Web apps architecture
Download as PPTX, PDF2 likes4,422 views
discussions about different types of architectures used in web applications, pros and cons of each architecture. MVC design patters and comparison with 3-tier.
1 of 22
Downloaded 164 times





















Ad
Recommended
Introduction to Web Architecture



Introduction to Web ArchitectureChamnap Chhorn The document provides an introduction to basic web architecture, including HTML, URIs, HTTP, cookies, database-driven websites, AJAX, web services, XML, and JSON. It discusses how the web is a two-tiered architecture with a web browser displaying information from a web server. Key components like HTTP requests and responses are outlined. Extension of web architecture with server-side processing using languages like PHP and client-side processing with JavaScript are also summarized.
IOT15_Unit6.pptx



IOT15_Unit6.pptxsuptel This document discusses technologies for building Internet of Things (IoT) systems, including cloud storage models, communication APIs, and cloud services. It covers WAMP for messaging between IoT devices and cloud applications. It also describes using Python/Django web frameworks to build IoT backend apps, and Amazon Web Services like EC2, S3, RDS, and DynamoDB for hosting and storing IoT data in the cloud at scale. Finally, it mentions SkyNet as an open-source IoT messaging platform and provides examples of IoT applications for home automation, smart cities, and environmental monitoring.
CLOUD COMPUTING SERVICES - Cloud Reference Modal



CLOUD COMPUTING SERVICES - Cloud Reference ModalSwarnaSLcse Cloud Reference Modal
Given brief description of cloud reference modal of all three layers in detail.
System and network administration network services



System and network administration network servicesUc Man Network services like DNS, DHCP, FTP, SMTP, SNMP, proxy servers, and Active Directory Services provide shared resources to devices on a network. DNS in particular converts domain names to IP addresses, caching responses for a period of time specified by their Time to Live (TTL) value to reduce server load. However, DNS was not originally designed with security in mind and is vulnerable to issues like cache poisoning. DHCP automatically assigns temporary IP addresses to devices on a network. Active Directory is a directory service used by Windows domains to centrally manage network resources and user access through objects, sites, forests, trees and domains.
VIRTUALIZATION STRUCTURES TOOLS.docx



VIRTUALIZATION STRUCTURES TOOLS.docxkumari36 There are three main virtual machine architectures: hypervisor/VMM architecture, host-based virtualization, and para-virtualization. The hypervisor/VMM architecture inserts a virtualization layer between the hardware and operating system to allow multiple operating systems to run simultaneously on the same physical machine. Host-based virtualization builds a virtualization layer on top of the host operating system, which still manages the hardware. Para-virtualization requires modifying guest operating systems and provides APIs for improved performance over full virtualization. KVM is an example of para-virtualization that uses the existing Linux kernel for scheduling and memory management.
Distributed system architecture



Distributed system architectureYisal Khan A distributed system is a collection of computational and storage devices connected through a communications network. In this type of system, data, software, and users are distributed.
Python libraries for data science



Python libraries for data sciencenilashri2 Python is often a choice for development that needs to be applied for census and data analysis to work, or data scientists whose work should be integrated into web applications or the production environment. In particular, python actually looks at the learning point of the machine. The combination of python's teaching and library libraries makes it particularly suited to develop modern lenses and predecessors forecasts directly connected to the production process.
Data science training in Chennai.
Are you interested
Call now:+91 996 252 8294
Overview of computing paradigm



Overview of computing paradigmRipal Ranpara It Includes:
Recent trends in Computing : Grid Computing, Cluster Computing;Distributed Computing;Utility Computing;Cloud Computing
Block Level and File Level



Block Level and File LevelIntegral university, India Types of Virtualization, Block and File level, comparison of both, protocols needed to implement these.
Deductive databases



Deductive databasesJohn Popoola A presentation on a special category of databases called Deductive Databases. It is an attempt to merge logic programming with relational database. Other types include Object-oriented databases, Graph databases, XML databases, Multi-model databases, etc.
Real time scheduling - basic concepts



Real time scheduling - basic conceptsStudent About real time system task scheduling basic concepts.It deals with task, instance,data sharing and their types.It also covers various important terminologies regarding scheduling algorithms.
Client-Server Computing



Client-Server ComputingCloudbells.com Client/server computing involves separating tasks between client and server machines. The client makes requests that are processed by the server, which returns results to the client. Key elements are the client, server, and network connecting them. Major focus is on the software handling tasks like the user interface, application logic, and data management between client and server. Different types of servers specialize in files, data, computing tasks, databases, and communication between networks.
Implementation issues software engineering



Implementation issues software engineeringrishi ram khanal This document discusses various implementation issues in software development, including reuse, configuration management, and host-target development. It notes that modern software is often constructed through reuse and that configuration management is needed to track different software versions. Development usually occurs on a host system while execution is on a target system, which can have different architectures and platforms. The document provides details on different levels of reuse, configuration management activities, tools that aid development, and challenges that can arise with reuse and managing development across host-target systems.
Distributed DBMS - Unit 6 - Query Processing



Distributed DBMS - Unit 6 - Query ProcessingGyanmanjari Institute Of Technology Query Processing : Query Processing Problem, Layers of Query Processing Query Processing in Centralized Systems – Parsing & Translation, Optimization, Code generation, Example Query Processing in Distributed Systems – Mapping global query to local, Optimization,
A Reference architecture for the Internet of things 



A Reference architecture for the Internet of things WSO2 This document discusses WSO2 products and capabilities. It mentions several WSO2 products and services for API management, integration, and identity and access management. It concludes by inviting the reader to contact them for more information on how WSO2 products can address their needs.
Cloud computing lab experiments



Cloud computing lab experimentsrichendraravi This document outlines the curriculum for a Cloud Computing lab class, including 7 experiments covering topics like Hadoop MapReduce, HDFS, deploying and using cloud services, managing cloud resources, security compliance in the cloud, performance evaluation of cloud services, and case studies of platforms like Google App Engine, Microsoft Azure, Hadoop and Amazon. It is signed by the head of the computer science department.
Database fragmentation



