policies, baselines, risk acceptance models and checklists for application security reviews. Specific defenses include user awareness training, least privileged access, patching, network segmentation, input validation, logging and encryption. The document argues that with the right foundations, organizations do not need large budgets for security and can prevent common hacking techniques.
DevSecOps : an Introduction



DevSecOps : an IntroductionPrashanth B. P. DevSecOps is a cultural change that incorporates security practices into software development through people, processes, and technologies. It aims to address security without slowing delivery by establishing secure-by-design approaches, automating security tools and processes, and promoting collaboration between developers, security engineers, and operations teams. As software and connected devices continue proliferating, application security must be a central focus of the development lifecycle through a DevSecOps methodology.
Security Checkpoints in Agile SDLC



Security Checkpoints in Agile SDLCRahul Raghavan Product Engineering teams have started to realize the importance of software security. This has resulted in the trend where teams are taking efforts to include it as part of their software development life cycle; as opposed to treating it as another item in their checklist prior to release. However, the real challenge is in trying to find the balance between agility and quality which is where many team find this an uphill task.
While there is no golden standard when it comes to implementing software security, product teams should focus on bringing about systematic and cultural practices within their teams. This should help them to bring about the required efficiency to enable software security as a market differentiator.
This slide-deck on Software Security Initiative focuses on translating a plan of action into sustainable activities as part of the secure software development life cycle that can be adopted by engineering teams. The slides will delve deep into aspects like identifying and designing security checkpoints in the SDLC alongside concepts such as Threat Modelling in Agile, AppSec Toolchain and Security Regressions.
This was presented as a we45 Webinar on April 12, 2018
An Introduction to Secure Application Development



An Introduction to Secure Application DevelopmentChristopher Frenz The document discusses application security best practices. It notes that 60% of internet attacks target web applications, with SQL injection and XSS making up 80% of vulnerabilities. It recommends that security be incorporated throughout the entire software development lifecycle, from requirements to testing. Key steps include threat modeling, secure coding practices, code reviews, fuzz testing and penetration testing. Ongoing maintenance is also important.
Threat modelling & apps testing



Threat modelling & apps testingAdrian Munteanu The document discusses threat modeling and application security testing. It begins by noting a lack of secure coding knowledge among developers and testers. It then uses an analogy comparing building applications to building cars, noting many similarities in unsecure practices. This is followed by sections on vulnerabilities versus security, common application vulnerabilities, and industry solutions. The document concludes by discussing threat modeling and provides an example using the OWASP Threat Dragon tool.
"Threat Model Every Story": Practical Continuous Threat Modeling Work for You...



"Threat Model Every Story": Practical Continuous Threat Modeling Work for You...Izar Tarandach How to do threat modeling in the age of Agile and DevOps. A practical methodology for teams focusing on developers. Also, an introduction to PyTM as a tool for threat-modeling-with-code.
Threat Modeling Lessons From Star Wars



Threat Modeling Lessons From Star WarsAdam Shostack Everyone knows you ought to threat model, but in practical reality it turns out to be tricky. If past efforts to threat model haven't panned out, perhaps part of the problem is confusion over what works, and how the various approaches conflict or align. This talk captures lessons from years of work helping people throughout the software industry threat model more effectively. It's designed to help security pros, developers and systems managers, all of whom will leave with both threat modeling lessons from Star Wars and a proven foundation, enabling them to threat model effectively.
NTXISSACSC2 - Threat Modeling Part 1 - Overview by Brad Andrews



NTXISSACSC2 - Threat Modeling Part 1 - Overview by Brad AndrewsNorth Texas Chapter of the ISSA Brad Andrews, CEO, RBA Communications
Threat Modeling Overview
This session will cover the basic elements of threat modeling, looking at what it does and why it is important. The goal is to provide a high level overview of the process and the use of things like data flow diagrams to look for trust boundaries attacks may come across. We will go through some common threats and hopefully a list of dangers to watch out for when carrying out threat modeling. The session will then work to interactively develop a flow diagram of Amazon.com and possibly another subject if we have time. This will all be based on looking at the system as a user, without any insider knowledge, though Threat Modeling is normally carried out by those who do know the system well.
SC conference - Building AppSec Teams



SC conference - Building AppSec TeamsDinis Cruz This document discusses building application security teams. It begins by introducing the author and their background in application security. It then discusses creating an environment where security enables business goals rather than hinders them. It suggests embedding security into culture by focusing on quality, testing, and engineering. It discusses the importance of application security policies being customized and delivered effectively. It emphasizes the need for application security activities like threat modeling and code reviews to avoid relying on "security pixie dust". It argues that even non-software companies should view themselves as software companies due to their reliance on code. Finally, it discusses building application security teams internally by training and educating developers rather than exclusively hiring specialists.
Security Champions - Introduce them in your Organisation



Security Champions - Introduce them in your OrganisationIves Laaf How to get security software development established, training of teams. A methodology based on the concept of security champions and owasp tools and guides.
Cyber Security # Lec 3 



Cyber Security # Lec 3 Kabul Education University 1. Cybersecurity risk management involves identifying vulnerabilities and risks, assessing their likelihood and impact, and implementing measures to reduce risks to acceptable levels.
2. A risk analysis was presented that identifies assets, threats, vulnerabilities, assesses impact of threats, likelihood of vulnerabilities being exploited, and determines overall risk levels.
3. Managing cybersecurity risk is a team effort that requires addressing both technical risks like vulnerabilities in systems, as well as human risks from employees through training to reduce threats.
Threat modeling (Hacker Stories) workshop



Threat modeling (Hacker Stories) workshopTy Sbano The document outlines the agenda for a threat modeling workshop. The workshop includes three sessions: (1) BYOTM where attendees bring their own threat models to work on together, (2) an advanced threat modeling session on applying rapid techniques in a DevOps environment, and (3) an introductory threat modeling primer. The document then provides more details on topics covered in each session, including customizing approaches to organizational needs, key threat modeling terms, and frameworks that can be used. It emphasizes the importance of focusing threat modeling efforts on adding value and keeping practices sustainable.
Injecting Threat Modeling into the SDLC by Susan Bradley



Injecting Threat Modeling into the SDLC by Susan BradleyQA or the Highway The document discusses injecting threat modeling into the software development lifecycle (SDLC). It provides examples of security issues that could have been prevented with threat modeling, such as the Equifax data breach. Threat modeling is a structured approach to identify, quantify, and address security risks. It should be used during requirements, design, and development phases of both new and existing functionality. The process involves data flow diagrams, identifying threats and proposed responses, prioritizing mitigations, and using techniques like STRIDE. Threat modeling sessions should gather documentation and cross-functional teams to holistically understand risks. Identified risks are then evaluated and prioritized to determine how to handle each risk.
Agile and Secure SDLC



Agile and Secure SDLCNazar Tymoshyk, CEH, Ph.D. This document discusses implementing a secure software development lifecycle (SDLC) to improve application security. It outlines why the traditional approach of only involving security experts does not work. Instead, it proposes integrating security practices throughout each phase of the development process, including requirements, design, implementation, verification, and release. This includes training developers, conducting threat modeling and security testing, using security tools in continuous integration, and analyzing results to address issues early. The goal is to reduce security defects over time by changing developer mindsets and integrating security as applications are built.
Experts Live 2022 - Attack Surface Reduction rules...your best ally against r...



