Writing secure code
Download as PPTX, PDF2 likes131 views
Reading Between The Lines- How to learn writing secure code the second time around, when the first time got your name on the security report!
1 of 59
Downloaded 19 times



















![XPATH Injection
Remediation:
● Encode the following control characters:
○ Braces “(“ “ )”
○ Equals “=”
○ Single Quotes “'”
○ Square Brackets “[“ “]”
○ Colon “:”
○ Comma “,”
○ Asterix “*”
○ Forward slash “/”
○ WHITESPACE characters
● Parameterized XPATH Queries](https://image.slidesharecdn.com/writingsecurecode-180928110657/85/Writing-secure-code-21-320.jpg)






































Ad
Recommended
Finding Needles in Haystacks



Finding Needles in Haystackssnyff This document summarizes Louis Nyffenegger's talk on code review and capture-the-flag exercises for finding security vulnerabilities. The talk discusses different approaches to code review like grepping for bugs, following user inputs, reviewing functionality, and reading all code. It also provides tips for getting started with capture-the-flag exercises by focusing on weaknesses rather than vulnerabilities and combining issues. An example application is provided for attendees to practice on, and common weaknesses are listed that could lead to vulnerabilities like hardcoded credentials, cross-site scripting, and remote code execution.
Ruxmon feb 2013 what happened to rails



Ruxmon feb 2013 what happened to railssnyff Louis Nyffenegger gave a talk about the recent vulnerabilities discovered in Ruby on Rails. Several vulnerabilities allowed remote code execution by injecting malicious YAML payloads that were parsed by Rails. These issues arose due to assumptions that Rails was secure, increased scrutiny as its popularity grew, and its flexible parsing of requests. Upgrades and removing unnecessary parsers can help mitigate risks going forward.
Hack proof your ASP NET Applications



Hack proof your ASP NET ApplicationsSarvesh Kushwaha This presentation includes information about different attacks on an asp.net web application and how to secure from those attacks.
Ruxmon cve 2012-2661



Ruxmon cve 2012-2661snyff Louis Nyffenegger discovered a SQL injection vulnerability in ActiveRecord, the ORM used in Ruby on Rails applications. He demonstrated how to exploit it locally by creating two states (true/false) based on the response time of SQL queries with sleep commands. This allowed him to extract data bit-by-bit to retrieve the database version. He then explained how to modify the exploit to send HTTP requests to a remote vulnerable application by properly encoding the injected SQL.
Neoito — Secure coding practices



Neoito — Secure coding practicesNeoito Secure coding is the practice of developing computer software in a way that guards against the accidental introduction of security vulnerabilities. Defects, bugs and logic flaws are consistently the primary cause of commonly exploited software vulnerabilities. Through the analysis of thousands of reported vulnerabilities, security professionals have discovered that most vulnerabilities stem from a relatively small number of common software programming errors. By identifying the insecure coding practices that lead to these errors and educating developers on secure alternatives, organizations can take proactive steps to help significantly reduce or eliminate vulnerabilities in software before deployment.
Session by: Akash S Prakash
OWASP_Top_Ten_Proactive_Controls_v32.pptx



OWASP_Top_Ten_Proactive_Controls_v32.pptxnmk42194 The OWASP Top Ten Proactive Controls 2.0 document introduces new proactive controls to the Top Ten list and provides more practical examples and contributions from the community. It includes some best practices for building secure mobile apps. The document then describes 10 proactive controls addressing common vulnerabilities like injection, XSS, access control issues etc. It provides details on each control with examples and references.
OWASP_Top_Ten_Proactive_Controls_v2.pptx



OWASP_Top_Ten_Proactive_Controls_v2.pptxcgt38842 The OWASP Top Ten Proactive Controls v2 introduces new proactive controls to the Top Ten list, provides more practical examples and case studies, and has contributions from a large number of non-OWASP community members, while also including some best practices for building secure mobile applications. It outlines 10 proactive controls for application security including verifying for security early and often, parameterizing queries, encoding data before use in a parser, validating all inputs, implementing identity and authentication controls, implementing appropriate access controls, protecting data, implementing logging and intrusion detection, leveraging security frameworks and libraries, and handling errors and exceptions.
Leveraging Playwright for API Testing.pdf



Leveraging Playwright for API Testing.pdfSteve Wortham API helps to build the core of any application in the modern software architecture. They facilitate communication between different systems and services over the network. Due to their utmost importance, it becomes very important to ensure that they work as expected and efficiently handle the different scenarios without breaking.
OWASP_Top_Ten_Proactive_Controls_v2.pptx



OWASP_Top_Ten_Proactive_Controls_v2.pptxjohnpragasam1 The OWASP Top Ten Proactive Controls v2 introduces new proactive controls to the Top Ten list. It includes more practical examples and contributions from the OWASP community and non-OWASP community. It also includes some best practices to consider when building mobile apps, such as secure storage, authentication, etc. The document then lists 10 proactive controls, including verifying for security early and often, parameterizing queries, encoding data, validating all inputs, implementing identity and authentication controls, implementing appropriate access controls, protecting data, implementing logging and intrusion detection, leveraging security frameworks and libraries, and handling errors and exceptions.
OWASP_Top_Ten_Proactive_Controls version 2



OWASP_Top_Ten_Proactive_Controls version 2ssuser18349f1 an introduction to OWASP top ten proactive control
OWASP_Top_Ten_Proactive_Controls_v2.pptx