Database fragmentationPunjab College Of Technical Education This document discusses database fragmentation in distributed database management systems (DDBMS). Database fragmentation allows a single database object to be broken into multiple segments that can be stored across different sites on a network. This improves efficiency, security, parallelism, availability, reliability and performance. There are three main types of fragmentation: horizontal, vertical, and mixed. Horizontal fragmentation breaks data by attributes like location, vertical by attributes like departments, and mixed uses both. While fragmentation provides advantages, it also increases complexity, cost, and makes security and integrity control more difficult.
Lec1,2



Lec1,2alaa223 This document provides an overview of information retrieval systems, including their definition, objectives, and key functional processes. An information retrieval system aims to minimize the time and effort users spend locating needed information by supporting search generation, presenting relevant results, and allowing iterative refinement of searches. The major functional processes involve normalizing input items, selectively disseminating new items to users, searching archived documents and user-created indexes. Information retrieval systems differ from database management systems in their handling of unstructured text-based information rather than strictly structured data.
remote procedure calls



remote procedure callsAshish Kumar Remote Procedure Calls (RPC) allow a program to execute a procedure in another address space without needing to know where it is located. RPC uses client and server stubs that conceal the underlying message passing between client and server processes. The client stub packs the procedure call into a message and sends it to the server stub, which unpacks it and executes the procedure before returning any results. This makes remote procedure calls appear as local procedure calls to improve transparency. IDL is used to define interfaces and generate client/server stubs automatically to simplify development of distributed applications using RPC.
Distributed DBMS - Unit 1 - Introduction



Distributed DBMS - Unit 1 - IntroductionGyanmanjari Institute Of Technology Introduction: Distributed Data Processing, Distributed Database Systems, Promises of DDBSs, Complicating factors, Problem areas
Wot



WotPRAVEENSRC2113003011 The document discusses the Web of Things and Cloud of Things. It describes the Web of Things as using existing web standards to simplify creating IoT applications by allowing real-world objects to be part of the World Wide Web. The Cloud of Things leverages cloud computing technologies to support the IoT. Standards like SOA and middleware platforms are discussed as ways to provide unified architectures for the Web and Cloud of Things.
Memory management



Memory managementRajni Sirohi The document discusses memory management in operating systems. It covers key concepts like logical versus physical addresses, binding logical addresses to physical addresses, and different approaches to allocating memory like contiguous allocation. It also discusses dynamic storage allocation using a buddy system to merge adjacent free spaces, as well as compaction techniques to reduce external fragmentation by moving free memory blocks together. Memory management aims to efficiently share physical memory between processes using mechanisms like partitioning memory and enforcing protection boundaries.
Nano computing.



Nano computing.Sunny Sundeep The document discusses nano computing, which uses devices that are extremely small, around 100 nm in size. It describes different types of nano computers including electronic, mechanical, chemical, and quantum. It explains how nano computing works by storing data using atomic quantum states or spin. The advantages are high performance, low power usage, and smaller devices. Challenges include the high costs and difficulties of manufacturing at the nano scale. The future of nano computing could include new memory technologies and standards to utilize the new systems.
Introduction to parallel processing



Introduction to parallel processingPage Maker This presentation contains flynn's classification,difference between SIMD and MIMD some applications of parallel processing
Mining single dimensional boolean association rules from transactional



Mining single dimensional boolean association rules from transactionalramya marichamy The document discusses mining frequent itemsets and generating association rules from transactional databases. It introduces the Apriori algorithm, which uses a candidate generation-and-test approach to iteratively find frequent itemsets. Several improvements to Apriori's efficiency are also presented, such as hashing techniques, transaction reduction, and approaches that avoid candidate generation like FP-trees. The document concludes by discussing how Apriori can be applied to answer iceberg queries, a common operation in market basket analysis.
Message and Stream Oriented Communication



Message and Stream Oriented CommunicationDilum Bandara Message and Stream Oriented Communication in distributed systems. Persistent vs. Transient Communication. Event queues, Pub/sub networks, MPI, Stream-based communication, Multicast communication
Cloud Computing_Unit 1- Part 1.pptx



Cloud Computing_Unit 1- Part 1.pptxVivek Shelke Cloud Computing at a Glance, the Vision of Cloud Computing, Defining a Cloud, A Closer Look, Cloud Computing Reference Model, Characteristics and Benefits, Challenges Ahead, Historical Developments. Virtualization: Introduction, Characteristics of Virtualized Environment, Taxonomy of Virtualization Techniques, Virtualization and Cloud computing, Pros and Cons of Virtualization, Technology Examples- VMware and Microsoft Hyper-V.
Chapter 12 - Mass Storage Systems



Chapter 12 - Mass Storage SystemsWayne Jones Jnr Chapter 12 discusses mass storage systems and their role in operating systems. It describes the physical structure of disks and tapes and how they are accessed. Disks are organized into logical blocks that are mapped to physical sectors. Disks connect to computers via I/O buses and controllers. RAID systems improve reliability through redundancy across multiple disks. Operating systems provide services for disk scheduling, management, and swap space. Tertiary storage uses tape drives and removable disks to archive less frequently used data in large installations.
Lec 4.ppt



Lec 4.pptSami Mughal The document discusses various software architectures, including layered architecture, virtual machines, and interaction architectures like Model View Controller (MVC). It describes layered architecture as decomposing a system into hierarchical layers, with each layer having a defined responsibility. MVC separates an application into three components - the model, the view, and the controller. The model manages the data and business logic, the view displays the data, and the controller handles input and invoking changes. Variations like MVC-II separate the controller and view into distinct modules. Overall the document provides an overview of common software architectures and design patterns for structuring interactive applications.
J2 ee archi



J2 ee archisaurabhshertukde This document discusses J2EE (Java 2 Platform, Enterprise Edition), which is a Java platform for developing and running large-scale, multi-tiered, scalable, reliable, and secure network applications. It provides an architecture that simplifies development and maintenance of enterprise applications. Some key points made are:
- J2EE aims to reduce server downtime, increase scalability, provide application stability, security and simplicity.
- It allows "develop once, deploy anywhere" capability and supports n-tier architectures and component-based development.
- J2EE applications are best suited for tasks like providing access to corporate databases, building dynamic web apps, automating communications, and implementing complex business logic.
Ad
More Related Content
What's hot (20)
Block Level and File Level



Block Level and File LevelIntegral university, India Types of Virtualization, Block and File level, comparison of both, protocols needed to implement these.
Deductive databases



