Xml For Dummies Chapter 6 Adding Character(S) To Xml
Download as PPTX, PDF0 likes713 views
This document provides an overview of character encodings and how they are handled in XML. It discusses the limitations of 7-bit and 8-bit character encodings and how Unicode addresses these by supporting a much wider range of characters with 16-bit encoding. It also describes how characters maps to numeric codes in Unicode/ISO 10646 and how UTF encodings implement Unicode. Additional topics covered include common character sets, using Unicode characters, and resources for finding character entity information.
1 of 12
Download to read offline











Ad
Recommended
Unicode Fundamentals 



Unicode Fundamentals SamiHsDU You will get all the basic informations about Unicode from this one slide InShaAllah (if Allah, the lord of the worlds wishes).
UTF-8: The Secret of Character Encoding



UTF-8: The Secret of Character EncodingBert Pattyn The document discusses character encoding standards like ASCII, UTF-8, and UTF-16. It explains that UTF-8 uses 1-4 bytes per character and has become the standard for XML and web content. The document raises questions about choosing the right encoding based on the characters, software, and browsers used.
Unicode



UnicodeDevin Humbert Character encodings map characters to binary representations using code points. Unicode is a widely adopted standard that assigns unique code points to characters. It is divided into planes with 65,536 code points each. UTF-8 is a common encoding format that uses variable-length octets to represent code points efficiently. While Unicode supports many languages, some criticize its complexity and that it does not include all possible scripts.
Unicode



Unicodemissstevenson01 Unicode is an alternative character encoding standard to ASCII that can represent many more characters and languages. It was originally a 16-bit encoding that could represent around 7,000 characters, but now uses 8, 16, or 32 bits per character, allowing it to encode over 137,000 characters in the current version. While Unicode supports more languages by encoding more symbols, it also uses more computer memory than ASCII to store each character.
Unicode



UnicodeSidhartha Sahoo The document discusses the Unicode character encoding standard. It describes how earlier 8-bit character encoding systems were limited and could not represent all languages, which led to many conflicting encoding systems. Unicode addressed this by providing a universal encoded character set that could represent every character for all present and historic written languages, with each character assigned a unique numeric value. The Unicode standard aims to facilitate international exchange of text and language-independent software.
Unicode Encoding Forms



Unicode Encoding FormsMehdi Hasan Unicode provides a standard way to encode characters from all languages. This introduced the problem of how to represent these characters in memory and storage. Several encoding forms were developed, including UTF-8, UTF-16, and UTF-32, each with their own advantages and disadvantages. UTF-8 became popular as it is backwards compatible with ASCII and uses variable length encoding for efficient storage. Notepad and browsers can determine the encoding of a file or page through a Byte Order Mark or HTTP header respectively. In practice, UTF-8 is commonly recommended due to its efficiency and compatibility.
The Good, the Bad, and the Ugly: What Happened to Unicode and PHP 6



The Good, the Bad, and the Ugly: What Happened to Unicode and PHP 6Andrei Zmievski n the halcyon days of early 2005, a project was launched to bring long overdue native Unicode and internationalization support to PHP. It was deemed so far reaching and important that PHP needed to have a version bump. After more than 4 years of development, the project (and PHP 6 for now) was shelved. This talk will introduce Unicode and i18n concepts, explain why Web needs Unicode, why PHP needs Unicode, how we tried to solve it (with examples), and what eventually happened. No sordid details will be left uncovered.
Internationalisation And Globalisation



Internationalisation And GlobalisationAlan Dean This is a very old presentation but if you gloss over the usage of VB6 there is plenty of value. I presented this to the VBUG Annual Conference in 2003.
Io



IoMinal Maniar This document discusses I/O streams in Java, which allow reading and writing of data from sources and to destinations. It describes input and output streams, character and byte streams, and the Unicode standard for representing written languages internationally. Unicode was developed to solve the problems with different encodings for languages in various standards, and assigns a unique code value to each character. The document also mentions the File class, which contains methods for obtaining file properties and renaming/deleting files, and BufferedReader and BufferedWriter which improve I/O performance.
Using unicode with php



Using unicode with phpElizabeth Smith 1. Unicode is an international standard for representing characters across different languages. It allows websites and software to support multiple languages.
2. When working with Unicode in PHP, it is important to use UTF-8 encoding, and extensions like intl provide helpful internationalization functions.
3. Common issues include character encoding problems between databases, files and PHP strings, so ensuring consistent encoding is crucial.
Your Guide to be a Software Engineer



Your Guide to be a Software EngineerAhmed Mater This document provides guidance on how to become a good software engineer. It discusses what programming is, different types of computer languages, popular programming majors, and how to learn software programming. The document recommends starting with online courses to learn programming basics and the integrated development environment. It also advises supplementing courses with books for a more comprehensive understanding and to develop an open mind. Community websites are recommended for discussions and problem solving help. The overall guidance is that both courses and books are important for learning, but courses are best to start as a beginner.
Strings and encodings



Strings and encodingsbradleygrainger Unicode was designed to solve the problems of encoding multilingual documents by assigning each character a unique integer code. However, simply encoding text does not specify how to interpret byte sequences, so metadata is needed to indicate the encoding. There are several common ways encoding can be specified, such as in file formats, HTTP headers, or by detecting patterns in the byte data. Failure to correctly determine the encoding can result in corrupted text being displayed.
Adam Goucher I18n And L10n



Adam Goucher I18n And L10nAdam Goucher I18N refers to internationalization and L10N refers to localization. The document provides an overview of these concepts and gives recommendations for implementing them technically. It defines internationalization as enabling an application to support different languages and localization as customizing an application for a specific locale. It recommends using Unicode and UTF-8 encoding, resource bundles to externalize strings, and testing translations early and continuously to implement internationalization and localization correctly.
PDT DC015 Chapter 2 Computer System 2017/2018 (e)



PDT DC015 Chapter 2 Computer System 2017/2018 (e)Fizaril Amzari Omar The document discusses different coding schemes used in data processing, including ASCII, EBCDIC, and Unicode. ASCII uses 8 bits to represent characters and can represent 256 characters, while EBCDIC is traditionally used on mainframe computers. Unicode uses 16 or 32 bits and can represent over 65,000 characters to support different languages.
Notes on a Standard: Unicode



Notes on a Standard: UnicodeElena-Oana Tabaranu This document provides an overview of the Unicode standard for character encoding. It discusses the design goals of being universal, consistent, and able to encode all written languages. Unicode represents characters as abstract code points from 0 to 10FFFF in hexadecimal and defines UTF-8, UTF-16, and UTF-32 encoding forms to represent these code points with 8, 16, or 32-bit units. The encoding forms allow lossless transformation between representations. UTF-8 is commonly used in XML documents while UTF-16 and UTF-32 are used by different operating systems.
Unicode 101



Unicode 101davidfstr This document provides an overview of Unicode and character encodings to avoid corrupting international text. It discusses:
- The difference between bytes and characters, noting that characters are often multiple bytes wide and an encoding is needed to interpret byte sequences as character sequences.
- Common mistakes like assuming a default encoding, mixing bytes and characters, and not specifying an encoding which can lead to text being corrupted when read by systems using different encodings.
- Encoding issues that can occur in different languages and file types like text files, HTML, XML, if an encoding is not properly declared or honored.
The key lessons are: you must know the character encoding to interpret byte sequences correctly, and bytes and characters should not be
Character Encoding issue with PHP