Experts Live 2022 - Attack Surface Reduction rules...your best ally against r...PimJacobs3 Attack Surface Reduction rules in Windows Defender can help defend against ransomware attacks by reducing common techniques used by ransomware. The rules target suspicious software behaviors to prevent attacks. There are different rule categories and operating modes that can be used. Configuring and monitoring the rules through Endpoint Manager was demonstrated. Tips were provided on how and where to start implementing Attack Surface Reduction rules, such as creating individual policies, using audit mode initially, and using Advanced Hunting queries to identify compatibility issues. Resources for further information on Attack Surface Reduction rules were also shared.
Null bachav



Null bachavNaga Venkata Sunil Alamuri This presentation discusses the importance of threat Modeling. This presentation also discusses about different ways to perform threat modeling. This threat modeling should be done during the design phase of the application development. The main aim of the threat modeling is to identify the import assets or functionalities of the application and to protect them. Threat Modeling cuts down the cost of application development as it identifies the issues during the design phase. In this presentation we also discuss about basics of Mobile Threat Modeling. This presentation mainly concentrates on STRIDE and DREAD.
SDLC & DevSecOps



SDLC & DevSecOpsIrina Kostina The document discusses security best practices across the software development lifecycle (SDLC). It covers:
- The Microsoft Security Development Lifecycle (SDL) methodology which includes activities like threat modeling, security testing, using approved tools and cryptography standards, managing third-party components, and establishing an incident response process.
- Static and dynamic application security testing (SAST and DAST) - SAST analyzes source code for vulnerabilities while DAST tests running applications. Both have tradeoffs in terms of when issues are found, expenses to fix, and what types of vulnerabilities are discovered.
- DevSecOps practices like integrating security activities into each stage of development through techniques like incremental threat modeling, automated testing, and continuous
BSides Vienna 2015



BSides Vienna 2015Daniel Liber This document discusses integrating security practices into agile software development processes. It begins with an overview of agile development principles and how security frameworks can sometimes conflict with an agile approach. It then discusses strategies for collaborating with development teams on security, including designating security champions within teams and providing customized security training. The document closes by highlighting the importance of catching security issues early in the development process, citing statistics about the frequency and costs of breaches that result from insecure software releases.
Webinar–Segen oder Fluch?



Webinar–Segen oder Fluch?Synopsys Software Integrity Group Die Zeiten ändern sich und verlangen immer mehr Aufmerksamkeit. Dies trifft speziell im Bereich Open-Source-Software zu. Die Komplexität gerade in der Technologiebranche ist enorm, gerade wenn der Sicherheitsaspekt eine wichtige Rolle spielt.
Die Nutzung von Open-Source ist bereits beachtlich und nimmt stetig zu. Im Vergleich zum letzten Jahr ist die Anzahl der Unternehmen, die OSS verwenden enorm gestiegen. In Deutschland setzen 69% der befragten Unternehmen OSS ein und der Trend steigt stetig. Im globalen Vergleich verwenden laut des OSSRA Berichts 2019 (Open Source Sicherheits-und Risikoanalyse) 60% der befragten Unternehmen Open Source im analysierten Code im Jahr 2018; eine 3%ige Steigerung zum Vorjahr.
Webinar–Mobile Application Hardening Protecting Business Critical Apps



Webinar–Mobile Application Hardening Protecting Business Critical AppsSynopsys Software Integrity Group During this talk, we looked at some of the typical controls that Android/iOS applications exhibit, how they work, how to spot them, and how to sidestep them. We’ll demonstrate analysis and techniques using free open source tooling such as Radare and Frida, and for some parts, we’ll use IDA Pro. And since “automation” is the buzzword of the year, we’ll discuss how to automate some of these activities, which typically take up most of the assessment window.
For more information, please visit our website at www.synopsys.com/software
Ad
More Related Content
Similar to Synopsys Security Event Israel Presentation: Value Driven Threat Modeling (20)
Threat Modeling - Locking the Door to Vulnerabilities



Threat Modeling - Locking the Door to VulnerabilitiesSecurity Innovation Did you lock the door before leaving your house this morning? If you did, you threat modeled without even realizing it. Threat modeling is identifying potential threats (house robbery) and implementing measures to mitigate the risk (locking your door).
Protecting valuable assets, no matter if personal assets or business-related assets such as the software you are developing, threat modeling should become an instinctual and necessary part of your process.
Our talk highlights how nearly 50% of security flaws can be mitigated through threat modeling. We help you prevent and mitigate risks by utilizing a reliable and hard-hitting analysis technique that can be applied to individual applications or across an entire portfolio. We show you how to effectively apply these techniques at the start of the design phase and throughout every phase of the development lifecycle so you can maximize the ROI of your security efforts.
Topics covered include:
• Threat Modeling 101
• The propagating effect of poor design
• Tabletop exercise – a world with and without threat modeling
• Best practices and metrics for every stakeholder
OWASP based Threat Modeling Framework



OWASP based Threat Modeling FrameworkChaitanya Bhatt Creating a custom Threat Modeling feedback model in an agile environment.
Youtube : https://www.youtube.com/watch?v=pXr75ufG1uM
Ryan Elkins - Simple Security Defense to Thwart an Army of Cyber Ninja Warriors



Ryan Elkins - Simple Security Defense to Thwart an Army of Cyber Ninja WarriorsRyan Elkins The document provides guidance on implementing simple yet effective security defenses to thwart cyber attacks. It recommends building security programs with key components like policies, baselines, risk acceptance models and checklists for application security reviews. Specific defenses include user awareness training, least privileged access, patching, network segmentation, input validation, logging and encryption. The document argues that with the right foundations, organizations do not need large budgets for security and can prevent common hacking techniques.
DevSecOps : an Introduction



DevSecOps : an IntroductionPrashanth B. P. DevSecOps is a cultural change that incorporates security practices into software development through people, processes, and technologies. It aims to address security without slowing delivery by establishing secure-by-design approaches, automating security tools and processes, and promoting collaboration between developers, security engineers, and operations teams. As software and connected devices continue proliferating, application security must be a central focus of the development lifecycle through a DevSecOps methodology.
Security Checkpoints in Agile SDLC



Security Checkpoints in Agile SDLCRahul Raghavan Product Engineering teams have started to realize the importance of software security. This has resulted in the trend where teams are taking efforts to include it as part of their software development life cycle; as opposed to treating it as another item in their checklist prior to release. However, the real challenge is in trying to find the balance between agility and quality which is where many team find this an uphill task.
While there is no golden standard when it comes to implementing software security, product teams should focus on bringing about systematic and cultural practices within their teams. This should help them to bring about the required efficiency to enable software security as a market differentiator.
This slide-deck on Software Security Initiative focuses on translating a plan of action into sustainable activities as part of the secure software development life cycle that can be adopted by engineering teams. The slides will delve deep into aspects like identifying and designing security checkpoints in the SDLC alongside concepts such as Threat Modelling in Agile, AppSec Toolchain and Security Regressions.
This was presented as a we45 Webinar on April 12, 2018
An Introduction to Secure Application Development