Deductive databasesJohn Popoola A presentation on a special category of databases called Deductive Databases. It is an attempt to merge logic programming with relational database. Other types include Object-oriented databases, Graph databases, XML databases, Multi-model databases, etc.
Real time scheduling - basic concepts



Real time scheduling - basic conceptsStudent About real time system task scheduling basic concepts.It deals with task, instance,data sharing and their types.It also covers various important terminologies regarding scheduling algorithms.
Client-Server Computing



Client-Server ComputingCloudbells.com Client/server computing involves separating tasks between client and server machines. The client makes requests that are processed by the server, which returns results to the client. Key elements are the client, server, and network connecting them. Major focus is on the software handling tasks like the user interface, application logic, and data management between client and server. Different types of servers specialize in files, data, computing tasks, databases, and communication between networks.
Implementation issues software engineering



Implementation issues software engineeringrishi ram khanal This document discusses various implementation issues in software development, including reuse, configuration management, and host-target development. It notes that modern software is often constructed through reuse and that configuration management is needed to track different software versions. Development usually occurs on a host system while execution is on a target system, which can have different architectures and platforms. The document provides details on different levels of reuse, configuration management activities, tools that aid development, and challenges that can arise with reuse and managing development across host-target systems.
Distributed DBMS - Unit 6 - Query Processing



Distributed DBMS - Unit 6 - Query ProcessingGyanmanjari Institute Of Technology Query Processing : Query Processing Problem, Layers of Query Processing Query Processing in Centralized Systems – Parsing & Translation, Optimization, Code generation, Example Query Processing in Distributed Systems – Mapping global query to local, Optimization,
A Reference architecture for the Internet of things 



A Reference architecture for the Internet of things WSO2 This document discusses WSO2 products and capabilities. It mentions several WSO2 products and services for API management, integration, and identity and access management. It concludes by inviting the reader to contact them for more information on how WSO2 products can address their needs.
Cloud computing lab experiments



Cloud computing lab experimentsrichendraravi This document outlines the curriculum for a Cloud Computing lab class, including 7 experiments covering topics like Hadoop MapReduce, HDFS, deploying and using cloud services, managing cloud resources, security compliance in the cloud, performance evaluation of cloud services, and case studies of platforms like Google App Engine, Microsoft Azure, Hadoop and Amazon. It is signed by the head of the computer science department.
Database fragmentation



Database fragmentationPunjab College Of Technical Education This document discusses database fragmentation in distributed database management systems (DDBMS). Database fragmentation allows a single database object to be broken into multiple segments that can be stored across different sites on a network. This improves efficiency, security, parallelism, availability, reliability and performance. There are three main types of fragmentation: horizontal, vertical, and mixed. Horizontal fragmentation breaks data by attributes like location, vertical by attributes like departments, and mixed uses both. While fragmentation provides advantages, it also increases complexity, cost, and makes security and integrity control more difficult.
Lec1,2



Lec1,2alaa223 This document provides an overview of information retrieval systems, including their definition, objectives, and key functional processes. An information retrieval system aims to minimize the time and effort users spend locating needed information by supporting search generation, presenting relevant results, and allowing iterative refinement of searches. The major functional processes involve normalizing input items, selectively disseminating new items to users, searching archived documents and user-created indexes. Information retrieval systems differ from database management systems in their handling of unstructured text-based information rather than strictly structured data.
remote procedure calls



remote procedure callsAshish Kumar Remote Procedure Calls (RPC) allow a program to execute a procedure in another address space without needing to know where it is located. RPC uses client and server stubs that conceal the underlying message passing between client and server processes. The client stub packs the procedure call into a message and sends it to the server stub, which unpacks it and executes the procedure before returning any results. This makes remote procedure calls appear as local procedure calls to improve transparency. IDL is used to define interfaces and generate client/server stubs automatically to simplify development of distributed applications using RPC.
Distributed DBMS - Unit 1 - Introduction



Distributed DBMS - Unit 1 - IntroductionGyanmanjari Institute Of Technology Introduction: Distributed Data Processing, Distributed Database Systems, Promises of DDBSs, Complicating factors, Problem areas
Wot



WotPRAVEENSRC2113003011 The document discusses the Web of Things and Cloud of Things. It describes the Web of Things as using existing web standards to simplify creating IoT applications by allowing real-world objects to be part of the World Wide Web. The Cloud of Things leverages cloud computing technologies to support the IoT. Standards like SOA and middleware platforms are discussed as ways to provide unified architectures for the Web and Cloud of Things.
Memory management



Memory managementRajni Sirohi The document discusses memory management in operating systems. It covers key concepts like logical versus physical addresses, binding logical addresses to physical addresses, and different approaches to allocating memory like contiguous allocation. It also discusses dynamic storage allocation using a buddy system to merge adjacent free spaces, as well as compaction techniques to reduce external fragmentation by moving free memory blocks together. Memory management aims to efficiently share physical memory between processes using mechanisms like partitioning memory and enforcing protection boundaries.
Nano computing.



Nano computing.Sunny Sundeep The document discusses nano computing, which uses devices that are extremely small, around 100 nm in size. It describes different types of nano computers including electronic, mechanical, chemical, and quantum. It explains how nano computing works by storing data using atomic quantum states or spin. The advantages are high performance, low power usage, and smaller devices. Challenges include the high costs and difficulties of manufacturing at the nano scale. The future of nano computing could include new memory technologies and standards to utilize the new systems.
Introduction to parallel processing



Introduction to parallel processingPage Maker This presentation contains flynn's classification,difference between SIMD and MIMD some applications of parallel processing
Mining single dimensional boolean association rules from transactional



Mining single dimensional boolean association rules from transactionalramya marichamy The document discusses mining frequent itemsets and generating association rules from transactional databases. It introduces the Apriori algorithm, which uses a candidate generation-and-test approach to iteratively find frequent itemsets. Several improvements to Apriori's efficiency are also presented, such as hashing techniques, transaction reduction, and approaches that avoid candidate generation like FP-trees. The document concludes by discussing how Apriori can be applied to answer iceberg queries, a common operation in market basket analysis.
Message and Stream Oriented Communication



