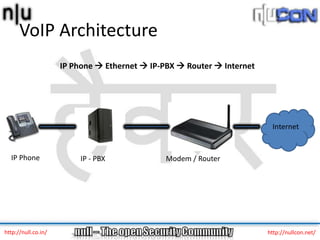
VoIP – vulnerabilities and attacks
Download as PPTX, PDF11 likes16,987 views
The document discusses vulnerabilities and attacks against Voice over IP (VoIP) systems. It begins with an introduction to VoIP architecture, components, and protocols. It then covers vulnerabilities and common attack vectors against VoIP, such as identity spoofing, eavesdropping, password cracking, and denial of service attacks. The document demonstrates some example attacks and outlines tools that can be used for scanning, attacking, and testing the security of VoIP systems. It concludes with recommendations for countermeasures like firewalls, encryption, and network hardening to better secure VoIP infrastructures.
1 of 30
Downloaded 468 times





























Ad
Recommended
VoIP Wars: Attack of the Cisco Phones



VoIP Wars: Attack of the Cisco PhonesFatih Ozavci This document discusses security vulnerabilities in hosted VoIP environments. It summarizes techniques for attacking Cisco phones and VoIP infrastructure, including spoofing caller ID, manipulating SIP trust relationships, and escalating privileges on Cisco Unified Communications Manager and VOSS Domain Manager services. The document outlines methods for gaining persistent access to networks and manipulating call forwarding, speed dials and other phone settings.
Voip security



Voip securityShethwala Ridhvesh This document discusses security issues and solutions related to Voice over IP (VoIP) systems. It begins with an introduction to VoIP and how it works, describing the protocols used including SIP, H.323, MGCP and RTP. It then outlines various security attacks on VoIP systems such as eavesdropping, denial of service attacks, and masquerading. Finally, it discusses approaches to enhancing VoIP security, including using encryption, firewalls, authentication, and secure protocols like SRTP.
Introduction into SIP protocol



Introduction into SIP protocolMichal Hrncirik Brief introduction into SIP protocol, how it works, common problems to solve. Tech. details about handshake, SIP Trunks and SIP trunking. Market research.
VoIP Security



VoIP SecurityDayanand Prabhakar This presentation describes the summary of VoIP infrastructure and related vulnerabilities and security concerns.
Assaulting diameter IPX network



Assaulting diameter IPX networkAlexandre De Oliveira Diameter protocol has been introduced to replace in many aspects SS7/SIGTRAN in the LTE and VoLTE networks, and such as these 2G/3G networks, Diameter also has its dedicated global roaming network named IPX (IP eXchange) that allows international roaming for LTE users..
Back in the days Diameter was already used by the PCRF in 2G/3G networks for charging purposes, but its usage has been extended to completely replace the signalization role of SS7/SIGTRAN in LTE networks. SS7/SIGTRAN security flows are now public after several publications, but what about Diameter security ? By replacing old and insecure protocols, does Diameter come with built-in security?
During the presentation, we will study how the IPX infrastructure operates and how security is taken into account nowadays regarding the newest 4G telecom technologies. Getting into different point of view allowed us to find major Diameter vulnerabilities via the IPX, which affect almost all the network elements HSS, MME, GMLC, PCRF, PDN GW, including DNS serving telecom TLDs. Understanding the mistakes that led to a former generation of telecom networks we came out with insecure protocols will maybe help us to push security by design in the future.
Nevertheless, as a telecom provider we will provide recommendations to secure LTE infrastructures and share technical countermeasures we have implemented against different Diameter attacks and fraud scenarios to protect our network and customers. Along with recommendations, we will present some ways on how to self audit and do self monitoring of your network, as we consider that telecom providers need to take back the control of their networks!
Troopers website link: https://www.troopers.de/events/troopers16/653_assaulting_ipx_diameter_roaming_network/
CCNA 1 Routing and Switching v5.0 Chapter 1



CCNA 1 Routing and Switching v5.0 Chapter 1Nil Menon This document summarizes key points from Chapter 1 of a Cisco networking textbook. It introduces networking concepts like LANs, WANs and the Internet. It discusses how networks are used in daily life for communication, work and entertainment. It also outlines trends that will impact networks, such as BYOD, online collaboration, video and cloud computing. The chapter objectives are to explain network topologies, devices and characteristics used in small to medium businesses.
Presentation of H323 protocol



Presentation of H323 protocolMd. Taiseen Azam H.323 is a standard for multimedia communications over packet-based networks. It defines protocols for real-time audio, video and data communications between endpoints such as terminals, gateways and multipoint control units. As an umbrella standard, H.323 references other protocols for functions like call signaling, bandwidth negotiation and transmission of audio and video data. H.323 provides scalable and flexible multimedia communication capabilities and has been widely adopted for voice and video conferencing over both internet and private networks.
SIP - The Basics



SIP - The BasicsJonas Borjesson SIP is a protocol for setting up and managing sessions over the internet, including voice and video calls. It allows users to locate each other and establish communication sessions between endpoints. SIP sets up sessions but does not handle the actual media, like audio, which is transported separately using protocols like RTP. SIP works by routing request and response messages between user agents through proxies and servers to initiate, negotiate, and terminate communication sessions.
Hacking SIP Like a Boss!



Hacking SIP Like a Boss!Fatih Ozavci This is my Athcon 2013 slide set. I also demonstrated that attacking mobile applications via SIP Trust, scanning via SIP proxies and MITM fuzzing in Live Demo.
5G Network Slicing



5G Network SlicingSridhar Bhaskaran Network slicing in 5G allows a single UE to connect to multiple network slices simultaneously. Each slice is identified by a Specific Network Slice Selection Assistance Information (S-NSSAI). The 5G core uses the S-NSSAI to select the appropriate functions like the Session Management Function (SMF) for each slice. This enables isolation of services and network functions on a per-slice basis. The Access and Mobility Management Function (AMF) is common across all slices, but the SMF and User Plane Function (UPF) can differ per slice. This facilitates customized network slices for different use cases and isolation of traffic and functions.
Sip Detailed , Call flows , Architecture descriptions , SIP services , sip se...



Sip Detailed , Call flows , Architecture descriptions , SIP services , sip se...ALTANAI BISHT The presentation is a compiled assembly from the SIP RFC' s, and original works of Alan Johnston and Henry Sinnreich . It contains Sip Detailed , Call flows , Architecture descriptions , SIP services , sip security , sip programming.
Understanding Session Border Controllers



Understanding Session Border Controllersstefansayer Over the past 10 years the Session Initiation Protocol (SIP) has moved from the toy of researchers and academics to the de-facto standard for telephony and multimedia services in mobile and fixed networks.
Probably one of the most emotionally fraught discussions in the context of SIP was whether Session Border Controllers (SBC) are good or evil.
SIP was designed with the vision of revolutionizing the way communication services are developed, deployed and operated. Following the end-to-end spirit of the Internet SIP was supposed to turn down the walled gardens of PSTN networks and free communication services from the grip of large telecom operators. By moving the intelligence to the end systems, developers were supposed to be able to develop new communication services that will innovate the way we communicate with each other.
This was to be achieved without having to wait for the approval of the various telecommunication standardization groups such as ETSI or the support of incumbent telecoms.
Session border controllers are usually implemented as SIP Back-to-Back User Agents (B2BUA) that are placed between a SIP user agent and a SIP proxy. The SBC then acts as the contact point for both the user agents and the proxy. Thereby the SBC actually breaks the end-to-end behavior of SIP, which has led various people to deem the SBC as an evil incarnation of the old telecom way of thinking. Regardless of this opposition, SBCs have become a central part of any SIP deployment.
In this paper we will first give a brief overview of how SIP works and continue with a description of what SBCs do and the different use cases for deploying SBCs.
3GPP IMS



3GPP IMSChris Venteicher The document discusses 3GPP IMS (Internet Multimedia Core Network Subsystem), which defines standards for replacing GSM signaling with VoIP/SIP. IMS enables seamless integration of cellular voice services with wired VoIP and other IP services. Key components of IMS include the Proxy-CSCF, Serving-CSCF, and Interrogating-CSCF. The document outlines common call flows for registration, mobile-originated calls, and delivery of multimedia session capabilities between endpoints. IMS represents one of the largest planned VoIP/SIP deployments and helps drive adoption of new multimedia services on cellular networks.
Telnet & SSH Configuration



Telnet & SSH ConfigurationVinod Gour Telnet and SSH configuration on ubuntu and windows. this presentation show how we can configure telnet and ssh on windows and linux and what additional software we will have to required.
SIP Testing with FreeSWITCH



SIP Testing with FreeSWITCHMoises Silva This document provides an overview and introduction to SIP testing using FreeSWITCH. It discusses using FreeSWITCH to test other SIP systems by generating calls with various codecs and protocols. The document outlines an agenda for functionality tests, load tests, and security tests. Functionality tests are recommended to verify expected SIP behaviors and identify key functionality to automate test scenarios for. SIPp is introduced as a tool for low-level SIP performance and functionality testing, though it requires a strong understanding of SIP. The document emphasizes the importance of testing and provides resources for open-source testing tools.
5G Security Briefing



5G Security Briefing3G4G A detailed look at 5G security by experts from wenovator, Dr. Anand R. Prasad & Hans Christian Rudolph.
This webinar covers:
(1) 5G security
(2) Private networks security and
(3) Open vRAN security
To learn more about wenovator, visit their website: https://www.wenovator.com/
All our #3G4G5G slides and videos are available at:
Videos: https://www.youtube.com/3G4G5G
Slides: https://www.slideshare.net/3G4GLtd
Security Page: https://www.3g4g.co.uk/Security/
5G Page: https://www.3g4g.co.uk/5G/
Security Blog Posts: https://blog.3g4g.co.uk/search/label/Security
Free Training Videos: https://www.3g4g.co.uk/Training/
Wireless security presentation



Wireless security presentationMuhammad Zia This document discusses security issues with wireless networks and protocols. It describes common wireless standards like 802.11b, g, and a. It then covers security protocols that aimed to improve on WEP like WPA and WPA2, discussing their encryption methods. The document also outlines various threats to wireless security like eavesdropping, unauthorized access, and denial of service attacks. It concludes by listing some common wireless hacking tools.
Session initiation-protocol



Session initiation-protocolSanthosh Somu The document discusses the Session Initiation Protocol (SIP), which allows for multimedia communication sessions over IP networks. SIP establishes sessions for voice, video, messaging and other applications. It uses requests and responses to initiate sessions between users, locate users, invite them to sessions, and terminate sessions. SIP relies on user agents, proxy servers, redirect servers and registrar servers. It enables mobility and flexibility in setting up and modifying communication sessions across different devices.
Ims, Ip Multimedia System



Ims, Ip Multimedia Systemmanymbaboy The document provides an overview of IMS (IP Multimedia Subsystem), including its history, architecture, layers, benefits, and relationship to SIP (Session Initiation Protocol). IMS allows convergence of voice, video, and data over an IP-based network using SIP and other IETF protocols. It has a service plane for applications, a control plane for session management, and a media plane for transport.
MGCP Overview



