WEBINAR: Positive Security for APIs: What it is and why you need it!
- 1. Securing an API World A POSITIVE SECURITY MODEL FOR APIS ISABELLEMAUNY [email protected]
- 3. © COPYRIGHT 42CRUNCH | CONFIDENTIAL NEGATIVE SECURITY MODEL (BLACKLIST) 3 Access Allowed by default Block access for suspicious traffic Threats centric
- 4. © COPYRIGHT 42CRUNCH | CONFIDENTIAL POSITIVE SECURITY MODEL (WHITELIST) 4 Access Denied by default Allow Access only to approved traffic Trust centric
- 5. © COPYRIGHT 42CRUNCH | CONFIDENTIAL WHY A POSITIVE MODEL ? Much stricter access control Limited false positives More efficient ✓ Simple vs. very complex regular expressions for blacklisting No need to update when new threats are found 5
- 6. However…
- 7. © COPYRIGHT 42CRUNCH | CONFIDENTIAL KEEPING UP IS HARD… A whitelist is only powerful if complete! It requires lots of efforts to define and maintain up to date with constant applications changes ✓ High human cost, usually several people full time Traditionally been very hard to implement ✓ Which is why default WAF model is blacklisting 7
- 8. © COPYRIGHT 42CRUNCH | CONFIDENTIAL …BUT APIS ARE DIFFERENT! OpenAPI specification (OAS) can be leveraged to describe the API contract. Can be easily updated from code, or via specialized tools, so the whitelist is always in sync with the application. You can start addressing security straight from design time! OpenAPI lets you build the ultimate whitelist! ✓ And as bonus , you get better documentation! 8 OPENAPI INITIATIVE
- 9. © COPYRIGHT 42CRUNCH | CONFIDENTIAL HOW 42CRUNCH LEVERAGES OAS 9 Audit Service performs 200+ security checks on API Contract Scan service ensures API implementation conforms to API contract Protection service is automatically configured from API contract
- 10. © COPYRIGHT 42CRUNCH | CONFIDENTIAL OWASP API SECURITY TOP 10 10 • API1 : Broken Object Level Authorisation • API2 : Broken Authentication • API3 : Excessive Data Exposure • API4 : Lack of Resources & Rate Limiting • API5 : Missing Function/Resource Level Access Control • API6 : Mass Assignment • API7 : Security Misconfiguration • API8 : Injection • API9 : Improper Assets Management • API10 : Insufficient Logging & Monitoring DOWNLOAD
- 11. Addressing API threats with a positive model
- 12. © COPYRIGHT 42CRUNCH | CONFIDENTIAL EQUIFAX AND MANY MORE COMPANIES (2017) The Attack ✓ Remote command injection attack: server executes commands written in ONGL language when a Content-Type validation error is raised. ✓ Can also be exploited using the Content-Disposition or Content-Length headers The Breach ✓ One of the most important in history: 147 millions people worldwide, very sensitive data ✓ Equifax got fined $700 million in Sept 2019 Core Issue ✓ Remote command injection vulnerability in Apache Struts widely exploited during months. 12 A2 A3 A4 A5 A6 A10 A9 A8 A7 A1 https://blog.talosintelligence.com/2017/03/apache-0-day-exploited.html
- 13. © COPYRIGHT 42CRUNCH | CONFIDENTIAL CONTENT-TYPE IN OAS Declare “consumes” at API or operation level ✓ Limits Content-Type header value to specific mime types Declare all request headers 13 "consumes": [ “application/x-www-form-urlencoded”, “application/json” ],
- 14. © COPYRIGHT 42CRUNCH | CONFIDENTIAL HOW 42CRUNCH ADDRESSES THE PROBLEM At Audit time ✓ Detect that Consumes is not defined At Scan time ✓ Inject wrong Content-Type ✓ Inject wrong formats for all listed headers At Runtime ✓ Block any Content-Type that does not match Consumes value at Runtime ✓ Block any header not matching the description ✓ Block inbound data that does not match the Content-Type 14
- 15. © COPYRIGHT 42CRUNCH | CONFIDENTIAL HARBOUR REGISTRY The Attack ✓ Privilege escalation: become registry administrator The Breach ✓ 1300+ registries with default security settings Core Issue ✓ Mass Assignment vulnerability allows any normal user to become an admin ✓ POST /api/users {“username”:”test”,”email”:”[email protected]”,”realname ”:”noname”,”password”:”Password1u0021″,”comment”:null, “has_admin_role” = True} 15 A2 A3 A4 A5 A6 A10 A9 A8 A7 A1 https://unit42.paloaltonetworks.com/critical-vulnerability-in-harbor-enables-privilege-escalation-from-zero-to-admin-cve-2019-16097/
- 16. © COPYRIGHT 42CRUNCH | CONFIDENTIAL HOW OAS CAN BE USED ? Describe inbound schema for all requests Use different schemas by operation (retrieve user data vs. update user data) 16 "UsersItem": { "type": "object", "additionalProperties": false, "properties": { "_id": { "type": "number", "format": "integer", "minimum": 0, "maximum": 999999 }, "email": { "type": "string", "format": "email", "pattern": “<email_regex>”, "minLength": 10, "maxLength": 60 },… "is_admin": { "description": "is admin", "type": "boolean" }, …