Message and Stream Oriented CommunicationDilum Bandara Message and Stream Oriented Communication in distributed systems. Persistent vs. Transient Communication. Event queues, Pub/sub networks, MPI, Stream-based communication, Multicast communication
Cloud Computing_Unit 1- Part 1.pptx



Cloud Computing_Unit 1- Part 1.pptxVivek Shelke Cloud Computing at a Glance, the Vision of Cloud Computing, Defining a Cloud, A Closer Look, Cloud Computing Reference Model, Characteristics and Benefits, Challenges Ahead, Historical Developments. Virtualization: Introduction, Characteristics of Virtualized Environment, Taxonomy of Virtualization Techniques, Virtualization and Cloud computing, Pros and Cons of Virtualization, Technology Examples- VMware and Microsoft Hyper-V.
Chapter 12 - Mass Storage Systems



Chapter 12 - Mass Storage SystemsWayne Jones Jnr Chapter 12 discusses mass storage systems and their role in operating systems. It describes the physical structure of disks and tapes and how they are accessed. Disks are organized into logical blocks that are mapped to physical sectors. Disks connect to computers via I/O buses and controllers. RAID systems improve reliability through redundancy across multiple disks. Operating systems provide services for disk scheduling, management, and swap space. Tertiary storage uses tape drives and removable disks to archive less frequently used data in large installations.
Similar to Web apps architecture (20)
Lec 4.ppt



Lec 4.pptSami Mughal The document discusses various software architectures, including layered architecture, virtual machines, and interaction architectures like Model View Controller (MVC). It describes layered architecture as decomposing a system into hierarchical layers, with each layer having a defined responsibility. MVC separates an application into three components - the model, the view, and the controller. The model manages the data and business logic, the view displays the data, and the controller handles input and invoking changes. Variations like MVC-II separate the controller and view into distinct modules. Overall the document provides an overview of common software architectures and design patterns for structuring interactive applications.
J2 ee archi



J2 ee archisaurabhshertukde This document discusses J2EE (Java 2 Platform, Enterprise Edition), which is a Java platform for developing and running large-scale, multi-tiered, scalable, reliable, and secure network applications. It provides an architecture that simplifies development and maintenance of enterprise applications. Some key points made are:
- J2EE aims to reduce server downtime, increase scalability, provide application stability, security and simplicity.
- It allows "develop once, deploy anywhere" capability and supports n-tier architectures and component-based development.
- J2EE applications are best suited for tasks like providing access to corporate databases, building dynamic web apps, automating communications, and implementing complex business logic.
2-Tier and 3-Tier Architecture of Enterprise Resource Planning



2-Tier and 3-Tier Architecture of Enterprise Resource PlanningS M Qamar Abbas This document compares 2-tier and 3-tier architecture. 2-tier architecture has a presentation layer on the client and data stored on a server, providing direct communication between the two. 3-tier architecture adds an application layer between the client and database server to process requests and business logic before communicating with the other layers. The 3-tier model is more popular as it provides benefits like improved performance, security, and scalability compared to the 2-tier architecture.
MVC Pattern. Flex implementation of MVC



MVC Pattern. Flex implementation of MVCAnton Krasnoshchok This presentation will guide you through the MVC Pattern and Flex implementation of MVC (Cairgorm and Mate Frameworks)
http://blog.go4flash.com/articles/flex-articles/mvc-pattern-presentation-cairngorm-vs-mate/
Software Architecture - Architecture Styles and Patterns-1.pdf



Software Architecture - Architecture Styles and Patterns-1.pdfjordantsagmo présente les styles architecturaux et les patterns architecturaux dans de façon claire et concis.vous y trouverez la différence explicitement présenté entre style et pattern architectural
N tier architecture



N tier architectureNidhi Saurav The document discusses N-tier architecture, which divides applications into multiple tiers or layers. A 1-tier architecture has all components on one machine. A 2-tier architecture separates the user interface from data storage. A 3-tier architecture separates the presentation, application/business logic, and data tiers. N-tier architecture provides finer granularity by separating an application into even smaller, specialized modules. This improves flexibility, scalability, and the ability to update and maintain parts of the application independently. A common example is a shopping cart application, which separates components like the user interface, business logic for tasks like payment processing, and data access into independent tiers.
N tier architecture



N tier architectureNidhi Saurav The document discusses N-tier architecture, which divides applications into multiple tiers or layers. A 1-tier architecture has all components on one machine. A 2-tier architecture separates the user interface from data storage. A 3-tier architecture separates the presentation, application/business logic, and data tiers. N-tier architecture provides finer granularity by separating an application into smaller specialized modules or functions across multiple tiers. This improves flexibility, scalability, and the ability to update or replace components independently. A common example is a shopping cart application, which separates components like the user interface, business logic for processing orders, and data storage across tiers.
N tier architecture



N tier architectureNidhi Saurav The document discusses N-tier architecture, which divides applications into multiple tiers or layers. A 1-tier architecture has all components on one machine. A 2-tier architecture separates the user interface from data storage. A 3-tier architecture separates the presentation, application/business logic, and data tiers. N-tier architecture provides finer granularity by separating an application into smaller specialized modules or functions across multiple tiers, improving flexibility and scalability. An example is a shopping cart application with tiers for the client/user interface, presentation, business logic/integration, and data.
N tier architecture



N tier architectureNidhi Saurav The document discusses N-tier architecture, which divides applications into multiple tiers or layers. A 1-tier architecture has all components on one machine. A 2-tier architecture separates the user interface from data storage. A 3-tier architecture separates the presentation, application/business logic, and data tiers. N-tier architecture provides finer granularity by separating an application into smaller specialized modules or functions across multiple tiers. This improves flexibility, scalability, and the ability to update or replace components independently. A common example is a shopping cart application, which separates components like the user interface, business logic for processing orders, and data access across different tiers or servers.
N tier architecture



N tier architectureNidhi Saurav The document discusses N-tier architecture, which divides applications into multiple tiers or layers. A 1-tier architecture has all components on one machine. A 2-tier architecture separates the user interface from data storage. A 3-tier architecture separates the presentation, application/business logic, and data tiers. N-tier architecture provides finer granularity by separating an application into smaller specialized modules or functions across multiple tiers, improving flexibility and scalability. An example is a shopping cart application, which separates components like the user interface, business logic for processing orders, and data storage across tiers.
N tier architecture