An Introduction to Secure Application DevelopmentChristopher Frenz The document discusses application security best practices. It notes that 60% of internet attacks target web applications, with SQL injection and XSS making up 80% of vulnerabilities. It recommends that security be incorporated throughout the entire software development lifecycle, from requirements to testing. Key steps include threat modeling, secure coding practices, code reviews, fuzz testing and penetration testing. Ongoing maintenance is also important.
Threat modelling & apps testing



Threat modelling & apps testingAdrian Munteanu The document discusses threat modeling and application security testing. It begins by noting a lack of secure coding knowledge among developers and testers. It then uses an analogy comparing building applications to building cars, noting many similarities in unsecure practices. This is followed by sections on vulnerabilities versus security, common application vulnerabilities, and industry solutions. The document concludes by discussing threat modeling and provides an example using the OWASP Threat Dragon tool.
"Threat Model Every Story": Practical Continuous Threat Modeling Work for You...



"Threat Model Every Story": Practical Continuous Threat Modeling Work for You...Izar Tarandach How to do threat modeling in the age of Agile and DevOps. A practical methodology for teams focusing on developers. Also, an introduction to PyTM as a tool for threat-modeling-with-code.
Threat Modeling Lessons From Star Wars



Threat Modeling Lessons From Star WarsAdam Shostack Everyone knows you ought to threat model, but in practical reality it turns out to be tricky. If past efforts to threat model haven't panned out, perhaps part of the problem is confusion over what works, and how the various approaches conflict or align. This talk captures lessons from years of work helping people throughout the software industry threat model more effectively. It's designed to help security pros, developers and systems managers, all of whom will leave with both threat modeling lessons from Star Wars and a proven foundation, enabling them to threat model effectively.
NTXISSACSC2 - Threat Modeling Part 1 - Overview by Brad Andrews



NTXISSACSC2 - Threat Modeling Part 1 - Overview by Brad AndrewsNorth Texas Chapter of the ISSA Brad Andrews, CEO, RBA Communications
Threat Modeling Overview
This session will cover the basic elements of threat modeling, looking at what it does and why it is important. The goal is to provide a high level overview of the process and the use of things like data flow diagrams to look for trust boundaries attacks may come across. We will go through some common threats and hopefully a list of dangers to watch out for when carrying out threat modeling. The session will then work to interactively develop a flow diagram of Amazon.com and possibly another subject if we have time. This will all be based on looking at the system as a user, without any insider knowledge, though Threat Modeling is normally carried out by those who do know the system well.
SC conference - Building AppSec Teams



SC conference - Building AppSec TeamsDinis Cruz This document discusses building application security teams. It begins by introducing the author and their background in application security. It then discusses creating an environment where security enables business goals rather than hinders them. It suggests embedding security into culture by focusing on quality, testing, and engineering. It discusses the importance of application security policies being customized and delivered effectively. It emphasizes the need for application security activities like threat modeling and code reviews to avoid relying on "security pixie dust". It argues that even non-software companies should view themselves as software companies due to their reliance on code. Finally, it discusses building application security teams internally by training and educating developers rather than exclusively hiring specialists.
Security Champions - Introduce them in your Organisation



Security Champions - Introduce them in your OrganisationIves Laaf How to get security software development established, training of teams. A methodology based on the concept of security champions and owasp tools and guides.
Cyber Security # Lec 3 



Cyber Security # Lec 3 Kabul Education University 1. Cybersecurity risk management involves identifying vulnerabilities and risks, assessing their likelihood and impact, and implementing measures to reduce risks to acceptable levels.
2. A risk analysis was presented that identifies assets, threats, vulnerabilities, assesses impact of threats, likelihood of vulnerabilities being exploited, and determines overall risk levels.
3. Managing cybersecurity risk is a team effort that requires addressing both technical risks like vulnerabilities in systems, as well as human risks from employees through training to reduce threats.
Threat modeling (Hacker Stories) workshop



Threat modeling (Hacker Stories) workshopTy Sbano The document outlines the agenda for a threat modeling workshop. The workshop includes three sessions: (1) BYOTM where attendees bring their own threat models to work on together, (2) an advanced threat modeling session on applying rapid techniques in a DevOps environment, and (3) an introductory threat modeling primer. The document then provides more details on topics covered in each session, including customizing approaches to organizational needs, key threat modeling terms, and frameworks that can be used. It emphasizes the importance of focusing threat modeling efforts on adding value and keeping practices sustainable.
Injecting Threat Modeling into the SDLC by Susan Bradley



Injecting Threat Modeling into the SDLC by Susan BradleyQA or the Highway The document discusses injecting threat modeling into the software development lifecycle (SDLC). It provides examples of security issues that could have been prevented with threat modeling, such as the Equifax data breach. Threat modeling is a structured approach to identify, quantify, and address security risks. It should be used during requirements, design, and development phases of both new and existing functionality. The process involves data flow diagrams, identifying threats and proposed responses, prioritizing mitigations, and using techniques like STRIDE. Threat modeling sessions should gather documentation and cross-functional teams to holistically understand risks. Identified risks are then evaluated and prioritized to determine how to handle each risk.
Agile and Secure SDLC



Agile and Secure SDLCNazar Tymoshyk, CEH, Ph.D. This document discusses implementing a secure software development lifecycle (SDLC) to improve application security. It outlines why the traditional approach of only involving security experts does not work. Instead, it proposes integrating security practices throughout each phase of the development process, including requirements, design, implementation, verification, and release. This includes training developers, conducting threat modeling and security testing, using security tools in continuous integration, and analyzing results to address issues early. The goal is to reduce security defects over time by changing developer mindsets and integrating security as applications are built.
Experts Live 2022 - Attack Surface Reduction rules...your best ally against r...



