various shell commands in unix operating system.pptx
- 2. Ls command • List Files using ls with no option • ls with no option list files and directories in bare format where we won’t be able to view details like file types, size, modified date and time, permission and links etc.
- 3. • List Files With option –l • Here, ls -l (-l is character not one) shows file or directory, size, modified date and time, file or folder name and owner of file and it’s permission.
- 4. • View Hidden Files • List all files including hidden file starting with ‘.‘.
- 5. • List Files with Human Readable Format with option -lh • With combination of -lh option, shows sizes in human readable format.
- 6. • List Files in Reverse Order • The following command with ls -r option display files and directories in reverse order. • Shows version of ls command • Check version of ls command.
- 7. • Show Help Page • List help page of ls command with their option.
- 8. pwd command • pwd‘ stands for ‘Print Working Directory‘. As the name states, command ‘pwd‘ prints the current working directory or simply the directory user is, at present. It prints the current directory name with the complete path starting from root (/). This command is built in shell command and is available on most of the shell – bash, Bourne shell, ksh, zsh, etc. • Basic syntax of pwd: #pwd[option]
- 9. • If both ‘-L‘ and ‘-P‘ options are used, option ‘L‘ is taken into priority. If no option is specified at the prompt, pwd will avoid all symlinks, i.e., take option ‘-P‘ into account. • Note: A ‘pwd’ command is often used without options and never used with arguments. Options Description -L (logical) Use PWD from environment, even if it contains symbolic links -P (physical) Avoid all symbolic links –help Display this help and exit –version Output version information and exit
- 11. tty • tty is a place where the running command runs.
- 12. cat command • Syntax cat[option][file]… • Display Contains of File • In the below example, it will show contains of /etc/passwd file.
- 13. • View Contains of Multiple Files in terminal • In below example, it will display contains of test and test1 file in terminal.
- 14. • Create a File with Cat Command • We will create a file called test2 file with below command. • Awaits input from user, type desired text and press CTRL+D (hold down Ctrl Key and type ‘d‘) to exit. The text will be written in test2 file. You can see contains of file with following cat command.
- 15. • Use Cat Command with More & Less Options • If file having large number of contains that won’t fit in output terminal and screen scrolls up very fast, we can use parameters more and less with cat command as show above. • Display Line Numbers in File • With -n option you could see the line numbers of a file song.txt in the output terminal.
- 16. • Display Multiple Files at Once • In the below example we have three files test, test1 and test2 and able to view the contains of those file as shown above. We need to separate each file with ; (semi colon).
- 17. • Use Standard Output with Redirection Operator • We can redirect standard output of a file into a new file else existing file with ‘>‘ (greater than) symbol. Careful, existing contains of test1 will be overwritten by contains of test file. #cat test > test1 • Appending Standard Output with Redirection Operator • Appends in existing file with ‘>>‘ (double greater than) symbol. Here, contains of test file will be appended at the end of test1 file. #cat test >> test1 • Redirecting Multiple Files Contain in a Single File • This will create a file called test3 and all output will be redirected in a newly created file. #cat test test1 test2 > test3
- 18. who command • who command is a tool print information about users who are currently logged in. who command only see a real user who logged in. $who [options] [filename]
- 19. whoami command • whoami command is used both in Unix Operating System and as well as in Windows Operating System. • It is basically the concatenation of the strings “who”,”am”,”i” as whoami. • It displays the username of the current user when this command is invoked. • It is similar as running the id command with the options -un.
- 20. rm command • To run rm command, type rm followed by filename. Please remember, that by default rm will not ask any confirmation. • Remove a file # rm xyz.log • Remove multiple file with specific extension • If you have multiple file with the same extension and you want to delete them, you can use this syntax : # rm *.log