N tier architectureNidhi Saurav The document discusses N-tier architecture, which divides applications into multiple tiers or layers. A 1-tier architecture has all components on one machine. A 2-tier architecture separates the user interface from data storage. A 3-tier architecture separates the presentation, application/business logic, and data tiers. N-tier architecture provides finer granularity by separating an application into smaller specialized modules or functions across multiple tiers. This improves flexibility, scalability, and the ability to update or replace components independently. A common example is a shopping cart application, which separates components like the user interface, business logic for processing orders, and data access across different tiers or servers.
N tier architecture



N tier architectureNidhi Saurav The document discusses N-tier architecture, which divides applications into multiple tiers or layers. A 1-tier architecture has all components on one machine. A 2-tier architecture separates the user interface from data storage. A 3-tier architecture separates the presentation, application/business logic, and data tiers. N-tier architecture provides finer granularity by separating an application into smaller specialized modules or functions across multiple tiers. This improves flexibility, scalability, and the ability to update or replace components independently. A common example is a shopping cart application, which separates components like the user interface, business logic for processing orders, and data access across different tiers or servers.
N tier architecture



N tier architectureNidhi Saurav The document discusses N-tier architecture, which divides applications into multiple tiers or layers. A 1-tier architecture has all components on one machine. A 2-tier architecture separates the user interface from data storage. A 3-tier architecture separates the presentation, application/business logic, and data tiers. N-tier architecture provides finer granularity by separating an application into smaller specialized modules or functions across multiple tiers. This improves flexibility, scalability, and the ability to update or replace components independently. A common example is a shopping cart application, which separates components like the user interface, business logic for processing orders, and data access across different tiers or servers.
N tier architecture



N tier architectureNidhi Saurav The document discusses N-tier architecture, which divides applications into multiple tiers or layers. A 1-tier architecture has all components on one machine. A 2-tier architecture separates the user interface from data storage. A 3-tier architecture separates the presentation, application/business logic, and data tiers. N-tier architecture provides finer granularity by separating an application into even smaller, specialized modules. This improves flexibility, scalability, and the ability to update and maintain parts of the application independently. A common example is a shopping cart application, which separates components like the user interface, business logic for tasks like payment processing, and data access into independent tiers.
Pattern oriented architecture for web based architecture



Pattern oriented architecture for web based architectureshuchi tripathi This document discusses web application architecture and design patterns. It describes a three-layer architecture with presentation, application, and data layers. For the presentation layer, forms are commonly used to structure user interfaces. The application layer focuses on business processes and components. The data access layer exposes database data. Popular design patterns like MVC, PAC, and others are explained as ways to achieve separation of concerns and improve maintainability. MVC divides the presentation layer into separate controller and view components. PAC defines a hierarchical structure of cooperating agents with presentation, abstraction, and control components.
Web technology and commerce unit 2



Web technology and commerce unit 2arun0501 The document discusses the three-tier architecture model for web applications. It describes each of the three tiers - presentation, application, and data - and their roles. The presentation tier (web browser) sends requests to the application tier (dynamic web content like PHP), which then queries and updates the database in the data tier. This separation of concerns into logical layers allows for improved flexibility, maintainability, reusability, scalability, and reliability compared to traditional single-tier applications.
Android DesignArchitectures.pptx



Android DesignArchitectures.pptxSafnaSaff1 The document discusses several popular architecture patterns used in Android development: MVC, MVP, and MVVM. It provides details on each pattern, including how they separate the model, view, and controller/presenter layers. MVC follows the standard Android approach but can result in large activities. MVP improves on this by delegating most work to presenter objects. MVVM leverages data binding between view models and views, keeping activities lightweight. Overall, applying an architecture provides modularity, testability, and ease of maintenance.
Client server architecture in .net by varun tiwari



Client server architecture in .net by varun tiwariBosco Technical Training Society, Don Bosco Technical School (Aff. GGSIP University, New Delhi) The document discusses different application architectures: single-tier, two-tier, three-tier, and n-tier. In a single-tier architecture, all application elements exist in a single process. A two-tier architecture divides the application into client and server tiers. A three-tier architecture adds a business tier between the client and server tiers. An n-tier architecture further divides business services into multiple manageable units across multiple tiers.
Interaction-Oriented Architecture.pptx



Interaction-Oriented Architecture.pptxGodwin Monserate The document discusses interaction-oriented software architectures, specifically Model-View-Controller (MVC) and Presentation-Abstraction-Control (PAC) architectures. MVC separates a software application into three parts - the model manages the core data and logic, the view displays the data to the user, and the controller handles input. PAC uses multiple interacting agents that each contain a presentation component, abstraction component, and control component to coordinate communication. Both styles aim to separate user interaction from data processing and support interactive applications.
MVC(Model View Controller),Web,Enterprise,Mobile



MVC(Model View Controller),Web,Enterprise,Mobilenaral Model-view-controller (MVC) is a software architectural pattern that separates application logic from user interface. It is commonly used for web applications and mobile applications. MVC promotes separation of concerns, where the model manages application data and logic, the view manages presentation, and the controller manages input and interaction between model and view. MVC makes applications easier to maintain and extend through loose coupling of these components.
Client server architecture in .net by varun tiwari



Client server architecture in .net by varun tiwariBosco Technical Training Society, Don Bosco Technical School (Aff. GGSIP University, New Delhi)
Ad
More from Tanmoy Barman (7)
Java rmi



Java rmiTanmoy Barman This document defines and describes Java RMI (Remote Method Invocation). RMI allows a Java program running on one JVM to invoke methods on another JVM, enabling client-server programming. It discusses the goals of RMI including minimizing differences between local and remote objects. The architecture of RMI including layers for the application, proxies, remote references, and transport is described. Finally, it compares RMI to other remote object technologies like CORBA.
Jini



JiniTanmoy Barman JINI is a programming model that enables the configuration and deployment of distributed systems. It allows devices to easily join a community network with minimal configuration or human intervention. In a JINI network, services (resources) can be hardware or software written in Java that provide functionality through distributed interfaces. Clients can locate and access services through a lookup service. When a device joins the network, it registers with the lookup service, and clients can discover available services. This allows different users connected to the network to easily share resources.
JDBC: java DataBase connectivity