MGCP OverviewWilliam Lee MGCP is a protocol used to control media gateways that convert between audio signals and data packets. It uses a master-slave architecture with a media gateway controlled by a call agent. MGCP commands include CRCX to create connections, MDCX to modify them, and DLCX to delete them. Basic call flows include the media gateway registering with the call agent, creating a call by requesting digits and notifying of events, and terminating a call by deleting connections on hook events.
Network security 10EC832 vtu notes



Network security 10EC832 vtu notesJayanth Dwijesh H P NETWORK SECURITY
UNIT - 1
Services, mechanisms and attacks, The OSI security architecture, A model for network security. 6 Hrs
UNIT - 2
SYMMETRIC CIPHERS: Symmetric Cipher Model, Substitution Techniques, Transposition Techniques, Simplified DES, Data encryption standard (DES), The strength of DES, Differential and Linear Cryptanalysis, Block Cipher Design Principles and Modes of Operation, Evaluation Criteria for Advanced Encryption Standard, The AES Cipher. 7 Hrs
UNIT - 3
Principles of Public-Key Cryptosystems, The RSA algorithm, Key Management, Diffie - Hellman Key Exchange, Elliptic Curve Arithmetic, Authentication functions, Hash Functions. 6 Hrs
UNIT - 4
Digital signatures, Authentication Protocols, Digital Signature Standard. 7 Hrs
UNIT - 5
Web Security Consideration, Security socket layer (SSL) and Transport layer security, Secure Electronic Transaction. 6 Hrs
UNIT - 6
Intruders, Intrusion Detection, Password Management. 6 Hrs
UNIT - 7
MALICIOUS SOFTWARE: Viruses and Related Threats, Virus Countermeasures. 7 Hrs
UNIT - 8
Firewalls Design Principles, Trusted Systems. 6 Hrs
TEXT BOOK:
1. Cryptography and Network Security, William Stalling, Pearson Education, 2003.
REFERENCE BOOKS:
1. Cryptography and Network Security, Behrouz A. Forouzan, TMH, 2007.
2. Cryptography and Network Security, Atul Kahate, TMH, 2003.
Indroduction to SIP



Indroduction to SIPChien Cheng Wu SIP is a signaling protocol used to establish multimedia sessions over IP networks. It allows clients to discover each other and establish communication sessions for voice, video, or other multimedia applications. The document provides an introduction to key SIP concepts including logical entities, request/response messages, basic call flows, and the SDP protocol for negotiating media parameters. It also describes how Wireshark can be used as a development tool to analyze SIP signaling packets.
Internet Traffic Monitoring and Analysis



Internet Traffic Monitoring and AnalysisInformation Technology This document discusses internet traffic monitoring and analysis. It describes:
1) The growth of internet usage and evolving network environments that require reliable monitoring.
2) Real-world applications of monitoring including network usage analysis, planning, SLA monitoring, and security attack detection.
3) POSTECH's research activities including MRTG+, WebTrafMon, and their next-generation system NG-MON for high-speed monitoring.
WPA2



WPA2Mshari Alabdulkarim WPA2 is the latest security standard for Wi-Fi networks. It uses AES encryption and 802.1X/EAP authentication to securely transmit data between wireless devices and access points. The four phase process establishes a secure communication context through agreeing on security policies, generating a master key, creating temporary keys, and using the keys to encrypt transmissions. WPA2 provides stronger security than previous standards like WEP and WPA through more robust encryption and authentication methods.
Root via sms. 4G security assessment 



Root via sms. 4G security assessment Sergey Gordeychik Having developed a test set, we started to research how safe it is for clients to use 4G networks of the telecommunication companies. During the research we have tested SIM-cards, 4G USB modems, radio components, IP access network. First of all we looked for the vulnerabilities that could be exploited remotely, via IP or radio network.
And the result was not late in arriving. In some cases we managed to attack SIM-cards and install a malicious Java applet there, we were able to update remotely USB modem firmware, to change password on a selfcare portal via SMS and even to get access to the internal technological network of a carrier.
Further attack evolution helped to understand how it is possible to use a simple SMS as an exploit that is able not only to compromise a USB modem and all the communications that go through it, but also to install bootkit on a box, that this modem is connected to.
Security Information and Event Management (SIEM)



Security Information and Event Management (SIEM)k33a This document provides an overview of security information and event management (SIEM). It defines SIEM as software and services that combine security information management (SIM) and security event management (SEM). The key objectives of SIEM are to identify threats and breaches, collect audit logs for security and compliance, and conduct investigations. SIEM solutions centralize log collection, correlate events in real-time, generate reports, and provide log retention, forensics and compliance reporting capabilities. The document discusses typical SIEM features, architecture, deployment options, and reasons for SIEM implementation failures.
Dipping to MNP DB



Dipping to MNP DBBangladesh Network Operators Group Recently as per the initiative of BTRC all telecom operator shifted to the Mobile Number Portability (MNP) platform. In this scenario, any subscriber can change operator without changing his/her current number including the prefix. In order to do that, there has been established a central MNP database. All operators require to up to date with this database and perform query for each of their outbound call. MNP database will give the information of current recipient and donor operator routing code. Operator requires to query the current recipient routing code before sending call to the ICX. In this paper, authors target is to give suggestion how to keep this local MNP database up to date and synchronize with the central database. Further, how this local database can be used for dipping to generate outbound calls to current recipient operator using opensource SIP Server and Session Border Controller (SBC). To perform that, authors shows how to use asterisk as dipping server using AGI scripting and it will be used as Back to Back User Agent (B2BUA). Also shows how kamailio an open source SIP Express Router (SER) can be used to perform MNP dipping to MySQL database. Finally, after the implementation of MNP service although calling service is working fine but most ported numbers did not receive the SMS specially OTP. Therefore, on these context author's shows how to create secure post API to perform the dipping to local MNP database from SMS gateway to connect to the original routing number before sending the SMS to client. Here, API will return the current recipient, donor code and routing number to send SMS as JSON data format against a normal cell phone number.
Ipsec



IpsecRupesh Mishra This document provides an overview of IPSec, including:
- IPSec aims to secure IP communications by providing authentication, integrity, and confidentiality. It operates in transport and tunnel modes.
- The Internet Key Exchange (IKE) negotiates and establishes security associations to secure communications between two endpoints.
- IPSec policy defines which encryption, hashing, and authentication methods apply to different network traffic using protection suites and proposals.
The Art of VoIP Hacking - Defcon 23 Workshop



The Art of VoIP Hacking - Defcon 23 WorkshopFatih Ozavci VoIP attacks have evolved, and they are targeting Unified Communications (UC), commercial services, hosted environment and call centres using major vendor and protocol vulnerabilities. This workshop is designed to demonstrate these cutting edge VoIP attacks, and improve the VoIP skills of the incident response teams, penetration testers and network engineers. Signalling protocols are the centre of UC environments, but also susceptible to IP spoofing, trust issues, call spoofing, authentication bypass and invalid signalling flows. They can be hacked with legacy techniques, but a set of new attacks will be demonstrated in this workshop. This workshop includes basic attack types for UC infrastructure, advanced attacks to the SIP and Skinny protocol weaknesses, network infrastructure attacks, value added services analysis, Cdr/Log/Billing analysis and Viproy use to analyse signalling services using novel techniques. Also the well-known attacks to the network infrastructure will be combined with the current VoIP vulnerabilities to test the target workshop network. Attacking VoIP services requires limited knowledge today with the Viproy Penetration Testing Kit (written by Fatih). It has a dozen modules to test trust hacking issues, information collected from SIP and Skinny services, gaining unauthorised access, call redirection, call spoofing, brute-forcing VoIP accounts, Cisco CUCDM exploitation and debugging services using as MITM. Furthermore, Viproy provides these attack modules in the Metasploit Framework environment with full integration. The workshop contains live demonstration of practical VoIP attacks and usage of the Viproy modules.
In this hands-on workshop, attendees will learn about basic attack types for UC infrastructure, advanced attacks to the SIP protocol weaknesses, Cisco Skinny protocol hacking, hacking Cisco CUCDM and CUCM servers, network infrastructure attacks, value added services analysis, Cdr/Log/Billing analysis and Viproy VoIP pen-test kit to analyse VoIP services using novel techniques. New CDP, CUCDM and Cisco Skinny modules and techniques of Viproy will be demonstrated in the workshop as well.
Voice Over IP (VoIP)



Voice Over IP (VoIP)habib_786 VoIP allows users to make phone calls using an Internet connection instead of a traditional phone line. It works by converting voice signals to digital data that is transmitted in packets over the Internet. A VoIP network uses protocols like SIP and RTP to setup calls and transmit voice data. Components include VoIP protocols, gateways to interface with the PSTN, and codecs to compress voice signals. Businesses are attracted to VoIP as it can help reduce costs while improving utilization of bandwidth and network management. However, security risks like hacking and eavesdropping exist since VoIP uses the public Internet.
Ad
More Related Content
What's hot (20)
Hacking SIP Like a Boss!



Hacking SIP Like a Boss!Fatih Ozavci This is my Athcon 2013 slide set. I also demonstrated that attacking mobile applications via SIP Trust, scanning via SIP proxies and MITM fuzzing in Live Demo.
5G Network Slicing



5G Network SlicingSridhar Bhaskaran Network slicing in 5G allows a single UE to connect to multiple network slices simultaneously. Each slice is identified by a Specific Network Slice Selection Assistance Information (S-NSSAI). The 5G core uses the S-NSSAI to select the appropriate functions like the Session Management Function (SMF) for each slice. This enables isolation of services and network functions on a per-slice basis. The Access and Mobility Management Function (AMF) is common across all slices, but the SMF and User Plane Function (UPF) can differ per slice. This facilitates customized network slices for different use cases and isolation of traffic and functions.
Sip Detailed , Call flows , Architecture descriptions , SIP services , sip se...