OWASP_Top_Ten_Proactive_Controls_v2.pptxazida3 The document discusses validating all inputs to prevent cross-site scripting (XSS) attacks. It introduces the OWASP HTML Sanitizer Project, which is a Java library that sanitizes HTML to allow untrusted user input to be safely embedded in web pages. The sanitizer removes malicious code while keeping desired markup, through a policy-based approach. Sample usages demonstrated validate specific elements like images and links. The project aims to protect against XSS while allowing third-party content through a tested, securely-designed library.
Secure coding in C#



Secure coding in C#Siddharth Bezalwar - The document discusses common web application vulnerabilities like SQL injection, cross-site scripting, and cross-site request forgery.
- It provides examples of vulnerable code and outlines secure coding practices to prevent these vulnerabilities, such as using parameterized queries to prevent SQL injection, encoding user input to prevent XSS, and using anti-forgery tokens to prevent CSRF.
- Additional topics covered include secure password storage, configuration hardening through web.config settings, and implementation of security controls like encryption and encoding using libraries like ESAPI.
Top Ten Java Defense for Web Applications v2



Top Ten Java Defense for Web Applications v2Jim Manico The presentation describes a series of secure coding techniques to help Java developers build secure web applications.
Higher Level Malware



Higher Level MalwareCTruncer This talk is about developing malware in higher level languages. Languages such as Python or C# can give you the flexibility to quickly develop malware and use it on client engagements.
Dmytro Kochergin - "The OWASP TOP 10 - Typical Attacks on Web Applications an...



Dmytro Kochergin - "The OWASP TOP 10 - Typical Attacks on Web Applications an...LogeekNightUkraine Dmytro Kochergin - "The OWASP TOP 10 - Typical Attacks on Web Applications and How to Protect Against Them"
FIPS 140-2 Validations in a Secure Enclave



FIPS 140-2 Validations in a Secure EnclavewolfSSL Secure enclaves are becoming a popular way to separate and protect sensitive code and data from other processes running on a system. A FIPS 140-2 validated cryptographic software module is currently required to run power-on self tests when loaded, but security of the module can be taken one step further by validating the module inside a secure enclave, such as Intel SGX.
wolfSSL has been working on FIPS 140-2 validating the wolfCrypt library running inside an Intel SGX enclave. This session will discuss the advantages, challenges, and process of FIPS 140-2 validating a cryptographic software module inside Intel SGX and how the same process could be applied to other secure enclave environments.
Web security: Securing Untrusted Web Content in Browsers



Web security: Securing Untrusted Web Content in BrowsersPhú Phùng This document summarizes a seminar on securing untrusted web content at browsers. It discusses how 92% of websites use JavaScript, which can pose security issues if third-party scripts are malicious or compromised. The seminar presents an approach using lightweight self-protecting JavaScript that enforces security policies without browser modifications. This is done by sandboxing untrusted code execution and intercepting API calls according to enforcement rules defined in policy files. Real-world attacks are also examined that were carried out by injecting malicious code into third-party scripts on major websites.
Coding Security: Code Mania 101



Coding Security: Code Mania 101Narudom Roongsiriwong, CISSP The document discusses several coding security practices for developing secure software, including input validation, output handling, parameterizing queries, identity and authentication controls, and access controls. It provides examples and recommendations for implementing each practice to prevent common vulnerabilities like injection and data tampering. The goal is to integrate security at the code level from the beginning to reduce risks.
Joomla Code Quality Control and Automation Testing



Joomla Code Quality Control and Automation TestingShyam Sunder Verma The document discusses code quality control for Joomla projects using automated tools for testing, analysis, and integration. It covers unit testing with PHPUnit, static analysis with PHP Code Sniffer and PHP Mess Detector, code coverage with PHPUnit, profiling with Xdebug, documentation with PHPDocumentor, and continuous integration with Phing and CruiseControl. Automating these processes improves code quality by detecting issues early.
Introduction to K6



Introduction to K6Knoldus Inc. This document provides an overview and demonstration of K6, an open-source load testing tool. It discusses key aspects of K6 including what it is, why it should be used, and how to perform load testing with its various components. The document demonstrates K6's capabilities for load testing APIs, microservices, and websites using JavaScript scripts. It also shows how to integrate K6 with CI/CD pipelines using GitHub Actions.
Understanding and preventing sql injection attacks



Understanding and preventing sql injection attacksKevin Kline SQL Injection attacks are one of the most common hacker tricks used on the web. Learn what a SQL injection attack is and why you should be concerned about them.
This all new session is loaded with demos. You’ll get to witness first-hand several different types of SQL injection attacks, how to find them, and how to block them.
Hp fortify source code analyzer(sca)



Hp fortify source code analyzer(sca)Nagaraju Repala The document provides information on HP Fortify Source Code Analyzer (SCA). It can analyze source code for various languages like Java, .NET, PHP etc. to identify security vulnerabilities. The installation process involves extracting files and providing a license key. System requirements vary based on the size and complexity of the code being analyzed. Reports can be generated in different templates like OWASP Top 10. Filter sets help classify issues by priority. Commands are available to customize and optimize scans.
Progressive Web App Testing With Cypress.io



Progressive Web App Testing With Cypress.ioKnoldus Inc. Cypress.io is a frontend automation testing tool built for modern web applications developed on some of the emerging technologies like Reactjs, Ionic, Vue, and Angular.
Cypress is a test automation tool that can perform fast, easy and reliable testing for anything that runs in a browser.
CS166 Final project