- 21. • Remove a directory • Removing directory is a little bit tricky. If you are sure that the directory is empty, then we can use -d parameter to remove it. # rm –d documents/ • But when the directory is not empty, you have to empty the directory first, or you can remove them recursively. To remove recursively, use -r or -R parameter. # rm –r documents/ • Add interactive confirmation before deleting • If you feel more comfortable to have interactive confirmation, you can use - i parameter with rm command. Here’s a sample of deleting directory recursively with interactive confirmation. # rm –ri documents/
- 22. mkdir command • Running mkdir without any parameter will create directory under the current directory • Create multiple directories #mkdir aa bb cc • Add directory include its sub-directory • When you want to created a include its sub-directory, you will need to use - p parameter. #mkdir –p aa/bb • Set access privilege • Using -m parameter, we can also set the access privilege for the new directory on- the-fly.
- 23. rmdir command • rmdir [OPTION] {directory-name} • To delete directory called foo #rmdir foo • Remove DIRECTORY and its ancestors • For example remove directory structure sales/99/march #rmdir –p sales/99/march
- 24. touch command • The touch command is a standard command used in UNIX/Linux operating system which is used to create, change and modify timestamps of a file. #touch filename • The file which is created can be viewed by ls command and to get more details about the file you can use long listing command ll or ls -l command . • Touch command to create multiple files: Touch command can be used to create the multiple numbers of files at the same time. These files would be empty while creation. #touch file1 file2 file3
- 25. cd command • Change from current directory to /usr/local. • Change from current directory to /usr/local/lib using absolute path.
- 26. • Change from current working directory to /usr/local/lib using relative path. • Move one directory back from where you are now.
- 27. • Change Current directory to parent directory. • Move to users home directory from anywhere.
- 28. cal command- display a calendar • A single parameter specifies the 4 digit year (1 - 9999) to be displayed. Two parameters denote the Month (1 - 12) and Year (1 - 9999). If arguments are not specified, the current month is displayed. A year starts on 01 Jan.
- 30. cat command- Append Data To a File
- 31. • Create another text file called bar.txt $ echo 'For desktop usage I prefer Apple OS X unix operating systems.' > bar.txt • Display both files on the screen, enter: $ cat foo.txt $ cat bar.txt • To append a contains of bar.txt to to foo.txt, enter: $ cat bar.txt >> foo.txt $ cat foo.txt • To append a ‘Use unix or die’ text to foo.txt file, enter: $ echo 'Use unix or die' >> foo.txt $ cat foo.txt
- 33. cat command- concatenation # sample.txt This is a sample text file # sample1.txt This is a another sample text file To concatenate two files. $ cat sample.txt sample1.txt > sample2.txt $ cat sample2.txt This is a sample text file This is a another sample text file
- 34. mv command • mv stands for move. mv is used to move one or more files or directories from one place to another in a file system like UNIX. It has two distinct functions: (i) It renames a file or folder. (ii) It moves a group of files to a different directory. • No additional space is consumed on a disk during renaming. This command normally works silently means no prompt for confirmation. • Syntax: mv [Option] source destination $ mv geek.txt b.txt
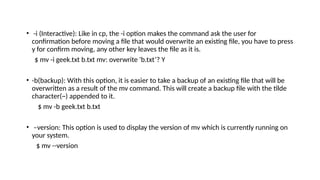
- 35. • -i (Interactive): Like in cp, the -i option makes the command ask the user for confirmation before moving a file that would overwrite an existing file, you have to press y for confirm moving, any other key leaves the file as it is. $ mv -i geek.txt b.txt mv: overwrite 'b.txt’? Y • -b(backup): With this option, it is easier to take a backup of an existing file that will be overwritten as a result of the mv command. This will create a backup file with the tilde character(~) appended to it. $ mv -b geek.txt b.txt • –version: This option is used to display the version of mv which is currently running on your system. $ mv --version
- 36. cp command- copy one or more files to another location. • Copy sample.txt to sample.bak $ cat sample.txt This is a sample file $ cp sample.txt sample.bak $ cat sample.bak This is a sample file • Copy sample directory to home directory $ cp -f /user/sample/* >
- 37. man command • man command in Linux is used to display the user manual of any command that we can run on the terminal. It provides a detailed view of the command which includes NAME, SYNOPSIS, DESCRIPTION, OPTIONS, EXIT STATUS, RETURN VALUES, ERRORS, FILES, VERSIONS, EXAMPLES, AUTHORS. • Syntax : $man [OPTION]... [COMMAND NAME]... eg. $ man printf
- 39. • $ man -f ls