Sip Detailed , Call flows , Architecture descriptions , SIP services , sip se...ALTANAI BISHT The presentation is a compiled assembly from the SIP RFC' s, and original works of Alan Johnston and Henry Sinnreich . It contains Sip Detailed , Call flows , Architecture descriptions , SIP services , sip security , sip programming.
Understanding Session Border Controllers



Understanding Session Border Controllersstefansayer Over the past 10 years the Session Initiation Protocol (SIP) has moved from the toy of researchers and academics to the de-facto standard for telephony and multimedia services in mobile and fixed networks.
Probably one of the most emotionally fraught discussions in the context of SIP was whether Session Border Controllers (SBC) are good or evil.
SIP was designed with the vision of revolutionizing the way communication services are developed, deployed and operated. Following the end-to-end spirit of the Internet SIP was supposed to turn down the walled gardens of PSTN networks and free communication services from the grip of large telecom operators. By moving the intelligence to the end systems, developers were supposed to be able to develop new communication services that will innovate the way we communicate with each other.
This was to be achieved without having to wait for the approval of the various telecommunication standardization groups such as ETSI or the support of incumbent telecoms.
Session border controllers are usually implemented as SIP Back-to-Back User Agents (B2BUA) that are placed between a SIP user agent and a SIP proxy. The SBC then acts as the contact point for both the user agents and the proxy. Thereby the SBC actually breaks the end-to-end behavior of SIP, which has led various people to deem the SBC as an evil incarnation of the old telecom way of thinking. Regardless of this opposition, SBCs have become a central part of any SIP deployment.
In this paper we will first give a brief overview of how SIP works and continue with a description of what SBCs do and the different use cases for deploying SBCs.
3GPP IMS



3GPP IMSChris Venteicher The document discusses 3GPP IMS (Internet Multimedia Core Network Subsystem), which defines standards for replacing GSM signaling with VoIP/SIP. IMS enables seamless integration of cellular voice services with wired VoIP and other IP services. Key components of IMS include the Proxy-CSCF, Serving-CSCF, and Interrogating-CSCF. The document outlines common call flows for registration, mobile-originated calls, and delivery of multimedia session capabilities between endpoints. IMS represents one of the largest planned VoIP/SIP deployments and helps drive adoption of new multimedia services on cellular networks.
Telnet & SSH Configuration



Telnet & SSH ConfigurationVinod Gour Telnet and SSH configuration on ubuntu and windows. this presentation show how we can configure telnet and ssh on windows and linux and what additional software we will have to required.
SIP Testing with FreeSWITCH



SIP Testing with FreeSWITCHMoises Silva This document provides an overview and introduction to SIP testing using FreeSWITCH. It discusses using FreeSWITCH to test other SIP systems by generating calls with various codecs and protocols. The document outlines an agenda for functionality tests, load tests, and security tests. Functionality tests are recommended to verify expected SIP behaviors and identify key functionality to automate test scenarios for. SIPp is introduced as a tool for low-level SIP performance and functionality testing, though it requires a strong understanding of SIP. The document emphasizes the importance of testing and provides resources for open-source testing tools.
5G Security Briefing



5G Security Briefing3G4G A detailed look at 5G security by experts from wenovator, Dr. Anand R. Prasad & Hans Christian Rudolph.
This webinar covers:
(1) 5G security
(2) Private networks security and
(3) Open vRAN security
To learn more about wenovator, visit their website: https://www.wenovator.com/
All our #3G4G5G slides and videos are available at:
Videos: https://www.youtube.com/3G4G5G
Slides: https://www.slideshare.net/3G4GLtd
Security Page: https://www.3g4g.co.uk/Security/
5G Page: https://www.3g4g.co.uk/5G/
Security Blog Posts: https://blog.3g4g.co.uk/search/label/Security
Free Training Videos: https://www.3g4g.co.uk/Training/
Wireless security presentation



Wireless security presentationMuhammad Zia This document discusses security issues with wireless networks and protocols. It describes common wireless standards like 802.11b, g, and a. It then covers security protocols that aimed to improve on WEP like WPA and WPA2, discussing their encryption methods. The document also outlines various threats to wireless security like eavesdropping, unauthorized access, and denial of service attacks. It concludes by listing some common wireless hacking tools.
Session initiation-protocol



Session initiation-protocolSanthosh Somu The document discusses the Session Initiation Protocol (SIP), which allows for multimedia communication sessions over IP networks. SIP establishes sessions for voice, video, messaging and other applications. It uses requests and responses to initiate sessions between users, locate users, invite them to sessions, and terminate sessions. SIP relies on user agents, proxy servers, redirect servers and registrar servers. It enables mobility and flexibility in setting up and modifying communication sessions across different devices.
Ims, Ip Multimedia System



Ims, Ip Multimedia Systemmanymbaboy The document provides an overview of IMS (IP Multimedia Subsystem), including its history, architecture, layers, benefits, and relationship to SIP (Session Initiation Protocol). IMS allows convergence of voice, video, and data over an IP-based network using SIP and other IETF protocols. It has a service plane for applications, a control plane for session management, and a media plane for transport.
MGCP Overview



MGCP OverviewWilliam Lee MGCP is a protocol used to control media gateways that convert between audio signals and data packets. It uses a master-slave architecture with a media gateway controlled by a call agent. MGCP commands include CRCX to create connections, MDCX to modify them, and DLCX to delete them. Basic call flows include the media gateway registering with the call agent, creating a call by requesting digits and notifying of events, and terminating a call by deleting connections on hook events.
Network security 10EC832 vtu notes



Network security 10EC832 vtu notesJayanth Dwijesh H P NETWORK SECURITY
UNIT - 1
Services, mechanisms and attacks, The OSI security architecture, A model for network security. 6 Hrs
UNIT - 2
SYMMETRIC CIPHERS: Symmetric Cipher Model, Substitution Techniques, Transposition Techniques, Simplified DES, Data encryption standard (DES), The strength of DES, Differential and Linear Cryptanalysis, Block Cipher Design Principles and Modes of Operation, Evaluation Criteria for Advanced Encryption Standard, The AES Cipher. 7 Hrs
UNIT - 3
Principles of Public-Key Cryptosystems, The RSA algorithm, Key Management, Diffie - Hellman Key Exchange, Elliptic Curve Arithmetic, Authentication functions, Hash Functions. 6 Hrs
UNIT - 4
Digital signatures, Authentication Protocols, Digital Signature Standard. 7 Hrs
UNIT - 5
Web Security Consideration, Security socket layer (SSL) and Transport layer security, Secure Electronic Transaction. 6 Hrs
UNIT - 6
Intruders, Intrusion Detection, Password Management. 6 Hrs
UNIT - 7
MALICIOUS SOFTWARE: Viruses and Related Threats, Virus Countermeasures. 7 Hrs
UNIT - 8
Firewalls Design Principles, Trusted Systems. 6 Hrs
TEXT BOOK:
1. Cryptography and Network Security, William Stalling, Pearson Education, 2003.
REFERENCE BOOKS:
1. Cryptography and Network Security, Behrouz A. Forouzan, TMH, 2007.
2. Cryptography and Network Security, Atul Kahate, TMH, 2003.
Indroduction to SIP



Indroduction to SIPChien Cheng Wu SIP is a signaling protocol used to establish multimedia sessions over IP networks. It allows clients to discover each other and establish communication sessions for voice, video, or other multimedia applications. The document provides an introduction to key SIP concepts including logical entities, request/response messages, basic call flows, and the SDP protocol for negotiating media parameters. It also describes how Wireshark can be used as a development tool to analyze SIP signaling packets.
Internet Traffic Monitoring and Analysis



Internet Traffic Monitoring and AnalysisInformation Technology This document discusses internet traffic monitoring and analysis. It describes:
1) The growth of internet usage and evolving network environments that require reliable monitoring.
2) Real-world applications of monitoring including network usage analysis, planning, SLA monitoring, and security attack detection.
3) POSTECH's research activities including MRTG+, WebTrafMon, and their next-generation system NG-MON for high-speed monitoring.
WPA2



WPA2Mshari Alabdulkarim WPA2 is the latest security standard for Wi-Fi networks. It uses AES encryption and 802.1X/EAP authentication to securely transmit data between wireless devices and access points. The four phase process establishes a secure communication context through agreeing on security policies, generating a master key, creating temporary keys, and using the keys to encrypt transmissions. WPA2 provides stronger security than previous standards like WEP and WPA through more robust encryption and authentication methods.
Root via sms. 4G security assessment 



Root via sms. 4G security assessment Sergey Gordeychik Having developed a test set, we started to research how safe it is for clients to use 4G networks of the telecommunication companies. During the research we have tested SIM-cards, 4G USB modems, radio components, IP access network. First of all we looked for the vulnerabilities that could be exploited remotely, via IP or radio network.
And the result was not late in arriving. In some cases we managed to attack SIM-cards and install a malicious Java applet there, we were able to update remotely USB modem firmware, to change password on a selfcare portal via SMS and even to get access to the internal technological network of a carrier.
Further attack evolution helped to understand how it is possible to use a simple SMS as an exploit that is able not only to compromise a USB modem and all the communications that go through it, but also to install bootkit on a box, that this modem is connected to.
Security Information and Event Management (SIEM)



Security Information and Event Management (SIEM)k33a This document provides an overview of security information and event management (SIEM). It defines SIEM as software and services that combine security information management (SIM) and security event management (SEM). The key objectives of SIEM are to identify threats and breaches, collect audit logs for security and compliance, and conduct investigations. SIEM solutions centralize log collection, correlate events in real-time, generate reports, and provide log retention, forensics and compliance reporting capabilities. The document discusses typical SIEM features, architecture, deployment options, and reasons for SIEM implementation failures.
Dipping to MNP DB



Dipping to MNP DBBangladesh Network Operators Group Recently as per the initiative of BTRC all telecom operator shifted to the Mobile Number Portability (MNP) platform. In this scenario, any subscriber can change operator without changing his/her current number including the prefix. In order to do that, there has been established a central MNP database. All operators require to up to date with this database and perform query for each of their outbound call. MNP database will give the information of current recipient and donor operator routing code. Operator requires to query the current recipient routing code before sending call to the ICX. In this paper, authors target is to give suggestion how to keep this local MNP database up to date and synchronize with the central database. Further, how this local database can be used for dipping to generate outbound calls to current recipient operator using opensource SIP Server and Session Border Controller (SBC). To perform that, authors shows how to use asterisk as dipping server using AGI scripting and it will be used as Back to Back User Agent (B2BUA). Also shows how kamailio an open source SIP Express Router (SER) can be used to perform MNP dipping to MySQL database. Finally, after the implementation of MNP service although calling service is working fine but most ported numbers did not receive the SMS specially OTP. Therefore, on these context author's shows how to create secure post API to perform the dipping to local MNP database from SMS gateway to connect to the original routing number before sending the SMS to client. Here, API will return the current recipient, donor code and routing number to send SMS as JSON data format against a normal cell phone number.
Ipsec



IpsecRupesh Mishra This document provides an overview of IPSec, including:
- IPSec aims to secure IP communications by providing authentication, integrity, and confidentiality. It operates in transport and tunnel modes.
- The Internet Key Exchange (IKE) negotiates and establishes security associations to secure communications between two endpoints.
- IPSec policy defines which encryption, hashing, and authentication methods apply to different network traffic using protection suites and proposals.
Viewers also liked (20)
The Art of VoIP Hacking - Defcon 23 Workshop