Character Encoding issue with PHPRavi Raj This document discusses character encoding issues with PHP and Unicode. It provides an overview of character sets and encodings like UTF-8. When working with Unicode, any part of the technology stack could fail, from editors to version control to databases. UTF-8 is recommended as it is backwards compatible with ASCII and supports Unicode. The document offers tips for getting PHP and CodeIgniter to properly support UTF-8, such as changing config settings and database collations. Fully supporting Unicode across technologies can be challenging but is important.
Understand unicode & utf8 in perl (2)



Understand unicode & utf8 in perl (2)Jerome Eteve I'm not a Unicode Guru, but working with third parties, I often find that a lot of people consistently fail to get the basics right about Unicode and encoding. There must be something esoteric about it. So here's yet another set of slides about Unicode/UTF8 in Perl.
It's not meant to be a comprehensive presentation of all Unicode things in Perl. It's meant to insist on a couple of guidelines and give some pointers to get a good start writing a unicode compliant application and avoiding common issues.
Uncdtalk



UncdtalkBilal Maqbool ツ Unicode is a standard for representing characters across different platforms and languages. It defines coding schemes like UTF-8, UTF-16, and UTF-32 to represent characters as binary values. UTF-16 uses 16-bit values for most characters but introduces surrogate pairs to represent some characters requiring two 16-bit values. UTF-32 uses 32-bit values for all characters. UTF-8 varies the number of bytes per character from 1 to 4 to optimize for English. Unicode aims to support all languages with a single encoding scheme.
SignWriting in Unicode Next



SignWriting in Unicode NextStephen Slevinski Updated for UTC #156, this presentation discusses the Center for Sutton Movement Writing's proposal for the full script support of Sutton SignWriting in Unicode.
Python



PythonDr. SURBHI SAROHA This document provides an overview of the Python programming language. It describes what Python is, how it can be used for web development, software development, mathematics, and system scripting. It also covers Python's syntax features like indentation, variables, comments, and data types. Key reasons for using Python include its ability to run on different platforms, simple English-like syntax, and support for procedural, object-oriented, and functional programming.
Introduction to W3C I18N Best Practices



Introduction to W3C I18N Best PracticesGopal Venkatesan This document provides an introduction to internationalization best practices. It discusses internationalization vocabulary, common problems encountered like encoding issues, and internationalization support in Java and PHP. Key topics covered include Unicode, locales, formatting numbers and dates, and using resource bundles to externalize strings.
Unicode and kurdish fonts



Unicode and kurdish fontsc_s_halabja what is char glyphs and font?
what is standard Unicode?
arabic and Kurdish Unicode.
how to change Arabic font to Kurdish Unicode.
M.FLORENCE DAYANA WEB DESIGN -Unit 5 XML



M.FLORENCE DAYANA WEB DESIGN -Unit 5 XMLDr.Florence Dayana XML Introduction,Syntax of XML,Well formed XML Documents,XML Document Structure,Document Type Definitions,XML Namespace,XML Schemas,DOM(Document Object Model)
X Laran Ax



X Laran AxESPEJO 25 Un hombre se toma el día libre para jugar al golf. Durante el juego, una rana le aconseja sobre qué palos usar, lo que le permite jugar muy bien. La rana luego le dice que vayan a Las Vegas, donde el hombre gana mucho dinero apostando. Más tarde, la rana le dice que se postule como presidente, y sorprendentemente gana. Años después en el cargo, el hombre quiere recompensar a la rana, y ésta le pide un beso, transformándose luego en una hermosa doncella.
Xing Sardegna newsletter gennaio 2010



Xing Sardegna newsletter gennaio 2010Andrea ADSLLOSO Portoghese The newsletter provides an update on the XING Ambassador Program and upcoming events. It discusses the success of events held by Ambassadors around the world in 2009 and introduces new features like paid ticketing to help organize events. It highlights some of the top-attended events in various cities and names the Ambassador of the Month for their contributions. Finally, it previews several official XING events scheduled in January 2010 across different regions.
Ad
More Related Content
What's hot (16)
Io



IoMinal Maniar This document discusses I/O streams in Java, which allow reading and writing of data from sources and to destinations. It describes input and output streams, character and byte streams, and the Unicode standard for representing written languages internationally. Unicode was developed to solve the problems with different encodings for languages in various standards, and assigns a unique code value to each character. The document also mentions the File class, which contains methods for obtaining file properties and renaming/deleting files, and BufferedReader and BufferedWriter which improve I/O performance.
Using unicode with php



Using unicode with phpElizabeth Smith 1. Unicode is an international standard for representing characters across different languages. It allows websites and software to support multiple languages.
2. When working with Unicode in PHP, it is important to use UTF-8 encoding, and extensions like intl provide helpful internationalization functions.
3. Common issues include character encoding problems between databases, files and PHP strings, so ensuring consistent encoding is crucial.
Your Guide to be a Software Engineer



Your Guide to be a Software EngineerAhmed Mater This document provides guidance on how to become a good software engineer. It discusses what programming is, different types of computer languages, popular programming majors, and how to learn software programming. The document recommends starting with online courses to learn programming basics and the integrated development environment. It also advises supplementing courses with books for a more comprehensive understanding and to develop an open mind. Community websites are recommended for discussions and problem solving help. The overall guidance is that both courses and books are important for learning, but courses are best to start as a beginner.
Strings and encodings



Strings and encodingsbradleygrainger Unicode was designed to solve the problems of encoding multilingual documents by assigning each character a unique integer code. However, simply encoding text does not specify how to interpret byte sequences, so metadata is needed to indicate the encoding. There are several common ways encoding can be specified, such as in file formats, HTTP headers, or by detecting patterns in the byte data. Failure to correctly determine the encoding can result in corrupted text being displayed.
Adam Goucher I18n And L10n



Adam Goucher I18n And L10nAdam Goucher I18N refers to internationalization and L10N refers to localization. The document provides an overview of these concepts and gives recommendations for implementing them technically. It defines internationalization as enabling an application to support different languages and localization as customizing an application for a specific locale. It recommends using Unicode and UTF-8 encoding, resource bundles to externalize strings, and testing translations early and continuously to implement internationalization and localization correctly.
PDT DC015 Chapter 2 Computer System 2017/2018 (e)



PDT DC015 Chapter 2 Computer System 2017/2018 (e)Fizaril Amzari Omar The document discusses different coding schemes used in data processing, including ASCII, EBCDIC, and Unicode. ASCII uses 8 bits to represent characters and can represent 256 characters, while EBCDIC is traditionally used on mainframe computers. Unicode uses 16 or 32 bits and can represent over 65,000 characters to support different languages.
Notes on a Standard: Unicode



Notes on a Standard: UnicodeElena-Oana Tabaranu This document provides an overview of the Unicode standard for character encoding. It discusses the design goals of being universal, consistent, and able to encode all written languages. Unicode represents characters as abstract code points from 0 to 10FFFF in hexadecimal and defines UTF-8, UTF-16, and UTF-32 encoding forms to represent these code points with 8, 16, or 32-bit units. The encoding forms allow lossless transformation between representations. UTF-8 is commonly used in XML documents while UTF-16 and UTF-32 are used by different operating systems.
Unicode 101



Unicode 101davidfstr This document provides an overview of Unicode and character encodings to avoid corrupting international text. It discusses:
- The difference between bytes and characters, noting that characters are often multiple bytes wide and an encoding is needed to interpret byte sequences as character sequences.
- Common mistakes like assuming a default encoding, mixing bytes and characters, and not specifying an encoding which can lead to text being corrupted when read by systems using different encodings.
- Encoding issues that can occur in different languages and file types like text files, HTML, XML, if an encoding is not properly declared or honored.
The key lessons are: you must know the character encoding to interpret byte sequences correctly, and bytes and characters should not be
Character Encoding issue with PHP