CS166 Final projectKaya Ota This document describes a final project for a computer science course involving various cybersecurity vulnerabilities and techniques for preventing them. It discusses SQL injection and demonstrates how to prevent it using prepared statements. It also covers cross-site scripting (XSS), cross-site request forgery (CSRF), and ways to mitigate these risks, such as input validation and using synchronized tokens. The project code repository and demo sites for vulnerable and secure code are provided.
Security in CI/CD Pipelines: Tips for DevOps Engineers



Security in CI/CD Pipelines: Tips for DevOps EngineersDevOps.com While DevOps is becoming a new norm for most of the companies, security is typically still behind. The new architectures create a number of new process considerations and technical issues. In this practical talk, we will present an overview of the practical issues that go into making security a part of DevOps processes. Will cover incorporating security into existing CI/CD pipelines and tools DevOps professionals need to know to implement the automation and adhere to secure coding practices.
Join Stepan Ilyin, Chief Product Officer at Wallarm for an engaging conversation where you’ll learn:
Methodologies and tooling for dynamic and static security testing
Composite and OSS license analysis benefits
Secrets and analysis and secrets management approaches in distributed applications
Security automation and integration in CI/CD
Apps, APIs and workloads protection in cloud-native K8s enabled environments
Salesforce Developer Online Training.pdf



Salesforce Developer Online Training.pdfSpiritsoftsTraining Enroll for expert level Online Salesforce Developer Training Classes, Learn Salesforce Developer Training by certified experts. Attend the Demo for free & you will find Spiritsofts is the best Online Training Institute within reasonable fee along with course material.
The Training in Salesforce Developer Course is every thing we explained based on real time scenarios,it works which we do in companies.
Experts Training sessions will absolutely help you to get in-depth knowledge on the subject.
Consulthink @ GDG Meets U - L'Aquila2014 - Codelab: Android Security -Il ke...



Consulthink @ GDG Meets U - L'Aquila2014 - Codelab: Android Security -Il ke...Consulthinkspa This document discusses Android key management and cryptography. It covers symmetric and asymmetric encryption algorithms like AES and RSA. It describes using the Android Keystore to securely store cryptographic keys and how PBKDF2 can be used to derive keys from passwords. It also demonstrates how apps can be reversed to extract hardcoded keys and discusses more secure alternatives like storing keys on a server.
Cypress Best Pratices for Test Automation



Cypress Best Pratices for Test AutomationKnoldus Inc. Cypress best practices to write reliable and high-quality test codes while performing Cypress testing.
Salesforce Data Cloud- Hyperscale data platform, built for Salesforce.



Salesforce Data Cloud- Hyperscale data platform, built for Salesforce.Dele Amefo Salesforce Data Cloud- Hyperscale data platform, built for Salesforce.
How can one start with crypto wallet development.pptx



How can one start with crypto wallet development.pptxlaravinson24 This presentation is a beginner-friendly guide to developing a crypto wallet from scratch. It covers essential concepts such as wallet types, blockchain integration, key management, and security best practices. Ideal for developers and tech enthusiasts looking to enter the world of Web3 and decentralized finance.
Ad
More Related Content
Similar to Writing secure code (20)
OWASP_Top_Ten_Proactive_Controls_v2.pptx



OWASP_Top_Ten_Proactive_Controls_v2.pptxjohnpragasam1 The OWASP Top Ten Proactive Controls v2 introduces new proactive controls to the Top Ten list. It includes more practical examples and contributions from the OWASP community and non-OWASP community. It also includes some best practices to consider when building mobile apps, such as secure storage, authentication, etc. The document then lists 10 proactive controls, including verifying for security early and often, parameterizing queries, encoding data, validating all inputs, implementing identity and authentication controls, implementing appropriate access controls, protecting data, implementing logging and intrusion detection, leveraging security frameworks and libraries, and handling errors and exceptions.
OWASP_Top_Ten_Proactive_Controls version 2



OWASP_Top_Ten_Proactive_Controls version 2ssuser18349f1 an introduction to OWASP top ten proactive control
OWASP_Top_Ten_Proactive_Controls_v2.pptx



OWASP_Top_Ten_Proactive_Controls_v2.pptxazida3 The document discusses validating all inputs to prevent cross-site scripting (XSS) attacks. It introduces the OWASP HTML Sanitizer Project, which is a Java library that sanitizes HTML to allow untrusted user input to be safely embedded in web pages. The sanitizer removes malicious code while keeping desired markup, through a policy-based approach. Sample usages demonstrated validate specific elements like images and links. The project aims to protect against XSS while allowing third-party content through a tested, securely-designed library.
Secure coding in C#



Secure coding in C#Siddharth Bezalwar - The document discusses common web application vulnerabilities like SQL injection, cross-site scripting, and cross-site request forgery.
- It provides examples of vulnerable code and outlines secure coding practices to prevent these vulnerabilities, such as using parameterized queries to prevent SQL injection, encoding user input to prevent XSS, and using anti-forgery tokens to prevent CSRF.
- Additional topics covered include secure password storage, configuration hardening through web.config settings, and implementation of security controls like encryption and encoding using libraries like ESAPI.
Top Ten Java Defense for Web Applications v2



Top Ten Java Defense for Web Applications v2Jim Manico The presentation describes a series of secure coding techniques to help Java developers build secure web applications.
Higher Level Malware



Higher Level MalwareCTruncer This talk is about developing malware in higher level languages. Languages such as Python or C# can give you the flexibility to quickly develop malware and use it on client engagements.
Dmytro Kochergin - "The OWASP TOP 10 - Typical Attacks on Web Applications an...