- 17. © COPYRIGHT 42CRUNCH | CONFIDENTIAL HOW 42CRUNCH ADDRESSES THE PROBLEM At Audit time ✓ Detects that schemas are not associated to requests ✓ Analyzes how well data is defined (patterns, min, max, enums) ✓ Highlights usage of “additional properties” At Scan time ✓ Injects additional properties ✓ Injects improper data At Runtime ✓ Enforces schema definition ✓ Enforces Additional Properties restrictions ✓ Block non-declared VERBs (block unwanted POST) 17
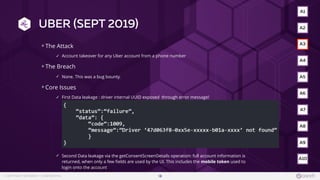
- 18. © COPYRIGHT 42CRUNCH | CONFIDENTIAL UBER (SEPT 2019) The Attack ✓ Account takeover for any Uber account from a phone number The Breach ✓ None. This was a bug bounty. Core Issues ✓ First Data leakage : driver internal UUID exposed through error message! ✓ Second Data leakage via the getConsentScreenDetails operation: full account information is returned, when only a few fields are used by the UI. This includes the mobile token used to login onto the account 18 A2 A3 A4 A5 A6 A10 A9 A8 A7 A1
- 19. © COPYRIGHT 42CRUNCH | CONFIDENTIAL HOW OAS CAN BE USED ? Describe thoroughly all potential responses Define the produces value ✓ Which data will be returned Use different schemas by operation (retrieve user data vs. update user data) 19 ”produces”: [ "application/json" ], "responses": { "200": { "description": “successful..”, "schema": { "type": "array", "minItems": 0, "maxItems": 50, "items": { "$ref": "#/definitions/ UsersItem" } } "403": { "description": “invalid…”, "schema": { "type": "object", "properties": { "message": { "type": "string", "pattern": "xxxx", "minLength": 1, "maxLength": 255 }, “success”: …
- 20. © COPYRIGHT 42CRUNCH | CONFIDENTIAL HOW 42CRUNCH ADDRESSES THE PROBLEM At Audit time ✓ Analyzes which responses should be defined depending on verb (GET, POST, …) ✓ Detects that schemas are not associated to responses ✓ Analyzes how well data is defined (patterns, min, max, enums) ✓ Highlights usage of “additional properties” At Scan time ✓ Validates responses are all defined in contract ✓ Validates responses match schemas defined in contract At Runtime ✓ Block responses that do not match “Produces” value (unknown mime-type) ✓ Blocks responses that do not match schema definition ✓ Block non-declared responses (unknown HTTP codes) ✓ Enforces Additional Properties restrictions 20
- 21. © COPYRIGHT 42CRUNCH | CONFIDENTIAL A POSITIVE MODEL FOR API SECURITY WITH 42CRUNCH Leverage OAS and build the ultimate whitelist at design time! ✓ Right in your IDE with our VSCode extension ✓ Thorough report with priorities to act upon Ensure API Contract is up to date via automated audit and scan at integration/testing time ✓ Include API Contract audit and scan in your favorite CI/CD pipeline Leverage the power of OAS to protect your APIs at runtime ✓ Lightweight, Kubernetes-ready firewall to automatically protect your APIs from API contract! 21
- 22. Securing an API World CONTACT US: [email protected] Start testing your API contracts today on apisecurity.io!
- 23. © COPYRIGHT 42CRUNCH | CONFIDENTIAL RESOURCES • 42Crunch Website • Free OAS Security Audit • OpenAPI VS Code Extension • OpenAPI Spec Encyclopedia • OWASP API Security Top 10 • APIsecurity.io













![© COPYRIGHT 42CRUNCH | CONFIDENTIAL
CONTENT-TYPE IN OAS
Declare “consumes” at API or operation level
✓ Limits Content-Type header value to specific mime types
Declare all request headers
13
"consumes": [
“application/x-www-form-urlencoded”,
“application/json”
],](https://image.slidesharecdn.com/42crunch-positivesecuritymodel-webinar-191216190825/85/WEBINAR-Positive-Security-for-APIs-What-it-is-and-why-you-need-it-13-320.jpg)




![© COPYRIGHT 42CRUNCH | CONFIDENTIAL
HOW OAS CAN BE USED ?
Describe thoroughly all potential responses
Define the produces value
✓ Which data will be returned
Use different schemas by operation (retrieve
user data vs. update user data)
19
”produces”: [
"application/json"
],
"responses": {
"200": {
"description": “successful..”,
"schema": {
"type": "array",
"minItems": 0,
"maxItems": 50,
"items": {
"$ref": "#/definitions/
UsersItem"
}
}
"403": {
"description": “invalid…”,
"schema": {
"type": "object",
"properties": {
"message": {
"type": "string",
"pattern": "xxxx",
"minLength": 1,
"maxLength": 255
},
“success”: …](https://image.slidesharecdn.com/42crunch-positivesecuritymodel-webinar-191216190825/85/WEBINAR-Positive-Security-for-APIs-What-it-is-and-why-you-need-it-19-320.jpg)