Experts Live 2022 - Attack Surface Reduction rules...your best ally against r...PimJacobs3 Attack Surface Reduction rules in Windows Defender can help defend against ransomware attacks by reducing common techniques used by ransomware. The rules target suspicious software behaviors to prevent attacks. There are different rule categories and operating modes that can be used. Configuring and monitoring the rules through Endpoint Manager was demonstrated. Tips were provided on how and where to start implementing Attack Surface Reduction rules, such as creating individual policies, using audit mode initially, and using Advanced Hunting queries to identify compatibility issues. Resources for further information on Attack Surface Reduction rules were also shared.
Null bachav



Null bachavNaga Venkata Sunil Alamuri This presentation discusses the importance of threat Modeling. This presentation also discusses about different ways to perform threat modeling. This threat modeling should be done during the design phase of the application development. The main aim of the threat modeling is to identify the import assets or functionalities of the application and to protect them. Threat Modeling cuts down the cost of application development as it identifies the issues during the design phase. In this presentation we also discuss about basics of Mobile Threat Modeling. This presentation mainly concentrates on STRIDE and DREAD.
SDLC & DevSecOps



SDLC & DevSecOpsIrina Kostina The document discusses security best practices across the software development lifecycle (SDLC). It covers:
- The Microsoft Security Development Lifecycle (SDL) methodology which includes activities like threat modeling, security testing, using approved tools and cryptography standards, managing third-party components, and establishing an incident response process.
- Static and dynamic application security testing (SAST and DAST) - SAST analyzes source code for vulnerabilities while DAST tests running applications. Both have tradeoffs in terms of when issues are found, expenses to fix, and what types of vulnerabilities are discovered.
- DevSecOps practices like integrating security activities into each stage of development through techniques like incremental threat modeling, automated testing, and continuous
BSides Vienna 2015



BSides Vienna 2015Daniel Liber This document discusses integrating security practices into agile software development processes. It begins with an overview of agile development principles and how security frameworks can sometimes conflict with an agile approach. It then discusses strategies for collaborating with development teams on security, including designating security champions within teams and providing customized security training. The document closes by highlighting the importance of catching security issues early in the development process, citing statistics about the frequency and costs of breaches that result from insecure software releases.
More from Synopsys Software Integrity Group (20)
Webinar–Segen oder Fluch?



Webinar–Segen oder Fluch?Synopsys Software Integrity Group Die Zeiten ändern sich und verlangen immer mehr Aufmerksamkeit. Dies trifft speziell im Bereich Open-Source-Software zu. Die Komplexität gerade in der Technologiebranche ist enorm, gerade wenn der Sicherheitsaspekt eine wichtige Rolle spielt.
Die Nutzung von Open-Source ist bereits beachtlich und nimmt stetig zu. Im Vergleich zum letzten Jahr ist die Anzahl der Unternehmen, die OSS verwenden enorm gestiegen. In Deutschland setzen 69% der befragten Unternehmen OSS ein und der Trend steigt stetig. Im globalen Vergleich verwenden laut des OSSRA Berichts 2019 (Open Source Sicherheits-und Risikoanalyse) 60% der befragten Unternehmen Open Source im analysierten Code im Jahr 2018; eine 3%ige Steigerung zum Vorjahr.
Webinar–Mobile Application Hardening Protecting Business Critical Apps



Webinar–Mobile Application Hardening Protecting Business Critical AppsSynopsys Software Integrity Group During this talk, we looked at some of the typical controls that Android/iOS applications exhibit, how they work, how to spot them, and how to sidestep them. We’ll demonstrate analysis and techniques using free open source tooling such as Radare and Frida, and for some parts, we’ll use IDA Pro. And since “automation” is the buzzword of the year, we’ll discuss how to automate some of these activities, which typically take up most of the assessment window.
For more information, please visit our website at www.synopsys.com/software
Webinar–The 2019 Open Source Year in Review



Webinar–The 2019 Open Source Year in ReviewSynopsys Software Integrity Group This annual review will highlight the most significant legal developments related to open source software in 2019, including:
•Evolution of open source: control, sustainability, and politics
•Litigation update: Cambium and Artifex cases
•Patents and the open source community
•Impacts of government sanctions
•The shift left for compliance and rise of bug bounty programs
•And much, much more
For more information, please visit https://www.synopsys.com/software-integrity/managed-services/open-source-software-audit.html
Webinar–Best Practices for DevSecOps at Scale



Webinar–Best Practices for DevSecOps at ScaleSynopsys Software Integrity Group Today’s security professionals and software developers not only have to do more in less time; they have to do it securely. This means mitigating risk and addressing compliance requirements in an environment where:
• The threat landscape continues to evolve.
• Application portfolios and their risk profiles continue to shift.
• Security tools are difficult to deploy, configure, and integrate into workflows.
• Consumption models continue to change.
How can your internal resources keep pace in this dynamic environment? Managed application security testing can be just the relief valve your organization needs. In this webinar, we’ll discuss the need for managed application security testing, the sweet spots where it offers maximum value, what you should look for in a managed application security testing provider, and highlights from Synopsys’ Managed Services offering.
Today’s security professionals and software developers not only have to do more in less time; they have to do it securely. This means mitigating risk and addressing compliance requirements in an environment where:
• The threat landscape continues to evolve.
• Application portfolios and their risk profiles continue to shift.
• Security tools are difficult to deploy, configure, and integrate into workflows.
• Consumption models continue to change.
How can your internal resources keep pace in this dynamic environment? Managed application security testing can be just the relief valve your organization needs. In this webinar, we’ll discuss the need for managed application security testing, the sweet spots where it offers maximum value, what you should look for in a managed application security testing provider, and highlights from Synopsys’ Managed Services offering.
For more information, please visit our website at https://www.synopsys.com/software-integrity/managed-services.html
Webinar–That is Not How This Works



Webinar–That is Not How This WorksSynopsys Software Integrity Group During a recent webinar, Jonathan Knudsen presented: "That's Not How This Works: All Development Should Be Secure."
Development teams are pressured to push new software out quickly. But with speed comes risk. Anyone can write software, but if you want to create software that is safe, secure, and robust, you need the right process. Webinar attendees will learn:
• Why traditional approaches to software development usually end in tears and heartburn
• How a structured approach to secure software development lowers risk for you and your customers
• Why automation and security testing tools are key components in the implementation of a secure development life cycle
For more information, please visit our website at www.synopsys.com/software-integrity.html
Webinar–You've Got Your Open Source Audit Report–Now What? 



Webinar–You've Got Your Open Source Audit Report–Now What? Synopsys Software Integrity Group Companies’ use of open source software has surpassed the occasional and solidified itself as the mainstream. Effectively identifying and managing the compliance and security risks associated with open source software can be a difficult task. Whether a company is acquiring another company, preparing for acquisition or simply wanting to manage their use of open source, the universal first step is to figure out the composition of the code, often via an audit. But what do you do once you have the audit report?
For more information, please visit our website at https://www.synopsys.com/open-source-audit
Webinar–OWASP Top 10 for JavaScript for Developers



Webinar–OWASP Top 10 for JavaScript for DevelopersSynopsys Software Integrity Group During a recent webinar, Lewis Ardern, senior security consultant presented "OWASP Top 10 for JavaScript Developers."
19_10_EMEA_WB_Owasp Top 10 for Java Script Developers With the release of the OWASP Top 10 2017, we saw new contenders for the most critical security issues in the web application landscape. Much of the OWASP documentation concerning issues, remediation advice, and code samples focuses on Java, C++, and C#. However, it doesn’t give much attention to JavaScript. JavaScript has drastically changed over the last few years with the release of Angular, React, and Vue, alongside the growing use of Node.js and its libraries and frameworks. This talk will introduce you to the OWASP Top 10 by explaining JavaScript client and server-side vulnerabilities.
For more information, please visit our website at www.synopsys.com/standards
Webinar–The State of Open Source in M&A Transactions 



Webinar–The State of Open Source in M&A Transactions Synopsys Software Integrity Group During a recent webinar, West Monroe discussed, "The State of Open Source in M&A Transactions."
Based extensive experience in M&A, West Monroe Partners is on the front line when it comes to tech due diligence, and they’ve seen a few trends emerge when it comes to open source and M&A deals. Buyers and seller alike need to understand these trends to get the most value out of any transaction.
For more information, please visit our website at www.synopsys.com/open-source-audit
Webinar–5 ways to risk rank your vulnerabilities



Webinar–5 ways to risk rank your vulnerabilitiesSynopsys Software Integrity Group Vulnerabilities are an inevitable part of software development and management. Whether they’re in open source or custom code, new vulnerabilities will be discovered as a codebase ages. As stated in the 2019 Open Source Security and Risk Analysis report, 60% of the codebases audited in 2018 contained at least one known vulnerability. As the number of disclosures, patches, and updates grows, security professionals must decide which critical items to address immediately and which items to defer.
For more information, please visit our website at www.synopsys.com/software.
Do Design Quality and Code Quality Matter in Merger and Acquisition Tech Due ...