JDBC: java DataBase connectivityTanmoy Barman how to make connection to database using jdbc, step by step connection, types of driver available, jdbc data source.
Java server pages



Java server pagesTanmoy Barman JSP is a technology based on Java that produces dynamic web pages. JSP files contain HTML tags as well as special JSP tags where Java code is embedded. There are three main types of JSP elements - directives, scripting elements, and action elements. Directives provide information to the JSP engine, scripting elements contain Java code, and action elements perform tasks like accessing Java beans. Common implicit objects in JSP include application, page, session, and request objects. Java beans can be used with JSP through action tags like useBean, setProperty, and getProperty.
java Servlet technology



java Servlet technologyTanmoy Barman This document provides an overview of Java servlets including:
- Servlets allow Java code to generate dynamic web page content in response to HTTP requests. They are hosted by a servlet container inside a web server.
- The servlet lifecycle involves initialization, processing requests, and destruction. Common methods are init(), service(), destroy().
- The javax.servlet and javax.servlet.http APIs provide interfaces and classes for building servlets and handling HTTP requests/responses.
- Servlets can collaborate by forwarding or redirecting requests between servlets using methods like RequestDispatcher and HttpServletResponse.
- Session management techniques like cookies, hidden fields, and HTTP sessions allow servlets to maintain state across
introduction to channel borrowing scheme in cellular networks



introduction to channel borrowing scheme in cellular networksTanmoy Barman This document discusses channel borrowing schemes in cellular networks. It begins with an introduction to cellular networks and the limited radio spectrum allocated to them. It then describes three main types of channel allocation: fixed channel allocation, dynamic channel allocation, and hybrid channel allocation. Fixed allocation assigns specific channels to specific cells statically. Dynamic allocation allows channels to be assigned dynamically based on traffic. Hybrid allocation uses a combination of fixed and dynamic allocation. The document provides details on these schemes and compares their advantages and disadvantages.
INTRODUCTION TO CLOUD COMPUTING



INTRODUCTION TO CLOUD COMPUTINGTanmoy Barman Cloud computing refers to applications and services delivered over the internet through cloud services and infrastructure. There are different cloud service models including SaaS, PaaS, and IaaS. Cloud deployment models include private, public, hybrid, and community clouds. Cloud computing provides benefits like cost savings, scalability, reliability, and mobile access, but also poses challenges regarding security, continuous evolution, and lack of standards.
Ad
Recently uploaded (20)
Designing Low-Latency Systems with Rust and ScyllaDB: An Architectural Deep Dive



Designing Low-Latency Systems with Rust and ScyllaDB: An Architectural Deep DiveScyllaDB Want to learn practical tips for designing systems that can scale efficiently without compromising speed?
Join us for a workshop where we’ll address these challenges head-on and explore how to architect low-latency systems using Rust. During this free interactive workshop oriented for developers, engineers, and architects, we’ll cover how Rust’s unique language features and the Tokio async runtime enable high-performance application development.
As you explore key principles of designing low-latency systems with Rust, you will learn how to:
- Create and compile a real-world app with Rust
- Connect the application to ScyllaDB (NoSQL data store)
- Negotiate tradeoffs related to data modeling and querying
- Manage and monitor the database for consistently low latencies
Dev Dives: Automate and orchestrate your processes with UiPath Maestro



Dev Dives: Automate and orchestrate your processes with UiPath MaestroUiPathCommunity This session is designed to equip developers with the skills needed to build mission-critical, end-to-end processes that seamlessly orchestrate agents, people, and robots.
📕 Here's what you can expect:
- Modeling: Build end-to-end processes using BPMN.
- Implementing: Integrate agentic tasks, RPA, APIs, and advanced decisioning into processes.
- Operating: Control process instances with rewind, replay, pause, and stop functions.
- Monitoring: Use dashboards and embedded analytics for real-time insights into process instances.
This webinar is a must-attend for developers looking to enhance their agentic automation skills and orchestrate robust, mission-critical processes.
👨🏫 Speaker:
Andrei Vintila, Principal Product Manager @UiPath
This session streamed live on April 29, 2025, 16:00 CET.
Check out all our upcoming Dev Dives sessions at https://community.uipath.com/dev-dives-automation-developer-2025/.
TrsLabs - Fintech Product & Business Consulting



TrsLabs - Fintech Product & Business ConsultingTrs Labs Hybrid Growth Mandate Model with TrsLabs
Strategic Investments, Inorganic Growth, Business Model Pivoting are critical activities that business don't do/change everyday. In cases like this, it may benefit your business to choose a temporary external consultant.
An unbiased plan driven by clearcut deliverables, market dynamics and without the influence of your internal office equations empower business leaders to make right choices.
Getting things done within a budget within a timeframe is key to Growing Business - No matter whether you are a start-up or a big company
Talk to us & Unlock the competitive advantage
HCL Nomad Web – Best Practices and Managing Multiuser Environments



HCL Nomad Web – Best Practices and Managing Multiuser Environmentspanagenda Webinar Recording: https://www.panagenda.com/webinars/hcl-nomad-web-best-practices-and-managing-multiuser-environments/
HCL Nomad Web is heralded as the next generation of the HCL Notes client, offering numerous advantages such as eliminating the need for packaging, distribution, and installation. Nomad Web client upgrades will be installed “automatically” in the background. This significantly reduces the administrative footprint compared to traditional HCL Notes clients. However, troubleshooting issues in Nomad Web present unique challenges compared to the Notes client.
Join Christoph and Marc as they demonstrate how to simplify the troubleshooting process in HCL Nomad Web, ensuring a smoother and more efficient user experience.
In this webinar, we will explore effective strategies for diagnosing and resolving common problems in HCL Nomad Web, including
- Accessing the console
- Locating and interpreting log files
- Accessing the data folder within the browser’s cache (using OPFS)
- Understand the difference between single- and multi-user scenarios
- Utilizing Client Clocking
Quantum Computing Quick Research Guide by Arthur Morgan



