Why Security Engineer Need Shift-Left to DevSecOps?
- 1. Why Security Engineers Need to Shift-Left to DevSecOps Najib Radzuan
- 2. Agenda ○ ○
- 3. About Me Najib Radzuan ● He was a Developer ● He became IT Operations ● Finally become DevOps Engineer/ DevOps Leader / DevOps Institute Ambassador ● He is also a certified DevOps Leader, DevSecOps Professional , Azure DevOps Expert, & etc. ● Founder of DevOps4Me @devops4me @najibradzuan blog.devops4me.com
- 4. The Pitfall: Security & Compliance Company ● Failure to recognise cybersecurity basics ● Lack of Cybersecurity Policy ● Not enough IT Security Management Application Developer ● Uses Open-Source library which has a lot of security bug risks ● They don't have formal Application security training. ● Lacks a recovery plan for vulnerability risks. AppSec / InfoSec Eng. ● Not involved in product design/development ● The last person to handle security and compliance issues ● Cannot compete with Agility and Speed of DevOps team. ● DevSecOps also added to the pain due lack of CI/CD knowledge
- 5. Traditional Security Testing Plan Code Build Test Release Deploy Operate Monitor Security Testing The Pitfall ● A code review or penetration test it's conducted to find security flaws in the application at last Stage/Production environment. Your Developer might redo to eliminate the vulnerability. ● Bug/issue found when the project deadline is near or last-minute = project delayed ● Sometimes a bug/vulnerability is found by the client or external pentester Question: Do we expect all Developers to do security testing and do not make mistakes?
- 6. Solution DevSecOps & Shift-Left Approach ● Shifting left lets us deal with security issues early and often ● So shifting left reduces risk and the costs of fixing security issues.
- 7. DevSecOps DevSecOps is a modern model that provides that everyone in the team is responsible for security implementation in the application, from planning , design , development, QA / Testing to release, and in a production environment. Development Quality Assurance IT Operation Security DevSecOps
- 8. DevSecOps Benefit ● Cost-saving is accomplish by identifying and addressing security vulnerabilities during the development process, which also improves the speed of delivery. ● It Improved overall security by reducing vulnerabilities, reducing insecure defaults and increasing code coverage and automation by the use of Infrastructure as Code (IaC). ● Everyone is responsible for security. DevSecOps fosters a culture of transparency and accountability from the earliest stages of development. ● With help of DevSecOps, we are keeping up-to-date with the rapid creativity common to cybercrime by effectively managing security auditing, monitoring and notification systems.
- 9. DevSecOps Practice Practice Secure CodingEmbrace AutomationShift-LeftPeople Process - Neutralize senior management mindset in order for DevSecOps' strategy to be embraced. - Security specialists or “Security Champions” will play a key role in getting your DevSecOps journey right. - Training developers on how to develop secure code are important to note. - Until now, developer teams may have not prioritized this because the coding is the priority. However, security needs to be made aware of security-related facts in DevOps culture. - The obvious advantage of doing this is that you can recognise possible vulnerabilities and work to fix them faster. - The faster you notice any bugs, the cheaper it will be for you to fix them. - Automation is a key feature of DevSecOps to match the speed of security with your product delivery in a CI / CD environment, security automation is a must. - Choosing and continuing learning with the right security automation tool is key to the success of your company's products. - In general, different teams within an organization execute various tasks, with DevSecOps, everyone works on commonly agreed-upon processes and executing them to strengthen the extent of security in development.
- 10. DevSecOps Approach Pre-Commit Hooks IDE Plugin Developer Secrets Management Source Code - Software Composition Analysis (SCA) -Static Analysis Security Test (SAST) Pre-Build -Dynamic Analysis Security Test (DAST) Post-Build Continuous Integration (CI) Tool/Server - Defect Management - Security Metric -Artifact Security Scan Artifact -Compliance As a Code (CaC) - Inspec by Chef - Alert & Monitoring Production Vulnerability Management
- 11. DevSecOps Tools of the Trade Developer Source Code Pre-Build Post-Build Continuous Integration (CI) Tool/Server Vulnerability Management Artifact Production **Above just an example, we don’t endorse any tool. Retire.js
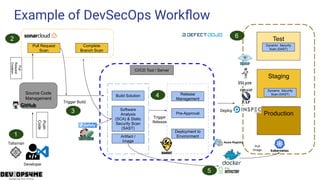
- 12. Example of DevSecOps Workflow Push Code Source Code Management Developer Pull Request Scan Pull Request Creation Complete Branch Scan Trigger Build CI/CD Tool / Server 1 2 3 Build Solution Software Analysis (SCA) & Static Security Scan (SAST) Artifact / Image 4 Test Staging ProductionTrigger Release Release Management Pre-Approval Deployment to Environment 5 6 Dynamic Security Scan (DAST) Dynamic Security Scan (DAST) Pull Image Deploy Talisman
- 13. How To Start DevSecOps? 1. Start Small – Always start with code analysis on a small project to implement DevSecOps and keep it as simple as possible to avoid burnout if you cannot find the right tool for your security test. Make sure to get help if you are in doubt about the process or toolchain. 2. Change Management – Increase pace and performance by encouraging everyone to make changes, and then decide if the change is good or bad. 3. Compliance Monitoring – Be prepared to inspect at any time ( i.e. being in a continuous state of compliance, including obtaining proof of compliance with GDPR, PCI, etc.). 4. Threat Modeling – Identify potential emerging threats with each code update and be able to respond quickly. 5. Vulnerability Assessment – Identify new vulnerabilities with code analysis, then analyze how quickly they are being responded to and patched. 6. Security Training – Train and upskill developers and IT Operations with guidelines for DevSecOps and other security skills.
- 14. Conclusion ● I think that every company/Security Engineers must make an effort to "Shift-Left" to a DevSecOps culture or methodologies and come up with a multidisciplinary security team. ● Approaching "Security As a Code", moving security practices to the left and educating software developers on critical testing and security practices are essential aspects to engage security as part of the DevOps process. ● The key is to be ready to start, to encourage experimentation, to be willing to fail, to learn and to move forward one step at a time.
- 15. Question & Answer “If you don’t ask, you will never get the answer.”