Do Design Quality and Code Quality Matter in Merger and Acquisition Tech Due ...Synopsys Software Integrity Group Dan Sturtevant, Silverthread and Niles Madison at Synopsys discussed design quality and code quality on a recent webinar.
In an acquisition where a software asset is a core part of the deal valuation, it’s important to understand the overall quality of the software prior to doing the deal. Buggy software is problematic and needs to be cleaned up, so assessing code quality is important. But also, with poorly designed software, every fix is costly and laborious. This can significantly impact the long-term viability of the application, and maintaining that software can seriously degrade ROI. That’s why understanding a software system’s design or architectural health and the likely 'cost of ownership' is key..
For more information, please visit our website at https://www.synopsys.com/open-source-audit
Webinar–Using Evidence-Based Security 



Webinar–Using Evidence-Based Security Synopsys Software Integrity Group During a recent webinar, Andrew Vanderstock, senior principal consultant at Synopsys presented "Using Evidence-Based Security in Your Secure Development Life Cycle." For more information on our products and services, please visit our website at www.synopsys.com/software.
Webinar–Delivering a Next Generation Vulnerability Feed



Webinar–Delivering a Next Generation Vulnerability FeedSynopsys Software Integrity Group The Synopsys Cybersecurity Research Center (CyRC) has a dedicated team of security analysts who specialize in sourcing, curating, and analyzing open source software vulnerabilities. The team delivers a customer-focused vulnerability feed comprising open source vulnerability reports called BDSAs (Black Duck Security Advisories). These reports are timely, accurate, and packed with relevant actionable information.
In this webinar, Siobhan Hunter, security research lead, reveals why the high-quality content of the BDSA feed is best in class, with examples of how our BDSA feed compares with the NVD and insights into how we discover and deliver valuable vulnerability information for our customers every day. For more information, please visit our website at https://www.synopsys.com/cyrc
Webinar–Financial Services Study Shows Why Investing in AppSec Matters



Webinar–Financial Services Study Shows Why Investing in AppSec MattersSynopsys Software Integrity Group This document summarizes a study on why investing in application security (appsec) matters for financial services organizations. The study found that over 50% of financial services firms had experienced theft of customer data due to insecure software. It also found that on average, only 34% of financial software and technology is tested for cybersecurity vulnerabilities. While addressing cybersecurity risks is important, the study noted that financial organizations face resource constraints, with only 45% believing they have adequate budgets for security and only 38% having necessary security skills. The document promotes the software integrity tools offered by Synopsys to help organizations build more secure software faster and address these challenges.
Webinar–What You Need To Know About Open Source Licensing



Webinar–What You Need To Know About Open Source LicensingSynopsys Software Integrity Group Virtually every organization uses open source software, and lots of it, to create efficiencies in software development. But left unmanaged, open source can introduce legal, IP, compliance, and other risks for the business. With over 2,500 different licenses in use, legal professionals and technical managers need to understand the license obligations associated with open source and how to mitigate risks. For more information, please visit our website at www.synopsys.com/open-source-audit
Webinar–Improving Fuzz Testing of Infotainment Systems and Telematics Units U...



Webinar–Improving Fuzz Testing of Infotainment Systems and Telematics Units U...Synopsys Software Integrity Group In the past few years, cybersecurity has become more intertwined into each step of the automotive development process. In particular, fuzz testing has proven to be a powerful approach to detect unknown vulnerabilities in automotive systems. However, with limited instrumentation, especially on systems such as in-vehicle infotainment (IVI) system and telematics units, there are several types of issues that go undetected, such as memory leaks and cases where the application crashes but restarts quickly. For more information, please visit www.synopsys.com/auto
Webinar–Why All Open Source Scans Aren't Created Equal



Webinar–Why All Open Source Scans Aren't Created EqualSynopsys Software Integrity Group During a recent webinar attendees learned how a purpose-built M&A open source audit differs from open source management tools and why it matters in tech due diligence. We covered: • The types of risk around open source software • Why depth of analysis matters, and what it results in during M&A diligence • Why accuracy, reporting, and expert human analysis are keys to thorough diligence.
For more information, please visit our website at www.synopsys.com/open-source-audit
Webinar–Is Your Software Security Supply Chain a Security Blind Spot?



Webinar–Is Your Software Security Supply Chain a Security Blind Spot?Synopsys Software Integrity Group Lysa Bryngelson, Sr. Product Manager for Black Duck Binary Analysis at Synopsys presented on a recent webinar. During the webinar, she discussed one of the biggest challenges companies face with third-party software is lack of visibility into the open source libraries used in the software they embed in their products. Over the last year, major security breaches have been attributed to exploits of vulnerabilities in open source frameworks used by Fortune 100 companies in education, government, financial services, retail, and media. For more information, please visit our website at www.synopsys.com/blackduck
Webinar–Sécurité Applicative et DevSecOps dans un monde Agile



Webinar–Sécurité Applicative et DevSecOps dans un monde AgileSynopsys Software Integrity Group Alors que l’adoption de DevOps pour des organisations Agile était une transition naturelle, le passage à DevSecOps a introduit de nouveaux défis. DevSecOps nécessite un changement important de mentalité et de culture d'entreprise pour intégrer les nouveaux outils et les nouvelles activités de sécurité. C’est la raison pour laquelle suivre le rythme d’Agile et la culture DevOps lors de l’introduction de la sécurité dans le cycle de développement logiciel (SDLC) est un défit pour de nombreuses entreprises.
Dans ce webinaire, Cem Nisanoglu explore le modèle opérationnel de DevSecOps et souligne l'importance de la gestion des changements, de l'automatisation, et des indicateurs de sécurité dans une transition vers DevSecOps, ainsi que la manière dont ces activités peuvent contribuer à la formation de sécurité, à des cycles de release plus rapides, et à l'optimisation des budgets de sécurité dans l’entreprise.
Webinar–Creating a Modern AppSec Toolchain to Quantify Service Risks