The Art of VoIP Hacking - Defcon 23 WorkshopFatih Ozavci VoIP attacks have evolved, and they are targeting Unified Communications (UC), commercial services, hosted environment and call centres using major vendor and protocol vulnerabilities. This workshop is designed to demonstrate these cutting edge VoIP attacks, and improve the VoIP skills of the incident response teams, penetration testers and network engineers. Signalling protocols are the centre of UC environments, but also susceptible to IP spoofing, trust issues, call spoofing, authentication bypass and invalid signalling flows. They can be hacked with legacy techniques, but a set of new attacks will be demonstrated in this workshop. This workshop includes basic attack types for UC infrastructure, advanced attacks to the SIP and Skinny protocol weaknesses, network infrastructure attacks, value added services analysis, Cdr/Log/Billing analysis and Viproy use to analyse signalling services using novel techniques. Also the well-known attacks to the network infrastructure will be combined with the current VoIP vulnerabilities to test the target workshop network. Attacking VoIP services requires limited knowledge today with the Viproy Penetration Testing Kit (written by Fatih). It has a dozen modules to test trust hacking issues, information collected from SIP and Skinny services, gaining unauthorised access, call redirection, call spoofing, brute-forcing VoIP accounts, Cisco CUCDM exploitation and debugging services using as MITM. Furthermore, Viproy provides these attack modules in the Metasploit Framework environment with full integration. The workshop contains live demonstration of practical VoIP attacks and usage of the Viproy modules.
In this hands-on workshop, attendees will learn about basic attack types for UC infrastructure, advanced attacks to the SIP protocol weaknesses, Cisco Skinny protocol hacking, hacking Cisco CUCDM and CUCM servers, network infrastructure attacks, value added services analysis, Cdr/Log/Billing analysis and Viproy VoIP pen-test kit to analyse VoIP services using novel techniques. New CDP, CUCDM and Cisco Skinny modules and techniques of Viproy will be demonstrated in the workshop as well.
Voice Over IP (VoIP)



Voice Over IP (VoIP)habib_786 VoIP allows users to make phone calls using an Internet connection instead of a traditional phone line. It works by converting voice signals to digital data that is transmitted in packets over the Internet. A VoIP network uses protocols like SIP and RTP to setup calls and transmit voice data. Components include VoIP protocols, gateways to interface with the PSTN, and codecs to compress voice signals. Businesses are attracted to VoIP as it can help reduce costs while improving utilization of bandwidth and network management. However, security risks like hacking and eavesdropping exist since VoIP uses the public Internet.
VoIP Wars : Return of the SIP 



VoIP Wars : Return of the SIP Fatih Ozavci This document discusses penetration testing of VoIP networks using the Viproy VoIP penetration testing kit. It begins with an introduction of the author and his background in VoIP security. It then demonstrates the Viproy kit in action and discusses basic attacks against SIP services like discovery, footprinting, and spoofing calls. It also covers more advanced attacks like the SIP proxy bounce attack, creating fake services to perform man-in-the-middle attacks, distributed denial of service attacks, and exploiting trust relationships between SIP gateways. The document concludes by discussing fuzzing SIP services and clients to find vulnerabilities.
VoIP Wars: Destroying Jar Jar Lync (Unfiltered version)



VoIP Wars: Destroying Jar Jar Lync (Unfiltered version)Fatih Ozavci Enterprise companies are increasingly using Microsoft Lync 2010/2013 (a.k.a Skype for Business 2015) services as call centre, internal communication, cloud communication and video conference platform. These services are based on the VoIP and instant messaging protocols, and support multiple client types such as Microsoft Office 365, Microsoft Lync, Skype for Business, IP phones and teleconference devices. Also the official clients are available for mobile devices (e.g. Windows phone, Android and iOS), desktops (Mac, Linux and Windows) and web applications developed with .NET framework. Although the Microsoft Lync platform has been developed along with the new technologies, it still suffers from old VoIP, teleconference and platform issues.
Modern VoIP attacks can be used to attack Microsoft Lync environments to obtain unauthorised access to the infrastructure. Open MS Lync frontend and edge servers, insecure federation security design, lack of encryption, insufficient defence for VoIP attacks and insecure compatibility options may allow attackers to hijack enterprise communications. The enterprise users and employees are also the next generation targets for these attackers. They can attack client soft phones and handsets using the broken communication, invalid protocol options and malicious messaging content to compromise sensitive business assets. These attacks may lead to privacy violations, legal issues, call/toll fraud and intelligence collection.
Attack vectors and practical threats against the Microsoft Lync ecosystem will be presented with newly published vulnerabilities and Microsoft Lync testing modules of the Viproy VoIP kit developed by the speaker. This will be accompanied by live demonstrations against a test environment.
• A brief introduction to Microsoft Lync ecosystem
• Security requirements, design vulnerabilities and priorities
• Modern threats against commercial Microsoft Lync services
• Demonstration of new attack vectors against target test platform
Voice over IP (VoIP)



Voice over IP (VoIP)Peter R. Egli Overview of VoIP (Voice over IP) and FoIP (Fax over IP) technologies like Session Initiation Protocol and H.323.
Even though voice over IP (VoIP) was hailed as a technological innovation, the idea to transport real-time traffic over TCP/IP networks was not new back in the 1990s when VoIP started being deployed in networks. Chapter 2.5 of the venerable RFC793 (TCP) shows both data oriented application traffic as well as voice being transported over IP based networks.
Nevertheless, VoIP puts high demands on signal and protocol processing capabilities so it became possible at reasonable costs only in the 1990s.
VoIP can be roughly split into two main functions. Signaling protocols like SIP (Session Initiation Protocol), H.323 and MGCP/H.248 are used to establish a conference session and the data path for transporting real-time voice data packets. SIP has largely supplanted H.323 in recent years to its simpler structure and packet sequences. MGCP and H.248 are mostly used in carrier backbone networks.
Protocols like RTP (Real Time Protocol) transport voice packets and provide the necessary information for receivers to equalize packet flow variations to provide a smooth playback of the original voice signal.
Voice codecs are one of the core functions of the data path. Voice compression reduces the bandwidth required to transport voice over an IP based network. Compression may be less of a concern in local area networks with gigabit speeds, on slower links like 3G (UMTS, LTE) it still makes a lot of sense.
The algorithms used in different codecs make use of various characteristics of the characteristics of human speech recognition. Redundant information is removed from the signals thus slightly reducing the quality, but greatly reducing the required bandwidth.
In VoIP networks, the echo problem is typically compounded by the increased delay incurred by packetization of voice signals. To counteract the echo problem, VoIP gear (hard phones, soft phones, gateways) include echo cancelers to remove echo signals from the transmit signal.
To transport facsimile over an IP based network, even more technology is needed. Facsimile protocols are very susceptible to delay and delay variation and thus need more compensation algorithms. Protocols like T.38 terminate facsimile protocols like T.30 (analog facsimile) and transport the fax images as digitized pictures over IP based networks.
VoIP Wars: The Phreakers Awaken



VoIP Wars: The Phreakers AwakenFatih Ozavci This document discusses vulnerabilities in voice over IP (VoIP) and unified communications systems. It begins by introducing the speaker and their background in VoIP security. It then outlines various attack vectors such as exploiting vulnerabilities in signaling protocols, message content, and unified messaging features to inject malicious content or execute code. The document emphasizes that securing UC involves more than just securing VoIP, and recommends approaches like secure infrastructure design, authentication, and client protection to help secure these systems.
What is VoIP and How it works?



What is VoIP and How it works?broadconnect The document is a presentation by BroadConnect Telecom that introduces VoIP technology and BroadConnect's VoIP-enabled products and services. It defines VoIP as the delivery of voice communications over IP networks using standards-based protocols. It then describes BroadConnect's SIP server, IP phones, gateways, audio/video conferencing units, and IP cameras. The presentation explains how VoIP works by using codecs like G.711 to transfer voice data over the IP network. It outlines VoIP's advantages of low cost and security, as well as its need for constant power and internet connectivity. BroadConnect provides hosted PBX, SIP trunking, phone lines, communication services, internet services, and hosting solutions to help businesses simplify communications
Voip powerpoint



Voip powerpointGW1992 VoIP stands for Voice over Internet Protocol. It allows users to make phone calls using an IP network rather than a traditional telephone network. VoIP works by converting voice into packets of data that travel over the internet through routers to reach the destination. While it is beginning to be used more in businesses due to lower costs, some reliability issues with lost data packets can cause jittering and lower sound quality compared to traditional phone networks.
Security Challenges In VoIP



Security Challenges In VoIPTomGilis Nowadays VoIP technologies have taken the upper hand offering many advantages compared to the traditional telephone network, but what are the security risks involved when voice and data networks come together. In this presentation, we will identify and evaluate these different security risks and their countermeasures both from a defensive as offensive position.
VoIP Wars: Destroying Jar Jar Lync (Filtered version)



VoIP Wars: Destroying Jar Jar Lync (Filtered version)Fatih Ozavci Enterprise companies are increasingly using Microsoft Lync 2010/2013 (a.k.a Skype for Business 2015) services as call centre, internal communication, cloud communication and video conference platform. These services are based on the VoIP and instant messaging protocols, and support multiple client types such as Microsoft Office 365, Microsoft Lync, Skype for Business, IP phones and teleconference devices. Also the official clients are available for mobile devices (e.g. Windows phone, Android and iOS), desktops (Mac, Linux and Windows) and web applications developed with .NET framework. Although the Microsoft Lync platform has been developed along with the new technologies, it still suffers from old VoIP, teleconference and platform issues.
Modern VoIP attacks can be used to attack Microsoft Lync environments to obtain unauthorised access to the infrastructure. Open MS Lync frontend and edge servers, insecure federation security design, lack of encryption, insufficient defence for VoIP attacks and insecure compatibility options may allow attackers to hijack enterprise communications. The enterprise users and employees are also the next generation targets for these attackers. They can attack client soft phones and handsets using the broken communication, invalid protocol options and malicious messaging content to compromise sensitive business assets. These attacks may lead to privacy violations, legal issues, call/toll fraud and intelligence collection.
Attack vectors and practical threats against the Microsoft Lync ecosystem will be presented with newly published vulnerabilities and Microsoft Lync testing modules of the Viproy VoIP kit developed by the speaker. This will be accompanied by live demonstrations against a test environment.
• A brief introduction to Microsoft Lync ecosystem
• Security requirements, design vulnerabilities and priorities
• Modern threats against commercial Microsoft Lync services
• Demonstration of new attack vectors against target test platform
SIP Beyond VoIP



SIP Beyond VoIPSaúl Ibarra Corretgé The document discusses using SIP (Session Initiation Protocol) for applications beyond just voice over IP (VoIP) communication. It describes how SIP was designed to be extensible with different media streams beyond just audio and video. It provides examples of using SIP for presence, instant messaging, file transfer and desktop sharing using protocols like SIMPLE, MSRP. It also discusses building collaboration tools with SIP, including features like conferencing, chat rooms and screen sharing. The document promotes moving beyond just VoIP with SIP to enable new communication and collaboration applications.
Introduction to SIP(Session Initiation Protocol)