Character Encoding issue with PHPRavi Raj This document discusses character encoding issues with PHP and Unicode. It provides an overview of character sets and encodings like UTF-8. When working with Unicode, any part of the technology stack could fail, from editors to version control to databases. UTF-8 is recommended as it is backwards compatible with ASCII and supports Unicode. The document offers tips for getting PHP and CodeIgniter to properly support UTF-8, such as changing config settings and database collations. Fully supporting Unicode across technologies can be challenging but is important.
Understand unicode & utf8 in perl (2)



Understand unicode & utf8 in perl (2)Jerome Eteve I'm not a Unicode Guru, but working with third parties, I often find that a lot of people consistently fail to get the basics right about Unicode and encoding. There must be something esoteric about it. So here's yet another set of slides about Unicode/UTF8 in Perl.
It's not meant to be a comprehensive presentation of all Unicode things in Perl. It's meant to insist on a couple of guidelines and give some pointers to get a good start writing a unicode compliant application and avoiding common issues.
Uncdtalk



UncdtalkBilal Maqbool ツ Unicode is a standard for representing characters across different platforms and languages. It defines coding schemes like UTF-8, UTF-16, and UTF-32 to represent characters as binary values. UTF-16 uses 16-bit values for most characters but introduces surrogate pairs to represent some characters requiring two 16-bit values. UTF-32 uses 32-bit values for all characters. UTF-8 varies the number of bytes per character from 1 to 4 to optimize for English. Unicode aims to support all languages with a single encoding scheme.
SignWriting in Unicode Next



SignWriting in Unicode NextStephen Slevinski Updated for UTC #156, this presentation discusses the Center for Sutton Movement Writing's proposal for the full script support of Sutton SignWriting in Unicode.
Python



PythonDr. SURBHI SAROHA This document provides an overview of the Python programming language. It describes what Python is, how it can be used for web development, software development, mathematics, and system scripting. It also covers Python's syntax features like indentation, variables, comments, and data types. Key reasons for using Python include its ability to run on different platforms, simple English-like syntax, and support for procedural, object-oriented, and functional programming.
Introduction to W3C I18N Best Practices



Introduction to W3C I18N Best PracticesGopal Venkatesan This document provides an introduction to internationalization best practices. It discusses internationalization vocabulary, common problems encountered like encoding issues, and internationalization support in Java and PHP. Key topics covered include Unicode, locales, formatting numbers and dates, and using resource bundles to externalize strings.
Unicode and kurdish fonts



Unicode and kurdish fontsc_s_halabja what is char glyphs and font?
what is standard Unicode?
arabic and Kurdish Unicode.
how to change Arabic font to Kurdish Unicode.
M.FLORENCE DAYANA WEB DESIGN -Unit 5 XML



M.FLORENCE DAYANA WEB DESIGN -Unit 5 XMLDr.Florence Dayana XML Introduction,Syntax of XML,Well formed XML Documents,XML Document Structure,Document Type Definitions,XML Namespace,XML Schemas,DOM(Document Object Model)
Viewers also liked (20)
X Laran Ax



X Laran AxESPEJO 25 Un hombre se toma el día libre para jugar al golf. Durante el juego, una rana le aconseja sobre qué palos usar, lo que le permite jugar muy bien. La rana luego le dice que vayan a Las Vegas, donde el hombre gana mucho dinero apostando. Más tarde, la rana le dice que se postule como presidente, y sorprendentemente gana. Años después en el cargo, el hombre quiere recompensar a la rana, y ésta le pide un beso, transformándose luego en una hermosa doncella.
Xing Sardegna newsletter gennaio 2010



Xing Sardegna newsletter gennaio 2010Andrea ADSLLOSO Portoghese The newsletter provides an update on the XING Ambassador Program and upcoming events. It discusses the success of events held by Ambassadors around the world in 2009 and introduces new features like paid ticketing to help organize events. It highlights some of the top-attended events in various cities and names the Ambassador of the Month for their contributions. Finally, it previews several official XING events scheduled in January 2010 across different regions.
Xi coneia pucallpa 2010

Xi coneia pucallpa 2010UNFV El documento presenta la información sobre el XI Congreso Nacional de Estudiantes de Ingeniería Agroindustrial que se llevará a cabo del 20 al 24 de setiembre de 2010 en la Universidad Nacional Intercultural de la Amazonía en Pucallpa, Perú. El congreso busca promover el intercambio cultural y científico-tecnológico entre estudiantes de ingeniería agroindustrial de diferentes universidades. Incluye conferencias magistrales, visitas industriales, concursos de proyectos e investigación, y exposiciones sobre tem
Xml holland - XQuery novelties - Geert Josten



Xml holland - XQuery novelties - Geert JostenDaidalos Latest news on Xquery standards: XQuery is gaining popularity. It has been used for many web applications around the world since its release. It is replacing proprietary middleware languages, in particular those for disclosing (XML) databases. The core standard is designed for querying of large collections of XML only, but several additional standards are in progress to get more functionality. Other additions add to the strength and maturity of XQuery as a programming language itself. Learn more? Read the presentation by Geert Josten, one of our Senior Content Engineers, presented last week at XML Holland in the Hardcore XML track.
Xequemate 31



Xequemate 31guestff87a6 A agenda apresenta uma lista de datas entre 27 de Julho e 2 de Agosto de 2009 para discussões sobre outsourcing no Departamento de Vendas Directas.
Place of Ecuador por Ximena Llumiquinga



Place of Ecuador por Ximena LlumiquingaXimena-Llumiquinga Ecuador offers many natural and cultural attractions for visitors to explore including waterfalls, volcanoes such as Pichincha and Chimborazo, beaches, and opportunities to go shopping, visit amusement parks, and enjoy nightlife activities like discos and karaoke. Typical Ecuadorian foods are also highlighted.
Xina Voyage(A De Mello)



Xina Voyage(A De Mello)franchyintercultural Este documento habla sobre la felicidad y el miedo. Explica que la felicidad es nuestra esencia y estado natural, pero que a veces nos apegamos a cosas y personas que creemos nos darán felicidad y esto nos hace sufrir. También dice que el miedo no es innato sino aprendido, y que proviene de recuerdos de situaciones pasadas angustiantes registradas en nuestra memoria.
Xi%20 cto%20menores%20de%20edad%20y%20iii%20cto%20divisiones%20varias%20aire%...