Webinar–Creating a Modern AppSec Toolchain to Quantify Service RisksSynopsys Software Integrity Group Tim Mackey is a principal security strategist with the Synopsys Cybersecurity Research Center(CyRC). Within this role, he engages with various technical and business communities to understand how application security is evolving with ever-expanding attack surfaces and increasingly sophisticated threats. He specializes in container security, virtualization, cloud technologies, distributed systems engineering, mission critical engineering, performance monitoring, and large-scale data center operations. Tim takes the lessons learned from these activities and delivers talks globally at conferences like RSA, KubeCon and InfoSec. For more information, please visit www.synopsys.com/software.
Webinar – Streamling Your Tech Due Diligence Process for Software Assets



Webinar – Streamling Your Tech Due Diligence Process for Software AssetsSynopsys Software Integrity Group During a recent webinar, Tim Mackey, Principal Security Strategist with the Synopsys Cyber Research Center discussed how to streamline the tech due diligence process.
For more information, please visit our website at www.synopsys.com/open-source-audit
Webinar–Mobile Application Hardening Protecting Business Critical Apps



Webinar–Mobile Application Hardening Protecting Business Critical AppsSynopsys Software Integrity Group
Do Design Quality and Code Quality Matter in Merger and Acquisition Tech Due ...



Do Design Quality and Code Quality Matter in Merger and Acquisition Tech Due ...Synopsys Software Integrity Group
Webinar–Financial Services Study Shows Why Investing in AppSec Matters



Webinar–Financial Services Study Shows Why Investing in AppSec MattersSynopsys Software Integrity Group
Webinar–Improving Fuzz Testing of Infotainment Systems and Telematics Units U...



Webinar–Improving Fuzz Testing of Infotainment Systems and Telematics Units U...Synopsys Software Integrity Group
Webinar–Is Your Software Security Supply Chain a Security Blind Spot?



Webinar–Is Your Software Security Supply Chain a Security Blind Spot?Synopsys Software Integrity Group
Webinar–Creating a Modern AppSec Toolchain to Quantify Service Risks



Webinar–Creating a Modern AppSec Toolchain to Quantify Service RisksSynopsys Software Integrity Group
Webinar – Streamling Your Tech Due Diligence Process for Software Assets



Webinar – Streamling Your Tech Due Diligence Process for Software AssetsSynopsys Software Integrity Group
Ad
Recently uploaded (20)
F-Secure Freedome VPN 2025 Crack Plus Activation New Version



F-Secure Freedome VPN 2025 Crack Plus Activation New Versionsaimabibi60507 Copy & Past Link 👉👉
https://dr-up-community.info/
F-Secure Freedome VPN is a virtual private network service developed by F-Secure, a Finnish cybersecurity company. It offers features such as Wi-Fi protection, IP address masking, browsing protection, and a kill switch to enhance online privacy and security .
How to Batch Export Lotus Notes NSF Emails to Outlook PST Easily?



How to Batch Export Lotus Notes NSF Emails to Outlook PST Easily?steaveroggers Migrating from Lotus Notes to Outlook can be a complex and time-consuming task, especially when dealing with large volumes of NSF emails. This presentation provides a complete guide on how to batch export Lotus Notes NSF emails to Outlook PST format quickly and securely. It highlights the challenges of manual methods, the benefits of using an automated tool, and introduces eSoftTools NSF to PST Converter Software — a reliable solution designed to handle bulk email migrations efficiently. Learn about the software’s key features, step-by-step export process, system requirements, and how it ensures 100% data accuracy and folder structure preservation during migration. Make your email transition smoother, safer, and faster with the right approach.
Read More:- https://www.esofttools.com/nsf-to-pst-converter.html
PDF Reader Pro Crack Latest Version FREE Download 2025



PDF Reader Pro Crack Latest Version FREE Download 2025mu394968 🌍📱👉COPY LINK & PASTE ON GOOGLE https://dr-kain-geera.info/👈🌍
PDF Reader Pro is a software application, often referred to as an AI-powered PDF editor and converter, designed for viewing, editing, annotating, and managing PDF files. It supports various PDF functionalities like merging, splitting, converting, and protecting PDFs. Additionally, it can handle tasks such as creating fillable forms, adding digital signatures, and performing optical character recognition (OCR).
Secure Test Infrastructure: The Backbone of Trustworthy Software Development



Secure Test Infrastructure: The Backbone of Trustworthy Software DevelopmentShubham Joshi A secure test infrastructure ensures that the testing process doesn’t become a gateway for vulnerabilities. By protecting test environments, data, and access points, organizations can confidently develop and deploy software without compromising user privacy or system integrity.
Landscape of Requirements Engineering for/by AI through Literature Review



Landscape of Requirements Engineering for/by AI through Literature ReviewHironori Washizaki Hironori Washizaki, "Landscape of Requirements Engineering for/by AI through Literature Review," RAISE 2025: Workshop on Requirements engineering for AI-powered SoftwarE, 2025.
Solidworks Crack 2025 latest new + license code



Solidworks Crack 2025 latest new + license codeaneelaramzan63 Copy & Paste On Google >>> https://dr-up-community.info/
The two main methods for installing standalone licenses of SOLIDWORKS are clean installation and parallel installation (the process is different ...
Disable your internet connection to prevent the software from performing online checks during installation
Designing AI-Powered APIs on Azure: Best Practices& Considerations



Designing AI-Powered APIs on Azure: Best Practices& ConsiderationsDinusha Kumarasiri AI is transforming APIs, enabling smarter automation, enhanced decision-making, and seamless integrations. This presentation explores key design principles for AI-infused APIs on Azure, covering performance optimization, security best practices, scalability strategies, and responsible AI governance. Learn how to leverage Azure API Management, machine learning models, and cloud-native architectures to build robust, efficient, and intelligent API solutions
WinRAR Crack for Windows (100% Working 2025)



WinRAR Crack for Windows (100% Working 2025)sh607827 copy and past on google ➤ ➤➤ https://hdlicense.org/ddl/
WinRAR Crack Free Download is a powerful archive manager that provides full support for RAR and ZIP archives and decompresses CAB, ARJ, LZH, TAR, GZ, ACE, UUE, .
Societal challenges of AI: biases, multilinguism and sustainability



Societal challenges of AI: biases, multilinguism and sustainabilityJordi Cabot Towards a fairer, inclusive and sustainable AI that works for everybody.
Reviewing the state of the art on these challenges and what we're doing at LIST to test current LLMs and help you select the one that works best for you
Exploring Wayland: A Modern Display Server for the Future



Exploring Wayland: A Modern Display Server for the FutureICS Wayland is revolutionizing the way we interact with graphical interfaces, offering a modern alternative to the X Window System. In this webinar, we’ll delve into the architecture and benefits of Wayland, including its streamlined design, enhanced performance, and improved security features.
Top 10 Client Portal Software Solutions for 2025.docx



Top 10 Client Portal Software Solutions for 2025.docxPortli Discover the top 10 client portal software solutions for 2025. Streamline communication, ensure security, and enhance client experience.
The Significance of Hardware in Information Systems.pdf



The Significance of Hardware in Information Systems.pdfdrewplanas10 The Significance of Hardware in Information Systems: The Types Of Hardware and What They Do
Adobe Master Collection CC Crack Advance Version 2025