Dmytro Kochergin - "The OWASP TOP 10 - Typical Attacks on Web Applications an...LogeekNightUkraine Dmytro Kochergin - "The OWASP TOP 10 - Typical Attacks on Web Applications and How to Protect Against Them"
FIPS 140-2 Validations in a Secure Enclave



FIPS 140-2 Validations in a Secure EnclavewolfSSL Secure enclaves are becoming a popular way to separate and protect sensitive code and data from other processes running on a system. A FIPS 140-2 validated cryptographic software module is currently required to run power-on self tests when loaded, but security of the module can be taken one step further by validating the module inside a secure enclave, such as Intel SGX.
wolfSSL has been working on FIPS 140-2 validating the wolfCrypt library running inside an Intel SGX enclave. This session will discuss the advantages, challenges, and process of FIPS 140-2 validating a cryptographic software module inside Intel SGX and how the same process could be applied to other secure enclave environments.
Web security: Securing Untrusted Web Content in Browsers



Web security: Securing Untrusted Web Content in BrowsersPhú Phùng This document summarizes a seminar on securing untrusted web content at browsers. It discusses how 92% of websites use JavaScript, which can pose security issues if third-party scripts are malicious or compromised. The seminar presents an approach using lightweight self-protecting JavaScript that enforces security policies without browser modifications. This is done by sandboxing untrusted code execution and intercepting API calls according to enforcement rules defined in policy files. Real-world attacks are also examined that were carried out by injecting malicious code into third-party scripts on major websites.
Coding Security: Code Mania 101



Coding Security: Code Mania 101Narudom Roongsiriwong, CISSP The document discusses several coding security practices for developing secure software, including input validation, output handling, parameterizing queries, identity and authentication controls, and access controls. It provides examples and recommendations for implementing each practice to prevent common vulnerabilities like injection and data tampering. The goal is to integrate security at the code level from the beginning to reduce risks.
Joomla Code Quality Control and Automation Testing



Joomla Code Quality Control and Automation TestingShyam Sunder Verma The document discusses code quality control for Joomla projects using automated tools for testing, analysis, and integration. It covers unit testing with PHPUnit, static analysis with PHP Code Sniffer and PHP Mess Detector, code coverage with PHPUnit, profiling with Xdebug, documentation with PHPDocumentor, and continuous integration with Phing and CruiseControl. Automating these processes improves code quality by detecting issues early.
Introduction to K6



Introduction to K6Knoldus Inc. This document provides an overview and demonstration of K6, an open-source load testing tool. It discusses key aspects of K6 including what it is, why it should be used, and how to perform load testing with its various components. The document demonstrates K6's capabilities for load testing APIs, microservices, and websites using JavaScript scripts. It also shows how to integrate K6 with CI/CD pipelines using GitHub Actions.
Understanding and preventing sql injection attacks



Understanding and preventing sql injection attacksKevin Kline SQL Injection attacks are one of the most common hacker tricks used on the web. Learn what a SQL injection attack is and why you should be concerned about them.
This all new session is loaded with demos. You’ll get to witness first-hand several different types of SQL injection attacks, how to find them, and how to block them.
Hp fortify source code analyzer(sca)



Hp fortify source code analyzer(sca)Nagaraju Repala The document provides information on HP Fortify Source Code Analyzer (SCA). It can analyze source code for various languages like Java, .NET, PHP etc. to identify security vulnerabilities. The installation process involves extracting files and providing a license key. System requirements vary based on the size and complexity of the code being analyzed. Reports can be generated in different templates like OWASP Top 10. Filter sets help classify issues by priority. Commands are available to customize and optimize scans.
Progressive Web App Testing With Cypress.io



Progressive Web App Testing With Cypress.ioKnoldus Inc. Cypress.io is a frontend automation testing tool built for modern web applications developed on some of the emerging technologies like Reactjs, Ionic, Vue, and Angular.
Cypress is a test automation tool that can perform fast, easy and reliable testing for anything that runs in a browser.
CS166 Final project



CS166 Final projectKaya Ota This document describes a final project for a computer science course involving various cybersecurity vulnerabilities and techniques for preventing them. It discusses SQL injection and demonstrates how to prevent it using prepared statements. It also covers cross-site scripting (XSS), cross-site request forgery (CSRF), and ways to mitigate these risks, such as input validation and using synchronized tokens. The project code repository and demo sites for vulnerable and secure code are provided.
Security in CI/CD Pipelines: Tips for DevOps Engineers



Security in CI/CD Pipelines: Tips for DevOps EngineersDevOps.com While DevOps is becoming a new norm for most of the companies, security is typically still behind. The new architectures create a number of new process considerations and technical issues. In this practical talk, we will present an overview of the practical issues that go into making security a part of DevOps processes. Will cover incorporating security into existing CI/CD pipelines and tools DevOps professionals need to know to implement the automation and adhere to secure coding practices.
Join Stepan Ilyin, Chief Product Officer at Wallarm for an engaging conversation where you’ll learn:
Methodologies and tooling for dynamic and static security testing
Composite and OSS license analysis benefits
Secrets and analysis and secrets management approaches in distributed applications
Security automation and integration in CI/CD
Apps, APIs and workloads protection in cloud-native K8s enabled environments
Salesforce Developer Online Training.pdf



Salesforce Developer Online Training.pdfSpiritsoftsTraining Enroll for expert level Online Salesforce Developer Training Classes, Learn Salesforce Developer Training by certified experts. Attend the Demo for free & you will find Spiritsofts is the best Online Training Institute within reasonable fee along with course material.
The Training in Salesforce Developer Course is every thing we explained based on real time scenarios,it works which we do in companies.
Experts Training sessions will absolutely help you to get in-depth knowledge on the subject.
Consulthink @ GDG Meets U - L'Aquila2014 - Codelab: Android Security -Il ke...