Xi%20 cto%20menores%20de%20edad%20y%20iii%20cto%20divisiones%20varias%20aire%...elarcoestandar Este documento anuncia la convocatoria del XI Campeonato de Andalucía de categorías menores de edad y el III Campeonato de Andalucía de divisiones varias de tiro con arco que se celebrarán en Chiclana, Cádiz. Se proporciona información sobre las categorías, fechas, inscripciones, premios, alojamientos recomendados y programa de actividades.
Xls issues in life sciences ed 12 april 2013



Xls issues in life sciences ed 12 april 2013ayanda hlope The document provides information for teachers regarding practical work in science. It discusses what practical work involves, how it contributes to understanding, the process skills developed, benefits for learning science, challenges, and how to address challenges like a lack of resources. It also covers investigations as the focus of practical work, comparing traditional and new approaches, and how teachers can facilitate learner-centered investigations. Safety procedures for the science laboratory are outlined.
Xii Encuentro Latinoamericano De Educadores



Xii Encuentro Latinoamericano De EducadoresAnaclara Dalla Valle Este documento trata sobre los nativos digitales y la necesidad de reinventar la educación para adaptarse a sus necesidades. Plantea que los estudiantes de hoy son multitareas, consumen y producen contenido en la red, y aprenden de forma convergente y multimedial. Propone una educación expandida donde los docentes sean mediadores y aprendan a enseñar de forma creativa utilizando la tecnología para abrir el mundo a los estudiantes.
Ad
Similar to Xml For Dummies Chapter 6 Adding Character(S) To Xml (20)
Data encryption and tokenization for international unicode



Data encryption and tokenization for international unicodeUlf Mattsson Unicode is an information technology standard for the consistent encoding, representation, and handling of text expressed in most of the world's writing systems. The standard is maintained by the Unicode Consortium, and as of March 2020, it has a total of 143,859 characters, with Unicode 13.0 (these characters consist of 143,696 graphic characters and 163 format characters) covering 154 modern and historic scripts, as well as multiple symbol sets and emoji. The character repertoire of the Unicode Standard is synchronized with ISO/IEC 10646, each being code-for-code identical with the other.
The Unicode Standard consists of a set of code charts for visual reference, an encoding method and set of standard character encodings, a set of reference data files, and a number of related items, such as character properties, rules for normalization, decomposition, collation, rendering, and bidirectional text display order (for the correct display of text containing both right-to-left scripts, such as Arabic and Hebrew, and left-to-right scripts). Unicode's success at unifying character sets has led to its widespread and predominant use in the internationalization and localization of computer software. The standard has been implemented in many recent technologies, including modern operating systems, XML, Java (and other programming languages), and the .NET Framework.
Unicode can be implemented by different character encodings. The Unicode standard defines Unicode Transformation Formats (UTF) UTF-8, UTF-16, and UTF-32, and several other encodings. The most commonly used encodings are UTF-8, UTF-16, and UCS-2 (a precursor of UTF-16 without full support for Unicode)
Unicode Primer for the Uninitiated



Unicode Primer for the UninitiatedLingoport (www.lingoport.com) This document provides an introduction to Unicode and character encoding standards. It explains that Unicode is a character set standard that supports all languages worldwide. It describes different character encoding schemes like UTF-8 and UTF-16 that are used to represent Unicode characters in binary. It highlights issues with older single-byte encodings and the benefits of adopting a Unicode encoding to support globalization.
Software Internationalization Crash Course



Software Internationalization Crash CourseWill Iverson Crash course in software internationalization and localization. Based on Java, but most of the information applicable for all web development.
Lecture_ASCII and Unicode.ppt



Lecture_ASCII and Unicode.pptAlula Tafere Unicode is a character encoding standard that aims to support all languages of the world. It evolved from limitations of earlier standards like ASCII that could only represent English characters. Unicode uses 16-bit or 32-bit encodings to represent over 1 million characters, as opposed to ASCII's 128 characters. Popular Unicode encodings include UTF-8, UTF-16, and UTF-32. The widespread adoption of Unicode has allowed globalization of text and the internet by supporting the simultaneous use of different languages.
Abap slide class4 unicode-plusfiles



Abap slide class4 unicode-plusfilesMilind Patil The document discusses Unicode and file handling topics for an ABAP workshop. It covers characters and encoding, ASCII standards, glyphs and fonts, extended ASCII issues, character sets and code pages, little and big endian formats, Unicode, Unicode transformation formats, Unicode in SAP systems, file interfaces, and error handling for files on application and presentation servers. Unicode provides a unique number for every character to standardize representation across languages, platforms, and programs.
Understanding Character Encodings



Understanding Character EncodingsMobisoft Infotech This document discusses character encodings and provides tips for properly handling encodings in programming. It begins with definitions of characters, scripts, and the need for character sets. It then discusses commonly used character sets like ASCII and Unicode. UTF-8, UTF-16, and UTF-32 encodings are explained as they allow representing all Unicode characters using variable number of bytes. The document concludes with programming language-specific tips and functions for detecting, parsing, and writing encodings in languages like PHP, Java, Objective-C, and C#.
Jun 29 new privacy technologies for unicode and international data standards ...



Jun 29 new privacy technologies for unicode and international data standards ...Ulf Mattsson Protecting the increasing use International Unicode characters is required by a growing number of Privacy Laws in many countries and general Privacy Concerns with private data. Current approaches to protect International Unicode characters will increase the size and change the data formats. This will break many applications and slow down business operations. The current approach is also randomly returning data in new and unexpected languages. New approach with significantly higher performance and a memory footprint can be customizable and fit on small IoT devices.
We will discuss new approaches to achieve portability, security, performance, small memory footprint and language preservation for privacy protecting of Unicode data. These new approaches provide granular protection for all Unicode languages and customizable alphabets and byte length preserving protection of privacy protected characters.
Old Approaches
Major Issues
Protecting the increasing use International Unicode characters is required by a growing number of Privacy Laws in many countries and general Privacy Concerns with private data.
Old approaches to protect International Unicode characters will typically increase the size and change the data formats.
This will break many applications and slow down business operations. This is an example of an old approach that is also randomly returning data in new and unexpected languages
What is Python Interpreter.pptx



What is Python Interpreter.pptxSudhanshiBakre1 The document discusses the Python interpreter, how it works by lexing, parsing, compiling and interpreting code. It also notes that the default encoding for Python source files is UTF-8, which allows use of characters from most languages in strings, comments and identifiers, and that internally the interpreter breaks code into tokens, generates an abstract syntax tree, compiles it into bytecode, and executes the bytecode using a virtual machine.
Encoding Nightmares (and how to avoid them)



Encoding Nightmares (and how to avoid them)Kenneth Farrall This document discusses character encoding and localization nightmares. It begins with examples of encoding issues causing problems like corrupted documents and data loss. It then explains the history of character encoding as the need for encoding non-English languages grew. This led to a "Tower of Babel" effect with different encodings representing different characters. The document outlines the rise of Unicode as a unified standard and provides four rules of thumb to avoid encoding nightmares, such as limiting applications and using UTF-8 encoding when possible. It concludes with tricks and tools for checking, converting, and working with encodings.
EXTENSIBLE MARKUP LANGUAGE BY SAIKIRAN PANJALA



EXTENSIBLE MARKUP LANGUAGE BY SAIKIRAN PANJALASaikiran Panjala XML is a markup language that structures documents by using tags to describe content. It is derived from SGML and allows users to define their own tags for exchanging data across different systems. XML documents use tags to describe data rather than display it like HTML. Documents must follow specific rules to be considered well-formed, including proper nesting of tags. XML is commonly used to transfer data between systems and has advantages like being human-readable and requiring less storage space than other formats.
Unicode



UnicodeAnkit Sharma This document discusses Unicode transformation formats. It explains that computers assign numbers to characters and that older 8-bit encoding systems were limited, causing conflicts when different encodings were used. Unicode provides a unique number for every character to allow for worldwide text interchange. It describes common encoding schemes like UTF-8, UTF-16 and UTF-32 that are used to encode Unicode, along with their characteristics and benefits. The document also lists some examples of where Unicode is used.
Comprehasive Exam - IT



Comprehasive Exam - ITguest6ddfb98 The document discusses different character encoding schemes used in computing, including binary-coded decimal (BCD), extended binary-coded decimal interchange code (EBCDIC), American Standard Code for Information Interchange (ASCII), Unicode, and UTF encodings. It provides details on how each scheme encodes decimal, alphanumeric, and multilingual characters, and compares their relative efficiencies and applications in different systems.
Unicode, PHP, and Character Set Collisions