- 40. chmod command • In Unix-like operating systems, the chmod command is used to change the access mode of a file. • The name is an abbreviation of change mode. • The references are used to distinguish the users to whom the permissions apply i.e. they are list of letters that specifies whom to give permissions. The references are represented by one or more of the following letters: • Reference Class Description u owner file's owner g group users who are members of the file's group o others users who are neither the file's owner nor members of the file's group a all All three of the above, same as ugo
- 41. • The operator is used to specify how the modes of a file should be adjusted. The following operators are accepted: • Operator Description + Adds the specified modes to the specified classes - Removes the specified modes from the specified classes = The modes specified are to be made the exact modes for the specified classes • The modes indicate which permissions are to be granted or removed from the specified classes. There are three basic modes which correspond to the basic permissions: r Permission to read the file. w Permission to write (or delete) the file. x Permission to execute the file, or, in the case of a directory, search it.
- 42. • change the assgn1_client.c permission so that the owner cannot write(w) in the file but can only read it. BEFORE: -rw-rw-r-- mik mik assgn1_client.c COMMAND: chmod u=r assgn1_client.c AFTER: -r--rw-r-- mik mik assgn1_client.c
- 43. grep command • The grep filter searches a file for a particular pattern of characters, and displays all lines that contain that pattern. The pattern that is searched in the file is referred to as the regular expression (grep stands for globally search for regular expression and print out). Syntax: # grep [options] pattern [files]
- 45. $cat > geekfile.txt unix is great os. unix is opensource. unix is free os. learn operating system. Unix linux which one you choose. uNix is easy to learn.unix is a multiuser os.Learn unix .unix is a powerful. Case insensitive search : The -i option enables to search for a string case insensitively in the give file. It matches the words like “UNIX”, “Unix”, “unix”. $grep -i "UNix" geekfile.txt Output: unix is great os. unix is opensource. unix is free os. Unix linux which one you choose. uNix is easy to learn.unix is a multiuser os.Learn unix .unix is
- 46. • Displaying the count of number of matches : We can find the number of lines that matches the given string/pattern $grep -c "unix" geekfile.txt Output: 2 • Display the file names that matches the pattern : We can just display the files that contains the given string/pattern. $grep -l "unix" * or $grep -l "unix" f1.txt f2.txt f3.xt f4.txt Output: geekfile.txt
- 47. tput command • tput utility uses the terminfo database to make the values of terminal-dependent capabilities and information available to the shell, to initialize or reset the terminal, or return the long name of the requested terminal type. • Set the Cursor Position using tput cup $ tput cup 2 3 • Clear the Screen Using tput clear $ tput clear • Get the Number of Columns and Lines of a Terminal $ tput cols • displays number of lines of your terminal screen $ tput lines • Change the Terminal Background Color using tput setb $ tput setb 4
- 48. bc command • bc command is used for command line calculator. It is similar to basic calculator by using which we can do basic mathematical calculations. • Arithmetic operations are the most basic in any kind of programming language. Linux or Unix operating system provides the bc command and expr command for doing arithmetic calculations. These commands are used in bash or shell script also for evaluating arithmetic expressions. Syntax: bc [ -hlwsqv ] [long-options] [ file ... ] Options: -h, {- -help } : Print the usage and exit -i, {- -interactive } : Force interactive mode -l, {- -mathlib } : Define the standard math library -w, {- -warn } : Give warnings for extensions to POSIX bc -s, {- -standard } : Process exactly the POSIX bc language -q, {- -quiet } : Do not print the normal GNU bc welcome -v, {- -version } : Print the version number and copyright and quit
- 49. • The bc command supports the following features: • Arithmetic operators • Increment or Decrement operators • Assignment operators • Comparison or Relational operators • Logical or Boolean operators • Math functions • Conditional statements • Iterative statements
- 50. $ echo "12+5" | bc Output 17 $ echo "10^2" | bc Output 100 $ echo "var=10;var" | bc Output 10 Assign 10 to the variable and print the value on the terminal. $ echo "var=10;var^=2;var" | bc Output 100 Squares the value of the variable and print the value on the terminal.