Introduction to SIP(Session Initiation Protocol)William Lee Session Initiation Protocol (SIP) is a signaling protocol for managing multimedia communication sessions over Internet Protocol (IP) networks. SIP can be used to establish two-party or multiparty sessions that include voice, video, chat, gaming, and other forms of media. The document introduces SIP architecture, message format, and common call flows including registration, basic call setup, call modification, call hold, and three-way conferencing.
voip gateway



voip gatewayNayomi Ranamuka A VoIP gateway acts as an interface between a public switched telephone network (PSTN) and an IP network, converting voice and fax calls between the two in real time. Key functions include voice and fax compression/decompression, packetization, and call routing. There are analog gateways for connecting PSTN lines to VoIP systems and digital gateways for connecting PBX systems. When selecting a gateway, factors to consider include call load, supported protocols and compatibility, and cost.
Voice over Internet Protocol (VoIP) using Asterisk



Voice over Internet Protocol (VoIP) using AsteriskSameer Verma Voice over Internet Protocol (VoIP) using Asterisk - a presentation made to the Silicon Valley Linux Users Group
Voice over internet protocol (VoIP) 



Voice over internet protocol (VoIP) Namra Afzal Internet protocol (VoIP) is the technology of digitizing sound, compressing it, breaking it up into data packets, and sending it over an IP network.The conventional technique used for sending voice is PSTN (public switched telephone network) . As data traffic has higher speed than telephone traffic, so what we do most of the time we prefer to send voice over data networks. Voice over internet protocol (VoIP) is a method of telephone communication over a data network.
Introduction to VoIP



Introduction to VoIPPaloSanto Solutions Introduction to VoIP, 2nd chapter of "Unified Communications with Elastix" Vol.1
We recommend to read the chapter along with the presentation.
http://elx.ec/chapter2
VoIP Seminar



VoIP SeminarHossein Yavari VoIP Introduction Seminar with KNTU university -- Feb 2017
VOIP, Telephony Systems, Networking
Voip



VoipYasin Virani This document provides an overview of Voice over Internet Protocol (VoIP) technology. It discusses what VoIP is, how it works, its components, advantages like lower costs, and disadvantages like potential quality issues. The document also compares VoIP to the traditional Public Switched Telephone Network (PSTN) and explores VoIP alternatives and the future of the technology. Overall, the document serves as an introduction to VoIP and its capabilities for voice communication over the internet.
Voip introduction



Voip introductiondaksh bhatt VoIP, or Voice over Internet Protocol, is a technology that allows users to make voice calls using an Internet connection instead of a regular phone line. It works by converting voice signals into digital data packets that travel over the Internet and are then reconstructed at the other end. There are several VoIP protocols used and many applications that employ VoIP, including Skype. VoIP offers advantages over traditional phone service like lower costs, additional features included for free, and the ability to make calls from any Internet-connected device.
VOIP Presentation 



VOIP Presentation tofael1 Voice over Internet Protocol (VoIP) allows users to make voice calls using an internet connection rather than a regular phone line. It works by encoding voice input and transmitting it as data packets over the internet. VoIP provides several benefits including lower costs, portability through mobile apps, and additional features like video calling. However, it also has some disadvantages like potential quality issues when making international calls and reliance on an internet connection to place calls.
Ad
Similar to VoIP – vulnerabilities and attacks (20)
Meletis Belsis - Voip security



Meletis Belsis - Voip securityMeletis Belsis MPhil/MRes/BSc VoIP Security: An Overview discusses the security challenges of Voice over IP (VoIP) technology. It notes that VoIP inherits vulnerabilities from TCP/IP networks and uses the corporate network, making it complex to secure. Common VoIP threats include denial of service attacks, interception attacks, covert channels, and vulnerabilities in VoIP platforms. The document outlines example attacks and tools used by hackers. It recommends countermeasures like network separation, encryption of SIP and RTP, firewalls, intrusion detection systems, and hardening VoIP infrastructure and devices. VoIP honeypots can also be used to detect attackers.
I N T E R O P09 Suhas Desai Secure Your Vo I P Network With Open Source



I N T E R O P09 Suhas Desai Secure Your Vo I P Network With Open SourceSuhas Desai The document discusses securing VoIP networks with open source tools. It describes how open source testing tools like SiVuS and SIP Bomber can be used to assess the security of VoIP implementations. SiVuS is a vulnerability scanner that discovers SIP components, generates attack messages, and produces a security findings report. SIP Bomber tests SIP protocol implementations by generating messages and validating passwords. The document advocates using open source tools to securely configure servers, clients, gateways, and firewalls before deploying VoIP networks.
Introduction to VoIP Security



Introduction to VoIP Securityn|u - The Open Security Community VoIP, or Voice over IP, converts analog voice signals to digital bits which are transmitted in packets over data networks. This allows for voice calls to be made over the internet. However, VoIP inherits vulnerabilities from both telephone and computer networks. Common attacks against VoIP systems aim to disrupt availability through DoS attacks, compromise integrity through spoofing, or violate confidentiality through eavesdropping. Proper security measures include separating VoIP and data infrastructure, using secure protocols, encryption, and VoIP-aware firewalls.
VOIP services



VOIP servicesPankaj Saharan This document provides an overview of VoIP services through a seminar presentation. It discusses how VoIP came about as an alternative to traditional circuit-switched telephony using the PSTN. VoIP allows carrying voice calls over an IP network by digitizing and packetizing voice streams using protocols like SIP and H.323. Some key benefits of VoIP include reduced costs, increased flexibility, and mobility. Popular VoIP service providers include Skype, while security poses ongoing challenges to VoIP adoption.
Understanding VoIP - 1



Understanding VoIP - 1Adebayo Ojo The document provides an overview of VoIP components, standards, architectures and implementation choices. It discusses key VoIP elements like terminals, packetized voice, soft switches, media servers, gateways, LANs/WANs and standards. It also describes common VoIP architectures for computer-computer, computer-phone, phone-phone communication over the internet. Finally, it outlines VoIP solutions for businesses using VoIP-enabled PBXs, replacing PBXs with softswitches, and hosted PBX solutions.
Fuzzing Janus @ IPTComm 2019



Fuzzing Janus @ IPTComm 2019Lorenzo Miniero The slides for the "Fuzzing Janus for fun and profit" paper I presented at IPTComm 2019, in Chicago. Simon (Romano) came up with the title, as a homage to the famous "Smashing the stack for fun and profit" article.
voip elements by Karan singh cypher 



voip elements by Karan singh cypher Karan Maker This document provides an overview of key concepts related to Voice over IP (VoIP) technology. It defines common VoIP terms and standards, describes how VoIP works by breaking analog voice signals into digital packets, and outlines typical system elements like softswitches, terminals, and gateways. It also discusses media standards, signaling protocols, quality of service measures, fax transmission methods, and various Patton Electronics VoIP products.
Linux VOIP 



Linux VOIP chanmyaeag VoIP stands for Voice over Internet Protocol. It allows users to make voice calls via a broadband internet connection instead of a regular phone line. There are several VoIP protocols that convert voice into digital signals to transmit over the internet, like SIP and H.323. Users can make VoIP calls from their computers using softphones, or through an Analog Telephone Adapter connected to a regular phone. Setting up a PBX server allows creating a full-featured VoIP phone system. VoIP provides advantages over traditional PSTN phone networks like lower costs and additional features included free of charge.
Fuzzing RTC @ Kamailio World 2019



Fuzzing RTC @ Kamailio World 2019Lorenzo Miniero My talk on the excellent work Alessandro Toppi did at Meetecho on investigating the different code fuzzing options, and how it was eventually integrated in Janus for improving the robustness of the WebRTC stack (RTP, RTCP and SDP currently). It includes considerations on sharing corpora files and making this all distributed via OSS-Fuzz.
Voip



VoipAbd17m This document provides an overview of Voice over Internet Protocol (VoIP) technology. It describes how VoIP works by converting voice signals to digital data that is transmitted over the Internet using packet switching. Common VoIP protocols like SIP and H.323 are discussed along with VoIP components like softphones, gateways, and codecs. Advantages of VoIP include low cost and flexibility, while disadvantages include reliability issues and lack of service during power outages. The document recommends that most VoIP issues will be addressed by 2008 when it will gain widespread consumer acceptance.
Practical Fundamentals of Voice over IP (VoIP) for Engineers and Technicians



Practical Fundamentals of Voice over IP (VoIP) for Engineers and TechniciansLiving Online In the past five years, technologies have converged to such an extent that one can transmit voice, fax and video over the same internet protocol network that one uses for data. This workshop examines Voice over IP (VoIP) technologies and provides you with the skills to competently implement a VoIP network for your organisation. Numerous case studies and exercises throughout the course ensure that you get a good grasp on the technologies used. Solid practical advice is given on application, implementation and most importantly troubleshooting these systems.
MORE INFORMATION: http://www.idc-online.com/content/practical-fundamentals-voice-over-ip-voip-engineers-and-technicians-3
Introduction to VoIP, RTP and SIP 



Introduction to VoIP, RTP and SIP ThousandEyes Join us for an introductory webinar on VoIP and learn:
- The fundamental principles of VoIP including RTP and SIP
- What voice metrics to measure and why they matter
- The different methods to monitor and troubleshoot VoIP
BlackHat Hacking - Hacking VoIP.



BlackHat Hacking - Hacking VoIP.Sumutiu Marius This document summarizes a presentation on hacking VoIP systems. It begins with introductions of the presenters and an overview of VoIP security risks. The agenda is then outlined, covering footprinting, scanning, and enumerating VoIP systems to obtain information. Techniques for exploiting the underlying network through man-in-the-middle attacks and eavesdropping are discussed. Finally, exploiting VoIP applications through fuzzing, denial of service, and signaling manipulation will be covered.
WebRTC meetup barcelona 2017



WebRTC meetup barcelona 2017Juan De Bravo WebRTC in Telefonica with TU and Tuenti
TU and Tuenti are exploring using WebRTC for their voice services. This would allow for calling across multiple devices using the same account. They are investigating using their existing XMPP/chat infrastructure for signaling and WebRTC standards like ICE, SRTP, and DTLS for media negotiation and security. Challenges include handling the cellular network leg and avoiding issues like "splash ringing" during call setup across devices on different networks.
Media Handling in FreeSWITCH



Media Handling in FreeSWITCHMoises Silva This document discusses media handling in FreeSWITCH. It covers topics like audio codecs, transcoding, codec negotiation, bypass media, proxy media, and Sangoma transcoding. The document provides details on common audio codecs supported by FreeSWITCH, how transcoding works in FreeSWITCH, codec negotiation algorithms, different media modes like bypass and proxy media, and Sangoma hardware transcoding cards. It aims to give an overview of key concepts around media and codecs in FreeSWITCH.
Multipath TCP