Unicode, PHP, and Character Set CollisionsRay Paseur In recent years UTF-8 has become the dominant character encoding scheme, supplanting extended ASCII. This has led to an uneasy transition for users of PHP, where the assumption has always been that one character equals one byte. This presentation is for the DC PHP Developers' Community meeting on September 10, 2014. It examines the history of character set encoding and the ways that the PHP community is responding to the transition to UTF-8. Not surprisingly, there are surprises in the process! The slides are derived from the article here:
http://iconoun.com/articles/collisions
Computers and text



Computers and textchitcharonko The document discusses the history of fonts and font technologies. It describes:
- How Apple's choice of 72 pixels per inch resolution for early Macintosh monitors matched printing standards.
- How Postscript became the desktop publishing standard in the 1980s, allowing scalable outline fonts.
- The development of TrueType by Apple and Microsoft as an alternative to Postscript that could render fonts on low-resolution screens.
- How OpenType was later developed to incorporate benefits of Postscript and TrueType, becoming the industry standard.
4.language expert rendering unicode text on ascii editor for indian languages...



4.language expert rendering unicode text on ascii editor for indian languages...EditorJST In this paper we introduce the Language Engine which addresses rendering of Unicode characters on a ASCII supportable editor. Unicode characters are related to Indian regional languages based on their character sets. With the application of Parse Engine, Language Engine and Rules Engine to identify the language and convert from Unicode to ASCII in the target editor to resolve rendering problem, also improvises file size reduction. Parse Engine parses the input text character by character and checks if it is a new text or already parsed. Inference Engine checks the Unicode character and identifies the language. Respective Language Engine is loaded with rules. Rules Engine identifies the corresponding ASCII text to be placed in output. Here Rules stored in Rules Engine are composed of XML formats and comes from manual entry. Input Unicode text can come from any source of input. Finally, the output composed from the output file is pasted on the ASCII editor with the installation of the font renders the correct text.
Using unicode with php



Using unicode with phpElizabeth Smith 1. The document discusses internationalization and Unicode support in PHP, covering topics like encodings, locales, formatting numbers and dates for different languages, and database and browser considerations.
2. It provides an overview of PHP extensions and functions for internationalization, including Intl, mbstring, and Iconv, and discusses their strengths and limitations.
3. Examples of internationalization practices in popular PHP frameworks and applications are examined, highlighting both best practices and common pitfalls.
13001620124_AashishAgarwal_Data representation.text and numbers.pdf



13001620124_AashishAgarwal_Data representation.text and numbers.pdfssusercf82c42 This document discusses data representation in computer networks. It defines data and describes how all data inside computers must be converted to binary form to be processed. It then discusses various forms of data representation including numbers, text, images, audio and video. The document outlines goals of understanding how data is represented and converted to machine language for numbers and text. It provides examples of binary representation of numbers and the ASCII code for representing text characters. Finally, it discusses calculating file sizes based on the number of ASCII characters.
chapter-2.pptx



chapter-2.pptxRithinA1 Computers represent both numeric and non-numeric characters using predefined codes. The ASCII code represents 128 characters using 7 bits, while ASCII-8 extends this to 256 characters using 8 bits. ISCII was developed for Indian languages and allows simultaneous use of English and Indian scripts using 8 bits per character. Unicode is now the universal standard adopted by all platforms that assigns a unique number to every character worldwide for interchange, processing and display of written texts across languages.
How To Build And Launch A Successful Globalized App From Day One Or All The ...



How To Build And Launch A Successful Globalized App From Day One Or All The ...agileware Significant compromises are often made taking a product to market that cause downstream pain—success can mean endless hours re-architecting and retrofitting to go global, get past 508 compliance at universities or integrate partners. The good news is there are freely available technologies and strategies to avoid the pain. Learn from Zimbra’s experiences with ZCS and Zimbra Desktop (an offline-capable AJAX email application) including a checklist of do’s and don’ts and a deep dive into: i18n and l10n, 508 compliance (Americans with Disabilities Act), skinning, templates, time-date formatting and more.
From http://en.oreilly.com/oscon2008/public/schedule/detail/4834
Character sets and alphabets



Character sets and alphabetsRazinaShamim The document discusses different character sets used in computing. It describes the ASCII character set which uses 128 characters and numbers to represent English letters, numbers and symbols. It also discusses the extended character set which includes 255 characters like symbols and international letters. Finally, it introduces Unicode which began in 1989 and aims to support encoding for all languages and alphabets in the world using up to 65,000 characters, grouping related symbols into scripts to serve multiple languages.
Ad
More from phanleson (20)
Learning spark ch01 - Introduction to Data Analysis with Spark



Learning spark ch01 - Introduction to Data Analysis with Sparkphanleson Learning spark ch01 - Introduction to Data Analysis with Spark
References to Spark Course
Course : Introduction to Big Data with Apache Spark : http://ouo.io/Mqc8L5
Course : Spark Fundamentals I : http://ouo.io/eiuoV
Course : Functional Programming Principles in Scala : http://ouo.io/rh4vv
Firewall - Network Defense in Depth Firewalls



Firewall - Network Defense in Depth Firewallsphanleson This document discusses key concepts related to network defense in depth. It defines common terms like firewalls, DMZs, IDS, and VPNs. It also covers techniques for packet filtering, application inspection, network address translation, and virtual private networks. The goal of defense in depth is to implement multiple layers of security and not rely on any single mechanism.
Mobile Security - Wireless hacking



Mobile Security - Wireless hackingphanleson This document discusses wireless security and protocols such as WEP, WPA, and 802.11i. It describes weaknesses in WEP such as vulnerabilities in the RC4 encryption algorithm that allow attacks like dictionary attacks. It introduces WPA as an improvement over WEP that uses stronger encryption keys, protocols like TKIP that change keys dynamically, and AES encryption in 802.11i as stronger alternatives. It also discusses authentication methods like 802.1X that distribute unique keys to each user to address issues with shared keys in WEP.
Authentication in wireless - Security in Wireless Protocols



Authentication in wireless - Security in Wireless Protocolsphanleson The document discusses authentication protocols for wireless devices. It begins by describing the authentication problem and some basic client-server protocols. It then introduces the challenge-response protocol which aims to prevent replay attacks by including a random number in the response. However, this protocol is still vulnerable to man-in-the-middle and reflection attacks. The document proposes improvements like including an identifier in the hashed response to prevent message manipulation attacks. Overall, the document provides an overview of authentication challenges for wireless devices and the development of challenge-response protocols to address these issues.
E-Commerce Security - Application attacks - Server Attacks



E-Commerce Security - Application attacks - Server Attacksphanleson Application Vulnerabilities and Attacks
Vulnerability and Exploits
E-Commerce Security , Application attacks , Server Attacks
Hacking web applications



Hacking web applicationsphanleson Hacking web applications
E-Commerce Security, Hacking Web Applications, SQL injection, XSS, Brute Force Methods
HBase In Action - Chapter 04: HBase table design



HBase In Action - Chapter 04: HBase table designphanleson HBase In Action - Chapter 04: HBase table design
Learning HBase, Real-time Access to Your Big Data, Data Manipulation at Scale, Big Data, Text Mining, HBase, Deploying HBase
HBase In Action - Chapter 10 - Operations



HBase In Action - Chapter 10 - Operationsphanleson HBase In Action - Chapter 10: Operations
Learning HBase, Real-time Access to Your Big Data, Data Manipulation at Scale, Big Data, Text Mining, HBase, Deploying HBase
Hbase in action - Chapter 09: Deploying HBase