Consulthink @ GDG Meets U - L'Aquila2014 - Codelab: Android Security -Il ke...Consulthinkspa This document discusses Android key management and cryptography. It covers symmetric and asymmetric encryption algorithms like AES and RSA. It describes using the Android Keystore to securely store cryptographic keys and how PBKDF2 can be used to derive keys from passwords. It also demonstrates how apps can be reversed to extract hardcoded keys and discusses more secure alternatives like storing keys on a server.
Cypress Best Pratices for Test Automation



Cypress Best Pratices for Test AutomationKnoldus Inc. Cypress best practices to write reliable and high-quality test codes while performing Cypress testing.
Recently uploaded (20)
Salesforce Data Cloud- Hyperscale data platform, built for Salesforce.



Salesforce Data Cloud- Hyperscale data platform, built for Salesforce.Dele Amefo Salesforce Data Cloud- Hyperscale data platform, built for Salesforce.
How can one start with crypto wallet development.pptx



How can one start with crypto wallet development.pptxlaravinson24 This presentation is a beginner-friendly guide to developing a crypto wallet from scratch. It covers essential concepts such as wallet types, blockchain integration, key management, and security best practices. Ideal for developers and tech enthusiasts looking to enter the world of Web3 and decentralized finance.
Microsoft AI Nonprofit Use Cases and Live Demo_2025.04.30.pdf



Microsoft AI Nonprofit Use Cases and Live Demo_2025.04.30.pdfTechSoup In this webinar we will dive into the essentials of generative AI, address key AI concerns, and demonstrate how nonprofits can benefit from using Microsoft’s AI assistant, Copilot, to achieve their goals.
This event series to help nonprofits obtain Copilot skills is made possible by generous support from Microsoft.
What You’ll Learn in Part 2:
Explore real-world nonprofit use cases and success stories.
Participate in live demonstrations and a hands-on activity to see how you can use Microsoft 365 Copilot in your own work!
PDF Reader Pro Crack Latest Version FREE Download 2025



PDF Reader Pro Crack Latest Version FREE Download 2025mu394968 🌍📱👉COPY LINK & PASTE ON GOOGLE https://dr-kain-geera.info/👈🌍
PDF Reader Pro is a software application, often referred to as an AI-powered PDF editor and converter, designed for viewing, editing, annotating, and managing PDF files. It supports various PDF functionalities like merging, splitting, converting, and protecting PDFs. Additionally, it can handle tasks such as creating fillable forms, adding digital signatures, and performing optical character recognition (OCR).
Solidworks Crack 2025 latest new + license code



Solidworks Crack 2025 latest new + license codeaneelaramzan63 Copy & Paste On Google >>> https://dr-up-community.info/
The two main methods for installing standalone licenses of SOLIDWORKS are clean installation and parallel installation (the process is different ...
Disable your internet connection to prevent the software from performing online checks during installation
Expand your AI adoption with AgentExchange



Expand your AI adoption with AgentExchangeFexle Services Pvt. Ltd. AgentExchange is Salesforce’s latest innovation, expanding upon the foundation of AppExchange by offering a centralized marketplace for AI-powered digital labor. Designed for Agentblazers, developers, and Salesforce admins, this platform enables the rapid development and deployment of AI agents across industries.
Email: [email protected]
Phone: +1(630) 349 2411
Website: https://www.fexle.com/blogs/agentexchange-an-ultimate-guide-for-salesforce-consultants-businesses/?utm_source=slideshare&utm_medium=pptNg
What Do Contribution Guidelines Say About Software Testing? (MSR 2025)



What Do Contribution Guidelines Say About Software Testing? (MSR 2025)Andre Hora Software testing plays a crucial role in the contribution process of open-source projects. For example, contributions introducing new features are expected to include tests, and contributions with tests are more likely to be accepted. Although most real-world projects require contributors to write tests, the specific testing practices communicated to contributors remain unclear. In this paper, we present an empirical study to understand better how software testing is approached in contribution guidelines. We analyze the guidelines of 200 Python and JavaScript open-source software projects. We find that 78% of the projects include some form of test documentation for contributors. Test documentation is located in multiple sources, including CONTRIBUTING files (58%), external documentation (24%), and README files (8%). Furthermore, test documentation commonly explains how to run tests (83.5%), but less often provides guidance on how to write tests (37%). It frequently covers unit tests (71%), but rarely addresses integration (20.5%) and end-to-end tests (15.5%). Other key testing aspects are also less frequently discussed: test coverage (25.5%) and mocking (9.5%). We conclude by discussing implications and future research.
TestMigrationsInPy: A Dataset of Test Migrations from Unittest to Pytest (MSR...