Quantum Computing Quick Research Guide by Arthur MorganArthur Morgan This is a Quick Research Guide (QRG).
QRGs include the following:
- A brief, high-level overview of the QRG topic.
- A milestone timeline for the QRG topic.
- Links to various free online resource materials to provide a deeper dive into the QRG topic.
- Conclusion and a recommendation for at least two books available in the SJPL system on the QRG topic.
QRGs planned for the series:
- Artificial Intelligence QRG
- Quantum Computing QRG
- Big Data Analytics QRG
- Spacecraft Guidance, Navigation & Control QRG (coming 2026)
- UK Home Computing & The Birth of ARM QRG (coming 2027)
Any questions or comments?
- Please contact Arthur Morgan at [email protected].
100% human made.
Procurement Insights Cost To Value Guide.pptx



Procurement Insights Cost To Value Guide.pptxJon Hansen Procurement Insights integrated Historic Procurement Industry Archives, serves as a powerful complement — not a competitor — to other procurement industry firms. It fills critical gaps in depth, agility, and contextual insight that most traditional analyst and association models overlook.
Learn more about this value- driven proprietary service offering here.
Mobile App Development Company in Saudi Arabia



Mobile App Development Company in Saudi ArabiaSteve Jonas EmizenTech is a globally recognized software development company, proudly serving businesses since 2013. With over 11+ years of industry experience and a team of 200+ skilled professionals, we have successfully delivered 1200+ projects across various sectors. As a leading Mobile App Development Company In Saudi Arabia we offer end-to-end solutions for iOS, Android, and cross-platform applications. Our apps are known for their user-friendly interfaces, scalability, high performance, and strong security features. We tailor each mobile application to meet the unique needs of different industries, ensuring a seamless user experience. EmizenTech is committed to turning your vision into a powerful digital product that drives growth, innovation, and long-term success in the competitive mobile landscape of Saudi Arabia.
Linux Support for SMARC: How Toradex Empowers Embedded Developers



Linux Support for SMARC: How Toradex Empowers Embedded DevelopersToradex Toradex brings robust Linux support to SMARC (Smart Mobility Architecture), ensuring high performance and long-term reliability for embedded applications. Here’s how:
• Optimized Torizon OS & Yocto Support – Toradex provides Torizon OS, a Debian-based easy-to-use platform, and Yocto BSPs for customized Linux images on SMARC modules.
• Seamless Integration with i.MX 8M Plus and i.MX 95 – Toradex SMARC solutions leverage NXP’s i.MX 8 M Plus and i.MX 95 SoCs, delivering power efficiency and AI-ready performance.
• Secure and Reliable – With Secure Boot, over-the-air (OTA) updates, and LTS kernel support, Toradex ensures industrial-grade security and longevity.
• Containerized Workflows for AI & IoT – Support for Docker, ROS, and real-time Linux enables scalable AI, ML, and IoT applications.
• Strong Ecosystem & Developer Support – Toradex offers comprehensive documentation, developer tools, and dedicated support, accelerating time-to-market.
With Toradex’s Linux support for SMARC, developers get a scalable, secure, and high-performance solution for industrial, medical, and AI-driven applications.
Do you have a specific project or application in mind where you're considering SMARC? We can help with Free Compatibility Check and help you with quick time-to-market
For more information: https://www.toradex.com/computer-on-modules/smarc-arm-family
Special Meetup Edition - TDX Bengaluru Meetup #52.pptx



Special Meetup Edition - TDX Bengaluru Meetup #52.pptxshyamraj55 We’re bringing the TDX energy to our community with 2 power-packed sessions:
🛠️ Workshop: MuleSoft for Agentforce
Explore the new version of our hands-on workshop featuring the latest Topic Center and API Catalog updates.
📄 Talk: Power Up Document Processing
Dive into smart automation with MuleSoft IDP, NLP, and Einstein AI for intelligent document workflows.
AI EngineHost Review: Revolutionary USA Datacenter-Based Hosting with NVIDIA ...



AI EngineHost Review: Revolutionary USA Datacenter-Based Hosting with NVIDIA ...SOFTTECHHUB I started my online journey with several hosting services before stumbling upon Ai EngineHost. At first, the idea of paying one fee and getting lifetime access seemed too good to pass up. The platform is built on reliable US-based servers, ensuring your projects run at high speeds and remain safe. Let me take you step by step through its benefits and features as I explain why this hosting solution is a perfect fit for digital entrepreneurs.
Transcript: #StandardsGoals for 2025: Standards & certification roundup - Tec...



Transcript: #StandardsGoals for 2025: Standards & certification roundup - Tec...BookNet Canada Book industry standards are evolving rapidly. In the first part of this session, we’ll share an overview of key developments from 2024 and the early months of 2025. Then, BookNet’s resident standards expert, Tom Richardson, and CEO, Lauren Stewart, have a forward-looking conversation about what’s next.
Link to recording, presentation slides, and accompanying resource: https://bnctechforum.ca/sessions/standardsgoals-for-2025-standards-certification-roundup/
Presented by BookNet Canada on May 6, 2025 with support from the Department of Canadian Heritage.
#StandardsGoals for 2025: Standards & certification roundup - Tech Forum 2025



#StandardsGoals for 2025: Standards & certification roundup - Tech Forum 2025BookNet Canada Book industry standards are evolving rapidly. In the first part of this session, we’ll share an overview of key developments from 2024 and the early months of 2025. Then, BookNet’s resident standards expert, Tom Richardson, and CEO, Lauren Stewart, have a forward-looking conversation about what’s next.
Link to recording, transcript, and accompanying resource: https://bnctechforum.ca/sessions/standardsgoals-for-2025-standards-certification-roundup/
Presented by BookNet Canada on May 6, 2025 with support from the Department of Canadian Heritage.
How analogue intelligence complements AI



How analogue intelligence complements AIPaul Rowe
Artificial Intelligence is providing benefits in many areas of work within the heritage sector, from image analysis, to ideas generation, and new research tools. However, it is more critical than ever for people, with analogue intelligence, to ensure the integrity and ethical use of AI. Including real people can improve the use of AI by identifying potential biases, cross-checking results, refining workflows, and providing contextual relevance to AI-driven results.
News about the impact of AI often paints a rosy picture. In practice, there are many potential pitfalls. This presentation discusses these issues and looks at the role of analogue intelligence and analogue interfaces in providing the best results to our audiences. How do we deal with factually incorrect results? How do we get content generated that better reflects the diversity of our communities? What roles are there for physical, in-person experiences in the digital world?
Enhancing ICU Intelligence: How Our Functional Testing Enabled a Healthcare I...