Multipath TCPOlivier Bonaventure The Transmission Control Protocol (TCP) is used by the vast majority of applications to transport their data reliably across the Internet and in the cloud. TCP was designed in the 1970s and has slowly evolved since then. Today's networks are multipath: mobile devices have multiple wireless interfaces, datacenters have many redundant paths between servers, and multihoming has become the norm for big server farms. Meanwhile, TCP is essentially a single-path protocol: when a TCP connection is established, the connection is bound to the IP addresses of the two communicating hosts and these cannot change. Multipath TCP (MPTCP) is a major modification to TCP that allows multiple paths to be used simultaneously by a single transport connection. Multipath TCP circumvents the issues mentioned above and several others that affect TCP. The IETF is currently finalising the Multipath TCP RFC and an implementation in the Linux kernel is available today.
This tutorial will present in details the design of Multipath TCP and the role that it could play in cloud environments. We will start with a presentation of the current Internet landscape and explain how various types of middleboxes have influenced the design of Multipath TCP. Second we will describe in details the connection establishment and release procedures as well as the data transfer mechanisms that are specific to Multipath TCP. We will then discuss several use cases for the deployment of Multipath TCP including improving the performance of datacenters and
mobile WiFi offloading on smartphones. All these use cases are key when both accessing cloud-based services or when providing them. We will end the tutorial with some open research issues.
This tutorial was given at the IEEE Cloud'Net 2012 conference in novembrer 2012.
The pptx version containing animations that are not shown here is available from http://www.multipath-tcp.org
VoIP (Voice over Internet Protocol)



VoIP (Voice over Internet Protocol)Abdullah Shah VoIP allows users to make voice calls over the internet instead of traditional phone lines. It works by converting voice signals to digital data packets that are transmitted over the internet and then reconverted at their destination. Key components include gateways, codecs, servers, and protocols like SIP and H.323. VoIP offers advantages like lower costs and integration with other systems but relies on internet connectivity and faces some security risks.
Softswitch



SoftswitchVoIP Infotech VoIP InfoTech provides direct solution to route the calls from one network to varied networks through the prescribed path of internet protocol. This prescribed path of VOIP SoftSwitch technology route calls on integrated network circuits and packets based networks like PTSN; instead, of conventional landlines.
Softswitch



SoftswitchVoIP Infotech VoIP InfoTech provides direct solution to route the calls from one network to varied networks through the prescribed path of internet protocol. This prescribed path of VOIP SoftSwitch technology route calls on integrated network circuits and packets based networks like PTSN; instead, of conventional landlines.
Ad
More from n|u - The Open Security Community (20)
Hardware security testing 101 (Null - Delhi Chapter)



Hardware security testing 101 (Null - Delhi Chapter)n|u - The Open Security Community Arun Mane is the founder and director of AmynaSec Labs. He is a security speaker and trainer who has presented at many conferences including Defcon, Blackhat, Nullcon, and HITB. His areas of expertise include security testing of IoT devices, connected vehicles, medical devices, and industrial control systems. Some common issues he finds include devices being publicly accessible, having backdoors, hardcoded credentials, and crypto or web application management problems. His testing methodology involves assessing web and mobile applications, embedded device communications, hardware testing through reverse engineering, and analyzing communication protocols and stored data.
Osint primer



Osint primern|u - The Open Security Community This document outlines an agenda for a presentation on open-source intelligence (OSINT) gathering techniques. The agenda includes an introduction to OSINT, different types of intelligence gathering, a scenario example, OSINT gathering tactics and tools like Shodan, TheHarvester and Google dorks, applications of OSINT, a demonstration, references for OSINT, and a conclusion. Key OSINT tools that will be demonstrated include Twitter, Shodan, TheHarvester and Google dorks for gathering information from public online sources.
SSRF exploit the trust relationship



SSRF exploit the trust relationshipn|u - The Open Security Community This document provides an overview of server-side request forgery (SSRF) vulnerabilities, including what SSRF is, its impact, common attacks, bypassing filters, and mitigations. SSRF allows an attacker to induce the application to make requests to internal or external servers from the server side, bypassing access controls. This can enable attacks on the server itself or other backend systems and escalate privileges. The document discusses techniques for exploiting trust relationships and bypassing blacklists/whitelists to perform SSRF attacks. It also covers blind SSRF and ways to detect them using out-of-band techniques. Mitigations include avoiding user input that can trigger server requests, sanitizing input, whitelist
Nmap basics



Nmap basicsn|u - The Open Security Community Nmap is a network scanning tool that can perform port scanning, operating system detection, and version detection among other features. It works by sending TCP and UDP packets to a target machine and examining the response, comparing it to its database to determine open ports and operating system. There are different scanning techniques that can be used like TCP SYN scanning, UDP scanning, and OS detection. Nmap also includes a scripting engine that allows users to write scripts to automate networking tasks. The presentation concludes with demonstrating Nmap's features through some examples.
Metasploit primary



Metasploit primaryn|u - The Open Security Community The document provides an introduction and overview of the Metasploit Framework. It defines key terms like vulnerability, exploit, and payload. It outlines the scenario of testing a subnet to find vulnerabilities. It describes the main features of msfconsole like searching for modules, using specific modules, and configuring options. It promotes understanding and proper use, emphasizing that Metasploit alone does not make someone a hacker.
Api security-testing



Api security-testingn|u - The Open Security Community 1) The document provides guidance on testing APIs for security weaknesses, including enumerating the attack surface, common tools to use, what to test for (e.g. authentication, authorization, injections), and demo apps to practice on.
2) It recommends testing authentication and authorization mechanisms like tokens, injections attacks on state-changing requests, and how data is consumed client-side.
3) The document also discusses testing for denial of service conditions, data smuggling through middleware, API rate limiting, and cross-origin requests.
Introduction to TLS 1.3



Introduction to TLS 1.3n|u - The Open Security Community TLS 1.3 is an update to the Transport Layer Security protocol that improves security and privacy. It removes vulnerable optional parts of TLS 1.2 and only supports strong ciphers to implement perfect forward secrecy. The handshake process is also significantly shortened. TLS 1.3 provides security benefits by removing outdated ciphers and privacy benefits by enabling perfect forward secrecy by default, ensuring only endpoints can decrypt traffic even if server keys are compromised in the future.
Gibson 101 -quick_introduction_to_hacking_mainframes_in_2020_null_infosec_gir...



Gibson 101 -quick_introduction_to_hacking_mainframes_in_2020_null_infosec_gir...n|u - The Open Security Community This document provides an introduction to hacking mainframes in 2020. It begins with an overview of mainframe systems and terminology. It then discusses reconnaissance methods like port scanning and credential theft to gain initial access. Next, it covers conducting internal reconnaissance to escalate privileges by exploiting surrogate users, APF authorized libraries, and UNIX privilege escalation techniques. The document aims to provide enough context for curiosity about hacking mainframe systems.
Talking About SSRF,CRLF



Talking About SSRF,CRLFn|u - The Open Security Community The document discusses CRLF injection and SSRF vulnerabilities. CRLF injection occurs when user input is directly parsed into response headers without sanitization, allowing special characters to be injected. SSRF is when a server is induced to make HTTP requests to domains of an attacker's choosing, potentially escalating access. Mitigations include sanitizing user input, implementing whitelists for allowed domains/protocols, and input validation.
Building active directory lab for red teaming



Building active directory lab for red teamingn|u - The Open Security Community The document provides an overview of Active Directory, including its components and how it is used to centrally manage users, computers, and other objects within a network. It discusses key Active Directory concepts such as forests, domains, organizational units, users, computers, and domain trusts. It also provides step-by-step instructions for setting up an Active Directory lab environment for red teaming purposes and integrating a client machine into the domain.
Owning a company through their logs



Owning a company through their logsn|u - The Open Security Community A security engineer discusses how logs and passive reconnaissance can reveal sensitive information like AWS credentials. The engineer searched for open Jenkins and SonarQube instances which led to discovering Slack channels containing AWS access keys. Key lessons are to know your boundaries, automate mundane tasks, don't presume systems mask secrets, and persistence is important in security work.
Introduction to shodan



Introduction to shodann|u - The Open Security Community Shodan is a search engine that indexes internet-connected devices and provides information about devices, banners, and metadata. It works by generating random IP addresses and port scans to retrieve banner information from devices. This information is then stored in a searchable database. Users can search Shodan's database using filters like country, city, IP address, operating system, and ports. Shodan can be accessed through its website or command line interface. While useful for security research, Shodan also raises privacy and security concerns by revealing information about unprotected devices.
Cloud security 



Cloud security n|u - The Open Security Community This document outlines an agenda for discussing cloud security. It begins with an introduction to cloud computing and deployment models. It then discusses challenges of cloud computing and why cloud security is important. Specific threats like data breaches and account hijacking are listed. The document reviews the shared responsibility model and scope of security in public clouds. It describes cloud security penetration testing methods like static and dynamic application testing. Finally, it provides prerequisites and methods for conducting cloud penetration testing, including reconnaissance, threat modeling, and following standard testing methodologies.
Detecting persistence in windows



Detecting persistence in windowsn|u - The Open Security Community This document discusses several techniques for maintaining persistence on Windows systems, including modifying accessibility features, injecting into image file execution options, using AppInit DLLs, application shimming, BITS jobs, registry run keys, and Windows Management Instrumentation event subscriptions. It provides details on how each technique works, common implementations, required privileges, relevant data sources, and example event log entries.
Frida - Objection Tool Usage



Frida - Objection Tool Usagen|u - The Open Security Community Frida is a dynamic instrumentation toolkit that allows injecting JavaScript into applications. Objection is a runtime mobile exploration toolkit powered by Frida that helps assess the security of mobile apps. It supports iOS and Android. Objection allows exploring apps by listing classes, methods, and injecting scripts to enable dynamic analysis like dumping keychain entries.
OSQuery - Monitoring System Process



OSQuery - Monitoring System Processn|u - The Open Security Community Osquery is an open source tool that allows users to perform SQL queries on their system to retrieve information. It supports various platforms and makes it easy to get details about the system. Osquery consists of Osqueryi, Osqueryd, and Osqueryctl components. Basic queries can be run in user context mode to view system information, configuration, and tables. Osqueryd runs in daemon mode and can be configured using packs and decorators to monitor specific events and files. Osqueryctl is used to control the Osquery daemon process.
DevSecOps Jenkins Pipeline -Security



DevSecOps Jenkins Pipeline -Securityn|u - The Open Security Community This document discusses DevSecOps, beginning with an introduction from Tibin Lukose. It then covers some challenges in DevSecOps such as developers lacking security skills, cultural challenges, and difficulties balancing speed, coverage and accuracy in testing. The document proposes a model DevSecOps company, Infosys, and provides a demo and contact information for any further questions.
Extensible markup language attacks



Extensible markup language attacksn|u - The Open Security Community This document provides an introduction to XML and related technologies like libxml2, XSLT, XPath, and XML attacks. It discusses the basics of XML including elements, tags, attributes, and validation. It also describes common XML libraries and tools like libxml2, xmllint, and xsltproc. Finally, it provides an overview of different types of XML attacks like XML injection, XPath injection, XXE, and XSLT injection.
Linux for hackers



Linux for hackersn|u - The Open Security Community This document contains the agenda for a presentation on Linux for hackers. The agenda includes discussing the Linux file system, managing virtual machines smartly, command line tools like alias, tee, pipe, grep, cut, uniq, and xargs, Bash scripting, logging, and proxy chaining. It also mentions demonstrating several commands and tools. The presentation aims to be an interactive session where the presenter will answer any questions from attendees.
Android Pentesting



Android Pentestingn|u - The Open Security Community This document provides an overview of Android penetration testing. It discusses requirements and tools for static and dynamic analysis, including Apptitude, Genymotion, and ADB. It covers analyzing the Android manifest and classes.dex files. It also describes vulnerabilities in WebViews, such as loading cleartext content and improper SSL handling. Best practices for coding securely on Android are also presented.
Gibson 101 -quick_introduction_to_hacking_mainframes_in_2020_null_infosec_gir...