Hbase in action - Chapter 09: Deploying HBasephanleson Hbase in action - Chapter 09: Deploying HBase
Learning HBase, Real-time Access to Your Big Data, Data Manipulation at Scale, Big Data, Text Mining, HBase, Deploying HBase
Learning spark ch11 - Machine Learning with MLlib



Learning spark ch11 - Machine Learning with MLlibphanleson Introduction to Big Data with Apache Spark : http://ouo.io/Mqc8L5
Learning spark ch11 - Machine Learning with MLlib
Learning spark ch10 - Spark Streaming



Learning spark ch10 - Spark Streamingphanleson This chapter discusses Spark Streaming and provides an overview of its key concepts. It describes the architecture and abstractions in Spark Streaming including transformations on data streams. It also covers input sources, output operations, fault tolerance mechanisms, and performance considerations for Spark Streaming applications. The chapter concludes by noting how knowledge from Spark can be applied to streaming and real-time applications.
Learning spark ch09 - Spark SQL



Learning spark ch09 - Spark SQLphanleson This chapter discusses Spark SQL, which allows querying Spark data with SQL. It covers initializing Spark SQL, loading data from sources like Hive, Parquet, JSON and RDDs, caching data, writing UDFs, and performance tuning. The JDBC server allows sharing cached tables and queries between programs. SchemaRDDs returned by queries or loaded from data represent the data structure that SQL queries operate on.
Learning spark ch07 - Running on a Cluster



Learning spark ch07 - Running on a Clusterphanleson This chapter discusses running Spark applications on a cluster. It describes Spark's runtime architecture with a driver program and executor processes. It also covers options for deploying Spark, including the standalone cluster manager, Hadoop YARN, Apache Mesos, and Amazon EC2. The chapter provides guidance on configuring resources, packaging code, and choosing a cluster manager based on needs.
Learning spark ch06 - Advanced Spark Programming



Learning spark ch06 - Advanced Spark Programmingphanleson This chapter introduces advanced Spark programming features such as accumulators, broadcast variables, working on a per-partition basis, piping to external programs, and numeric RDD operations. It discusses how accumulators aggregate information across partitions, broadcast variables efficiently distribute large read-only values, and how to optimize these processes. It also covers running custom code on each partition, interfacing with other programs, and built-in numeric RDD functionality. The chapter aims to expand on core Spark concepts and functionality.
Learning spark ch05 - Loading and Saving Your Data



Learning spark ch05 - Loading and Saving Your Dataphanleson The document discusses various file formats and methods for loading and saving data in Spark, including text files, JSON, CSV, SequenceFiles, object files, and Hadoop input/output formats. It provides examples of loading and saving each of these file types in Python, Scala, and Java code. The examples demonstrate how to read data from files into RDDs and DataFrames and how to write RDD data out to files in the various formats.
Learning spark ch04 - Working with Key/Value Pairs



Learning spark ch04 - Working with Key/Value Pairsphanleson Learning spark ch04 - Working with Key/Value Pairs
Course : Introduction to Big Data with Apache Spark : http://ouo.io/Mqc8L5
Course : Spark Fundamentals I : http://ouo.io/eiuoV
Course : Functional Programming Principles in Scala : http://ouo.io/rh4vv
Learning spark ch01 - Introduction to Data Analysis with Spark



Learning spark ch01 - Introduction to Data Analysis with Sparkphanleson Learning spark ch01 - Introduction to Data Analysis with Spark
References to Spark Course
Course : Introduction to Big Data with Apache Spark : http://ouo.io/Mqc8L5
Course : Spark Fundamentals I : http://ouo.io/eiuoV
Course : Functional Programming Principles in Scala : http://ouo.io/rh4vv
Hướng Dẫn Đăng Ký LibertaGia - A guide and introduciton about Libertagia



Hướng Dẫn Đăng Ký LibertaGia - A guide and introduciton about Libertagiaphanleson Hướng Dẫn Đăng Ký LibertaGia - A guide and introduciton about Libertagia
Lecture 1 - Getting to know XML



Lecture 1 - Getting to know XMLphanleson XML FOR DUMMIES
The document is a chapter from the book "XML for Dummies" that introduces XML. It discusses what XML is, including that it is a markup language and is flexible for exchanging data. It also examines common uses of XML such as classifying information, enforcing rules on data, and outputting information in different ways. Additionally, it clarifies what XML is not, namely that it is not just for web pages, not a database, and not a programming language. The chapter concludes by discussing how to build an XML document using editors that facilitate markup and enforce document rules.
Lecture 4 - Adding XTHML for the Web



Lecture 4 - Adding XTHML for the Webphanleson This document discusses the differences between HTML, XML, and XHTML. It covers how XHTML combines the structure of XML with the familiar tags of HTML. Key points include:
- HTML was designed for displaying web pages, XML for data exchange, and XHTML uses HTML tags with XML syntax.
- XML allows custom tags, separates content from presentation, and is self-describing, while HTML focuses on display.
- Converting to XHTML requires following XML syntax rules like closing all tags, using empty element syntax, proper nesting, and lowercase tags and attribute quotes.
Recently uploaded (20)
TrustArc Webinar: Consumer Expectations vs Corporate Realities on Data Broker...



TrustArc Webinar: Consumer Expectations vs Corporate Realities on Data Broker...TrustArc Most consumers believe they’re making informed decisions about their personal data—adjusting privacy settings, blocking trackers, and opting out where they can. However, our new research reveals that while awareness is high, taking meaningful action is still lacking. On the corporate side, many organizations report strong policies for managing third-party data and consumer consent yet fall short when it comes to consistency, accountability and transparency.
This session will explore the research findings from TrustArc’s Privacy Pulse Survey, examining consumer attitudes toward personal data collection and practical suggestions for corporate practices around purchasing third-party data.
Attendees will learn:
- Consumer awareness around data brokers and what consumers are doing to limit data collection
- How businesses assess third-party vendors and their consent management operations
- Where business preparedness needs improvement
- What these trends mean for the future of privacy governance and public trust
This discussion is essential for privacy, risk, and compliance professionals who want to ground their strategies in current data and prepare for what’s next in the privacy landscape.
UiPath Community Berlin: Orchestrator API, Swagger, and Test Manager API



UiPath Community Berlin: Orchestrator API, Swagger, and Test Manager APIUiPathCommunity Join this UiPath Community Berlin meetup to explore the Orchestrator API, Swagger interface, and the Test Manager API. Learn how to leverage these tools to streamline automation, enhance testing, and integrate more efficiently with UiPath. Perfect for developers, testers, and automation enthusiasts!
📕 Agenda
Welcome & Introductions
Orchestrator API Overview
Exploring the Swagger Interface
Test Manager API Highlights
Streamlining Automation & Testing with APIs (Demo)
Q&A and Open Discussion
Perfect for developers, testers, and automation enthusiasts!
👉 Join our UiPath Community Berlin chapter: https://community.uipath.com/berlin/
This session streamed live on April 29, 2025, 18:00 CET.
Check out all our upcoming UiPath Community sessions at https://community.uipath.com/events/.
How analogue intelligence complements AI