Enhancing ICU Intelligence: How Our Functional Testing Enabled a Healthcare I...Impelsys Inc. Impelsys provided a robust testing solution, leveraging a risk-based and requirement-mapped approach to validate ICU Connect and CritiXpert. A well-defined test suite was developed to assess data communication, clinical data collection, transformation, and visualization across integrated devices.
The Evolution of Meme Coins A New Era for Digital Currency ppt.pdf



The Evolution of Meme Coins A New Era for Digital Currency ppt.pdfAbi john Analyze the growth of meme coins from mere online jokes to potential assets in the digital economy. Explore the community, culture, and utility as they elevate themselves to a new era in cryptocurrency.
DevOpsDays Atlanta 2025 - Building 10x Development Organizations.pptx



DevOpsDays Atlanta 2025 - Building 10x Development Organizations.pptxJustin Reock Building 10x Organizations with Modern Productivity Metrics
10x developers may be a myth, but 10x organizations are very real, as proven by the influential study performed in the 1980s, ‘The Coding War Games.’
Right now, here in early 2025, we seem to be experiencing YAPP (Yet Another Productivity Philosophy), and that philosophy is converging on developer experience. It seems that with every new method we invent for the delivery of products, whether physical or virtual, we reinvent productivity philosophies to go alongside them.
But which of these approaches actually work? DORA? SPACE? DevEx? What should we invest in and create urgency behind today, so that we don’t find ourselves having the same discussion again in a decade?
Generative Artificial Intelligence (GenAI) in Business



Generative Artificial Intelligence (GenAI) in BusinessDr. Tathagat Varma My talk for the Indian School of Business (ISB) Emerging Leaders Program Cohort 9. In this talk, I discussed key issues around adoption of GenAI in business - benefits, opportunities and limitations. I also discussed how my research on Theory of Cognitive Chasms helps address some of these issues
Splunk Security Update | Public Sector Summit Germany 2025



Splunk Security Update | Public Sector Summit Germany 2025Splunk Splunk Security Update
Sprecher: Marcel Tanuatmadja
Web apps architecture
- 1. 1-tier,2-tier, 3-tier and MVC Different Web apps Architectures by Tanmoy Barman
- 2. Contents Why n-tier? Layers. Monolithic or 1-tier architecture. 2-tier architecture. 3-tier architecture. Need of MVC. MVC architecture. MVC components. Comparison between MVC and 3-tier.
- 3. Why n-tier? Need of e-commerce solutions; increase in users and merchant sites all over the world. Applications should be scalable, user-friendly, have tight security and easily maintainable.
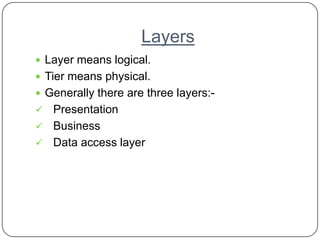
- 4. Layers Layer means logical. Tier means physical. Generally there are three layers:- Presentation Business Data access layer
- 5. Layers Presentation Layer:- involves with client and application interaction. Provides user friendly interface for the clients. Business Layer:- contains the application code or the core functionalities of the application or what the application will perform. Data access Layer:- involves with the maintaining database and storage of data.
- 7. Monolithic or 1-tier Presentation layer, Business layer and Data Access layer are tightly connected. As the layers are tightly connected(depends on each other), if any of the layer code are changed then other layers should be affected and the codes in other layers need to be changed.
- 8. Monolithic or 1-tier Traditional approaches of the applications are based on this type of architecture. Typically implementation of 1-tier architecture can be a C program running in a computer.
- 9. 2-tier
- 10. 2-tier In this type of architectures the presentation layer, the business logic layer are separated from the data access layer. The advantages of this layer is that the code of the data access layer can be changed any time without affecting the code of the other layer i.e. the whole database and the layer can be changed anytime. The database(i.e. the data access layer) can be present anywhere around but the other two layers should be together(tightly connected).
- 11. 2-tier As the presentation and the business logic are still connected they should be present at the client side to work together; due to the concentration of the client this type of client is called thick client. Problems faced by this type of architecture is the client should always get the updated copies of the application if there is a change in the application codes or application developer modifies the application. The application developer may not want to give the code to the relatively third parities even if the code is pre compiled.
- 12. 2-tier Another problem is that the client may not want to install the code into his/her machine for using a particular application.
- 13. 3-tier
- 14. 3-tier In this type of architecture the presentation layer, the business logic layer and the data access layer are separated from each other and are present on three different tiers therefore they are loosely connected. The main advantages is that any change in the code in one layer will not affect the other layers and the platform can also be changed independently. Now the web designer can concentrate on the design of the user interface i.e. the presentation logic, the application developer concentrate on developing the application i.e. the business logic and the database manager can handle the
- 15. 3-tier Today’s application are based on 3-tier architecture which are scalable, easy to maintain, components are reusable and faster development.
- 16. Need of MVC Architecture Need to access the data from different context such as mobiles, touch screen, desktop, etc. Need to show the data in different context such as mobiles, touch screen, desktop, etc. Need to show multiple views of the same data such as Thumbnails, List or details. Need to change the designs without changing the core business logic.
- 17. MVC Solutions Separate the core business logic form the presentation logic. Separate views for the same data.
- 18. MVC Architecture
- 19. MVC Components Model: It contains the core functionalities and the business logic of the application. It accepts the state query from the model and controller and it provides the updated information to the view component. View: This component is responsible for the presentation logic and the user interaction between the application. The model provides different information to different user which can be represented in different ways. The main work of the view component is to provide the suitable information to the user.
- 20. MVC Components Controller: It accepts the user input through the view component and process them and if any changes are required then it perform the changes after that it response to the client.
- 21. MVC Vs. 3-tier In MVC architecture the components communicate directly with each other in order to maintain a coherent user interaction but in case of 3-tier the presentation layer(front end) communicates with the data access layer(back end) through the business layer(middleware). In 3-tier the Layers are present on three different tiers or machines where as in MVC the layers are present on single tier or machines.
- 22. Thank You