TestMigrationsInPy: A Dataset of Test Migrations from Unittest to Pytest (MSR...Andre Hora Unittest and pytest are the most popular testing frameworks in Python. Overall, pytest provides some advantages, including simpler assertion, reuse of fixtures, and interoperability. Due to such benefits, multiple projects in the Python ecosystem have migrated from unittest to pytest. To facilitate the migration, pytest can also run unittest tests, thus, the migration can happen gradually over time. However, the migration can be timeconsuming and take a long time to conclude. In this context, projects would benefit from automated solutions to support the migration process. In this paper, we propose TestMigrationsInPy, a dataset of test migrations from unittest to pytest. TestMigrationsInPy contains 923 real-world migrations performed by developers. Future research proposing novel solutions to migrate frameworks in Python can rely on TestMigrationsInPy as a ground truth. Moreover, as TestMigrationsInPy includes information about the migration type (e.g., changes in assertions or fixtures), our dataset enables novel solutions to be verified effectively, for instance, from simpler assertion migrations to more complex fixture migrations. TestMigrationsInPy is publicly available at: https://github.com/altinoalvesjunior/TestMigrationsInPy.
Secure Test Infrastructure: The Backbone of Trustworthy Software Development



Secure Test Infrastructure: The Backbone of Trustworthy Software DevelopmentShubham Joshi A secure test infrastructure ensures that the testing process doesn’t become a gateway for vulnerabilities. By protecting test environments, data, and access points, organizations can confidently develop and deploy software without compromising user privacy or system integrity.
Avast Premium Security Crack FREE Latest Version 2025



Avast Premium Security Crack FREE Latest Version 2025mu394968 🌍📱👉COPY LINK & PASTE ON GOOGLE https://dr-kain-geera.info/👈🌍
Avast Premium Security is a paid subscription service that provides comprehensive online security and privacy protection for multiple devices. It includes features like antivirus, firewall, ransomware protection, and website scanning, all designed to safeguard against a wide range of online threats, according to Avast.
Key features of Avast Premium Security:
Antivirus: Protects against viruses, malware, and other malicious software, according to Avast.
Firewall: Controls network traffic and blocks unauthorized access to your devices, as noted by All About Cookies.
Ransomware protection: Helps prevent ransomware attacks, which can encrypt your files and hold them hostage.
Website scanning: Checks websites for malicious content before you visit them, according to Avast.
Email Guardian: Scans your emails for suspicious attachments and phishing attempts.
Multi-device protection: Covers up to 10 devices, including Windows, Mac, Android, and iOS, as stated by 2GO Software.
Privacy features: Helps protect your personal data and online privacy.
In essence, Avast Premium Security provides a robust suite of tools to keep your devices and online activity safe and secure, according to Avast.
Download YouTube By Click 2025 Free Full Activated



Download YouTube By Click 2025 Free Full Activatedsaniamalik72555 Copy & Past Link 👉👉
https://dr-up-community.info/
"YouTube by Click" likely refers to the ByClick Downloader software, a video downloading and conversion tool, specifically designed to download content from YouTube and other video platforms. It allows users to download YouTube videos for offline viewing and to convert them to different formats.
Pixologic ZBrush Crack Plus Activation Key [Latest 2025] New Version![Pixologic ZBrush Crack Plus Activation Key [Latest 2025] New Version](https://cdn.slidesharecdn.com/ss_thumbnails/fashionevolution2-250322112409-f76abaa7-250428124909-b51264ff-250504160528-fc2bb1c5-thumbnail.jpg?width=560&fit=bounds)
![Pixologic ZBrush Crack Plus Activation Key [Latest 2025] New Version](https://cdn.slidesharecdn.com/ss_thumbnails/fashionevolution2-250322112409-f76abaa7-250428124909-b51264ff-250504160528-fc2bb1c5-thumbnail.jpg?width=560&fit=bounds)
![Pixologic ZBrush Crack Plus Activation Key [Latest 2025] New Version](https://cdn.slidesharecdn.com/ss_thumbnails/fashionevolution2-250322112409-f76abaa7-250428124909-b51264ff-250504160528-fc2bb1c5-thumbnail.jpg?width=560&fit=bounds)
![Pixologic ZBrush Crack Plus Activation Key [Latest 2025] New Version](https://cdn.slidesharecdn.com/ss_thumbnails/fashionevolution2-250322112409-f76abaa7-250428124909-b51264ff-250504160528-fc2bb1c5-thumbnail.jpg?width=560&fit=bounds)
Pixologic ZBrush Crack Plus Activation Key [Latest 2025] New Versionsaimabibi60507 Copy & Past Link👉👉
https://dr-up-community.info/
Pixologic ZBrush, now developed by Maxon, is a premier digital sculpting and painting software renowned for its ability to create highly detailed 3D models. Utilizing a unique "pixol" technology, ZBrush stores depth, lighting, and material information for each point on the screen, allowing artists to sculpt and paint with remarkable precision .
The Significance of Hardware in Information Systems.pdf



The Significance of Hardware in Information Systems.pdfdrewplanas10 The Significance of Hardware in Information Systems: The Types Of Hardware and What They Do
Exceptional Behaviors: How Frequently Are They Tested? (AST 2025)