How analogue intelligence complements AIPaul Rowe
Artificial Intelligence is providing benefits in many areas of work within the heritage sector, from image analysis, to ideas generation, and new research tools. However, it is more critical than ever for people, with analogue intelligence, to ensure the integrity and ethical use of AI. Including real people can improve the use of AI by identifying potential biases, cross-checking results, refining workflows, and providing contextual relevance to AI-driven results.
News about the impact of AI often paints a rosy picture. In practice, there are many potential pitfalls. This presentation discusses these issues and looks at the role of analogue intelligence and analogue interfaces in providing the best results to our audiences. How do we deal with factually incorrect results? How do we get content generated that better reflects the diversity of our communities? What roles are there for physical, in-person experiences in the digital world?
TrsLabs Consultants - DeFi, WEb3, Token Listing



TrsLabs Consultants - DeFi, WEb3, Token ListingTrs Labs Enter the world of web3 with experienced strategic partner.
Open your business to new opportunities.
Big Data Analytics Quick Research Guide by Arthur Morgan



Big Data Analytics Quick Research Guide by Arthur MorganArthur Morgan This is a Quick Research Guide (QRG).
QRGs include the following:
- A brief, high-level overview of the QRG topic.
- A milestone timeline for the QRG topic.
- Links to various free online resource materials to provide a deeper dive into the QRG topic.
- Conclusion and a recommendation for at least two books available in the SJPL system on the QRG topic.
QRGs planned for the series:
- Artificial Intelligence QRG
- Quantum Computing QRG
- Big Data Analytics QRG
- Spacecraft Guidance, Navigation & Control QRG (coming 2026)
- UK Home Computing & The Birth of ARM QRG (coming 2027)
Any questions or comments?
- Please contact Arthur Morgan at [email protected].
100% human made.
HCL Nomad Web – Best Practices und Verwaltung von Multiuser-Umgebungen



HCL Nomad Web – Best Practices und Verwaltung von Multiuser-Umgebungenpanagenda Webinar Recording: https://www.panagenda.com/webinars/hcl-nomad-web-best-practices-und-verwaltung-von-multiuser-umgebungen/
HCL Nomad Web wird als die nächste Generation des HCL Notes-Clients gefeiert und bietet zahlreiche Vorteile, wie die Beseitigung des Bedarfs an Paketierung, Verteilung und Installation. Nomad Web-Client-Updates werden “automatisch” im Hintergrund installiert, was den administrativen Aufwand im Vergleich zu traditionellen HCL Notes-Clients erheblich reduziert. Allerdings stellt die Fehlerbehebung in Nomad Web im Vergleich zum Notes-Client einzigartige Herausforderungen dar.
Begleiten Sie Christoph und Marc, während sie demonstrieren, wie der Fehlerbehebungsprozess in HCL Nomad Web vereinfacht werden kann, um eine reibungslose und effiziente Benutzererfahrung zu gewährleisten.
In diesem Webinar werden wir effektive Strategien zur Diagnose und Lösung häufiger Probleme in HCL Nomad Web untersuchen, einschließlich
- Zugriff auf die Konsole
- Auffinden und Interpretieren von Protokolldateien
- Zugriff auf den Datenordner im Cache des Browsers (unter Verwendung von OPFS)
- Verständnis der Unterschiede zwischen Einzel- und Mehrbenutzerszenarien
- Nutzung der Client Clocking-Funktion
Massive Power Outage Hits Spain, Portugal, and France: Causes, Impact, and On...



Massive Power Outage Hits Spain, Portugal, and France: Causes, Impact, and On...Aqusag Technologies In late April 2025, a significant portion of Europe, particularly Spain, Portugal, and parts of southern France, experienced widespread, rolling power outages that continue to affect millions of residents, businesses, and infrastructure systems.
Build Your Own Copilot & Agents For Devs



Build Your Own Copilot & Agents For DevsBrian McKeiver May 2nd, 2025 talk at StirTrek 2025 Conference.
Rusty Waters: Elevating Lakehouses Beyond Spark



Rusty Waters: Elevating Lakehouses Beyond Sparkcarlyakerly1 Spark is a powerhouse for large datasets, but when it comes to smaller data workloads, its overhead can sometimes slow things down. What if you could achieve high performance and efficiency without the need for Spark?
At S&P Global Commodity Insights, having a complete view of global energy and commodities markets enables customers to make data-driven decisions with confidence and create long-term, sustainable value. 🌍
Explore delta-rs + CDC and how these open-source innovations power lightweight, high-performance data applications beyond Spark! 🚀
Splunk Security Update | Public Sector Summit Germany 2025



Splunk Security Update | Public Sector Summit Germany 2025Splunk Splunk Security Update
Sprecher: Marcel Tanuatmadja
HCL Nomad Web – Best Practices and Managing Multiuser Environments



HCL Nomad Web – Best Practices and Managing Multiuser Environmentspanagenda Webinar Recording: https://www.panagenda.com/webinars/hcl-nomad-web-best-practices-and-managing-multiuser-environments/
HCL Nomad Web is heralded as the next generation of the HCL Notes client, offering numerous advantages such as eliminating the need for packaging, distribution, and installation. Nomad Web client upgrades will be installed “automatically” in the background. This significantly reduces the administrative footprint compared to traditional HCL Notes clients. However, troubleshooting issues in Nomad Web present unique challenges compared to the Notes client.
Join Christoph and Marc as they demonstrate how to simplify the troubleshooting process in HCL Nomad Web, ensuring a smoother and more efficient user experience.
In this webinar, we will explore effective strategies for diagnosing and resolving common problems in HCL Nomad Web, including
- Accessing the console
- Locating and interpreting log files
- Accessing the data folder within the browser’s cache (using OPFS)
- Understand the difference between single- and multi-user scenarios
- Utilizing Client Clocking
Manifest Pre-Seed Update | A Humanoid OEM Deeptech In France



Manifest Pre-Seed Update | A Humanoid OEM Deeptech In Francechb3 The latest updates on Manifest's pre-seed stage progress.
AI Changes Everything – Talk at Cardiff Metropolitan University, 29th April 2...



AI Changes Everything – Talk at Cardiff Metropolitan University, 29th April 2...Alan Dix Talk at the final event of Data Fusion Dynamics: A Collaborative UK-Saudi Initiative in Cybersecurity and Artificial Intelligence funded by the British Council UK-Saudi Challenge Fund 2024, Cardiff Metropolitan University, 29th April 2025
https://alandix.com/academic/talks/CMet2025-AI-Changes-Everything/
Is AI just another technology, or does it fundamentally change the way we live and think?
Every technology has a direct impact with micro-ethical consequences, some good, some bad. However more profound are the ways in which some technologies reshape the very fabric of society with macro-ethical impacts. The invention of the stirrup revolutionised mounted combat, but as a side effect gave rise to the feudal system, which still shapes politics today. The internal combustion engine offers personal freedom and creates pollution, but has also transformed the nature of urban planning and international trade. When we look at AI the micro-ethical issues, such as bias, are most obvious, but the macro-ethical challenges may be greater.
At a micro-ethical level AI has the potential to deepen social, ethnic and gender bias, issues I have warned about since the early 1990s! It is also being used increasingly on the battlefield. However, it also offers amazing opportunities in health and educations, as the recent Nobel prizes for the developers of AlphaFold illustrate. More radically, the need to encode ethics acts as a mirror to surface essential ethical problems and conflicts.
At the macro-ethical level, by the early 2000s digital technology had already begun to undermine sovereignty (e.g. gambling), market economics (through network effects and emergent monopolies), and the very meaning of money. Modern AI is the child of big data, big computation and ultimately big business, intensifying the inherent tendency of digital technology to concentrate power. AI is already unravelling the fundamentals of the social, political and economic world around us, but this is a world that needs radical reimagining to overcome the global environmental and human challenges that confront us. Our challenge is whether to let the threads fall as they may, or to use them to weave a better future.
Semantic Cultivators : The Critical Future Role to Enable AI