Gibson 101 -quick_introduction_to_hacking_mainframes_in_2020_null_infosec_gir...n|u - The Open Security Community
Recently uploaded (20)
Presentation on Tourism Product Development By Md Shaifullar Rabbi



Presentation on Tourism Product Development By Md Shaifullar RabbiMd Shaifullar Rabbi Presentation on Tourism Product Development By Md Shaifullar Rabbi, Assistant Manager- SABRE Bangladesh.
UNIT 3 NATIONAL HEALTH PROGRAMMEE. SOCIAL AND PREVENTIVE PHARMACY



UNIT 3 NATIONAL HEALTH PROGRAMMEE. SOCIAL AND PREVENTIVE PHARMACYDR.PRISCILLA MARY J NATIONAL HEALTH PROGRAMMEE
LDMMIA Reiki Master Spring 2025 Mini Updates



LDMMIA Reiki Master Spring 2025 Mini UpdatesLDM Mia eStudios As of Mid to April Ending, I am building a new Reiki-Yoga Series. No worries, they are free workshops. So far, I have 3 presentations so its a gradual process. If interested visit: https://www.slideshare.net/YogaPrincess
https://ldmchapels.weebly.com
Blessings and Happy Spring. We are hitting Mid Season.
Biophysics Chapter 3 Methods of Studying Macromolecules.pdf



Biophysics Chapter 3 Methods of Studying Macromolecules.pdfPKLI-Institute of Nursing and Allied Health Sciences Lahore , Pakistan. This chapter provides an in-depth overview of the viscosity of macromolecules, an essential concept in biophysics and medical sciences, especially in understanding fluid behavior like blood flow in the human body.
Key concepts covered include:
✅ Definition and Types of Viscosity: Dynamic vs. Kinematic viscosity, cohesion, and adhesion.
⚙️ Methods of Measuring Viscosity:
Rotary Viscometer
Vibrational Viscometer
Falling Object Method
Capillary Viscometer
🌡️ Factors Affecting Viscosity: Temperature, composition, flow rate.
🩺 Clinical Relevance: Impact of blood viscosity in cardiovascular health.
🌊 Fluid Dynamics: Laminar vs. turbulent flow, Reynolds number.
🔬 Extension Techniques:
Chromatography (adsorption, partition, TLC, etc.)
Electrophoresis (protein/DNA separation)
Sedimentation and Centrifugation methods.
To study the nervous system of insect.pptx



To study the nervous system of insect.pptxArshad Shaikh The *nervous system of insects* is a complex network of nerve cells (neurons) and supporting cells that process and transmit information. Here's an overview:
Structure
1. *Brain*: The insect brain is a complex structure that processes sensory information, controls behavior, and integrates information.
2. *Ventral nerve cord*: A chain of ganglia (nerve clusters) that runs along the insect's body, controlling movement and sensory processing.
3. *Peripheral nervous system*: Nerves that connect the central nervous system to sensory organs and muscles.
Functions
1. *Sensory processing*: Insects can detect and respond to various stimuli, such as light, sound, touch, taste, and smell.
2. *Motor control*: The nervous system controls movement, including walking, flying, and feeding.
3. *Behavioral responThe *nervous system of insects* is a complex network of nerve cells (neurons) and supporting cells that process and transmit information. Here's an overview:
Structure
1. *Brain*: The insect brain is a complex structure that processes sensory information, controls behavior, and integrates information.
2. *Ventral nerve cord*: A chain of ganglia (nerve clusters) that runs along the insect's body, controlling movement and sensory processing.
3. *Peripheral nervous system*: Nerves that connect the central nervous system to sensory organs and muscles.
Functions
1. *Sensory processing*: Insects can detect and respond to various stimuli, such as light, sound, touch, taste, and smell.
2. *Motor control*: The nervous system controls movement, including walking, flying, and feeding.
3. *Behavioral responses*: Insects can exhibit complex behaviors, such as mating, foraging, and social interactions.
Characteristics
1. *Decentralized*: Insect nervous systems have some autonomy in different body parts.
2. *Specialized*: Different parts of the nervous system are specialized for specific functions.
3. *Efficient*: Insect nervous systems are highly efficient, allowing for rapid processing and response to stimuli.
The insect nervous system is a remarkable example of evolutionary adaptation, enabling insects to thrive in diverse environments.
The insect nervous system is a remarkable example of evolutionary adaptation, enabling insects to thrive
YSPH VMOC Special Report - Measles Outbreak Southwest US 5-3-2025.pptx



YSPH VMOC Special Report - Measles Outbreak Southwest US 5-3-2025.pptxYale School of Public Health - The Virtual Medical Operations Center (VMOC) A measles outbreak originating in West Texas has been linked to confirmed cases in New Mexico, with additional cases reported in Oklahoma and Kansas. The current case count is 817 from Texas, New Mexico, Oklahoma, and Kansas. 97 individuals have required hospitalization, and 3 deaths, 2 children in Texas and one adult in New Mexico. These fatalities mark the first measles-related deaths in the United States since 2015 and the first pediatric measles death since 2003.
The YSPH Virtual Medical Operations Center Briefs (VMOC) were created as a service-learning project by faculty and graduate students at the Yale School of Public Health in response to the 2010 Haiti Earthquake. Each year, the VMOC Briefs are produced by students enrolled in Environmental Health Science Course 581 - Public Health Emergencies: Disaster Planning and Response. These briefs compile diverse information sources – including status reports, maps, news articles, and web content– into a single, easily digestible document that can be widely shared and used interactively. Key features of this report include:
- Comprehensive Overview: Provides situation updates, maps, relevant news, and web resources.
- Accessibility: Designed for easy reading, wide distribution, and interactive use.
- Collaboration: The “unlocked" format enables other responders to share, copy, and adapt seamlessly. The students learn by doing, quickly discovering how and where to find critical information and presenting it in an easily understood manner.
CURRENT CASE COUNT: 817 (As of 05/3/2025)
• Texas: 688 (+20)(62% of these cases are in Gaines County).
• New Mexico: 67 (+1 )(92.4% of the cases are from Eddy County)
• Oklahoma: 16 (+1)
• Kansas: 46 (32% of the cases are from Gray County)
HOSPITALIZATIONS: 97 (+2)
• Texas: 89 (+2) - This is 13.02% of all TX cases.
• New Mexico: 7 - This is 10.6% of all NM cases.
• Kansas: 1 - This is 2.7% of all KS cases.
DEATHS: 3
• Texas: 2 – This is 0.31% of all cases
• New Mexico: 1 – This is 1.54% of all cases
US NATIONAL CASE COUNT: 967 (Confirmed and suspected):
INTERNATIONAL SPREAD (As of 4/2/2025)
• Mexico – 865 (+58)
‒Chihuahua, Mexico: 844 (+58) cases, 3 hospitalizations, 1 fatality
• Canada: 1531 (+270) (This reflects Ontario's Outbreak, which began 11/24)
‒Ontario, Canada – 1243 (+223) cases, 84 hospitalizations.
• Europe: 6,814
To study Digestive system of insect.pptx



To study Digestive system of insect.pptxArshad Shaikh Education is one thing no one can take away from you.”
The ever evoilving world of science /7th class science curiosity /samyans aca...



The ever evoilving world of science /7th class science curiosity /samyans aca...Sandeep Swamy The Ever-Evolving World of
Science
Welcome to Grade 7 Science4not just a textbook with facts, but an invitation to
question, experiment, and explore the beautiful world we live in. From tiny cells
inside a leaf to the movement of celestial bodies, from household materials to
underground water flows, this journey will challenge your thinking and expand
your knowledge.
Notice something special about this book? The page numbers follow the playful
flight of a butterfly and a soaring paper plane! Just as these objects take flight,
learning soars when curiosity leads the way. Simple observations, like paper
planes, have inspired scientific explorations throughout history.
How to Customize Your Financial Reports & Tax Reports With Odoo 17 Accounting



How to Customize Your Financial Reports & Tax Reports With Odoo 17 AccountingCeline George The Accounting module in Odoo 17 is a complete tool designed to manage all financial aspects of a business. Odoo offers a comprehensive set of tools for generating financial and tax reports, which are crucial for managing a company's finances and ensuring compliance with tax regulations.
How to track Cost and Revenue using Analytic Accounts in odoo Accounting, App...



How to track Cost and Revenue using Analytic Accounts in odoo Accounting, App...Celine George Analytic accounts are used to track and manage financial transactions related to specific projects, departments, or business units. They provide detailed insights into costs and revenues at a granular level, independent of the main accounting system. This helps to better understand profitability, performance, and resource allocation, making it easier to make informed financial decisions and strategic planning.
Michelle Rumley & Mairéad Mooney, Boole Library, University College Cork. Tra...



Michelle Rumley & Mairéad Mooney, Boole Library, University College Cork. Tra...Library Association of Ireland
K12 Tableau Tuesday - Algebra Equity and Access in Atlanta Public Schools



K12 Tableau Tuesday - Algebra Equity and Access in Atlanta Public Schoolsdogden2 Algebra 1 is often described as a “gateway” class, a pivotal moment that can shape the rest of a student’s K–12 education. Early access is key: successfully completing Algebra 1 in middle school allows students to complete advanced math and science coursework in high school, which research shows lead to higher wages and lower rates of unemployment in adulthood.
Learn how The Atlanta Public Schools is using their data to create a more equitable enrollment in middle school Algebra classes.
How to Subscribe Newsletter From Odoo 18 Website



How to Subscribe Newsletter From Odoo 18 WebsiteCeline George Newsletter is a powerful tool that effectively manage the email marketing . It allows us to send professional looking HTML formatted emails. Under the Mailing Lists in Email Marketing we can find all the Newsletter.
Unit 6_Introduction_Phishing_Password Cracking.pdf



Unit 6_Introduction_Phishing_Password Cracking.pdfKanchanPatil34 Initial stages of attacks, Phishing, Password Cracking, guidelines to prevent password attacks, Strong password, weak password,
Political History of Pala dynasty Pala Rulers NEP.pptx



Political History of Pala dynasty Pala Rulers NEP.pptxArya Mahila P. G. College, Banaras Hindu University, Varanasi, India. The Pala kings were people-protectors. In fact, Gopal was elected to the throne only to end Matsya Nyaya. Bhagalpur Abhiledh states that Dharmapala imposed only fair taxes on the people. Rampala abolished the unjust taxes imposed by Bhima. The Pala rulers were lovers of learning. Vikramshila University was established by Dharmapala. He opened 50 other learning centers. A famous Buddhist scholar named Haribhadra was to be present in his court. Devpala appointed another Buddhist scholar named Veerdeva as the vice president of Nalanda Vihar. Among other scholars of this period, Sandhyakar Nandi, Chakrapani Dutta and Vajradatta are especially famous. Sandhyakar Nandi wrote the famous poem of this period 'Ramcharit'.
Niamh Lucey, Mary Dunne. Health Sciences Libraries Group (LAI). Lighting the ...