![pwd command
• pwd‘ stands for ‘Print Working Directory‘. As the name states,
command ‘pwd‘ prints the current working directory or simply the
directory user is, at present. It prints the current directory name with
the complete path starting from root (/). This command is built in
shell command and is available on most of the shell – bash, Bourne
shell, ksh, zsh, etc.
• Basic syntax of pwd:
#pwd[option]](https://image.slidesharecdn.com/shellcommands-250423042933-a26de539/85/various-shell-commands-in-unix-operating-system-pptx-8-320.jpg)



![cat command
• Syntax
cat[option][file]…
• Display Contains of File
• In the below example, it will show contains of /etc/passwd file.](https://image.slidesharecdn.com/shellcommands-250423042933-a26de539/85/various-shell-commands-in-unix-operating-system-pptx-12-320.jpg)





![who command
• who command is a tool print information about users who are
currently logged in. who command only see a real user who logged
in.
$who [options] [filename]](https://image.slidesharecdn.com/shellcommands-250423042933-a26de539/85/various-shell-commands-in-unix-operating-system-pptx-18-320.jpg)




![rmdir command
• rmdir [OPTION] {directory-name}
• To delete directory called foo
#rmdir foo
• Remove DIRECTORY and its ancestors
• For example remove directory structure sales/99/march
#rmdir –p sales/99/march](https://image.slidesharecdn.com/shellcommands-250423042933-a26de539/85/various-shell-commands-in-unix-operating-system-pptx-23-320.jpg)










![mv command
• mv stands for move. mv is used to move one or more files or directories from one
place to another in a file system like UNIX. It has two distinct functions:
(i) It renames a file or folder.
(ii) It moves a group of files to a different directory.
• No additional space is consumed on a disk during renaming. This command normally
works silently means no prompt for confirmation.
• Syntax:
mv [Option] source destination
$ mv geek.txt b.txt](https://image.slidesharecdn.com/shellcommands-250423042933-a26de539/85/various-shell-commands-in-unix-operating-system-pptx-34-320.jpg)

![man command
• man command in Linux is used to display the user manual of any
command that we can run on the terminal. It provides a detailed
view of the command which includes NAME, SYNOPSIS,
DESCRIPTION, OPTIONS, EXIT STATUS, RETURN VALUES, ERRORS,
FILES, VERSIONS, EXAMPLES, AUTHORS.
• Syntax :
$man [OPTION]... [COMMAND NAME]...
eg.
$ man printf](https://image.slidesharecdn.com/shellcommands-250423042933-a26de539/85/various-shell-commands-in-unix-operating-system-pptx-37-320.jpg)





![grep command
• The grep filter searches a file for a particular pattern of characters,
and displays all lines that contain that pattern. The pattern that is
searched in the file is referred to as the regular expression (grep
stands for globally search for regular expression and print out).
Syntax:
# grep [options] pattern [files]](https://image.slidesharecdn.com/shellcommands-250423042933-a26de539/85/various-shell-commands-in-unix-operating-system-pptx-43-320.jpg)




![bc command
• bc command is used for command line calculator. It is similar to basic calculator by using which we can
do basic mathematical calculations.
• Arithmetic operations are the most basic in any kind of programming language. Linux or Unix operating
system provides the bc command and expr command for doing arithmetic calculations. These
commands are used in bash or shell script also for evaluating arithmetic expressions.
Syntax:
bc [ -hlwsqv ] [long-options] [ file ... ]
Options:
-h, {- -help } : Print the usage and exit
-i, {- -interactive } : Force interactive mode
-l, {- -mathlib } : Define the standard math library
-w, {- -warn } : Give warnings for extensions to POSIX bc
-s, {- -standard } : Process exactly the POSIX bc language
-q, {- -quiet } : Do not print the normal GNU bc welcome
-v, {- -version } : Print the version number and copyright and quit](https://image.slidesharecdn.com/shellcommands-250423042933-a26de539/85/various-shell-commands-in-unix-operating-system-pptx-48-320.jpg)

















