Exceptional Behaviors: How Frequently Are They Tested? (AST 2025)Andre Hora Exceptions allow developers to handle error cases expected to occur infrequently. Ideally, good test suites should test both normal and exceptional behaviors to catch more bugs and avoid regressions. While current research analyzes exceptions that propagate to tests, it does not explore other exceptions that do not reach the tests. In this paper, we provide an empirical study to explore how frequently exceptional behaviors are tested in real-world systems. We consider both exceptions that propagate to tests and the ones that do not reach the tests. For this purpose, we run an instrumented version of test suites, monitor their execution, and collect information about the exceptions raised at runtime. We analyze the test suites of 25 Python systems, covering 5,372 executed methods, 17.9M calls, and 1.4M raised exceptions. We find that 21.4% of the executed methods do raise exceptions at runtime. In methods that raise exceptions, on the median, 1 in 10 calls exercise exceptional behaviors. Close to 80% of the methods that raise exceptions do so infrequently, but about 20% raise exceptions more frequently. Finally, we provide implications for researchers and practitioners. We suggest developing novel tools to support exercising exceptional behaviors and refactoring expensive try/except blocks. We also call attention to the fact that exception-raising behaviors are not necessarily “abnormal” or rare.
Download Wondershare Filmora Crack [2025] With Latest![Download Wondershare Filmora Crack [2025] With Latest](https://cdn.slidesharecdn.com/ss_thumbnails/neo4j-howkgsareshapingthefutureofgenerativeaiatawssummitlondonapril2024-240426125209-2d9db05d-250419-250428115407-a04afffa-thumbnail.jpg?width=560&fit=bounds)
![Download Wondershare Filmora Crack [2025] With Latest](https://cdn.slidesharecdn.com/ss_thumbnails/neo4j-howkgsareshapingthefutureofgenerativeaiatawssummitlondonapril2024-240426125209-2d9db05d-250419-250428115407-a04afffa-thumbnail.jpg?width=560&fit=bounds)
![Download Wondershare Filmora Crack [2025] With Latest](https://cdn.slidesharecdn.com/ss_thumbnails/neo4j-howkgsareshapingthefutureofgenerativeaiatawssummitlondonapril2024-240426125209-2d9db05d-250419-250428115407-a04afffa-thumbnail.jpg?width=560&fit=bounds)
![Download Wondershare Filmora Crack [2025] With Latest](https://cdn.slidesharecdn.com/ss_thumbnails/neo4j-howkgsareshapingthefutureofgenerativeaiatawssummitlondonapril2024-240426125209-2d9db05d-250419-250428115407-a04afffa-thumbnail.jpg?width=560&fit=bounds)
Download Wondershare Filmora Crack [2025] With Latesttahirabibi60507 Copy & Past Link 👉👉
http://drfiles.net/
Wondershare Filmora is a video editing software and app designed for both beginners and experienced users. It's known for its user-friendly interface, drag-and-drop functionality, and a wide range of tools and features for creating and editing videos. Filmora is available on Windows, macOS, iOS (iPhone/iPad), and Android platforms.
Douwan Crack 2025 new verson+ License code



Douwan Crack 2025 new verson+ License codeaneelaramzan63 Copy & Paste On Google >>> https://dr-up-community.info/
Douwan Preactivated Crack Douwan Crack Free Download. Douwan is a comprehensive software solution designed for data management and analysis.
WinRAR Crack for Windows (100% Working 2025)



WinRAR Crack for Windows (100% Working 2025)sh607827 copy and past on google ➤ ➤➤ https://hdlicense.org/ddl/
WinRAR Crack Free Download is a powerful archive manager that provides full support for RAR and ZIP archives and decompresses CAB, ARJ, LZH, TAR, GZ, ACE, UUE, .
Landscape of Requirements Engineering for/by AI through Literature Review



Landscape of Requirements Engineering for/by AI through Literature ReviewHironori Washizaki Hironori Washizaki, "Landscape of Requirements Engineering for/by AI through Literature Review," RAISE 2025: Workshop on Requirements engineering for AI-powered SoftwarE, 2025.
Mastering Fluent Bit: Ultimate Guide to Integrating Telemetry Pipelines with ...