Semantic Cultivators : The Critical Future Role to Enable AIartmondano By 2026, AI agents will consume 10x more enterprise data than humans, but with none of the contextual understanding that prevents catastrophic misinterpretations.
Social Media App Development Company-EmizenTech



Social Media App Development Company-EmizenTechSteve Jonas EmizenTech is a trusted Social Media App Development Company with 11+ years of experience in building engaging and feature-rich social platforms. Our team of skilled developers delivers custom social media apps tailored to your business goals and user expectations. We integrate real-time chat, video sharing, content feeds, notifications, and robust security features to ensure seamless user experiences. Whether you're creating a new platform or enhancing an existing one, we offer scalable solutions that support high performance and future growth. EmizenTech empowers businesses to connect users globally, boost engagement, and stay competitive in the digital social landscape.
Designing Low-Latency Systems with Rust and ScyllaDB: An Architectural Deep Dive



Designing Low-Latency Systems with Rust and ScyllaDB: An Architectural Deep DiveScyllaDB Want to learn practical tips for designing systems that can scale efficiently without compromising speed?
Join us for a workshop where we’ll address these challenges head-on and explore how to architect low-latency systems using Rust. During this free interactive workshop oriented for developers, engineers, and architects, we’ll cover how Rust’s unique language features and the Tokio async runtime enable high-performance application development.
As you explore key principles of designing low-latency systems with Rust, you will learn how to:
- Create and compile a real-world app with Rust
- Connect the application to ScyllaDB (NoSQL data store)
- Negotiate tradeoffs related to data modeling and querying
- Manage and monitor the database for consistently low latencies
Cyber Awareness overview for 2025 month of security



Cyber Awareness overview for 2025 month of securityriccardosl1 Cyber awareness training educates employees on risk associated with internet and malicious emails
tecnologias de las primeras civilizaciones.pdf



tecnologias de las primeras civilizaciones.pdffjgm517 descaripcion detallada del avance de las tecnologias en mesopotamia, egipto, roma y grecia.
Xml For Dummies Chapter 6 Adding Character(S) To Xml
- 1. XML FOR DUMMIESBook author: Lucinda Dykes and Ed TittelSlides Prepared by Cong TanPart 2 : XML and The WebChapter 6: Adding Character(s) to XML.
- 2. ContentsAbout Character Encodings.Introducing Unicode.Character Sets, Fonts, Scripts, and Glyphs.For Each Character, a Code.Key Character Sets.Using Unicode Character s.Finding Character Entity Information.
- 3. 1. About Character Encodings. Clearly, the trend is toward longer bit strings to encode character data, so size does matter when representing character data. Here’s why: A 7-bit string can represent a maximum of 27 , or 128, different characters… An 8-bit string can represent a maximum of 28 , or 256, different characters, including everything a 7-bit encoding can handle, and leaves room for what some experts call higher-order characters. A 16-bit string can represent a maximum of 216 , or 56.536, different characters. Some modern computers still use 8-bit encodings to represent most character data. Windows NT, Window 2000, and Window XP, however, use 16-bit encoding for internal representations of text and most global solutions use 16-bit encoding to support all possible languages and characters.
- 4. 2. Introducing Unicode.Today, Unicode defines just over 96.000 different character codes. The default, character set used to encode all HTML document on the Web. Many people —including numerous XML experts —refer to the XML character set as “Unicode”. Note that XML 1.0, 2nd Edition references Unicode 2.0 and 3.0, and XML 1.1 references Unicode 4.0, whereas the 1st Edition of XML 1.0 references only Unicode 2.0… For more information about Unicode characters, symbols, history, and the current standard, you can find a plethora of information at the Unicode consortium’s Web site at www.unicode.org.
- 5. 3. Character Sets, Fonts, Scripts, and Glyphs.To see what’s in XML scripts that 7-or 8-bit character encodings can’t cover —which means special symbols or non-Roman alphabets —you’ll need a few extra local ingredients: A character set that matches the script you’re trying to read and display. Software that understands the character set for the script. An electronic font that allows the character set to be displayed on screen. All these ingredients are necessary to work with alternate character sets. Character sets represent a mapping from a script to a set of corresponding numeric character codes. Fonts represent a collection of glyphs for the numeric character codes in a character set. Finally, to create text to match the alphabets used in a script, you need an input tool —such as a text or XML editor —that can work with the character set and its corresponding font.
- 6. 4. For Each Character, a Code.In the Unicode/ISO 10646 character set, individual characters correspond to specific 16-bit numbers. Numeric entities take one of two forms, decimal or hexadecimal. For example: Each numeric entity in XML has an associated text encoding. If some specific encoding is not defined in a numeric entity’s definition, the default is an encoding called UTF-8, which stands for Unicode Transformation Format, 8-bit form. UTF and UCS are mechanisms for implementing Unicode. UTF versions include UTF-32, UTF-16,UTF-8,UTF-EBCDIC, and UTF-7 UCS versions include UCS-4 and UCS-2. UTF-16 used mainly for internal processing. က<!-- &# indicates a decimal number -->ༀ<!-- &#x indicates a hexadecimal number-->
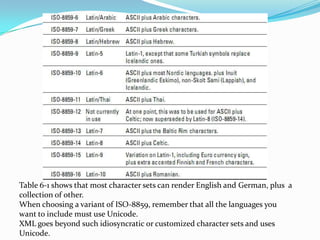
- 7. 5. Key Character Sets.Most computers today use some variant of the ASCII, an 8-bit character set that handles the basic Roman alphabet used for English, along with punctuation, numbers, and simple symbols. Most European languages match standard ASCII values from 0 to 127 and go on from there to define alternate mappings between character codes and local script characters for values from 128 to 255.Non-Roman alphabets, such as Hebrew, Japanese, and Thai, depend on special character sets that include basic ASCII(0-127, or 0-255) . A listing of character sets built around the ASCII framework appears in Table 6-1.
- 9. Table 6-1 shows that most character sets can render English and German, plus a collection of other.When choosing a variant of ISO-8859, remember that all the languages you want to include must use Unicode.XML goes beyond such idiosyncratic or customized character sets and uses Unicode.
- 10. 6. Using Unicode Characters. So do many modern word processors —for instance, Word 97, and later versions support a format called encoded text that uses Unicode encoding. If you don’t have already access to such tools and want to save XML file in Unicode format, you must use a conversion tool. Several different tools , both freeware and commercial products, are available, depending on your OS. Widely used tools such as Netscape Navigator(version 4.1 or newer) and IE(version 5 or newer) can handle most ISO-8859 variants. If you want to use an alternate character encoding, you must identify that encoding in your XML document’s prolog as follows: Note that XML parsers are required to support only UTF-8 and UTF-16 encodings, so the encoding attribute in an XML document prolog might not work with all such tools.<?xml version=”1.0” encoding=”ISO-8859-9”?>
- 11. 7. Finding Character Entity Information. Resource : The Unicode Standard, version 4.0 or you can also find plenty of encoding information online, for example: www.unicode.org/ucd/ You’ll also find the XHTML entity lists useful in this context: Latin-1: www.w3.org/TR/xhtml1/DTD/xhtml-lat1.ent. Special: www.w3.org/TR/xhtml1/DTD/xhtml-special.ent Symbols: www.w3.org/TR/xhtml1/DTD/xhtml-symbol.ent
- 12. THE END