Niamh Lucey, Mary Dunne. Health Sciences Libraries Group (LAI). Lighting the ...Library Association of Ireland
Biophysics Chapter 3 Methods of Studying Macromolecules.pdf



Biophysics Chapter 3 Methods of Studying Macromolecules.pdfPKLI-Institute of Nursing and Allied Health Sciences Lahore , Pakistan.
YSPH VMOC Special Report - Measles Outbreak Southwest US 5-3-2025.pptx



YSPH VMOC Special Report - Measles Outbreak Southwest US 5-3-2025.pptxYale School of Public Health - The Virtual Medical Operations Center (VMOC)
Michelle Rumley & Mairéad Mooney, Boole Library, University College Cork. Tra...



Michelle Rumley & Mairéad Mooney, Boole Library, University College Cork. Tra...Library Association of Ireland
Political History of Pala dynasty Pala Rulers NEP.pptx



Political History of Pala dynasty Pala Rulers NEP.pptxArya Mahila P. G. College, Banaras Hindu University, Varanasi, India.
Niamh Lucey, Mary Dunne. Health Sciences Libraries Group (LAI). Lighting the ...



Niamh Lucey, Mary Dunne. Health Sciences Libraries Group (LAI). Lighting the ...Library Association of Ireland
VoIP – vulnerabilities and attacks
- 1. VoIP – Vulnerabilities and Attacks Presented by - push
- 2. Agenda • Introduction to VoIP – VoIP Architecture – VoIP Components – VoIP Protocols • A PenTester Perspective – Attack Vectors – Scanning – Attacks – Tools of Trade – Countermeasures and Security http://null.co.in/ http://nullcon.net/
- 3. Remember Something? http://null.co.in/ http://nullcon.net/
- 4. VoIP • IP Telephony • Voice over Internet Protocol • Subset of IP Telephony • Transmission of “Voice” over Packet-Switched Network. • Is it only Voice??? – Data, Audio, Video http://null.co.in/ http://nullcon.net/
- 5. VoIP • Voice Analog Signals are converted to digital bits - “Sampled” and transmitted in packets Analog Voice Signals 101010101010 1101101101 Analog Voice 1010101010101101101 101010101010110110 Signals 101 1101 101010101010 1101101101 Internet 1010101010101101101 101010101010110110 101 1101 http://null.co.in/ http://nullcon.net/
- 6. VoIP Architecture Ordinary Phone ATA Ethernet Router Internet http://null.co.in/ http://nullcon.net/
- 7. VoIP Architecture IP Phone Ethernet IP-PBX Router Internet Internet IP Phone IP - PBX Modem / Router http://null.co.in/ http://nullcon.net/
- 8. VoIP Architecture Softphone Phone Ethernet Router Internet Internet http://null.co.in/ http://nullcon.net/
- 9. VoIP Architecture http://null.co.in/ http://nullcon.net/
- 10. VoIP Components • User Agents (devices) • Redirect Servers • Media gateways • Registrar Servers • Signaling gateways • Location Servers • Network management system • Gatekeepers • Billing systems • Proxy Servers GW Gateway MG Media Gateway GK Gatekeeper MGC Media Gateway Controller NMS Network Management System IVR Interactive Voice Response http://null.co.in/ http://nullcon.net/
- 11. VoIP Protocols • Vendor Proprietary • Signaling Protocols • Media Protocols http://null.co.in/ http://nullcon.net/
- 12. VoIP Protocols SIP Session Initiation Protocol SAP Session Announcement Protocol SGCP Simple Gateway Control Protocol MIME Multipurpose Internet Mail IPDC Internet Protocol device Control Extensions – Set of Standards RTP Real Time Transmission Protocol IAX Inter-Asterisk eXchange SRTP Secure Real Time Transmission Protocol Megaco H.248 Gateway Control Protocol RTCP RTP Control Protocol RVP over IP Remote Voice Protocol over IP SRTCP Secure RTP Control Protocol RTSP Real Time Streaming Protocol MGCP Media Gateway Control Protocol SCCP Skinny Client Control Protocol (Cisco). SDP Session Description Protocol UNISTIM Unified Network Stimulus (Nortel). http://null.co.in/ http://nullcon.net/
- 13. VoIP Protocols - SIP http://null.co.in/ http://nullcon.net/
- 14. VoIP Protocols – H.323 http://null.co.in/ http://nullcon.net/
- 15. A PenTester Perspective http://null.co.in/ http://nullcon.net/
- 16. VoIP – Attack Vectors • Vulnerabilities of Both Data and Telephone Network • CIA Triad http://null.co.in/ http://nullcon.net/
- 17. VoIP - Scanning • Scanning a network for VoIP enabled systems / devices. • Tools for Scanning and Enumeration : – Nmap port scanner – Smap sip scanner. Finds SIP Enabled Servers – Svmap sip scanner – Svwar sip extension enumerator – Iwar VoIP Enabled modem Dialer – Metasploit Modules : • H.323 version scanner • SIP enumerator SIP Username enumerator(UDP) • SIP enumerator_tcp SIP Username Enumerator(TCP) • Options SIP scanner(TCP) • Options_tcp SIP scanner(UDP) http://null.co.in/ http://nullcon.net/
- 18. VoIP – Scanning Demo • Nmap scan http://null.co.in/ http://nullcon.net/
- 19. VoIP – Common Ports Protocol TCP Port UDP Port SIP 5060 5060 SIP-TLS 5061 5061 IAX2 - 4569 http – web based 80 / 8080 - management console tftp - 69 RTP - 5004 RTCP - 5005 IAX1 - 5036 SCCP 2000 SCCPS 2443 H.323 1720 http://null.co.in/ http://nullcon.net/
- 20. VoIP – Scanning Demo • Smap • svmap http://null.co.in/ http://nullcon.net/
- 21. VoIP – Scanning Demo • Metasploit Scanner http://null.co.in/ http://nullcon.net/
- 22. VoIP - Attacks • Identity Spoofing • Conversation Eavesdropping / Sniffing • Password Cracking • Man-In-The-Middle • SIP-Bye DoS • SIP Bombing • RTP Insertion Attacks • Web Based Management Console Hacks • Fuzzing • Default Passwords http://null.co.in/ http://nullcon.net/
- 23. VoIP – Attacks Demo • Identity – Caller ID Spoofing – Tools Used : • Metasploit- SIP_INVITE_Spoof • VoIP Fuzzer – Protos -Sip http://null.co.in/ http://nullcon.net/
- 24. VoIP – Attacks Demo • Conversation Eavesdropping – Tools used : • Cain & Abel • Ettercap • Arpspoof • Wireshark http://null.co.in/ http://nullcon.net/
- 25. VoIP – Attacks Demo • Man-In-The-Middle – Tools Used : • Wireshark • Arpspoof / ettercap • RTPInject • RTPmixsound http://null.co.in/ http://nullcon.net/
- 26. VoIP – Attacks Demo • Password Cracking – Tools Used : • SIPDump • SIPCrack • svcrack http://null.co.in/ http://nullcon.net/
- 27. VoIP - Attacks Some Default Passwords for VoIP Devices and Consoles: Device / Console Username Password Uniden UIP1868P VoIP - admin phone Web Interface Hitachi IP5000 VOIP WIFI - 0000 Phone 1.5.6 Vonage VoIP Telephone user user Adapter Grandstream Phones - Web Administrator /admin admin Adimistrator Interface user user •Asterisk Manager User Accounts are configured in /etc/asterisk/manager.conf http://null.co.in/ http://nullcon.net/
- 28. VoIP – Audit & PenTest Tools • UCSniff • MetaSploit Modules : – Auxillary Modules • VoIPHopper • SIP enumerator SIP Username enumerator • SIP enumerator_tcp SIP USERNAME • Vomit Enumerator • VoIPong • Options SIP scanner • Options_tcp SIP scanner • IAX Flood • Asterisk_login Asterisk Manager Login Utility – Exploits • InviteFlood • Aol_icq_downloadagent AOL ICQ Arbitary File Downlowd • RTPFlood • Aim_triton_cseq AIM triton 1.0.4 CSeq Buffer Overflow • IAXFlood • Sipxezphone_cseq sipxezphone 0.35a Cseq Filed Overflow • BYE-TearDown • Sipxphone_cseq sipxPhone 2.6.0.27 Cseq Buffer Overflow http://null.co.in/ http://nullcon.net/
- 29. Countermeasures & Security • Separate Infrasrtucture • Do not integrate Data and VoIP Networks • VoIP-aware Firewalls, • Secure Protocols like SRTP, • Session Encryption using SIP/TLS, SCCP/TLS • Harden Network Security – IDS – IPS - NIPS http://null.co.in/ http://nullcon.net/
- 30. Thank You See you all @ nullcon - Delhi http://null.co.in/ http://nullcon.net/
Editor's Notes
- #5: IP Telephony - 1990
- #30: Run all VoIP traffic through a separate Internet connection, separating voice and data into their own network segments (VLAN). Set up separate servers dedicated just to VoIP traffic and firewall them apart from the rest of your network. VoIP connections between different buildings use a Virtual Private Network (VPN) to authenticate users to prevent spoofing. Avoid use of cheap VoIP systems. Encrypt any VoIP traffic to keep it confidential and prevent eavesdropping by network sniffers. Put VoIP servers in a secure physical location. Make sure all routers and servers hosting your VoIP system have been hardened and all unnecessary services turned off and ports closed. Restrict access to VoIP servers to only system administrators and log and monitor all access. Use intrusion detection systems to monitor malicious attempts to access your VoIP network. Employ a defense-in-depth of strategy with multiple layers of security, including dedicated VoIP-ready firewalls. Test all devices that send, receive or parse VoIP protocols, including handsets, softphones, SIP proxies, H.323 gateways, call managers and firewalls that VoIP messages pass through.