Adobe Master Collection CC Crack Advance Version 2025kashifyounis067 🌍📱👉COPY LINK & PASTE ON GOOGLE http://drfiles.net/ 👈🌍
Adobe Master Collection CC (Creative Cloud) is a comprehensive subscription-based package that bundles virtually all of Adobe's creative software applications. It provides access to a wide range of tools for graphic design, video editing, web development, photography, and more. Essentially, it's a one-stop-shop for creatives needing a broad set of professional tools.
Key Features and Benefits:
All-in-one access:
The Master Collection includes apps like Photoshop, Illustrator, InDesign, Premiere Pro, After Effects, Audition, and many others.
Subscription-based:
You pay a recurring fee for access to the latest versions of all the software, including new features and updates.
Comprehensive suite:
It offers tools for a wide variety of creative tasks, from photo editing and illustration to video editing and web development.
Cloud integration:
Creative Cloud provides cloud storage, asset sharing, and collaboration features.
Comparison to CS6:
While Adobe Creative Suite 6 (CS6) was a one-time purchase version of the software, Adobe Creative Cloud (CC) is a subscription service. CC offers access to the latest versions, regular updates, and cloud integration, while CS6 is no longer updated.
Examples of included software:
Adobe Photoshop: For image editing and manipulation.
Adobe Illustrator: For vector graphics and illustration.
Adobe InDesign: For page layout and desktop publishing.
Adobe Premiere Pro: For video editing and post-production.
Adobe After Effects: For visual effects and motion graphics.
Adobe Audition: For audio editing and mixing.
Interactive odoo dashboards for sales, CRM , Inventory, Invoice, Purchase, Pr...



Interactive odoo dashboards for sales, CRM , Inventory, Invoice, Purchase, Pr...AxisTechnolabs Interactive Odoo Dashboard for various business needs can provide users with dynamic, visually appealing dashboards tailored to their specific requirements. such a module that could support multiple dashboards for different aspects of a business
✅Visit And Buy Now : https://bit.ly/3VojWza
✅This Interactive Odoo dashboard module allow user to create their own odoo interactive dashboards for various purpose.
App download now :
Odoo 18 : https://bit.ly/3VojWza
Odoo 17 : https://bit.ly/4h9Z47G
Odoo 16 : https://bit.ly/3FJTEA4
Odoo 15 : https://bit.ly/3W7tsEB
Odoo 14 : https://bit.ly/3BqZDHg
Odoo 13 : https://bit.ly/3uNMF2t
Try Our website appointment booking odoo app : https://bit.ly/3SvNvgU
👉Want a Demo ?📧 [email protected]
➡️Contact us for Odoo ERP Set up : 091066 49361
👉Explore more apps: https://bit.ly/3oFIOCF
👉Want to know more : 🌐 https://www.axistechnolabs.com/
#odoo #odoo18 #odoo17 #odoo16 #odoo15 #odooapps #dashboards #dashboardsoftware #odooerp #odooimplementation #odoodashboardapp #bestodoodashboard #dashboardapp #odoodashboard #dashboardmodule #interactivedashboard #bestdashboard #dashboard #odootag #odooservices #odoonewfeatures #newappfeatures #odoodashboardapp #dynamicdashboard #odooapp #odooappstore #TopOdooApps #odooapp #odooexperience #odoodevelopment #businessdashboard #allinonedashboard #odooproducts
TestMigrationsInPy: A Dataset of Test Migrations from Unittest to Pytest (MSR...



TestMigrationsInPy: A Dataset of Test Migrations from Unittest to Pytest (MSR...Andre Hora Unittest and pytest are the most popular testing frameworks in Python. Overall, pytest provides some advantages, including simpler assertion, reuse of fixtures, and interoperability. Due to such benefits, multiple projects in the Python ecosystem have migrated from unittest to pytest. To facilitate the migration, pytest can also run unittest tests, thus, the migration can happen gradually over time. However, the migration can be timeconsuming and take a long time to conclude. In this context, projects would benefit from automated solutions to support the migration process. In this paper, we propose TestMigrationsInPy, a dataset of test migrations from unittest to pytest. TestMigrationsInPy contains 923 real-world migrations performed by developers. Future research proposing novel solutions to migrate frameworks in Python can rely on TestMigrationsInPy as a ground truth. Moreover, as TestMigrationsInPy includes information about the migration type (e.g., changes in assertions or fixtures), our dataset enables novel solutions to be verified effectively, for instance, from simpler assertion migrations to more complex fixture migrations. TestMigrationsInPy is publicly available at: https://github.com/altinoalvesjunior/TestMigrationsInPy.
FL Studio Producer Edition Crack 2025 Full Version



FL Studio Producer Edition Crack 2025 Full Versiontahirabibi60507 Copy & Past Link 👉👉
http://drfiles.net/
FL Studio is a Digital Audio Workstation (DAW) software used for music production. It's developed by the Belgian company Image-Line. FL Studio allows users to create and edit music using a graphical user interface with a pattern-based music sequencer.
Exploring Code Comprehension in Scientific Programming: Preliminary Insight...



Exploring Code Comprehension in Scientific Programming: Preliminary Insight...University of Hawai‘i at Mānoa This presentation explores code comprehension challenges in scientific programming based on a survey of 57 research scientists. It reveals that 57.9% of scientists have no formal training in writing readable code. Key findings highlight a "documentation paradox" where documentation is both the most common readability practice and the biggest challenge scientists face. The study identifies critical issues with naming conventions and code organization, noting that 100% of scientists agree readable code is essential for reproducible research. The research concludes with four key recommendations: expanding programming education for scientists, conducting targeted research on scientific code quality, developing specialized tools, and establishing clearer documentation guidelines for scientific software.
Presented at: The 33rd International Conference on Program Comprehension (ICPC '25)
Date of Conference: April 2025
Conference Location: Ottawa, Ontario, Canada
Preprint: https://arxiv.org/abs/2501.10037
Adobe Lightroom Classic Crack FREE Latest link 2025