Mastering Fluent Bit: Ultimate Guide to Integrating Telemetry Pipelines with ...Eric D. Schabell It's time you stopped letting your telemetry data pressure your budgets and get in the way of solving issues with agility! No more I say! Take back control of your telemetry data as we guide you through the open source project Fluent Bit. Learn how to manage your telemetry data from source to destination using the pipeline phases covering collection, parsing, aggregation, transformation, and forwarding from any source to any destination. Buckle up for a fun ride as you learn by exploring how telemetry pipelines work, how to set up your first pipeline, and exploring several common use cases that Fluent Bit helps solve. All this backed by a self-paced, hands-on workshop that attendees can pursue at home after this session (https://o11y-workshops.gitlab.io/workshop-fluentbit).
Ad
Writing secure code
- 1. Writing Secure Code How to learn writing secure code the second time around, when the first time got your name on the security report! Madhura P M Senior Security Analyst
- 2. Agenda ● Vulnerabilities ○ SQL Injection ○ XML Injection and XXE Attack ○ XPATH Injection ○ Formula Injection ○ Command Injection ○ Cross-Site Scripting ○ Session Fixation ○ Unrestricted File Upload ● Languages Covered: ○ Java ○ ASP.NET ○ PHP ○ Cold Fusion
- 3. Overview ● Code Review- First step of a Security Audit ● Emphasis on- Implementing Security in Dev Phase of SDLC ● Approx 75% remediations happen at code level ● Manual review over using SAST tools
- 4. Secure Code Review ● Knowing the language and framework used ● Familiarity with available security features of the framework ● Knowing which secure public APIs and libraries to use ● Identifying the entry and exit points in the application
- 6. SQL Injection Cause: Ability of an attacker to change context in an SQL Query causing data to be interpreted as part of the query. Remediation: ● Parameterized queries ● Use whitelisting where parameterization is not possible
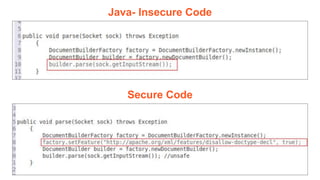
- 7. JAVA- Insecure Code Secure Code
- 8. ASP.NET- Insecure Code Secure Code
- 9. PHP- Insecure Code Secure Code
- 10. PHP- Using PDOs
- 11. COLDFUSION- Unsafe Code Safe Code
- 13. XML Injection and XXE Attack Remediation: ● Encode the following XML-specific control characters: ○ Ampersand (&) ○ Open Angle Bracket (<) ○ Close Angle Bracket (>) ○ Single-quote (') ○ Double-quote (") ○ Whitespace characters ● Disable DTD or Doctype Entities to prevent XXE. Billion laughs
- 14. Java- Insecure Code Secure Code
- 15. Java- Disabling General and Parameter entities Using XML Reader
- 16. ASP.NET- Secure Code- Using XMLDoc Secure Code- Using XMLReader
- 17. PHP- Secure Code Secure Code
- 18. JAVA- XML Injection Remediation
- 19. COLDFUSION- XML Injection Remediation
- 20. XPATH Injection
- 21. XPATH Injection Remediation: ● Encode the following control characters: ○ Braces “(“ “ )” ○ Equals “=” ○ Single Quotes “'” ○ Square Brackets “[“ “]” ○ Colon “:” ○ Comma “,” ○ Asterix “*” ○ Forward slash “/” ○ WHITESPACE characters ● Parameterized XPATH Queries
- 23. JAVA- Using Parameterized Queries
- 24. ASP.NET Using Parameterized Queries
- 26. COLDFUSION- Using Encoding COLDFUSION- Using Parameterized Queries
- 28. Formula Injection Remediation: ● Escape all untrusted input before inserting it into spreadsheet data fields. ● In Microsoft Excel, this is accomplished by placing a single- quote (‘) before the content. ● Ensure that no cells begin with any of the following characters. ○ Equals to ("=") ○ Plus ("+") ○ Minus ("-") ○ At ("@")
- 29. JAVA- Implementing Regex Checks
- 30. ASP.NET- Implementing Regex Checks
- 31. PHP- Using with Writer objects Using with Stream objects
- 33. Command Injection Remediation: ● Avoid inserting user-supplied data into commands executed by the operating system. ● Perform strict input validation via whitelist. ● In Unix, characters with special meaning on the command line include SPACE, TAB, NEWLINE, ;, (, ), <, >, |, and &. ● Java and .NET provide a very comprehensive set of standard libraries. It is always safer to use these libraries instead of making system calls.
- 34. JAVA- Using Regex for whitelisting
- 35. ASP.NET- Whitelisting Characters COLDFUSION- Whitelisting Characters
- 36. PHP- Using Sanitization Methods PHP- Whitelisting Characters
- 38. Cross-Site Scripting (XSS) Remediation: ● Values that are obtained from Requests/APIs/Databases etc should be validated using regex. ● Escaping malicious characters from user input. ● Output Encoding before displaying on webpages. ● HTTP Headers for added security: ○ X-XSS Protection ○ Content Security Policy
- 39. JAVA- Using OWASP ESAPI class
- 40. JAVA- Using Java Encoder Library
- 41. ASP.NET- Using AntiXSS Library
- 42. PHP- Using Contextual Encoding
- 43. COLDFUSION- Application.cfc Using Antisamy methods
- 44. Session Fixation
- 45. Remediation: ● Session identifiers must be regenerated and re-issued after every login. ● Validate Session IDs for every incoming request. ● Ensure that each Session ID generated is unique. ● Use Secure Random Number Generators to generate 128/256 bits long Session IDs. ● Invalidate the session after a user logs out. ● The Session Cookie should be set with “Secure” and “HttpOnly” attributes. Session Fixation
- 46. JAVA- Invalidate Session JAVA SPRING- Invalidate Session
- 51. Unrestricted File Upload Remediation: ● Validation should be done on file’s name and extension. ● Magic Number of the file (first few bytes of the file which specifies the file type) should be validated. ● An Upper limit on file size should be enforced. ● Frequency of file uploads should be validated. ● Uploaded file should be scanned for malwares/viruses before saving files on the production server.
- 52. JAVA- Insecure File Upload
- 53. JAVA- Check File Metadata
- 54. ASP.NET- Upload Valid PDF
- 55. PHP- Upload Valid Image
- 56. COLDFUSION- Upload Valid Image
- 58. Q & A
- 59. Come Join Us At ● AppSecUSA, San Jose - Oct 9 & 10 ● AppSec Australia, Melbourne - Oct 15 & 16 ● Djangocon, San Diego - Oct 17 ● SANS, Denver - Oct 22 ● LASCON, Austin - Oct 25 & 26 ● Code Blue, Tokyo - Oct 29 & 30 For more visit www.we45.com and subscribe to our newsletter.