Adobe Lightroom Classic Crack FREE Latest link 2025kashifyounis067 🌍📱👉COPY LINK & PASTE ON GOOGLE http://drfiles.net/ 👈🌍
Adobe Lightroom Classic is a desktop-based software application for editing and managing digital photos. It focuses on providing users with a powerful and comprehensive set of tools for organizing, editing, and processing their images on their computer. Unlike the newer Lightroom, which is cloud-based, Lightroom Classic stores photos locally on your computer and offers a more traditional workflow for professional photographers.
Here's a more detailed breakdown:
Key Features and Functions:
Organization:
Lightroom Classic provides robust tools for organizing your photos, including creating collections, using keywords, flags, and color labels.
Editing:
It offers a wide range of editing tools for making adjustments to color, tone, and more.
Processing:
Lightroom Classic can process RAW files, allowing for significant adjustments and fine-tuning of images.
Desktop-Focused:
The application is designed to be used on a computer, with the original photos stored locally on the hard drive.
Non-Destructive Editing:
Edits are applied to the original photos in a non-destructive way, meaning the original files remain untouched.
Key Differences from Lightroom (Cloud-Based):
Storage Location:
Lightroom Classic stores photos locally on your computer, while Lightroom stores them in the cloud.
Workflow:
Lightroom Classic is designed for a desktop workflow, while Lightroom is designed for a cloud-based workflow.
Connectivity:
Lightroom Classic can be used offline, while Lightroom requires an internet connection to sync and access photos.
Organization:
Lightroom Classic offers more advanced organization features like Collections and Keywords.
Who is it for?
Professional Photographers:
PCMag notes that Lightroom Classic is a popular choice among professional photographers who need the flexibility and control of a desktop-based application.
Users with Large Collections:
Those with extensive photo collections may prefer Lightroom Classic's local storage and robust organization features.
Users who prefer a traditional workflow:
Users who prefer a more traditional desktop workflow, with their original photos stored on their computer, will find Lightroom Classic a good fit.
Microsoft AI Nonprofit Use Cases and Live Demo_2025.04.30.pdf



Microsoft AI Nonprofit Use Cases and Live Demo_2025.04.30.pdfTechSoup In this webinar we will dive into the essentials of generative AI, address key AI concerns, and demonstrate how nonprofits can benefit from using Microsoft’s AI assistant, Copilot, to achieve their goals.
This event series to help nonprofits obtain Copilot skills is made possible by generous support from Microsoft.
What You’ll Learn in Part 2:
Explore real-world nonprofit use cases and success stories.
Participate in live demonstrations and a hands-on activity to see how you can use Microsoft 365 Copilot in your own work!
Exploring Code Comprehension in Scientific Programming: Preliminary Insight...



Exploring Code Comprehension in Scientific Programming: Preliminary Insight...University of Hawai‘i at Mānoa
Ad
Synopsys Security Event Israel Presentation: Value Driven Threat Modeling
- 1. VALUE DRIVEN THREAT MODELING A Lightweight Approach By Avi Douglen
- 2. Summary ■ Threat Modeling is great, but not used enough ■ Developers should Threat Model too! – Not just security ■ Prioritize by business value ■ Make it quick, make it lightweight, make it Agile
- 4. About Me ■ Email: [email protected] ■ Twitter: @sec_tigger ■ He / Him ■ The important things: – Whisky: smokey – Beer: stout – Coffee: strong ■ Software Security @ ■ Researcher / Developer / Architect ■ OWASP Israel Leader ■ Moderator Security.StackExchange ■ Volunteer High School teacher ■ Threat Model Project Leader
- 5. What is Threat Modeling? ■ Structured security-based analysis ■ Framework to understand threats ■ Review of Design Elements ■ Prioritize Mitigations by Risk
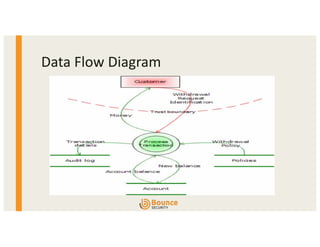
- 6. “Classic” Threat Modeling ■ Data Flows and Attack Surface ■ Focus on Assets, Trust Boundaries ■ Visually with DFDs or other diagrams ■ Step#0: Scoping the Model ■ Step#1: Decompose the Application ■ Step#2: Identify the Threats (and risk level) ■ Step#3: Determine the Countermeasures ■ Step#4: Analyze Result
- 8. Classic Methodologies ■ STRIDE / STRIDE-per-element ■ Attack Trees ■ Asset-Focused ■ Software-centric ■ Attacker-focused ■ Risk-Based
- 9. STRIDE Per-Element ■ SSppooooffiinngg ■ TTaammppeerriinngg ■ RReeppuuddiiaattiioonn ■ IInnffoorrmmaattiioonn DDiisscclloossuurree ■ DDeenniiaall ooff SSeerrvviiccee ■ EElleevvaattiioonn ooff PPrriivviilleeggeess
- 11. Attack Trees
- 12. P.A.S.T.A ■ Risk-Based Methodology for higher assurance ■ PProcess for AAttack SSimulation and TThreat AAnalysis ■ Seven stage process:
- 15. From a Developer’s Perspective ■ Takes too much time!
- 16. From a Developer’s Perspective ■ “Security is everybody’s job”
- 17. From a Developer’s Perspective ■ “Think like an attacker”
- 18. From a Developer’s Perspective ■ Use case approach to user story development
- 19. From a Developer’s Perspective ■ Big Model Up Front
- 20. From a Developer’s Perspective ■ Threat model separate from design documentation
- 21. From a Developer’s Perspective ■ Usually out of date, often before its complete
- 22. From a Developer’s Perspective ■ Wasted time on unrealistic threats
- 23. From a Developer’s Perspective ■ Dependent on Security
- 24. From a Developer’s Perspective ■ Security team drops in and out
- 25. From a Developer’s Perspective ■ Security team doesn’t scale
- 26. From a Developer’s Perspective
- 30. Back to Basics ■ 4 core questions of threat modeling: 1. What are you building? 2. What can go wrong? 3. What are you going to do about it? 4. Did we do a good job? ■ “All Threat Models are wrong, some are useful”
- 31. Reframing TM ■ Accept that it’s wrong, focus on the usefulness 1. Why are we building this? 2. What needs to go right? 3. How do we make sure that happens?
- 33. Value Driven Process ■ Start from standard baseline – Skip obvious threats (e.g. XSS, HTTPS) – Relies on basic code hygiene – Security training for all developers and testers! – Threat Library ■ Threat model each User Story / Epic – During “Discovery” or Sprint Planning – Agile approach of “just enough” threat model – Threat model goes into the User Story
- 34. Value Driven Process ■ Find the value of each feature – Follow the money! – How do people die?
- 35. Value Driven Process ■ State story goals ■ Describe correct flow and conditions ■ Highlight assumptions and failure states ■ Validate assumptions and enforce conditions ■ Explicitly handle failure states
- 36. Value Driven for Non-Developers ■ Result of Threat Model: x Cross Site Request Forgery (CSRF) <-> x Stored XSS <-> x AuthZ Bypass <-> x Denial of Service <-> ■ Black-Box Threat Modeling ü Unauthenticated Access to Cash Transfer ü Admin Takeover ü Change Delivery Address ü Loss of Revenue/Market
- 37. Benefits over Classic TM ■ Much quicker – faster to useful TM ■ In tune with pace of development ■ Iterative – just like agile development ■ More natural for developers ■ Documentation always up to date ■ Better communication ■ Easier to integrate with eg Scrum, Kanban ■ Don’t need piles of consultants ■ Scalable
- 38. Limitations ■ Not complete ■ Misses a LOT of threats ■ Relies on developer experience ■ Security champion must be part of team ■ Low assurance for high risk systems
- 39. Summary ■ Developers – start threat modeling!! ■ TM should be part of dev workflow ■ Focus on business value ■ Start with the useful part of TM – and stop there ■ Skip the overkill – until you really need it
- 40. THANKS FOR LISTENING! Find me on Twitter: @sec_tigger

